This Week in Scams: The AI “Truman Show” Scam Draining Bank Accounts

We’re back with another roundup of must-know scams and cybersecurity news making headlines this week, including a scam that features the name of the Jim Carrey movie, The Truman Show.
Let’s break it down.
Why Reports Call it the “Truman Show” Scam
So, why the name of this scam?
In the 1998 film The Truman Show, the main character unknowingly lives inside a staged reality TV world where everything around him is carefully controlled. In the “Truman Show” scam, criminals try to place victims into a similarly staged investment environment, complete with fake group chats, fake investors, and fake profits designed to build trust. It doesn’t actually have anything to do with the movie.
What is the “Truman Show” Scam?
The “Truman Show” scam is an AI-powered investment scam where criminals create an entire fake online community to convince victims an investment opportunity is real.
According to reports, scammers invite people into group chats on platforms like Telegram or WhatsApp that appear full of investors sharing tips and celebrating profits. In reality, many of the participants, moderators, and conversations may be run by AI bots designed to simulate a lively trading community.
Security researchers say the moderator and the other “investors” in the group may actually be AI-driven bots, programmed to simulate real conversations and enthusiasm around the investment strategy.
The scam often includes:
- A group chat on Telegram or WhatsApp
- A downloadable trading app or website
- Screenshots showing fake profits
- Encouragement from “other members” to invest more
The app itself may appear legitimate. But in reality, it often redirects users to a malicious website where scammers collect personal and financial information.
Once victims deposit money, the criminals can quickly drain accounts or block withdrawals.
McAfee’s State of the Scamiverse research shows just how convincing scams have become. One in three Americans (33%) say they feel less confident spotting scams than they did a year ago, as criminals increasingly use polished branding, realistic conversations, and AI-generated content to make fraudulent opportunities look legitimate.
Why this works: people naturally trust social proof. When it looks like dozens of other investors are making money, people lower their skepticism.
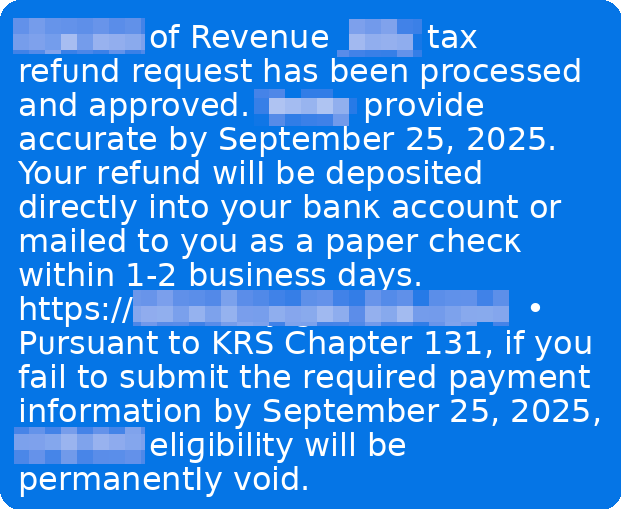
Fake Government Letters Are Targeting Residents Across Towns
Another scam to be aware of this week includes spoofed letters impersonating local government offices.
According to reporting from WGME in Maine, residents in multiple towns recently received official-looking notices requesting payment for supposed municipal fees tied to development applications.
The letters appeared convincing. They used formal language, official seals, and department names. But there was a problem.
One of the notices claimed it came from a “Board of Commissioners,” even though the town in question does not have one.
Officials say the letters instructed recipients to send payments by wire transfer, a method legitimate government offices almost never use for these kinds of transactions.
McAfee’s experts say these scams are effective because they rely on volume. Fraudsters send thousands of letters hoping a small percentage of recipients will respond before verifying the request. And remember, these types of scams occur all the time and across the globe. While today’s reports are in Maine, it’s important to be vigilant wherever you live.
Red flags to watch for:
- Requests for wire transfers, gift cards, or crypto payments
- Pressure to pay quickly to avoid penalties
- Official-looking letters with subtle inconsistencies
- Contact information that doesn’t match the official government website
The safest move is simple: verify the request independently. Contact the government office directly using phone numbers listed on its official website, not the ones in the letter.
LexisNexis Confirms Data Breach After Hackers Leak Files
Meanwhile, a well-known data analytics company is dealing with a breach after hackers published stolen files online.
According to BleepingComputer, LexisNexis Legal & Professional confirmed that attackers accessed some of its servers and obtained limited customer and business information. The confirmation came after a hacking group leaked roughly 2GB of stolen data on underground forums.
LexisNexis says the compromised systems contained mostly older or “legacy” data from before 2020, including:
- Customer names
- User IDs
- Business contact information
- Product usage details
- Support tickets and survey responses
The company says highly sensitive financial information, Social Security numbers, and active passwords were not part of the exposed data.
However, attackers claim they accessed millions of database records and hundreds of thousands of cloud user profiles tied to the company’s systems.
LexisNexis says it has contained the intrusion and is working with cybersecurity experts and law enforcement.
Why breaches like this matter: even when the stolen data appears limited, it can still be used in targeted phishing attacks.
For example, scammers might use real names, email addresses, or business roles to send convincing messages that appear legitimate.
Breaches often trigger waves of follow-up scams weeks or months later. (We know we cover this one a lot, but it’s key to remember!)
McAfee’s Safety Tips This Week
A few simple habits can make these schemes much easier to spot.
- Be skeptical of investment groups online. Real trading communities rarely pressure you to deposit money quickly or download unfamiliar apps.
- Verify government payment requests independently. If you receive a letter demanding payment, contact the agency directly using information from its official website.
- Treat breach-related messages cautiously. After a breach makes headlines, phishing emails often follow pretending to offer “account verification” or “security updates.”
- Avoid clicking unfamiliar links in emails or texts. Tools like McAfee’s free WebAdvisor can help flag risky websites and block known malicious pages before they load.
- Pause before sending money or personal information. Many scams rely on urgency. Slowing down gives you time to verify what’s real.
We’ll be back next week with another roundup of the scams and cybersecurity news making headlines and what they mean for your digital safety.
The post This Week in Scams: The AI “Truman Show” Scam Draining Bank Accounts appeared first on McAfee Blog.


.jpg)