
They came by phone, by text, by email, and they even weaseled their way into people’s love lives—an entire host of scams that we covered here in our blogs throughout the year.
Today, we look back, picking five noteworthy scams that firmly established new trends, along with one in particular that gives us a hint at the face of scams to come.
Let’s start it off with one scam that pinged plenty of phones over the spring and summer: those toll road texts.
It was the hot new scam of 2025 that increased by 900% in one year: the toll road scam.
There’s a good chance you got a few of these this year,scam texts that say you have an unpaid tab for tolls and that you need to pay right away. And as always, they come with a handy link where you can pay up and avoid that threat of a “late fee.”
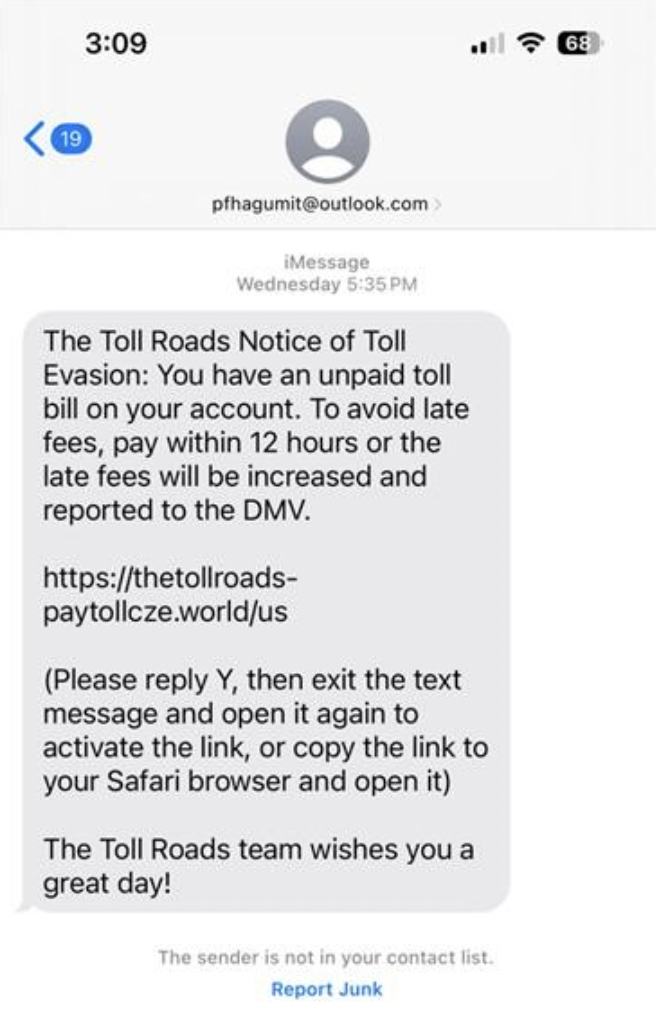
Of course, links like those took people to phishing sites where people gave scammers their payment info, which led to fraudulent charges on their cards. In some instances, the scammers took it a step further by asking for driver’s license and Social Security numbers, key pieces of info for big-time identity theft.
Who knows what the hot new text scam for 2026 will be, yet here are several ways you can stop text scams in their tracks, no matter what form they take:
Don’t click on any links in unexpected texts (or respond to them, either). Scammers want you to react quickly, but it’s best to stop and check it out.
Check to see if the text is legit. Reach out to the company that apparently contacted you using a phone number or website you know is real—not the info from the text.
Get our Scam Detector. It automatically detects scams by scanning URLs in your text messages. If you accidentally tap or click? Don’t worry, it blocks risky sites if you follow a suspicious link.
It started with a DM. And a few months later, it cost her $1,200.
Earlier this year, we brought you the story of 25-year-old computer programmer Maggie K. who fell for a romance scam on Instagram. Her story played out like so many. When she and her online boyfriend finally agreed to meet in person, he claimed he missed his flight and needed money to rebook. Desperate to finally see him, she sent the money and never heard from him again.
But here’s the twist—he wasn’t real in the first place.
When she reported the scam to police, they determined his images were all made with AI. In Maggie’s words, “That was the scariest part—I had trusted someone who never even existed.”
Maggie isn’t alone. Our own research earlier this year revealed that more than half (52%) of people have been scammed out of money or pressured to send money or gifts by someone they met online.
Moreover, we found that scammers have fueled those figures with the use of AI. Of people we surveyed, more than 1 in 4 (26%) said they—or someone they know—have been approached by an AI chatbot posing as a real person on a dating app or social media.
We expect this trend will only continue, as AI tools make it easier and more efficient to pull off romance scams on an increasingly larger scale.
Even so, the guidelines for avoiding romance scams remain the same:
The job offer sounds simple enough … go online, review products, like videos, or do otherwise simple tasks and get paid doing it—until it’s time to get paid.
It’s a new breed of job scam that took root this spring, one where victims found themselves “paying to get paid.”
The FTC dubbed these scams as “gamified job scams” or “task scams.” Given the way these scams work, the naming fits.
It starts with a text or direct message from a “recruiter” offering work with the promise of making good money by “liking” or “rating” sets of videos or product images in an app, all with the vague purpose of “product optimization.” With each click, you earn a “commission” and see your “earnings” rack up in the app. You might even get a payout, somewhere between $5 and $20, just to earn your trust.
Then comes the hook.
Like a video game, the scammer sweetens the deal by saying the next batch of work can “level up” your earnings. But if you want to claim your “earnings” and book more work, you need to pay up. So you make the deposit, complete the task set, and when you try to get your pay the scammer and your money are gone. It was all fake.
This scam and others like it fall right in line with McAfee data that uncovered a spike in job-related scams of 1,000% between May and July,which undoubtedly built on 2024’s record-setting job scam losses of $501 million.
A proper recruiter will reach out to you by email or via a job networking site. Moreover, per the FTC, any job that pays you to “like” or “rate” content is against the law. That alone says it’s a scam.
In the case of job offers in general, look up the company. Check out their background and see if it matches up with the job they’re pitching. In the U.S., The Better Business Bureau (BBB) offers a list of businesses you can search.
Any case where you’re asked to pay to up front, with any form of payment, refuse, whether that’s for “training,” “equipment,” or more work. It’s a sign of a scam.
Prince Harry, Taylor Swift, and now the Today show’s Al Roker, too, they’ve all found themselves as the AI-generated spokesperson for deepfake scams.
In the past, a deepfake Prince Harry pushed bogus investments, while another deepfake of Taylor Swift hawked a phony cookware deal. Then, this spring, a deepfake of Al Roker used his image and voice to promote a bogus hypertension cure—claiming, falsely, that he had suffered “a couple of heart attacks.”
The fabricated clip appeared on Facebook, which appeared convincing enough to fool plenty of people, including some of Roker’s own friends. “I’ve had some celebrity friends call because their parents got taken in by it,” said Roker.
While Meta quickly removed the video from Facebook after being contacted by TODAY, the damage was done. The incident highlights a growing concern in the digital age: how easy it is to create—and believe—convincing deepfakes.
Roker put it plainly, “We used to say, ‘Seeing is believing.’ Well, that’s kind of out the window now.”
In all, this stands as a good reminder to be skeptical of celebrity endorsements on social media. If public figure fronts an apparent deal for an investment, cookware, or a hypertension “cure” in your feed, think twice. And better yet, let our Scam Detector help you spot what’s real and what’s fake out there.
And to close things out, a look at some recent news, which also serves as a look ahead.
Last September, researchers spotted something unseen before:a cyberattack almost entirely run by agentic AI.
What is Agentic AI?
Definition: Artificial intelligence systems that can independently plan, make decisions, and work toward specific goals with minimal human intervention; in this way, it executes complex tasks by adapting to new info and situations on its own.
Reported by AI researcher Anthropic, a Chinese state-sponsored group allegedly used the company’s Claude Code agent to automate most of an espionage campaign across nearly thirty organizations. Attackers allegedly bypassed guardrails that typically prevent such malicious use with jailbreaking techniques, which broke down their attacks into small, seemingly innocent tasks. That way, Claude orchestrated a large-scale attack it wouldn’t otherwise execute.
Once operational, the agent performed reconnaissance, wrote exploit code, harvested credentials, identified high-value databases, created backdoors, and generated documentation of the intrusion. By Anthropic’s estimate, they completed 80–90% of the work without any human involvement.
According to Anthropic: “At the peak of its attack, the AI made thousands of requests, often multiple per second—an attack speed that would have been, for human hackers, simply impossible to match.”
We knew this moment was coming, and now the time has arrived: what once took weeks of human effort to execute a coordinated attack now boils down to minutes as agentic AI does the work on someone’s behalf.
In 2026, we can expect to see more attacks led by agentic AI, along with AI-led scams as well, which raises an important question that Anthropic answers head-on:
If AI models can be misused for cyberattacks at this scale, why continue to develop and release them? The answer is that the very abilities that allow Claude to be used in these attacks also make it crucial for cyber defense. When sophisticated cyberattacks inevitably occur, our goal is for Claude—into which we’ve built strong safeguards—to assist cybersecurity professionals to detect, disrupt, and prepare for future versions of the attack.
That gets to the heart of security online: it’s an ever-evolving game. As new technologies arise, those who protect and those who harm one-up each other in a cycle of innovation and exploits. As we’re on the side of innovation here, you can be sure we’ll continue to roll out protections that keep you safer out there. Even as AI changes the game, our commitment remains the same.
We’re taking a little holiday break here and we’ll be back with our weekly roundups again in 2026. Looking forward to catching up with you then and helping you stay safer in the new year.
The post This Year in Scams: A 2025 Retrospective, and a Look Ahead at 2026 appeared first on McAfee Blog.

If you’re in the market for insurance right now, keep an eye out for scammers in the mix. They’re out in full force once again this open enrollment season.
As people across the U.S. sign up for, renew, or change their health insurance plans, scammers want to cash in as people rush to get their coverage set. And scammers have several factors working in their favor.
For starters, many people find the insurance marketplace confusing, frustrating, and even intimidating, all feelings that scammers can take advantage of. Moreover, concerns about getting the right level of coverage at an affordable price also play into the hands of scammers.
Amidst all this uncertainty and time pressure, health insurance scams crop up online. Whether under the guise of helping people navigate the complex landscape or by offering seemingly low-cost quotes, scammers prey on insurance seekers by stealing their personal information, Social Security numbers, and money.
According to the FBI, health insurance scams cost families millions each year. In some cases, the costs are up front. People pay for fraudulent insurance and have their personal info stolen. And for many, the follow-on costs are far worse, where victims go in for emergency care and find that their treatment isn’t covered—leaving them with a hefty bill.
Like so many of the scams we cover here in our blogs, you can spot health insurance scams relatively quickly once you get to know their ins and outs.
Here’s how some of those scams can play out.
Some are “one and done scams” where the scammer promises a policy or service and then disappears after stealing money and personal info—much like an online shopping scam. It’s a quick and dirty hit where scammers quickly get what they want by reaching victims the usual ways, such as through texts, emails, paid search results, and social media. In the end, victims end up on a phishing site where they think they’re locking in a good deal but handing over their info to scammers instead.
Other scams play a long con game, milking victims for thousands and thousands of dollars over time. The following complaint lodged by one victim in Washington state provides a typical example:
A man purchased a plan to cover himself, his wife, and his two children, only to learn there was no coverage. He was sold a second policy, with the same result, and offered a refund if he purchased a third policy. When he filed a complaint, his family still had no coverage, and he was seeking a refund for more than $20,000 and reimbursement for $55,000 in treatments and prescriptions he’d paid out of pocket.
Scams like these are known as ghost broker scams where scammers pose as insurance brokers who take insurance premiums and pocket the money, leaving victims thinking they have coverage when they don’t. In some cases, scammers initially apply for a genuine policy with a legitimate carrier, only to cancel it later, while still taking premiums from the victim as their “broker.” Many victims only find out that they got scammed when they attempt to file a claim.
Another type of scam comes in the form of policy cancellation scams. These work like any number of other account-based scams, where a scammer pretends to be a customer service rep at a bank, utility, or credit card company. In the insurance version of it, scammers email, text, or call with some bad news—the person’s policy is about to get cancelled. Yet not to worry, the victim can keep the policy active they hand over some personal and financial info. It’s just one more way that scammers use urgency and fear to steal to commit identity theft and fraud.
As said, health insurance scams become relatively easy to spot once you know the tricks that scammers use. The Federal Trade Commission (FTC) offers up its list of the ones they typically use the most:
1)Someone says they’re from the government and need money or your personal info.Government agencies don’t call people out of the blue to ask them for money or personal info. No one from the government will ask you to verify your Social Security, bank account, or credit card number, and they won’t ask you to wire money or pay by gift card or cryptocurrency.
If you have a question about Health Insurance Marketplace®, contact the government directly at: HealthCare.gov or 1-800-318-2596
2) Someone tries to sell you a medical discount plan. Legitimate medical discount plans differ from health insurance. They supplement it. In that way, they don’t pay for any of your medical expenses. Rather, they’re membership programs where you pay a recurring fee for access to a network of providers who offer their services at pre-negotiated, reduced rates. The FTC strongly advises thorough research before participating in one, as some take people’s money and offer very little in return. Call your caregiver and see if they really participate in the program and in what way. And always review the details of any medical discount plan in writing before you sign up.
3) Someone wants your sensitive personal info in exchange for a price quote. The Affordable Care Act’s (ACA’s) official government site is HealthCare.gov. It lets you compare prices on health insurance plans, check your eligibility for healthcare subsidies, and begin enrollment. But HealthCare.gov will only ask for your monthly income and your age to give you a price quote. Never enter personal financial info like your Social Security number, bank account, or credit card number to get a quote for health insurance.
4) Someone wants money to help you navigate the Health Insurance Marketplace. The people who offer legitimate help with the Health Insurance Marketplace (sometimes called Navigators or Assisters) are not allowed to charge you and won’t ask you for personal or financial info. If they ask for money, it’s a scam. Go to HealthCare.govand click “Find Local Help” to learn more.
1)For health insurance, visit a trusted source like HealthCare.gov or your state marketplace. Doing so helps guarantee that you’ll get the kind of fully compliant coverage you want.
2) Make sure the insurance covers you in your state. Not every insurer is licensed to operate in your state. Double-check that the one you’re dealing with is. A good place to start is to visit the site for your state’s insurance commission. It should have resources that let you look up the insurance companies, agents, and brokers in your state.
3) For any insurance, research the company offering it. Run a search with the company name and add “scam” or “fraud” to it. See if any relevant news or complaints show up. And if the plan you’re being offered sounds too good to be true, it probably is.
4) Watch out for high-pressure sales. Don’t pay anything up front and be cautious if a company is forcing you to make quick decisions.
5) Guard your personal info. Never share your personal info, account details, or Social Security number over text or email. Make sure you’re really working with a legitimate company and that you submit any info through a secure submissions process.
6) Block bad links to phishing sites. Many insurance scams rely on phishing sites to steal personal info. A combination of our Web Protection and Scam Detector can steer you clear of them. They’ll alert you if a link might take you to one. It’ll also block those sites if you accidentally tap or click on a bad link.
7) Monitor your identity and credit. In some health insurance scams, your personal info winds up in wrong hands, which can lead to identity fraud and theft. And the problem is that you only find out once the damage is done. Actively monitoring your identity and credit can spot a problem before it becomes an even bigger one. You can take care of both easily with our identity monitoring and credit monitoring.
Additionally, our identity theft coverage can help if the unexpected happens with up to $2 million in identity theft coverage and identity restoration support if determined you’re a victim of identity theft.
You’ll find these protections and more in McAfee+.
The post How To Spot Health Insurance Scams This Open Enrollment Season appeared first on McAfee Blog.

Imagine a day where you didn’t have to juggle passwords.
No more sticky notes. No more notebooks with dozens of passwords scribbled in, crossed out, and scribbled in again. No more forgetting and resetting. No more typing them in all the time.
And even better, imagine secure accounts, likely even more secure than you could keep them on your own.
That’s the power of a password manager in your life.
A password manager does the work of creating strong, unique passwords for each and every one of your accounts. And considering the hundred or so accounts you have, that’s something that would take plenty of time if you did all that work on your own.
In all, a password manager can turn the pain of juggling passwords into a real comfort.
Before we get into how a password manager can make your life easier while making your accounts more secure, let’s look at what makes up a bad password. Here are a few examples:
Obvious passwords: Password-cracking programs start by entering a list of common (and arguably lazy) passwords. These may include the simple “password” or “1234567”. Others include common keyboard paths like “qwerty.” Even longer keyboard paths like “qwertyuiop” are well known to hackers and their tools as well.
Dictionary words: Hacking tools also look for common dictionary words strung together, which helps them crack longer passwords in chunks. The same goes for passwords that contain the name of the app or service in them. These are “no brainer” words found in passwords that make passwords even easier to crack.
Repeated passwords: You may think you have such an unbreakable password that you want to use it for all your accounts. However, this means that if hackers compromise one of your accounts, all your other accounts are vulnerable. This is a favorite tactic of hackers. They’ll target less secure accounts and services and then attempt to re-use those credentials on more secure services like online bank and credit card companies.
Personal information passwords: Passwords that include your birthday, dog’s name, or nickname leave you open to attack. While they’re easy for you to remember, they’re also easy for a hacker to discover—such as with a quick trip to your social media profile, particularly if it is not set to private.
If any of the above sounds familiar, you’ll want to replace any of your bad passwords with strong ones.
We can point to three things that make up a strong password, which makes it difficult to hack.
Your password is:
Long: A longer password is potentially a stronger password when it comes to a “brute force” attack, where a hacker uses an automated trial-and-error system to break it. For example, an eight-character password using uppercase and lowercase letters, numbers, and symbols can get hacked in minutes. Kick it up to 16 characters and it becomes incredibly more difficult to break—provided it doesn’t rely on common words or phrases. McAfee can help you generate a strong password, for stronger security with our random password generator.
Complex: To increase the security of your password, it should have a combination of uppercase letters, lowercase letters, symbols, and numbers like mentioned above.
Unique: Every one of your accounts should have its own password.
Now, apply this to the hundred or so accounts you keep and creating strong passwords for all of them really does call for a lot of work.
Given its ease of use and the big security boost it gives you and all your accounts, the answer is yes.
A password manager does the work of creating strong, unique passwords for your accounts. These will take the form of a string of random numbers, letters, and characters. They won’t be memorable, but the manager does the memorizing for you. You only need to remember a single password to access the tools of your manager.
A strong password manager also stores your passwords securely. Our password manager protects your passwords by scrambling them with AES-256, one of the strongest encryption algorithms available. Only you can decrypt and access your info with the factors you choose. Additionally, our password manager uses multi-factor authentication (MFA), so you’ll be verified by at least two factors before being signed in.
Aside from the comfort of convenience a password manager can give you, it gives you another level of assurance—extra protection in an age of data breaches, because you’ll have unique passwords where one compromise won’t lead to others.
And whether or not you go with a password manager to create those strong and unique passwords, make sure you use MFA on every account that offers it. MFA offers another layer of protection by adding another factor into the login process, such as something you own like a text to your phone or notification to an authentication app. That way if a hacker has your password, they’ll still be locked out of your account because they lack that MFA code.
In some cases, you really don’t need some of your old accounts and the passwords that come along with them. Maybe they’re old and unused. Or maybe they were for a one-time purchase at an online store you won’t visit again. Deleting these accounts is a smart move because they’re yet more places where your personal info is stored—and subject to a data breach.
Our Online Account Cleanup can help, which you can find in all our McAfee+ plans. It scans for accounts in your name, gives you a full list, and shows you which types of accounts might be riskier than others. From there you can decide which ones you want to delete, along with the personal info linked to them. In our McAfee+ Ultimate plans, you get full-service Online Account Cleanup, which sends the data deletion requests for you.
Between this and a password manager, you’ll have one less thing to juggle—your passwords, and one less thing to worry about—if they’re secure from hackers.
The post Why “Strong Passwords” Aren’t Enough Anymore—and What to Do Instead appeared first on McAfee Blog.

Pets, poisoned AI search results, and a phone call that sounds like it’s coming straight from the federal government, this week’s scams don’t have much in common except one thing: they’re getting harder to spot.
In today’s edition of This Week in Scams, we’re breaking down the biggest security lapses and the tactics scammers used to exploit them, and what you can do to stay ahead of the latest threats.
If you’re a Petco customer, you’ll want to know about not one but two data security lapses in the past week.
First, as reported by TechCrunch on Monday, Petco followed Texas data privacy laws by filing a data breach with the attorney general’s office. In that filing, Petco reported that the affected data included names, Social Security numbers, and driver’s license numbers. Further info including account numbers, credit and debit card numbers, and dates of birth were also mentioned in the filing.
Also according to Techcrunch, the company filed similar notices in California and Massachusetts.
To date, Petco has not made a comment about the size of the breach and the number of people affected.
Different states have different policies for reporting data breaches. In some cases, that helps us put a figure to the size of the breach, as some states require companies to disclose the total number of people caught up in the breach. That’s not the case here, so the full scope of the attack remains in question, at least for right now.
As of Thursday, we know Petco reported that 329 Texans were affected along with seven Massachusetts residents, per the respective reports filed. California’s report does not contain the number of Californians affected, yet laws in that state require businesses to report breaches that affect 500 or more people, so at least 500 people were affected there.
Below you can see the form letter Petco sent to affected Californians in accordance with California’s data privacy laws:

In it, you can see that Petco discovered that “a setting within one of our software applications … inadvertently allowed certain files to become accessible online.” Further, Petco said that it “immediately took steps to correct the issue and to remove the files from further online access,” and that it “corrected” the setting and implemented unspecified “additional security measures.”
So while no foul play appears to have been behind the breach, it’s still no less risky and concerning for Petco’s customers. We’ll cover what you can do about that in a moment after we cover yet another data issue at Petco through its Vetco clinics.
Also within the same timeframe, yet more research and reporting from Techcrunch uncovered a second security lapse that exposed personal info online. From their article:
“TechCrunch identified a vulnerability in how Vetco’s website generates copies of PDF documents for its customers.
“Vetco’s customer portal, located at petpass.com, allows customers to log in and obtain veterinary records and other documents relating to their pet’s care. But TechCrunch found that the PDF generating page on Vetco’s website was public and not protected with a password.
“As such, it was possible for anyone on the internet to access sensitive customer files directly from Vetco’s servers by modifying the web address to input a customer’s unique identification number. Vetco customer numbers are sequential, which means one could access other customers’ data simply by changing a customer number by one or two digits.”
With the size and reach of the Petco breach still unknown, and the impact of the Vetco security lapse also unknown, we advise caution for all Petco customers. At minimum, monitor transactions and keep an eye on your credit report for any suspicious activity. And it’s always a good time to update a weak password.
For those who received a notification, we advise the following:
Check your credit, consider a security freeze, and get ID theft protection. You can get all three working for you with McAfee+ Advanced or McAfee+ Ultimate.
Monitor transactions across your accounts, also available in McAfee+ Advanced and Ultimate.
Keep an eye out for phishing attacks. Use our Scam Detector to spot any follow-on attacks.
Update your passwords. Strong and unique passwords are best. Our password manager can help you create and store them securely.
And use two-factor authentication on all your accounts. Enabling two-factor authentication provides an added layer of security.

What to do if your Social Security number was breached.
If you think your Social Security number was caught up in the breach, act quickly.
You might want to be careful when searching for customer service numbers while in AI mode. Or with an AI search engine. It could connect you to a scammer.
From The Times comes reports of scammers manipulating the AI in platforms like Google and Perplexity so that their search results return scam numbers instead of a proper customer service numbers for, say, British Airways.
How do they manipulate those results? By spamming the internet with false info that gets picked up and then amplified by AI.
“[S]cammers have started seeding fake call center numbers on the web so the AI is tricked into thinking it is genuine …
“Criminals have set up YouTube channels with videos claiming to help with customer support, which are packed with airline brand names and scam numbers designed to be scraped and reused by the AI.
“Bot-generated reviews on Yelp or video descriptions on YouTube are filled with fraudulent numbers as are airline and travel web forums.”
And with these tactics, scammers could poison the results for just about any organization, business, or brand. Not just airlines. Per The Times, “The scammers have also hijacked government sites, university domains, and even fitness sites to place scam numbers, which fools the AI into thinking they are genuine.”
This reveals a current limitation with many AI platforms. Largely they can’t distinguish when people deliberately feed them bad info, as seen in the case here.
Yet even as this attack is new, our advice remains the same: any time you want to ring up a customer service line, get the number directly from the company’s official website. Not from AI search and not by clicking a paid search result that shows up first (scammers can poison them too).
Are you under investigation for money laundering? Of course not. But this scam wants you to think so—and to pay up.
On Tuesday, the Federal Trade Commission (FTC) issued a consumer alert warning that people are reporting getting unexpected calls from someone saying they’re “FTC agent” John Krebs. Apparently “Agent Krebs” is telling people that they’re under investigation for money laundering—and that a deposit to a Bitcoin ATM can resolve the matter.
Of course, it’s a scam.
For starters, the FTC doesn’t have “agents.” And the idea of clearing one’s name in an investigation with a Bitcoin payment is a sure-fire sign of a scam. Lastly, any time someone asks for payment with Bitcoin or other payment methods that are near-impossible to recover (think wire transfers and gift cards), those are big red flags.
Apart from hanging up and holding on to your money, the FTC offers the following guidance, which holds true for any scam call:
As always, here’s a quick list of a few stories that caught our eye this week:
AI tools transform Christmas shopping as people turn to chatbots
National cybercrime network operating for 14 years dismantled in Indonesia
Why is AI becoming the go-to support for our children’s mental health?
We’ll see you next Friday with a special edition to close out 2025 … This Year in Scams.
The post This Week in Scams: Petco Breach Warning, and Watch Out for Fake Federal Calls appeared first on McAfee Blog.

It looks harmless enough.
A digital party invitation lands in your inbox or phone. You click to see the details. Then it asks you to log in or create an account before revealing the event.
That’s where the scam begins.
Fake e-vite phishing scams are on the rise, and they take advantage of something simple: social trust. You’re far more likely to click an invitation than a generic “account alert” or “delivery notice.”
And that’s exactly why scammers are using them.
In fact, here’s a screenshot of a fake phishing email I recently got this holiday season:
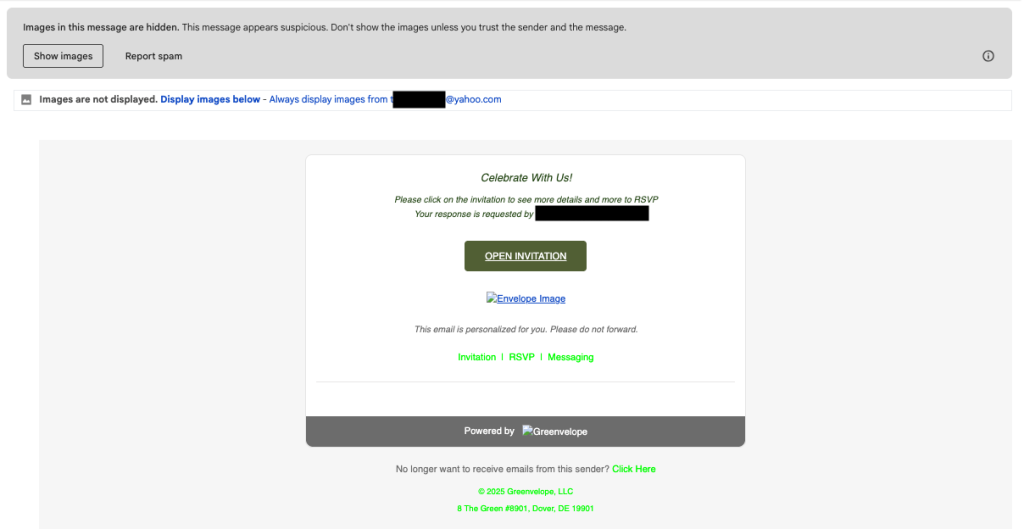
When you click the “open invitation” link, it immediately asks you to sign in or create an account with your personal information. That’s the step where scammers steal your private data.
A fake e-vite scam is a phishing attack that pretends to be a real invitation from platforms like Paperless Post or other digital invitation services.
The goal is to trick you into:
Once scammers have your login information, they can:
Here’s the most common flow:
Because this starts with something familiar and social, many people don’t realize it’s phishing until accounts are already compromised. Plus, scammers then use your email and name to trick friends and family into trusting more fake e-vites from your account.
Paperless Post has publicly acknowledged these scams and shared what legitimate messages actually look like.
Legitimate Paperless Post Emails Will Never:
Official Paperless Post Email Domains:
Legitimate invitations and account messages only come from:
Official support emails only come from:
If the sender does not match one of these exactly, it’s a scam.
Paperless Post also notes that verified emails may display a blue checkmark in supported inboxes to confirm authenticity.
If you see any of the following, do not click:
Modern phishing attacks don’t rely on sloppy design anymore. Many now use:
Invitation phishing is especially powerful because:
If you entered any information into a suspicious invitation page:
The faster you act, the more damage you can prevent.
The post Think That Party Invite Is Real? Fake E-Vite Scams Are the New Phishing Trap appeared first on McAfee Blog.

AI-powered browsers give you much more than a window to the web. They represent an entirely new way to experience the internet, with an AI “agent” working by your side.
We’re entering an age where you can delegate all kinds of tasks to a browser, and with that comes a few things you’ll want to keep in mind when using AI browsers like ChatGPT’s Atlas, Perplexity’s Comet, and others.
So, what’s the allure of this new breed of browser? The answer is that it’s highly helpful, and plenty more.
By design, these “agentic” AI browsers actively assist you with the things you do online. They can automate tasks and interpret your intentions when you make a request. Further, they can work proactively by anticipating things you might need or by offering suggestions.
In a way, an AI browser works like a personal assistant. It can summarize the pages in several open tabs, conduct research on just about any topic you ask it to, or even track down the lowest airfare to Paris in the month of May. Want it to order ink for your printer and some batteries for your remote? It can do that too. And that’s just to name a few possibilities.
As you can see, referring to the AI in these browsers as “agentic” fits. It truly works like an agent on your behalf, a capability that promises to get more powerful over time.
But as with any new technology, early adopters should balance excitement with awareness, especially when it comes to privacy and security. You might have seen some recent headlines that shared word of security concerns with these browsers.
The reported exploits vary, as does the harm they can potentially inflict. That ranges from stealing personal info, gaining access to Gmail and Google Drive files, installing malware, and injecting the AI’s “memory” with malicious instructions, which can follow from session to session and device to device, wherever a user logs in.
Our own research has shown that some of these attacks are now tougher to pull off than they were initially, particularly as the AI browser companies continue to put guardrails in place. If anything, this reinforces a long-standing truth about online security, it’s a cat-and-mouse game. Tech companies put protections in place, bad actors discover an exploit, companies put further protections in place, new exploits crop up, and so on. It’s much the same in the rapidly evolving space of AI browsers. The technology might be new, but the game certainly isn’t.
While these reports don’t mean AI browsers are necessarily unsafe to use, they do underscore how fast this space is evolving…and why caution is smart as the tech matures.
It’s still early days for AI-powered browsers and understanding the security and privacy implications of their use. With that, we strongly recommend the following to help reduce your risk:
Don’t let an AI browser do what you wouldn’t let a stranger do. Handle things like your banking, finances, and health on your own. And the same certainly goes for all the info tied to those aspects of your life.
Pay attention to confirmations. As of today, agentic browsers still require some level of confirmation from the user to perform key actions (like processing a payment, sending an email, or updating a calendar entry). Pay close attention to them, so you can prevent your browser from doing something you don’t want it to do.
Use the “logged out” mode, if possible. As of this writing, at least one AI browser, Atlas, gives you the option to use the agent in the logged-out mode.i This limits its access to sensitive data and the risk of it taking actions on your behalf with your credentials.
If possible, disable “model learning.” By turning it off, you reduce the amount of personal info stored and processed by the AI provider for AI training purposes, which can minimize security and privacy risks.
Set privacy controls to the strictest options available. Further, understand what privacy policies the AI developer has in place. For example, some AI providers have policies that allow people to review your interactions with the AI as part of its training. These policies vary from company to company, and they tend to undergo changes. Keeping regular tabs on the privacy policy of the AI browser you use makes for a privacy-smart move.
Keep yourself informed. The capabilities, features, and privacy policies of AI-powered browsers continue to evolve rapidly. Set up news alerts about the AI browser you use and see if any issues get reported and, if so, how the AI developer has responded. Do routine searches pairing the name of the AI browser with “privacy.”
McAfee’s award-winning protection helps you browse safer, whether you’re testing out new AI tools or just surfing the web.
McAfee offers comprehensive privacy services, including personal info scans and removal plus a secure VPN.
Plus, protections like McAfee’s Scam Detector automatically alert you to suspicious texts, emails, and videos before harm can happen—helping you manage your online presence confidently and safeguard your digital life for the long term. Likewise, Web Protection can help you steer you clear of suspicious websites that might take advantage of AI browsers.
The post How to Stay Safe on Your New AI Browser appeared first on McAfee Blog.

Internet security refers to tactics that protect your online activities from a variety of cyberthreats such as malware, phishing attacks, scams, and even unauthorized access by hackers. In this article, we will highlight the importance of internet security in safeguarding your digital network and outline what you can do to have a comprehensive online security system in place.
Internet usage has become central to our daily life. In 2024 alone, DataReportal reported that around 5.56 billion—that’s 67.9%—of the world’s population were connected to the internet. This was 136 million more than the year before, resulting in the creation of approximately 402.7 million terabytes of data each day. With this wealth of information, it is no wonder that cybercriminals are scrambling to make billions of dollars off the internet.
Globally, the average cost of data breaches rose by 10% between 2023 and 2024, totaling an estimated $4.88 million. This staggering amount included not only the loss in business revenues but also recovery costs and regulatory fines. For this reason, it has become important to implement internet security to protect our online personal data, activities, and devices from cyberthreats and unauthorized access.
While internet security is sometimes confused with, it’s important to point out their subtle distinctions. Internet security focuses on protecting your activities and data as they travel across the web, while cybersecurity is focused on protecting digital assets such as systems, networks, and data from cyberthreats. These two concepts work together to create your complete digital protection environment.
Internet security threats come in a variety of forms, complexities, and detectability. Some of the common threats we face today include:
While internet security threats may seem overwhelming at first glance, solutions are available to safeguard your computer or mobile devices. Below is a detailed look at some security measures.
Your home network serves as the foundation of your digital life, connecting all your devices and enabling your online activities. Having a strong network security foundation with multiple layers of protection will keep your connections and data safe from cyber threats.
Your router serves as the gateway between your home devices and the internet, making it a critical security component. Start by changing your router’s default administrator username and password immediately after setup. These factory defaults are widely known and easily exploited by attackers. Choose a strong, unique password that combines letters, numbers, and symbols to prevent unauthorized access to your router’s settings.
Enable WPA3 encryption on your wireless network, as it provides the strongest protection for your Wi-Fi connections. If your router doesn’t support WPA3, use WPA2 as a minimum standard. These protocols scramble your data as it travels between devices and your router, making it unreadable to anyone attempting to intercept your communications.
Create a unique network name or service set identifier (SSID) that doesn’t reveal your router manufacturer or model number, and pair it with a complex Wi-Fi password at least 12 characters long with a mix of uppercase and lowercase letters, numbers, and special characters. Avoid using personal information such as your address or name in either your network name or password, as this information can help attackers guess your password.
Regularly update your router’s firmware to patch security vulnerabilities and improve performance. Check your router manufacturer’s website quarterly for updates if automatic updates aren’t available, as outdated firmware often contains known security flaws that cybercriminals actively exploit.
Separate the guest network for visitors and smart home devices to protect your primary network where you store sensitive data. If a guest’s device is compromised or if a smart device has security vulnerabilities, the threat can’t easily spread to your main computers and phones. Configure your guest network with a strong password and consider time limits for access.
Enable access point isolation, also called client isolation, on your wireless network to prevent potentially compromised devices from attacking other devices on the same network. If you are an advanced user, consider creating separate virtual networks (VLANs) for different device types, such as keeping work computers on a different network segment than entertainment devices.
Modern routers include built-in firewalls that monitor suspicious activity in incoming and outgoing network traffic, and block potentially harmful connections and unnecessary ports and services.
Antivirus programs are engineered to prevent, detect, and remove viruses and other types of malicious software. Antivirus software can run automatic scans on specific files or directories to make sure no malicious activity is present, and no network or data breach has occurred.
McAfee’s antivirus software comes with key security capabilities such as malware detection, quarantine, and removal, as well as options for scanning files and applications, and an advanced firewall for home network security.
Multi-factor authentication is an authentication method that requires at least two pieces of evidence before granting access to a website. Using this method adds another layer of security to your applications and reduces the likelihood of a data breach.
Web browsers vary widely in terms of the security features, with some offering just the basics and others providing a more complete range of features. Ideally, you should opt for a browser that offers the following security features:
When properly implemented, these steps help ensure that your internet connection remains private, your data stays secure, and unauthorized users can’t access your network resources. Regular maintenance of these security settings, combined with staying informed about emerging threats, gives you the foundation for safe and confident internet use.
These days, smartphones and tablets hold more personal information than ever before—from banking details and photos to work emails and location data. While this convenience makes life easier, it also creates new opportunities for cybercriminals to target your mobile devices. As you secure your network and desktop or laptop devices, so should you treat your mobile devices with the same care. Here are some straightforward security practices that you can implement to significantly reduce your exposure to mobile threats:
Here are answers to the most common questions about protecting yourself online.
What does internet security cover?
Internet security protects you from a wide range of online threats including viruses, malware, phishing attacks, identity theft, and data breaches. It also covers your devices, personal information, online accounts, and network connections to help you browse, shop, and communicate safely online.
How is internet security different from antivirus software?
While antivirus software focuses specifically on detecting and removing malicious programs, internet security provides comprehensive protection that includes antivirus plus additional features such as firewalls, web protection, email security, identity monitoring, and safe browsing tools.
Do Macs and smartphones need internet security protection?
Yes, all devices that connect to the internet can be targeted by cybercriminals. Mobile devices and Macs face increasing security threats including malicious apps, phishing attempts, and network attacks, making protection essential regardless of your device type.
How can I stay safe on public Wi-Fi?
Avoid accessing sensitive accounts or making purchases on public Wi-Fi networks. When you must use public Wi-Fi, stick to encrypted websites with the “https” in the URL, avoid automatic connections, and consider using a VPN for added protection.
How can you keep children safe online?
As children grow older, their internet use becomes more extensive. To keep them safe online, educate them about the risks of web browsing and about best practices to avoid online threats like not sharing passwords. Explain which information should be shared and which should be kept private. Instruct them to never click on links from unknown sources. Set up parental controls on certain websites to filter inappropriate content and keep a child-friendly interface.
What are the signs that my account has been compromised?
Watch for unexpected password reset emails, unfamiliar login notifications, unusual account activity, friends receiving spam from your accounts, or unauthorized charges on your financial statements. If you notice any of these signs, change your passwords immediately and contact the relevant service providers.
How often should I update my software and devices?
Enable automatic updates whenever possible and install security patches as soon as they become available. Regular updates fix security vulnerabilities that criminals actively exploit, so staying current is one of your best defenses against cyber threats.
As more cyberthreats emerge and expand both in scope and sophistication, it’s essential that you protect your internet activities. Effective protection doesn’t have to be complicated. Taking steps to install antivirus software, create strong and unique passwords, enable your firewall, and use multi-factor authentication will help build a strong defense against online threats.
Start implementing these internet security measures today and enjoy the confidence that comes with knowing you’re protected online.
For added security, consider using an all-in-one antivirus solution like McAfee+ to safeguard your devices from online threats. Let McAfee handle your security while you focus on enjoying the internet.
The post What Is Internet Security? appeared first on McAfee Blog.

For this week in scams, we have fake AI-generated shopping images that could spoil your holidays, scammers use an Apple Support ticket in a takeover attempt, and a PlayStation scam partly powered by AI.
Let’s start with those fake ads, because holiday shopping is in full swing.
Turns out that three-quarters of people (74%) can’t correctly identify a fake AI-generated social media ad featuring popular holiday gifts—which could leave them open to online shopping scams.
That finding, and several others, comes by way of research from Santander, a financial services company in the UK.
Here’s a quick rundown of what else they found:
From the study … could you tell these ads are both fake?
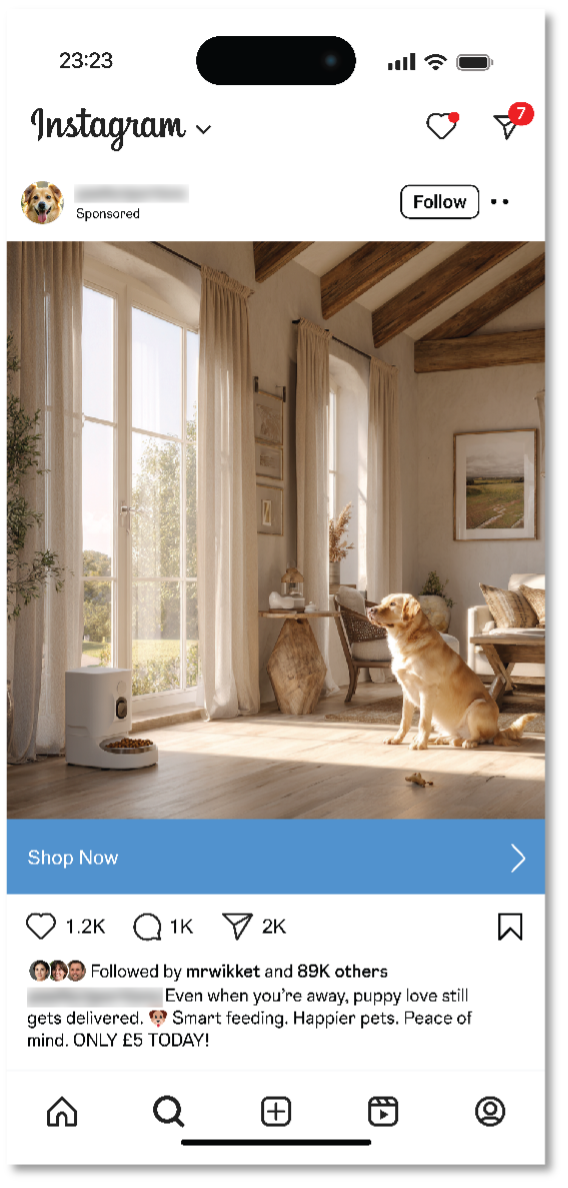
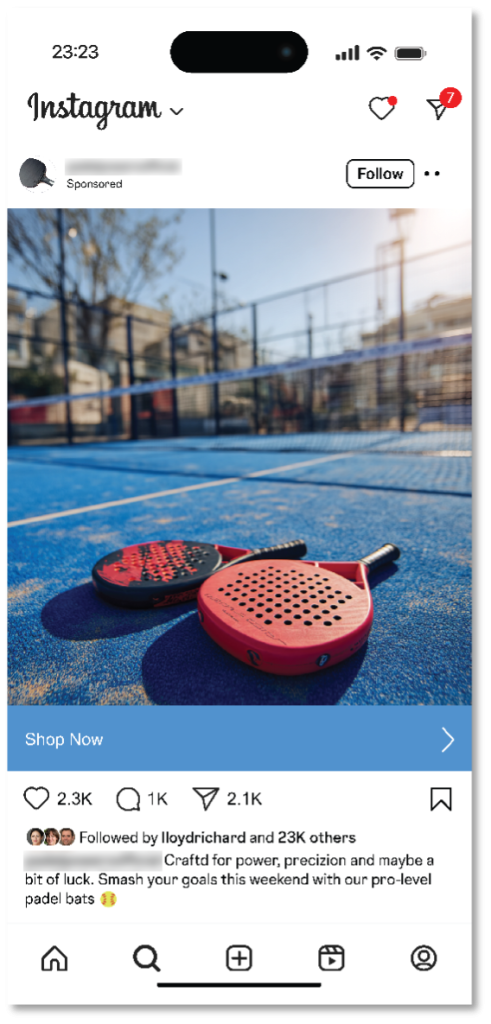
In all, cheap and readily available AI tools make spinning up fake ads quick and easy work. The same goes for launching websites where those “goods” can get sold. In the past, we’ve seen scammers take two different approaches when they use social media ads and websites to lure in their victims:
During the holidays, scammers pump out ads that offer seemingly outstanding deals on hot items. Of course, the offer and the site where it’s “sold” is fake. Victims hand over their personal info and credit card number, never to see the items they thought they’d purchased. On top of the money a victim loses, the scammer also has their card info and can run up its tab or sell it to others on the dark web.
In this case, the scammer indeed sells and delivers something. But you don’t get what you paid for. The item looks, feels, fits, or works entirely differently than what was advertised. In this way, people wind up with a cheaply made item cobbled together with inferior materials. Worse yet, these scams potentially prop up sweatshops, child labor, and other illegal operations in the process. Nothing about these sites and the things they sell on them are genuine.
So, fake AI shopping ads are out there. What should you look out for? Here’s a quick list:
“I almost lost everything—my photos, my email, my entire digital life.”
So opens a recent Medium post from Eric Moret recounting how he almost handed over his Apple Account to a scammer armed with a real Apple Support ticket to make this elaborate phishing attack look legit.
Over the course of nearly 30 minutes, a scammer calmly and professionally walked Moret through a phony account takeover attempt.
It started with two-factor authentication notifications that claimed someone was trying to access his iCloud account. Three minutes later, he got a call from an Atlanta-based number. The caller said they were with Apple Support. “Your account is under attack. We’re opening a ticket to help you. Someone will contact you shortly.”
Seconds later came another call from the same number, which is where the scam fully kicked in. The person also said they were from Apple Support and that they’d opened a case on Moret’s behalf. Sure enough, when directed, Moret opened his email and saw a legitimate case number from a legitimate Apple address.
The caller then told him to reset his password, which he did. Moret received a text with a link to a site where he could, apparently, close his case.
Note that at no time did the scammers ask him for his two-factor authentication code throughout this process, which is always the sign of a scam. However, the scammers had another way to get it.
The link took him to a site called “appeal-apple dot com,” which was in fact a scam site. However, the page looked official to him, and he entered a six-digit code “confirmation code” sent by text to finish the process.
That “confirmation code” was actually a fresh two-factor authentication code. With that finally in hand, the scammers signed in. Moret received a notice that a new device had logged into his account. Moret quickly reset his password again, which kicked them out and stopped the attack.
Maybe you didn’t get a scam call from “Emma” or “Carl” at Wal-Mart, but plenty of people did. Around eight million in all. Now the Federal Communications Commission’s (FCC) Enforcement Bureau wants to put a stop to them.
“Emma” and “Carl” are in fact a couple of AI voices fronting a scam framed around the bogus purchase of a PlayStation. It’s garnered its share of complaints, so much that the FCC has stepped in. It alleges that SK Teleco, a voice service provider, provisioned at least some of these calls, and that it must immediately stop.
According to the FCC, the call plays out like this:
“A preauthorized purchase of PlayStation 5 special edition with Pulse 3D headset is being ordered from your Walmart account for an amount of 919 dollars 45 cents. To cancel your order or to connect with one of our customer support representatives, please press ‘1.’ Thank you.”
Pressing “1” connects you to a live operator who asks for personal identifiable such as Social Security numbers to cancel the “purchase.”
If you were wondering, it’s unlawful to place calls to cellphones containing artificial or prerecorded voice messages absent an emergency purpose or prior express consent. According to the FCC’s press release, SK Teleco didn’t respond to a request to investigate the calls. The FCC further alleges that it’s unlikely the company has any such consent.
Per the FCC, “If SK Teleco fails to take swift action to prevent scam calls, the FCC will require all other providers to no longer accept call traffic from SK Teleco.”
We’ll see how this plays out, yet it’s a good reminder to report scam calls. When it comes to any kind of scam, law enforcement and federal agencies act on complaints.
Here’s a quick list of a few stories that caught our eye this week:
Scammers pose as law enforcement, threaten jail time if you don’t pay (with audio)
Deepfake of North Carolina lawmaker used in award-winning Brazilian Whirlpool video
What happens when you kick millions of teens off social media? Australia’s about to find out
We’ll see you next Friday with more updates, scam news, and ways you can stay safer out there.
The post This Week in Scams: Phony AI Ads, Apple Account Takeover Attempts, and a PlayStation Scam appeared first on McAfee Blog.

Unfortunately in today’s world, scammers are coming at us from all angles to trick us to get us to part with our hard-earned money. We all need to be vigilant in protecting ourselves online. If you aren’t paying attention, even if you know what to look for, they can get you. There are numerous ways to detect fake sites or emails, phishing, and other scams.
Before we delve into the signs of fake websites, we will first take a closer look at the common types of scam that use websites, what happens when you accidentally access a fake website, and what you can do in case you unknowingly purchased items from it.
Fake or scam websites are fraudulent sites that look legitimate while secretly attempting to steal your personal information, money, or account access.
These deceptive platforms masquerade as trustworthy businesses or organizations, sending urgent messages such as popular shopping websites offering fantastic limited-time deals, banking websites requesting immediate account verification, government portals claiming you owe taxes or are eligible for refunds, and shipping companies asking for delivery fees.
The urgency aims to trick you into logging in and sharing sensitive details—credit card numbers, Social Security information, login credentials, and personal data. Once you submit your data, the scammers will steal your identity, drain your accounts, or sell your details to other criminals on the dark web.
These scam websites have become increasingly prevalent because they’re relatively inexpensive to create and can reach millions of potential victims quickly through email and text campaigns, social media ads, and search engine manipulation.
Cybersecurity researchers and consumer protection agencies discover these fraudulent sites through various methods, including monitoring suspicious domain registrations, analyzing reported phishing attempts, and tracking unusual web traffic patterns. According to the FBI’s Internet Crime Complaint Center, losses from cyber-enabled fraud amounted to $13.7 billion, with fake websites representing a significant portion of these losses.
Visiting a fake website, accidentally or intentionally, can expose you to several serious security risks that can impact your digital life and financial well-being:
Scammers use different tricks to make fake websites look real, but most of them fall into familiar patterns. Knowing the main types of scam sites helps you recognize danger faster. This section lists the most common categories of scam websites, how they work, and the red flags that give them away before they can steal your information or money.
Understanding these common scam types helps you recognize fake sites before they can steal your information or money. When in doubt, verify legitimacy by visiting official websites directly through bookmarks or search engines rather than clicking suspicious links.
For the latest warnings and protection guidance, check resources from the Federal Trade Commission and the FBI’s Internet Crime Complaint Center.
You can protect yourself by learning to recognize the warning signs of fake sites. By understanding what these scams look like and how they operate, you’ll be better equipped to shop, bank, and browse online with confidence. Remember, legitimate companies will never pressure you to provide sensitive information through unsolicited emails or urgent pop-up messages.
Most scams usually start out from social engineering tactics such as phishing, smishing, and fake social media messages with suspicious links, before leading you to a fake website.
From these communications, the scammers impersonate legitimate organizations before finally executing their malevolent intentions. To avoid being tricked, it is essential to recognize the warning signs wherever you encounter them.
Fake emails are among the most common phishing attempts you’ll encounter. If you see any of these signs in an unsolicited email, it is best not to engage:
Smishing messages bear the same signs as phishing emails and have become increasingly sophisticated. These fake messages often appear to come from delivery services, banks, or government agencies. Common tactics include fake package delivery notifications, urgent banking alerts, or messages claiming you’ve won prizes or need to verify account information.
Legitimate organizations typically don’t include clickable links in unsolicited text messages, especially for account-related actions. When in doubt, don’t click the link—instead, open your banking app directly or visit the official website by typing the URL manually.
Social media platforms give scammers new opportunities to create convincing fake profiles and pages. They might impersonate customer service accounts, create fake giveaways, or send direct messages requesting personal information. These fake sites often use profile pictures and branding that closely resemble legitimate companies.
Unusual sender behavior is another indicator of a scam across all platforms. This includes messages from contacts you haven’t heard from in years, communications from brands you don’t typically interact with, or requests that seem out of character for the supposed sender.
Scammers have become increasingly cunning in creating fake websites that closely mimic legitimate businesses and services. Here are some real-life examples of how cybercriminals use fake websites to victimize consumers:
Scammers exploit your trust in the United States Postal Service (USPS), designing sophisticated fake websites to steal your personal information, payment details, or money. They know you’re expecting a package or need to resolve a delivery issue, making you more likely to enter sensitive information without carefully verifying the site’s authenticity.
USPS-themed smishing attacks arrive as text messages stating your package is delayed, undeliverable, or requires immediate action. Common phrases include “Pay $1.99 to reschedule delivery” or “Your package is held – click here to release.”
Scammers use various URL manipulation techniques to make their fake sites appear official. Watch for these red flags:
Always verify package information and delivery issues through official USPS channels before taking any action on suspicious websites or messages:
Reporting fake USPS websites helps protect others from falling victim to these scams and assists law enforcement in tracking down perpetrators.
Remember that legitimate USPS services are free for standard delivery confirmation and tracking. Any website demanding payment for basic package tracking or delivery should be treated as suspicious and verified through official USPS channels before providing any personal or financial information.
According to the Federal Trade Commission, tech support scams cost Americans nearly $1.5 billion in 2024. These types of social engineering attacks are increasingly becoming sophisticated, making it more important than ever to verify security alerts through official channels.
Sadly, many scammers are misusing the McAfee name to create fake tech support pop-up scams and trick you into believing your computer is infected or your protection has expired and hoping you’ll act without thinking.
These pop-ups typically appear while you’re browsing and claim your computer is severely infected with viruses, malware, or other threats. They use official-looking McAfee logos, colors, and messaging to appear legitimate to get you to call a fake support number, download malicious software, or pay for unnecessary services.
Learning to detect fake sites and pop-ups protects you from scam. Be on the lookout for these warning signs:
If you see a suspicious pop-up claiming to be from McAfee, here’s exactly what you should do:
To check if your McAfee protection is genuinely active and up-to-date:
Remember, legitimate McAfee software updates and notifications come through the installed program itself, not through random browser pop-ups. Your actual McAfee protection works quietly in the background without bombarding you with alarming messages.
Stay protected by trusting your installed McAfee software and always verifying security alerts through official McAfee channels such as your installed McAfee dashboard or the official website.
Be prepared and know how to respond quickly when something doesn’t feel right. If you suspect you’ve encountered a fake website, trust your instincts and take these protective steps immediately.
Recognizing fake sites and emails becomes easier with practice. The key is to trust your instincts—if something feels suspicious or too good to be true, take a moment to verify through official channels. With the simple verification techniques covered in this guide, you can confidently navigate the digital world and spot fake sites and emails before they cause harm.
Your best defense is to make these quick security checks a regular habit—verify URLs, look for secure connections, and trust your instincts when something feels off. Go directly to the source or bookmark your most-used services and always navigate to them. Enable two-factor authentication on important accounts, and remember that legitimate companies will never ask for sensitive information via email. Maintaining healthy skepticism about unsolicited communications will protect not only your personal information but also help create a safer online environment for everyone.
For the latest information on fake websites and scams and to report them, visit the Federal Trade Commission’s scam alerts or the FBI’s Internet Crime Complaint Center.
The post Ways to Tell if a Website Is Fake appeared first on McAfee Blog.

When it comes to online safety, independent testing matters. And in the latest AV-Comparatives Real-World Protection Test, McAfee earned the highest possible rating, ADVANCED+, with a 99.5% protection rate. It’s the kind of recognition that helps shoppers understand which tools truly hold up in real-life conditions, not just in controlled lab environments.
For anyone navigating today’s mix of emails, downloads, suspicious links, and AI-driven scams, independent results like these are a clear signal: strong protection still makes a real difference.
The Real-World Protection Test is an independent evaluation run by AV-Comparatives, a trusted third-party security testing lab. The test measures how well antivirus and online protection tools block real threats that people encounter every day, including dangerous URLs, malicious downloads, phishing pages, and harmful files attempting to run on a device.
This type of testing is widely cited by major tech publications and review sites because it reflects actual user behavior rather than controlled lab simulations.
According to AV-Comparatives, their Real-World Protection Test is designed to measure how security products perform in situations people face every day: clicking a link, opening a file, visiting a site for the first time.
It’s one of the most widely cited sources in tech journalism and consumer product reviews, and it often shapes how online shoppers evaluate cybersecurity tools.
Here’s why tests like these are used in tech reviews, buying guides, and search engine rankings:
McAfee has earned an ADVANCED+ rating in all tests since June 2022, demonstrating our consistency and reliability in the moments that matter most: when a threat appears disguised as something routine.
The latest evaluation included 19 consumer security products, each tested across the full attack chain, from the moment a malicious URL is accessed to the instant a dangerous file tries to execute.
Unlike benchmark tests that focus on one part of the process, this assessment mirrors real user behavior. AV-Comparatives notes that the methodology is meant to be “as realistic as possible,” and the results often reveal meaningful differences in both protection and false positives.
With this round of testing, McAfee maintains its cycle of highest ratings in every Real-World Protection Test, while several well-known competitors were downgraded due to high false-positive counts.
A high protection score matters most when you’re simply going about your day — shopping, banking, downloading a file, or clicking a link you think is safe. Independent recognition signals three core things:
Strong results indicate that advanced threats, misleading links, and malicious downloads are blocked before they can cause harm.
With only four false positives out of nearly 500 samples, McAfee flagged less than 1% of clean files incorrectly. For context: the industry average in this test was 10 false positives, and one competitor even misidentified 75, meaning it labeled nearly 16% of harmless activity as a threat.
The takeaway is simple: strong protection shouldn’t get in your way, and these results show it doesn’t.
Criminals now use AI to make fake emails, websites, and support messages look real. Testing that mirrors those real-world conditions helps consumers see which tools stay ahead of that curve.
McAfee’s threat protection, the same technology validated in this test, is built into McAfee+ Premium, McAfee+ Advanced, McAfee+ Ultimate, McAfee Total Protection, and McAfee LiveSafe.
McAfee’s built-in Scam Detector, included in all core plans, automatically detects scams across text, email, and video, blocks dangerous links, and identifies deepfakes—stopping harm before it happens.
The post McAfee Named ADVANCED+ in Real-World Protection — What That Means for You appeared first on McAfee Blog.

Scammers aren’t worried about ending up on the naughty list. If anything, they’re doubling down in 2025.
This year, scammers are impersonating major brands with startling accuracy, from fake delivery updates to cloned checkout pages.
Our McAfee Labs researchers analyzed real scam texts, emails, and URLs from October through early November, along with consumer survey data, to identify the patterns shaping this season’s fraud.
Here’s what shoppers need to know, what’s trending upward, and how to spot the fakes before they reach your cart.
A brand-impersonation scam is when criminals copy a real brand, like a retailer, tech company, bank, or delivery service, to make fake emails, texts, ads, or websites that look legitimate.
Their goal is to trick shoppers into clicking, entering account details, or making a payment.
McAfee Labs’ brand impersonation analysis shows criminals focusing on the items people shop for most — tech gifts, luxury goods, and high-demand drops.
Fake versions of these brands typically include:
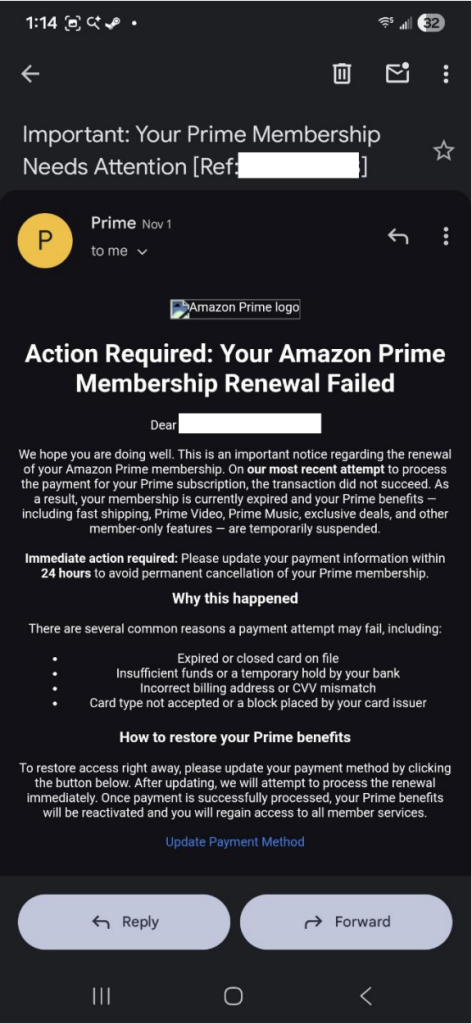
Scammers are getting better at copying the brands you trust, but avoiding the fakes gets much easier when you slow down, verify what you see, and use tools that check links and messages before you click.
Here’s what actually helps during a season when realistic-looking scams are everywhere:
If you get a message about an order, refund, delivery issue, or account lockout, don’t click the link.
Go directly to the retailer’s app or type the URL manually.
This single habit eliminates most holiday scams.
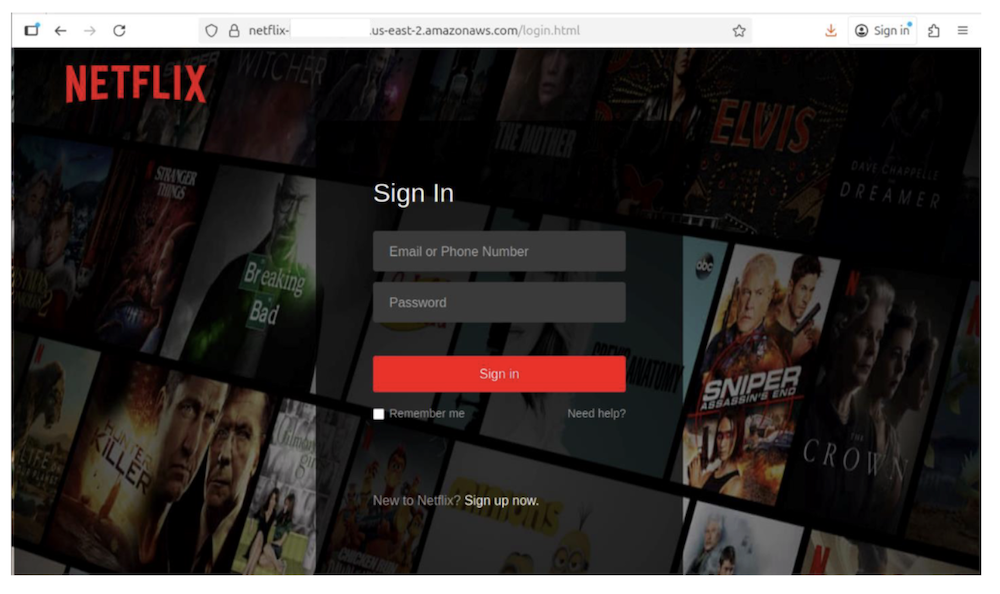
Scammers can recreate logos, colors, and templates perfectly.
What they can’t easily mimic:
If the sender looks off, the message is off.
McAfee’s online protection adds a critical layer of holiday safety, especially when scammers imitate retailers with near-perfect accuracy.
Key protections include:
Web Protection
Blocks malicious or suspicious websites before they load — including fake checkout pages, login portals, and support sites.
Scam Detector
Built into all core McAfee plans. It flags scam texts, emails, and even deepfake-style video promotions, letting you know a link or message is unsafe before you interact with it.
Password Manager
Creates and stores strong, unique passwords so a stolen login from one retailer doesn’t unlock your whole digital life.
Identity & Financial Monitoring
Transaction Monitoring and Credit Monitoring can alert you to unusual activity — a crucial safety net when stolen logins, card numbers, or personal details circulate quickly during the holidays.
These tools help counter the exact tactics scammers rely on: cloned websites, fake brand emails, and phishing links disguised as legitimate retailers.
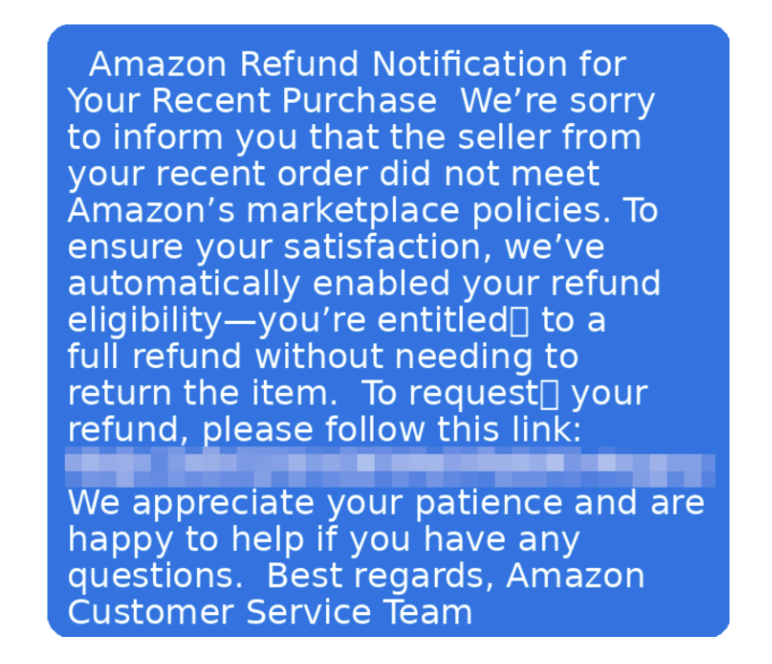
Even if a scammer gets your password, they can’t get in without your one-time code.
Legitimate companies don’t ask you to “act in minutes,” pay fees to “unlock” an account, or claim you must stay on the line.
Pressure is a tactic — not customer service.
Check your banking and shopping accounts weekly.
Small unauthorized charges often appear before large ones.
The post The Most Impersonated Brands in Holiday Shopping, Ranked appeared first on McAfee Blog.