
The value of Bitcoin has had its ups and downs since its inception in 2013, but its recent skyrocket in value has created renewed interest in this virtual currency. The rapid growth of this alternative currency has dominated headlines and ignited a cryptocurrency boom that has consumers everywhere wondering how to get a slice of the Bitcoin pie. For those who want to join the craze without trading traditional currencies like U.S. dollars (i.e., fiat currency), a process called Bitcoin mining is an entry point. However, Bitcoin mining poses a number of security risks that you need to know.
Mining for Bitcoin is like mining for gold—you put in the work and you get your reward. But instead of back-breaking labor, you earn the currency with your time and computer processing power. Miners, as they are called, essentially maintain and secure Bitcoin’s decentralized accounting system. Bitcoin transactions are recorded in a digital ledger called a blockchain. Bitcoin miners update the ledger by downloading a special piece of software that allows them to verify and collect new transactions. Then, they must solve a mathematical puzzle to secure access to add a block of transactions to the chain. In return, they earn Bitcoins, as well as a transaction fee.
As the digital currency has matured, Bitcoin mining has become more challenging. In the beginning, a Bitcoin user could mine on their home computer and earn a good amount of the digital currency, but these days the math problems have become so complicated that it requires a lot of expensive computing power. This is where the risks come in. Since miners need an increasing amount of computer power to earn Bitcoin, some have started compromising public Wi-Fi networks so they can access users’ devices.
One example of this security breach happened at a coffee shop in Buenos Aires, which was infected with malware that caused a 10-second delay when logging in to the cafe’s Wi-Fi network. The malware authors used this time delay to access the users’ laptops for mining. In addition to public Wi-Fi networks, millions of websites are being compromised to access users’ devices for mining. When an attacker loads mining software onto devices without the owner’s permission, it’s called a cryptocurrency mining encounter or cryptojacking.
It’s estimated that 50 out of every 100,000 devices have encountered a cryptocurrency miner. Cryptojacking is a widespread problem and can slow down your device; though, that’s not the worst that can happen. Utility costs are also likely to go through the roof. A device that is cryptojacked could have 100 percent of its resources used for mining, causing the device to overheat, essentially destroying it.
Now that you know a little about mining and the Bitcoin security risks associated with it, here are some tips to keep your devices safe as you monitor the cryptocurrency market:
The post Bitcoin Security: Mining Threats You Need to Know appeared first on McAfee Blog.
On Sunday, July 20, Microsoft Corp. issued an emergency security update for a vulnerability in SharePoint Server that is actively being exploited to compromise vulnerable organizations. The patch comes amid reports that malicious hackers have used the SharePoint flaw to breach U.S. federal and state agencies, universities, and energy companies.

Image: Shutterstock, by Ascannio.
In an advisory about the SharePoint security hole, a.k.a. CVE-2025-53770, Microsoft said it is aware of active attacks targeting on-premises SharePoint Server customers and exploiting vulnerabilities that were only partially addressed by the July 8, 2025 security update.
The Cybersecurity & Infrastructure Security Agency (CISA) concurred, saying CVE-2025-53770 is a variant on a flaw Microsoft patched earlier this month (CVE-2025-49706). Microsoft notes the weakness applies only to SharePoint Servers that organizations use in-house, and that SharePoint Online and Microsoft 365 are not affected.
The Washington Post reported on Sunday that the U.S. government and partners in Canada and Australia are investigating the hack of SharePoint servers, which provide a platform for sharing and managing documents. The Post reports at least two U.S. federal agencies have seen their servers breached via the SharePoint vulnerability.
According to CISA, attackers exploiting the newly-discovered flaw are retrofitting compromised servers with a backdoor dubbed “ToolShell” that provides unauthenticated, remote access to systems. CISA said ToolShell enables attackers to fully access SharePoint content — including file systems and internal configurations — and execute code over the network.
Researchers at Eye Security said they first spotted large-scale exploitation of the SharePoint flaw on July 18, 2025, and soon found dozens of separate servers compromised by the bug and infected with ToolShell. In a blog post, the researchers said the attacks sought to steal SharePoint server ASP.NET machine keys.
“These keys can be used to facilitate further attacks, even at a later date,” Eye Security warned. “It is critical that affected servers rotate SharePoint server ASP.NET machine keys and restart IIS on all SharePoint servers. Patching alone is not enough. We strongly advise defenders not to wait for a vendor fix before taking action. This threat is already operational and spreading rapidly.”
Microsoft’s advisory says the company has issued updates for SharePoint Server Subscription Edition and SharePoint Server 2019, but that it is still working on updates for supported versions of SharePoint 2019 and SharePoint 2016.
CISA advises vulnerable organizations to enable the anti-malware scan interface (AMSI) in SharePoint, to deploy Microsoft Defender AV on all SharePoint servers, and to disconnect affected products from the public-facing Internet until an official patch is available.
The security firm Rapid7 notes that Microsoft has described CVE-2025-53770 as related to a previous vulnerability — CVE-2025-49704, patched earlier this month — and that CVE-2025-49704 was part of an exploit chain demonstrated at the Pwn2Own hacking competition in May 2025. That exploit chain invoked a second SharePoint weakness — CVE-2025-49706 — which Microsoft unsuccessfully tried to fix in this month’s Patch Tuesday.
Microsoft also has issued a patch for a related SharePoint vulnerability — CVE-2025-53771; Microsoft says there are no signs of active attacks on CVE-2025-53771, and that the patch is to provide more robust protections than the update for CVE-2025-49706.
This is a rapidly developing story. Any updates will be noted with timestamps.
Thank you for following me! https://cybdetective.com
| Name | Link | Description | Price |
|---|---|---|---|
| Shodan | https://developer.shodan.io | Search engine for Internet connected host and devices | from $59/month |
| Netlas.io | https://netlas-api.readthedocs.io/en/latest/ | Search engine for Internet connected host and devices. Read more at Netlas CookBook | Partly FREE |
| Fofa.so | https://fofa.so/static_pages/api_help | Search engine for Internet connected host and devices | ??? |
| Censys.io | https://censys.io/api | Search engine for Internet connected host and devices | Partly FREE |
| Hunter.how | https://hunter.how/search-api | Search engine for Internet connected host and devices | Partly FREE |
| Fullhunt.io | https://api-docs.fullhunt.io/#introduction | Search engine for Internet connected host and devices | Partly FREE |
| IPQuery.io | https://ipquery.io | API for ip information such as ip risk, geolocation data, and asn details | FREE |
| Name | Link | Description | Price |
|---|---|---|---|
| Social Links | https://sociallinks.io/products/sl-api | Email info lookup, phone info lookup, individual and company profiling, social media tracking, dark web monitoring and more. Code example of using this API for face search in this repo | PAID. Price per request |
| Name | Link | Description | Price |
|---|---|---|---|
| Numverify | https://numverify.com | Global Phone Number Validation & Lookup JSON API. Supports 232 countries. | 250 requests FREE |
| Twillo | https://www.twilio.com/docs/lookup/api | Provides a way to retrieve additional information about a phone number | Free or $0.01 per request (for caller lookup) |
| Plivo | https://www.plivo.com/lookup/ | Determine carrier, number type, format, and country for any phone number worldwide | from $0.04 per request |
| GetContact | https://github.com/kovinevmv/getcontact | Find info about user by phone number | from $6,89 in months/100 requests |
| Veriphone | https://veriphone.io/ | Phone number validation & carrier lookup | 1000 requests/month FREE |
| Name | Link | Description | Price |
|---|---|---|---|
| Global Address | https://rapidapi.com/adminMelissa/api/global-address/ | Easily verify, check or lookup address | FREE |
| US Street Address | https://smartystreets.com/docs/cloud/us-street-api | Validate and append data for any US postal address | FREE |
| Google Maps Geocoding API | https://developers.google.com/maps/documentation/geocoding/overview | convert addresses (like "1600 Amphitheatre Parkway, Mountain View, CA") into geographic coordinates | 0.005 USD per request |
| Postcoder | https://postcoder.com/address-lookup | Find adress by postcode | £130/5000 requests |
| Zipcodebase | https://zipcodebase.com | Lookup postal codes, calculate distances and much more | 5000 requests FREE |
| Openweathermap geocoding API | https://openweathermap.org/api/geocoding-api | get geographical coordinates (lat, lon) by using name of the location (city name or area name) | 60 calls/minute 1,000,000 calls/month |
| DistanceMatrix | https://distancematrix.ai/product | Calculate, evaluate and plan your routes | $1.25-$2 per 1000 elements |
| Geotagging API | https://geotagging.ai/ | Predict geolocations by texts | Freemium |
| Name | Link | Description | Price |
|---|---|---|---|
| Approuve.com | https://appruve.co | Allows you to verify the identities of individuals, businesses, and connect to financial account data across Africa | Paid |
| Onfido.com | https://onfido.com | Onfido Document Verification lets your users scan a photo ID from any device, before checking it's genuine. Combined with Biometric Verification, it's a seamless way to anchor an account to the real identity of a customer. India | Paid |
| Superpass.io | https://surepass.io/passport-id-verification-api/ | Passport, Photo ID and Driver License Verification in India | Paid |
| Name | Link | Description | Price |
|---|---|---|---|
| Open corporates | https://api.opencorporates.com | Companies information | Paid, price upon request |
| Linkedin company search API | https://docs.microsoft.com/en-us/linkedin/marketing/integrations/community-management/organizations/company-search?context=linkedin%2Fcompliance%2Fcontext&tabs=http | Find companies using keywords, industry, location, and other criteria | FREE |
| Mattermark | https://rapidapi.com/raygorodskij/api/Mattermark/ | Get companies and investor information | free 14-day trial, from $49 per month |
| Name | Link | Description | Price |
|---|---|---|---|
| API OSINT DS | https://github.com/davidonzo/apiosintDS | Collect info about IPv4/FQDN/URLs and file hashes in md5, sha1 or sha256 | FREE |
| InfoDB API | https://www.ipinfodb.com/api | The API returns the location of an IP address (country, region, city, zipcode, latitude, longitude) and the associated timezone in XML, JSON or plain text format | FREE |
| Domainsdb.info | https://domainsdb.info | Registered Domain Names Search | FREE |
| BGPView | https://bgpview.docs.apiary.io/# | allowing consumers to view all sort of analytics data about the current state and structure of the internet | FREE |
| DNSCheck | https://www.dnscheck.co/api | monitor the status of both individual DNS records and groups of related DNS records | up to 10 DNS records/FREE |
| Cloudflare Trace | https://github.com/fawazahmed0/cloudflare-trace-api | Get IP Address, Timestamp, User Agent, Country Code, IATA, HTTP Version, TLS/SSL Version & More | FREE |
| Host.io | https://host.io/ | Get info about domain | FREE |
| Name | Link | Description | Price |
|---|---|---|---|
| BeVigil OSINT API | https://bevigil.com/osint-api | provides access to millions of asset footprint data points including domain intel, cloud services, API information, and third party assets extracted from millions of mobile apps being continuously uploaded and scanned by users on bevigil.com | 50 credits free/1000 credits/$50 |
| Name | Link | Description | Price |
|---|---|---|---|
| WebScraping.AI | https://webscraping.ai/ | Web Scraping API with built-in proxies and JS rendering | FREE |
| ZenRows | https://www.zenrows.com/ | Web Scraping API that bypasses anti-bot solutions while offering JS rendering, and rotating proxies apiKey Yes Unknown | FREE |
| Name | Link | Description | Price |
|---|---|---|---|
| Whois freaks | https://whoisfreaks.com/ | well-parsed and structured domain WHOIS data for all domain names, registrars, countries and TLDs since the birth of internet | $19/5000 requests |
| WhoisXMLApi | https://whois.whoisxmlapi.com | gathers a variety of domain ownership and registration data points from a comprehensive WHOIS database | 500 requests in month/FREE |
| IPtoWhois | https://www.ip2whois.com/developers-api | Get detailed info about a domain | 500 requests/month FREE |
| Name | Link | Description | Price |
|---|---|---|---|
| Ipstack | https://ipstack.com | Detect country, region, city and zip code | FREE |
| Ipgeolocation.io | https://ipgeolocation.io | provides country, city, state, province, local currency, latitude and longitude, company detail, ISP lookup, language, zip code, country calling code, time zone, current time, sunset and sunrise time, moonset and moonrise | 30 000 requests per month/FREE |
| IPInfoDB | https://ipinfodb.com/api | Free Geolocation tools and APIs for country, region, city and time zone lookup by IP address | FREE |
| IP API | https://ip-api.com/ | Free domain/IP geolocation info | FREE |
| Name | Link | Description | Price |
|---|---|---|---|
| Mylnikov API | https://www.mylnikov.org | public API implementation of Wi-Fi Geo-Location database | FREE |
| Wigle | https://api.wigle.net/ | get location and other information by SSID | FREE |
| Name | Link | Description | Price |
|---|---|---|---|
| PeetingDB | https://www.peeringdb.com/apidocs/ | Database of networks, and the go-to location for interconnection data | FREE |
| PacketTotal | https://packettotal.com/api.html | .pcap files analyze | FREE |
| Name | Link | Description | Price |
|---|---|---|---|
| Binlist.net | https://binlist.net/ | get information about bank by BIN | FREE |
| FDIC Bank Data API | https://banks.data.fdic.gov/docs/ | institutions, locations and history events | FREE |
| Amdoren | https://www.amdoren.com/currency-api/ | Free currency API with over 150 currencies | FREE |
| VATComply.com | https://www.vatcomply.com/documentation | Exchange rates, geolocation and VAT number validation | FREE |
| Alpaca | https://alpaca.markets/docs/api-documentation/api-v2/market-data/alpaca-data-api-v2/ | Realtime and historical market data on all US equities and ETFs | FREE |
| Swiftcodesapi | https://swiftcodesapi.com | Verifying the validity of a bank SWIFT code or IBAN account number | $39 per month/4000 swift lookups |
| IBANAPI | https://ibanapi.com | Validate IBAN number and get bank account information from it | Freemium/10$ Starter plan |
| Name | Link | Description | Price |
|---|---|---|---|
| EVA | https://eva.pingutil.com/ | Measuring email deliverability & quality | FREE |
| Mailboxlayer | https://mailboxlayer.com/ | Simple REST API measuring email deliverability & quality | 100 requests FREE, 5000 requests in month — $14.49 |
| EmailCrawlr | https://emailcrawlr.com/ | Get key information about company websites. Find all email addresses associated with a domain. Get social accounts associated with an email. Verify email address deliverability. | 200 requests FREE, 5000 requets — $40 |
| Voila Norbert | https://www.voilanorbert.com/api/ | Find anyone's email address and ensure your emails reach real people | from $49 in month |
| Kickbox | https://open.kickbox.com/ | Email verification API | FREE |
| FachaAPI | https://api.facha.dev/ | Allows checking if an email domain is a temporary email domain | FREE |
| Name | Link | Description | Price |
|---|---|---|---|
| Genderize.io | https://genderize.io | Instantly answers the question of how likely a certain name is to be male or female and shows the popularity of the name. | 1000 names/day free |
| Agify.io | https://agify.io | Predicts the age of a person given their name | 1000 names/day free |
| Nataonalize.io | https://nationalize.io | Predicts the nationality of a person given their name | 1000 names/day free |
| Name | Link | Description | Price |
|---|---|---|---|
| HaveIBeenPwned | https://haveibeenpwned.com/API/v3 | allows the list of pwned accounts (email addresses and usernames) | $3.50 per month |
| Psdmp.ws | https://psbdmp.ws/api | search in Pastebin | $9.95 per 10000 requests |
| LeakPeek | https://psbdmp.ws/api | searc in leaks databases | $9.99 per 4 weeks unlimited access |
| BreachDirectory.com | https://breachdirectory.com/api_documentation | search domain in data breaches databases | FREE |
| LeekLookup | https://leak-lookup.com/api | search domain, email_address, fullname, ip address, phone, password, username in leaks databases | 10 requests FREE |
| BreachDirectory.org | https://rapidapi.com/rohan-patra/api/breachdirectory/pricing | search domain, email_address, fullname, ip address, phone, password, username in leaks databases (possible to view password hashes) | 50 requests in month/FREE |
| Name | Link | Description | Price |
|---|---|---|---|
| Wayback Machine API (Memento API, CDX Server API, Wayback Availability JSON API) | https://archive.org/help/wayback_api.php | Retrieve information about Wayback capture data | FREE |
| TROVE (Australian Web Archive) API | https://trove.nla.gov.au/about/create-something/using-api | Retrieve information about TROVE capture data | FREE |
| Archive-it API | https://support.archive-it.org/hc/en-us/articles/115001790023-Access-Archive-It-s-Wayback-index-with-the-CDX-C-API | Retrieve information about archive-it capture data | FREE |
| UK Web Archive API | https://ukwa-manage.readthedocs.io/en/latest/#api-reference | Retrieve information about UK Web Archive capture data | FREE |
| Arquivo.pt API | https://github.com/arquivo/pwa-technologies/wiki/Arquivo.pt-API | Allows full-text search and access preserved web content and related metadata. It is also possible to search by URL, accessing all versions of preserved web content. API returns a JSON object. | FREE |
| Library Of Congress archive API | https://www.loc.gov/apis/ | Provides structured data about Library of Congress collections | FREE |
| BotsArchive | https://botsarchive.com/docs.html | JSON formatted details about Telegram Bots available in database | FREE |
| Name | Link | Description | Price |
|---|---|---|---|
| MD5 Decrypt | https://md5decrypt.net/en/Api/ | Search for decrypted hashes in the database | 1.99 EURO/day |
| Name | Link | Description | Price |
|---|---|---|---|
| BTC.com | https://btc.com/btc/adapter?type=api-doc | get information about addresses and transanctions | FREE |
| Blockchair | https://blockchair.com | Explore data stored on 17 blockchains (BTC, ETH, Cardano, Ripple etc) | $0.33 - $1 per 1000 calls |
| Bitcointabyse | https://www.bitcoinabuse.com/api-docs | Lookup bitcoin addresses that have been linked to criminal activity | FREE |
| Bitcoinwhoswho | https://www.bitcoinwhoswho.com/api | Scam reports on the Bitcoin Address | FREE |
| Etherscan | https://etherscan.io/apis | Ethereum explorer API | FREE |
| apilayer coinlayer | https://coinlayer.com | Real-time Crypto Currency Exchange Rates | FREE |
| BlockFacts | https://blockfacts.io/ | Real-time crypto data from multiple exchanges via a single unified API, and much more | FREE |
| Brave NewCoin | https://bravenewcoin.com/developers | Real-time and historic crypto data from more than 200+ exchanges | FREE |
| WorldCoinIndex | https://www.worldcoinindex.com/apiservice | Cryptocurrencies Prices | FREE |
| WalletLabels | https://www.walletlabels.xyz/docs | Labels for 7,5 million Ethereum wallets | FREE |
| Name | Link | Description | Price |
|---|---|---|---|
| VirusTotal | https://developers.virustotal.com/reference | files and urls analyze | Public API is FREE |
| AbuseLPDB | https://docs.abuseipdb.com/#introduction | IP/domain/URL reputation | FREE |
| AlienVault Open Threat Exchange (OTX) | https://otx.alienvault.com/api | IP/domain/URL reputation | FREE |
| Phisherman | https://phisherman.gg | IP/domain/URL reputation | FREE |
| URLScan.io | https://urlscan.io/about-api/ | Scan and Analyse URLs | FREE |
| Web of Thrust | https://support.mywot.com/hc/en-us/sections/360004477734-API- | IP/domain/URL reputation | FREE |
| Threat Jammer | https://threatjammer.com/docs/introduction-threat-jammer-user-api | IP/domain/URL reputation | ??? |
| Name | Link | Description | Price |
|---|---|---|---|
| Search4faces | https://search4faces.com/api.html | Detect and locate human faces within an image, and returns high-precision face bounding boxes. Face⁺⁺ also allows you to store metadata of each detected face for future use. | $21 per 1000 requests |
## Face Detection
| Name | Link | Description | Price |
|---|---|---|---|
| Face++ | https://www.faceplusplus.com/face-detection/ | Search for people in social networks by facial image | from 0.03 per call |
| BetaFace | https://www.betafaceapi.com/wpa/ | Can scan uploaded image files or image URLs, find faces and analyze them. API also provides verification (faces comparison) and identification (faces search) services, as well able to maintain multiple user-defined recognition databases (namespaces) | 50 image per day FREE/from 0.15 EUR per request |
## Reverse Image Search
| Name | Link | Description | Price |
|---|---|---|---|
| Google Reverse images search API | https://github.com/SOME-1HING/google-reverse-image-api/ | This is a simple API built using Node.js and Express.js that allows you to perform Google Reverse Image Search by providing an image URL. | FREE (UNOFFICIAL) |
| TinEyeAPI | https://services.tineye.com/TinEyeAPI | Verify images, Moderate user-generated content, Track images and brands, Check copyright compliance, Deploy fraud detection solutions, Identify stock photos, Confirm the uniqueness of an image | Start from $200/5000 searches |
| Bing Images Search API | https://www.microsoft.com/en-us/bing/apis/bing-image-search-api | With Bing Image Search API v7, help users scour the web for images. Results include thumbnails, full image URLs, publishing website info, image metadata, and more. | 1,000 requests free per month FREE |
| MRISA | https://github.com/vivithemage/mrisa | MRISA (Meta Reverse Image Search API) is a RESTful API which takes an image URL, does a reverse Google image search, and returns a JSON array with the search results | FREE? (no official) |
| PicImageSearch | https://github.com/kitUIN/PicImageSearch | Aggregator for different Reverse Image Search API | FREE? (no official) |
## AI Geolocation
| Name | Link | Description | Price |
|---|---|---|---|
| Geospy | https://api.geospy.ai/ | Detecting estimation location of uploaded photo | Access by request |
| Picarta | https://picarta.ai/api | Detecting estimation location of uploaded photo | 100 request/day FREE |
| Name | Link | Description | Price |
|---|---|---|---|
| Twitch | https://dev.twitch.tv/docs/v5/reference | ||
| YouTube Data API | https://developers.google.com/youtube/v3 | ||
| https://www.reddit.com/dev/api/ | |||
| Vkontakte | https://vk.com/dev/methods | ||
| Twitter API | https://developer.twitter.com/en | ||
| Linkedin API | https://docs.microsoft.com/en-us/linkedin/ | ||
| All Facebook and Instagram API | https://developers.facebook.com/docs/ | ||
| Whatsapp Business API | https://www.whatsapp.com/business/api | ||
| Telegram and Telegram Bot API | https://core.telegram.org | ||
| Weibo API | https://open.weibo.com/wiki/API文档/en | ||
| https://dev.xing.com/partners/job_integration/api_docs | |||
| Viber | https://developers.viber.com/docs/api/rest-bot-api/ | ||
| Discord | https://discord.com/developers/docs | ||
| Odnoklassniki | https://ok.ru/apiok | ||
| Blogger | https://developers.google.com/blogger/ | The Blogger APIs allows client applications to view and update Blogger content | FREE |
| Disqus | https://disqus.com/api/docs/auth/ | Communicate with Disqus data | FREE |
| Foursquare | https://developer.foursquare.com/ | Interact with Foursquare users and places (geolocation-based checkins, photos, tips, events, etc) | FREE |
| HackerNews | https://github.com/HackerNews/API | Social news for CS and entrepreneurship | FREE |
| Kakao | https://developers.kakao.com/ | Kakao Login, Share on KakaoTalk, Social Plugins and more | FREE |
| Line | https://developers.line.biz/ | Line Login, Share on Line, Social Plugins and more | FREE |
| TikTok | https://developers.tiktok.com/doc/login-kit-web | Fetches user info and user's video posts on TikTok platform | FREE |
| Tumblr | https://www.tumblr.com/docs/en/api/v2 | Read and write Tumblr Data | FREE |
!WARNING Use with caution! Accounts may be blocked permanently for using unofficial APIs.
| Name | Link | Description | Price |
|---|---|---|---|
| TikTok | https://github.com/davidteather/TikTok-Api | The Unofficial TikTok API Wrapper In Python | FREE |
| Google Trends | https://github.com/suryasev/unofficial-google-trends-api | Unofficial Google Trends API | FREE |
| YouTube Music | https://github.com/sigma67/ytmusicapi | Unofficial APi for YouTube Music | FREE |
| Duolingo | https://github.com/KartikTalwar/Duolingo | Duolingo unofficial API (can gather info about users) | FREE |
| Steam. | https://github.com/smiley/steamapi | An unofficial object-oriented Python library for accessing the Steam Web API. | FREE |
| https://github.com/ping/instagram_private_api | Instagram Private API | FREE | |
| Discord | https://github.com/discordjs/discord.js | JavaScript library for interacting with the Discord API | FREE |
| Zhihu | https://github.com/syaning/zhihu-api | FREE Unofficial API for Zhihu | FREE |
| Quora | https://github.com/csu/quora-api | Unofficial API for Quora | FREE |
| DnsDumbster | https://github.com/PaulSec/API-dnsdumpster.com | (Unofficial) Python API for DnsDumbster | FREE |
| PornHub | https://github.com/sskender/pornhub-api | Unofficial API for PornHub in Python | FREE |
| Skype | https://github.com/ShyykoSerhiy/skyweb | Unofficial Skype API for nodejs via 'Skype (HTTP)' protocol. | FREE |
| Google Search | https://github.com/aviaryan/python-gsearch | Google Search unofficial API for Python with no external dependencies | FREE |
| Airbnb | https://github.com/nderkach/airbnb-python | Python wrapper around the Airbnb API (unofficial) | FREE |
| Medium | https://github.com/enginebai/PyMedium | Unofficial Medium Python Flask API and SDK | FREE |
| https://github.com/davidyen1124/Facebot | Powerful unofficial Facebook API | FREE | |
| https://github.com/tomquirk/linkedin-api | Unofficial Linkedin API for Python | FREE | |
| Y2mate | https://github.com/Simatwa/y2mate-api | Unofficial Y2mate API for Python | FREE |
| Livescore | https://github.com/Simatwa/livescore-api | Unofficial Livescore API for Python | FREE |
| Name | Link | Description | Price |
|---|---|---|---|
| Google Custom Search JSON API | https://developers.google.com/custom-search/v1/overview | Search in Google | 100 requests FREE |
| Serpstack | https://serpstack.com/ | Google search results to JSON | FREE |
| Serpapi | https://serpapi.com | Google, Baidu, Yandex, Yahoo, DuckDuckGo, Bint and many others search results | $50/5000 searches/month |
| Bing Web Search API | https://www.microsoft.com/en-us/bing/apis/bing-web-search-api | Search in Bing (+instant answers and location) | 1000 transactions per month FREE |
| WolframAlpha API | https://products.wolframalpha.com/api/pricing/ | Short answers, conversations, calculators and many more | from $25 per 1000 queries |
| DuckDuckgo Instant Answers API | https://duckduckgo.com/api | An API for some of our Instant Answers, not for full search results. | FREE |
| Memex Marginalia | https://memex.marginalia.nu/projects/edge/api.gmi | An API for new privacy search engine | FREE |
| Name | Link | Description | Price |
|---|---|---|---|
| MediaStack | https://mediastack.com/ | News articles search results in JSON | 500 requests/month FREE |
| Name | Link | Description | Price |
|---|---|---|---|
| Darksearch.io | https://darksearch.io/apidoc | search by websites in .onion zone | FREE |
| Onion Lookup | https://onion.ail-project.org/ | onion-lookup is a service for checking the existence of Tor hidden services and retrieving their associated metadata. onion-lookup relies on an private AIL instance to obtain the metadata | FREE |
| Name | Link | Description | Price |
|---|---|---|---|
| Jackett | https://github.com/Jackett/Jackett | API for automate searching in different torrent trackers | FREE |
| Torrents API PY | https://github.com/Jackett/Jackett | Unofficial API for 1337x, Piratebay, Nyaasi, Torlock, Torrent Galaxy, Zooqle, Kickass, Bitsearch, MagnetDL,Libgen, YTS, Limetorrent, TorrentFunk, Glodls, Torre | FREE |
| Torrent Search API | https://github.com/Jackett/Jackett | API for Torrent Search Engine with Extratorrents, Piratebay, and ISOhunt | 500 queries/day FREE |
| Torrent search api | https://github.com/JimmyLaurent/torrent-search-api | Yet another node torrent scraper (supports iptorrents, torrentleech, torrent9, torrentz2, 1337x, thepiratebay, Yggtorrent, TorrentProject, Eztv, Yts, LimeTorrents) | FREE |
| Torrentinim | https://github.com/sergiotapia/torrentinim | Very low memory-footprint, self hosted API-only torrent search engine. Sonarr + Radarr Compatible, native support for Linux, Mac and Windows. | FREE |
| Name | Link | Description | Price |
|---|---|---|---|
| National Vulnerability Database CVE Search API | https://nvd.nist.gov/developers/vulnerabilities | Get basic information about CVE and CVE history | FREE |
| OpenCVE API | https://docs.opencve.io/api/cve/ | Get basic information about CVE | FREE |
| CVEDetails API | https://www.cvedetails.com/documentation/apis | Get basic information about CVE | partly FREE (?) |
| CVESearch API | https://docs.cvesearch.com/ | Get basic information about CVE | by request |
| KEVin API | https://kevin.gtfkd.com/ | API for accessing CISA's Known Exploited Vulnerabilities Catalog (KEV) and CVE Data | FREE |
| Vulners.com API | https://vulners.com | Get basic information about CVE | FREE for personal use |
| Name | Link | Description | Price |
|---|---|---|---|
| Aviation Stack | https://aviationstack.com | get information about flights, aircrafts and airlines | FREE |
| OpenSky Network | https://opensky-network.org/apidoc/index.html | Free real-time ADS-B aviation data | FREE |
| AviationAPI | https://docs.aviationapi.com/ | FAA Aeronautical Charts and Publications, Airport Information, and Airport Weather | FREE |
| FachaAPI | https://api.facha.dev | Aircraft details and live positioning API | FREE |
| Name | Link | Description | Price |
|---|---|---|---|
| Windy Webcams API | https://api.windy.com/webcams/docs | Get a list of available webcams for a country, city or geographical coordinates | FREE with limits or 9990 euro without limits |
## Regex
| Name | Link | Description | Price |
|---|---|---|---|
| Autoregex | https://autoregex.notion.site/AutoRegex-API-Documentation-97256bad2c114a6db0c5822860214d3a | Convert English phrase to regular expression | from $3.49/month |
| Name | Link |
|---|---|
| API Guessr (detect API by auth key or by token) | https://api-guesser.netlify.app/ |
| REQBIN Online REST & SOAP API Testing Tool | https://reqbin.com |
| ExtendClass Online REST Client | https://extendsclass.com/rest-client-online.html |
| Codebeatify.org Online API Test | https://codebeautify.org/api-test |
| SyncWith Google Sheet add-on. Link more than 1000 APIs with Spreadsheet | https://workspace.google.com/u/0/marketplace/app/syncwith_crypto_binance_coingecko_airbox/449644239211?hl=ru&pann=sheets_addon_widget |
| Talend API Tester Google Chrome Extension | https://workspace.google.com/u/0/marketplace/app/syncwith_crypto_binance_coingecko_airbox/449644239211?hl=ru&pann=sheets_addon_widget |
| Michael Bazzel APIs search tools | https://inteltechniques.com/tools/API.html |
| Name | Link |
|---|---|
| Convert curl commands to Python, JavaScript, PHP, R, Go, C#, Ruby, Rust, Elixir, Java, MATLAB, Dart, CFML, Ansible URI or JSON | https://curlconverter.com |
| Curl-to-PHP. Instantly convert curl commands to PHP code | https://incarnate.github.io/curl-to-php/ |
| Curl to PHP online (Codebeatify) | https://codebeautify.org/curl-to-php-online |
| Curl to JavaScript fetch | https://kigiri.github.io/fetch/ |
| Curl to JavaScript fetch (Scrapingbee) | https://www.scrapingbee.com/curl-converter/javascript-fetch/ |
| Curl to C# converter | https://curl.olsh.me |
| Name | Link |
|---|---|
| Sheety. Create API frome GOOGLE SHEET | https://sheety.co/ |
| Postman. Platform for creating your own API | https://www.postman.com |
| Reetoo. Rest API Generator | https://retool.com/api-generator/ |
| Beeceptor. Rest API mocking and intercepting in seconds (no coding). | https://beeceptor.com |
| Name | Link |
|---|---|
| RapidAPI. Market your API for millions of developers | https://rapidapi.com/solution/api-provider/ |
| Apilayer. API Marketplace | https://apilayer.com |
| Name | Link | Description |
|---|---|---|
| Keyhacks | https://github.com/streaak/keyhacks | Keyhacks is a repository which shows quick ways in which API keys leaked by a bug bounty program can be checked to see if they're valid. |
| All about APIKey | https://github.com/daffainfo/all-about-apikey | Detailed information about API key / OAuth token for different services (Description, Request, Response, Regex, Example) |
| API Guessr | https://api-guesser.netlify.app/ | Enter API Key and and find out which service they belong to |
| Name | Link | Description |
|---|---|---|
| APIDOG ApiHub | https://apidog.com/apihub/ | |
| Rapid APIs collection | https://rapidapi.com/collections | |
| API Ninjas | https://api-ninjas.com/api | |
| APIs Guru | https://apis.guru/ | |
| APIs List | https://apislist.com/ | |
| API Context Directory | https://apicontext.com/api-directory/ | |
| Any API | https://any-api.com/ | |
| Public APIs Github repo | https://github.com/public-apis/public-apis |
If you don't know how to work with the REST API, I recommend you check out the Netlas API guide I wrote for Netlas.io.
There it is very brief and accessible to write how to automate requests in different programming languages (focus on Python and Bash) and process the resulting JSON data.
Thank you for following me! https://cybdetective.com
A security architect with the National Labor Relations Board (NLRB) alleges that employees from Elon Musk‘s Department of Government Efficiency (DOGE) transferred gigabytes of sensitive data from agency case files in early March, using short-lived accounts configured to leave few traces of network activity. The NLRB whistleblower said the unusual large data outflows coincided with multiple blocked login attempts from an Internet address in Russia that tried to use valid credentials for a newly-created DOGE user account.

The cover letter from Berulis’s whistleblower statement, sent to the leaders of the Senate Select Committee on Intelligence.
The allegations came in an April 14 letter to the Senate Select Committee on Intelligence, signed by Daniel J. Berulis, a 38-year-old security architect at the NLRB.
NPR, which was the first to report on Berulis’s whistleblower complaint, says NLRB is a small, independent federal agency that investigates and adjudicates complaints about unfair labor practices, and stores “reams of potentially sensitive data, from confidential information about employees who want to form unions to proprietary business information.”
The complaint documents a one-month period beginning March 3, during which DOGE officials reportedly demanded the creation of all-powerful “tenant admin” accounts in NLRB systems that were to be exempted from network logging activity that would otherwise keep a detailed record of all actions taken by those accounts.
Berulis said the new DOGE accounts had unrestricted permission to read, copy, and alter information contained in NLRB databases. The new accounts also could restrict log visibility, delay retention, route logs elsewhere, or even remove them entirely — top-tier user privileges that neither Berulis nor his boss possessed.
Berulis writes that on March 3, a black SUV accompanied by a police escort arrived at his building — the NLRB headquarters in Southeast Washington, D.C. The DOGE staffers did not speak with Berulis or anyone else in NLRB’s IT staff, but instead met with the agency leadership.
“Our acting chief information officer told us not to adhere to standard operating procedure with the DOGE account creation, and there was to be no logs or records made of the accounts created for DOGE employees, who required the highest level of access,” Berulis wrote of their instructions after that meeting.
“We have built in roles that auditors can use and have used extensively in the past but would not give the ability to make changes or access subsystems without approval,” he continued. “The suggestion that they use these accounts was not open to discussion.”
Berulis found that on March 3 one of the DOGE accounts created an opaque, virtual environment known as a “container,” which can be used to build and run programs or scripts without revealing its activities to the rest of the world. Berulis said the container caught his attention because he polled his colleagues and found none of them had ever used containers within the NLRB network.
Berulis said he also noticed that early the next morning — between approximately 3 a.m. and 4 a.m. EST on Tuesday, March 4 — there was a large increase in outgoing traffic from the agency. He said it took several days of investigating with his colleagues to determine that one of the new accounts had transferred approximately 10 gigabytes worth of data from the NLRB’s NxGen case management system.
Berulis said neither he nor his co-workers had the necessary network access rights to review which files were touched or transferred — or even where they went. But his complaint notes the NxGen database contains sensitive information on unions, ongoing legal cases, and corporate secrets.
“I also don’t know if the data was only 10gb in total or whether or not they were consolidated and compressed prior,” Berulis told the senators. “This opens up the possibility that even more data was exfiltrated. Regardless, that kind of spike is extremely unusual because data almost never directly leaves NLRB’s databases.”
Berulis said he and his colleagues grew even more alarmed when they noticed nearly two dozen login attempts from a Russian Internet address (83.149.30,186) that presented valid login credentials for a DOGE employee account — one that had been created just minutes earlier. Berulis said those attempts were all blocked thanks to rules in place that prohibit logins from non-U.S. locations.
“Whoever was attempting to log in was using one of the newly created accounts that were used in the other DOGE related activities and it appeared they had the correct username and password due to the authentication flow only stopping them due to our no-out-of-country logins policy activating,” Berulis wrote. “There were more than 20 such attempts, and what is particularly concerning is that many of these login attempts occurred within 15 minutes of the accounts being created by DOGE engineers.”
According to Berulis, the naming structure of one Microsoft user account connected to the suspicious activity suggested it had been created and later deleted for DOGE use in the NLRB’s cloud systems: “DogeSA_2d5c3e0446f9@nlrb.microsoft.com.” He also found other new Microsoft cloud administrator accounts with nonstandard usernames, including “Whitesox, Chicago M.” and “Dancehall, Jamaica R.”
On March 5, Berulis documented that a large section of logs for recently created network resources were missing, and a network watcher in Microsoft Azure was set to the “off” state, meaning it was no longer collecting and recording data like it should have.
Berulis said he discovered someone had downloaded three external code libraries from GitHub that neither NLRB nor its contractors ever use. A “readme” file in one of the code bundles explained it was created to rotate connections through a large pool of cloud Internet addresses that serve “as a proxy to generate pseudo-infinite IPs for web scraping and brute forcing.” Brute force attacks involve automated login attempts that try many credential combinations in rapid sequence.
The complaint alleges that by March 17 it became clear the NLRB no longer had the resources or network access needed to fully investigate the odd activity from the DOGE accounts, and that on March 24, the agency’s associate chief information officer had agreed the matter should be reported to US-CERT. Operated by the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA), US-CERT provides on-site cyber incident response capabilities to federal and state agencies.
But Berulis said that between April 3 and 4, he and the associate CIO were informed that “instructions had come down to drop the US-CERT reporting and investigation and we were directed not to move forward or create an official report.” Berulis said it was at this point he decided to go public with his findings.
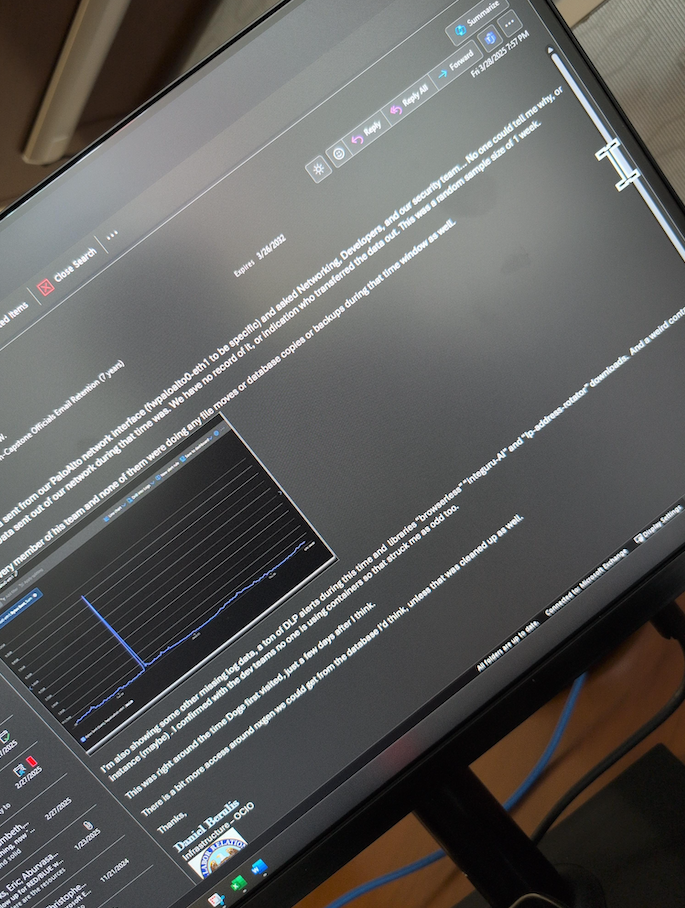
An email from Daniel Berulis to his colleagues dated March 28, referencing the unexplained traffic spike earlier in the month and the unauthorized changing of security controls for user accounts.
Tim Bearese, the NLRB’s acting press secretary, told NPR that DOGE neither requested nor received access to its systems, and that “the agency conducted an investigation after Berulis raised his concerns but ‘determined that no breach of agency systems occurred.'” The NLRB did not respond to questions from KrebsOnSecurity.
Nevertheless, Berulis has shared a number of supporting screenshots showing agency email discussions about the unexplained account activity attributed to the DOGE accounts, as well as NLRB security alerts from Microsoft about network anomalies observed during the timeframes described.
As CNN reported last month, the NLRB has been effectively hobbled since President Trump fired three board members, leaving the agency without the quorum it needs to function.
“Despite its limitations, the agency had become a thorn in the side of some of the richest and most powerful people in the nation — notably Elon Musk, Trump’s key supporter both financially and arguably politically,” CNN wrote.
Both Amazon and Musk’s SpaceX have been suing the NLRB over complaints the agency filed in disputes about workers’ rights and union organizing, arguing that the NLRB’s very existence is unconstitutional. On March 5, a U.S. appeals court unanimously rejected Musk’s claim that the NLRB’s structure somehow violates the Constitution.
Berulis shared screenshots with KrebsOnSecurity showing that on the day the NPR published its story about his claims (April 14), the deputy CIO at NLRB sent an email stating that administrative control had been removed from all employee accounts. Meaning, suddenly none of the IT employees at the agency could do their jobs properly anymore, Berulis said.
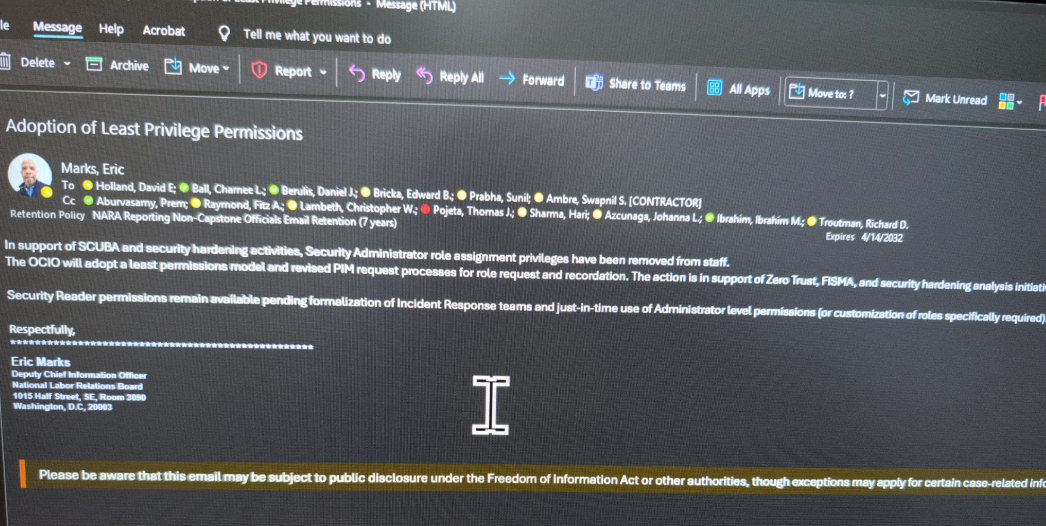
An email from the NLRB’s associate chief information officer Eric Marks, notifying employees they will lose security administrator privileges.
Berulis shared a screenshot of an agency-wide email dated April 16 from NLRB director Lasharn Hamilton saying DOGE officials had requested a meeting, and reiterating claims that the agency had no prior “official” contact with any DOGE personnel. The message informed NLRB employees that two DOGE representatives would be detailed to the agency part-time for several months.

An email from the NLRB Director Lasharn Hamilton on April 16, stating that the agency previously had no contact with DOGE personnel.
Berulis told KrebsOnSecurity he was in the process of filing a support ticket with Microsoft to request more information about the DOGE accounts when his network administrator access was restricted. Now, he’s hoping lawmakers will ask Microsoft to provide more information about what really happened with the accounts.
“That would give us way more insight,” he said. “Microsoft has to be able to see the picture better than we can. That’s my goal, anyway.”
Berulis’s attorney told lawmakers that on April 7, while his client and legal team were preparing the whistleblower complaint, someone physically taped a threatening note to Mr. Berulis’s home door with photographs — taken via drone — of him walking in his neighborhood.
“The threatening note made clear reference to this very disclosure he was preparing for you, as the proper oversight authority,” reads a preface by Berulis’s attorney Andrew P. Bakaj. “While we do not know specifically who did this, we can only speculate that it involved someone with the ability to access NLRB systems.”
Berulis said the response from friends, colleagues and even the public has been largely supportive, and that he doesn’t regret his decision to come forward.
“I didn’t expect the letter on my door or the pushback from [agency] leaders,” he said. “If I had to do it over, would I do it again? Yes, because it wasn’t really even a choice the first time.”
For now, Mr. Berulis is taking some paid family leave from the NLRB. Which is just as well, he said, considering he was stripped of the tools needed to do his job at the agency.
“They came in and took full administrative control and locked everyone out, and said limited permission will be assigned on a need basis going forward” Berulis said of the DOGE employees. “We can’t really do anything, so we’re literally getting paid to count ceiling tiles.”
Further reading: Berulis’s complaint (PDF).
Follow these steps to set up and run the API project:
git clone https://github.com/adriyansyah-mf/CentralizedFirewall
cd CentralizedFirewall
.env FileUpdate the environment variables in .env according to your configuration.
nano .env
docker compose up -d
This will start the API in detached mode.
Check if the containers are up:
docker psdocker compose down
docker compose restart
Let me know if you need any modifications! 🚀
sudo dpkg -i firewall-client_deb.deb
nano /usr/local/bin/config.ini
[settings]
api_url = API-URL
api_key = API-KEY
hostname = Node Hostname (make it unique and same as the hostname on the SIEM)
systemctl daemon-reload
systemctl start firewall-agent
systemctl status firewall-agent
Username: admin
Password: admin
You can change the default credential on the setting page
curl -X 'POST' \
'http://api-server:8000/general/add-ip?ip=123.1.1.99&hostname=test&apikey=apikey&comment=log' \
-H 'accept: application/json' \
-d ''
You can see the swagger documentation on the following link
http://api-server:8000/docs
DB=changeme
JWT_SECRET=changeme
PASSWORD_SALT=changme
PASSWORD_TOKEN_KEY=changme
OPENCTI_URL=changme
OPENCTI_TOKEN=changme
If you find this project helpful, consider supporting me through GitHub Sponsors
Clone the repository: bash git clone https://github.com/ALW1EZ/PANO.git cd PANO
Run the application:
./start_pano.sh
start_pano.bat
The startup script will automatically: - Check for updates - Set up the Python environment - Install dependencies - Launch PANO
In order to use Email Lookup transform You need to login with GHunt first. After starting the pano via starter scripts;
source venv/bin/activate
call venv\Scripts\activate
Visual node and edge styling
Timeline Analysis
Temporal relationship analysis
Map Integration
Connected services discovery
Username Analysis
Web presence analysis
Image Analysis
Entities are the fundamental building blocks of PANO. They represent distinct pieces of information that can be connected and analyzed:
📝 Text: Generic text content
Properties System
Transforms are automated operations that process entities to discover new information and relationships:
🔄 Enrichment: Add data to existing entities
Features
Helpers are specialized tools with dedicated UIs for specific investigation tasks:
🔄 Translator: Translate text between languages
Helper Features
We welcome contributions! To contribute to PANO:
Note: We use a single
mainbranch for development. All pull requests should be made directly tomain.
from dataclasses import dataclass
from typing import ClassVar, Dict, Any
from .base import Entity
@dataclass
class PhoneNumber(Entity):
name: ClassVar[str] = "Phone Number"
description: ClassVar[str] = "A phone number entity with country code and validation"
def init_properties(self):
"""Initialize phone number properties"""
self.setup_properties({
"number": str,
"country_code": str,
"carrier": str,
"type": str, # mobile, landline, etc.
"verified": bool
})
def update_label(self):
"""Update the display label"""
self.label = self.format_label(["country_code", "number"])
from dataclasses import dataclass
from typing import ClassVar, List
from .base import Transform
from entities.base import Entity
from entities.phone_number import PhoneNumber
from entities.location import Location
from ui.managers.status_manager import StatusManager
@dataclass
class PhoneLookup(Transform):
name: ClassVar[str] = "Phone Number Lookup"
description: ClassVar[str] = "Lookup phone number details and location"
input_types: ClassVar[List[str]] = ["PhoneNumber"]
output_types: ClassVar[List[str]] = ["Location"]
async def run(self, entity: PhoneNumber, graph) -> List[Entity]:
if not isinstance(entity, PhoneNumber):
return []
status = StatusManager.get()
operation_id = status.start_loading("Phone Lookup")
try:
# Your phone number lookup logic here
# Example: query an API for phone number details
location = Location(properties={
"country": "Example Country",
"region": "Example Region",
"carrier": "Example Carrier",
"source": "PhoneLookup transform"
})
return [location]
except Exception as e:
status.set_text(f"Error during phone lookup: {str(e)}")
return []
finally:
status.stop_loading(operation_id)
from PySide6.QtWidgets import (
QWidget, QVBoxLayout, QHBoxLayout, QPushButton,
QTextEdit, QLabel, QComboBox
)
from .base import BaseHelper
from qasync import asyncSlot
class DummyHelper(BaseHelper):
"""A dummy helper for testing"""
name = "Dummy Helper"
description = "A dummy helper for testing"
def setup_ui(self):
"""Initialize the helper's user interface"""
# Create input text area
self.input_label = QLabel("Input:")
self.input_text = QTextEdit()
self.input_text.setPlaceholderText("Enter text to process...")
self.input_text.setMinimumHeight(100)
# Create operation selector
operation_layout = QHBoxLayout()
self.operation_label = QLabel("Operation:")
self.operation_combo = QComboBox()
self.operation_combo.addItems(["Uppercase", "Lowercase", "Title Case"])
operation_layout.addWidget(self.operation_label)
operation_layout.addWidget(self.operation_combo)
# Create process button
self.process_btn = QPushButton("Process")
self.process_btn.clicked.connect(self.process_text)
# Create output text area
self.output_label = QLabel("Output:")
self.output_text = QTextEdit()
self.output_text.setReadOnly(True)
self.output_text.setMinimumHeight(100)
# Add widgets to main layout
self.main_layout.addWidget(self.input_label)
self.main_layout.addWidget(self.input_text)
self.main_layout.addLayout(operation_layout)
self.main_layout.addWidget(self.process_btn)
self.main_layout.addWidget(self.output_label)
self.main_layout.addWidget(self.output_text)
# Set dialog size
self.resize(400, 500)
@asyncSlot()
async def process_text(self):
"""Process the input text based on selected operation"""
text = self.input_text.toPlainText()
operation = self.operation_combo.currentText()
if operation == "Uppercase":
result = text.upper()
elif operation == "Lowercase":
result = text.lower()
else: # Title Case
result = text.title()
self.output_text.setPlainText(result)
This project is licensed under the Creative Commons Attribution-NonCommercial (CC BY-NC) License.
You are free to: - ✅ Share: Copy and redistribute the material - ✅ Adapt: Remix, transform, and build upon the material
Under these terms: - ℹ️ Attribution: You must give appropriate credit - 🚫 NonCommercial: No commercial use - 🔓 No additional restrictions
Special thanks to all library authors and contributors who made this project possible.
Created by ALW1EZ with AI ❤️
A message posted on Monday to the homepage of the U.S. Cybersecurity & Infrastructure Security Agency (CISA) is the latest exhibit in the Trump administration’s continued disregard for basic cybersecurity protections. The message instructed recently-fired CISA employees to get in touch so they can be rehired and then immediately placed on leave, asking employees to send their Social Security number or date of birth in a password-protected email attachment — presumably with the password needed to view the file included in the body of the email.
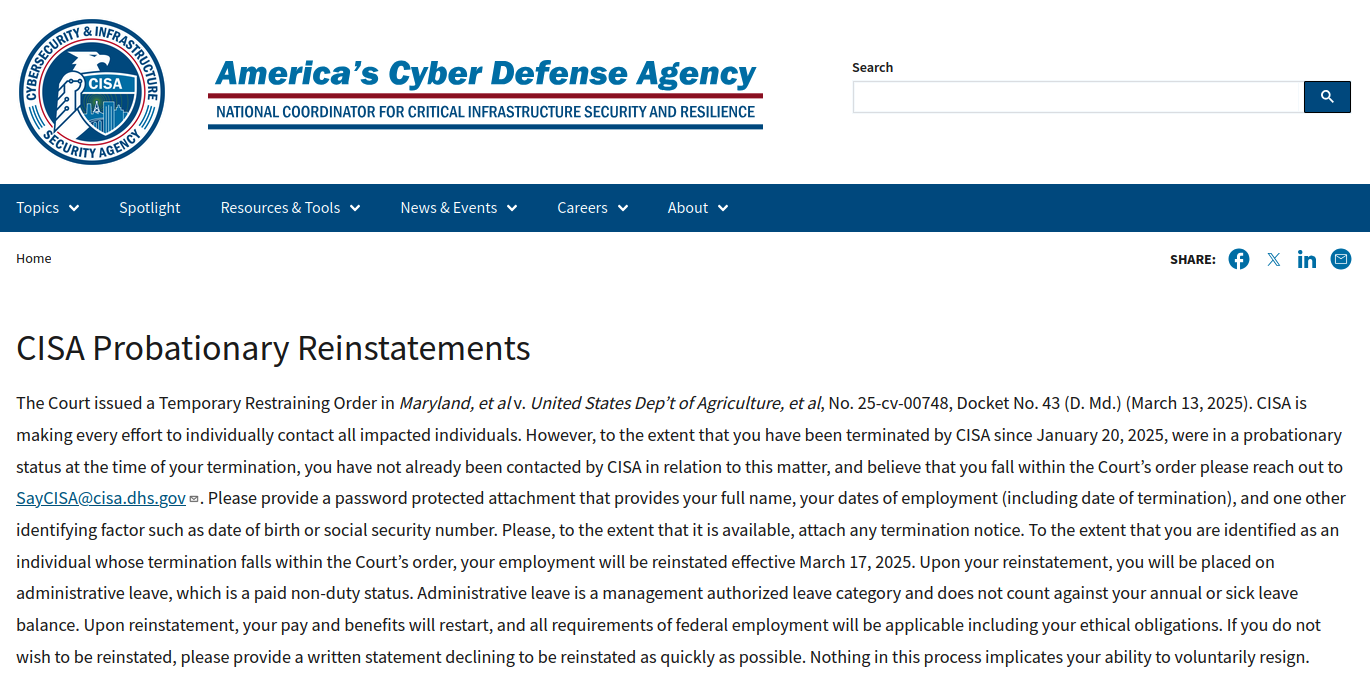
The homepage of cisa.gov as it appeared on Monday and Tuesday afternoon.
On March 13, a Maryland district court judge ordered the Trump administration to reinstate more than 130 probationary CISA employees who were fired last month. On Monday, the administration announced that those dismissed employees would be reinstated but placed on paid administrative leave. They are among nearly 25,000 fired federal workers who are in the process of being rehired.
A notice covering the CISA homepage said the administration is making every effort to contact those who were unlawfully fired in mid-February.
“Please provide a password protected attachment that provides your full name, your dates of employment (including date of termination), and one other identifying factor such as date of birth or social security number,” the message reads. “Please, to the extent that it is available, attach any termination notice.”
The message didn’t specify how affected CISA employees should share the password for any attached files, so the implicit expectation is that employees should just include the plaintext password in their message.
Email is about as secure as a postcard sent through the mail, because anyone who manages to intercept the missive anywhere along its path of delivery can likely read it. In security terms, that’s the equivalent of encrypting sensitive data while also attaching the secret key needed to view the information.
What’s more, a great many antivirus and security scanners have trouble inspecting password-protected files, meaning the administration’s instructions are likely to increase the risk that malware submitted by cybercriminals could be accepted and opened by U.S. government employees.
The message in the screenshot above was removed from the CISA homepage Tuesday evening and replaced with a much shorter notice directing former CISA employees to contact a specific email address. But a slightly different version of the same message originally posted to CISA’s website still exists at the website for the U.S. Citizenship and Immigration Services, which likewise instructs those fired employees who wish to be rehired and put on leave to send a password-protected email attachment with sensitive personal data.
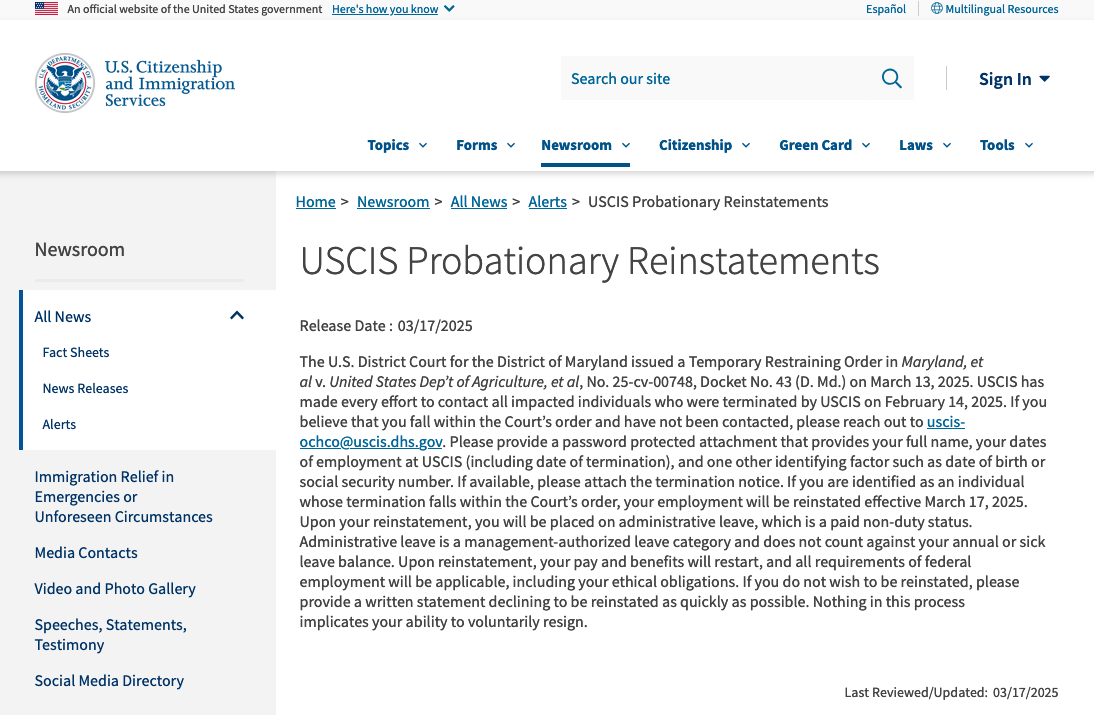
A message from the White House to fired federal employees at the U.S. Citizenship and Immigration Services instructs recipients to email personal information in a password-protected attachment.
This is hardly the first example of the administration discarding Security 101 practices in the name of expediency. Last month, the Central Intelligence Agency (CIA) sent an unencrypted email to the White House with the first names and first letter of the last names of recently hired CIA officers who might be easy to fire.
As cybersecurity journalist Shane Harris noted in The Atlantic, even those fragments of information could be useful to foreign spies.
“Over the weekend, a former senior CIA official showed me the steps by which a foreign adversary who knew only his first name and last initial could have managed to identify him from the single line of the congressional record where his full name was published more than 20 years ago, when he became a member of the Foreign Service,” Harris wrote. “The former official was undercover at the time as a State Department employee. If a foreign government had known even part of his name from a list of confirmed CIA officers, his cover would have been blown.”
The White House has also fired at least 100 intelligence staffers from the National Security Agency (NSA), reportedly for using an internal NSA chat tool to discuss their personal lives and politics. Testifying before the House Select Committee on the Communist Party earlier this month, the NSA’s former top cybersecurity official said the Trump administration’s attempts to mass fire probationary federal employees will be “devastating” to U.S. cybersecurity operations.
Rob Joyce, who spent 34 years at the NSA, told Congress how important those employees are in sustaining an aggressive stance against China in cyberspace.
“At my former agency, remarkable technical talent was recruited into developmental programs that provided intensive unique training and hands-on experience to cultivate vital skills,” Joyce told the panel. “Eliminating probationary employees will destroy a pipeline of top talent responsible for hunting and eradicating [Chinese] threats.”
Both the message to fired CISA workers and DOGE’s ongoing efforts to bypass vetted government networks for a faster Wi-Fi signal are emblematic of this administration’s overall approach to even basic security measures: To go around them, or just pretend they don’t exist for a good reason.
On Monday, The New York Times reported that U.S. Secret Service agents at the White House were briefly on alert last month when a trusted captain of Elon Musk’s “Department of Government Efficiency” (DOGE) visited the roof of the Eisenhower building inside the White House compound — to see about setting up a dish to receive satellite Internet access directly from Musk’s Starlink service.
The White House press secretary told The Times that Starlink had “donated” the service and that the gift had been vetted by the lawyer overseeing ethics issues in the White House Counsel’s Office. The White House claims the service is necessary because its wireless network is too slow.
Jake Williams, vice president for research and development at the cybersecurity consulting firm Hunter Strategy, told The Times “it’s super rare” to install Starlink or another internet provider as a replacement for existing government infrastructure that has been vetted and secured.
“I can’t think of a time that I have heard of that,” Williams said. “It introduces another attack point,” Williams said. “But why introduce that risk?”
Meanwhile, NBC News reported on March 7 that Starlink is expanding its footprint across the federal government.
“Multiple federal agencies are exploring the idea of adopting SpaceX’s Starlink for internet access — and at least one agency, the General Services Administration (GSA), has done so at the request of Musk’s staff, according to someone who worked at the GSA last month and is familiar with its network operations — despite a vow by Musk and Trump to slash the overall federal budget,” NBC wrote.
The longtime Musk employee who encountered the Secret Service on the roof in the White House complex was Christopher Stanley, the 33-year-old senior director for security engineering at X and principal security engineer at SpaceX.
On Monday, Bloomberg broke the news that Stanley had been tapped for a seat on the board of directors at the mortgage giant Fannie Mae. Stanley was added to the board alongside newly confirmed Federal Housing Finance Agency director Bill Pulte, the grandson of the late housing businessman and founder of PulteGroup — William J. Pulte.
In a nod to his new board role atop an agency that helps drive the nation’s $12 trillion mortgage market, Stanley retweeted a Bloomberg story about the hire with a smiley emoji and the comment “Tech Support.”
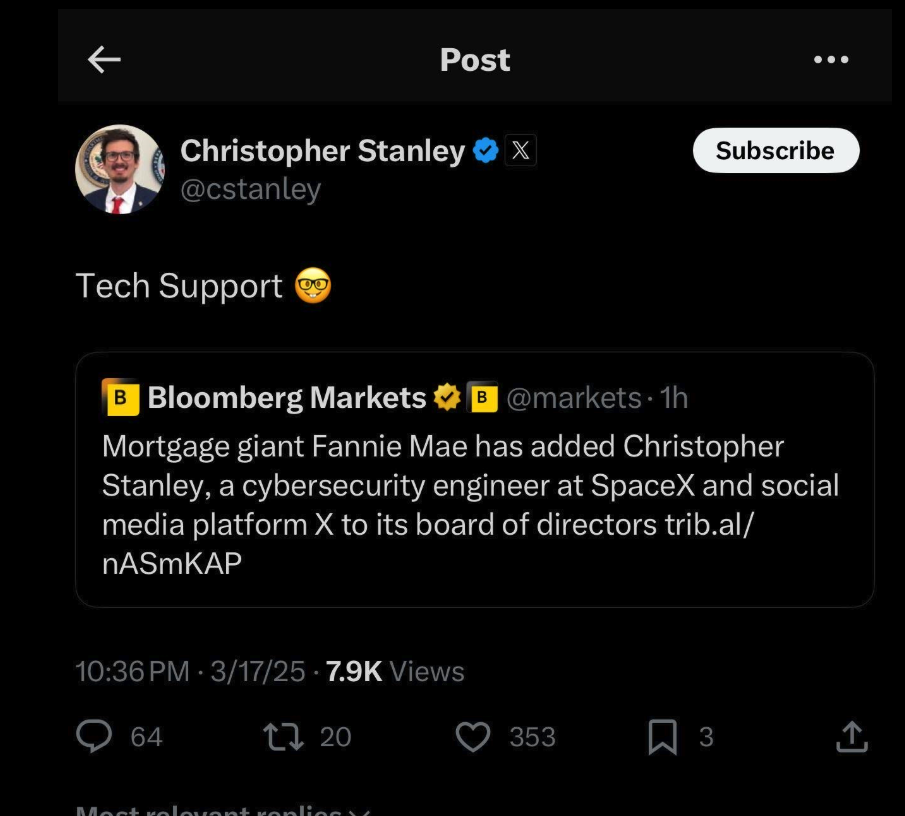
But earlier today, Bloomberg reported that Stanley had abruptly resigned from the Fannie board, and that details about the reason for his quick departure weren’t immediately clear. As first reported here last month, Stanley had a brush with celebrity on Twitter in 2015 when he leaked the user database for the DDoS-for-hire service LizardStresser, and soon faced threats of physical violence against his family.
My 2015 story on that leak did not name Stanley, but he exposed himself as the source by posting a video about it on his Youtube channel. A review of domain names registered by Stanley shows he went by the nickname “enKrypt,” and was the former owner of a pirated software and hacking forum called error33[.]net, as well as theC0re, a video game cheating community.
Stanley is one of more than 50 DOGE workers, mostly young men and women who have worked with one or more of Musk’s companies. The Trump administration remains dogged by questions about how many — if any — of the DOGE workers were put through the gauntlet of a thorough security background investigation before being given access to such sensitive government databases.
That’s largely because in one of his first executive actions after being sworn in for a second term on Jan. 20, President Trump declared that the security clearance process was simply too onerous and time-consuming, and that anyone so designated by the White House counsel would have full top secret/sensitive compartmented information (TS/SCI) clearances for up to six months. Translation: We accepted the risk, so TAH-DAH! No risk!
Presumably, this is the same counsel who saw no ethical concerns with Musk “donating” Starlink to the White House, or with President Trump summoning the media to film him hawking Cybertrucks and Teslas (a.k.a. “Teslers”) on the White House lawn last week.
Mr. Musk’s unelected role as head of an ad hoc executive entity that is gleefully firing federal workers and feeding federal agencies into “the wood chipper” has seen his Tesla stock price plunge in recent weeks, while firebombings and other vandalism attacks on property carrying the Tesla logo are cropping up across the U.S. and overseas and driving down Tesla sales.
President Trump and his attorney general Pam Bondi have dubiously asserted that those responsible for attacks on Tesla dealerships are committing “domestic terrorism,” and that vandals will be prosecuted accordingly. But it’s not clear this administration would recognize a real domestic security threat if it was ensconced squarely behind the Resolute Desk.
Or at the pinnacle of the Federal Bureau of Investigation (FBI). The Washington Post reported last month that Trump’s new FBI director Kash Patel was paid $25,000 last year by a film company owned by a dual U.S. Russian citizen that has made programs promoting “deep state” conspiracy theories pushed by the Kremlin.
“The resulting six-part documentary appeared on Tucker Carlson’s online network, itself a reliable conduit for Kremlin propaganda,” The Post reported. “In the film, Patel made his now infamous pledge to shut down the FBI’s headquarters in Washington and ‘open it up as a museum to the deep state.'”
When the head of the FBI is promising to turn his own agency headquarters into a mocking public exhibit on the U.S. National Mall, it may seem silly to fuss over the White House’s clumsy and insulting instructions to former employees they unlawfully fired.
Indeed, one consistent feedback I’ve heard from a subset of readers here is something to this effect: “I used to like reading your stuff more when you weren’t writing about politics all the time.”
My response to that is: “Yeah, me too.” It’s not that I’m suddenly interested in writing about political matters; it’s that various actions by this administration keep intruding on my areas of coverage.
A less charitable interpretation of that reader comment is that anyone still giving such feedback is either dangerously uninformed, being disingenuous, or just doesn’t want to keep being reminded that they’re on the side of the villains, despite all the evidence showing it.
Article II of the U.S. Constitution unambiguously states that the president shall take care that the laws be faithfully executed. But almost from Day One of his second term, Mr. Trump has been acting in violation of his sworn duty as president by choosing not to enforce laws passed by Congress (TikTok ban, anyone?), by freezing funds already allocated by Congress, and most recently by flouting a federal court order while simultaneously calling for the impeachment of the judge who issued it. Sworn to uphold, protect and defend The Constitution, President Trump appears to be creating new constitutional challenges with almost each passing day.
When Mr. Trump was voted out of office in November 2020, he turned to baseless claims of widespread “election fraud” to explain his loss — with deadly and long-lasting consequences. This time around, the rallying cry of DOGE and White House is “government fraud,” which gives the administration a certain amount of cover for its actions among a base of voters that has long sought to shrink the size and cost of government.
In reality, “government fraud” has become a term of derision and public scorn applied to anything or anyone the current administration doesn’t like. If DOGE and the White House were truly interested in trimming government waste, fraud and abuse, they could scarcely do better than consult the inspectors general fighting it at various federal agencies.
After all, the inspectors general likely know exactly where a great deal of the federal government’s fiscal skeletons are buried. Instead, Mr. Trump fired at least 17 inspectors general, leaving the government without critical oversight of agency activities. That action is unlikely to stem government fraud; if anything, it will only encourage such activity.
As Techdirt founder Mike Masnick noted in a recent column “Why Techdirt is Now a Democracy Blog (Whether We Like it or Not),” when the very institutions that made American innovation possible are being systematically dismantled, it’s not a “political” story anymore: It’s a story about whether the environment that enabled all the other stories we cover will continue to exist.
“This is why tech journalism’s perspective is so crucial right now,” Masnick wrote. “We’ve spent decades documenting how technology and entrepreneurship can either strengthen or undermine democratic institutions. We understand the dangers of concentrated power in the digital age. And we’ve watched in real-time as tech leaders who once championed innovation and openness now actively work to consolidate control and dismantle the very systems that enabled their success.”
“But right now, the story that matters most is how the dismantling of American institutions threatens everything else we cover,” Masnick continued. “When the fundamental structures that enable innovation, protect civil liberties, and foster open dialogue are under attack, every other tech policy story becomes secondary.”
One month into his second term, President Trump’s actions to shrink the government through mass layoffs, firings and withholding funds allocated by Congress have thrown federal cybersecurity and consumer protection programs into disarray. At the same time, agencies are battling an ongoing effort by the world’s richest man to wrest control over their networks and data.

Image: Shutterstock. Greg Meland.
The Trump administration has fired at least 130 employees at the federal government’s foremost cybersecurity body — the Cybersecurity and Infrastructure Security Agency (CISA). Those dismissals reportedly included CISA staff dedicated to securing U.S. elections, and fighting misinformation and foreign influence operations.
Earlier this week, technologists with Elon Musk’s Department of Government Efficiency (DOGE) arrived at CISA and gained access to the agency’s email and networked files. Those DOGE staffers include Edward “Big Balls” Coristine, a 19-year-old former denizen of the “Com,” an archipelago of Discord and Telegram chat channels that function as a kind of distributed cybercriminal social network.
The investigative journalist Jacob Silverman writes that Coristine is the grandson of Valery Martynov, a KGB double agent who spied for the United States. Silverman recounted how Martynov’s wife Natalya Martynova moved to the United States with her two children after her husband’s death.
“Her son became a Virginia police officer who sometimes posts comments on blogs about his historically famous father,” Silverman wrote. “Her daughter became a financial professional who married Charles Coristine, the proprietor of LesserEvil, a snack company. Among their children is a 19-year-old young man named Edward Coristine, who currently wields an unknown amount of power and authority over the inner-workings of our federal government.”
Another member of DOGE is Christopher Stanley, formerly senior director for security engineering at X and principal security engineer at Musk’s SpaceX. Stanley, 33, had a brush with celebrity on Twitter in 2015 when he leaked the user database for the DDoS-for-hire service LizardStresser, and soon faced threats of physical violence against his family.
My 2015 story on that leak did not name Stanley, but he exposed himself as the source by posting a video about it on his Youtube channel. A review of domain names registered by Stanley shows he went by the nickname “enKrypt,” and was the former owner of a pirated software and hacking forum called error33[.]net, as well as theC0re, a video game cheating community.
DOGE has been steadily gaining sensitive network access to federal agencies that hold a staggering amount of personal and financial information on Americans, including the Social Security Administration (SSA), the Department of Homeland Security, the Office of Personnel Management (OPM), and the Treasury Department.
Most recently, DOGE has sought broad access to systems at the Internal Revenue Service that contain the personal tax information on millions of Americans, including how much individuals earn and owe, property information, and even details related to child custody agreements. The New York Times reported Friday that the IRS had reached an agreement whereby a single DOGE employee — 25-year-old Gavin Kliger — will be allowed to see only anonymized taxpayer information.
The rapidity with which DOGE has rifled through one federal database after another in the name of unearthing “massive fraud” by government agencies has alarmed many security experts, who warned that DOGE’s actions bypassed essential safeguards and security measures.
“The most alarming aspect isn’t just the access being granted,” wrote Bruce Schneier and Davi Ottenheimer, referring to DOGE as a national cyberattack. “It’s the systematic dismantling of security measures that would detect and prevent misuse—including standard incident response protocols, auditing, and change-tracking mechanisms—by removing the career officials in charge of those security measures and replacing them with inexperienced operators.”
Jacob Williams is a former hacker with the U.S. National Security Agency who now works as managing director of the cybersecurity firm Hunter Labs. Williams kicked a virtual hornet’s nest last week when he posted on LinkedIn that the network incursions by DOGE were “a bigger threat to U.S. federal government information systems than China.”
Williams said while he doesn’t believe anyone at DOGE would intentionally harm the integrity and availability of these systems, it’s widely reported (and not denied) that DOGE introduced code changes into multiple federal IT systems. These code changes, he maintained, are not following the normal process for vetting and review given to federal government IT systems.
“For those thinking ‘I’m glad they aren’t following the normal federal government IT processes, those are too burdensome’ I get where you’re coming from,” Williams wrote. “But another name for ‘red tape’ are ‘controls.’ If you’re comfortable bypassing controls for the advancement of your agenda, I have questions – mostly about whether you do this in your day job too. Please tag your employer letting them know your position when you comment that controls aren’t important (doubly so if you work in cybersecurity). All satire aside, if you’re comfortable abandoning controls for expediency, I implore you to decide where the line is that you won’t cross in that regard.”
The DOGE website’s “wall of receipts” boasts that Musk and his team have saved the federal government more than $55 billion through staff reductions, lease cancellations and terminated contracts. But a team of reporters at The New York Times found the math that could back up those checks is marred with accounting errors, incorrect assumptions, outdated data and other mistakes.
For example, DOGE claimed it saved $8 billion in one contract, when the total amount was actually $8 million, The Times found.
“Some contracts the group claims credit for were double- or triple-counted,” reads a Times story with six bylines. “Another initially contained an error that inflated the totals by billions of dollars. While the DOGE team has surely cut some number of billions of dollars, its slapdash accounting adds to a pattern of recklessness by the group, which has recently gained access to sensitive government payment systems.”
So far, the DOGE website does not inspire confidence: We learned last week that the doge.gov administrators somehow left their database wide open, allowing someone to publish messages that ridiculed the site’s insecurity.
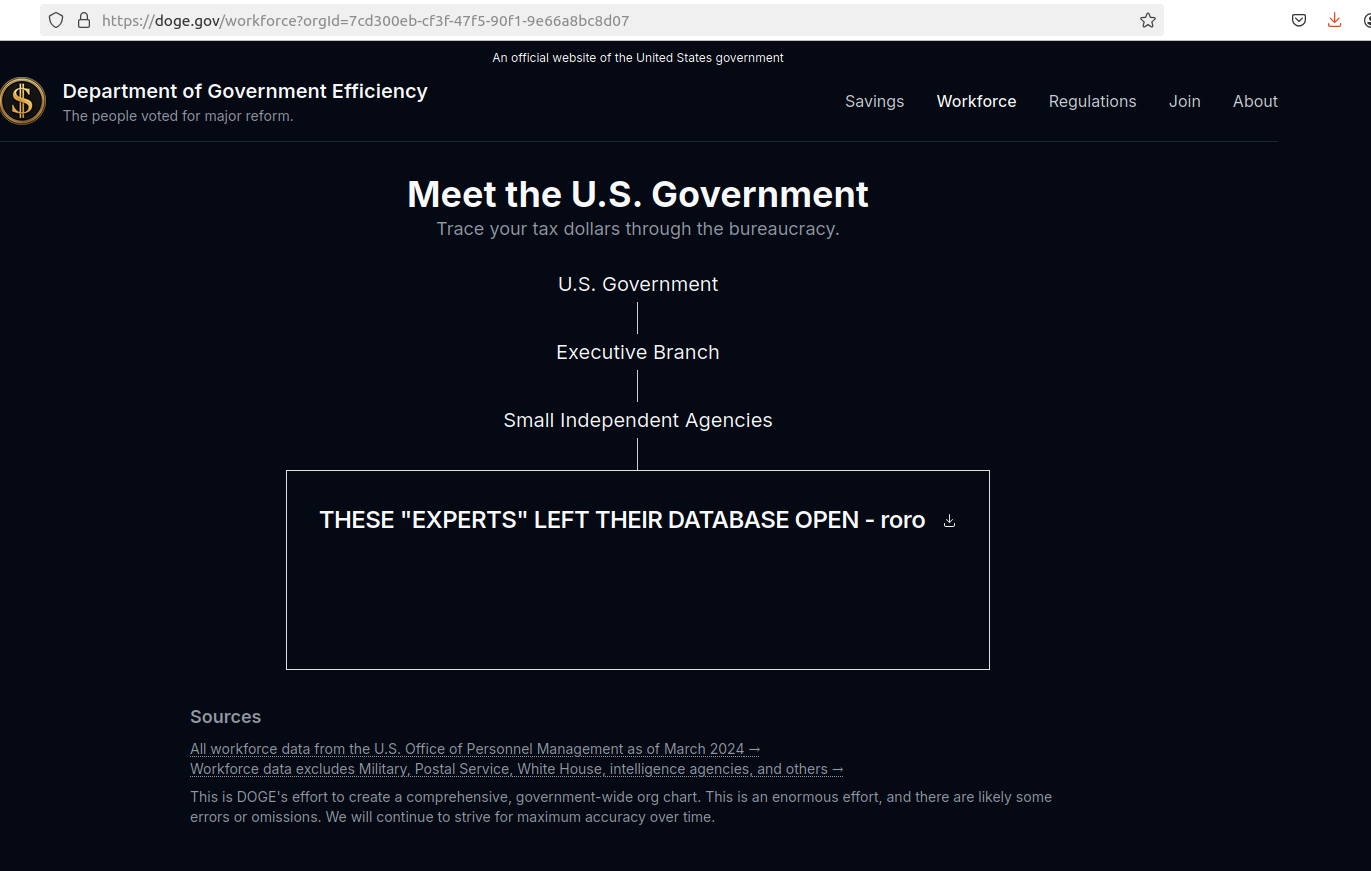
A screenshot of the DOGE website after it was defaced with the message: “These ‘experts’ left their database open – roro”
Trump’s efforts to grab federal agencies by their data has seen him replace career civil servants who refused to allow DOGE access to agency networks. CNN reports that Michelle King, acting commissioner of the Social Security Administration for more than 30 years, was shown the door after she denied DOGE access to sensitive information.
King was replaced by Leland Dudek, formerly a senior advisor in the SSA’s Office of Program Integrity. This week, Dudek posted a now-deleted message on LinkedIn acknowledging he had been placed on administrative leave for cooperating with DOGE.
“I confess,” Dudek wrote. “I bullied agency executives, shared executive contact information, and circumvented the chain of command to connect DOGE with the people who get stuff done. I confess. I asked where the fat was and is in our contracts so we can make the right tough choices.”
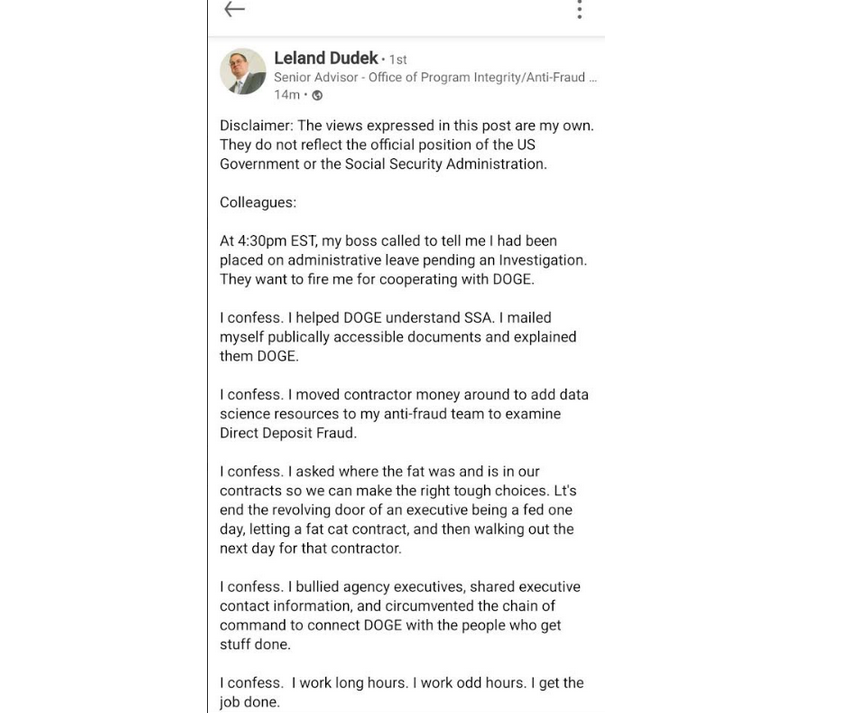
Dudek’s message on LinkedIn.
According to Wired, the National Institute of Standards and Technology (NIST) was also bracing this week for roughly 500 staffers to be fired, which could have serious impacts on NIST’s cybersecurity standards and software vulnerability tracking work.
“And cuts last week at the US Digital Service included the cybersecurity lead for the central Veterans Affairs portal, VA.gov, potentially leaving VA systems and data more vulnerable without someone in his role,” Wired’s Andy Greenberg and Lily Hay Newman wrote.
NextGov reports that Trump named the Department of Defense’s new chief information security officer: Katie Arrington, a former South Carolina state lawmaker who helped steer Pentagon cybersecurity contracting policy before being put on leave amid accusations that she disclosed classified data from a military intelligence agency.
NextGov notes that the National Security Agency suspended her clearance in 2021, although the exact reasons that led to the suspension and her subsequent leave were classified. Arrington argued that the suspension was a politically motivated effort to silence her.
Trump also appointed the former chief operating officer of the Republican National Committee as the new head of the Office of National Cyber Director. Sean Cairncross, who has no formal experience in technology or security, will be responsible for coordinating national cybersecurity policy, advising the president on cyber threats, and ensuring a unified federal response to emerging cyber-risks, Politico writes.
DarkReading reports that Cairncross would share responsibility for advising the president on cyber matters, along with the director of cyber at the White House National Security Council (NSC) — a group that advises the president on all matters security related, and not just cyber.
The president also ordered staffers at the Consumer Financial Protection Bureau (CFPB) to stop most work. Created by Congress in 2011 to be a clearinghouse of consumer complaints, the CFPB has sued some of the nation’s largest financial institutions for violating consumer protection laws.
The CFPB says its actions have put nearly $18 billion back in Americans’ pockets in the form of monetary compensation or canceled debts, and imposed $4 billion in civil money penalties against violators. The CFPB’s homepage has featured a “404: Page not found” error for weeks now.
Trump has appointed Russell Vought, the architect of the conservative policy playbook Project 2025, to be the CFPB’s acting director. Vought has publicly favored abolishing the agency, as has Elon Musk, whose efforts to remake X into a payments platform would otherwise be regulated by the CFPB.
The New York Times recently published a useful graphic showing all of the government staffing changes, including the firing of several top officials, affecting agencies with federal investigations into or regulatory battles with Musk’s companies. Democrats on the House Judiciary Committee also have released a comprehensive account (PDF) of Musk’s various conflicts of interest.
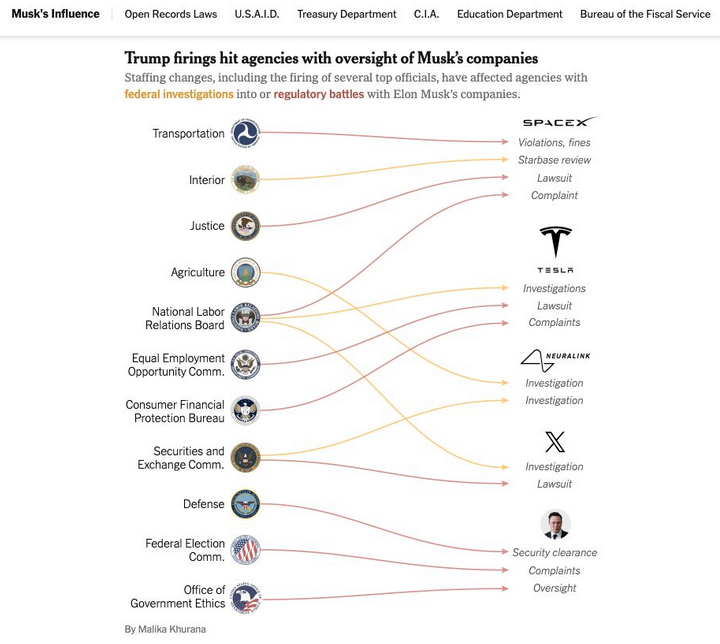
Image: nytimes.com
As the Times notes, Musk and his companies have repeatedly failed to comply with federal reporting protocols aimed at protecting state secrets, and these failures have prompted at least three federal reviews. Those include an inquiry launched last year by the Defense Department’s Office of Inspector General. Four days after taking office, Trump fired the DoD inspector general along with 17 other inspectors general.
The Trump administration also shifted the enforcement priorities of the U.S. Securities and Exchange Commission (SEC) away from prosecuting misconduct in the cryptocurrency sector, reassigning lawyers and renaming the unit to focus more on “cyber and emerging technologies.”
Reuters reports that the former SEC chair Gary Gensler made fighting misconduct in a sector he termed the “wild west” a priority for the agency, targeting not only cryptocurrency fraudsters but also the large firms that facilitate trading such as Coinbase.
On Friday, Coinbase said the SEC planned to withdraw its lawsuit against the crypto exchange. Also on Friday, the cryptocurrency exchange Bybit announced on X that a cybersecurity breach led to the theft of more than $1.4 billion worth of cryptocurrencies — making it the largest crypto heist ever.
On Feb. 10, Trump ordered executive branch agencies to stop enforcing the U.S. Foreign Corrupt Practices Act, which froze foreign bribery investigations, and even allows for “remedial actions” of past enforcement actions deemed “inappropriate.”
Trump’s action also disbanded the Kleptocracy Asset Recovery Initiative and KleptoCapture Task Force — units which proved their value in corruption cases and in seizing the assets of sanctioned Russian oligarchs — and diverted resources away from investigating white-collar crime.
That’s according to the independent Organized Crime and Corruption Reporting Project (OCCRP), an investigative journalism outlet that until very recently was funded in part by the U.S. Agency for International Development (USAID).
The OCCRP lost nearly a third of its funding and was forced to lay off 43 reporters and staff after Trump moved to shutter USAID and freeze its spending. NBC News reports the Trump administration plans to gut the agency and leave fewer than 300 staffers on the job out of the current 8,000 direct hires and contractors.
The Global Investigative Journalism Network wrote this week that the sudden hold on USAID foreign assistance funding has frozen an estimated $268 million in agreed grants for independent media and the free flow of information in more than 30 countries — including several under repressive regimes.
Elon Musk has called USAID “a criminal organization” without evidence, and promoted fringe theories on his social media platform X that the agency operated without oversight and was rife with fraud. Just months before the election, USAID’s Office of Inspector General announced an investigation into USAID’s oversight of Starlink satellite terminals provided to the government of Ukraine.
KrebsOnSecurity this week heard from a trusted source that all outgoing email from USAID now carries a notation of “sensitive but unclassified,” a designation that experts say could make it more difficult for journalists and others to obtain USAID email records under the Freedom of Information Act (FOIA). On Feb. 20, Fedscoop reported also hearing the same thing from multiple sources, noting that the added message cannot be seen by senders until after the email is sent.
On Feb. 18, Trump issued an executive order declaring that only the U.S. attorney general and the president can provide authoritative interpretations of the law for the executive branch, and that this authority extends to independent agencies operating under the executive branch.
Trump is arguing that Article II, Clause 1 of the Constitution vests this power with the president. However, jurist.org writes that Article II does not expressly state the president or any other person in the executive branch has the power to interpret laws.
“The article states that the president is required to ‘take care that the laws be faithfully executed,'” Juris noted. “Jurisdiction to interpret laws and determine constitutionality belongs to the judicial branch under Article III. The framers of the Constitution designed the separation of duties to prevent any single branch of government from becoming too powerful.”
The executive order requires all agencies to submit to “performance standards and management objectives” to be established by the White House Office of Management and Budget, and to report periodically to the president.
Those performance metrics are already being requested: Employees at multiple federal agencies on Saturday reported receiving an email from the Office of Personnel Management ordering them to reply with a set of bullet points justifying their work for the past week.
“Please reply to this email with approx. 5 bullets of what you accomplished last week and cc your manager,” the notice read. “Please do not send any classified information, links, or attachments. Deadline is this Monday at 11:59 p.m. EST.”
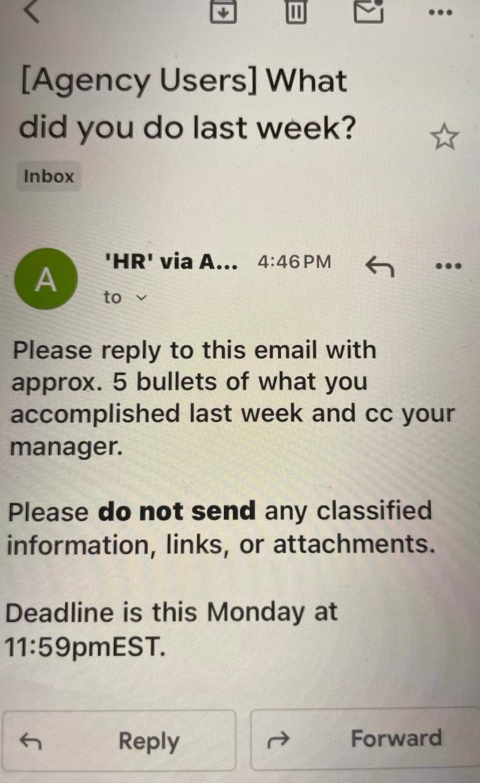
An email sent by the OPM to more than two million federal employees late in the afternoon EST on Saturday, Feb. 22.
In a social media post Saturday, Musk said the directive came at the behest of President Trump, and that failure to respond would be taken as a resignation. Meanwhile, Bloomberg writes the Department of Justice has been urging employees to hold off replying out of concern doing so could trigger ethics violations. The National Treasury Employees Union also is advising its employees not to respond.
A legal battle over Trump’s latest executive order is bound to join more than 70 other lawsuits currently underway to halt the administration’s efforts to massively reduce the size of the federal workforce through layoffs, firings and attrition.
On Feb. 15, the president posted on social media, “He who saves his Country does not violate any Law,” citing a quote often attributed to the French dictator Napoleon Bonaparte. Four days later, Trump referred to himself as “the king” on social media, while the White House nonchalantly posted an illustration of him wearing a crown.
Trump has been publicly musing about running for an unconstitutional third-term in office, a statement that some of his supporters dismiss as Trump just trying to rile his liberal critics. However, just days after Trump began his second term, Rep. Andy Ogles (R-Tenn.) introduced a bill to amend the Constitution so that Trump — and any other future president — can be elected to serve a third term.
This week at the Conservative Political Action Conference (CPAC), Rep. Ogles reportedly led a group of Trump supporters calling itself the “Third Term Project,” which is trying to gain support for the bill from GOP lawmakers. The event featured images of Trump depicted as Caesar.

A banner at the CPAC conference this week in support of The Third Term Project, a group of conservatives trying to gain support for a bill to amend the Constitution and allow Trump to run for a third term.
Russia continues to be among the world’s top exporters of cybercrime, narcotics, money laundering, human trafficking, disinformation, war and death, and yet the Trump administration has suddenly broken with the Western world in normalizing relations with Moscow.
This week President Trump stunned U.S. allies by repeating Kremlin talking points that Ukraine is somehow responsible for Russia’s invasion, and that Ukrainian President Volodymyr Zelensky is a “dictator.” The president repeated these lies even as his administration is demanding that Zelensky give the United States half of his country’s mineral wealth in exchange for a promise that Russia will cease its territorial aggression there.
President Trump’s servility toward an actual dictator — Russian President Vladimir Putin — does not bode well for efforts to improve the cybersecurity of U.S. federal IT networks, or the private sector systems on which the government is largely reliant. In addition, this administration’s baffling moves to alienate, antagonize and sideline our closest allies could make it more difficult for the United States to secure their ongoing cooperation in cybercrime investigations.
It’s also startling how closely DOGE’s approach so far hews to tactics typically employed by ransomware gangs: A group of 20-somethings with names like “Big Balls” shows up on a weekend and gains access to your servers, deletes data, locks out key staff, takes your website down, and prevents you from serving customers.
When the federal executive starts imitating ransomware playbooks against its own agencies while Congress largely gazes on in either bewilderment or amusement, we’re in four-alarm fire territory. At least in theory, one can negotiate with ransomware purveyors.

Data Privacy Week is here, and there’s no better time to shine a spotlight on one of the biggest players in the personal information economy: data brokers. These entities collect, buy, and sell hundreds—sometimes thousands—of data points on individuals like you. But how do they manage to gather so much information, and for what purpose? From your browsing habits and purchase history to your location data and even more intimate details, these digital middlemen piece together surprisingly comprehensive profiles. The real question is: where are they getting it all, and why is your personal data so valuable to them? Let’s unravel the mystery behind the data broker industry.
Data brokers aggregate user info from various sources on the internet. They collect, collate, package, and sometimes even analyze this data to create a holistic and coherent version of you online. This data then gets put up for sale to nearly anyone who’ll buy it. That can include marketers, private investigators, tech companies, and sometimes law enforcement as well. They’ll also sell to spammers and scammers. (Those bad actors need to get your contact info from somewhere — data brokers are one way to get that and more.)
And that list of potential buyers goes on, which includes but isn’t limited to:
These companies and social media platforms use your data to better understand target demographics and the content with which they interact. While the practice isn’t unethical in and of itself (personalizing user experiences and creating more convenient UIs are usually cited as the primary reasons for it), it does make your data vulnerable to malicious attacks targeted toward big-tech servers.
Most of your online activities are related. Devices like your phone, laptop, tablets, and even fitness watches are linked to each other. Moreover, you might use one email ID for various accounts and subscriptions. This online interconnectedness makes it easier for data brokers to create a cohesive user profile.
Mobile phone apps are the most common way for data brokerage firms to collect your data. You might have countless apps for various purposes, such as financial transactions, health and fitness, or social media.
A number of these apps usually fall under the umbrella of the same or subsidiary family of apps, all of which work toward collecting and supplying data to big tech platforms. Programs like Google’s AdSense make it easier for developers to monetize their apps in exchange for the user information they collect.
Data brokers also collect data points like your home address, full name, phone number, and date of birth. They have automated scraping tools to quickly collect relevant information from public records (think sales of real estate, marriages, divorces, voter registration, and so on).
Lastly, data brokers can gather data from other third parties that track your cookies or even place trackers or cookies on your browsers. Cookies are small data files that track your online activities when visiting different websites. They track your IP address and browsing history, which third parties can exploit. Cookies are also the reason you see personalized ads and products.
Data brokers collate your private information into one package and sell it to “people search” websites. As mentioned above, practically anyone can access these websites and purchase extensive consumer data, for groups of people and individuals alike.
Next, marketing and sales firms are some of data brokers’ biggest clients. These companies purchase massive data sets from data brokers to research your data profile. They have advanced algorithms to segregate users into various consumer groups and target you specifically. Their predictive algorithms can suggest personalized ads and products to generate higher lead generation and conversation percentages for their clients.
We tend to accept the terms and conditions that various apps ask us to accept without thinking twice or reading the fine print. You probably cannot proceed without letting the app track certain data or giving your personal information. To a certain extent, we trade some of our privacy for convenience. This becomes public information, and apps and data brokers collect, track, and use our data however they please while still complying with the law.
There is no comprehensive privacy law in the U.S. on a federal level. This allows data brokers to collect personal information and condense it into marketing insights. While not all methods of gathering private data are legal, it is difficult to track the activities of data brokers online (especially on the dark web). As technology advances, there are also easier ways to harvest and exploit data.
As of March 2024, 15 states in the U.S. have data privacy laws in place. That includes California, Virginia, Connecticut, Colorado, Utah, Iowa, Indiana, Tennessee, Oregon, Montana, Texas, Delaware, Florida, New Jersey, and New Hampshire.[i] The laws vary by state, yet generally, they grant rights to individuals around the collection, use, and disclosure of their personal data by businesses.
However, these laws make exceptions for certain types of data and certain types of collectors. In short, these laws aren’t absolute.
Some data brokers let you remove your information from their websites. There are also extensive guides available online that list the method by which you can opt-out of some of the biggest data brokering firms. For example, a guide by Griffin Boyce, the systems administrator at Harvard University’s Berkman Klein Center for Internet and Society, provides detailed information on how to opt-out of a long list of data broker companies.
Yet the list of data brokers is long. Cleaning up your personal data online can quickly eat up your time, as it requires you to reach out to multiple data brokers and opt-out.
Rather than removing yourself one by one from the host of data broker sites out there, you have a solid option: our Personal Data Cleanup.
Personal Data Cleanup scans data broker sites and shows you which ones are selling your personal info. It also provides guidance on how you can remove your data from those sites. And if you want to save time on manually removing that info, you have options. Our McAfee+ Advanced and Ultimate plans come with full-service Personal Data Cleanup, which sends requests to remove your data automatically.
If the thought of your personal info getting bought and sold in such a public way bothers you, our Personal Data Cleanup can put you back in charge of it.
[i] https://pro.bloomberglaw.com/insights/privacy/state-privacy-legislation-tracker/
The post How Data Brokers Sell Your Identity appeared first on McAfee Blog.

McAfee threat researchers have identified several consumer brands and product categories most frequently used by cybercriminals to trick consumers into clicking on malicious links in the first weeks of this holiday shopping season. As holiday excitement peaks and shoppers hunt for the perfect gifts and amazing deals, scammers are taking advantage of the buzz. The National Retail Federation projects holiday spending will reach between $979.5 and $989 billion this year, and cybercriminals are capitalizing by creating scams that mimic the trusted brands and categories consumers trust. From October 1 to November 12, 2024, McAfee safeguarded its customers from 624,346 malicious or suspicious URLs tied to popular consumer brand names – a clear indication that bad actors are exploiting trusted brand names to deceive holiday shoppers.
McAfee’s threat research also reveals a 33.82% spike in malicious URLs targeting consumers with these brands’ names in the run-up to Black Friday and Cyber Monday. This rise in fraudulent activity aligns with holiday shopping patterns during a time when consumers may be more susceptible to clicking on offers from well-known brands like Apple, Yeezy, and Louis Vuitton, especially when deals seem too good to be true – pointing to the need for consumers to stay vigilant, especially with offers that seem unusually generous or come from unverified sources.
McAfee threat researchers have identified a surge in counterfeit sites and phishing scams that use popular luxury brands and tech products to lure consumers into “deals” on fake e-commerce sites designed to appear as official brand pages. While footwear and handbags were identified as the top two product categories exploited by cybercrooks during this festive time, the list of most exploited brands extends beyond those borders:
By mimicking trusted brands like these, offering unbelievable deals, or posing as legitimate customer service channels, cybercrooks create convincing traps designed to steal personal information or money. Here are some of the most common tactics scammers are using this holiday season:
With holiday shopping in full swing, it’s essential for consumers to stay one step ahead of scammers. By understanding the tactics cybercriminals use and taking a few precautionary measures, shoppers can protect themselves from falling victim to fraud. Here are some practical tips for safe shopping this season:
McAfee’s threat research team analyzed malicious or suspicious URLs that McAfee’s web reputation technology identified as targeting customers, by using a list of key company and product brand names—based on insights from a Potter Clarkson report on frequently faked brands—to query the URLs. This methodology captures instances where users either clicked on or were directed to dangerous sites mimicking trusted brands. Additionally, the team queried anonymized user activity from October 1st through November 12th.
The image below is a screenshot of a fake / malicious / scam site: Yeezy is a popular product brand formerly from Adidas found in multiple Malicious/Suspicious URLs. Often, they present themselves as official Yeezy and/or Adidas shopping sites.
The image below is a screenshot of a fake / malicious / scam site: The Apple brand was a popular target for scammers. Many sites were either knock offs, scams, or in this case, a fake customer service page designed to lure users into a scam.
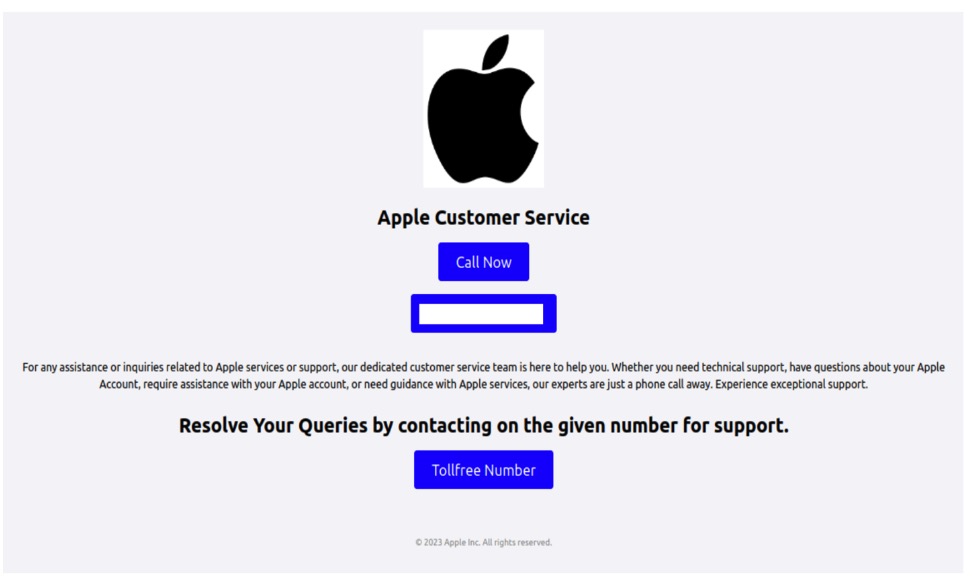
The image below is a screenshot of a fake / malicious / scam site: This particular (fake) Apple sales site used Apple within its URL and name to appear more official. Oddly, this site also sells Samsung Android phones.
The image below is a screenshot of a fake / malicious / scam site: This site, now taken down, is a scam site purporting to sell Nike shoes.
The image below is a screenshot of a fake / malicious / scam site: Louis Vuitton is a popular brand for counterfeit and scams. Particularly their handbags. Here is one site that was entirely focused on Louis Vuitton Handbags.
The image below is a screenshot of a fake / malicious / scam site: This site presents itself as the official Louis Vuitton site selling handbags and clothes.
The image below is a screenshot of a fake / malicious / scam site: This site uses too-good-to-be-true deals on branded items including this Louis Vuitton Bomber jacket.
The image below is a screenshot of a fake / malicious / scam site: Rolex is a popular watch brand for counterfeits and scams. This site acknowledges it sells counterfeits and makes no effort to indicate this on the product.
The post This Holiday Season, Watch Out for These Cyber-Grinch Tricks Used to Scam Holiday Shoppers appeared first on McAfee Blog.
secator is a task and workflow runner used for security assessments. It supports dozens of well-known security tools and it is designed to improve productivity for pentesters and security researchers.
Curated list of commands
Unified input options
Unified output schema
CLI and library usage
Distributed options with Celery
Complexity from simple tasks to complex workflows
secator integrates the following tools:
| Name | Description | Category |
|---|---|---|
| httpx | Fast HTTP prober. | http |
| cariddi | Fast crawler and endpoint secrets / api keys / tokens matcher. | http/crawler |
| gau | Offline URL crawler (Alien Vault, The Wayback Machine, Common Crawl, URLScan). | http/crawler |
| gospider | Fast web spider written in Go. | http/crawler |
| katana | Next-generation crawling and spidering framework. | http/crawler |
| dirsearch | Web path discovery. | http/fuzzer |
| feroxbuster | Simple, fast, recursive content discovery tool written in Rust. | http/fuzzer |
| ffuf | Fast web fuzzer written in Go. | http/fuzzer |
| h8mail | Email OSINT and breach hunting tool. | osint |
| dnsx | Fast and multi-purpose DNS toolkit designed for running DNS queries. | recon/dns |
| dnsxbrute | Fast and multi-purpose DNS toolkit designed for running DNS queries (bruteforce mode). | recon/dns |
| subfinder | Fast subdomain finder. | recon/dns |
| fping | Find alive hosts on local networks. | recon/ip |
| mapcidr | Expand CIDR ranges into IPs. | recon/ip |
| naabu | Fast port discovery tool. | recon/port |
| maigret | Hunt for user accounts across many websites. | recon/user |
| gf | A wrapper around grep to avoid typing common patterns. | tagger |
| grype | A vulnerability scanner for container images and filesystems. | vuln/code |
| dalfox | Powerful XSS scanning tool and parameter analyzer. | vuln/http |
| msfconsole | CLI to access and work with the Metasploit Framework. | vuln/http |
| wpscan | WordPress Security Scanner | vuln/multi |
| nmap | Vulnerability scanner using NSE scripts. | vuln/multi |
| nuclei | Fast and customisable vulnerability scanner based on simple YAML based DSL. | vuln/multi |
| searchsploit | Exploit searcher. | exploit/search |
Feel free to request new tools to be added by opening an issue, but please check that the tool complies with our selection criterias before doing so. If it doesn't but you still want to integrate it into secator, you can plug it in (see the dev guide).
pipx install secator
pip install secator
wget -O - https://raw.githubusercontent.com/freelabz/secator/main/scripts/install.sh | sh
docker run -it --rm --net=host -v ~/.secator:/root/.secator freelabz/secator --help
alias secator="docker run -it --rm --net=host -v ~/.secator:/root/.secator freelabz/secator"
secator --help
git clone https://github.com/freelabz/secator
cd secator
docker-compose up -d
docker-compose exec secator secator --help
Note: If you chose the Bash, Docker or Docker Compose installation methods, you can skip the next sections and go straight to Usage.
secator uses external tools, so you might need to install languages used by those tools assuming they are not already installed on your system.
We provide utilities to install required languages if you don't manage them externally:
secator install langs go
secator install langs ruby
secator does not install any of the external tools it supports by default.
We provide utilities to install or update each supported tool which should work on all systems supporting apt:
secator install tools
secator install tools <TOOL_NAME>
secator install tools httpx
Please make sure you are using the latest available versions for each tool before you run secator or you might run into parsing / formatting issues.
secator comes installed with the minimum amount of dependencies.
There are several addons available for secator:
secator install addons worker
secator install addons google
secator install addons mongodb
secator install addons redis
secator install addons dev
secator install addons trace
secator install addons build
secator makes remote API calls to https://cve.circl.lu/ to get in-depth information about the CVEs it encounters. We provide a subcommand to download all known CVEs locally so that future lookups are made from disk instead:
secator install cves
To figure out which languages or tools are installed on your system (along with their version):
secator health
secator --help
Run a fuzzing task (ffuf):
secator x ffuf http://testphp.vulnweb.com/FUZZ
Run a url crawl workflow:
secator w url_crawl http://testphp.vulnweb.com
Run a host scan:
secator s host mydomain.com
and more... to list all tasks / workflows / scans that you can use:
secator x --help
secator w --help
secator s --help
To go deeper with secator, check out: * Our complete documentation * Our getting started tutorial video * Our Medium post * Follow us on social media: @freelabz on Twitter and @FreeLabz on YouTube
Malicious hackers are exploiting a zero-day vulnerability in Versa Director, a software product used by many Internet and IT service providers. Researchers believe the activity is linked to Volt Typhoon, a Chinese cyber espionage group focused on infiltrating critical U.S. networks and laying the groundwork for the ability to disrupt communications between the United States and Asia during any future armed conflict with China.
Image: Shutterstock.com
Versa Director systems are primarily used by Internet service providers (ISPs), as well as managed service providers (MSPs) that cater to the IT needs of many small to mid-sized businesses simultaneously. In a security advisory published Aug. 26, Versa urged customers to deploy a patch for the vulnerability (CVE-2024-39717), which the company said is fixed in Versa Director 22.1.4 or later.
Versa said the weakness allows attackers to upload a file of their choosing to vulnerable systems. The advisory placed much of the blame on Versa customers who “failed to implement system hardening and firewall guidelines…leaving a management port exposed on the internet that provided the threat actors with initial access.”
Versa’s advisory doesn’t say how it learned of the zero-day flaw, but its vulnerability listing at mitre.org acknowledges “there are reports of others based on backbone telemetry observations of a 3rd party provider, however these are unconfirmed to date.”
Those third-party reports came in late June 2024 from Michael Horka, senior lead information security engineer at Black Lotus Labs, the security research arm of Lumen Technologies, which operates one of the global Internet’s largest backbones.
In an interview with KrebsOnSecurity, Horka said Black Lotus Labs identified a web-based backdoor on Versa Director systems belonging to four U.S. victims and one non-U.S. victim in the ISP and MSP sectors, with the earliest known exploit activity occurring at a U.S. ISP on June 12, 2024.
“This makes Versa Director a lucrative target for advanced persistent threat (APT) actors who would want to view or control network infrastructure at scale, or pivot into additional (or downstream) networks of interest,” Horka wrote in a blog post published today.
Black Lotus Labs said it assessed with “medium” confidence that Volt Typhoon was responsible for the compromises, noting the intrusions bear the hallmarks of the Chinese state-sponsored espionage group — including zero-day attacks targeting IT infrastructure providers, and Java-based backdoors that run in memory only.
In May 2023, the National Security Agency (NSA), the Federal Bureau of Investigation (FBI), and the Cybersecurity Infrastructure Security Agency (CISA) issued a joint warning (PDF) about Volt Typhoon, also known as “Bronze Silhouette” and “Insidious Taurus,” which described how the group uses small office/home office (SOHO) network devices to hide their activity.
In early December 2023, Black Lotus Labs published its findings on “KV-botnet,” thousands of compromised SOHO routers that were chained together to form a covert data transfer network supporting various Chinese state-sponsored hacking groups, including Volt Typhoon.
In January 2024, the U.S. Department of Justice disclosed the FBI had executed a court-authorized takedown of the KV-botnet shortly before Black Lotus Labs released its December report.
In February 2024, CISA again joined the FBI and NSA in warning Volt Typhoon had compromised the IT environments of multiple critical infrastructure organizations — primarily in communications, energy, transportation systems, and water and wastewater sectors — in the continental and non-continental United States and its territories, including Guam.
“Volt Typhoon’s choice of targets and pattern of behavior is not consistent with traditional cyber espionage or intelligence gathering operations, and the U.S. authoring agencies assess with high confidence that Volt Typhoon actors are pre-positioning themselves on IT networks to enable lateral movement to OT [operational technology] assets to disrupt functions,” that alert warned.
In a speech at Vanderbilt University in April, FBI Director Christopher Wray said China is developing the “ability to physically wreak havoc on our critical infrastructure at a time of its choosing,” and that China’s plan is to “land blows against civilian infrastructure to try to induce panic.”
Ryan English, an information security engineer at Lumen, said it’s disappointing his employer didn’t at least garner an honorable mention in Versa’s security advisory. But he said he’s glad there are now a lot fewer Versa systems exposed to this attack.
“Lumen has for the last nine weeks been very intimate with their leadership with the goal in mind of helping them mitigate this,” English said. “We’ve given them everything we could along the way, so it kind of sucks being referenced just as a third party.”

Phishing attacks have all kinds of lures. And many are so tried and true that it makes them easy to spot.
The target of a phishing attack is you. More specifically, your personal info and your money. Whether a scammer reaches out by email, with a text, or through a direct message, that’s what they’re after. And with a link, they whisk you off to a sketchy site designed to take them from you.
Just how much phishing is going on? To date, we’ve identified more than half a billion malicious sites out there. A number that grows daily. Because these attacks often succeed. One big reason why — they play on people’s emotions.
Phishing attacks always involve a form of “social engineering,” which is an academic way of saying that scammers use manipulation in their attacks. Commonly, scammers pretend to be a legitimate person or business.
You can get a better idea of how this works by learning about some of the most popular scams circulating today:
The CEO Scam
This scam appears as an email from a leader in your organization, asking for highly sensitive info like company accounts, employee salaries, and Social Security numbers. The hackers “spoof”, or fake, the boss’ email address so it looks like a legitimate internal company email. That’s what makes this scam so convincing — the lure is that you want to do your job and please your boss. But keep this scam in mind if you receive an email asking for confidential or highly sensitive info. Ask the apparent sender directly whether the request is real before acting.
The Urgent Email Attachment
Phishing emails that try to trick you into downloading a dangerous attachment that can infect your computer and steal your private info have been around for a long time. This is because they work. You’ve probably received emails asking you to download attachments confirming a package delivery, trip itinerary, or prize. They might urge you to “respond immediately!” The lure here is offering you something you want and invoking a sense of urgency to get you to click.
The “Lucky” Text or Email
How fortunate! You’ve won a free gift, an exclusive service, or a great deal on a trip to Las Vegas. Just remember, whatever “limited time offer” you’re being sold, it’s probably a phishing scam designed to get you to give up your credit card number or identity info. The lure here is something free or exciting at what appears to be little or no cost to you.
The Romance Scam
This one can happen completely online, over the phone, or in person after contact is established. But the romance scam always starts with someone supposedly looking for love. The scammer often puts a phony ad online or poses as a friend-of-a-friend on social media and contacts you directly. But what starts as the promise of love or partnership, often leads to requests for money or pricey gifts. The scammer will sometimes spin a hardship story, saying they need to borrow money to come visit you or pay their phone bill so they can stay in touch. The lure here is simple — love and acceptance.
While you can’t outright stop phishing attacks from making their way to your computer or phone, you can do several things to keep yourself from falling for them. Further, you can do other things that might make it more difficult for scammers to reach you.
The content and the tone of the message can tell you quite a lot. Threatening messages or ones that play on fear are often phishing attacks, such as angry messages from a so-called tax agent looking to collect back taxes. Other messages will lean heavily on urgency, like a phony overdue payment notice. And during the holidays, watch out for loud, overexcited messages about deep discounts on hard-to-find items. Instead of linking you to a proper e-commerce site, they might link you to a scam shopping site that does nothing but steal your money and the account info you used to pay them. In all, phishing attacks indeed smell fishy. Slow down and review that message with a critical eye. It might tip you off to a scam.
Some phishing attacks can look rather convincing. So much so that you’ll want to follow up on them, like if your bank reports irregular activity on your account or a bill appears to be past due. In these cases, don’t click on the link in the message. Go straight to the website of the business or organization in question and access your account from there. Likewise, if you have questions, you can always reach out to their customer service number or web page.
When scammers contact you via social media, that can be a tell-tale sign of a scam. Consider, would an income tax collector contact you over social media? The answer there is no. For example, in the U.S. the Internal Revenue Service (IRS) makes it clear that they will never contact taxpayers via social media. (Let alone send angry, threatening messages.) In all, legitimate businesses and organizations don’t use social media as a channel for official communications. They’ve accepted ways they will, and will not, contact you. If you have any doubts about a communication you received, contact the business or organization in question directly. Follow up with one of their customer service representatives.
Some phishing attacks involve attachments packed with malware, like ransomware, viruses, and keyloggers. If you receive a message with such an attachment, delete it. Even if you receive an email with an attachment from someone you know, follow up with that person. Particularly if you weren’t expecting an attachment from them. Scammers often hijack or spoof email accounts of everyday people to spread malware.
On computers and laptops, you can hover your cursor over links without clicking on them to see the web address. Take a close look at the addresses the message is using. If it’s an email, look at the email address. Maybe the address doesn’t match the company or organization at all. Or maybe it looks like it almost does, yet it adds a few letters or words to the name. This marks yet another sign that you might have a phishing attack on your hands. Scammers also use the common tactic of a link shortener, which creates links that almost look like strings of indecipherable text. These shortened links mask the true address, which might indeed be a link to a scam site. Delete the message. If possible, report it. Many social media platforms and messaging apps have built-in controls for reporting suspicious accounts and messages.
On social media and messaging platforms, stick to following, friending, and messaging people who you really know. As for those people who contact you out of the blue, be suspicious. Sad to say, they’re often scammers canvassing these platforms for victims. Better yet, where you can, set your profile to private, which makes it more difficult for scammers to select and stalk you for an attack.
How’d that scammer get your phone number or email address anyway? Chances are, they pulled that info off a data broker site. Data brokers buy, collect, and sell detailed personal info, which they compile from several public and private sources, such as local, state, and federal records, plus third parties like supermarket shopper’s cards and mobile apps that share and sell user data. Moreover, they’ll sell it to anyone who pays for it, including people who’ll use that info for scams. You can help reduce those scam texts and calls by removing your info from those sites. Our Personal Data Cleanup scans some of the riskiest data broker sites and shows you which ones are selling your personal info.
Online protection software can protect you in several ways. First, it can offer web protection features that can identify malicious links and downloads, which can help prevent clicking them. Further, features like our web protection can steer you away from dangerous websites and block malware and phishing sites if you accidentally click on a malicious link. Additionally, our Scam Protection feature warns you of sketchy links in emails, texts, and messages. And overall, strong virus and malware protection can further block any attacks on your devices. Be sure to protect your smartphones in addition to your computers and laptops as well, particularly given all the sensitive things we do on them, like banking, shopping, and booking rides and travel.
The post How to Spot Phishing Lures appeared first on McAfee Blog.

If you want to protect your identity, finances, and privacy online, you have a pretty powerful tool at hand. It’s online protection software. Today’s protection is built to get that job done.
For starters, online protection has evolved tremendously over recent years, making it more comprehensive than ever. It goes far beyond antivirus. And it protects more than your devices. It protects you. Your identity. Your finances. Your privacy.
Given how much of daily life has shifted to our computers and phones, like our finances and shopping, there’s a strong case for getting comprehensive online protection in place.
Granted, we’re an online protection company. And of course, we hope you’ll give our protection like McAfee+ a close look. With that, a quick rundown of what it can do for you and your identity, finances, and privacy helps. In all, it shows just how comprehensive this protection gets.
This form of protection starts with Identity Monitoring. It checks the dark web for your personal info, including email, government IDs, credit card and bank account numbers, and more. If any of it shows up on the dark web, it sends you an alert with guidance that can help protect you from identity theft.
Should the unexpected happen, our Identity Theft Coverage & Restoration can get you on the path to recovery. It offers up to $2 million in coverage for legal fees, travel, and funds lost because of identity theft. Further, a licensed recovery pro can do the work for you, taking the necessary steps to repair your identity and credit.
Another way identity thieves get what they want is through scam texts, emails, and messages. You can keep clear of their shady links with our new AI-powered Scam Protection. It automatically detects links that can send you to scam sites and other destinations that steal personal info. If you accidentally click? Don’t worry, we can block risky sites if you click on a suspicious link in texts, emails, social media, and more.
As you conduct so many of your finances online, it only makes sense that you can keep tabs on them just as easily. Features like our Credit Monitoring keep an eye on changes to your credit score, report, and accounts with timely notifications and guidance so you can take action to tackle identity theft.
And if you spot something out of the ordinary, our Security Freeze can quickly stop unauthorized access. It freezes credit card, bank, and utility accounts and prevents thieves from opening new ones in your name.
Rounding things out, you also have transaction monitoring features. They track transactions on credit cards and bank accounts — shooting you a notice if unusual activity occurs. They also track retirement accounts, investments, and loans for questionable transactions. Finally, further features can help prevent a bank account takeover and keep others from taking out short-term payday loans in your name.
Several features get the job done. Our Social Privacy Manager helps you adjust more than 100 privacy settings across your social media accounts in only a few clicks. This way, your personal info is only visible to the people you want to share it with.
Another big intrusion on your privacy comes at the hands of online data brokers. They drive a multi-billion-dollar industry by collecting, batching, and selling people’s personal info. To anyone. That includes hackers, spammers, and scammers who use it to their own ends. Yet you can get your info removed from some of the worst offenders out there. Personal Data Cleanup scans data broker sites and shows you which ones are selling your personal info and helps you remove it.
Another great tool for protecting your privacy comes in the form of a VPN. As a “virtual private network,” it encrypts your activity. Think of a VPN as a private tunnel for your internet traffic. It hides your search habits and history from those who might use that info to build a profile of you — whether to serve up targeted ads or to steal personal info for identity theft. In all, a VPN gives you one of the most secure ways you can go online.
The post How to Protect Your Identity, Finances, and Security Online appeared first on McAfee Blog.

For millions of people, it’s not a workday without it — video conferencing. And plenty of business gets done that way, which has made conferencing a target for hackers. That then begs the important question, how secure is video conferencing?
The answer is pretty secure if you’re using a reputable service. Yet you can take further steps to keep hackers and party crashers out of your meetings.
Hackers and party crashers are likely motivated by one of two things: financial gain or mischief.
Given that some meetings involve confidential or sensitive info, someone might have financial motivation to join in, spy on, or record the meeting. Recently, we saw the lengths at least one AI company went to when it spied on a competitor’s video conference call.[i]
And of course, some bad actors want to cause a disruption. As we saw in recent years, they’ll barge right into a meeting and create a ruckus with rude speech and other antics.
Falling somewhere in between, some hackers might try to intrude on a meeting and slip a malware-laden attachment into chat.[ii] For one, that can lead to a major disruption. And in a business context, financial disruption as well.
How do they pull it off? The typical avenues of attack apply. They might use stolen or hijacked accounts. The meeting was inadvertently set to “public,” allowing anyone with a link to join. Otherwise, they might compromise a victim’s device to piggyback their way in.
Use a service with end-to-end encryption.
Put simply, end-to-end encryption provides a solid defense against prying eyes. With it in place, this form of encryption makes it particularly difficult for hackers to tap into the call and the data shared within it. Secure video conferencing should use 256-bit AES GCM encryption for audio and video, and for sharing of screens, whiteboard apps, and the like. On a related note, read the service’s privacy policy and ensure that its privacy, security, and data measures fit your needs.
Make your meetings private and protect them with a password.
Keep the uninvited out. First, setting your meeting to private (invitees only) will help keep things secure. Some apps also provide a notification to the meeting organizer when an invite gets forwarded. Use that feature if it’s available. Also, a password provides another hurdle for a hacker or bad actor to clear. Use a fresh one for each meeting.
Use the waiting room.
Many services put attendees into a waiting room before they enter the meeting proper. Use this feature to control who comes in and out.
Block users from taking control of the screen.
Welcome or unwelcome, you can keep guests from taking over the screen. Select the option to block everyone except the host (you) from screen sharing.
Turn on automatic updates on your conferencing app.
By turning on automatic updates, you’ll get the latest security patches and enhancements for your video conferencing tool as soon as they become available.
Get wise to phishing scams.
Some interlopers make it into meetings by impersonating others. Just as bad actors use phishing emails and texts to steal personal financial info, they’ll use them to steal company credentials as well. Our Phishing Scam Protection Guide can show you how to steer clear of these attacks.
Use online protection software.
Comprehensive online protection software like ours can make for safer calls in several ways. For one, it protects you against malware attacks, such as if a bad actor tries to slip a sketchy download into your meeting. Further, it includes a password manager that creates and stores strong, unique passwords securely. This can help increase the security of your video conferencing account.
This is a new one. AI deepfake technology continues to evolve, we find ourselves at the point where scammers can create AI imposters in real time.
We’ve seen them use this technology in romance scams, where scammers take on entirely new looks and voices on video calls. And we’ve seen at least one group of scammers bilk a company out of $25 million with deepfaked executives on a call.[iii]
Strange as it might sound, this kind of deepfake technology is possible today. And realizing that fact is the first step toward prevention. Next, that calls for extra scrutiny.
Any time-sensitive info or sums of money are involved, get confirmation of the request. Place a phone call to the person after receiving the request to ensure it’s indeed legitimate. Better yet, meet the individual in person if possible. In all, contact them outside the email, message, or call that initially made the request to ensure you’re not dealing with an imposter.
With the right provider and right steps in place, video calls can be quite secure. Use a solution that offers end-to-end encryption, keep your app updated for the latest security measures, and lock down the app’s security settings. Also, recognize that AI has changed the way we look at just about everything online — including people on the other side of the screen. As we’ve seen, AI imposters on calls now fall into the realm of possibility. A costly one at that.
[i] https://www.nytimes.com/2023/08/07/technology/ai-start-ups-competition.html
[ii] https://www.pcmag.com/news/hackers-circulate-malware-by-breaking-into-microsoft-teams-meetings
[iii] https://www.cnn.com/2024/02/04/asia/deepfake-cfo-scam-hong-kong-intl-hnk/index.html
The post How Secure is Video Conferencing? appeared first on McAfee Blog.

We all love free stuff. (Costco samples, anyone?) However, when it comes to your family’s security, do free online protection tools offer the coverage you truly need?
Not always. In fact, they might invade the privacy you’re trying to protect.
Here’s why.
Free tools don’t offer the level of advanced protection that life on today’s internet needs. For starters, you’ll want malware and antivirus protection that’s as sophisticated as the threats they shut down. Ours includes AI technology and has for years now, which helps it shut down even the latest strains of malware as they hit the internet for the first time. We’re seeing plenty of that, as hackers have also turned to AI tools to code their malicious software.
Malware and antivirus protection protects your devices. Yet a comprehensive approach protects something else. You and your family.
Comprehensive online protection looks after your family’s privacy and identity. That keeps you safe from prying eyes and things like fraud and identity theft. Today’s comprehensive protection offers more features than ever, and far more than you’ll find in a free, and so incomplete, offering.
Consider this short list of what comprehensive online protection like ours offers you and your family:
Scam Protection
Is that email, text, or message packing a scam link? Our scam protection lets you know before you click that link. It uses AI to sniff out bad links. And if you click or tap on one, no worries. It blocks links to malicious sites.
Web Protection
Like scam protection, our web protection sniffs out sketchy links while you browse. So say you stumble across a great-looking offer in a bed of search results. If it’s a link to a scam site, you’ll spot it. Also like scam protection, it blocks the site if you accidentally hit the link.
Transaction Monitoring
This helps you nip fraud in the bud. Based on the settings you provide, transaction monitoring keeps an eye out for unusual activity on your credit and debit cards. That same monitoring can extend to retirement, investment, and loan accounts as well. It can further notify you if someone tries to change the contact info on your bank accounts or take out a short-term loan in your name.
Credit Monitoring
This is an important thing to do in today’s password- and digital-driven world. Credit monitoring uncovers any inconsistencies or outright instances of fraud in your credit reports. Then it helps put you on the path to setting them straight. It further keeps an eye on your reports overall by providing you with notifications if anything changes in your history or score.
Social Privacy Manager
Our social privacy manager puts you in control of who sees what on social media. With it, you can secure your profiles the way you want. It helps you adjust more than 100 privacy settings across your social media accounts in just a few clicks. It offers recommendations as you go and makes sure your personal info is only visible to the people you want. You can even limit some of the ways that social media sites are allowed to use your data for greater peace of mind.
Personal Data Cleanup
This provides you with another powerful tool for protecting your privacy. Personal Data Cleanup removes your personal info from some of the sketchiest data broker sites out there. And they’ll sell those lines and lines of info about you to anyone. Hackers and spammers included. Personal Data Cleanup scans data broker sites and shows you which ones are selling your personal info. From there, it provides guidance for removing your data from those sites. Further, when part of our McAfee+ Advanced and Ultimate, it sends requests to remove your data automatically.
Password Manager
Scammers love weak or reused passwords. Even more so when they’re weak and reused. It offers them an easy avenue to force their way into people’s accounts. Our password manager creates and securely stores strong, unique passwords for you. That saves you the hassle of creating strong, unique passwords for your dozens and dozens of accounts. And helps protect you from fraud.
Identity Theft Coverage & Restoration
This provides you with extra assurance while you shop. Say the unfortunate happens to you and find yourself a victim of identity theft. Our coverage and restoration plan provides up to $2 million in lawyer fees and reimbursement for lawyer fees and stolen funds. Further, a licensed expert can help you repair your identity and credit. In all, this saves you money and your time if theft happens to you.
Say your online protection leaves gaps in your family’s safety, or that it uses less-effective methods and technologies. That exposes you to threats — threats can cost you time and money alike if one of those threats gets through.
One example, consider the online crimes reported to the U.S. Federal Trade Commission. In 2023, they fielded 5.4 million fraud reports. Of them, 2.6 million reported a loss for a total of $10 billion. The median loss was $500 across all reports. Of course, that’s only the median dollar amount. That number can climb much higher in individual cases.
Source: U.S. Federal Trade Commission
Without question, protection is prevention, which can spare you some significant financial losses. Not to mention the time and stress of restoring your credit and identity — and getting your money back.
A “free” solution has to make its money somehow.
Free security solutions sometimes carry in-app advertising. More importantly, they might try to gather your user data to target ads or share it with others to make a profit. Also by advertising for premium products, the vendor indirectly admits that a free solution doesn’t provide enough security.
Further, these tools also offer little to no customer support, leaving users to handle any technical difficulties on their own. What’s more, most free security solutions are meant for use on only one device, whereas the average person owns several connected devices. And that’s certainly the case for many families.
Lastly, free solutions often limit a person’s online activity too. Many impose limits on which browser or email program the user can leverage, which can be inconvenient as many already have a preferred browser or email platform.
Free security products might provide the basics, but a comprehensive solution can protect you from a host of other risks — ones that could get in the way of enjoying your time online.
With comprehensive online protection in place, your family’s devices get protection from the latest threats in the ever-evolving security landscape. It keeps your devices safe. And it keeps you safe. With that, we hope you’ll give us a close look when you decide to upgrade to comprehensive protection.
The post Why Should I Pay for Online Protection? appeared first on McAfee Blog.

“Antivirus software slows down my PC.” This is a comment that is often heard when talking about antivirus and malware protection.
That might be the case with many security products, but it’s not the case with McAfee. Independent tests since 2016 have proven that McAfee is not only good at catching malware and viruses, but also one of the lightest security products available today.
Antivirus forms a major cornerstone of online protection software. It protects your devices against malware and viruses through a combination of prevention, detection, and removal. Ours uses AI to detect the absolute latest threats — and has for several years now.
For decades, people have installed antivirus software on their computers. Today, it can also protect your smartphones and tablets as well. In fact, we recommend installing it on those devices as well because they’re connected, just like a computer. And any device that connects to the internet is a potential target for malware and viruses.
One important distinction about antivirus is its name, a name that first came into use years ago when viruses first appeared on the scene. However, antivirus protects you from more than viruses. It protects against the broad category of malware too — things like spyware, ransomware, and keyloggers.
To measure how much impact online protection software has on PC performance, some independent test labs include performance impact benchmarks in their security product tests. The most well-known of these test labs are AV-TEST, which is based in Germany, and Austria-based AV-Comparatives. These independent labs are among the most reputable and well-known anti-malware test labs in the world.
Over the years, we’ve tested strongly. Those results got stronger still with the release of our McAfee Next-gen Threat Protection.
McAfee’s AI-powered security just got faster and stronger. Our Next-gen Threat Protection takes up less disk space, reduces its background processes by 75%, and scans 3x faster than before. This makes your time online safer without slowing down your browsing, shopping, streaming, and gaming.
And the results show it.
Even with strong protection continuously monitoring all activity on your PC and laptop for threats, the best kind of antivirus keeps your devices running quickly.
Advances in our already high-performing protection have solidified our excellent standing in independent tests. The labs run them regularly, and we take pride in knowing that we’re not only protecting you, we’re keeping you moving along at a good clip.
The post Does Antivirus Software Slow You Down? appeared first on McAfee Blog.

Smartphone hacking is the unauthorized access to and control over a mobile device or its communications. This goes beyond a simple malware infection; it’s a targeted breach aimed at stealing your personal data, spying on your activities, or using your device for malicious purposes.
Unlike general viruses that may just slow down your device, a hack can lead to severe real-world consequences. This article aims to increase your awareness about hacking methods, how to prevent it or determine if your phone has been infiltrated, and how to protect your phone moving forward.
Your smartphone is a goldmine of personal information, making it a high-value target for cybercriminals whose motivations are typically centered on financial gain and identity theft. Hackers seek banking credentials, credit card numbers, and access to payment apps for direct financial theft. Meanwhile, stealing your personal information—like emails, contacts, and passwords—allows them to commit identity fraud or sell on dark-web markets.
Beyond money, attackers may use your phone for surveillance, secretly activating your camera or microphone to spy on you. In other cases, they may hijack your device’s resources to include it in a botnet for larger attacks or hold your files hostage with ransomware. Understanding these threats is the first step in knowing how to protect yourself from them, so it’s vital to learn the methods hackers use to get into your phone.
While both iOS and Android are secure, their core philosophies create different opportunities for hackers. Android’s open-source nature allows for greater customization, including the ability to “sideload” third-party apps from outside the official Google Play Store. Unvetted apps with malicious code are a primary vector for malware.
In contrast, Apple’s iOS’s closed ecosystem makes it much harder to install unauthorized software. For this reason, many attacks targeting iPhones rely on social engineering, sophisticated zero-day exploits that target unknown vulnerabilities, or jailbroken devices, which strips away Apple’s built-in protections.
To protect your device, tailor your defense to its ecosystem. The best practice for Android users is to stick to the Google Play Store and ensure Google Play Protect is active, as it continuously scans your apps for harmful behavior. iPhone users concerned about targeted attacks should activate Lockdown Mode, an extreme feature that limits functionality to reduce the potential attack surface. Regardless of your platform, keeping your operating system updated is the single most important step you can take to stay secure.
Wondering how your phone gets compromised? Hackers use several common pathways.
A hacker might install spyware after you jailbreak or root your smartphone to bypass the security of their respective stores. Jailbreaking or rooting gives smartphone users more control over their devices, such as removing pre-installed apps and installing third-party apps from unvetted sources. However, this action removes barriers that keep viruses and malware from entering the smartphone’s system and spreading to apps, files, devices and other networks. And because Apple and Google don’t review the apps in those sources, this allows the hacker to post a bad app with relative ease.
Apple has a strict review policy before apps are approved for posting in the App Store. Meanwhile, Google started applying AI-powered threat detection, stronger privacy policies, supercharged developer tools, industry-wide alliances, and other methods in its app reviews. Bad actors, however, could still sneak malware into the stores by uploading infected app versions during updates. Other times, they’ll embed malicious code that triggers only in certain countries or encrypt malicious code into the app they submit, making it difficult for reviewers to sniff out.
Cybercriminals have several sophisticated methods to hack smartphones remotely. One common technique is phishing, where you might receive a text or email with a malicious link that, when clicked, installs spyware on your device. Another remote hacking vector is through unsecured public Wi-Fi networks, where hackers can intercept your data. Spyware can also be delivered via SMS payloads that require no user interaction.
Smishing (SMS phishing) is a common and effective way for hackers to attack your phone, where they send an urgent text with a malicious link, like a fake delivery notification or a bank alert, to trick you into clicking without thinking. Once you click, the link can lead to a fake website designed to steal your login credentials or directly download malware onto your device. Attackers also use MMS messages to send malicious files, like images or videos, which in some rare “zero-click” exploits, can infect your phone without you even opening the message.
To protect yourself, treat all unexpected links in text messages with suspicion. Never click on a link from an unknown sender. A key preventive step is to go into your messaging app’s settings and disable the automatic download of MMS files. This prevents malicious media from loading onto your device automatically. Always verify urgent requests by contacting the company or person directly through a trusted channel, not by using the contact information provided in the suspicious text.
In this method, hackers use techniques like drive-by downloads, which silently installs malware onto your device the moment a page loads—no click required. Malvertising is where malicious code is hidden in online ads that, if served on a site you visit, can trigger a spyware or ransomware download. These attacks are most effective against devices with outdated web browsers, as they target known security holes that have since been patched.
Fake “update required” pop-ups are designed to scare you into installing malicious software disguised as a critical browser update. To protect yourself, always keep your mobile browser and operating system fully updated. Use your browser’s built-in safe-browsing features, and be cautious about granting permissions or clicking links on unfamiliar websites.
These two sophisticated attacks can give a hacker complete control over your phone number. In a SIM-swap attack, a criminal tricks your mobile carrier into transferring your phone number to a SIM card they control. In phone cloning, they copy the identifying information from your phone to another, making a functional duplicate. In either case, the attacker can then intercept your calls, texts, and two-factor authentication codes.
Proactive defense includes setting up a unique PIN or password on your account for an extra layer of security. Switch to an eSIM if possible, as eSIMs are not as easily swapped as physical cards. If you suspect an attack, immediately report the issue to your carrier and check your financial and email accounts for unauthorized activity. You can also use the dial codes, like *#62#, to see if your calls are being forwarded to an unknown number.
Malicious apps and spyware can secretly access your camera and microphone, potentially livestreaming audio and video to an attacker without your knowledge. Key warning signs include the camera indicator light turning on unexpectedly, significant and unexplained battery drain, or finding unfamiliar photos and videos in your gallery. To protect yourself, regularly audit the apps installed on your phone. Go into your device’s settings to review which apps have permission to access your camera and revoke access for any that don’t need it.
Network-based attacks occur over unsecured public Wi-Fi where attackers can intercept your data. Finally, unsecure cloud backups can be a weak point, as a compromised password for your Apple or Google account could give a hacker access to all the data you’ve stored. Knowing these attack vectors is the first step toward understanding how to know if your phone is hacked.
Because we spend so much time on our phones, it’s fairly easy to tell when something isn’t working right. Sometimes those issues are symptoms of an infection. Possible signs that your device has been hacked include:
If these symptoms are present, use the following tools to verify whether your device has been compromised:
The results of the scan are in: your smartphone has clearly been hacked. There is no time to lose. To start the process of blocking the hacker or removing the malware, follow these essential first steps:
Persistent problems with your smartphone after a factory reset, may indicate a sophisticated, low-level hack. If you are the victim of significant financial fraud or identity theft, or if the hack involves sensitive legal or corporate data, it is crucial to stop using your smartphone and get assistance. In these cases, continued use could tamper with evidence.
After reporting the hacking incident to your mobile carrier, and authorities, you may need a certified digital forensic analyst for deep analysis, especially in corporate or legal cases. Before you call, gather key information: the make and model of your phone, the date you first noticed issues, a list of suspicious apps or messages, and any known fraudulent activity on your accounts.
Certain dial codes, also known as Unstructured Supplementary Service Data (USSD) or Man-Machine Interface (MMI) codes, can help you check for signs of suspicious activity or hidden configurations. These codes can reveal call forwarding, SIM tracking, or conditional redirects that may indicate a compromise:
You can take simple, effective steps to protect yourself and your device from hackers. Here are some practical tips, from the basic to the more layered steps, to help you block hackers from accessing your phone.
To avoid the hassle of having a hacked phone in the first place, here are some fundamental measures you can do as part of your routine:
Beyond the foundational advice, fortifying your smartphone requires a layered defense. We suggest the following actions you can apply:
Securing your device doesn’t have to be complicated or time-consuming. In fact, many powerful protections are just a tap away. This quick checklist offers quick and simple security settings you can enable with minimal effort.
Does dialing *#21# show if I’m hacked? This code shows if your calls and messages are being forwarded, which can be a sign of a hack, but it doesn’t detect other types of malware or spyware.
Can iPhones get viruses? While less common due to Apple’s strong security structure, iPhones can still be compromised, especially through malicious apps from outside the App Store or sophisticated phishing attacks.
Will a factory reset remove spyware? In most cases, yes. A factory reset erases all data and apps on your device, including most forms of malware and spyware, returning it to its original state.
Can my phone be hacked while powered off? A phone that is truly powered off cannot be hacked remotely. When the device is off, its wireless radios (cellular, Wi-Fi, Bluetooth) are inactive, and the operating system is not running, cutting off any connection for an attacker to exploit. In Airplane Mode, only the radios are disabled, but leaves the OS running.
The myth of a phone being hacked while off often stems from two things: advanced, targeted attacks that fake a shutdown to compromise firmware, or physical attacks like a “cold boot” where a forensics expert with physical access can extract data from the RAM shortly after shutdown. To mitigate these extremely rare risks, always ensure your phone is fully encrypted, a default setting on modern iPhones and Androids, to make data unreadable even if accessed physically.
For everyday security, shutting off your phone is a good first step to sever any potential malicious connection.
Does my iPhone need antivirus? If your iPhone is not jailbroken, you don’t need antivirus. But your phone should still get extra protection to deal with other cyberthreats such as scammy text messages, phishing and AI-driven attempts. Comprehensive online protection software like McAfee keeps you and your phone safer. It can:
Those are only some of the many McAfee capabilities that protect you and your phone.
Recognizing the signs your phone is hacked is the critical first step, but swift and correct action is what truly protects you.
You can usually determine your smartphone has been hacked by observing any unusual behavior patterns, such as unexplained battery drain, data usage spikes, a blitz of ad pop-ups, unexplained charges on your banking accounts, and even mysterious calls, texts, or apps. Another way to confirm a breach is by running built-in diagnostics such as security scans and security keys. If any of the odd behaviors listed above sound familiar, don’t wait. Take immediate action and implement a layered defense.
In the first place, you can significantly reduce your risk of being hacked through regular software updates, careful app management, and smart browsing habits. Another important component is installing a complete privacy, identity and device solution like McAfee that provides comprehensive protection.
Don’t wait until you suspect a breach; adopt these protective strategies today to keep your digital life private and secure.
The post How to Tell If Your Phone Has Been Hacked and What to Do appeared first on McAfee Blog.

When it comes to protecting your privacy, take a close look at your social media use—because sharing can quickly turn into oversharing.
The term “oversharing” carries several different definitions. Yet in our case here, oversharing means saying more than one should to more people than they should. Consider the audience you have across your social media profiles. Perhaps you have dozens, if not hundreds of friends and followers. All with various degrees of closeness and familiarity. Who among them can you absolutely trust with the information you share?
And you might be sharing more than you think. Posts have a way of saying more than one thing, like:
“This is the pool at the rental home I’m staying at this week. Amazing!” Which also tells everyone, “My home is empty for the next few days.”
“I can’t start my workday without a visit to my favorite coffee shop.” Which also says, “If you ever want to track me down in person, you can find me at this location practically any weekday morning.”
One can quickly point to other examples of oversharing. Unintentional oversharing at that.
A first-day-of-school picture can tell practical strangers which elementary school your children attend, say if the picture includes the school’s reader board in it. A snapshot of you joking around with a co-worker might reveal a glimpse of company information. Maybe because of what’s written on the whiteboard behind the two of you. And in one extreme example, there’s the case of an assault on a pop star. Her attacker tracked her down through her selfie, determining her location through the reflection in her eyes.
The list goes on.
That’s not to say “don’t post.” More accurately, it’s “consider what you’re posting and who gets to see it.” You have control over what you post, and to some degree, who gets to see those posts. That combination is key to your privacy—and the privacy of others too.
1) Be more selective with your settings: Social media platforms like Facebook, Instagram, and others give you the option of making your profile and posts visible to friends only. Choosing this setting keeps the broader internet from seeing what you’re doing, saying, and posting—not to mention your relationships and likes. Taking a “friends only” approach to your social media profiles can help protect your privacy because that gives a possible scammer or stalker much less material to work with. Yet further, some platforms allow you to create sub-groups of friends and followers. With a quick review of your network, you can create a sub-group of your most trusted friends and restrict your posts to them as needed.
2) Say “no” to strangers bearing friend requests: Be critical of the invitations you receive. Out-and-out strangers might be more than just a stranger. They might be a fake account designed to gather information on users for purposes of fraud. There are plenty of fake accounts too. In fact, in Q1 of 2023 alone, Facebook took action on 426 million fake accounts. Reject such requests.
3) Consider what you post: Think about posting those vacation pictures after you get back so people don’t know you’re away when you’re away. Also, consider if your post pinpoints where you are or where you go regularly. Do you want people in your broader network to know that? Closely review the pics you take and see if there’s any revealing information in the background. If so, you can crop it out (think notes on a whiteboard, reflections in a window, or revealing location info). Further, ask anyone you want to include in their post for their permission. In all, consider their privacy too.
While we’re on the topic, you can take a few other steps that can make you more private online. In addition to your social media usage, other steps can help keep more of your private and personal information with you—where it belongs:
Granted, “social” is arguably the opposite of “private.” Using social media involves sharing, by its very definition. Yet any oversharing can lead to privacy issues.
Maybe you want close friends to know what’s going on, but what about that so-so acquaintance deep in your friends list? How well do you really know them? And to what extent do you want them to know exacting details about where you are, where your kids go to school, and so on? Those are questions you ultimately must answer, and ultimately have some control over depending on what you share on social media.
Also important to consider is this: if you post anything on the internet, consider it front-page news. Even with social media privacy settings in place, there’s no guarantee that someone won’t copy your posts or pics and pass them along to others.
The flipside to the topic of social media and privacy is the platform you’re using. It’s no secret that social media companies gather hosts of personal information about their users in exchange for free use of their platforms. Certainly, that’s a topic unto itself. We cover what social media companies know about you in this article here—along with a few steps that can help you limit what they know as well.
When it comes to your privacy and social media, it depends largely on how you use it. How you use various privacy and audience settings offers one way to manage it. The other is you and the information you put out there for others to see.
The post Sharing Isn’t Always Caring: Tips to Help Protect Your Online Privacy appeared first on McAfee Blog.

What is our real job as parents? Is it to ensure our kids get good grades? – Maybe. Or is it ensuring we can give them the latest and greatest clothing and devices? Mmmm, not really. When all is said and done, I believe our real job is to keep our kids safe, teach them to be independent, and set them up for success – both online and offline.
As first-generation digital parents, many of us are learning on the job. While we can still glean advice from our own parents on dealing with our teenager’s hormones and driving challenges, there’s no intergenerational wisdom for anything digital. So, it is inevitable that many of us parents feel unsure about how and why to be proactive about online safety.
With four grown boys, 12 nieces and nephews, and almost 13 years in this job talking to families about online safety, I’ve developed a pretty good understanding of how families want to live their lives online, their biggest concerns, and how they value safety and security. Here’s what I’ve learnt:
I’ve often dreamt about wrapping my boys in cotton wool and keeping them away from the real world. But unfortunately, that’s not how it works. The internet definitely has some hugely positive features for teens and tweens but there are some challenges too. Here is what parents are most concerned about:
1. Social Media
Without a doubt, tween and teen social media usage would currently be the biggest concern for most parents. In Australia, there is currently a move to delay children using social media to 16. The Prime Minister is a fan as are many state and territory leaders. There’s no doubt parents are concerned about the impact social media is having on their children’s mental health. Whether dealing with followers, friends, or FOMO (fear of missing out), harassment, or exposure to unhelpful, or even dangerous influencers, parents are worried and often feel helpless about how best to help their kids.
2. Bullying
Parents have every right to be concerned. Cyberbullying does happen. In fact, 1 child in 3 reports being the victim of cyberbullying according to a UNICEF study. And in a study conducted by McAfee in 2022 that does a deep dive into the various types of bullying, there’s no doubt that the problem is still very much a reality.
3. Inappropriate Content
There really isn’t anything you can’t find online. And therein lies the problem. With just a few clicks, a curious, unsupervised 10-year-old could access images and information that would be wildly inappropriate and potentially traumatic. And yes, I’m talking sex, drugs and rock and roll themes! There are things online that little, inexperienced eyes are just not ready for – I am not even sure I am either, to be honest!
4. Screen Time
While I think many parents still find the word screen time a little triggering, I think some parents now realise that not all screen time ‘was created equally’. It’s more about the quality and potential benefit of screen time as opposed to the actual time spent on the screen. For example, playing an interactive, good quality science game as opposed to scrolling on Instagram – clearly the game wins!
However, parents are still very concerned that screen time doesn’t dominate their kids’ lives and adversely affects their kids’ levels of physical activity, face-to-face time with family and friends, and their ability to sleep.
While there is no silver bullet here, being proactive about your family’s online security is THE best way of protecting your family members, minimising the risk of unpleasant interactions, and setting them up for a positive online experience. And it will also reduce your stress big time – so it’s a complete no-brainer!!
Here are 5 things you can kick off today that will have a profound impact on your family’s online security:
1. Talk, talk, talk!!
Yes, that’s right – simply talk! Engaging with your kids about their online lives – what they like to do, sites and apps they use and any concerns they have is one of the best ways to keep them safe. As is sharing your own stories. If your kids know that you understand the digital world, they will be far more likely to come to you if they experience any issues at all. And that’s exactly what we want!!
2. Parental Controls and Monitoring
Parental controls can work really well alongside a proactive educational approach to online safety. As well as teaching kids healthy digital habits, they can also help parents monitor usage, set limits, and even keep tabs on their kids’ whereabouts. Gold!! Check out more details here.
3. Social Media Safety
Undertake an audit of all family member’s privacy settings to ensure that are set to the highest level. This will ensure only trusted people can view and interact with your kids’ profiles. Also, remind your kids not to overshare as it could lead to their identities being stolen. And check out McAfee’s Social Privacy Manager which can help you manage more than 100 privacy settings on social media accounts in seconds.
4. Make a Plan In Case of Aggressive Behaviour
As a cup-half-full type, I’m not a fan of negativity but I am a fan of plans. So, I do recommend creating an action plan for your kids in case they encounter something tricky online, in particular bullying or aggressive behaviour. I recommend you tell them to take screenshots, disengage, tell someone they trust (ideally you), and report the behaviour to the relevant social media platform or app. In some cases, you could involve your child’s school however this obviously depends on the perpetrator.
5. Passwords please!
I know you have probably heard it before, but password management is such a powerful way of staying safe online. In an ideal world, every online account should have its own unique password. Why? Well, if your logins get stolen in a data breach then the cybercriminals will not be able to reuse them to log into any of your other accounts.
And while you’re at it, ensure all passwords are at least 8-10 characters long, and contain random symbols, numbers and both upper and lowercase letters. If all is too hard, simply engage a password manager that will both generate and remember all the passwords for you. What a relief!
And of course, it goes without saying that a big part of being safe online is having super-duper internet protection software that will give you (and your family members) the best chance of a safe and secure online experience. McAfee+’s family plans not only give you a secure VPN, 24/7 identity and financial monitoring and alerts but AI-powered text scam detection and advanced anti-virus that will protect each of your family members from fake texts, risky links, viruses, malware and more. Sounds like a plan to me!!
Till next time
Stay safe everyone!
Alex
The post What Security Means to Families appeared first on McAfee Blog.

The number of people who use VPNs (virtual private networks) continues to mushroom. Recent research shows that 46% of American adults now use a VPN — 23% of which use it for strictly personal purposes.[i] Within that mix, 43% said they use a free VPN service. Yet “free” VPNs often come with a price. Typically at the expense of your privacy.
A personal VPN establishes a secure tunnel over the internet, offering you both privacy and freedom from IP-based tracking. It protects your identity and financial info by encrypting, or scrambling, the data that flows through the tunnel. Moreover, it can mask your true location, making it appear as though you are connecting from somewhere else.
Sometimes a VPN is included in more robust security software, as it is in our McAfee+ plans. It’s also, but often it is a standalone tool, that is offered for a monthly subscription rate or for free. While it might be tempting to go for a free option, there are some serious considerations that you should take to heart.
Because free VPNs don’t charge a subscription, many make revenue indirectly through advertising. This means that users get bombarded with ads. And they get exposed to tracking by the provider. In fact, one study of 283 free VPN providers found that 72% included trackers.[ii] The irony is worth pointing out. Many people use VPNs to shroud their browsing from advertisers and other data collectors. Meanwhile, free VPNs often lead to that exact kind of exposure.
But beyond the frustration of ads, slowness, and upgrade prompts is the fact that some free VPN tools include malware that can put your sensitive info at risk. The same study found that 38% of the free VPN applications in the Google Play Store were found to have malware, such as keyloggers, and some even stole data from devices.
Also concerning is how these free providers handle your data. In one worrying case, security researchers uncovered seven VPN providers that gathered user logs despite pledges not to.[iii]
Clearly, many so-called “free” VPNs aren’t free at all.
VPNs are critical tools for enhancing our privacy and shouldn’t be an avenue opening the door to new risks. That’s why your best bet is to look for a paid VPN with the following features:
Unlimited bandwidth — You want your network connection to stay secure no matter how much time you spend online.
Speedy performance — We all know how frustrating a sluggish internet connection can be when you are trying to get things done. Whether connecting for productivity, education, or entertainment, we’re all dependent on bandwidth. That’s why it’s important to choose a high-speed VPN that enhances your privacy, without sacrificing the quality of your connection.
Multiple device protection — These days many of us toggle between mobile devices, laptops, and computers, so they should all be able to connect securely.
Less battery drain — Some free mobile VPNs zap your battery life, making users less likely to stay protected. You shouldn’t have to choose between your battery life and safeguarding your privacy.
Ease of use — For technology to really work, it has to be convenient. After all, these technologies should power your connected life, not serve as a hindrance.
Fortunately, we don’t have to sacrifice convenience, or pay high prices, for a VPN that can offer a high level of privacy and protection. A comprehensive security suite like McAfee+ includes our standalone VPN with auto-renewal and takes the worry out of connecting, so you can focus on what’s important to you and your family, and enjoy quality time together.
[i] https://www.security.org/resources/vpn-consumer-report-annual/
[ii] https://www.icir.org/vern/papers/vpn-apps-imc16.pdf
[iii] https://www.pcmag.com/news/7-vpn-services-found-recording-user-logs-despite-no-log-pledge
The post How Free VPNs Come With a Price appeared first on McAfee Blog.

As election season approaches, the importance of safeguarding our democratic processes has never been more critical. Ensuring election security is not just the responsibility of government bodies but also of every individual voter. This blog post aims to provide valuable insights and practical tips for consumers to protect their votes and understand the mechanisms in place to secure elections.
Election security encompasses a broad range of practices designed to ensure the integrity, confidentiality, and accessibility of the voting process. This includes safeguarding against cyber threats, ensuring the accuracy of voter registration databases, protecting the physical security of voting equipment, and maintaining transparency in the vote counting process. As voters, being aware of these elements helps us appreciate the complexity and importance of secure elections.
One of the first steps to secure your vote is to ensure that you are registered correctly. Check your voter registration status well in advance of the election day through your local election office or official state website. This helps to avoid any last-minute issues and ensures your eligibility to vote.
Misinformation can spread rapidly, especially during election periods. Rely on official sources for information about polling locations, voting procedures, and deadlines. Avoid sharing unverified information on social media and report any suspicious content to the relevant authorities.
Whether you are voting in person or by mail, make sure to follow the recommended procedures. If voting by mail, request your ballot from a verified source and return it through secure methods such as official drop boxes or by mail with sufficient time to ensure it is received before the deadline.
Scammers often target voters to steal personal information. Be cautious of unsolicited phone calls, emails, or texts asking for your personal details. Official election offices will not request sensitive information such as your Social Security number via these methods.
If you notice anything unusual at your polling place or have concerns about the voting process, report it immediately to election officials. This includes any signs of tampering with voting machines, suspicious behavior, or attempts to intimidate voters.
Familiarize yourself with the voting process in your area. This includes knowing your polling location, understanding what identification is required, and learning about the different ways you can cast your vote. Many states provide detailed guides and resources for first-time voters.
Plan your voting day in advance. Decide whether you will vote in person or by mail, and make sure you have all necessary documentation ready. If you are voting in person, consider going during off-peak hours to avoid long lines.
Before you head to the polls, research the candidates and issues on the ballot. This will help you make informed decisions and feel more confident in your choices.
Don’t hesitate to ask for help if you need it. Election officials and poll workers are there to assist you. Additionally, many organizations offer support for first-time voters, including transportation to polling places and information hotlines.
Understand the security measures your state has implemented to protect the election process. This might include the use of paper ballots, post-election audits, and cybersecurity protocols. Being aware of these measures can increase your confidence in the election’s integrity.
If your state offers early voting, take advantage of it. Early voting can reduce the stress of long lines and crowded polling places on election day, making the process smoother and more secure.
Encourage friends and family to vote and educate them about election security. A well-informed electorate is a key component of a secure and fair election.
Keep up with reputable news sources to stay informed about any potential security threats or changes in the voting process. This will help you stay prepared and responsive to any issues that might arise.
By following these tips and staying vigilant, every voter can contribute to a secure and fair election process. Remember, your vote is your voice, and protecting it is essential for the health of our democracy. Happy voting!
The post What You Need to Know About Election Security appeared first on McAfee Blog.
JA4+ is a suite of network Fingerprinting methods that are easy to use and easy to share. These methods are both human and machine readable to facilitate more effective threat-hunting and analysis. The use-cases for these fingerprints include scanning for threat actors, malware detection, session hijacking prevention, compliance automation, location tracking, DDoS detection, grouping of threat actors, reverse shell detection, and many more.
Please read our blogs for details on how JA4+ works, why it works, and examples of what can be detected/prevented with it:
JA4+ Network Fingerprinting (JA4/S/H/L/X/SSH)
JA4T: TCP Fingerprinting (JA4T/TS/TScan)
To understand how to read JA4+ fingerprints, see Technical Details
This repo includes JA4+ Python, Rust, Zeek and C, as a Wireshark plugin.
JA4/JA4+ support is being added to:
GreyNoise
Hunt
Driftnet
DarkSail
Arkime
GoLang (JA4X)
Suricata
Wireshark
Zeek
nzyme
Netresec's CapLoader
NetworkMiner">Netresec's NetworkMiner
NGINX
F5 BIG-IP
nfdump
ntop's ntopng
ntop's nDPI
Team Cymru
NetQuest
Censys
Exploit.org's Netryx
cloudflare.com/bots/concepts/ja3-ja4-fingerprint/">Cloudflare
fastly
with more to be announced...
| Application | JA4+ Fingerprints |
|---|---|
| Chrome |
JA4=t13d1516h2_8daaf6152771_02713d6af862 (TCP) JA4=q13d0312h3_55b375c5d22e_06cda9e17597 (QUIC) JA4=t13d1517h2_8daaf6152771_b0da82dd1658 (pre-shared key) JA4=t13d1517h2_8daaf6152771_b1ff8ab2d16f (no key) |
| IcedID Malware Dropper | JA4H=ge11cn020000_9ed1ff1f7b03_cd8dafe26982 |
| IcedID Malware |
JA4=t13d201100_2b729b4bf6f3_9e7b989ebec8 JA4S=t120300_c030_5e2616a54c73
|
| Sliver Malware |
JA4=t13d190900_9dc949149365_97f8aa674fd9 JA4S=t130200_1301_a56c5b993250 JA4X=000000000000_4f24da86fad6_bf0f0589fc03 JA4X=000000000000_7c32fa18c13e_bf0f0589fc03
|
| Cobalt Strike |
JA4H=ge11cn060000_4e59edc1297a_4da5efaf0cbd JA4X=2166164053c1_2166164053c1_30d204a01551
|
| SoftEther VPN |
JA4=t13d880900_fcb5b95cb75a_b0d3b4ac2a14 (client) JA4S=t130200_1302_a56c5b993250 JA4X=d55f458d5a6c_d55f458d5a6c_0fc8c171b6ae
|
| Qakbot | JA4X=2bab15409345_af684594efb4_000000000000 |
| Pikabot | JA4X=1a59268f55e5_1a59268f55e5_795797892f9c |
| Darkgate | JA4H=po10nn060000_cdb958d032b0 |
| LummaC2 | JA4H=po11nn050000_d253db9d024b |
| Evilginx | JA4=t13d191000_9dc949149365_e7c285222651 |
| Reverse SSH Shell | JA4SSH=c76s76_c71s59_c0s70 |
| Windows 10 | JA4T=64240_2-1-3-1-1-4_1460_8 |
| Epson Printer | JA4TScan=28960_2-4-8-1-3_1460_3_1-4-8-16 |
For more, see ja4plus-mapping.csv
The mapping file is unlicensed and free to use. Feel free to do a pull request with any JA4+ data you find.
Recommended to have tshark version 4.0.6 or later for full functionality. See: https://pkgs.org/search/?q=tshark
Download the latest JA4 binaries from: Releases.
sudo apt install tshark
./ja4 [options] [pcap]
1) Install Wireshark https://www.wireshark.org/download.html which will install tshark 2) Add tshark to $PATH
ln -s /Applications/Wireshark.app/Contents/MacOS/tshark /usr/local/bin/tshark
./ja4 [options] [pcap]
1) Install Wireshark for Windows from https://www.wireshark.org/download.html which will install tshark.exe
tshark.exe is at the location where wireshark is installed, for example: C:\Program Files\Wireshark\thsark.exe
2) Add the location of tshark to your "PATH" environment variable in Windows.
(System properties > Environment Variables... > Edit Path)
3) Open cmd, navigate the ja4 folder
ja4 [options] [pcap]
An official JA4+ database of fingerprints, associated applications and recommended detection logic is in the process of being built.
In the meantime, see ja4plus-mapping.csv
Feel free to do a pull request with any JA4+ data you find.
JA4+ is a set of simple yet powerful network fingerprints for multiple protocols that are both human and machine readable, facilitating improved threat-hunting and security analysis. If you are unfamiliar with network fingerprinting, I encourage you to read my blogs releasing JA3 here, JARM here, and this excellent blog by Fastly on the State of TLS Fingerprinting which outlines the history of the aforementioned along with their problems. JA4+ brings dedicated support, keeping the methods up-to-date as the industry changes.
All JA4+ fingerprints have an a_b_c format, delimiting the different sections that make up the fingerprint. This allows for hunting and detection utilizing just ab or ac or c only. If one wanted to just do analysis on incoming cookies into their app, they would look at JA4H_c only. This new locality-preserving format facilitates deeper and richer analysis while remaining simple, easy to use, and allowing for extensibility.
For example; GreyNoise is an internet listener that identifies internet scanners and is implementing JA4+ into their product. They have an actor who scans the internet with a constantly changing single TLS cipher. This generates a massive amount of completely different JA3 fingerprints but with JA4, only the b part of the JA4 fingerprint changes, parts a and c remain the same. As such, GreyNoise can track the actor by looking at the JA4_ac fingerprint (joining a+c, dropping b).
Current methods and implementation details:
| Full Name | Short Name | Description | |---|---|---| | JA4 | JA4 | TLS Client Fingerprinting
| JA4Server | JA4S | TLS Server Response / Session Fingerprinting | JA4HTTP | JA4H | HTTP Client Fingerprinting | JA4Latency | JA4L | Latency Measurment / Light Distance | JA4X509 | JA4X | X509 TLS Certificate Fingerprinting | JA4SSH | JA4SSH | SSH Traffic Fingerprinting | JA4TCP | JA4T | TCP Client Fingerprinting | JA4TCPServer | JA4TS | TCP Server Response Fingerprinting | JA4TCPScan | JA4TScan | Active TCP Fingerprint Scanner
The full name or short name can be used interchangeably. Additional JA4+ methods are in the works...
To understand how to read JA4+ fingerprints, see Technical Details
JA4: TLS Client Fingerprinting is open-source, BSD 3-Clause, same as JA3. FoxIO does not have patent claims and is not planning to pursue patent coverage for JA4 TLS Client Fingerprinting. This allows any company or tool currently utilizing JA3 to immediately upgrade to JA4 without delay.
JA4S, JA4L, JA4H, JA4X, JA4SSH, JA4T, JA4TScan and all future additions, (collectively referred to as JA4+) are licensed under the FoxIO License 1.1. This license is permissive for most use cases, including for academic and internal business purposes, but is not permissive for monetization. If, for example, a company would like to use JA4+ internally to help secure their own company, that is permitted. If, for example, a vendor would like to sell JA4+ fingerprinting as part of their product offering, they would need to request an OEM license from us.
All JA4+ methods are patent pending.
JA4+ is a trademark of FoxIO
JA4+ can and is being implemented into open source tools, see the License FAQ for details.
This licensing allows us to provide JA4+ to the world in a way that is open and immediately usable, but also provides us with a way to fund continued support, research into new methods, and the development of the upcoming JA4 Database. We want everyone to have the ability to utilize JA4+ and are happy to work with vendors and open source projects to help make that happen.
ja4plus-mapping.csv is not included in the above software licenses and is thereby a license-free file.
Q: Why are you sorting the ciphers? Doesn't the ordering matter?
A: It does but in our research we've found that applications and libraries choose a unique cipher list more than unique ordering. This also reduces the effectiveness of "cipher stunting," a tactic of randomizing cipher ordering to prevent JA3 detection.
Q: Why are you sorting the extensions?
A: Earlier in 2023, Google updated Chromium browsers to randomize their extension ordering. Much like cipher stunting, this was a tactic to prevent JA3 detection and "make the TLS ecosystem more robust to changes." Google was worried server implementers would assume the Chrome fingerprint would never change and end up building logic around it, which would cause issues whenever Google went to update Chrome.
So I want to make this clear: JA4 fingerprints will change as application TLS libraries are updated, about once a year. Do not assume fingerprints will remain constant in an environment where applications are updated. In any case, sorting the extensions gets around this and adding in Signature Algorithms preserves uniqueness.
Q: Doesn't TLS 1.3 make fingerprinting TLS clients harder?
A: No, it makes it easier! Since TLS 1.3, clients have had a much larger set of extensions and even though TLS1.3 only supports a few ciphers, browsers and applications still support many more.
John Althouse, with feedback from:
Josh Atkins
Jeff Atkinson
Joshua Alexander
W.
Joe Martin
Ben Higgins
Andrew Morris
Chris Ueland
Ben Schofield
Matthias Vallentin
Valeriy Vorotyntsev
Timothy Noel
Gary Lipsky
And engineers working at GreyNoise, Hunt, Google, ExtraHop, F5, Driftnet and others.
Contact John Althouse at john@foxio.io for licensing and questions.
Copyright (c) 2024, FoxIO