

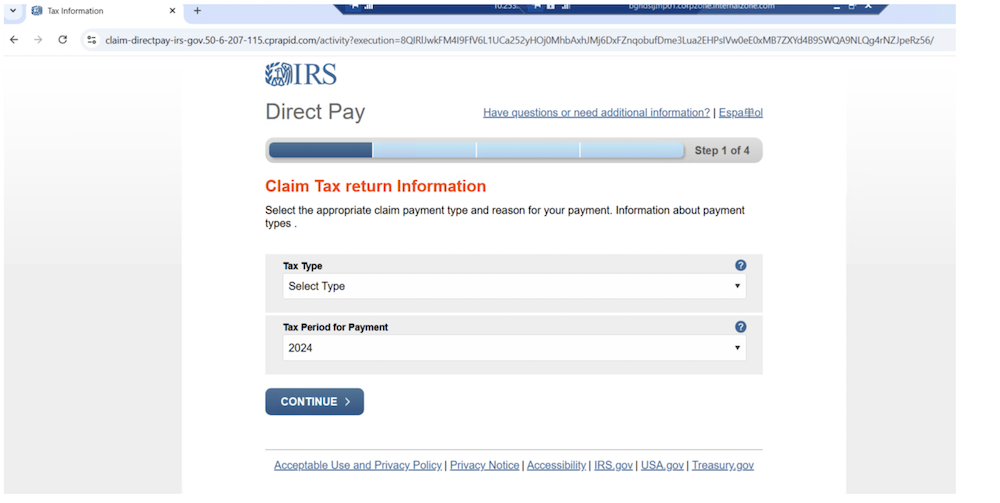
 McAfee Blogs
McAfee Blogs
It’s been a big year for big data breaches. Billions of records on millions of people have been exposed at an estimated cost of nearly $10 trillion dollars to people and businesses alike worldwide.[i]
While we still have a few weeks in the year left to go, here’s a roundup of five of the most noteworthy breaches this year. And while you can’t prevent big data breaches from happening, you can still take several preventive steps to protect yourself from the fallout. We’ll cover them here too.
The National Public Data (NPD) breach
News of a major data breach that involved nearly three billion records came to light over the summer from a somewhat unusual source — a class-action complaint filed in Florida.
The complaint concerned National Public Data (NPD), a company that provides background checks. Per their website, “[NPD obtains] information from various public record databases, court records, state and national databases, and other repositories nationwide.”
The complaint alleged that NPD was hit by a data breach in or around April 2024. [ii] The complaint filed in the U.S. District Court further alleges:
- The company had sensitive info breached, such as full names; current and past addresses spanning at least the last three decades); Social Security numbers; info about parents, siblings, and other relatives (including some who have been deceased for nearly 20 years); and other personal info.
- The company “scraped” this info from non-public sources. This info was collected without the consent of the person who filed the complaint and the billions of others who might qualify to join in the class action complaint.
- The company “assumed legal and equitable duties to those individuals to protect and safeguard that information from unauthorized access and intrusion.”
Typically, companies self-report these breaches, thanks to regulations and legislation that require them to do so in a timely manner. That way, initial word of breaches reaches customers through emails, news reports, and sometimes through notifications to certain state attorney generals.
In this case, it appeared that no notices were immediately sent to potential victims.
As to how the primary plaintiff discovered the breach, he “received a notification from his identity theft protection service provider notifying him that his [personal info] was compromised as a direct result of the ‘nationalpublicdata.com’ breach …” (And you can certainly add online protection software to the list of ways you can find out about a data breach before a company notifies you.)
Further, in June, The Register reported that a hacker group by the name of USDoD claimed it hacked the records of 2.9 billion people and put them up for sale on the dark web.[iii] The price tag, U.S. $3.5 million. The group further claimed that the records include U.S., Canadian, and British citizens.
The Ticketmaster breach
Just how big was the Ticketmaster data breach? It appears that over a half-billion people might have had their personal info compromised.
Ticketmaster’s parent company, Live Nation Entertainment, first announced the breach in late May. The company said that it had identified “unauthorized activity” from April 2 to May 18, 2024.
Soon after, the noted hacking group ShinyHunters claimed responsibility for the breach.[iv] According to the hackers, their 1.3 terabyte haul of data includes 560 million people — along with a mix of their names, addresses, email addresses, phone numbers, order information, and partial payment card details. They allegedly posted that info for sale on the dark web in late May.[v]
Live Nation then began notifying potential victims by physical mail, stating:
“The personal information that may have been obtained by the third party may have included your name, basic contact information, and <extra>.”
Per a support document posted by Ticketmaster, the <extra> part varied by individual. Depending on what was compromised, that might have included “email, phone number, encrypted credit card information as well as some other personal information provided to [Ticketmaster].”[vi]
A breach at insurance and financial tech vendor, Infosys McCamish Systems
Also affecting millions of people in 2024, a breach at Infosys McCamish Systems (IMS), a company that provides solutions and services to insurance companies and financial institutions. Per an announcement from IMS[vii], the company,
“[D]etermined that unauthorized activity occurred between October 29, 2023, and November 2, 2023. Through the investigation, it was also determined that data was subject to unauthorized access and acquisition.”
There’s a good chance you haven’t heard of IMS before reading this article. Yet to put the attack in perspective, it affected people who hold accounts with companies like Bank of America, Oceanview Life and Annuity Company, Fidelity Investments Life Insurance, Newport Group, and Union Labor Life Insurance.
Also per IMS, the full run of personal info swept up in the attack included:
| · Social Security Numbers
· Dates of birth
· Medical records
· Biometric data
· Email address and passwords
· Usernames and passwords
|
· Driver’s license and state ID numbers
· Financial account info
· Payment card info
· Passport numbers
· Tribal ID numbers
· US military ID numbers
|
Notifications went out to potential victims in several ways and at several times. Bank of America sent notices to 50,000 people in February, alerting them that their info was compromised by an unidentified third party.[viii] Fidelity Investments Life Insurance notified 28,000 potential victims in March.[ix] In late June, IMS began contacting the six million potential victims overall — eight months after the date of the initial attack.[x]
A breach at a U.S. debt collector — Financial Business and Consumer Solutions
The second breach involves (FBCS), a bonded collection agency based on the U.S. east coast. On February 26, 2024, the company noted unauthorized access to their systems, which covered a twelve-day period starting on February 14.[xi] In an April notice of a “data event,” FBCS stated that people might have had the following info compromised:
“[C]onsumer name, address, date of birth, Social Security number, driver’s license number, other state identification number, medical claims information, provider information, and clinical information (including diagnosis/conditions, medications, and other treatment information), and/or health insurance information.”
FBCS went on to say that the compromised info varied from person to person.
Initially, the scope of the breach appeared to approach two million victims.[xii] Several updated filings continued to increase that number. At last reporting, the figure had ballooned to more than four million people affected.[xiii]
The AT&T breach
In April, mobile carrier AT&T learned that hackers had stolen the call and text logs of nearly all its customers, estimated at nearly 100 million people. That further included customers who used Cricket, Boost Mobile, and Consumer Cellular, which are mobile virtual network operators (MVNOs) that use AT&T’s network.
The compromised data covered a period between May 1, 2022, and October 31, 2022, with a small number of records from January 2, 2023, also affected. According to AT&T, hackers gained access through a third-party cloud platform account.[xiv]
The stolen data revealed the phone numbers customers communicated with, along with the frequency and total duration of calls and texts for specific periods. In this way, the breach affected more than just customers of AT&T — it affected anyone who may have called or texted with an AT&T customer.
However, AT&T assured customers that the content of calls or texts, timestamps, Social Security numbers, dates of birth, or other personal details were not compromised.
Of concern, a determined hacker with access to the data could infer a lot from these logs, such as businesses and people customers regularly speak with. In turn, this could fuel phishing scams by giving them extra credibility if the scammer poses as the businesses and people involved.
How to protect yourself against data breaches
These breaches show the risks and frustrations that we, as consumers, face in the wake of such attacks. It often takes months before we receive any kind of notification. And of course, that gap gives hackers plenty of time to do their damage. They might use stolen info to commit identity crimes, or they might sell it to others who’ll do the same. Sometimes, we’re in the dark about a data breach until we get hit with a case of identity theft ourselves.
Indeed, plenty of breaches go unreported or under-reported. Even so, word of an attack that affects you might take some time to reach you. With that, preventative measures offer the strongest protection from data breaches.
To fully cover yourself, we suggest the following:
Check your credit, consider a security freeze, and get ID theft protection.
With your personal info potentially on the dark web, strongly consider taking preventive measures now. Checking your credit and getting identity theft protection can help keep you safer in the aftermath of a breach. Further, a security freeze can help prevent identity theft if you spot any unusual activity. You can get all three in place with our McAfee+ Advanced or Ultimate plans. Features include:
-
Credit monitoring keeps an eye on changes to your credit score, report, and accounts with timely notifications and guidance so you can take action to tackle identity theft.
-
Security freeze protects you proactively by stopping unauthorized access to existing credit card, bank, and utility accounts or from new ones being opened in your name. And it won’t affect your credit score.
-
ID Theft & Restoration Coverage gives you $2 million in identity theft coverage and identity restoration support if it is determined you’re a victim of identity theft. This way, you can cover losses and repair your credit and identity with a licensed recovery expert.
Monitor your identity and transactions.
Breaches and leaks can lead to exposure, particularly on dark web marketplaces where personal info gets bought and sold. Our Identity Monitoring can help notify you quickly if that happens. It keeps tabs on everything from email addresses to IDs and phone numbers for signs of breaches. If spotted, it offers advice that can help secure your accounts before they’re used for identity theft.
Also in our McAfee+ plans, you’ll find several types of transaction monitoring that can spot unusual activity. These features track transactions on credit cards and bank accounts — along with retirement accounts, investments, and loans for questionable transactions. Finally, further features can help prevent a bank account takeover and keep others from taking out short-term payday loans in your name.
Keep an eye out for phishing attacks.
With some personal info in hand, bad actors might seek out more. They might follow up a breach with rounds of phishing attacks that direct you to bogus sites designed to steal your personal info — either by tricking you into providing it or by stealing it without your knowledge. So look out for phishing attacks, particularly after breaches.
If you are contacted by a company, make certain the communication is legitimate. Bad actors might pose as them to steal personal info. Don’t click or tap on links sent in emails, texts, or messages. Instead, go straight to the appropriate website or contact them by phone directly.
For even more security, you can use our Text Scam Detector. It scans links in texts and lets you know if it’s risky. And if you accidentally click or tap a bad link, it blocks the sketchy sites they can take you to.
Update your passwords and use two-factor authentication.
Changing your password is a strong preventive measure. Strong and unique passwords are best, which means never reusing your passwords across different sites and platforms. Using a password manager helps you keep on top of it all, while also storing your passwords securely.
While a strong and unique password is a good first line of defense, enabling two-factor authentication across your accounts helps your cause by providing an added layer of security. It’s increasingly common to see nowadays, where banks and all manner of online services will only allow access to your accounts after you’ve provided a one-time passcode sent to your email or smartphone.
[i] https://www.statista.com/forecasts/1280009/cost-cybercrime-worldwide
[ii]https://www.bloomberglaw.com/public/desktop/document/HofmannvJericoPicturesIncDocketNo024cv61383SDFlaAug012024CourtDoc?doc_id=X6S27DVM6H69DSQO6MTRAQRIVBS
[iii] https://www.theregister.com/2024/06/03/usdod_data_dump/
[iv] https://www.pcmag.com/news/ticketmaster-confirms-user-email-addresses-phone-numbers-stolen-in-hack
[v] https://www.sec.gov/Archives/edgar/data/1335258/000133525824000081/lyv-20240520.htm
[vi] https://help.ticketmaster.com/hc/en-us/articles/26110487861137-Ticketmaster-Data-Security-Incident
[vii] https://www.infosysbpm.com/mccamish/about/notice-of-cybersecurity-incident.html
[viii] https://www.bankinfosecurity.com/bank-america-responds-to-breach-a-4487
[ix] https://www.securityweek.com/fidelity-investments-notifying-28000-people-of-data-breach/
[x] https://www.maine.gov/agviewer/content/ag/985235c7-cb95-4be2-8792-a1252b4f8318/b152fd39-9f84-4ca5-a149-d20b94ed8ef6.html
[xi] https://www.fbcs-inc.com/cyber-incident/
[xii] https://www.maine.gov/agviewer/content/ag/985235c7-cb95-4be2-8792-a1252b4f8318/5fe1ede5-aafd-4da2-b1a4-0057a6cdadc6.shtml
[xiii] https://www.maine.gov/agviewer/content/ag/985235c7-cb95-4be2-8792-a1252b4f8318/7e6ff931-a035-480f-a977-e11a8af7f768.html
[xiv] https://about.att.com/story/2024/addressing-illegal-download.html
The post 2024 Data Breaches Wrapped appeared first on McAfee Blog.
 “Follow” button
“Follow” button






















 AI 300 Series processors
AI 300 Series processors





