Real-time face swap and video deepfake with a single click and only a single image.
This deepfake software is designed to be a productive tool for the AI-generated media industry. It can assist artists in animating custom characters, creating engaging content, and even using models for clothing design.
We are aware of the potential for unethical applications and are committed to preventative measures. A built-in check prevents the program from processing inappropriate media (nudity, graphic content, sensitive material like war footage, etc.). We will continue to develop this project responsibly, adhering to the law and ethics. We may shut down the project or add watermarks if legally required.
Ethical Use: Users are expected to use this software responsibly and legally. If using a real person's face, obtain their consent and clearly label any output as a deepfake when sharing online.
Content Restrictions: The software includes built-in checks to prevent processing inappropriate media, such as nudity, graphic content, or sensitive material.
Legal Compliance: We adhere to all relevant laws and ethical guidelines. If legally required, we may shut down the project or add watermarks to the output.
User Responsibility: We are not responsible for end-user actions. Users must ensure their use of the software aligns with ethical standards and legal requirements.
By using this software, you agree to these terms and commit to using it in a manner that respects the rights and dignity of others.
Users are expected to use this software responsibly and legally. If using a real person's face, obtain their consent and clearly label any output as a deepfake when sharing online. We are not responsible for end-user actions.
1. Select a face 2. Select which camera to use 3. Press live!
Retain your original mouth for accurate movement using Mouth Mask

Use different faces on multiple subjects simultaneously

Watch movies with any face in real-time
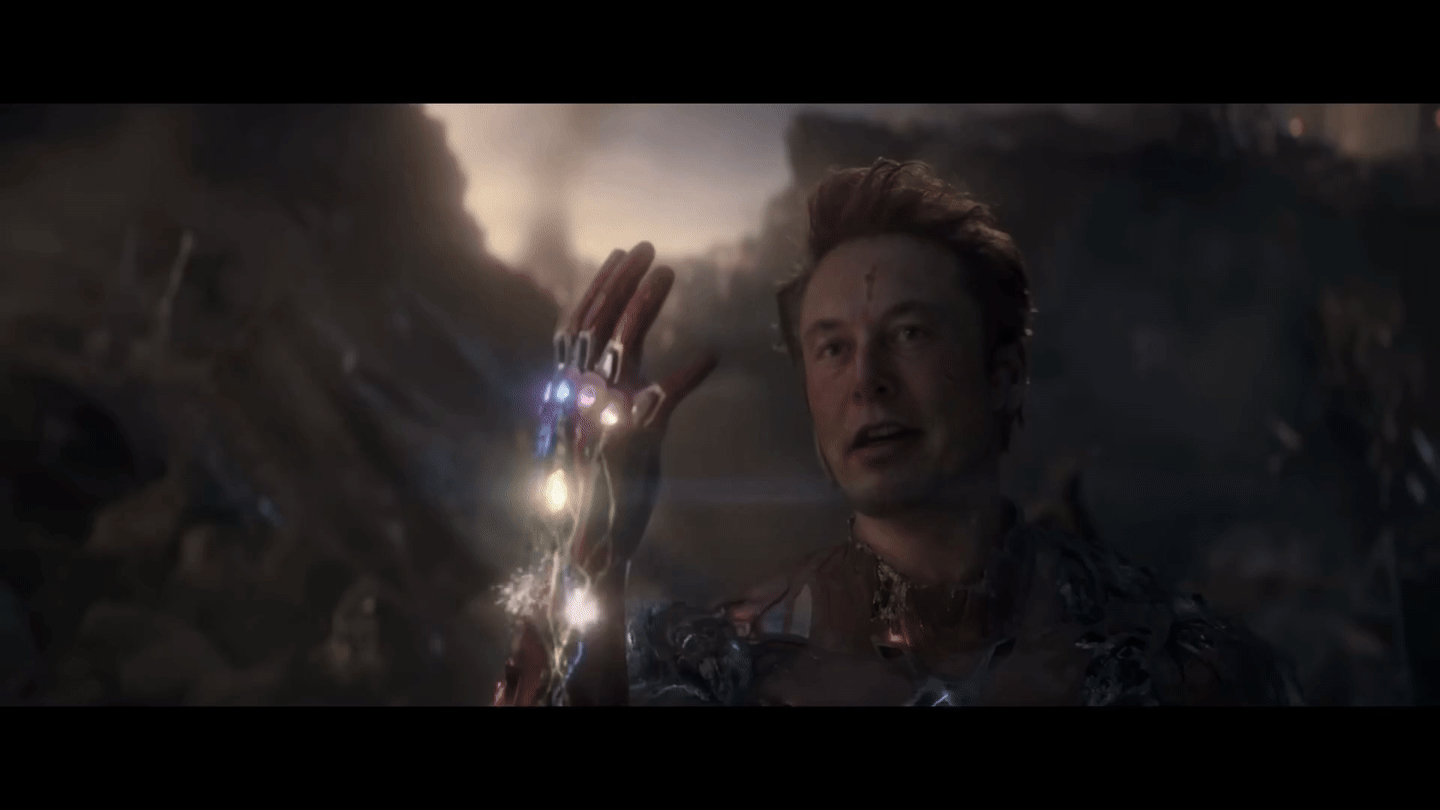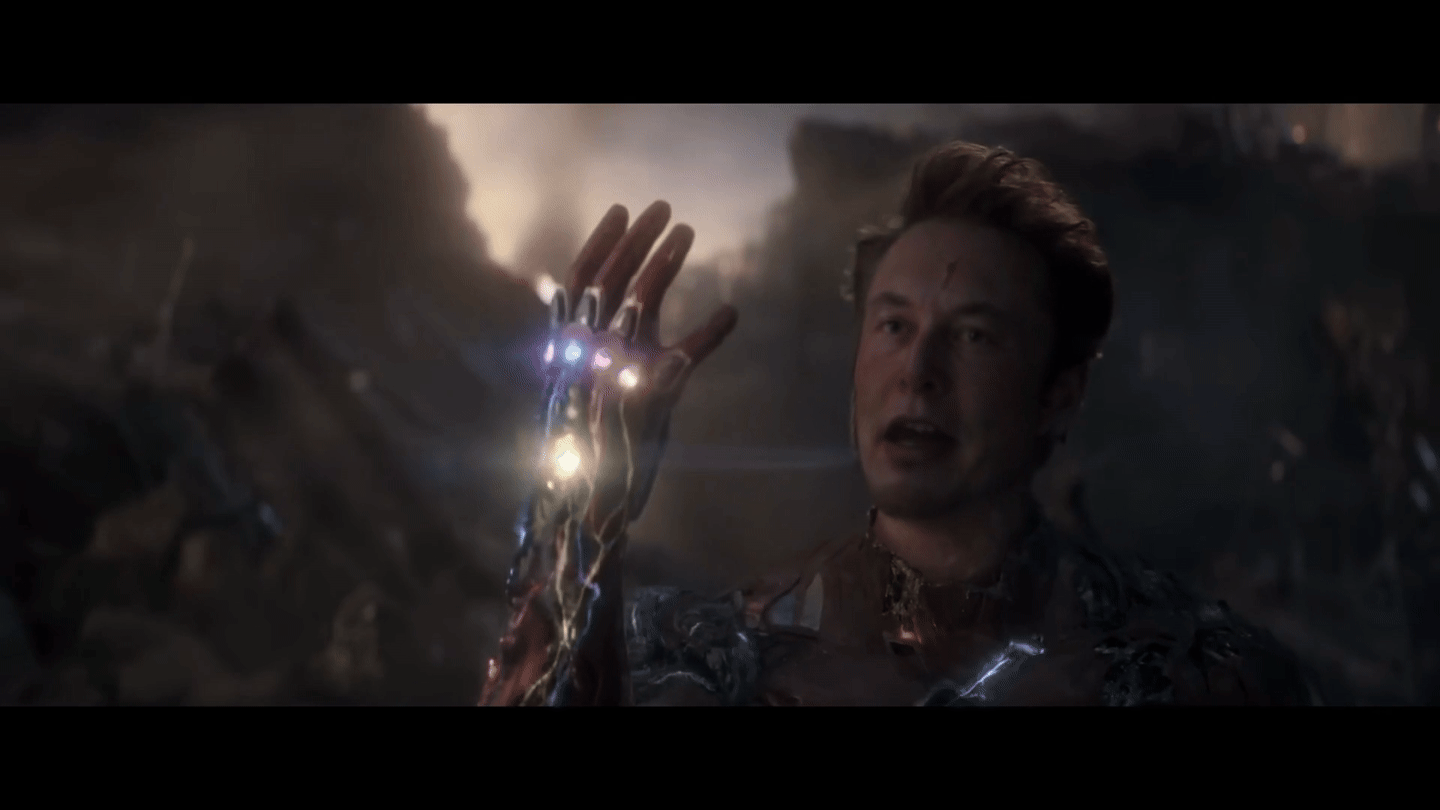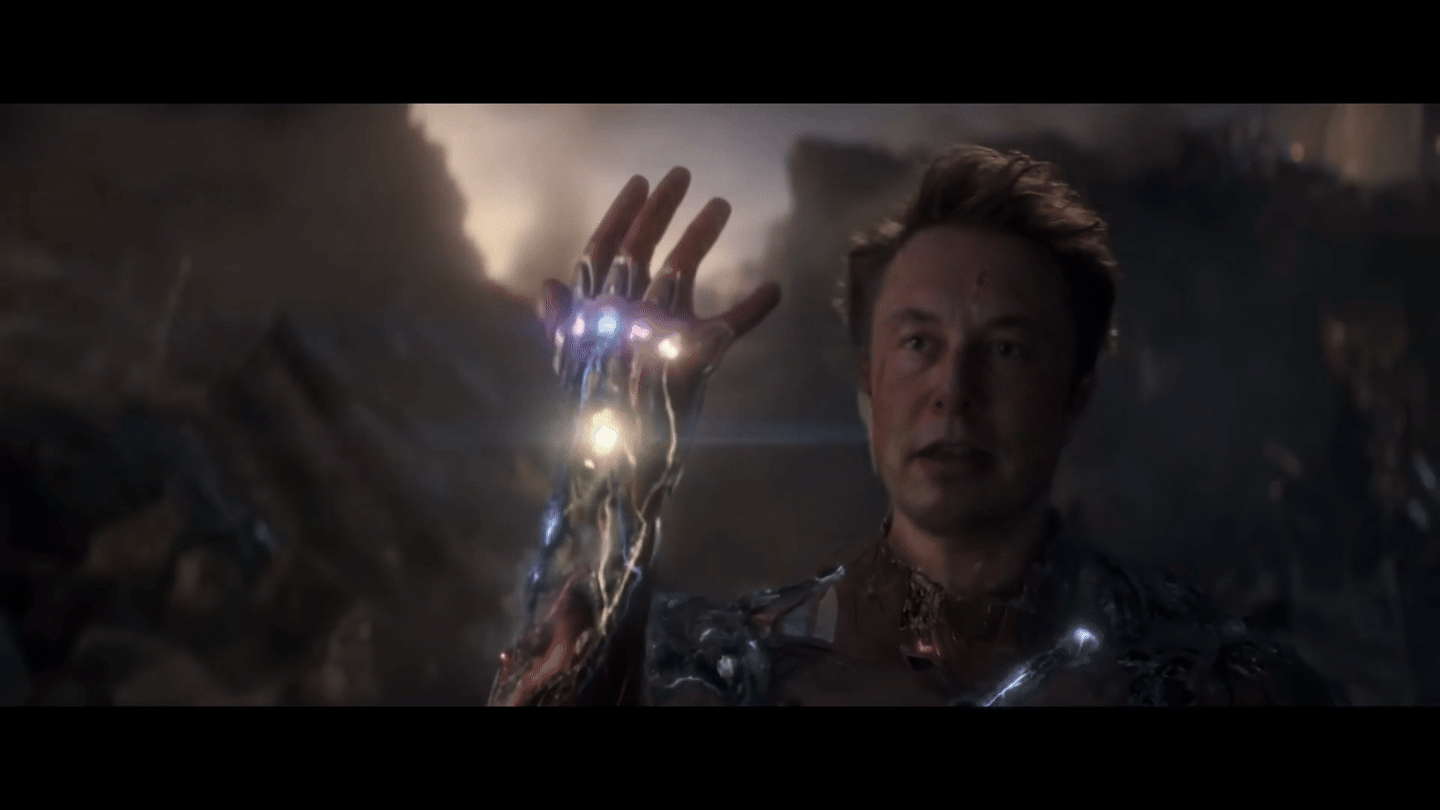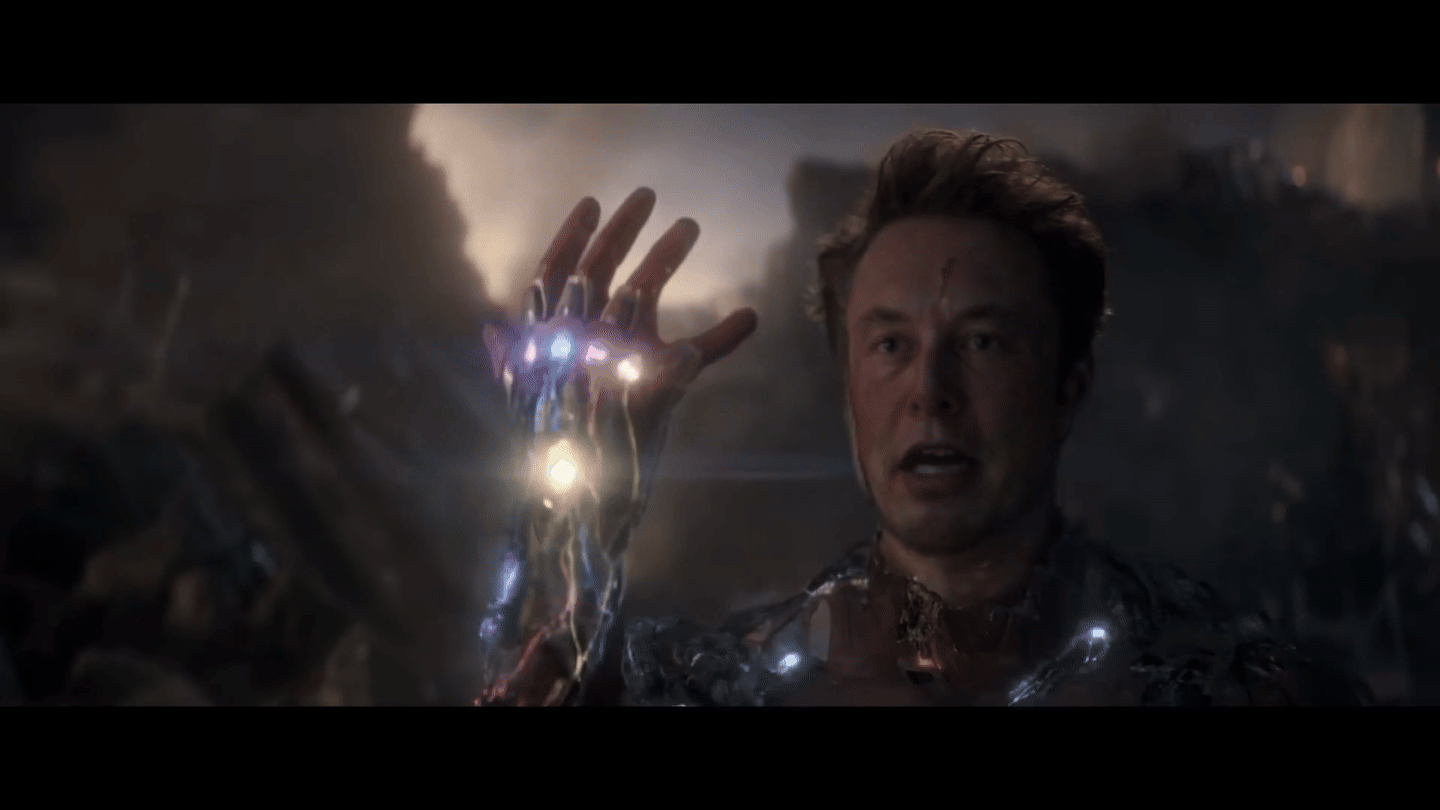
Run Live shows and performances

Create Your Most Viral Meme Yet

Created using Many Faces feature in Deep-Live-Cam
Surprise people on Omegle
Please be aware that the installation requires technical skills and is not for beginners. Consider downloading the prebuilt version.
git clone https://github.com/hacksider/Deep-Live-Cam.git
cd Deep-Live-Cam
python -m venv venv
venv\Scripts\activate
pip install -r requirements.txt
# Install Python 3.10 (specific version is important)
brew install python@3.10
# Install tkinter package (required for the GUI)
brew install python-tk@3.10
# Create and activate virtual environment with Python 3.10
python3.10 -m venv venv
source venv/bin/activate
# Install dependencies
pip install -r requirements.txt
# Deactivate the virtual environment
rm -rf venv
# Reinstall the virtual environment
python -m venv venv
source venv/bin/activate
# install the dependencies again
pip install -r requirements.txt
pip uninstall onnxruntime onnxruntime-gpu
pip install onnxruntime-gpu==1.16.3
python run.py --execution-provider cuda
pip uninstall onnxruntime onnxruntime-silicon
pip install onnxruntime-silicon==1.13.1
python3.10 run.py --execution-provider coreml
pip uninstall onnxruntime onnxruntime-coreml
pip install onnxruntime-coreml==1.13.1
python run.py --execution-provider coreml
pip uninstall onnxruntime onnxruntime-directml
pip install onnxruntime-directml==1.15.1
python run.py --execution-provider directml
pip uninstall onnxruntime onnxruntime-openvino
pip install onnxruntime-openvino==1.15.0
python run.py --execution-provider openvino
1. Image/Video Mode
python run.py.2. Webcam Mode
python run.py.Check out these helpful guides to get the most out of Deep-Live-Cam:
Visit our official blog for more tips and tutorials.
options:
-h, --help show this help message and exit
-s SOURCE_PATH, --source SOURCE_PATH select a source image
-t TARGET_PATH, --target TARGET_PATH select a target image or video
-o OUTPUT_PATH, --output OUTPUT_PATH select output file or directory
--frame-processor FRAME_PROCESSOR [FRAME_PROCESSOR ...] frame processors (choices: face_swapper, face_enhancer, ...)
--keep-fps keep original fps
--keep-audio keep original audio
--keep-frames keep temporary frames
--many-faces process every face
--map-faces map source target faces
--mouth-mask mask the mouth region
--video-encoder {libx264,libx265,libvpx-vp9} adjust output video encoder
--video-quality [0-51] adjust output video quality
--live-mirror the live camera display as you see it in the front-facing camera frame
--live-resizable the live camera frame is resizable
--max-memory MAX_MEMORY maximum amount of RAM in GB
--execution-provider {cpu} [{cpu} ...] available execution provider (choices: cpu, ...)
--execution-threads EXECUTION_THREADS number of execution threads
-v, --version show program's version number and exit
Looking for a CLI mode? Using the -s/--source argument will make the run program in cli mode.
We are always open to criticism and are ready to improve, that's why we didn't cherry-pick anything.
Feel free to make suggestions
Find devices in a particular city. city:"Bangalore"
Find devices in a particular country. country:"IN"
Find devices by giving geographical coordinates. geo:"56.913055,118.250862"
country:us country:ru country:de city:chicago
Find devices matching the hostname. server: "gws" hostname:"google" hostname:example.com -hostname:subdomain.example.com hostname:example.com,example.org
Find devices based on an IP address or /x CIDR. net:210.214.0.0/16
org:microsoft org:"United States Department"
asn:ASxxxx
Find devices based on operating system. os:"windows 7"
Find devices based on open ports. proftpd port:21
Find devices before or after between a given time. apache after:22/02/2009 before:14/3/2010
Self signed certificates ssl.cert.issuer.cn:example.com ssl.cert.subject.cn:example.com
Expired certificates ssl.cert.expired:true
ssl.cert.subject.cn:example.com
device:firewall device:router device:wap device:webcam device:media device:"broadband router" device:pbx device:printer device:switch device:storage device:specialized device:phone device:"voip" device:"voip phone" device:"voip adaptor" device:"load balancer" device:"print server" device:terminal device:remote device:telecom device:power device:proxy device:pda device:bridge
os:"windows 7" os:"windows server 2012" os:"linux 3.x"
product:apache product:nginx product:android product:chromecast
cpe:apple cpe:microsoft cpe:nginx cpe:cisco
server: nginx server: apache server: microsoft server: cisco-ios
dc:14:de:8e:d7:c1:15:43:23:82:25:81:d2:59:e8:c0
http.html:/dana-na
http.title:"Index of /" http.html:".pem"
onion-location
"product:MySQL" mysql port:"3306"
"product:MongoDB" mongodb port:27017
"MongoDB Server Information { "metrics":" "Set-Cookie: mongo-express=" "200 OK" "MongoDB Server Information" port:27017 -authentication
kibana content-legth:217
port:9200 json port:"9200" all:elastic port:"9200" all:"elastic indices"
"product:Memcached"
"product:CouchDB" port:"5984"+Server: "CouchDB/2.1.0"
"port:5432 PostgreSQL"
"port:8087 Riak"
"product:Redis"
"product:Cassandra"
"Server: Prismview Player"
"in-tank inventory" port:10001
No auth required to access CLI terminal. "privileged command" GET
P372 "ANPR enabled"
mikrotik streetlight
"voter system serial" country:US
May allow for ATM Access availability NCR Port:"161"
"Cisco IOS" "ADVIPSERVICESK9_LI-M"
"[2J[H Encartele Confidential"
http.title:"Tesla PowerPack System" http.component:"d3" -ga3ca4f2
"Server: gSOAP/2.8" "Content-Length: 583"
Shodan made a pretty sweet Ship Tracker that maps ship locations in real time, too!
"Cobham SATCOM" OR ("Sailor" "VSAT")
title:"Slocum Fleet Mission Control"
"Server: CarelDataServer" "200 Document follows"
http.title:"Nordex Control" "Windows 2000 5.0 x86" "Jetty/3.1 (JSP 1.1; Servlet 2.2; java 1.6.0_14)"
"[1m[35mWelcome on console"
Secured by default, thankfully, but these 1,700+ machines still have no business being on the internet.
"DICOM Server Response" port:104
"Server: EIG Embedded Web Server" "200 Document follows"
"Siemens, SIMATIC" port:161
"Server: Microsoft-WinCE" "Content-Length: 12581"
"HID VertX" port:4070
"log off" "select the appropriate"
Helps to find the charging status of tesla powerpack. http.title:"Tesla PowerPack System" http.component:"d3" -ga3ca4f2
title:"xzeres wind"
"html:"PIPS Technology ALPR Processors""
"port:502"
"port:1911,4911 product:Niagara"
"port:18245,18246 product:"general electric""
"port:5006,5007 product:mitsubishi"
"port:2455 operating system"
"port:102"
"port:47808"
"port:5094 hart-ip"
"port:9600 response code"
"port:2404 asdu address"
"port:20000 source address"
"port:44818"
"port:1962 PLC"
"port:789 product:"Red Lion Controls"
"port:20547 PLC"
"authentication disabled" port:5900,5901 "authentication disabled" "RFB 003.008"
99.99% are secured by a secondary Windows login screen.
"\x03\x00\x00\x0b\x06\xd0\x00\x00\x124\x00"
product:"cobalt strike team server" product:"Cobalt Strike Beacon" ssl.cert.serial:146473198 - default certificate serial number ssl.jarm:07d14d16d21d21d07c42d41d00041d24a458a375eef0c576d23a7bab9a9fb1 ssl:foren.zik
http.html_hash:-1957161625 product:"Brute Ratel C4"
ssl:"Covenant" http.component:"Blazor"
ssl:"MetasploitSelfSignedCA"
Routers which got compromised hacked-router-help-sos
product:"Redis key-value store"
Find Citrix Gateway. title:"citrix gateway"
Command-line access inside Kubernetes pods and Docker containers, and real-time visualization/monitoring of the entire infrastructure.
title:"Weave Scope" http.favicon.hash:567176827
"X-Jenkins" "Set-Cookie: JSESSIONID" http.title:"Dashboard"
Jenkins Unrestricted Dashboard x-jenkins 200
"Docker Containers:" port:2375
"Docker-Distribution-Api-Version: registry" "200 OK" -gitlab
"dnsmasq-pi-hole" "Recursion: enabled"
"port: 53" Recursion: Enabled
"root@" port:23 -login -password -name -Session
NO password required for telnet access. port:23 console gateway
"polycom command shell"
nport -keyin port:23
A tangential result of Google's sloppy fractured update approach. 🙄 More information here.
"Android Debug Bridge" "Device" port:5555
Lantronix password port:30718 -secured
"Citrix Applications:" port:1604
Vulnerable (kind of "by design," but especially when exposed).
"smart install client active"
PBX "gateway console" -password port:23
http.title:"- Polycom" "Server: lighttpd" "Polycom Command Shell" -failed port:23
"Polycom Command Shell" -failed port:23
Example: Polycom Video Conferencing
"Server: Bomgar" "200 OK"
"Intel(R) Active Management Technology" port:623,664,16992,16993,16994,16995 "Active Management Technology"
HP-ILO-4 !"HP-ILO-4/2.53" !"HP-ILO-4/2.54" !"HP-ILO-4/2.55" !"HP-ILO-4/2.60" !"HP-ILO-4/2.61" !"HP-ILO-4/2.62" !"HP-iLO-4/2.70" port:1900
"Press Enter for Setup Mode port:9999"
Helps to find the cleartext wifi passwords in Shodan. html:"def_wirelesspassword"
The wp-config.php if accessed can give out the database credentials. http.html:"* The wp-config.php creation script uses this file"
"x-owa-version" "IE=EmulateIE7" "Server: Microsoft-IIS/7.0"
"x-owa-version" "IE=EmulateIE7" http.favicon.hash:442749392
"X-AspNet-Version" http.title:"Outlook" -"x-owa-version"
"X-MS-Server-Fqdn"
Produces ~500,000 results...narrow down by adding "Documents" or "Videos", etc.
"Authentication: disabled" port:445
"Authentication: disabled" NETLOGON SYSVOL -unix port:445
"Authentication: disabled" "Shared this folder to access QuickBooks files OverNetwork" -unix port:445
"220" "230 Login successful." port:21
"Set-Cookie: iomega=" -"manage/login.html" -http.title:"Log In"
Redirecting sencha port:9000
"Server: Logitech Media Server" "200 OK"
Example: Logitech Media Servers
"X-Plex-Protocol" "200 OK" port:32400
"CherryPy/5.1.0" "/home"
"IPC$ all storage devices"
title:camera
webcam has_screenshot:true
"d-Link Internet Camera, 200 OK"
"Hipcam RealServer/V1.0"
"Server: yawcam" "Mime-Type: text/html"
("webcam 7" OR "webcamXP") http.component:"mootools" -401
"Server: IP Webcam Server" "200 OK"
html:"DVR_H264 ActiveX"
With username:admin and password: :P NETSurveillance uc-httpd Server: uc-httpd 1.0.0
"Serial Number:" "Built:" "Server: HP HTTP"
ssl:"Xerox Generic Root"
"SERVER: EPSON_Linux UPnP" "200 OK"
"Server: EPSON-HTTP" "200 OK"
"Server: KS_HTTP" "200 OK"
"Server: CANON HTTP Server"
"Server: AV_Receiver" "HTTP/1.1 406"
Apple TVs, HomePods, etc.
"\x08_airplay" port:5353
"Chromecast:" port:8008
"Model: PYNG-HUB"
"Server: calibre" http.status:200 http.title:calibre
title:"OctoPrint" -title:"Login" http.favicon.hash:1307375944
"ETH - Total speed"
Substitute .pem with any extension or a filename like phpinfo.php.
http.title:"Index of /" http.html:".pem"
Exposed wp-config.php files containing database credentials.
http.html:"* The wp-config.php creation script uses this file"
"Minecraft Server" "protocol 340" port:25565
net:175.45.176.0/22,210.52.109.0/24,77.94.35.0/24
Pantheon is a GUI application that allows users to display information regarding network cameras in various countries as well as an integrated live-feed for non-protected cameras.
Pantheon allows users to execute an API crawler. There was original functionality without the use of any API's (like Insecam), but Google TOS kept getting in the way of the original scraping mechanism.
git clone https://github.com/josh0xA/Pantheon.gitcd Pantheonpip3 install -r requirements.txtpython3 pantheon.py
chmod +x distros/ubuntu_install.sh./distros/ubuntu_install.shchmod +x distros/debian-kali_install.sh./distros/debian-kali_install.sh(Enter) on a selected IP:Port to establish a Pantheon webview of the camera. (Use this at your own risk)
(Left-click) on a selected IP:Port to view the geolocation of the camera.
(Right-click) on a selected IP:Port to view the HTTP data of the camera (Ctrl+Left-click for Mac).
Adjust the map as you please to see the markers.
The developer of this program, Josh Schiavone, is not resposible for misuse of this data gathering tool. Pantheon simply provides information that can be indexed by any modern search engine. Do not try to establish unauthorized access to live feeds that are password protected - that is illegal. Furthermore, if you do choose to use Pantheon to view a live-feed, do so at your own risk. Pantheon was developed for educational purposes only. For further information, please visit: https://joshschiavone.com/panth_info/panth_ethical_notice.html
MIT License
Copyright (c) Josh Schiavone






