A Ukrainian man indicted in 2012 for conspiring with a prolific hacking group to steal tens of millions of dollars from U.S. businesses was arrested in Italy and is now in custody in the United States, KrebsOnSecurity has learned.
Sources close to the investigation say Yuriy Igorevich Rybtsov, a 41-year-old from the Russia-controlled city of Donetsk, Ukraine, was previously referenced in U.S. federal charging documents only by his online handle “MrICQ.” According to a 13-year-old indictment (PDF) filed by prosecutors in Nebraska, MrICQ was a developer for a cybercrime group known as “Jabber Zeus.”
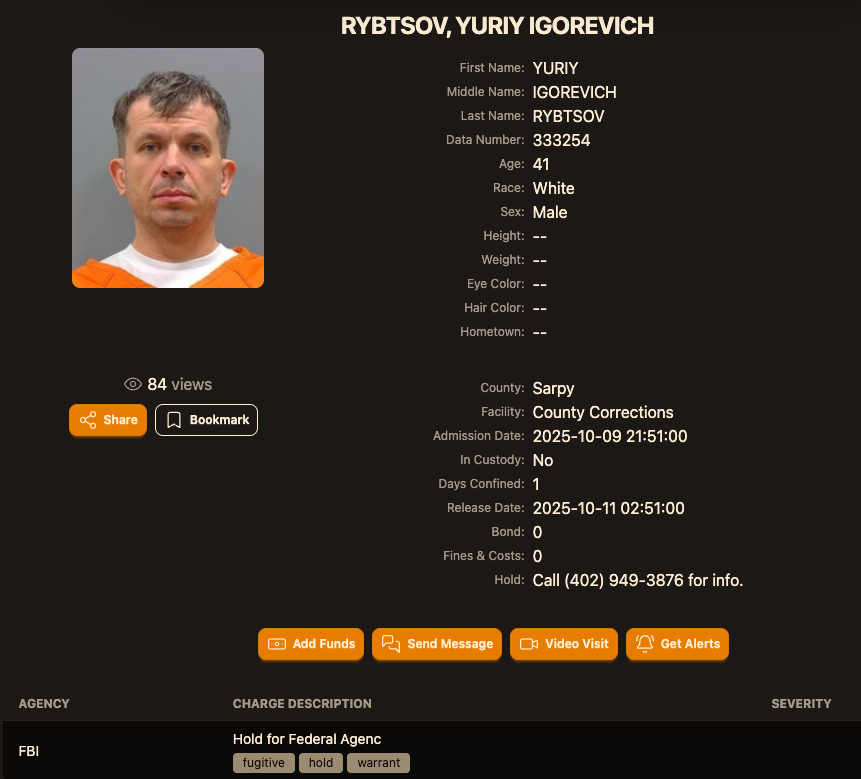
Image: lockedup dot wtf.
The Jabber Zeus name is derived from the malware they used — a custom version of the ZeuS banking trojan — that stole banking login credentials and would send the group a Jabber instant message each time a new victim entered a one-time passcode at a financial institution website. The gang targeted mostly small to mid-sized businesses, and they were an early pioneer of so-called “man-in-the-browser” attacks, malware that can silently intercept any data that victims submit in a web-based form.
Once inside a victim company’s accounts, the Jabber Zeus crew would modify the firm’s payroll to add dozens of “money mules,” people recruited through elaborate work-at-home schemes to handle bank transfers. The mules in turn would forward any stolen payroll deposits — minus their commissions — via wire transfers to other mules in Ukraine and the United Kingdom.
The 2012 indictment targeting the Jabber Zeus crew named MrICQ as “John Doe #3,” and said this person handled incoming notifications of newly compromised victims. The Department of Justice (DOJ) said MrICQ also helped the group launder the proceeds of their heists through electronic currency exchange services.
Two sources familiar with the Jabber Zeus investigation said Rybtsov was arrested in Italy, although the exact date and circumstances of his arrest remain unclear. A summary of recent decisions (PDF) published by the Italian Supreme Court states that in April 2025, Rybtsov lost a final appeal to avoid extradition to the United States.
According to the mugshot website lockedup[.]wtf, Rybtsov arrived in Nebraska on October 9, and was being held under an arrest warrant from the U.S. Federal Bureau of Investigation (FBI).
The data breach tracking service Constella Intelligence found breached records from the business profiling site bvdinfo[.]com showing that a 41-year-old Yuriy Igorevich Rybtsov worked in a building at 59 Barnaulska St. in Donetsk. Further searching on this address in Constella finds the same apartment building was shared by a business registered to Vyacheslav “Tank” Penchukov, the leader of the Jabber Zeus crew in Ukraine.

Vyacheslav “Tank” Penchukov, seen here performing as “DJ Slava Rich” in Ukraine, in an undated photo from social media.
Penchukov was arrested in 2022 while traveling to meet his wife in Switzerland. Last year, a federal court in Nebraska sentenced Penchukov to 18 years in prison and ordered him to pay more than $73 million in restitution.
Lawrence Baldwin is founder of myNetWatchman, a threat intelligence company based in Georgia that began tracking and disrupting the Jabber Zeus gang in 2009. myNetWatchman had secretly gained access to the Jabber chat server used by the Ukrainian hackers, allowing Baldwin to eavesdrop on the daily conversations between MrICQ and other Jabber Zeus members.
Baldwin shared those real-time chat records with multiple state and federal law enforcement agencies, and with this reporter. Between 2010 and 2013, I spent several hours each day alerting small businesses across the country that their payroll accounts were about to be drained by these cybercriminals.
Those notifications, and Baldwin’s tireless efforts, saved countless would-be victims a great deal of money. In most cases, however, we were already too late. Nevertheless, the pilfered Jabber Zeus group chats provided the basis for dozens of stories published here about small businesses fighting their banks in court over six- and seven-figure financial losses.
Baldwin said the Jabber Zeus crew was far ahead of its peers in several respects. For starters, their intercepted chats showed they worked to create a highly customized botnet directly with the author of the original Zeus Trojan — Evgeniy Mikhailovich Bogachev, a Russian man who has long been on the FBI’s “Most Wanted” list. The feds have a standing $3 million reward for information leading to Bogachev’s arrest.

Evgeniy M. Bogachev, in undated photos.
The core innovation of Jabber Zeus was an alert that MrICQ would receive each time a new victim entered a one-time password code into a phishing page mimicking their financial institution. The gang’s internal name for this component was “Leprechaun,” (the video below from myNetWatchman shows it in action). Jabber Zeus would actually re-write the HTML code as displayed in the victim’s browser, allowing them to intercept any passcodes sent by the victim’s bank for multi-factor authentication.
“These guys had compromised such a large number of victims that they were getting buried in a tsunami of stolen banking credentials,” Baldwin told KrebsOnSecurity. “But the whole point of Leprechaun was to isolate the highest-value credentials — the commercial bank accounts with two-factor authentication turned on. They knew these were far juicier targets because they clearly had a lot more money to protect.”
Baldwin said the Jabber Zeus trojan also included a custom “backconnect” component that allowed the hackers to relay their bank account takeovers through the victim’s own infected PC.
“The Jabber Zeus crew were literally connecting to the victim’s bank account from the victim’s IP address, or from the remote control function and by fully emulating the device,” he said. “That trojan was like a hot knife through butter of what everyone thought was state-of-the-art secure online banking at the time.”
Although the Jabber Zeus crew was in direct contact with the Zeus author, the chats intercepted by myNetWatchman show Bogachev frequently ignored the group’s pleas for help. The government says the real leader of the Jabber Zeus crew was Maksim Yakubets, a 38-year Ukrainian man with Russian citizenship who went by the hacker handle “Aqua.”

Alleged Evil Corp leader Maksim “Aqua” Yakubets. Image: FBI
The Jabber chats intercepted by Baldwin show that Aqua interacted almost daily with MrICQ, Tank and other members of the hacking team, often facilitating the group’s money mule and cashout activities remotely from Russia.
The government says Yakubets/Aqua would later emerge as the leader of an elite cybercrime ring of at least 17 hackers that referred to themselves internally as “Evil Corp.” Members of Evil Corp developed and used the Dridex (a.k.a. Bugat) trojan, which helped them siphon more than $100 million from hundreds of victim companies in the United States and Europe.
This 2019 story about the government’s $5 million bounty for information leading to Yakubets’s arrest includes excerpts of conversations between Aqua, Tank, Bogachev and other Jabber Zeus crew members discussing stories I’d written about their victims. Both Baldwin and I were interviewed at length for a new weekly six-part podcast by the BBC that delves deep into the history of Evil Corp. Episode One focuses on the evolution of Zeus, while the second episode centers on an investigation into the group by former FBI agent Jim Craig.

Image: https://www.bbc.co.uk/programmes/w3ct89y8
A 20-year-old Florida man at the center of a prolific cybercrime group known as “Scattered Spider” was sentenced to 10 years in federal prison today, and ordered to pay roughly $13 million in restitution to victims.
Noah Michael Urban of Palm Coast, Fla. pleaded guilty in April 2025 to charges of wire fraud and conspiracy. Florida prosecutors alleged Urban conspired with others to steal at least $800,000 from five victims via SIM-swapping attacks that diverted their mobile phone calls and text messages to devices controlled by Urban and his co-conspirators.

A booking photo of Noah Michael Urban released by the Volusia County Sheriff.
Although prosecutors had asked for Urban to serve eight years, Jacksonville news outlet News4Jax.com reports the federal judge in the case today opted to sentence Urban to 120 months in federal prison, ordering him to pay $13 million in restitution and undergo three years of supervised release after his sentence is completed.
In November 2024 Urban was charged by federal prosecutors in Los Angeles as one of five members of Scattered Spider (a.k.a. “Oktapus,” “Scatter Swine” and “UNC3944”), which specialized in SMS and voice phishing attacks that tricked employees at victim companies into entering their credentials and one-time passcodes at phishing websites. Urban pleaded guilty to one count of conspiracy to commit wire fraud in the California case, and the $13 million in restitution is intended to cover victims from both cases.
The targeted SMS scams spanned several months during the summer of 2022, asking employees to click a link and log in at a website that mimicked their employer’s Okta authentication page. Some SMS phishing messages told employees their VPN credentials were expiring and needed to be changed; other missives advised employees about changes to their upcoming work schedule.
That phishing spree netted Urban and others access to more than 130 companies, including Twilio, LastPass, DoorDash, MailChimp, and Plex. The government says the group used that access to steal proprietary company data and customer information, and that members also phished people to steal millions of dollars worth of cryptocurrency.
For many years, Urban’s online hacker aliases “King Bob” and “Sosa” were fixtures of the Com, a mostly Telegram and Discord-based community of English-speaking cybercriminals wherein hackers boast loudly about high-profile exploits and hacks that almost invariably begin with social engineering. King Bob constantly bragged on the Com about stealing unreleased rap music recordings from popular artists, presumably through SIM-swapping attacks. Many of those purloined tracks or “grails” he later sold or gave away on forums.
Noah “King Bob” Urban, posting to Twitter/X around the time of his sentencing today.
Sosa also was active in a particularly destructive group of accomplished criminal SIM-swappers known as “Star Fraud.” Cyberscoop’s AJ Vicens reported in 2023 that individuals within Star Fraud were likely involved in the high-profile Caesars Entertainment and MGM Resorts extortion attacks that same year.
The Star Fraud SIM-swapping group gained the ability to temporarily move targeted mobile numbers to devices they controlled by constantly phishing employees of the major mobile providers. In February 2023, KrebsOnSecurity published data taken from the Telegram channels for Star Fraud and two other SIM-swapping groups showing these crooks focused on SIM-swapping T-Mobile customers, and that they collectively claimed internal access to T-Mobile on 100 separate occasions over a 7-month period in 2022.
Reached via one of his King Bob accounts on Twitter/X, Urban called the sentence unjust, and said the judge in his case discounted his age as a factor.
“The judge purposefully ignored my age as a factor because of the fact another Scattered Spider member hacked him personally during the course of my case,” Urban said in reply to questions, noting that he was sending the messages from a Florida county jail. “He should have been removed as a judge much earlier on. But staying in county jail is torture.”
A court transcript (PDF) from a status hearing in February 2025 shows Urban was telling the truth about the hacking incident that happened while he was in federal custody. It involved an intrusion into a magistrate judge’s email account, where a copy of Urban’s sealed indictment was stolen. The judge told attorneys for both sides that a co-defendant in the California case was trying to find out about Mr. Urban’s activity in the Florida case.
“What it ultimately turned into a was a big faux pas,” Judge Harvey E. Schlesinger said. “The Court’s password…business is handled by an outside contractor. And somebody called the outside contractor representing Judge Toomey saying, ‘I need a password change.’ And they gave out the password change. That’s how whoever was making the phone call got into the court.”
A Texas firm recently charged with conspiring to distribute synthetic opioids in the United States is at the center of a vast network of companies in the U.S. and Pakistan whose employees are accused of using online ads to scam westerners seeking help with trademarks, book writing, mobile app development and logo designs, a new investigation reveals.
In an indictment (PDF) unsealed last month, the U.S. Department of Justice said Dallas-based eWorldTrade “operated an online business-to-business marketplace that facilitated the distribution of synthetic opioids such as isotonitazene and carfentanyl, both significantly more potent than fentanyl.”
Launched in 2017, eWorldTrade[.]com now features a seizure notice from the DOJ. eWorldTrade operated as a wholesale seller of consumer goods, including clothes, machinery, chemicals, automobiles and appliances. The DOJ’s indictment includes no additional details about eWorldTrade’s business, origins or other activity, and at first glance the website might appear to be a legitimate e-commerce platform that also just happened to sell some restricted chemicals.

A screenshot of the eWorldTrade homepage on March 25, 2025. Image: archive.org.
However, an investigation into the company’s founders reveals they are connected to a sprawling network of websites that have a history of extortionate scams involving trademark registration, book publishing, exam preparation, and the design of logos, mobile applications and websites.
Records from the U.S. Patent and Trademark Office (USPTO) show the eWorldTrade mark is owned by an Azneem Bilwani in Karachi (this name also is in the registration records for the now-seized eWorldTrade domain). Mr. Bilwani is perhaps better known as the director of the Pakistan-based IT provider Abtach Ltd., which has been singled out by the USPTO and Google for operating trademark registration scams (the main offices for eWorldtrade and Abtach share the same address in Pakistan).
In November 2021, the USPTO accused Abtach of perpetrating “an egregious scheme to deceive and defraud applicants for federal trademark registrations by improperly altering official USPTO correspondence, overcharging application filing fees, misappropriating the USPTO’s trademarks, and impersonating the USPTO.”
Abtach offered trademark registration at suspiciously low prices compared to legitimate costs of over USD $1,500, and claimed they could register a trademark in 24 hours. Abtach reportedly rebranded to Intersys Limited after the USPTO banned Abtach from filing any more trademark applications.
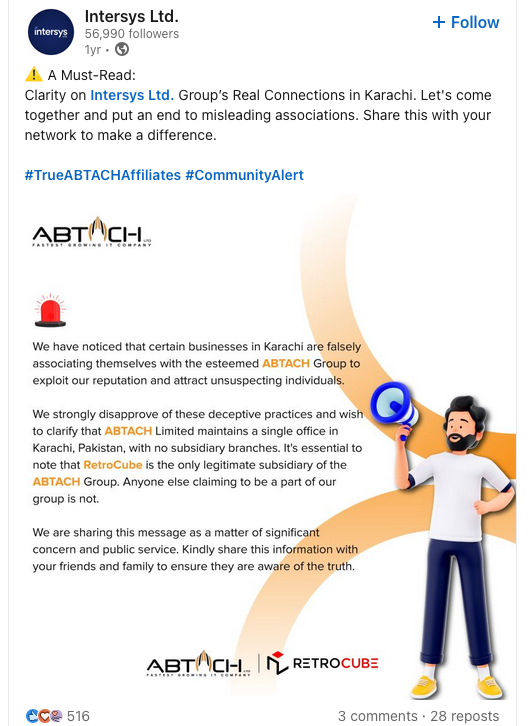
In a note published to its LinkedIn profile, Intersys Ltd. asserted last year that certain scam firms in Karachi were impersonating the company.
Many of Abtach’s employees are former associates of a similar company in Pakistan called Axact that was targeted by Pakistani authorities in a 2015 fraud investigation. Axact came under law enforcement scrutiny after The New York Times ran a front-page story about the company’s most lucrative scam business: Hundreds of sites peddling fake college degrees and diplomas.
People who purchased fake certifications were subsequently blackmailed by Axact employees posing as government officials, who would demand additional payments under threats of prosecution or imprisonment for having bought fraudulent “unauthorized” academic degrees. This practice created a continuous cycle of extortion, internally referred to as “upselling.”
“Axact took money from at least 215,000 people in 197 countries — one-third of them from the United States,” The Times reported. “Sales agents wielded threats and false promises and impersonated government officials, earning the company at least $89 million in its final year of operation.”
Dozens of top Axact employees were arrested, jailed, held for months, tried and sentenced to seven years for various fraud violations. But a 2019 research brief on Axact’s diploma mills found none of those convicted had started their prison sentence, and that several had fled Pakistan and never returned.
“In October 2016, a Pakistan district judge acquitted 24 Axact officials at trial due to ‘not enough evidence’ and then later admitted he had accepted a bribe (of $35,209) from Axact,” reads a history (PDF) published by the American Association of Collegiate Registrars and Admissions Officers.
In 2021, Pakistan’s Federal Investigation Agency (FIA) charged Bilwani and nearly four dozen others — many of them Abtach employees — with running an elaborate trademark scam. The authorities called it “the biggest money laundering case in the history of Pakistan,” and named a number of businesses based in Texas that allegedly helped move the proceeds of cybercrime.

A page from the March 2021 FIA report alleging that Digitonics Labs and Abtach employees conspired to extort and defraud consumers.
The FIA said the defendants operated a large number of websites offering low-cost trademark services to customers, before then “ignoring them after getting the funds and later demanding more funds from clients/victims in the name of up-sale (extortion).” The Pakistani law enforcement agency said that about 75 percent of customers received fake or fabricated trademarks as a result of the scams.
The FIA found Abtach operates in conjunction with a Karachi firm called Digitonics Labs, which earned a monthly revenue of around $2.5 million through the “extortion of international clients in the name of up-selling, the sale of fake/fabricated USPTO certificates, and the maintaining of phishing websites.”
According the Pakistani authorities, the accused also ran countless scams involving ebook publication and logo creation, wherein customers are subjected to advance-fee fraud and extortion — with the scammers demanding more money for supposed “copyright release” and threatening to release the trademark.
Also charged by the FIA was Junaid Mansoor, the owner of Digitonics Labs in Karachi. Mansoor’s U.K.-registered company Maple Solutions Direct Limited has run at least 700 ads for logo design websites since 2015, the Google Ads Transparency page reports. The company has approximately 88 ads running on Google as of today.

Junaid Mansoor. Source: youtube/@Olevels․com School.
Mr. Mansoor is actively involved with and promoting a Quran study business called quranmasteronline[.]com, which was founded by Junaid’s brother Qasim Mansoor (Qasim is also named in the FIA criminal investigation). The Google ads promoting quranmasteronline[.]com were paid for by the same account advertising a number of scam websites selling logo and web design services.
Junaid Mansoor did not respond to requests for comment. An address in Teaneck, New Jersey where Mr. Mansoor previously lived is listed as an official address of exporthub[.]com, a Pakistan-based e-commerce website that appears remarkably similar to eWorldTrade (Exporthub says its offices are in Texas). Interestingly, a search in Google for this domain shows ExportHub currently features multiple listings for fentanyl citrate from suppliers in China and elsewhere.
The CEO of Digitonics Labs is Muhammad Burhan Mirza, a former Axact official who was arrested by the FIA as part of its money laundering and trademark fraud investigation in 2021. In 2023, prosecutors in Pakistan charged Mirza, Mansoor and 14 other Digitonics employees with fraud, impersonating government officials, phishing, cheating and extortion. Mirza’s LinkedIn profile says he currently runs an educational technology/life coach enterprise called TheCoach360, which purports to help young kids “achieve financial independence.”
Reached via LinkedIn, Mr. Mirza denied having anything to do with eWorldTrade or any of its sister companies in Texas.
“Moreover, I have no knowledge as to the companies you have mentioned,” said Mr. Mirza, who did not respond to follow-up questions.
The current disposition of the FIA’s fraud case against the defendants is unclear. The investigation was marred early on by allegations of corruption and bribery. In 2021, Pakistani authorities alleged Bilwani paid a six-figure bribe to FIA investigators. Meanwhile, attorneys for Mr. Bilwani have argued that although their client did pay a bribe, the payment was solicited by government officials. Mr. Bilwani did not respond to requests for comment.
KrebsOnSecurity has learned that the people and entities at the center of the FIA investigations have built a significant presence in the United States, with a strong concentration in Texas. The Texas businesses promote websites that sell logo and web design, ghostwriting, and academic cheating services. Many of these entities have recently been sued for fraud and breach of contract by angry former customers, who claimed the companies relentlessly upsold them while failing to produce the work as promised.
For example, the FIA complaints named Retrocube LLC and 360 Digital Marketing LLC, two entities that share a street address with eWorldTrade: 1910 Pacific Avenue, Suite 8025, Dallas, Texas. Also incorporated at that Pacific Avenue address is abtach[.]ae, a web design and marketing firm based in Dubai; and intersyslimited[.]com, the new name of Abtach after they were banned by the USPTO. Other businesses registered at this address market services for logo design, mobile app development, and ghostwriting.
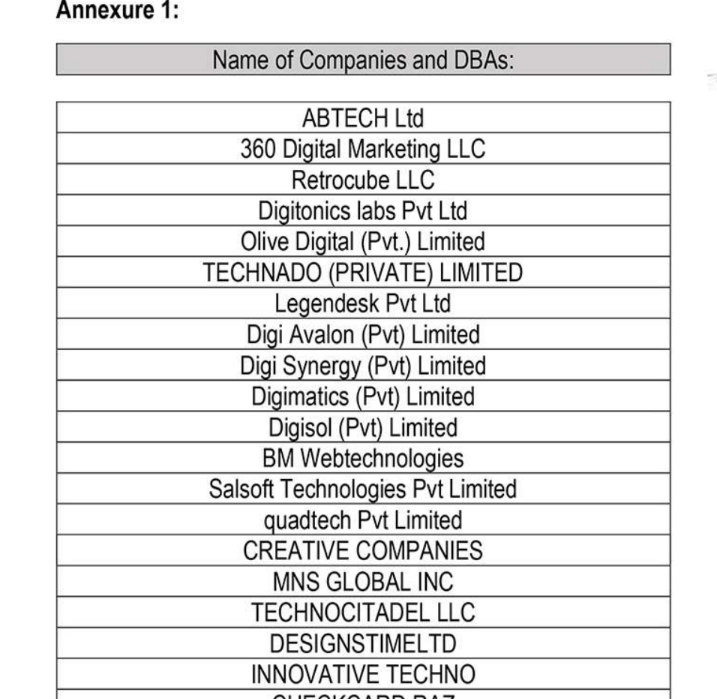
A list published in 2021 by Pakistan’s FIA of different front companies allegedly involved in scamming people who are looking for help with trademarks, ghostwriting, logos and web design.
360 Digital Marketing’s website 360digimarketing[.]com is owned by an Abtach front company called Abtech LTD. Meanwhile, business records show 360 Digi Marketing LTD is a U.K. company whose officers include former Abtach director Bilwani; Muhammad Saad Iqbal, formerly Abtach, now CEO of Intersys Ltd; Niaz Ahmed, a former Abtach associate; and Muhammad Salman Yousuf, formerly a vice president at Axact, Abtach, and Digitonics Labs.
Google’s Ads Transparency Center finds 360 Digital Marketing LLC ran at least 500 ads promoting various websites selling ghostwriting services . Another entity tied to Junaid Mansoor — a company called Octa Group Technologies AU — has run approximately 300 Google ads for book publishing services, promoting confusingly named websites like amazonlistinghub[.]com and barnesnoblepublishing[.]co.
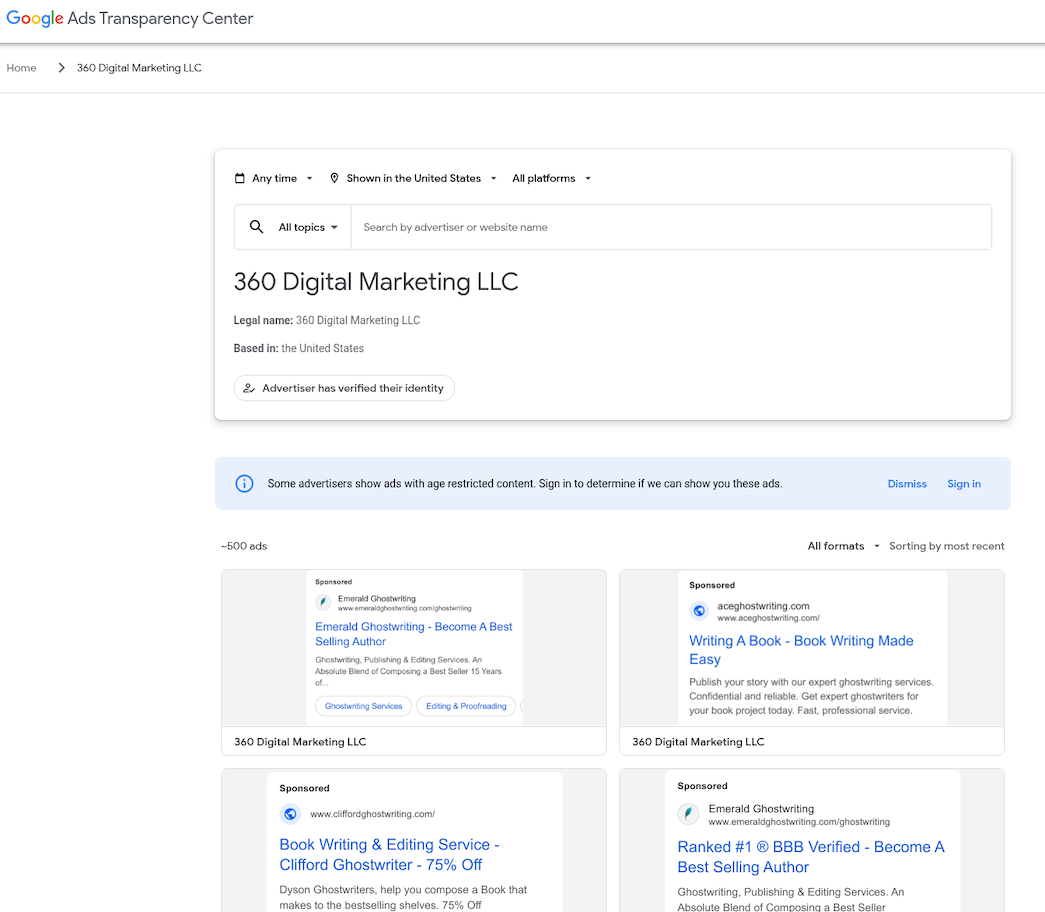
360 Digital Marketing LLC ran approximately 500 ads for scam ghostwriting sites.
Rameez Moiz is a Texas resident and former Abtach product manager who has represented 360 Digital Marketing LLC and RetroCube. Moiz told KrebsOnSecurity he stopped working for 360 Digital Marketing in the summer of 2023. Mr. Moiz did not respond to follow-up questions, but an Upwork profile for him states that as of April 2025 he is employed by Dallas-based Vertical Minds LLC.
In April 2025, California resident Melinda Will sued the Texas firm Majestic Ghostwriting — which is doing business as ghostwritingsquad[.]com — alleging they scammed her out of $100,000 after she hired them to help write her book. Google’s ad transparency page shows Moiz’s employer Vertical Minds LLC paid to run approximately 55 ads for ghostwritingsquad[.]com and related sites.
Ms. Will’s lawsuit is just one of more than two dozen complaints over the past four years wherein plaintiffs sued one of this group’s web design, wiki editing or ghostwriting services. In 2021, a New Jersey man sued Octagroup Technologies, alleging they ripped him off when he paid a total of more than $26,000 for the design and marketing of a web-based mapping service.
The plaintiff in that case did not respond to requests for comment, but his complaint alleges Octagroup and a myriad other companies it contracted with produced minimal work product despite subjecting him to relentless upselling. That case was decided in favor of the plaintiff because the defendants never contested the matter in court.
In 2023, 360 Digital Marketing LLC and Retrocube LLC were sued by a woman who said they scammed her out of $40,000 over a book she wanted help writing. That lawsuit helpfully showed an image of the office front door at 1910 Pacific Ave Suite 8025, which featured the logos of 360 Digital Marketing, Retrocube, and eWorldTrade.

The front door at 1910 Pacific Avenue, Suite 8025, Dallas, Texas.
The lawsuit was filed pro se by Leigh Riley, a 64-year-old career IT professional who paid 360 Digital Marketing to have a company called Talented Ghostwriter co-author and promote a series of books she’d outlined on spirituality and healing.
“The main reason I hired them was because I didn’t understand what I call the formula for writing a book, and I know there’s a lot of marketing that goes into publishing,” Riley explained in an interview. “I know nothing about that stuff, and these guys were convincing that they could handle all aspects of it. Until I discovered they couldn’t write a damn sentence in English properly.”
Riley’s well-documented lawsuit (not linked here because it features a great deal of personal information) includes screenshots of conversations with the ghostwriting team, which was constantly assigning her to new writers and editors, and ghosting her on scheduled conference calls about progress on the project. Riley said she ended up writing most of the book herself because the work they produced was unusable.
“Finally after months of promising the books were printed and on their way, they show up at my doorstep with the wrong title on the book,” Riley said. When she demanded her money back, she said the people helping her with the website to promote the book locked her out of the site.
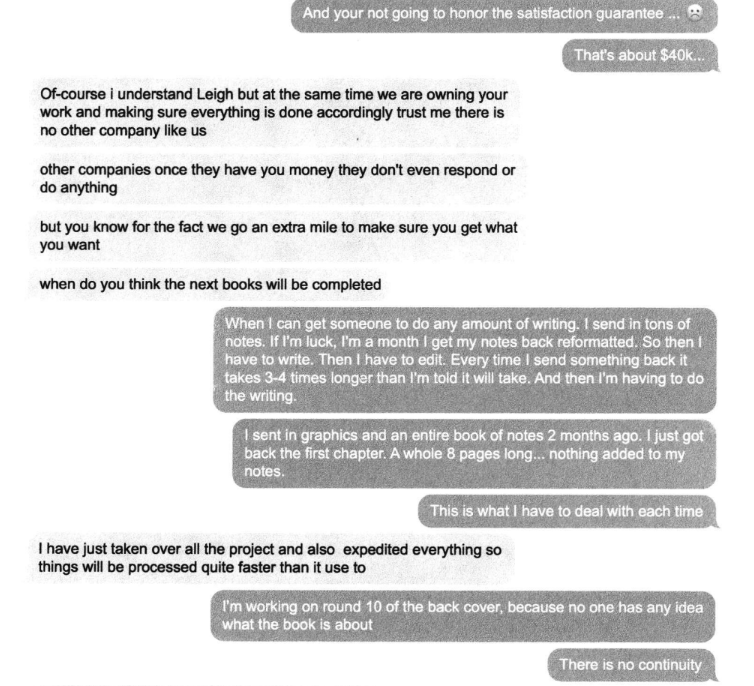
A conversation snippet from Leigh Riley’s lawsuit against Talented Ghostwriter, aka 360 Digital Marketing LLC. “Other companies once they have you money they don’t even respond or do anything,” the ghostwriting team manager explained.
Riley decided to sue, naming 360 Digital Marketing LLC and Retrocube LLC, among others. The companies offered to settle the matter for $20,000, which she accepted. “I didn’t have money to hire a lawyer, and I figured it was time to cut my losses,” she said.
Riley said she could have saved herself a great deal of headache by doing some basic research on Talented Ghostwriter, whose website claims the company is based in Los Angeles. According to the California Secretary of State, however, there is no registered entity by that name. Rather, the address claimed by talentedghostwriter[.]com is a vacant office building with a “space available” sign in the window.
California resident Walter Horsting discovered something similar when he sued 360 Digital Marketing in small claims court last year, after hiring a company called Vox Ghostwriting to help write, edit and promote a spy novel he’d been working on. Horsting said he paid Vox $3,300 to ghostwrite a 280-page book, and was upsold an Amazon marketing and publishing package for $7,500.
In an interview, Horsting said the prose that Vox Ghostwriting produced was “juvenile at best,” forcing him to rewrite and edit the work himself, and to partner with a graphical artist to produce illustrations. Horsting said that when it came time to begin marketing the novel, Vox Ghostwriting tried to further upsell him on marketing packages, while dodging scheduled meetings with no follow-up.
“They have a money back guarantee, and when they wouldn’t refund my money I said I’m taking you to court,” Horsting recounted. “I tried to serve them in Los Angeles but found no such office exists. I talked to a salon next door and they said someone else had recently shown up desperately looking for where the ghostwriting company went, and it appears there are a trail of corpses on this. I finally tracked down where they are in Texas.”
It was the same office that Ms. Riley served her lawsuit against. Horsting said he has a court hearing scheduled later this month, but he’s under no illusions that winning the case means he’ll be able to collect.
“At this point, I’m doing it out of pride more than actually expecting anything to come to good fortune for me,” he said.
The following mind map was helpful in piecing together key events, individuals and connections mentioned above. It’s important to note that this graphic only scratches the surface of the operations tied to this group. For example, in Case 2 we can see mention of academic cheating services, wherein people can be hired to take online proctored exams on one’s behalf. Those who hire these services soon find themselves subject to impersonation and blackmail attempts for larger and larger sums of money, with the threat of publicly exposing their unethical academic cheating activity.
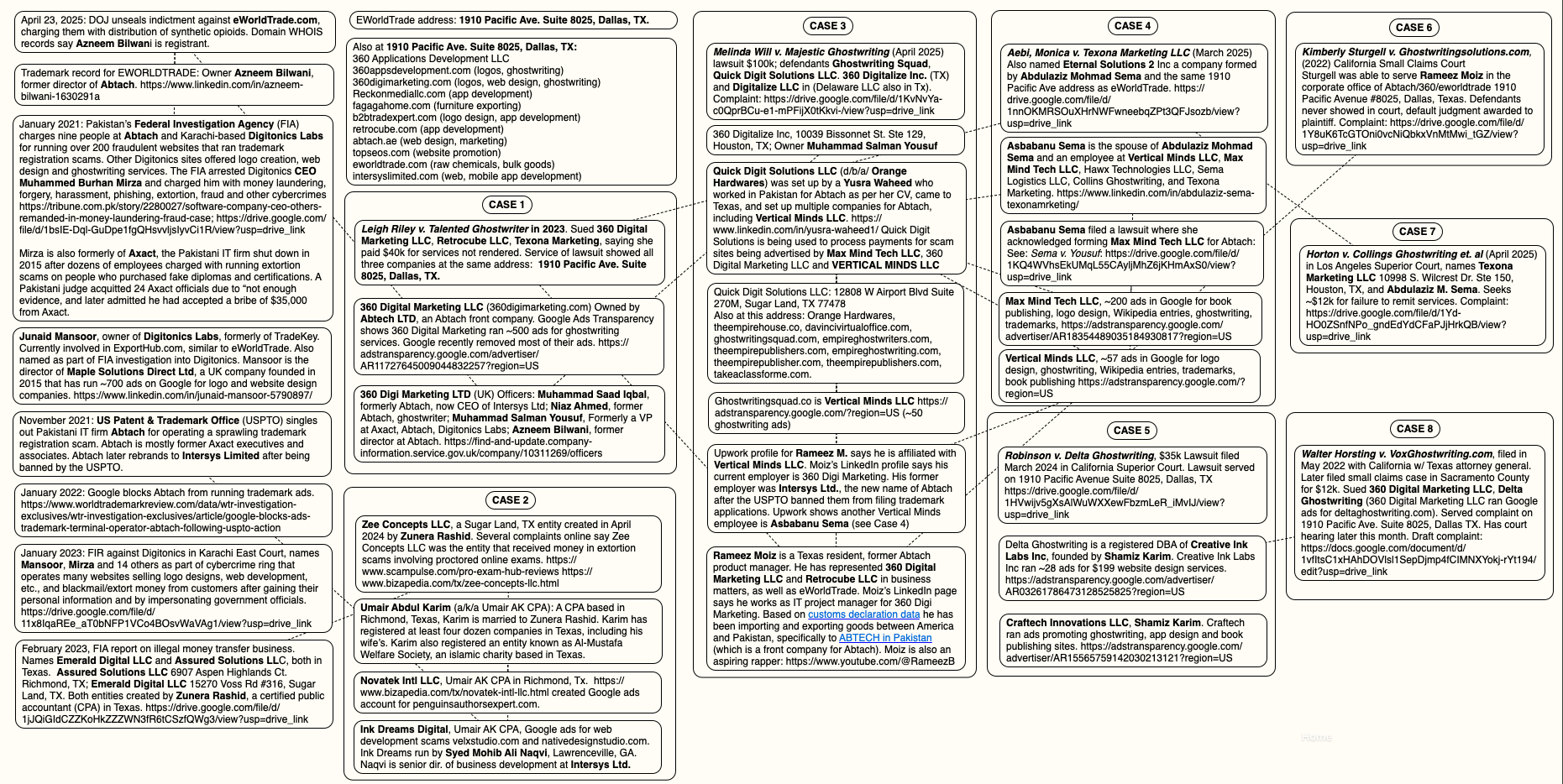
A “mind map” illustrating the connections between and among entities referenced in this story. Click to enlarge.
KrebsOnSecurity reviewed the Google Ad Transparency links for nearly 500 different websites tied to this network of ghostwriting, logo, app and web development businesses. Those website names were then fed into spyfu.com, a competitive intelligence company that tracks the reach and performance of advertising keywords. Spyfu estimates that between April 2023 and April 2025, those websites spent more than $10 million on Google ads.
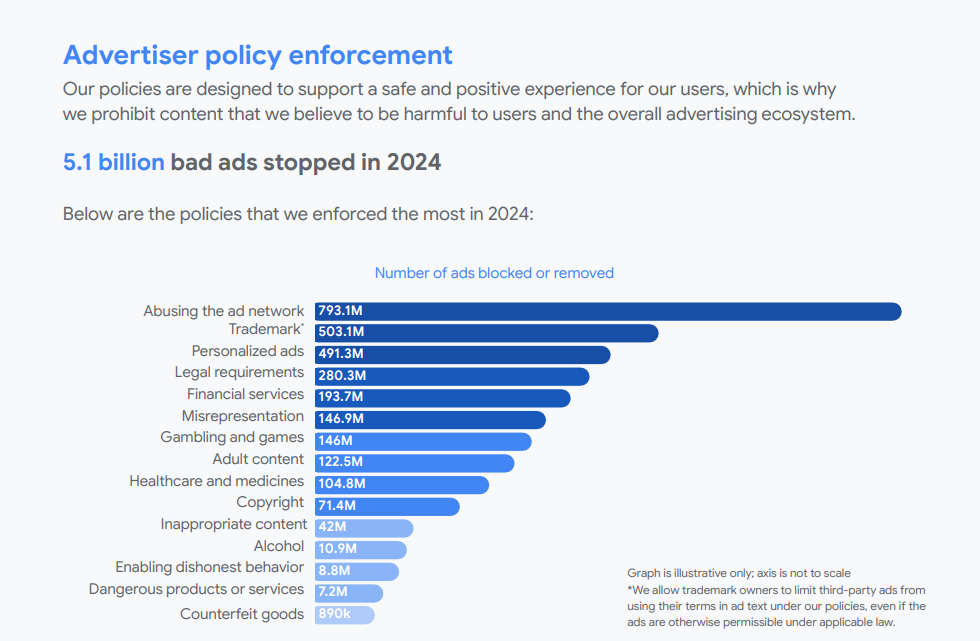
Reached for comment, Google said in a written statement that it is constantly policing its ad network for bad actors, pointing to an ads safety report (PDF) showing Google blocked or removed 5.1 billion bad ads last year — including more than 500 million ads related to trademarks.
“Our policy against Enabling Dishonest Behavior prohibits products or services that help users mislead others, including ads for paper-writing or exam-taking services,” the statement reads. “When we identify ads or advertisers that violate our policies, we take action, including by suspending advertiser accounts, disapproving ads, and restricting ads to specific domains when appropriate.”
Google did not respond to specific questions about the advertising entities mentioned in this story, saying only that “we are actively investigating this matter and addressing any policy violations, including suspending advertiser accounts when appropriate.”
From reviewing the ad accounts that have been promoting these scam websites, it appears Google has very recently acted to remove a large number of the offending ads. Prior to my notifying Google about the extent of this ad network on April 28, the Google Ad Transparency network listed over 500 ads for 360 Digital Marketing; as of this publication, that number had dwindled to 10.
On April 30, Google announced that starting this month its ads transparency page will display the payment profile name as the payer name for verified advertisers, if that name differs from their verified advertiser name. Searchengineland.com writes the changes are aimed at increasing accountability in digital advertising.
This spreadsheet lists the domain names, advertiser names, and Google Ad Transparency links for more than 350 entities offering ghostwriting, publishing, web design and academic cheating services.
KrebsOnSecurity would like to thank the anonymous security researcher NatInfoSec for their assistance in this investigation.
For further reading on Abtach and its myriad companies in all of the above-mentioned verticals (ghostwriting, logo design, etc.), see this Wikiwand entry.
A 23-year-old Scottish man thought to be a member of the prolific Scattered Spider cybercrime group was extradited last week from Spain to the United States, where he is facing charges of wire fraud, conspiracy and identity theft. U.S. prosecutors allege Tyler Robert Buchanan and co-conspirators hacked into dozens of companies in the United States and abroad, and that he personally controlled more than $26 million stolen from victims.
Scattered Spider is a loosely affiliated criminal hacking group whose members have broken into and stolen data from some of the world’s largest technology companies. Buchanan was arrested in Spain last year on a warrant from the FBI, which wanted him in connection with a series of SMS-based phishing attacks in the summer of 2022 that led to intrusions at Twilio, LastPass, DoorDash, Mailchimp, and many other tech firms.

Tyler Buchanan, being escorted by Spanish police at the airport in Palma de Mallorca in June 2024.
As first reported by KrebsOnSecurity, Buchanan (a.k.a. “tylerb”) fled the United Kingdom in February 2023, after a rival cybercrime gang hired thugs to invade his home, assault his mother, and threaten to burn him with a blowtorch unless he gave up the keys to his cryptocurrency wallet. Buchanan was arrested in June 2024 at the airport in Palma de Mallorca while trying to board a flight to Italy. His extradition to the United States was first reported last week by Bloomberg.
Members of Scattered Spider have been tied to the 2023 ransomware attacks against MGM and Caesars casinos in Las Vegas, but it remains unclear whether Buchanan was implicated in that incident. The Justice Department’s complaint against Buchanan makes no mention of the 2023 ransomware attack.
Rather, the investigation into Buchanan appears to center on the SMS phishing campaigns from 2022, and on SIM-swapping attacks that siphoned funds from individual cryptocurrency investors. In a SIM-swapping attack, crooks transfer the target’s phone number to a device they control and intercept any text messages or phone calls to the victim’s device — including one-time passcodes for authentication and password reset links sent via SMS.
In August 2022, KrebsOnSecurity reviewed data harvested in a months-long cybercrime campaign by Scattered Spider involving countless SMS-based phishing attacks against employees at major corporations. The security firm Group-IB called them by a different name — 0ktapus, because the group typically spoofed the identity provider Okta in their phishing messages to employees at targeted firms.
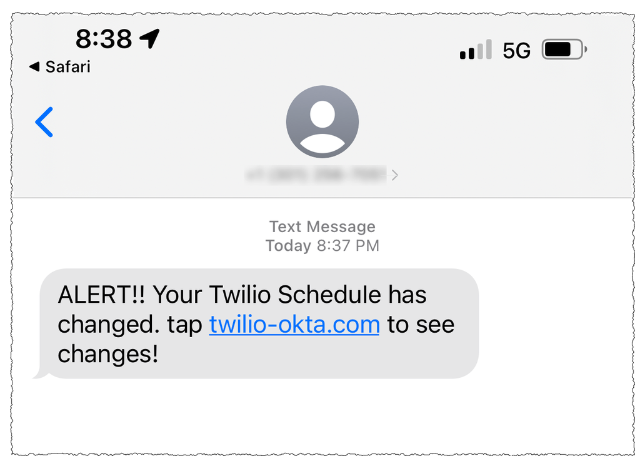
A Scattered Spider/0Ktapus SMS phishing lure sent to Twilio employees in 2022.
The complaint against Buchanan (PDF) says the FBI tied him to the 2022 SMS phishing attacks after discovering the same username and email address was used to register numerous Okta-themed phishing domains seen in the campaign. The domain registrar NameCheap found that less than a month before the phishing spree, the account that registered those domains logged in from an Internet address in the U.K. FBI investigators said the Scottish police told them the address was leased to Buchanan from January 26, 2022 to November 7, 2022.
Authorities seized at least 20 digital devices when they raided Buchanan’s residence, and on one of those devices they found usernames and passwords for employees of three different companies targeted in the phishing campaign.
“The FBI’s investigation to date has gathered evidence showing that Buchanan and his co-conspirators targeted at least 45 companies in the United States and abroad, including Canada, India, and the United Kingdom,” the FBI complaint reads. “One of Buchanan’s devices contained a screenshot of Telegram messages between an account known to be used by Buchanan and other unidentified co-conspirators discussing dividing up the proceeds of SIM swapping.”
U.S. prosecutors allege that records obtained from Discord showed the same U.K. Internet address was used to operate a Discord account that specified a cryptocurrency wallet when asking another user to send funds. The complaint says the publicly available transaction history for that payment address shows approximately 391 bitcoin was transferred in and out of this address between October 2022 and
February 2023; 391 bitcoin is presently worth more than $26 million.
In November 2024, federal prosecutors in Los Angeles unsealed criminal charges against Buchanan and four other alleged Scattered Spider members, including Ahmed Elbadawy, 23, of College Station, Texas; Joel Evans, 25, of Jacksonville, North Carolina; Evans Osiebo, 20, of Dallas; and Noah Urban, 20, of Palm Coast, Florida. KrebsOnSecurity reported last year that another suspected Scattered Spider member — a 17-year-old from the United Kingdom — was arrested as part of a joint investigation with the FBI into the MGM hack.
Mr. Buchanan’s court-appointed attorney did not respond to a request for comment. The accused faces charges of wire fraud conspiracy, conspiracy to obtain information by computer for private financial gain, and aggravated identity theft. Convictions on the latter charge carry a minimum sentence of two years in prison.
Documents from the U.S. District Court for the Central District of California indicate Buchanan is being held without bail pending trial. A preliminary hearing in the case is slated for May 6.
Federal prosecutors in Los Angeles this week unsealed criminal charges against five men alleged to be members of a hacking group responsible for dozens of cyber intrusions at major U.S. technology companies between 2021 and 2023, including LastPass, MailChimp, Okta, T-Mobile and Twilio.

A visual depiction of the attacks by the SMS phishing group known as Scattered Spider, and Oktapus. Image: Amitai Cohen twitter.com/amitaico.
The five men, aged 20 to 25, are allegedly members of a hacking conspiracy dubbed “Scattered Spider” and “Oktapus,” which specialized in SMS-based phishing attacks that tricked employees at tech firms into entering their credentials and one-time passcodes at phishing websites.
The targeted SMS scams asked employees to click a link and log in at a website that mimicked their employer’s Okta authentication page. Some SMS phishing messages told employees their VPN credentials were expiring and needed to be changed; other phishing messages advised employees about changes to their upcoming work schedule.
These attacks leveraged newly-registered domains that often included the name of the targeted company, such as twilio-help[.]com and ouryahoo-okta[.]com. The phishing websites were normally kept online for just one or two hours at a time, meaning they were often yanked offline before they could be flagged by anti-phishing and security services.
The phishing kits used for these campaigns featured a hidden Telegram instant message bot that forwarded any submitted credentials in real-time. The bot allowed the attackers to use the phished username, password and one-time code to log in as that employee at the real employer website.
In August 2022, multiple security firms gained access to the server that was receiving data from that Telegram bot, which on several occasions leaked the Telegram ID and handle of its developer, who used the nickname “Joeleoli.”
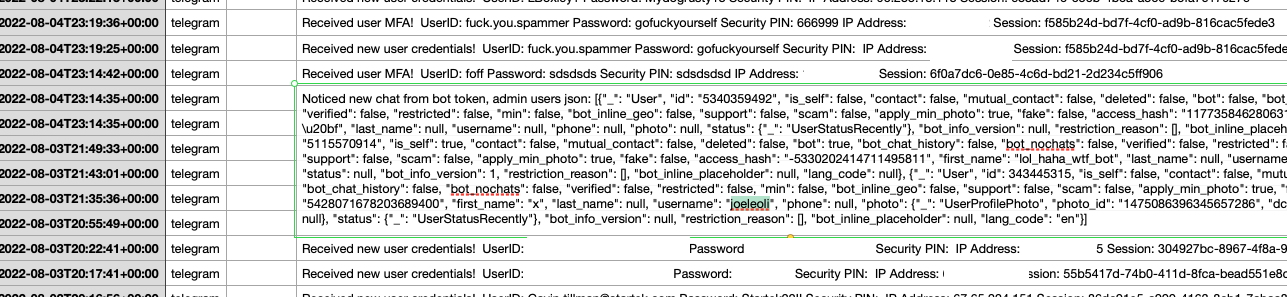
The Telegram username “Joeleoli” can be seen sandwiched between data submitted by people who knew it was a phish, and data phished from actual victims. Click to enlarge.
That Joeleoli moniker registered on the cybercrime forum OGusers in 2018 with the email address joelebruh@gmail.com, which also was used to register accounts at several websites for a Joel Evans from North Carolina. Indeed, prosecutors say Joeleoli’s real name is Joel Martin Evans, and he is a 25-year-old from Jacksonville, North Carolina.
One of Scattered Spider’s first big victims in its 2022 SMS phishing spree was Twilio, a company that provides services for making and receiving text messages and phone calls. The group then used their access to Twilio to attack at least 163 of its customers. According to prosecutors, the group mainly sought to steal cryptocurrency from victim companies and their employees.
“The defendants allegedly preyed on unsuspecting victims in this phishing scheme and used their personal information as a gateway to steal millions in their cryptocurrency accounts,” said Akil Davis, the assistant director in charge of the FBI’s Los Angeles field office.
Many of the hacking group’s phishing domains were registered through the registrar NameCheap, and FBI investigators said records obtained from NameCheap showed the person who managed those phishing websites did so from an Internet address in Scotland. The feds then obtained records from Virgin Media, which showed the address was leased for several months to Tyler Buchanan, a 22-year-old from Dundee, Scotland.

A Scattered Spider phishing lure sent to Twilio employees.
As first reported here in June, Buchanan was arrested in Spain as he tried to board a flight bound for Italy. The Spanish police told local media that Buchanan, who allegedly went by the alias “Tylerb,” at one time possessed Bitcoins worth $27 million.
The government says much of Tylerb’s cryptocurrency wealth was the result of successful SIM-swapping attacks, wherein crooks transfer the target’s phone number to a device they control and intercept any text messages or phone calls sent to the victim — including one-time passcodes for authentication, or password reset links sent via SMS.
According to several SIM-swapping channels on Telegram where Tylerb was known to frequent, rival SIM-swappers hired thugs to invade his home in February 2023. Those accounts state that the intruders assaulted Tylerb’s mother in the home invasion, and that they threatened to burn him with a blowtorch if he didn’t give up the keys to his cryptocurrency wallets. Tylerb was reputed to have fled the United Kingdom after that assault.

A still frame from a video released by the Spanish national police, showing Tyler Buchanan being taken into custody at the airport.
Prosecutors allege Tylerb worked closely on SIM-swapping attacks with Noah Michael Urban, another alleged Scattered Spider member from Palm Coast, Fla. who went by the handles “Sosa,” “Elijah,” and “Kingbob.”
Sosa was known to be a top member of the broader cybercriminal community online known as “The Com,” wherein hackers boast loudly about high-profile exploits and hacks that almost invariably begin with social engineering — tricking people over the phone, email or SMS into giving away credentials that allow remote access to corporate networks.
In January 2024, KrebsOnSecurity broke the news that Urban had been arrested in Florida in connection with multiple SIM-swapping attacks. That story noted that Sosa’s alter ego Kingbob routinely targeted people in the recording industry to steal and share “grails,” a slang term used to describe unreleased music recordings from popular artists.
FBI investigators identified a fourth alleged member of the conspiracy – Ahmed Hossam Eldin Elbadawy, 23, of College Station, Texas — after he used a portion of cryptocurrency funds stolen from a victim company to pay for an account used to register phishing domains.
The indictment unsealed Wednesday alleges Elbadawy controlled a number of cryptocurrency accounts used to receive stolen funds, along with another Texas man — Evans Onyeaka Osiebo, 20, of Dallas.
Members of Scattered Spider are reputed to have been involved in a September 2023 ransomware attack against the MGM Resorts hotel chain that quickly brought multiple MGM casinos to a standstill. In September 2024, KrebsOnSecurity reported that a 17-year-old from the United Kingdom was arrested last year by U.K. police as part of an FBI investigation into the MGM hack.
Evans, Elbadawy, Osiebo and Urban were all charged with one count of conspiracy to commit wire fraud, one count of conspiracy, and one count of aggravated identity theft. Buchanan, who is named as an indicted co-conspirator, was charged with conspiracy to commit wire fraud, conspiracy, wire fraud, and aggravated identity theft.
A Justice Department press release states that if convicted, each defendant would face a statutory maximum sentence of 20 years in federal prison for conspiracy to commit wire fraud, up to five years in federal prison for the conspiracy count, and a mandatory two-year consecutive prison sentence for aggravated identity theft. Buchanan would face up to 20 years in prison for the wire fraud count as well.
Further reading:
A 25-year-old man in Ontario, Canada has been arrested for allegedly stealing data from and extorting more than 160 companies that used the cloud data service Snowflake.

Image: https://www.pomerium.com/blog/the-real-lessons-from-the-snowflake-breach
On October 30, Canadian authorities arrested Alexander Moucka, a.k.a. Connor Riley Moucka of Kitchener, Ontario, on a provisional arrest warrant from the United States. Bloomberg first reported Moucka’s alleged ties to the Snowflake hacks on Monday.
At the end of 2023, malicious hackers learned that many large companies had uploaded huge volumes of sensitive customer data to Snowflake accounts that were protected with little more than a username and password (no multi-factor authentication required). After scouring darknet markets for stolen Snowflake account credentials, the hackers began raiding the data storage repositories used by some of the world’s largest corporations.
Among those was AT&T, which disclosed in July that cybercriminals had stolen personal information and phone and text message records for roughly 110 million people — nearly all of its customers. Wired.com reported in July that AT&T paid a hacker $370,000 to delete stolen phone records.
A report on the extortion attacks from the incident response firm Mandiant notes that Snowflake victim companies were privately approached by the hackers, who demanded a ransom in exchange for a promise not to sell or leak the stolen data. All told, more than 160 Snowflake customers were relieved of data, including TicketMaster, Lending Tree, Advance Auto Parts and Neiman Marcus.
Moucka is alleged to have used the hacker handles Judische and Waifu, among many others. These monikers correspond to a prolific cybercriminal whose exploits were the subject of a recent story published here about the overlap between Western, English-speaking cybercriminals and extremist groups that harass and extort minors into harming themselves or others.
On May 2, 2024, Judische claimed on the fraud-focused Telegram channel Star Chat that they had hacked Santander Bank, one of the first known Snowflake victims. Judische would repeat that claim in Star Chat on May 13 — the day before Santander publicly disclosed a data breach — and would periodically blurt out the names of other Snowflake victims before their data even went up for sale on the cybercrime forums.
404 Media reports that at a court hearing in Ontario this morning, Moucka called in from a prison phone and said he was seeking legal aid to hire an attorney.
Mandiant has attributed the Snowflake compromises to a group it calls “UNC5537,” with members based in North America and Turkey. Sources close to the investigation tell KrebsOnSecurity the UNC5537 member in Turkey is John Erin Binns, an elusive American man indicted by the U.S. Department of Justice (DOJ) for a 2021 breach at T-Mobile that exposed the personal information of at least 76.6 million customers.
Update: The Justice Department has unsealed an indictment (PDF) against Moucka and Binns, charging them with one count of conspiracy; 10 counts of wire fraud; four counts of computer fraud and abuse; two counts of extortion in relation to computer fraud; and two counts aggravated identity theft.
In a statement on Moucka’s arrest, Mandiant said UNC5537 aka Alexander ‘Connor’ Moucka has proven to be one of the most consequential threat actors of 2024.
“In April 2024, UNC5537 launched a campaign, systematically compromising misconfigured SaaS instances across over a hundred organizations,” wrote Austin Larsen, Mandiant’s senior threat analyst. “The operation, which left organizations reeling from significant data loss and extortion attempts, highlighted the alarming scale of harm an individual can cause using off-the-shelf tools.”
Sources involved in the investigation said UNC5537 has focused on hacking into telecommunications companies around the world. Those sources told KrebsOnSecurity that Binns and Judische are suspected of stealing data from India’s largest state-run telecommunications firm Bharat Sanchar Nigam Ltd (BNSL), and that the duo even bragged about being able to intercept or divert phone calls and text messages for a large portion of the population of India.
Judische appears to have outsourced the sale of databases from victim companies who refuse to pay, delegating some of that work to a cybercriminal who uses the nickname Kiberphant0m on multiple forums. In late May 2024, Kiberphant0m began advertising the sale of hundreds of gigabytes of data stolen from BSNL.
“Information is worth several million dollars but I’m selling for pretty cheap,” Kiberphant0m wrote of the BSNL data in a post on the English-language cybercrime community Breach Forums. “Negotiate a deal in Telegram.”

Also in May 2024, Kiberphant0m took to the Russian-language hacking forum XSS to sell more than 250 gigabytes of data stolen from an unnamed mobile telecom provider in Asia, including a database of all active customers and software allowing the sending of text messages to all customers.
On September 3, 2024, Kiberphant0m posted a sales thread on XSS titled “Selling American Telecom Access (100B+ Revenue).” Kiberphant0m’s asking price of $200,000 was apparently too high because they reposted the sales thread on Breach Forums a month later, with a headline that more clearly explained the data was stolen from Verizon‘s “push-to-talk” (PTT) customers — primarily U.S. government agencies and first responders.
404Media reported recently that the breach does not appear to impact the main consumer Verizon network. Rather, the hackers broke into a third party provider and stole data on Verizon’s PTT systems, which are a separate product marketed towards public sector agencies, enterprises, and small businesses to communicate internally.
Investigators say Moucka shared a home in Kitchener with other tenants, but not his family. His mother was born in Chechnya, and he speaks Russian in addition to French and English. Moucka’s father died of a drug overdose at age 26, when the defendant was roughly five years old.
A person claiming to be Judische began communicating with this author more than three months ago on Signal after KrebsOnSecurity started asking around about hacker nicknames previously used by Judische over the years.
Judische admitted to stealing and ransoming data from Snowflake customers, but he said he’s not interested in selling the information, and that others have done this with some of the data sets he stole.
“I’m not really someone that sells data unless it’s crypto [databases] or credit cards because they’re the only thing I can find buyers for that actually have money for the data,” Judische told KrebsOnSecurity. “The rest is just ransom.”
Judische has sent this reporter dozens of unsolicited and often profane messages from several different Signal accounts, all of which claimed to be an anonymous tipster sharing different identifying details for Judische. This appears to have been an elaborate effort by Judische to “detrace” his movements online and muddy the waters about his identity.
Judische frequently claimed he had unparalleled “opsec” or operational security, a term that refers to the ability to compartmentalize and obfuscate one’s tracks online. In an effort to show he was one step ahead of investigators, Judische shared information indicating someone had given him a Mandiant researcher’s assessment of who and where they thought he was. Mandiant says those were discussion points shared with select reporters in advance of the researcher’s recent talk at the LabsCon security conference.
But in a conversation with KrebsOnSecurity on October 26, Judische acknowledged it was likely that the authorities were closing in on him, and said he would seriously answer certain questions about his personal life.
“They’re coming after me for sure,” he said.
In several previous conversations, Judische referenced suffering from an unspecified personality disorder, and when pressed said he has a condition called “schizotypal personality disorder” (STPD).
According to the Cleveland Clinic, schizotypal personality disorder is marked by a consistent pattern of intense discomfort with relationships and social interactions: “People with STPD have unusual thoughts, speech and behaviors, which usually hinder their ability to form and maintain relationships.”
Judische said he was prescribed medication for his psychological issues, but that he doesn’t take his meds. Which might explain why he never leaves his home.
“I never go outside,” Judische allowed. “I’ve never had a friend or true relationship not online nor in person. I see people as vehicles to achieve my ends no matter how friendly I may seem on the surface, which you can see by how fast I discard people who are loyal or [that] I’ve known a long time.”
Judische later admitted he doesn’t have an official STPD diagnosis from a physician, but said he knows that he exhibits all the signs of someone with this condition.
“I can’t actually get diagnosed with that either,” Judische shared. “Most countries put you on lists and restrict you from certain things if you have it.”
Asked whether he has always lived at his current residence, Judische replied that he had to leave his hometown for his own safety.
“I can’t live safely where I’m from without getting robbed or arrested,” he said, without offering more details.
A source familiar with the investigation said Moucka previously lived in Quebec, which he allegedly fled after being charged with harassing others on the social network Discord.
Judische claims to have made at least $4 million in his Snowflake extortions. Judische said he and others frequently targeted business process outsourcing (BPO) companies, staffing firms that handle customer service for a wide range of organizations. They also went after managed service providers (MSPs) that oversee IT support and security for multiple companies, he claimed.
“Snowflake isn’t even the biggest BPO/MSP multi-company dataset on our networks, but what’s been exfiltrated from them is well over 100TB,” Judische bragged. “Only ones that don’t pay get disclosed (unless they disclose it themselves). A lot of them don’t even do their SEC filing and just pay us to fuck off.”
The other half of UNC5537 — 24-year-old John Erin Binns — was arrested in Turkey in late May 2024, and currently resides in a Turkish prison. However, it is unclear if Binns faces any immediate threat of extradition to the United States, where he is currently wanted on criminal hacking charges tied to the 2021 breach at T-Mobile.
A person familiar with the investigation said Binns’s application for Turkish citizenship was inexplicably approved after his incarceration, leading to speculation that Binns may have bought his way out of a sticky legal situation.
Under the Turkish constitution, a Turkish citizen cannot be extradited to a foreign state. Turkey has been criticized for its “golden passport” program, which provides citizenship and sanctuary for anyone willing to pay several hundred thousand dollars.

This is an image of a passport that Binns shared in one of many unsolicited emails to KrebsOnSecurity since 2021. Binns never explained why he sent this in Feb. 2023.
Binns’s alleged hacker alter egos — “IRDev” and “IntelSecrets” — were at once feared and revered on several cybercrime-focused Telegram communities, because he was known to possess a powerful weapon: A massive botnet. From reviewing the Telegram channels Binns frequented, we can see that others in those communities — including Judische — heavily relied on Binns and his botnet for a variety of cybercriminal purposes.
The IntelSecrets nickname corresponds to an individual who has claimed responsibility for modifying the source code for the Mirai “Internet of Things” botnet to create a variant known as “Satori,” and supplying it to others who used it for criminal gain and were later caught and prosecuted.
Since 2020, Binns has filed a flood of lawsuits naming various federal law enforcement officers and agencies — including the FBI, the CIA, and the U.S. Special Operations Command (PDF), demanding that the government turn over information collected about him and seeking restitution for his alleged kidnapping at the hands of the CIA.
Binns claims he was kidnapped in Turkey and subjected to various forms of psychological and physical torture. According to Binns, the U.S. Central Intelligence Agency (CIA) falsely told their counterparts in Turkey that he was a supporter or member of the Islamic State (ISIS), a claim he says led to his detention and torture by the Turkish authorities.
However, in a 2020 lawsuit he filed against the CIA, Binns himself acknowledged having visited a previously ISIS-controlled area of Syria prior to moving to Turkey in 2017.

A segment of a lawsuit Binns filed in 2020 against the CIA, in which he alleges U.S. put him on a terror watch list after he traveled to Syria in 2017.
Sources familiar with the investigation told KrebsOnSecurity that Binns was so paranoid about possible surveillance on him by American and Turkish intelligence agencies that his erratic behavior and online communications actually brought about the very government snooping that he feared.
In several online chats in late 2023 on Discord, IRDev lamented being lured into a law enforcement sting operation after trying to buy a rocket launcher online. A person close to the investigation confirmed that at the beginning of 2023, IRDev began making earnest inquiries about how to purchase a Stinger, an American-made portable weapon that operates as an infrared surface-to-air missile.
Sources told KrebsOnSecurity Binns’ repeated efforts to purchase the projectile earned him multiple visits from the Turkish authorities, who were justifiably curious why he kept seeking to acquire such a powerful weapon.
A careful study of Judische’s postings on Telegram and Discord since 2019 shows this user is more widely known under the nickname “Waifu,” a moniker that corresponds to one of the more accomplished “SIM swappers” in the English-language cybercrime community over the years.
SIM swapping involves phishing, tricking or bribing mobile phone company employees for credentials needed to redirect a target’s mobile phone number to a device the attackers control — allowing thieves to intercept incoming text messages and phone calls.
Several SIM-swapping channels on Telegram maintain a frequently updated leaderboard of the 100 richest SIM-swappers, as well as the hacker handles associated with specific cybercrime groups (Waifu is ranked #24). That list has long included Waifu on a roster of hackers for a group that called itself “Beige.”
The term “Beige Group” came up in reporting on two stories published here in 2020. The first was in an August 2020 piece called Voice Phishers Targeting Corporate VPNs, which warned that the COVID-19 epidemic had brought a wave of targeted voice phishing attacks that tried to trick work-at-home employees into providing access to their employers’ networks. Frequent targets of the Beige group included employees at numerous top U.S. banks, ISPs, and mobile phone providers.
The second time Beige Group was mentioned by sources was in reporting on a breach at the domain registrar GoDaddy. In November 2020, intruders thought to be associated with the Beige Group tricked a GoDaddy employee into installing malicious software, and with that access they were able to redirect the web and email traffic for multiple cryptocurrency trading platforms. Other frequent targets of the Beige group included employees at numerous top U.S. banks, ISPs, and mobile phone providers.
Judische’s various Telegram identities have long claimed involvement in the 2020 GoDaddy breach, and he didn’t deny his alleged role when asked directly. Judische said he prefers voice phishing or “vishing” attacks that result in the target installing data-stealing malware, as opposed to tricking the user into entering their username, password and one-time code.
“Most of my ops involve malware [because] credential access burns too fast,” Judische explained.
The Telegram channels that the Judische/Waifu accounts frequented over the years show this user divided their time between posting in channels dedicated to financial cybercrime, and harassing and stalking others in harm communities like Leak Society and Court.
Both of these Telegram communities are known for victimizing children through coordinated online campaigns of extortion, doxing, swatting and harassment. People affiliated with harm groups like Court and Leak Society will often recruit new members by lurking on gaming platforms, social media sites and mobile applications that are popular with young people, including Discord, Minecraft, Roblox, Steam, Telegram, and Twitch.
“This type of offence usually starts with a direct message through gaming platforms and can move to more private chatrooms on other virtual platforms, typically one with video enabled features, where the conversation quickly becomes sexualized or violent,” warns a recent alert from the Royal Canadian Mounted Police (RCMP) about the rise of sextortion groups on social media channels.
“One of the tactics being used by these actors is sextortion, however, they are not using it to extract money or for sexual gratification,” the RCMP continued. “Instead they use it to further manipulate and control victims to produce more harmful and violent content as part of their ideological objectives and radicalization pathway.”
Some of the largest such known groups include those that go by the names 764, CVLT, Kaskar, 7997, 8884, 2992, 6996, 555, Slit Town, 545, 404, NMK, 303, and H3ll.
On the various cybercrime-oriented channels Judische frequented, he often lied about his or others’ involvement in various breaches. But Judische also at times shared nuggets of truth about his past, particularly when discussing the early history and membership of specific Telegram- and Discord-based cybercrime and harm groups.
Judische claimed in multiple chats, including on Leak Society and Court, that they were an early member of the Atomwaffen Division (AWD), a white supremacy group whose members are suspected of having committed multiple murders in the U.S. since 2017.
In 2019, KrebsOnSecurity exposed how a loose-knit group of neo-Nazis, some of whom were affiliated with AWD, had doxed and/or swatted nearly three dozen journalists at a range of media publications. Swatting involves communicating a false police report of a bomb threat or hostage situation and tricking authorities into sending a heavily armed police response to a targeted address.
Judsiche also told a fellow denizen of Court that years ago he was active in an older harm community called “RapeLash,” a truly vile Discord server known for attracting Atomwaffen members. A 2018 retrospective on RapeLash posted to the now defunct neo-Nazi forum Fascist Forge explains that RapeLash was awash in gory, violent images and child pornography.
A Fascist Forge member named “Huddy” recalled that RapeLash was the third incarnation of an extremist community also known as “FashWave,” short for Fascist Wave.
“I have no real knowledge of what happened with the intermediary phase known as ‘FashWave 2.0,’ but FashWave 3.0 houses multiple known Satanists and other degenerates connected with AWD, one of which got arrested on possession of child pornography charges, last I heard,” Huddy shared.
In June 2024, a Mandiant employee told Bloomberg that UNC5537 members have made death threats against cybersecurity experts investigating the hackers, and that in one case the group used artificial intelligence to create fake nude photos of a researcher to harass them.
Allison Nixon is chief research officer with the New York-based cybersecurity firm Unit 221B. Nixon is among several researchers who have faced harassment and specific threats of physical violence from Judische.
Nixon said Judische is likely to argue in court that his self-described psychological disorder(s) should somehow excuse his long career in cybercrime and in harming others.
“They ran a misinformation campaign in a sloppy attempt to cover up the hacking campaign,” Nixon said of Judische. “Coverups are an acknowledgment of guilt, which will undermine a mental illness defense in court. We expect that violent hackers from the [cybercrime community] will experience increasingly harsh sentences as the crackdown continues.”
5:34 p.m. ET: Updated story to include a clarification from Mandiant. Corrected Moucka’s age.
Nov. 21, 2024: Included link to a criminal indictment against Moucka and Binns.
The parents of a 19-year-old Connecticut honors student accused of taking part in a $243 million cryptocurrency heist in August were carjacked a week later — while out house-hunting in a brand new Lamborghini. Prosecutors say the couple was beaten and briefly kidnapped by six young men who traveled from Florida as part of a botched plan to hold the parents for ransom.

Image: ABC7NY. youtube.com/watch?v=xoiaGzwrunY
Late in the afternoon of Aug. 25, 2024 in Danbury, Ct., a married couple in their 50s pulled up to a gated community in a new Lamborghini Urus (investigators say the sports car still had temporary tags) when they were intentionally rear-ended by a Honda Civic.
A witness told police they saw three men exit a van that was following the Honda, and said the men began assaulting the couple and forcing them into the van. Local police officers spotted the van speeding from the scene and pursued it, only to find the vehicle crashed and abandoned a short distance away.
Inside the disabled van the police found the couple with their hands and feet bound in duct tape, the man visibly bruised after being assaulted with a baseball bat. Danbury police soon reported arresting six suspects in the kidnapping, all men aged 18-26 from Florida. They also recovered the abandoned Lamborghini from a wooded area.
A criminal complaint (PDF) filed on Sept. 24 against the six men does not name the victims, referring to them only as a married couple from Danbury with the initials R.C. and S.C. But prosecutors in Connecticut said they were targeted “because the co-conspirators believed the victims’ son had access to significant amounts of digital currency.”
What made the Miami men so convinced R.C. and S.C.’s son was loaded with cryptocurrency? Approximately one week earlier, on Aug. 19, a group of cybercriminals that allegedly included the couple’s son executed a sophisticated phone-based social engineering attack in which they stole $243 million worth of cryptocurrency from a victim in Washington, D.C.
That’s according to ZachXBT, a frequently cited crypto crime investigator who published a lengthy thread that broke down how the theft was carried out and ultimately exposed by the perpetrators themselves.
ZachXBT’s post included a screen recording of a Discord chat session made by one of the participants to the $243 million robbery, noting that two of the people involved managed to leak the username of the Microsoft Windows PCs they were using to participate in the chat.
One of the usernames leaked during the chat was Veer Chetal. According to ZachXBT, that name corresponds to a 19-year-old from Danbury who allegedly goes by the nickname “Wiz,” although in the leaked video footage he allegedly used the handle “Swag.” Swag was reportedly involved in executing the early stages of the crypto heist — gaining access to the victim’s Gmail and iCloud accounts.
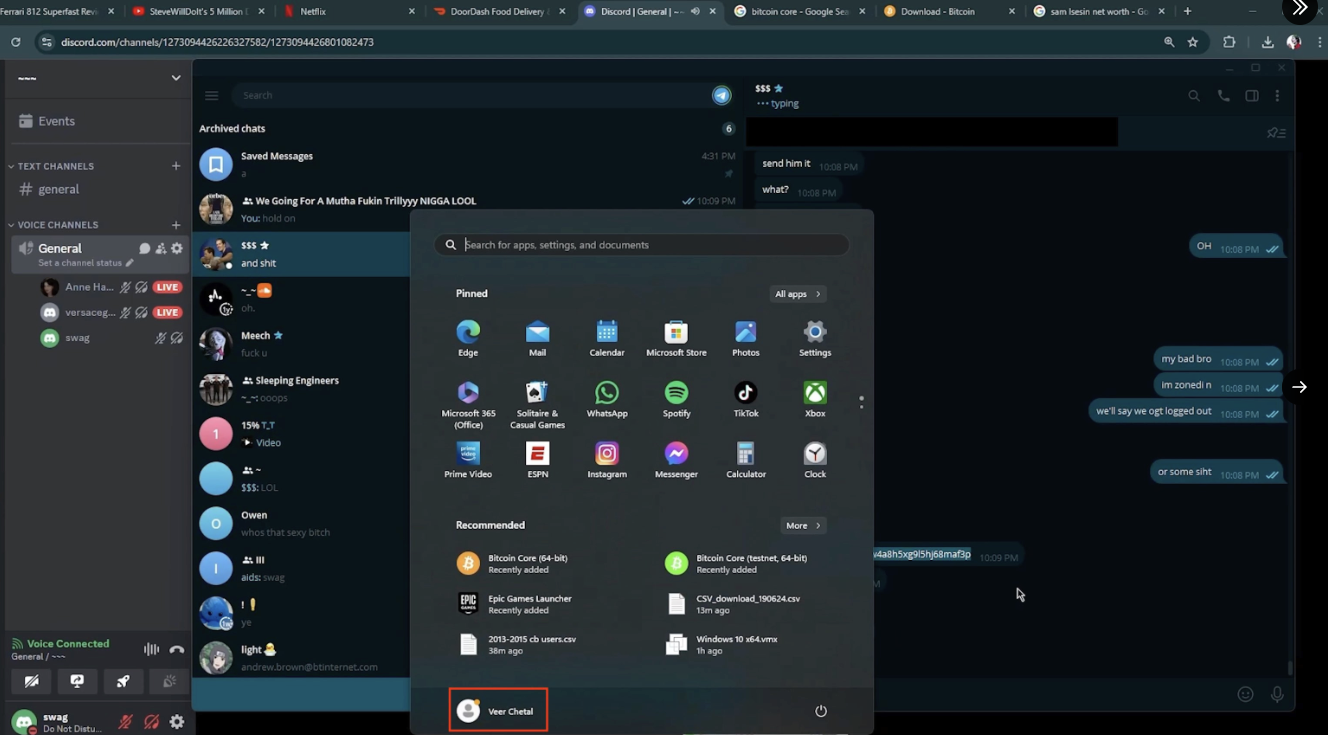
A still shot from a video screenshare in which one of the participants on the Discord voice chat used the Windows username Veer Chetal. Image: x.com/zachxbt
The same day ZachXBT published his findings, a criminal indictment was issued in Washington D.C. charging two of the men he named as involved in the heist. Prosecutors allege Malone “Greavys” Lam, 20, of Miami and Los Angeles, and Jeandiel “Box” Serrano, 21, of Los Angeles conspired to steal and launder over $230 million in cryptocurrency from a victim in Washington, D.C. The indictment alleges Lam and Serrano were helped by other unnamed co-conspirators.
“Lam and Serrano then allegedly spent the laundered cryptocurrency proceeds on international travel, nightclubs, luxury automobiles, watches, jewelry, designer handbags, and rental homes in Los Angeles and Miami,” reads a press release from the U.S. Department of Justice.
By tracing the flow of funds stolen in the heist, ZachXBT concluded that Wiz received a large percentage from the theft, noting that “additional comfort [in naming him as involved] was gained as throughout multiple recordings accomplices refer to him as ‘Veer’ on audio and in chats.”
“A cluster of [cryptocurrency] addresses tied to both Box/Wiz received $41M+ from two exchanges over the past few weeks primarily flowing to luxury goods brokers to purchase cars, watches, jewelry, and designer clothes,” ZachXBT wrote.
KrebsOnSecurity sought comment from Veer Chetal, and from his parents — Radhika Chetal and Suchil Chetal. This story will be updated in the event that anyone representing the Chetal family responds. Veer Chetal has not been publicly charged with any crime.
According to a news brief published by a private Catholic high school in Danbury that Veer Chetal attended, in 2022 he successfully completed Harvard’s Future Lawyers Program, a “unique pre-professional program where students, guided by qualified Harvard undergraduate instructors, learn how to read and build a case, how to write position papers, and how to navigate a path to law school.” A November 2022 story at patch.com quoted Veer Chetal (class of 2024) crediting the Harvard program with his decision to pursue a career in law.
It remains unclear which Chetal family member acquired the 2023 Lamborghini Urus, which has a starting price of around $233,000. Sushil Chetal’s LinkedIn profile says he is a vice president at the investment bank Morgan Stanley.
It is clear that other alleged co-conspirators to the $243 million heist displayed a conspicuous consumption of wealth following the date of the heist. ZachXBT’s post chronicled Malone’s flashy lifestyle, in which he allegedly used the stolen money to purchase more than 10 vehicles, rent palatial properties, travel with friends on chartered jets, and spend between $250,000 and $500,000 a night at clubs in Los Angeles and Miami.
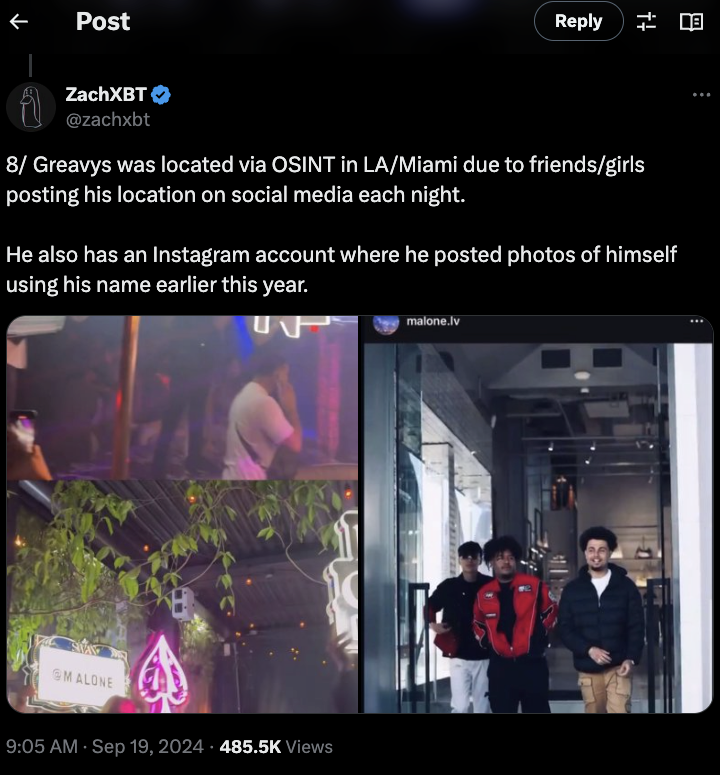
In the photo on the bottom right, Greavys/Lam is the individual on the left wearing shades. They are pictured leaving a luxury goods store. Image: x.com/zachxbt
WSVN-TV in Miami covered an FBI raid of a large rented waterfront home around the time Malone and Serrano were arrested. The news station interviewed a neighbor of the home’s occupants, who reported a recent large party at the residence wherein the street was lined with high-end luxury vehicles — all of them with temporary paper tags.
ZachXBT unearthed a video showing a person identified as Wiz at a Miami nightclub earlier this year, wherein they could be seen dancing to the crowd’s chants while holding an illuminated sign with the message, “I win it all.”
It appears that all of the suspects in the cyber heist (and at least some of the alleged carjackers) are members of The Com, an archipelago of crime-focused chat communities which collectively functions as a kind of distributed cybercriminal social network that facilitates instant collaboration.
As documented in last month’s deep dive on top Com members, The Com is also a place where cybercriminals go to boast about their exploits and standing within the community, or to knock others down a peg or two. Prominent Com members are endlessly sniping over who pulled off the most impressive heists, or who has accumulated the biggest pile of stolen virtual currencies.
And as often as they extort and rob victims for financial gain, members of The Com are trying to wrest stolen money from their cybercriminal rivals — often in ways that spill over into physical violence in the real world.
One of the six Miami-area men arrested in the carjacking and extortion plot gone awry — Reynaldo “Rey” Diaz — was shot twice while parked in his bright yellow Corvette in Miami’s design district in 2022. In an interview with a local NBC television station, Diaz said he was probably targeted for the jewelry he was wearing, which he described as “pretty expensive.”
KrebsOnSecurity has learned Diaz also went by the alias “Pantic” on Telegram chat channels dedicated to stealing cryptocurrencies. Pantic was known for participating in several much smaller cyber heists in the past, and spending most of his cut on designer clothes and jewelry.
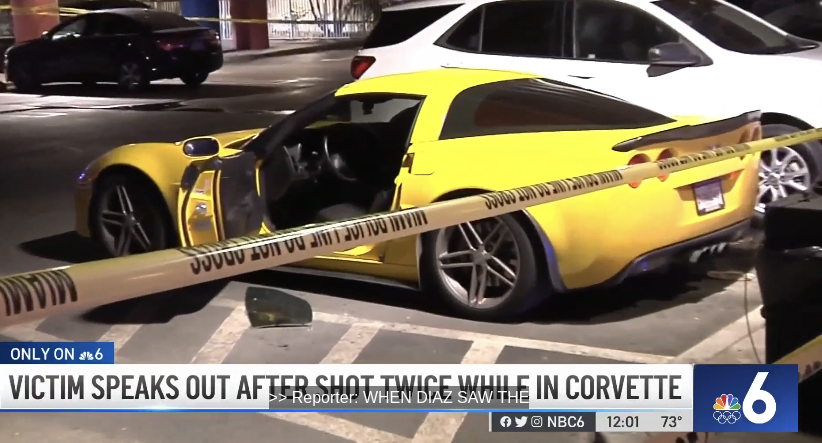
The Corvette that Diaz was sitting in when he was shot in 2022. Image: NBC 6, South Florida.
Earlier this year, Diaz was “doxed,” or publicly outed as Pantic, with his personal and family information posted on a harassment and extortion channel frequented by members of The Com. The reason cited for Pantic’s doxing was widely corroborated by multiple Com members: Pantic had inexplicably robbed two close friends at gunpoint, one of whom recently died of a drug overdose.
Government prosecutors say the brazen daylight carjacking was paid for and organized by 23-year-old Miami resident Angel “Chi Chi” Borrero. In 2022, Borrero was arrested in Miami for aggravated assault with a deadly weapon.
The six Miami men face charges including first-degree assault, kidnapping and reckless endangerment, and five of them are being held on a $1 million bond. One suspect is also charged with reckless driving, engaging police in pursuit and evading responsibility; his bond was set at $2 million. Lam and Serrano are each charged with conspiracy to commit wire fraud and conspiracy to launder money.
Cybercriminals hail from all walks of life and income levels, but some of the more accomplished cryptocurrency thieves also tend to be among the more privileged, and from relatively well-off families. In other words, these individuals aren’t stealing to put food on the table: They’re doing it so they can amass all the trappings of instant wealth, and so they can boast about their crimes to others on The Com.
There is also a penchant among this crowd to call attention to their activities in conspicuous ways that hasten their arrest and criminal charging. In many ways, the story arc of the young men allegedly involved in the $243 million heist tracks closely to that of Joel Ortiz, a valedictorian who was sentenced in 2019 to 10 years in prison for stealing more than $5 million in cryptocurrencies.
Ortiz famously posted videos of himself and co-conspirators chartering flights and partying it up at LA nightclubs, with scantily clad women waving giant placards bearing their “OG” usernames — highly-prized, single-letter social media accounts that they’d stolen or purchased stolen from others.
Ortiz earned the distinction of being the first person convicted of SIM-swapping, a crime that involves using mobile phone company insiders or compromised employee accounts to transfer a target’s phone number to a mobile device controlled by the attackers. From there, the attacker can intercept any password reset links, and any one-time passcodes sent via SMS or automated voice calls.
But as the mobile carriers seek to make their networks less hospitable to SIM-swappers, and as more financial platforms seek to harden user account security, today’s crypto thieves are finding they don’t need SIM-swaps to steal obscene amounts of cryptocurrency. Not when tricking people over the phone remains such an effective approach.
According to ZachXBT, the crooks responsible for the $243 million theft initially compromised the target’s personal accounts after calling them as Google Support and using a spoofed number. The attackers also spoofed a call from account support representatives at the cryptocurrency exchange Gemini, claiming the target’s account had been hacked.
From there the target was social engineered over the phone into resetting multi-factor authentication and sending Gemini funds to a compromised wallet. ZachXBT says the attackers also convinced the victim to use AnyDesk to share their screen, and in doing so the victim leaked their private keys.
A California man accused of failing to pay taxes on tens of millions of dollars allegedly earned from cybercrime also paid local police officers hundreds of thousands of dollars to help him extort, intimidate and silence rivals and former business partners, the government alleges. KrebsOnSecurity has learned that many of the man’s alleged targets were members of UGNazi, a hacker group behind multiple high-profile breaches and cyberattacks back in 2012.

A photo released by the government allegedly showing Iza posing with several LASD officers on his payroll.
A federal complaint (PDF) filed last week said the Federal Bureau of Investigation (FBI) has been investigating Los Angeles resident Adam Iza. Also known as “Assad Faiq” and “The Godfather,” Iza is the founder of a cryptocurrency investment platform called Zort that advertised the ability to make smart trades based on artificial intelligence technology.
But the feds say investors in Zort soon lost their shorts, after Iza and his girlfriend began spending those investments on Lamborghinis, expensive jewelry, vacations, a $28 million home in Bel Air, even cosmetic surgery to extend the length of his legs.
The complaint states the FBI started looking at Iza after receiving multiple reports that he had on his payroll several active deputies with the Los Angeles Sheriff’s Department (LASD). Iza’s attorney did not immediately respond to requests for comment.
The complaint cites a letter from an attorney for a victim referenced only as “E.Z.,” who was seeking help related to an extortion and robbery allegedly committed by Iza. The government says that in March 2022, three men showed up at E.Z.’s home, and tried to steal his laptop in an effort to gain access to E.Z. cryptocurrency holdings online. A police report referenced in the complaint says three intruders were scared off when E.Z. fired several handgun rounds in the direction of his assailants.
The FBI later obtained a copy of a search warrant executed by LASD deputies in January 2022 for GPS location information on a phone belonging to E.Z., which shows an LASD deputy unlawfully added E.Z.’s mobile number to a list of those associated with an unrelated firearms investigation.
“Damn my guy actually filed the warrant,” Iza allegedly texted someone after the location warrant was entered. “That’s some serious shit to do for someone….risking a 24 years career. I pay him 280k a month for complete resources. They’re active-duty.”
The FBI alleges LASD officers had on several previous occasions tried to kidnap and extort E.Z. at Iza’s behest. The complaint references a November 2021 incident wherein Iza and E.Z. were in a car together when Iza asked to stop and get snacks at a convenience store. While they were still standing next to the car, a van with several armed LASD deputies showed up and tried to force E.Z. to hand over his phone. E.Z. escaped unharmed, and alerted 911.
E.Z. appears to be short for Enzo Zelocchi, a self-described “actor” who was featured in an ABC News story about a home invasion in Los Angeles around that same time as the March 2022 home invasion, in which Zelocchi is quoted as saying at least two men tried to rob him at gunpoint (we’ll revisit Zelocchi’s acting credits in a moment).

One of many self portraits published on the Instagram account of Enzo Zelocchi.
The criminal complaint makes frequent references to a co-conspirator of Iza (“CC-1”) — his girlfriend at the time — who allegedly helped Iza run his businesses and spend the millions plunked down by Zort investors. We know what E.Z. stands for because Iza’s girlfriend then was a woman named Iris Au, and in November 2022 she sued Zelocchi for allegedly stealing Iza’s laptop.
The complaint says Iza also harassed a man identified only as T.W., and refers to T.W. as one of two Americans currently incarcerated in the Philippines for murder. In December 2018, a then 21-year-old Troy Woody Jr. was arrested in Manila after he was spotted dumping the body of his dead girlfriend Tomi Masters into a local river.
Woody is accused of murdering Masters with the help of his best friend and roommate at the time: Mir Islam, a.k.a. “JoshTheGod,” referred to in the Iza complaint as “M.I.” Islam and Woody were both core members of UGNazi, a hacker collective that sprang up in 2012 and claimed credit for hacking and attacking a number of high-profile websites.
In June 2016, Islam was sentenced to a year in prison for an impressive array of crimes, including stalking people online and posting their personal data on the Internet. Islam also pleaded guilty to reporting dozens of phony bomb threats and fake hostage situations at the homes of celebrities and public officials (Islam participated in a swatting attack against this author in 2013).

Troy Woody Jr. (left) and Mir Islam, are currently in prison in the Philippines for murder.
In December 2022, Troy Woody Jr. sued Iza, Zelocchi and Zort, alleging (PDF) Iza and Zelocchi were involved in a 2018 home invasion at his residence, wherein Woody claimed his assailants stole laptops and phones containing more than $200 million in cryptocurrencies.
Woody’s complaint states that Masters also was present during his 2018 home invasion, as was another core UGNazi member: Eric “CosmoTheGod” Taylor. CosmoTheGod rocketed to Internet infamy in 2013 when he and a number of other hackers set up the Web site exposed[dot]su, which published the address, Social Security numbers and other personal information of public figures, including the former First Lady Michelle Obama, the then-director of the FBI and the U.S. attorney general. The group also swatted many of the people they doxed.
Exposed was built with the help of identity information obtained and/or stolen from ssndob dot ru.
In 2017, Taylor was sentenced to three years probation for participating in multiple swatting attacks, including the one against my home in 2013.
The complaint against Iza says the FBI interviewed Woody in Manila where he is currently incarcerated, and learned that Iza has been harassing him about passwords that would unlock access to cryptocurrencies. The FBI’s complaint leaves open the question of how Woody and Islam got the phones in the first place, but the implication is that Iza may have instigated the harassment by having mobile phones smuggled to the prisoners.
The government suggests its case against Iza was made possible in part thanks to Iza’s propensity for ripping off people who worked for him. The complaint cites information provided by a private investigator identified only as “K.C.,” who said Iza hired him to surveil Zelocchi but ultimately refused to pay him for much of the work.
K.C. stands for Kenneth Childs, who in 2022 sued Iris Au and Zort (PDF) for theft by deception and commercial disparagement, after it became clear his private eye services were being used as part of a scheme by the Zort founders to intimidate and extort others. Childs’ complaint says Iza clawed back tens of thousands of dollars in payments he’d previously made as part of their contract.
The government also included evidence provided by an associate of Iza’s — named only as “R.C.” — who was hired to throw a party at Iza’s home. According to the feds, Iza paid the associate $50,000 to craft the event to his liking, but on the day of the party Iza allegedly told R.C. he was unhappy with the event and demanded half of his money back.
When R.C. balked, Iza allegedly surrounded the man with armed LASD officers, who then extracted the payment by seizing his phone. The government says Iza kept R.C.’s phone and spent the remainder of his bank balance.
A photo Iza allegedly sent to Tassilo Heinrich immediately after Heinrich’s arrest on unsubstantiated drug charges.
The FBI said that after the incident at the party, Iza had his bribed sheriff deputies pull R.C. over and arrest him on phony drug charges. The complaint includes a photo of R.C. being handcuffed by the police, which the feds say Iza sent to R.C. in order to intimidate him even further. The drug charges were later dismissed for lack of evidence.
The government alleges Iza and Au paid the LASD officers using Zelle transfers from accounts tied to two different entities incorporated by one or both of them: Dream Agency and Rise Agency. The complaint further alleges that these two entities were the beneficiaries of a business that sold hacked and phished Facebook advertising accounts, and bribed Facebook employees to unblock ads that violated its terms of service.
The complaint says Iza ran this business with another individual identified only as “T.H.,” and that at some point T.H. had personal problems and checked himself into rehab. T.H. told the FBI that Iza responded by stealing his laptop and turning him in to the government.
KrebsOnSecurity has learned that T.H. in this case is Tassilo Heinrich, a man indicted in 2022 for hacking into the e-commerce platform Shopify, and leaking the user database for Ledger, a company that makes hardware wallets for storing cryptocurrencies.
Heinrich pleaded guilty and was sentenced to time served, three years of supervised release, and ordered to pay restitution to Shopify. Upon his release from custody, Heinrich told the FBI that Iza was still using his account at the public screenshot service Gyazo to document communications regarding his alleged bribing of LASD officers.
Prosecutors say Iza and Au portrayed themselves as glamorous and wealthy individuals who were successful social media influencers, but that most of that was a carefully crafted facade designed to attract investment from cryptocurrency enthusiasts. Meanwhile, the U.K. tabloids reported this summer that Au was dating Davide Sanclimenti, the 2022 co-winner on the dating reality show Love Island.

Au was featured on the July 2024 cover of “Womenpreneur Middle East.”
Recall that we promised to revisit Mr. Zelocchi’s claimed acting credits. Despite being briefly listed on the Internet Movie Data Base (imdb.com) as the most awarded science fiction actor of all time, it’s not clear whether Mr. Zelocchi has starred in any real movies.
Earlier this year, an Internet sleuth on Youtube showed that even though Zelocchi’s IMDB profile has him earning more awards than most other actors on the platform (here he is holding a Youtube top viewership award), Zelocchi is probably better known as the director of the movie once rated the absolute worst sci-fi flick on IMDB: A 2015 work called “Angel’s Apocalypse.” Most of the videos on Zelocchi’s Instagram page appear to be brief clips, some of which look more like a commercial for men’s cologne than scenes from a real movie.
A Reddit post from a year ago calling attention to Zelocchi’s sci-fi film Angel’s Apocalypse somehow earning more audience votes than any other movie in the same genre.
In many ways, the crimes described in this complaint and the various related civil lawsuits would prefigure a disturbing new trend within English-speaking cybercrime communities that has bubbled up in the past few years: The emergence of “violence-as-as-service” offerings that allow cybercriminals to anonymously extort and intimidate their rivals.
Found on certain Telegram channels are solicitations for IRL or “In Real Life” jobs, wherein people hire themselves out as willing to commit a variety of physical attacks in their local geographic area, such as slashing tires, firebombing a home, or tossing a brick through someone’s window.
Many of the cybercriminals in this community have stolen tens of millions of dollars worth of cryptocurrency, and can easily afford to bribe police officers. KrebsOnSecurity would expect to see more of this in the future as young, crypto-rich cybercriminals seek to corrupt people in authority to their advantage.
The Damn Vulnerable Drone is an intentionally vulnerable drone hacking simulator based on the popular ArduPilot/MAVLink architecture, providing a realistic environment for hands-on drone hacking.
The Damn Vulnerable Drone is a virtually simulated environment designed for offensive security professionals to safely learn and practice drone hacking techniques. It simulates real-world ArduPilot & MAVLink drone architectures and vulnerabilities, offering a hands-on experience in exploiting drone systems.
The Damn Vulnerable Drone aims to enhance offensive security skills within a controlled environment, making it an invaluable tool for intermediate-level security professionals, pentesters, and hacking enthusiasts.
Similar to how pilots utilize flight simulators for training, we can use the Damn Vulnerable Drone simulator to gain in-depth knowledge of real-world drone systems, understand their vulnerabilities, and learn effective methods to exploit them.
The Damn Vulnerable Drone platform is open-source and available at no cost and was specifically designed to address the substantial expenses often linked with drone hardware, hacking tools, and maintenance. Its cost-free nature allows users to immerse themselves in drone hacking without financial concerns. This accessibility makes the Damn Vulnerable Drone a crucial resource for those in the fields of information security and penetration testing, promoting the development of offensive cybersecurity skills in a safe environment.
The Damn Vulnerable Drone platform operates on the principle of Software-in-the-Loop (SITL), a simulation technique that allows users to run drone software as if it were executing on an actual drone, thereby replicating authentic drone behaviors and responses.
ArduPilot's SITL allows for the execution of the drone's firmware within a virtual environment, mimicking the behavior of a real drone without the need for physical hardware. This simulation is further enhanced with Gazebo, a dynamic 3D robotics simulator, which provides a realistic environment and physics engine for the drone to interact with. Together, ArduPilot's SITL and Gazebo lay the foundation for a sophisticated and authentic drone simulation experience.
While the current Damn Vulnerable Drone setup doesn't mirror every drone architecture or configuration, the integrated tactics, techniques and scenarios are broadly applicable across various drone systems, models and communication protocols.
A cyberattack that shut down two of the top casinos in Las Vegas last year quickly became one of the most riveting security stories of 2023. It was the first known case of native English-speaking hackers in the United States and Britain teaming up with ransomware gangs based in Russia. But that made-for-Hollywood narrative has eclipsed a far more hideous trend: Many of these young, Western cybercriminals are also members of fast-growing online groups that exist solely to bully, stalk, harass and extort vulnerable teens into physically harming themselves and others.

Image: Shutterstock.
In September 2023, a Russian ransomware group known as ALPHV/Black Cat claimed credit for an intrusion at the MGM Resorts hotel chain that quickly brought MGM’s casinos in Las Vegas to a standstill. While MGM was still trying to evict the intruders from its systems, an individual who claimed to have firsthand knowledge of the hack contacted multiple media outlets to offer interviews about how it all went down.
One account of the hack came from a 17-year-old in the United Kingdom, who told reporters the intrusion began when one of the English-speaking hackers phoned a tech support person at MGM and tricked them into resetting the password for an employee account.
The security firm CrowdStrike dubbed the group “Scattered Spider,” a recognition that the MGM hackers came from different cliques scattered across an ocean of Telegram and Discord servers dedicated to financially-oriented cybercrime.
Collectively, this archipelago of crime-focused chat communities is known as “The Com,” and it functions as a kind of distributed cybercriminal social network that facilitates instant collaboration.
But mostly, The Com is a place where cybercriminals go to boast about their exploits and standing within the community, or to knock others down a peg or two. Top Com members are constantly sniping over who pulled off the most impressive heists, or who has accumulated the biggest pile of stolen virtual currencies.
And as often as they extort victim companies for financial gain, members of The Com are trying to wrest stolen money from their cybercriminal rivals — often in ways that spill over into physical violence in the real world.
CrowdStrike would go on to produce and sell Scattered Spider action figures, and it featured a life-sized Scattered Spider sculpture at this year’s RSA Security Conference in San Francisco.
But marketing security products and services based on specific cybercriminal groups can be tricky, particularly if it turns out that robbing and extorting victims is by no means the most abhorrent activity those groups engage in on a daily basis.
KrebsOnSecurity examined the Telegram user ID number of the account that offered media interviews about the MGM hack — which corresponds to the screen name “@Holy” — and found the same account was used across a number of cybercrime channels that are entirely focused on extorting young people into harming themselves or others, and recording the harm on video.
Holy was known to possess multiple prized Telegram usernames, including @bomb, @halo, and @cute, as well as one of the highest-priced Telegram usernames ever put up for sale: @nazi.
In one post on a Telegram channel dedicated to youth extortion, this same user can be seen asking if anyone knows the current Telegram handles for several core members of 764, an extremist group known for victimizing children through coordinated online campaigns of extortion, doxing, swatting and harassment.
People affiliated with harm groups like 764 will often recruit new members by lurking on gaming platforms, social media sites and mobile applications that are popular with young people, including Discord, Minecraft, Roblox, Steam, Telegram, and Twitch.
“This type of offence usually starts with a direct message through gaming platforms and can move to more private chatrooms on other virtual platforms, typically one with video enabled features, where the conversation quickly becomes sexualized or violent,” warns a recent alert from the Royal Canadian Mounted Police (RCMP) about the rise of sextortion groups on social media channels.
“One of the tactics being used by these actors is sextortion, however, they are not using it to extract money or for sexual gratification,” the RCMP continued. “Instead they use it to further manipulate and control victims to produce more harmful and violent content as part of their ideological objectives and radicalization pathway.”
The 764 network is among the most populated harm communities, but there are plenty more. Some of the largest such known groups include CVLT, Court, Kaskar, Leak Society, 7997, 8884, 2992, 6996, 555, Slit Town, 545, 404, NMK, 303, and H3ll.
In March, a consortium of reporters from Wired, Der Spiegel, Recorder and The Washington Post examined millions of messages across more than 50 Discord and Telegram chat groups.
“The abuse perpetrated by members of com groups is extreme,” Wired’s Ali Winston wrote. “They have coerced children into sexual abuse or self-harm, causing them to deeply lacerate their bodies to carve ‘cutsigns’ of an abuser’s online alias into their skin.” The story continues:
“Victims have flushed their heads in toilets, attacked their siblings, killed their pets, and in some extreme instances, attempted or died by suicide. Court records from the United States and European nations reveal participants in this network have also been accused of robberies, in-person sexual abuse of minors, kidnapping, weapons violations, swatting, and murder.”
“Some members of the network extort children for sexual pleasure, some for power and control. Some do it merely for the kick that comes from manipulation. Others sell the explicit CSAM content produced by extortion on the dark web.”
KrebsOnSecurity has learned Holy is the 17-year-old who was arrested in July 2024 by the U.K.’s West Midlands Police as part of a joint investigation with the FBI into the MGM hack.
Early in their cybercriminal career (as a 15-year-old), @Holy went by the handle “Vsphere,” and was a proud member of the LAPSUS$ cybercrime group. Throughout 2022, LAPSUS$ would hack and social engineer their way into some of the world’s biggest technology companies, including EA Games, Microsoft, NVIDIA, Okta, Samsung, and T-Mobile.
Another timely example of the overlap between harm communities and top members of The Com can be found in a group of criminals who recently stole obscene amounts of customer records from users of the cloud data provider Snowflake.
At the end of 2023, malicious hackers figured out that many major companies have uploaded massive amounts of valuable and sensitive customer data to Snowflake servers, all the while protecting those Snowflake accounts with little more than a username and password (no multi-factor authentication required). The group then searched darknet markets for stolen Snowflake account credentials, and began raiding the data storage repositories used by some of the world’s largest corporations.
Among those that had data exposed in Snowflake was AT&T, which disclosed in July that cybercriminals had stolen personal information and phone and text message records for roughly 110 million people — nearly all its customers.
A report on the extortion group from the incident response firm Mandiant notes that Snowflake victim companies were privately approached by the hackers, who demanded a ransom in exchange for a promise not to sell or leak the stolen data. All told, more than 160 organizations were extorted, including TicketMaster, Lending Tree, Advance Auto Parts and Neiman Marcus.
On May 2, 2024, a user by the name “Judische” claimed on the fraud-focused Telegram channel Star Chat that they had hacked Santander Bank, one of the first known Snowflake victims. Judische would repeat that claim in Star Chat on May 13 — the day before Santander publicly disclosed a data breach — and would periodically blurt out the names of other Snowflake victims before their data even went up for sale on the cybercrime forums.
A careful review of Judische’s account history and postings on Telegram shows this user is more widely known under the nickname “Waifu,” an early moniker that corresponds to one of the more accomplished SIM-swappers in The Com over the years.
In a SIM-swapping attack, the fraudsters will phish or purchase credentials for mobile phone company employees, and use those credentials to redirect a target’s mobile calls and text messages to a device the attackers control.
Several channels on Telegram maintain a frequently updated leaderboard of the 100 richest SIM-swappers, as well as the hacker handles associated with specific cybercrime groups (Waifu is ranked #24). That leaderboard has long included Waifu on a roster of hackers for a group that called itself “Beige.”
Beige members were implicated in two stories published here in 2020. The first was an August 2020 piece called Voice Phishers Targeting Corporate VPNs, which warned that the COVID-19 epidemic had brought a wave of voice phishing or “vishing” attacks that targeted work-from-home employees via their mobile devices, and tricked many of those people into giving up credentials needed to access their employer’s network remotely.
Beige group members also have claimed credit for a breach at the domain registrar GoDaddy. In November 2020, intruders thought to be associated with the Beige Group tricked a GoDaddy employee into installing malicious software, and with that access they were able to redirect the web and email traffic for multiple cryptocurrency trading platforms.
The Telegram channels that Judische and his related accounts frequented over the years show this user divides their time between posting in SIM-swapping and cybercrime cashout channels, and harassing and stalking others in harm communities like Leak Society and Court.
Mandiant has attributed the Snowflake compromises to a group it calls “UNC5537,” with members based in North America and Turkey. KrebsOnSecurity has learned Judische is a 26-year-old software engineer in Ontario, Canada.
Sources close to the investigation into the Snowflake incident tell KrebsOnSecurity the UNC5537 member in Turkey is John Erin Binns, an elusive American man indicted by the U.S. Department of Justice (DOJ) for a 2021 breach at T-Mobile that exposed the personal information of at least 76.6 million customers.
Binns is currently in custody in a Turkish prison and fighting his extradition. Meanwhile, he has been suing almost every federal agency and agent that contributed investigative resources to his case.
In June 2024, a Mandiant employee told Bloomberg that UNC5537 members have made death threats against cybersecurity experts investigating the hackers, and that in one case the group used artificial intelligence to create fake nude photos of a researcher to harass them.
In June 2024, two American men pleaded guilty to hacking into a U.S. Drug Enforcement Agency (DEA) online portal that tapped into 16 different federal law enforcement databases. Sagar “Weep” Singh, a 20-year-old from Rhode Island, and Nicholas “Convict” Ceraolo, 25, of Queens, NY, were both active in SIM-swapping communities.
Singh and Ceraolo hacked into a number of foreign police department email accounts, and used them to make phony “emergency data requests” to social media platforms seeking account information about specific users they were stalking. According to the government, in each case the men impersonating the foreign police departments told those platforms the request was urgent because the account holders had been trading in child pornography or engaging in child extortion.
Eventually, the two men formed part of a group of cybercriminals known to its members as “ViLE,” who specialize in obtaining personal information about third-party victims, which they then used to harass, threaten or extort the victims, a practice known as “doxing.”
The U.S. government says Singh and Ceraolo worked closely with a third man — referenced in the indictment as co-conspirator #1 or “CC-1” — to administer a doxing forum where victims could pay to have their personal information removed.
The government doesn’t name CC-1 or the doxing forum, but CC-1’s hacker handle is “Kayte” (a.k.a. “KT“) which corresponds to the nickname of a 23-year-old man who lives with his parents in Coffs Harbor, Australia. For several years (with a brief interruption), KT has been the administrator of a truly vile doxing community known as the Doxbin.

A screenshot of the website for the cybercriminal group “ViLE.” Image: USDOJ.
People whose names and personal information appear on the Doxbin can quickly find themselves the target of extended harassment campaigns, account hacking, SIM-swapping and even swatting — which involves falsely reporting a violent incident at a target’s address to trick local police into responding with potentially deadly force.
A handful of Com members targeted by federal authorities have gone so far as to perpetrate swatting, doxing, and other harassment against the same federal agents who are trying to unravel their alleged crimes. This has led some investigators working cases involving the Com to begin redacting their names from affidavits and indictments filed in federal court.
In January 2024, KrebsOnSecurity broke the news that prosecutors in Florida had charged a 19-year-old alleged Scattered Spider member named Noah Michael Urban with wire fraud and identity theft. That story recounted how Urban’s alleged hacker identities “King Bob” and “Sosa” inhabited a world in which rival cryptocurrency theft rings frequently settled disputes through so-called “violence-as-a-service” offerings — hiring strangers online to perpetrate firebombings, beatings and kidnappings against their rivals.
Urban’s indictment shows the name of the federal agent who testified to it has been blacked out:
The final page of Noah Michael Urban’s indictment shows the investigating agent redacted their name from charging documents.
In June 2022, this blog told the story of two men charged with hacking into the Ring home security cameras of a dozen random people and then methodically swatting each of them. Adding insult to injury, the men used the compromised security cameras to record live footage of local police swarming those homes.

McCarty, in a mugshot.
James Thomas Andrew McCarty, Charlotte, N.C., and Kya “Chumlul” Nelson, of Racine, Wisc., conspired to hack into Yahoo email accounts belonging to victims in the United States. The two would check how many of those Yahoo accounts were associated with Ring accounts, and then target people who used the same password for both accounts.
The Telegram and Discord aliases allegedly used by McCarty — “Aspertaine” and “Couch,” among others — correspond to an identity that was active in certain channels dedicated to SIM-swapping.
What KrebsOnSecurity didn’t report at the time is that both ChumLul and Aspertaine were active members of CVLT, wherein those identities clearly participated in harassing and exploiting young teens online.
In June 2024, McCarty was sentenced to seven years in prison after pleading guilty to making hoax calls that elicited police SWAT responses. Nelson also pleaded guilty and received a seven-year prison sentence.
In March 2023, U.S. federal agents in New York announced they’d arrested “Pompompurin,” the alleged administrator of Breachforums, an English-language cybercrime forum where hacked corporate databases frequently appear for sale. In cases where the victim organization isn’t extorted in advance by hackers, being listed on Breachforums has often been the way many victims first learned of an intrusion.
Pompompurin had been a nemesis to the FBI for several years. In November 2021, KrebsOnSecurity broke the news that thousands of fake emails about a cybercrime investigation were blasted out from the FBI’s email systems and Internet addresses.
Pompompurin took credit for that stunt, and said he was able to send the FBI email blast by exploiting a flaw in an FBI portal designed to share information with state and local law enforcement authorities. The FBI later acknowledged that a software misconfiguration allowed someone to send the fake emails.
In December, 2022, KrebsOnSecurity detailed how hackers active on BreachForums had infiltrated the FBI’s InfraGard program, a vetted network designed to build cyber and physical threat information sharing partnerships with experts in the private sector. The hackers impersonated the CEO of a major financial company, applied for InfraGard membership in the CEO’s name, and were granted admission to the community.
The feds named Pompompurin as 21-year-old Peekskill resident Conor Brian Fitzpatrick, who was originally charged with one count of conspiracy to solicit individuals to sell unauthorized access devices (stolen usernames and passwords). But after FBI agents raided and searched the home where Fitzpatrick lived with his parents, prosecutors tacked on charges for possession of child pornography.
Recent actions by the DOJ indicate the government is well aware of the significant overlap between leading members of The Com and harm communities. But the government also is growing more sensitive to the criticism that it can often take months or years to gather enough evidence to criminally charge some of these suspects, during which time the perpetrators can abuse and recruit countless new victims.
Late last year, however, the DOJ signaled a new tactic in pursuing leaders of harm communities like 764: Charging them with domestic terrorism.
In December 2023, the government charged (PDF) a Hawaiian man with possessing and sharing sexually explicit videos and images of prepubescent children being abused. Prosecutors allege Kalana Limkin, 18, of Hilo, Hawaii, admitted he was an associate of CVLT and 764, and that he was the founder of a splinter harm group called Cultist. Limkin’s Telegram profile shows he also was active on the harm community Slit Town.
The relevant citation from Limkin’s complaint reads:
“Members of the group ‘764’ have conspired and continue to conspire in both online and in-person venues to engage in violent actions in furtherance of a Racially Motivated Violent Extremist ideology, wholly or in part through activities that violate federal criminal law meeting the statutory definition of Domestic Terrorism, defined in Title 18, United States Code, § 2331.”
Experts say charging harm groups under anti-terrorism statutes potentially gives the government access to more expedient investigative powers than it would normally have in a run-of-the-mill criminal hacking case.
“What it ultimately gets you is additional tools you can use in the investigation, possibly warrants and things like that,” said Mark Rasch, a former U.S. federal cybercrime prosecutor and now general counsel for the New York-based cybersecurity firm Unit 221B. “It can also get you additional remedies at the end of the case, like greater sanctions, more jail time, fines and forfeiture.”
But Rasch said this tactic can backfire on prosecutors who overplay their hand and go after someone who ends up challenging the charges in court.
“If you’re going to charge a hacker or pedophile with a crime like terrorism, that’s going to make it harder to get a conviction,” Rasch said. “It adds to the prosecutorial burden and increases the likelihood of getting an acquittal.”
Rasch said it’s unclear where it is appropriate to draw the line in the use of terrorism statutes to disrupt harm groups online, noting that there certainly are circumstances where individuals can commit violations of domestic anti-terrorism statutes through their Internet activity alone.
“The Internet is a platform like any other, where virtually any kind of crime that can be committed in the real world can also be committed online,” he said. “That doesn’t mean all misuse of computers fits within the statutory definition of terrorism.”
The RCMP’s advisory on sexual extortion of minors over the Internet lists a number of potential warning signs that teens may exhibit if they become entangled in these harm groups. The FBI urges anyone who believes their child or someone they know is being exploited to contact their local FBI field office, call 1-800-CALL-FBI, or report it online at tips.fbi.gov.

Most accomplished cybercriminals go out of their way to separate their real names from their hacker handles. But among certain old-school Russian hackers it is not uncommon to find major players who have done little to prevent people from figuring out who they are in real life. A case study in this phenomenon is “x999xx,” the nickname chosen by a venerated Russian hacker who specializes in providing the initial network access to various ransomware groups.
x999xx is a well-known “access broker” who frequently sells access to hacked corporate networks — usually in the form of remote access credentials — as well as compromised databases containing large amounts of personal and financial data.
In an analysis published in February 2019, cyber intelligence firm Flashpoint called x999xx one of the most senior and prolific members of the top-tier Russian-language cybercrime forum Exploit, where x999xx could be seen frequently advertising the sale of stolen databases and network credentials.
In August 2023, x999xx sold access to a company that develops software for the real estate industry. In July 2023, x999xx advertised the sale of Social Security numbers, names, and birthdays for the citizenry of an entire U.S. state (unnamed in the auction).
A month earlier, x999xx posted a sales thread for 80 databases taken from Australia’s largest retail company. “You may use this data to demand a ransom or do something different with it,” x999xx wrote on Exploit. “Unfortunately, the flaw was patched fast. [+] no one has used the data yet [+] the data hasn’t been used to send spam [+] the data is waiting for its time.”
In October 2022, x999xx sold administrative access to a U.S. healthcare provider.
The oldest account by the name x999xx appeared in 2009 on the Russian language cybercrime forum Verified, under the email address maxnm@ozersk.com. Ozersk is a city in the Chelyabinsk region of west-central Russia.
According to the breach tracking service Constella Intelligence, the address maxnm@ozersk.com was used more than a decade ago to create an account at Vktontakte (the Russian answer to Facebook) under the name Maxim Kirtsov from Ozersk. Mr. Kirtsov’s profile — “maxnm” — says his birthday is September 5, 1991.

Personal photos Maxnm shared on Vktontakte in 2016. The caption has been machine translated from Russian.
The user x999xx registered on the Russian language cybercrime community Zloy in 2014 using the email address maxnmalias-1@yahoo.com. Constella says this email address was used in 2022 at the Russian shipping service cdek.ru by a Maksim Georgievich Kirtsov from Ozersk.
Additional searches on these contact details reveal that prior to 2009, x999xx favored the handle Maxnm on Russian cybercrime forums. Cyber intelligence company Intel 471 finds the user Maxnm registered on Zloy in 2006 from an Internet address in Chelyabinsk, using the email address kirtsov@telecom.ozersk.ru.
That same email address was used to create Maxnm accounts on several other crime forums, including Spamdot and Exploit in 2005 (also from Chelyabinsk), and Damagelab in 2006.
A search in Constella for the Russian version of Kirtsov’s full name — Кирцов Максим Георгиевич — brings up multiple accounts registered to maksya@icloud.com.
A review of the digital footprint for maksya@icloud.com at osint.industries reveals this address was used a decade ago to register a still-active account at imageshack.com under the name x999xx. That account features numerous screenshots of financial statements from various banks, chat logs with other hackers, and even hacked websites.
x999xx’s Imageshack account includes screenshots of bank account balances from dozens of financial institutions, as well as chat logs with other hackers and pictures of homegrown weed.
Some of the photos in that Imageshack account also appear on Kirtsov’s Vkontakte page, including images of vehicles he owns, as well as pictures of potted marijuana plants. Kirtsov’s Vkontakte profile says that in 2012 he was a faculty member of the Ozersk Technological Institute National Research Nuclear University.
The Vkontakte page lists Kirtsov’s occupation as a website called ozersk[.]today, which on the surface appears to be a blog about life in Ozersk. However, in 2019 the security firm Recorded Future published a blog post which found this domain was being used to host a malicious Cobalt Strike server.
Cobalt Strike is a commercial network penetration testing and reconnaissance tool that is sold only to vetted partners. But stolen or ill-gotten Cobalt Strike licenses are frequently abused by cybercriminal gangs to help lay the groundwork for the installation of ransomware on a victim network.
In August 2023, x999xx posted a message on Exploit saying he was interested in buying a licensed version of Cobalt Strike. A month earlier, x999xx filed a complaint on Exploit against another forum member named Cobaltforce, an apparent onetime partner whose sudden and prolonged disappearance from the community left x999xx and others in the lurch. Cobaltforce recruited people experienced in using Cobalt Strike for ransomware operations, and offered to monetize access to hacked networks for a share of the profits.
DomainTools.com finds ozersk[.]today was registered to the email address dashin2008@yahoo.com, which also was used to register roughly two dozen other domains, including x999xx[.]biz. Virtually all of those domains were registered to Maxim Kirtsov from Ozersk. Below is a mind map used to track the identities mentioned in this story.
x999xx is a prolific member of the Russian webmaster forum “Gofuckbiz,” with more than 2,000 posts over nearly a decade, according to Intel 471. In one post from 2016, x999xx asked whether anyone knew where he could buy a heat lamp that simulates sunlight, explaining that one his pet rabbits had recently perished for lack of adequate light and heat. Mr. Kirtsov’s Vkontakte page includes several pictures of caged rabbits from 2015 and earlier.
Reached via email, Mr. Kirtsov acknowledged that he is x999xx. Kirtsov said he and his team are also regular readers of KrebsOnSecurity.
“We’re glad to hear and read you,” Kirtsov replied.
Asked whether he was concerned about the legal and moral implications of his work, Kirtsov downplayed his role in ransomware intrusions, saying he was more focused on harvesting data.
“I consider myself as committed to ethical practices as you are,” Kirtsov wrote. “I have also embarked on research and am currently mentoring students. You may have noticed my activities on a forum, which I assume you know of through information gathered from public sources, possibly using the new tool you reviewed.”
“Regarding my posts about selling access, I must honestly admit, upon reviewing my own actions, I recall such mentions but believe they were never actualized,” he continued. “Many use the forum for self-serving purposes, which explains why listings of targets for sale have dwindled — they simply ceased being viable.”
Kirtsov asserted that he is not interested in harming healthcare institutions, just in stealing their data.
“As for health-related matters, I was once acquainted with affluent webmasters who would pay up to $50 for every 1000 health-themed emails,” Kirtsov said. “Therefore, I had no interest in the more sensitive data from medical institutions like X-rays, insurance numbers, or even names; I focused solely on emails. I am proficient in SQL, hence my ease with handling data like IDs and emails. And i never doing spam or something like this.”
On the Russian crime forums, x999xx said he never targets anything or anyone in Russia, and that he has little to fear from domestic law enforcement agencies provided he remains focused on foreign adversaries.
x999xx’s lackadaisical approach to personal security mirrors that of Wazawaka, another top Russian access broker who sold access to countless organizations and even operated his own ransomware affiliate programs.
“Don’t shit where you live, travel local, and don’t go abroad,” Wazawaka said of his own personal mantra. “Mother Russia will help you. Love your country, and you will always get away with everything.”
In January 2022, KrebsOnSecurity followed clues left behind by Wazawaka to identify him as 32-year-old Mikhail Matveev from Khakassia, Russia. In May 2023, the U.S. Department of Justice indicted Matveev as a key figure in several ransomware groups that collectively extorted hundreds of millions of dollars from victim organizations. The U.S. State Department is offering a $10 million reward for information leading to the capture and/or prosecution of Matveev.
Perhaps in recognition that many top ransomware criminals are largely untouchable so long as they remain in Russia, western law enforcement agencies have begun focusing more on getting inside the heads of those individuals. These so-called “psyops” are aimed at infiltrating ransomware-as-a-service operations, disrupting major cybercrime services, and decreasing trust within cybercriminal communities.
When authorities in the U.S. and U.K. announced in February 2024 that they’d infiltrated and seized the infrastructure used by the infamous LockBit ransomware gang, they borrowed the existing design of LockBit’s victim shaming website to link instead to press releases about the takedown, and included a countdown timer that was eventually replaced with the personal details of LockBit’s alleged leader.
In May 2024, law enforcement agencies in the United States and Europe announced Operation Endgame, a coordinated action against some of the most popular cybercrime platforms for delivering ransomware and data-stealing malware. The Operation Endgame website also included a countdown timer, which served to tease the release of several animated videos that mimic the same sort of flashy, short advertisements that established cybercriminals often produce to promote their services online.
A proof-of-concept User-Defined Reflective Loader (UDRL) which aims to recreate, integrate, and enhance Cobalt Strike's evasion features!
| Contributor | Notable Contributions | |
|---|---|---|
| Bobby Cooke | @0xBoku | Project original author and maintainer |
| Santiago Pecin | @s4ntiago_p | Reflective Loader major enhancements |
| Chris Spehn | @ConsciousHacker | Aggressor scripting |
| Joshua Magri | @passthehashbrwn | IAT hooking |
| Dylan Tran | @d_tranman | Reflective Call Stack Spoofing |
| James Yeung | @5cript1diot | Indirect System Calls |
The built-in Cobalt Strike reflective loader is robust, handling all Malleable PE evasion features Cobalt Strike has to offer. The major disadvantage to using a custom UDRL is Malleable PE evasion features may or may not be supported out-of-the-box.
The objective of the public BokuLoader project is to assist red teams in creating their own in-house Cobalt Strike UDRL. The project aims to support all worthwhile CS Malleable PE evasion features. Some evasion features leverage CS integration, others have been recreated completely, and some are unsupported.
Before using this project, in any form, you should properly test the evasion features are working as intended. Between the C code and the Aggressor script, compilation with different versions of operating systems, compilers, and Java may return different results.
NtProtectVirtualMemory
obfuscate "true" with custom UDRL Aggressor script implementation.0x1000 bytes will be nulls.XGetProcAddress for resolving symbolsKernel32.GetProcAddress
xLoadLibrary for resolving DLL's base address & DLL LoadingTEB->PEB->PEB_LDR_DATA->InMemoryOrderModuleList
Kernel32.LoadLibraryA
| Command | Option(s) | Supported |
|---|---|---|
allocator | HeapAlloc, MapViewOfFile, VirtualAlloc | All supported via BokuLoader implementation |
module_x64 | string (DLL Name) | Supported via BokuLoader implementation. Same DLL stomping requirements as CS implementation apply |
obfuscate | true/false | HTTP/S beacons supported via BokuLoader implementation. SMB/TCP is currently not supported for obfuscate true. Details in issue. Accepting help if you can fix :) |
entry_point | RVA as decimal number | Supported via BokuLoader implementation |
cleanup | true | Supported via CS integration |
userwx | true/false | Supported via BokuLoader implementation |
sleep_mask | (true/false) or (Sleepmask Kit+true) | Supported. When using default "sleepmask true" (without sleepmask kit) set "userwx true". When using sleepmask kit which supports RX beacon.text memory (src47/Ekko) set "sleepmask true" && "userwx false". |
magic_mz_x64 | 4 char string | Supported via CS integration |
magic_pe | 2 char string | Supported via CS integration |
transform-x64 prepend | escaped hex string |
BokuLoader.cna Aggressor script modification |
transform-x64 strrep | string string |
BokuLoader.cna Aggressor script modification |
stomppe | true/false | Unsupported. BokuLoader does not copy beacon DLL headers over. First 0x1000 bytes of virtual beacon DLL are 0x00
|
checksum | number | Experimental. BokuLoader.cna Aggressor script modification |
compile_time | date-time string | Experimental. BokuLoader.cna Aggressor script modification |
image_size_x64 | decimal value | Unsupported |
name | string | Experimental. BokuLoader.cna Aggressor script modification |
rich_header | escaped hex string | Experimental. BokuLoader.cna Aggressor script modification |
stringw | string | Unsupported |
string | string | Unsupported |
make
BokuLoader.cna Aggressor scriptUse the Script Console to ensure BokuLoader was implemented in the beacon build
Does not support x86 option. The x86 bin is the original Reflective Loader object file.
RAW beacons works out of the box. When using the Artifact Kit for the beacon loader, the stagesize variable must be larger than the default.| Original Cobalt Strike String | BokuLoader Cobalt Strike String |
|---|---|
| ReflectiveLoader | BokuLoader |
| Microsoft Base Cryptographic Provider v1.0 | 12367321236742382543232341241261363163151d |
| (admin) | (tomin) |
| beacon | bacons |
Kernel32.LoadLibraryExA is called to map the DLL from diskKernel32.LoadLibraryExA is DONT_RESOLVE_DLL_REFERENCES (0x00000001)
RX or RWX memory will exist in the heap if sleepmask kit is not used.Kernel32.CreateFileMappingA & Kernel32.MapViewOfFile is called to allocate memory for the virtual beacon DLL.NtAllocateVirtualMemory, NtProtectVirtualMemory
ntdll.dll will not detect these systemcalls.mov eax, r11d; mov r11, r10; mov r10, rcx; jmp r11 assembly instructions within its executable memory.0x1000 bytes of the virtual beacon DLL are zeros.A 22-year-old man from the United Kingdom arrested this week in Spain is allegedly the ringleader of Scattered Spider, a cybercrime group suspected of hacking into Twilio, LastPass, DoorDash, Mailchimp, and nearly 130 other organizations over the past two years.
The Spanish daily Murcia Today reports the suspect was wanted by the FBI and arrested in Palma de Mallorca as he tried to board a flight to Italy.

A still frame from a video released by the Spanish national police shows Tylerb in custody at the airport.
“He stands accused of hacking into corporate accounts and stealing critical information, which allegedly enabled the group to access multi-million-dollar funds,” Murcia Today wrote. “According to Palma police, at one point he controlled Bitcoins worth $27 million.”
The cybercrime-focused Twitter/X account vx-underground said the U.K. man arrested was a SIM-swapper who went by the alias “Tyler.” In a SIM-swapping attack, crooks transfer the target’s phone number to a device they control and intercept any text messages or phone calls sent to the victim — including one-time passcodes for authentication, or password reset links sent via SMS.
“He is a known SIM-swapper and is allegedly involved with the infamous Scattered Spider group,” vx-underground wrote on June 15, referring to a prolific gang implicated in costly data ransom attacks at MGM and Caesars casinos in Las Vegas last year.
Sources familiar with the investigation told KrebsOnSecurity the accused is a 22-year-old from Dundee, Scotland named Tyler Buchanan, also allegedly known as “tylerb” on Telegram chat channels centered around SIM-swapping.
In January 2024, U.S. authorities arrested another alleged Scattered Spider member — 19-year-old Noah Michael Urban of Palm Coast, Fla. — and charged him with stealing at least $800,000 from five victims between August 2022 and March 2023. Urban allegedly went by the nicknames “Sosa” and “King Bob,” and is believed to be part of the same crew that hacked Twilio and a slew of other companies in 2022.
Investigators say Scattered Spider members are part of a more diffuse cybercriminal community online known as “The Com,” wherein hackers from different cliques boast loudly about high-profile cyber thefts that almost invariably begin with social engineering — tricking people over the phone, email or SMS into giving away credentials that allow remote access to corporate internal networks.
One of the more popular SIM-swapping channels on Telegram maintains a frequently updated leaderboard of the most accomplished SIM-swappers, indexed by their supposed conquests in stealing cryptocurrency. That leaderboard currently lists Sosa as #24 (out of 100), and Tylerb at #65.
In August 2022, KrebsOnSecurity wrote about peering inside the data harvested in a months-long cybercrime campaign by Scattered Spider involving countless SMS-based phishing attacks against employees at major corporations. The security firm Group-IB called the gang by a different name — 0ktapus, a nod to how the criminal group phished employees for credentials.
The missives asked users to click a link and log in at a phishing page that mimicked their employer’s Okta authentication page. Those who submitted credentials were then prompted to provide the one-time password needed for multi-factor authentication.
These phishing attacks used newly-registered domains that often included the name of the targeted company, and sent text messages urging employees to click on links to these domains to view information about a pending change in their work schedule. The phishing sites also featured a hidden Telegram instant message bot to forward any submitted credentials in real-time, allowing the attackers to use the phished username, password and one-time code to log in as that employee at the real employer website.
One of Scattered Spider’s first big victims in its 2022 SMS phishing spree was Twilio, a company that provides services for making and receiving text messages and phone calls. The group then pivoted, using their access to Twilio to attack at least 163 of its customers.

A Scattered Spider phishing lure sent to Twilio employees.
Among those was the encrypted messaging app Signal, which said the breach could have let attackers re-register the phone number on another device for about 1,900 users.
Also in August 2022, several employees at email delivery firm Mailchimp provided their remote access credentials to this phishing group. According to Mailchimp, the attackers used their access to Mailchimp employee accounts to steal data from 214 customers involved in cryptocurrency and finance.
On August 25, 2022, the password manager service LastPass disclosed a breach in which attackers stole some source code and proprietary LastPass technical information, and weeks later LastPass said an investigation revealed no customer data or password vaults were accessed.
However, on November 30, 2022 LastPass disclosed a far more serious breach that the company said leveraged data stolen in the August breach. LastPass said criminal hackers had stolen encrypted copies of some password vaults, as well as other personal information.
In February 2023, LastPass disclosed that the intrusion involved a highly complex, targeted attack against an engineer who was one of only four LastPass employees with access to the corporate vault. In that incident, the attackers exploited a security vulnerability in a Plex media server that the employee was running on his home network, and succeeded in installing malicious software that stole passwords and other authentication credentials. The vulnerability exploited by the intruders was patched back in 2020, but the employee never updated his Plex software.
Plex announced its own data breach one day before LastPass disclosed its initial August intrusion. On August 24, 2022, Plex’s security team urged users to reset their passwords, saying an intruder had accessed customer emails, usernames and encrypted passwords.
Sosa and Tylerb were both subjected to physical attacks from rival SIM-swapping gangs. These communities have been known to settle scores by turning to so-called “violence-as-a-service” offerings on cybercrime channels, wherein people can be hired to perform a variety geographically-specific “in real life” jobs, such as bricking windows, slashing car tires, or even home invasions.
In 2022, a video surfaced on a popular cybercrime channel purporting to show attackers hurling a brick through a window at an address that matches the spacious and upscale home of Urban’s parents in Sanford, Fl.
January’s story on Sosa noted that a junior member of his crew named “Foreshadow” was kidnapped, beaten and held for ransom in September 2022. Foreshadow’s captors held guns to his bloodied head while forcing him to record a video message pleading with his crew to fork over a $200,000 ransom in exchange for his life (Foreshadow escaped further harm in that incident).
According to several SIM-swapping channels on Telegram where Tylerb was known to frequent, rival SIM-swappers hired thugs to invade his home in February 2023. Those accounts state that the intruders assaulted Tylerb’s mother in the home invasion, and that they threatened to burn him with a blowtorch if he didn’t give up the keys to his cryptocurrency wallets. Tylerb was reputed to have fled the United Kingdom after that assault.
KrebsOnSecurity sought comment from Mr. Buchanan, and will update this story in the event he responds.
Thief Raccoon is a tool designed for educational purposes to demonstrate how phishing attacks can be conducted on various operating systems. This tool is intended to raise awareness about cybersecurity threats and help users understand the importance of security measures like 2FA and password management.
```bash git clone https://github.com/davenisc/thief_raccoon.git cd thief_raccoon
```bash apt install python3.11-venv
```bash python -m venv raccoon_venv source raccoon_venv/bin/activate
```bash pip install -r requirements.txt
Usage
```bash python app.py
After running the script, you will be presented with a menu to select the operating system. Enter the number corresponding to the OS you want to simulate.
If you are on the same local network (LAN), open your web browser and navigate to http://127.0.0.1:5000.
If you want to make the phishing page accessible over the internet, use ngrok.
Using ngrok
Download ngrok from ngrok.com and follow the installation instructions for your operating system.
Expose your local server to the internet:
Get the public URL:
After running the above command, ngrok will provide you with a public URL. Share this URL with your test subjects to access the phishing page over the internet.
How to install Ngrok on Linux?
```bash curl -s https://ngrok-agent.s3.amazonaws.com/ngrok.asc \ | sudo tee /etc/apt/trusted.gpg.d/ngrok.asc >/dev/null \ && echo "deb https://ngrok-agent.s3.amazonaws.com buster main" \ | sudo tee /etc/apt/sources.list.d/ngrok.list \ && sudo apt update \ && sudo apt install ngrok
```bash ngrok config add-authtoken xxxxxxxxx--your-token-xxxxxxxxxxxxxx
Deploy your app online
Put your app online at ephemeral domain Forwarding to your upstream service. For example, if it is listening on port http://localhost:8080, run:
```bash ngrok http http://localhost:5000
Example
```bash python app.py
```bash Select the operating system for phishing: 1. Windows 10 2. Windows 11 3. Windows XP 4. Windows Server 5. Ubuntu 6. Ubuntu Server 7. macOS Enter the number of your choice: 2
Open your browser and go to http://127.0.0.1:5000 or the ngrok public URL.
Disclaimer
This tool is intended for educational purposes only. The author is not responsible for any misuse of this tool. Always obtain explicit permission from the owner of the system before conducting any phishing tests.
License
This project is licensed under the MIT License. See the LICENSE file for details.
ScreenShots
Credits
Developer: @davenisc Web: https://davenisc.com
The C2 Cloud is a robust web-based C2 framework, designed to simplify the life of penetration testers. It allows easy access to compromised backdoors, just like accessing an EC2 instance in the AWS cloud. It can manage several simultaneous backdoor sessions with a user-friendly interface.
C2 Cloud is open source. Security analysts can confidently perform simulations, gaining valuable experience and contributing to the proactive defense posture of their organizations.
Reverse shells support:
C2 Cloud walkthrough: https://youtu.be/hrHT_RDcGj8
Ransomware simulation using C2 Cloud: https://youtu.be/LKaCDmLAyvM
Telegram C2: https://youtu.be/WLQtF4hbCKk
🔒 Anywhere Access: Reach the C2 Cloud from any location.
🔄 Multiple Backdoor Sessions: Manage and support multiple sessions effortlessly.
🖱️ One-Click Backdoor Access: Seamlessly navigate to backdoors with a simple click.
📜 Session History Maintenance: Track and retain complete command and response history for comprehensive analysis.
🛠️ Flask: Serving web and API traffic, facilitating reverse HTTP(s) requests.
🔗 TCP Socket: Serving reverse TCP requests for enhanced functionality.
🌐 Nginx: Effortlessly routing traffic between web and backend systems.
📨 Redis PubSub: Serving as a robust message broker for seamless communication.
🚀 Websockets: Delivering real-time updates to browser clients for enhanced user experience.
💾 Postgres DB: Ensuring persistent storage for seamless continuity.
Reverse TCP port: 8888
Clone the repo
Inspired by Villain, a CLI-based C2 developed by Panagiotis Chartas.
Distributed under the MIT License. See LICENSE for more information.

You consider yourself a responsible person when it comes to taking care of your physical possessions. You’ve never left your wallet in a taxi or lost an expensive ring down the drain. You never let your smartphone out of your sight, yet one day you notice it’s acting oddly.
Did you know that your device can fall into cybercriminals’ hands without ever leaving yours? SIM swapping is a method that allows criminals to take control of your smartphone and break into your online accounts.
Don’t worry: there are a few easy steps you can take to safeguard your smartphone from prying eyes and get back to using your devices confidently.
First off, what exactly is a SIM card? SIM stands for subscriber identity module, and it is a memory chip that makes your phone truly yours. It stores your phone plan and phone number, as well as all your photos, texts, contacts, and apps. In most cases, you can pop your SIM card out of an old phone and into a new one to transfer your photos, apps, etc.
Unlike what the name suggests, SIM swapping doesn’t require a cybercriminal to get access to your physical phone and steal your SIM card. SIM swapping can happen remotely. A hacker, with a few important details about your life in hand, can answer security questions correctly, impersonate you, and convince your mobile carrier to reassign your phone number to a new SIM card. At that point, the criminal can get access to your phone’s data and start changing your account passwords to lock you out of your online banking profile, email, and more.
SIM swapping was especially relevant right after the AT&T data leak. Cybercriminals stole millions of phone numbers and the users’ associated personal details. They could later use these details to SIM swap, allowing them to receive users’ text or email two-factor authentication codes and gain access to their personal accounts.
The most glaring sign that your phone number was reassigned to a new SIM card is that your current phone no longer connects to the cell network. That means you won’t be able to make calls, send texts, or surf the internet when you’re not connected to Wi-Fi. Since most people use their smartphones every day, you’ll likely find out quickly that your phone isn’t functioning as it should.
Additionally, when a SIM card is no longer active, the carrier will often send a notification text. If you receive one of these texts but didn’t deactivate your SIM card, use someone else’s phone or landline to contact your wireless provider.
Check out these tips to keep your device and personal information safe from SIM swapping.
With just a few simple steps, you can feel better about the security of your smartphone, cellphone number, and online accounts. If you’d like extra peace of mind, consider signing up for an identity theft protection service like McAfee+. McAfee, on average, detects suspicious activity ten months earlier than similar monitoring services. Time is of the essence in cases of SIM swapping and other identity theft schemes. An identity protection partner can restore your confidence in your online activities.
The post How to Protect Your Smartphone from SIM Swapping appeared first on McAfee Blog.
BackdoorSim is a remote administration and monitoring tool designed for educational and testing purposes. It consists of two main components: ControlServer and BackdoorClient. The server controls the client, allowing for various operations like file transfer, system monitoring, and more.
This tool is intended for educational purposes only. Misuse of this software can violate privacy and security policies. The developers are not responsible for any misuse or damage caused by this software. Always ensure you have permission to use this tool in your intended environment.
To set up BackdoorSim, you will need to install it on both the server and client machines.
shell $ git clone https://github.com/HalilDeniz/BackDoorSim.git
shell $ cd BackDoorSim
shell $ pip install -r requirements.txt
After starting both the server and client, you can use the following commands in the server's command prompt:
upload [file_path]: Upload a file to the client.download [file_path]: Download a file from the client.screenshot: Capture a screenshot from the client.sysinfo: Get system information from the client.securityinfo: Get security software status from the client.camshot: Capture an image from the client's webcam.notify [title] [message]: Send a notification to the client.help: Display the help menu.BackDoorSim is developed for educational purposes only. The creators of BackDoorSim are not responsible for any misuse of this tool. This tool should not be used in any unauthorized or illegal manner. Always ensure ethical and legal use of this tool.
If you are interested in tools like BackdoorSim, be sure to check out my recently released RansomwareSim tool
If you want to read our article about Backdoor
Contributions, suggestions, and feedback are welcome. Please create an issue or pull request for any contributions. 1. Fork the repository. 2. Create a new branch for your feature or bug fix. 3. Make your changes and commit them. 4. Push your changes to your forked repository. 5. Open a pull request in the main repository.
For any inquiries or further information, you can reach me through the following channels:
Three Americans were charged this week with stealing more than $400 million in a November 2022 SIM-swapping attack. The U.S. government did not name the victim organization, but there is every indication that the money was stolen from the now-defunct cryptocurrency exchange FTX, which had just filed for bankruptcy on that same day.
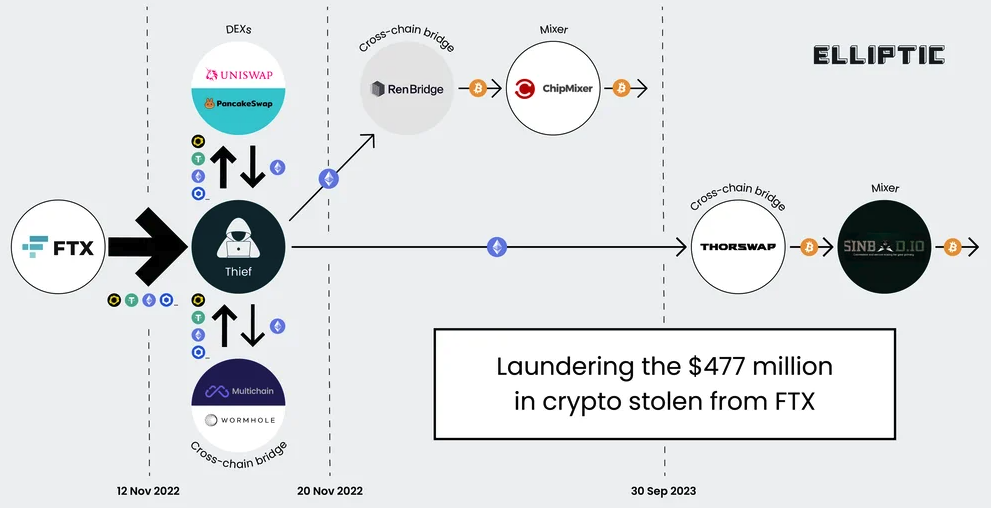
A graphic illustrating the flow of more than $400 million in cryptocurrencies stolen from FTX on Nov. 11-12, 2022. Image: Elliptic.co.
An indictment unsealed this week and first reported on by Ars Technica alleges that Chicago man Robert Powell, a.k.a. “R,” “R$” and “ElSwapo1,” was the ringleader of a SIM-swapping group called the “Powell SIM Swapping Crew.” Colorado resident Emily “Em” Hernandez allegedly helped the group gain access to victim devices in service of SIM-swapping attacks between March 2021 and April 2023. Indiana resident Carter Rohn, a.k.a. “Carti,” and “Punslayer,” allegedly assisted in compromising devices.
In a SIM-swapping attack, the crooks transfer the target’s phone number to a device they control, allowing them to intercept any text messages or phone calls sent to the victim, including one-time passcodes for authentication or password reset links sent via SMS.
The indictment states that the perpetrators in this heist stole the $400 million in cryptocurrencies on Nov. 11, 2022 after they SIM-swapped an AT&T customer by impersonating them at a retail store using a fake ID. However, the document refers to the victim in this case only by the name “Victim 1.”
Wired’s Andy Greenberg recently wrote about FTX’s all-night race to stop a $1 billion crypto heist that occurred on the evening of November 11:
“FTX’s staff had already endured one of the worst days in the company’s short life. What had recently been one of the world’s top cryptocurrency exchanges, valued at $32 billion only 10 months earlier, had just declared bankruptcy. Executives had, after an extended struggle, persuaded the company’s CEO, Sam Bankman-Fried, to hand over the reins to John Ray III, a new chief executive now tasked with shepherding the company through a nightmarish thicket of debts, many of which it seemed to have no means to pay.”
“FTX had, it seemed, hit rock bottom. Until someone—a thief or thieves who have yet to be identified—chose that particular moment to make things far worse. That Friday evening, exhausted FTX staffers began to see mysterious outflows of the company’s cryptocurrency, publicly captured on the Etherscan website that tracks the Ethereum blockchain, representing hundreds of millions of dollars worth of crypto being stolen in real time.”
The indictment says the $400 million was stolen over several hours between November 11 and 12, 2022. Tom Robinson, co-founder of the blockchain intelligence firm Elliptic, said the attackers in the FTX heist began to drain FTX wallets on the evening of Nov. 11, 2022 local time, and continuing until the 12th of November.
Robinson said Elliptic is not aware of any other crypto heists of that magnitude occurring on that date.
“We put the value of the cryptoassets stolen at $477 million,” Robinson said. “The FTX administrators have reported overall losses due to “unauthorized third-party transfers” of $413 million – the discrepancy is likely due to subsequent seizure and return of some of the stolen assets. Either way, it’s certainly over $400 million, and we are not aware of any other thefts from crypto exchanges on this scale, on this date.”
The SIM-swappers allegedly responsible for the $400 million crypto theft are all U.S. residents. But there are some indications they had help from organized cybercriminals based in Russia. In October 2023, Elliptic released a report that found the money stolen from FTX had been laundered through exchanges with ties to criminal groups based in Russia.
“A Russia-linked actor seems a stronger possibility,” Elliptic wrote. “Of the stolen assets that can be traced through ChipMixer, significant amounts are combined with funds from Russia-linked criminal groups, including ransomware gangs and darknet markets, before being sent to exchanges. This points to the involvement of a broker or other intermediary with a nexus in Russia.”
Nick Bax, director of analytics at the cryptocurrency wallet recovery firm Unciphered, said the flow of stolen FTX funds looks more like what his team has seen from groups based in Eastern Europe and Russian than anything they’ve witnessed from US-based SIM-swappers.
“I was a bit surprised by this development but it seems to be consistent with reports from CISA [the Cybersecurity and Infrastructure Security Agency] and others that “Scattered Spider” has worked with [ransomware] groups like ALPHV/BlackCat,” Bax said.
CISA’s alert on Scattered Spider says they are a cybercriminal group that targets large companies and their contracted information technology (IT) help desks.
“Scattered Spider threat actors, per trusted third parties, have typically engaged in data theft for extortion and have also been known to utilize BlackCat/ALPHV ransomware alongside their usual TTPs,” CISA said, referring to the group’s signature “Tactics, Techniques an Procedures.”
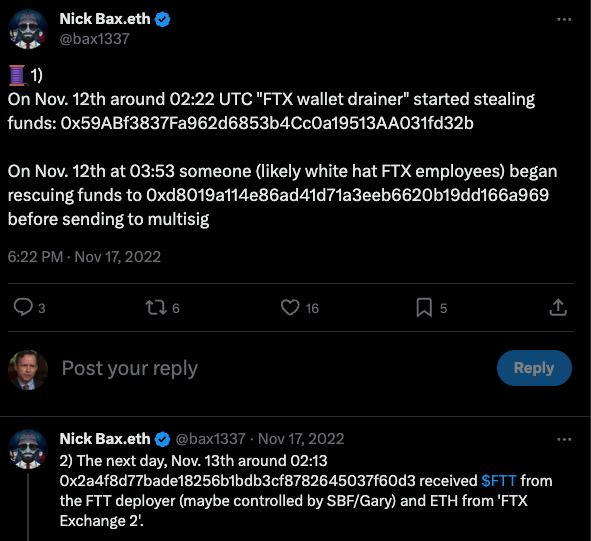
Nick Bax, posting on Twitter/X in Nov 2022 about his research on the $400 million FTX heist.
Earlier this week, KrebsOnSecurity published a story noting that a Florida man recently charged with being part of a SIM-swapping conspiracy is thought to be a key member of Scattered Spider, a hacking group also known as 0ktapus. That group has been blamed for a string of cyber intrusions at major U.S. technology companies during the summer of 2022.
Financial claims involving FTX’s bankruptcy proceedings are being handled by the financial and risk consulting giant Kroll. In August 2023, Kroll suffered its own breach after a Kroll employee was SIM-swapped. According to Kroll, the thieves stole user information for multiple cryptocurrency platforms that rely on Kroll services to handle bankruptcy proceedings.
KrebsOnSecurity sought comment for this story from Kroll, the FBI, the prosecuting attorneys, and Sullivan & Cromwell, the law firm handling the FTX bankruptcy. This story will be updated in the event any of them respond.
Attorneys for Mr. Powell said they do not know who Victim 1 is in the indictment, as the government hasn’t shared that information yet. Powell’s next court date is a detention hearing on Feb. 2, 2024.
Update, Feb. 3, 12:19 p.m. ET: The FBI declined a request to comment.
On Jan. 9, 2024, U.S. authorities arrested a 19-year-old Florida man charged with wire fraud, aggravated identity theft, and conspiring with others to use SIM-swapping to steal cryptocurrency. Sources close to the investigation tell KrebsOnSecurity the accused was a key member of a criminal hacking group blamed for a string of cyber intrusions at major U.S. technology companies during the summer of 2022.
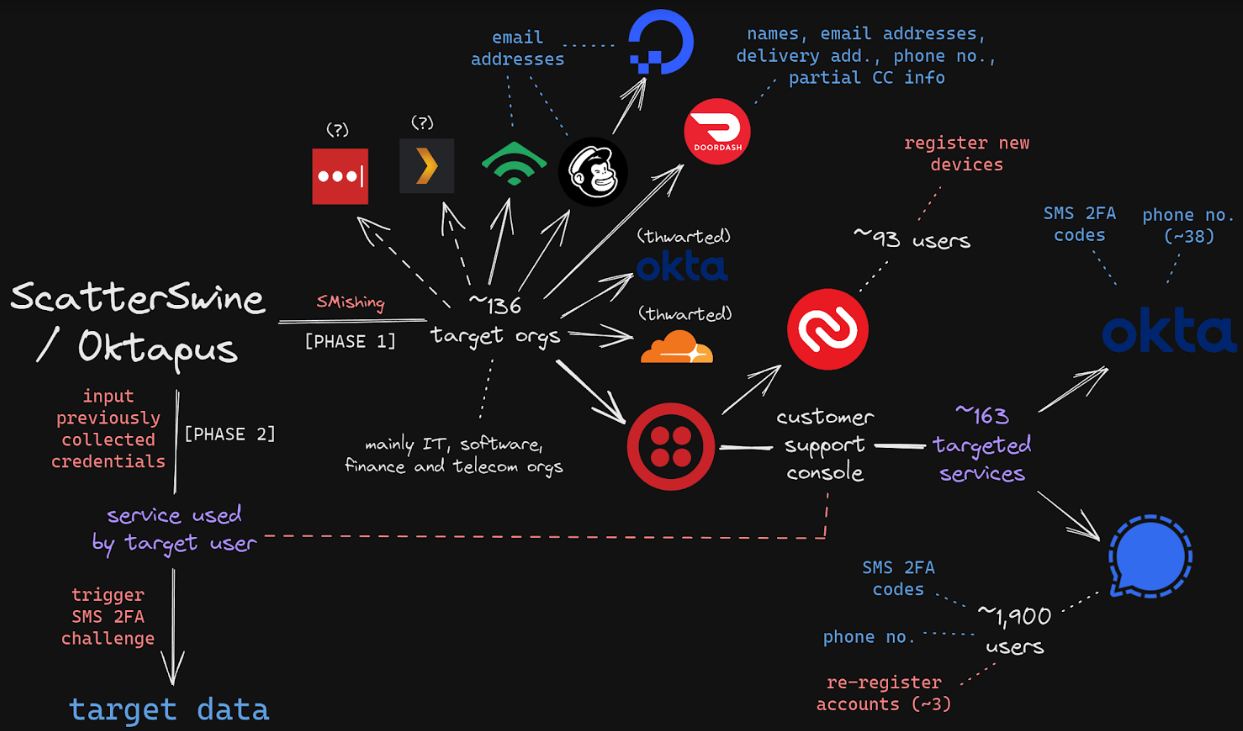
A graphic depicting how 0ktapus leveraged one victim to attack another. Image credit: Amitai Cohen of Wiz.
Prosecutors say Noah Michael Urban of Palm Coast, Fla., stole at least $800,000 from at least five victims between August 2022 and March 2023. In each attack, the victims saw their email and financial accounts compromised after suffering an unauthorized SIM-swap, wherein attackers transferred each victim’s mobile phone number to a new device that they controlled.
The government says Urban went by the aliases “Sosa” and “King Bob,” among others. Multiple trusted sources told KrebsOnSecurity that Sosa/King Bob was a core member of a hacking group behind the 2022 breach at Twilio, a company that provides services for making and receiving text messages and phone calls. Twilio disclosed in Aug. 2022 that an intrusion had exposed a “limited number” of Twilio customer accounts through a sophisticated social engineering attack designed to steal employee credentials.
Shortly after that disclosure, the security firm Group-IB published a report linking the attackers behind the Twilio intrusion to separate breaches at more than 130 organizations, including LastPass, DoorDash, Mailchimp, and Plex. Multiple security firms soon assigned the hacking group the nickname “Scattered Spider.”
Group-IB dubbed the gang by a different name — 0ktapus — which was a nod to how the criminal group phished employees for credentials. The missives asked users to click a link and log in at a phishing page that mimicked their employer’s Okta authentication page. Those who submitted credentials were then prompted to provide the one-time password needed for multi-factor authentication.

A booking photo of Noah Michael Urban released by the Volusia County Sheriff.
0ktapus used newly-registered domains that often included the name of the targeted company, and sent text messages urging employees to click on links to these domains to view information about a pending change in their work schedule. The phishing sites used a Telegram instant message bot to forward any submitted credentials in real-time, allowing the attackers to use the phished username, password and one-time code to log in as that employee at the real employer website.
0ktapus often leveraged information or access gained in one breach to perpetrate another. As documented by Group-IB, the group pivoted from its access to Twilio to attack at least 163 of its customers. Among those was the encrypted messaging app Signal, which said the breach could have let attackers re-register the phone number on another device for about 1,900 users.
Also in August 2022, several employees at email delivery firm Mailchimp provided their remote access credentials to this phishing group. According to an Aug. 12 blog post, the attackers used their access to Mailchimp employee accounts to steal data from 214 customers involved in cryptocurrency and finance.
On August 25, 2022, the password manager service LastPass disclosed a breach in which attackers stole some source code and proprietary LastPass technical information, and weeks later LastPass said an investigation revealed no customer data or password vaults were accessed.
However, on November 30, 2022 LastPass disclosed a far more serious breach that the company said leveraged data stolen in the August breach. LastPass said criminal hackers had stolen encrypted copies of some password vaults, as well as other personal information.
In February 2023, LastPass disclosed that the intrusion involved a highly complex, targeted attack against a DevOps engineer who was one of only four LastPass employees with access to the corporate vault. In that incident, the attackers exploited a security vulnerability in a Plex media server that the employee was running on his home network, and succeeded in installing malicious software that stole passwords and other authentication credentials. The vulnerability exploited by the intruders was patched back in 2020, but the employee never updated his Plex software.
As it happens, Plex announced its own data breach one day before LastPass disclosed its initial August intrusion. On August 24, 2022, Plex’s security team urged users to reset their passwords, saying an intruder had accessed customer emails, usernames and encrypted passwords.
A review of thousands of messages that Sosa and King Bob posted to several public forums and Discord servers over the past two years shows that the person behind these identities was mainly focused on two things: Sim-swapping, and trading in stolen, unreleased rap music recordings from popular artists.
Indeed, those messages show Sosa/King Bob was obsessed with finding new “grails,” the slang term used in some cybercrime discussion channels to describe recordings from popular artists that have never been officially released. It stands to reason that King Bob was SIM-swapping important people in the music industry to obtain these files, although there is little to support this conclusion from the public chat records available.
“I got the most music in the com,” King Bob bragged in a Discord server in November 2022. “I got thousands of grails.”
King Bob’s chats show he was particularly enamored of stealing the unreleased works of his favorite artists — Lil Uzi Vert, Playboi Carti, and Juice Wrld. When another Discord user asked if he has Eminem grails, King Bob said he was unsure.
“I have two folders,” King Bob explained. “One with Uzi, Carti, Juicewrld. And then I have ‘every other artist.’ Every other artist is unorganized as fuck and has thousands of random shit.”
King Bob’s posts on Discord show he quickly became a celebrity on Leaked[.]cx, one of most active forums for trading, buying and selling unreleased music from popular artists. The more grails that users share with the Leaked[.]cx community, the more their status and access on the forum grows.
The last cache of Leaked dot cx indexed by the archive.org on Jan. 11, 2024.
And King Bob shared a large number of his purloined tunes with this community. Still others he tried to sell. It’s unclear how many of those sales were ever consummated, but it is not unusual for a prized grail to sell for anywhere from $5,000 to $20,000.
In mid-January 2024, several Leaked[.]cx regulars began complaining that they hadn’t seen King Bob in a while and were really missing his grails. On or around Jan. 11, the same day the Justice Department unsealed the indictment against Urban, Leaked[.]cx started blocking people who were trying to visit the site from the United States.
Days later, frustrated Leaked[.]cx users speculated about what could be the cause of the blockage.
“Probs blocked as part of king bob investigation i think?,” wrote the user “Plsdontarrest.” “Doubt he only hacked US artists/ppl which is why it’s happening in multiple countries.”
On Sept. 21, 2022, KrebsOnSecurity told the story of a “Foreshadow,” the nickname chosen by a Florida teenager who was working for a SIM-swapping crew when he was abducted, beaten and held for a $200,000 ransom. A rival SIM-swapping group claimed that Foreshadow and his associates had robbed them of their fair share of the profits from a recent SIM-swap.
In a video released by his abductors on Telegram, a bloodied, battered Foreshadow was made to say they would kill him unless the ransom was paid.
As I wrote in that story, Foreshadow appears to have served as a “holder” — a term used to describe a low-level member of any SIM-swapping group who agrees to carry out the riskiest and least rewarding role of the crime: Physically keeping and managing the various mobile devices and SIM cards that are used in SIM-swapping scams.
KrebsOnSecurity has since learned that Foreshadow was a holder for a particularly active SIM-swapper who went by “Elijah,” which was another nickname that prosecutors say Urban used.

Shortly after Foreshadow’s hostage video began circulating on Telegram and Discord, multiple known actors in the SIM-swapping space told everyone in the channels to delete any previous messages with Foreshadow, claiming he was fully cooperating with the FBI.
This was not the first time Sosa and his crew were hit with violent attacks from rival SIM-swapping groups. In early 2022, a video surfaced on a popular cybercrime channel purporting to show attackers hurling a brick through a window at an address that matches the spacious and upscale home of Urban’s parents in Sanford, Fl.
“Brickings” are among the “violence-as-a-service” offerings broadly available on many cybercrime channels. SIM-swapping and adjacent cybercrime channels are replete with job offers for in-person assignments and tasks that can be found if one searches for posts titled, “If you live near,” or “IRL job” — short for “in real life” job.
A number of these classified ads are in service of performing brickings, where someone is hired to visit a specific address and toss a brick through the target’s window. Other typical IRL job offers involve tire slashings and even drive-by shootings.
Sosa was known to be a top member of the broader cybercriminal community online known as “The Com,” wherein hackers boast loudly about high-profile exploits and hacks that almost invariably begin with social engineering — tricking people over the phone, email or SMS into giving away credentials that allow remote access to corporate internal networks.
Sosa also was active in a particularly destructive group of accomplished criminal SIM-swappers known as “Star Fraud.” Cyberscoop’s AJ Vicens reported last year that individuals within Star Fraud were likely involved in the high-profile Caesars Entertainment an MGM Resorts extortion attacks.
“ALPHV, an established ransomware-as-a-service operation thought to be based in Russia and linked to attacks on dozens of entities, claimed responsibility for Caesars and MGM attacks in a note posted to its website earlier this month,” Vicens wrote. “Experts had said the attacks were the work of a group tracked variously as UNC 3944 or Scattered Spider, which has been described as an affiliate working with ALPHV made up of people in the United States and Britain who excel at social engineering.”
In February 2023, KrebsOnSecurity published data taken from the Telegram channels for Star Fraud and two other SIM-swapping groups showing these crooks focused on SIM-swapping T-Mobile customers, and that they collectively claimed access to T-Mobile on 100 separate occasions over a 7-month period in 2022.
The SIM-swapping groups were able to switch targeted phone numbers to another device on demand because they constantly phished T-Mobile employees into giving up credentials to employee-only tools. In each of those cases the goal was the same: Phish T-Mobile employees for access to internal company tools, and then convert that access into a cybercrime service that could be hired to divert any T-Mobile user’s text messages and phone calls to another device.
Allison Nixon, chief research officer at the New York cybersecurity consultancy Unit 221B, said the increasing brazenness of many Com members is a function of how long it has taken federal authorities to go after guys like Sosa.
“These incidents show what happens when it takes too long for cybercriminals to get arrested,” Nixon said. “If governments fail to prioritize this source of threat, violence originating from the Internet will affect regular people.”
The Daytona Beach News-Journal reports that Urban was arrested Jan. 9 and his trial is scheduled to begin in the trial term starting March 4 in Jacksonville. The publication said the judge overseeing Urban’s case denied bail because the defendant was a strong flight risk.
At Urban’s arraignment, it emerged that he had no fixed address and had been using an alias to stay at an Airbnb. The judge reportedly said that when a search warrant was executed at Urban’s residence, the defendant was downloading programs to delete computer files.
What’s more, the judge explained, despite telling authorities in May that he would not have any more contact with his co-conspirators and would not engage in cryptocurrency transactions, he did so anyway.
Urban entered a plea of not guilty. Urban’s court-appointed attorney said her client would have no comment at this time.
Prosecutors charged Urban with eight counts of wire fraud, one count of conspiracy to commit wire fraud, and five counts of aggravated identity theft. According to the government, if convicted Urban faces up to 20 years in federal prison on each wire fraud charge. He also faces a minimum mandatory penalty of two years in prison for the aggravated identity offenses, which will run consecutive to any other prison sentence imposed.
With the rapidly increasing variety of attack techniques and a simultaneous rise in the number of detection rules offered by EDRs (Endpoint Detection and Response) and custom-created ones, the need for constant functional testing of detection rules has become evident. However, manually re-running these attacks and cross-referencing them with detection rules is a labor-intensive task which is worth automating.
To address this challenge, I developed "PurpleKeep," an open-source initiative designed to facilitate the automated testing of detection rules. Leveraging the capabilities of the Atomic Red Team project which allows to simulate attacks following MITRE TTPs (Tactics, Techniques, and Procedures). PurpleKeep enhances the simulation of these TTPs to serve as a starting point for the evaluation of the effectiveness of detection rules.
Automating the process of simulating one or multiple TTPs in a test environment comes with certain challenges, one of which is the contamination of the platform after multiple simulations. However, PurpleKeep aims to overcome this hurdle by streamlining the simulation process and facilitating the creation and instrumentation of the targeted platform.
Primarily developed as a proof of concept, PurpleKeep serves as an End-to-End Detection Rule Validation platform tailored for an Azure-based environment. It has been tested in combination with the automatic deployment of Microsoft Defender for Endpoint as the preferred EDR solution. PurpleKeep also provides support for security and audit policy configurations, allowing users to mimic the desired endpoint environment.
To facilitate analysis and monitoring, PurpleKeep integrates with Azure Monitor and Log Analytics services to store the simulation logs and allow further correlation with any events and/or alerts stored in the same platform.
TLDR: PurpleKeep provides an Attack Simulation platform to serve as a starting point for your End-to-End Detection Rule Validation in an Azure-based environment.
The project is based on Azure Pipelines and requires the following to be able to run:
You can provide a security and/or audit policy file that will be loaded to mimic your Group Policy configurations. Use the Secure File option of the Library in Azure DevOps to make it accessible to your pipelines.
Refer to the variables file for your configurable items.
Deploying the infrastructure uses the Azure Pipeline to perform the following steps:
Currently only the Atomics from the public repository are supported. The pipelines takes a Technique ID as input or a comma seperate list of techniques, for example:
The logs of the simulation are ingested into the AtomicLogs_CL table of the Log Analytics Workspace.
There are currently two ways to run the simulation:
This pipeline will deploy a fresh platform after the simulation of each TTP. The Log Analytic workspace will maintain the logs of each run.
Warning: this will onboard a large number of hosts into your EDR
A fresh infrastructure will be deployed only at the beginning of the pipeline. All TTP's will be simulated on this instance. This is the fastests way to simulate and prevents onboarding a large number of devices, however running a lot of simulations in a same environment has the risk of contaminating the environment and making the simulations less stable and predictable.
Rayder is a command-line tool designed to simplify the orchestration and execution of workflows. It allows you to define a series of modules in a YAML file, each consisting of commands to be executed. Rayder helps you automate complex processes, making it easy to streamline repetitive modules and execute them parallelly if the commands do not depend on each other.
To install Rayder, ensure you have Go (1.16 or higher) installed on your system. Then, run the following command:
go install github.com/devanshbatham/rayder@v0.0.4Rayder offers a straightforward way to execute workflows defined in YAML files. Use the following command:
rayder -w path/to/workflow.yamlA workflow is defined in a YAML file with the following structure:
vars:
VAR_NAME: value
# Add more variables...
parallel: true|false
modules:
- name: task-name
cmds:
- command-1
- command-2
# Add more commands...
silent: true|false
# Add more modules...Rayder allows you to use variables in your workflow configuration, making it easy to parameterize your commands and achieve more flexibility. You can define variables in the vars section of your workflow YAML file. These variables can then be referenced within your command strings using double curly braces ({{}}).
To define variables, add them to the vars section of your workflow YAML file:
vars:
VAR_NAME: value
ANOTHER_VAR: another_value
# Add more variables...You can reference variables within your command strings using double curly braces ({{}}). For example, if you defined a variable OUTPUT_DIR, you can use it like this:
modules:
- name: example-task
cmds:
- echo "Output directory {{OUTPUT_DIR}}"You can also supply values for variables via the command line when executing your workflow. Use the format VARIABLE_NAME=value to provide values for specific variables. For example:
rayder -w path/to/workflow.yaml VAR_NAME=new_value ANOTHER_VAR=updated_valueIf you don't provide values for variables via the command line, Rayder will automatically apply default values defined in the vars section of your workflow YAML file.
Remember that variables supplied via the command line will override the default values defined in the YAML configuration.
Here's an example of how you can define, reference, and supply variables in your workflow configuration:
vars:
ORG: "example.org"
OUTPUT_DIR: "results"
modules:
- name: example-task
cmds:
- echo "Organization {{ORG}}"
- echo "Output directory {{OUTPUT_DIR}}"When executing the workflow, you can provide values for ORG and OUTPUT_DIR via the command line like this:
rayder -w path/to/workflow.yaml ORG=custom_org OUTPUT_DIR=custom_results_dirThis will override the default values and use the provided values for these variables.
Here's an example workflow configuration tailored for reverse whois recon and processing the root domains into subdomains, resolving them and checking which ones are alive:
vars:
ORG: "Acme, Inc"
OUTPUT_DIR: "results-dir"
parallel: false
modules:
- name: reverse-whois
silent: false
cmds:
- mkdir -p {{OUTPUT_DIR}}
- revwhoix -k "{{ORG}}" > {{OUTPUT_DIR}}/root-domains.txt
- name: finding-subdomains
cmds:
- xargs -I {} -a {{OUTPUT_DIR}}/root-domains.txt echo "subfinder -d {} -o {}.out" | quaithe -workers 30
silent: false
- name: cleaning-subdomains
cmds:
- cat *.out > {{OUTPUT_DIR}}/root-subdomains.txt
- rm *.out
silent: true
- name: resolving-subdomains
cmds:
- cat {{OUTPUT_DIR}}/root-subdomains.txt | dnsx -silent -threads 100 -o {{OUTPUT_DIR}}/resolved-subdomains.txt
silent: false
- name: checking-alive-subdomains
cmds:
- cat {{OUTPUT_DIR}}/resolved-subdomains.txt | httpx -silent -threads 100 0 -o {{OUTPUT_DIR}}/alive-subdomains.txt
silent: falseTo execute the above workflow, run the following command:
rayder -w path/to/reverse-whois.yaml ORG="Yelp, Inc" OUTPUT_DIR=resultsThe parallel field in the workflow configuration determines whether modules should be executed in parallel or sequentially. Setting parallel to true allows modules to run concurrently, making it suitable for modules with no dependencies. When set to false, modules will execute one after another.
Explore a collection of sample workflows and examples in the Rayder workflows repository. Stay tuned for more additions!
Inspiration of this project comes from Awesome taskfile project.
RansomwareSim is a simulated ransomware application developed for educational and training purposes. It is designed to demonstrate how ransomware encrypts files on a system and communicates with a command-and-control server. This tool is strictly for educational use and should not be used for malicious purposes.
Important: This tool should only be used in controlled environments where all participants have given consent. Do not use this tool on any system without explicit permission. For more, read SECURE
Clone the repository:
git clone https://github.com/HalilDeniz/RansomwareSim.gitNavigate to the project directory:
cd RansomwareSimInstall the required dependencies:
pip install -r requirements.txtcontrolpanel.py.controlpanel.py.RansomwareSim and the Decoder.RansomwareSim.main function in encoder.py to specify the target directory and other parameters.encoder.py to start the encryption process.decoder.py after the files have been encrypted.RansomwareSim is developed for educational purposes only. The creators of RansomwareSim are not responsible for any misuse of this tool. This tool should not be used in any unauthorized or illegal manner. Always ensure ethical and legal use of this tool.
Contributions, suggestions, and feedback are welcome. Please create an issue or pull request for any contributions.
For any inquiries or further information, you can reach me through the following channels:
T3SF is a framework that offers a modular structure for the orchestration of events based on a master scenario events list (MSEL) together with a set of rules defined for each exercise (optional) and a configuration that allows defining the parameters of the corresponding platform. The main module performs the communication with the specific module (Discord, Slack, Telegram, etc.) that allows the events to present the events in the input channels as injects for each platform. In addition, the framework supports different use cases: "single organization, multiple areas", "multiple organization, single area" and "multiple organization, multiple areas".
To use the framework with your desired platform, whether it's Slack or Discord, you will need to install the required modules for that platform. But don't worry, installing these modules is easy and straightforward.
To do this, you can follow this simple step-by-step guide, or if you're already comfortable installing packages with pip, you can skip to the last step!
# Python 3.6+ required
python -m venv .venv # We will create a python virtual environment
source .venv/bin/activate # Let's get inside it
pip install -U pip # Upgrade pipOnce you have created a Python virtual environment and activated it, you can install the T3SF framework for your desired platform by running the following command:
pip install "T3SF[Discord]" # Install the framework to work with Discordor
pip install "T3SF[Slack]" # Install the framework to work with SlackThis will install the T3SF framework along with the required dependencies for your chosen platform. Once the installation is complete, you can start using the framework with your platform of choice.
We strongly recommend following the platform-specific guidance within our Read The Docs! Here are the links:
We created this framework to simplify all your work!
$ docker run --rm -t --env-file .env -v $(pwd)/MSEL.json:/app/MSEL.json base4sec/t3sf:slackInside your .env file you have to provide the SLACK_BOT_TOKEN and SLACK_APP_TOKEN tokens. Read more about it here.
There is another environment variable to set, MSEL_PATH. This variable tells the framework in which path the MSEL is located. By default, the container path is /app/MSEL.json. If you change the mount location of the volume then also change the variable.
$ docker run --rm -t --env-file .env -v $(pwd)/MSEL.json:/app/MSEL.json base4sec/t3sf:discordInside your .env file you have to provide the DISCORD_TOKEN token. Read more about it here.
There is another environment variable to set, MSEL_PATH. This variable tells the framework in which path the MSEL is located. By default, the container path is /app/MSEL.json. If you change the mount location of the volume then also change the variable.
Once you have everything ready, use our template for the main.py, or modify the following code:
Here is an example if you want to run the framework with the Discord bot and a GUI.
from T3SF import T3SF
import asyncio
async def main():
await T3SF.start(MSEL="MSEL_TTX.json", platform="Discord", gui=True)
if __name__ == '__main__':
asyncio.run(main())Or if you prefer to run the framework without GUI and with Slack instead, you can modify the arguments, and that's it!
Yes, that simple!
await T3SF.start(MSEL="MSEL_TTX.json", platform="Slack", gui=False)If you need more help, you can always check our documentation here!
Arsenal is just a quick inventory, reminder and launcher for pentest commands.
This project written by pentesters for pentesters simplify the use of all the hard-to-remember commands
In arsenal you can search for a command, select one and it's prefilled directly in your terminal. This functionality is independent of the shell used. Indeed arsenal emulates real user input (with TTY arguments and IOCTL) so arsenal works with all shells and your commands will be in the history.
You have to enter arguments if needed, but arsenal supports global variables.
For example, during a pentest we can set the variable ip to prefill all commands using an ip with the right one.
To do that you just have to enter the following command in arsenal:
>set ip=10.10.10.10
Authors:
This project is inspired by navi (https://github.com/denisidoro/navi) because the original version was in bash and too hard to understand to add features
<argument|default_value>
python3 -m pip install arsenal-cli
alias a='arsenal')arsenal
git clone https://github.com/Orange-Cyberdefense/arsenal.git
cd arsenal
python3 -m pip install -r requirements.txt
./run
Inside your .bashrc or .zshrc add the path to run to help you do that you could launch the addalias.sh script
./addalias.sh
git clone https://aur.archlinux.org/arsenal.git
cd arsenal
makepkg -siyay -S arsenal./run -t # if you launch arsenal in a tmux window with one pane, it will split the window and send the command to the otherpane without quitting arsenal
# if the window is already splited the command will be send to the other pane without quitting arsenal
./run -t -e # just like the -t mode but with direct execution in the other pane without quitting arsenal
You could add your own cheatsheets insode the my_cheats folder or in the ~/.cheats folder.
You could also add additional paths to the file <arsenal_home>/arsenal/modules/config.py, arsenal reads .md (MarkDown) and .rst (RestructuredText).
<arsenal_home>/cheats: README.md and README.rst If you got on error on color init try :
export TERM='xterm-256color'
--
If you have the following exception when running Arsenal:
ImportError: cannot import name 'FullLoader'
First, check that requirements are installed:
pip install -r requirements.txt
If the exception is still there:
pip install -U PyYAML
https://orange-cyberdefense.github.io/ocd-mindmaps/img/pentest_ad_dark_2022_11.svg
AD mindmap black version
Exchange Mindmap (thx to @snovvcrash)
Active directory ACE mindmap
DoSinator is a versatile Denial of Service (DoS) testing tool developed in Python. It empowers security professionals and researchers to simulate various types of DoS attacks, allowing them to assess the resilience of networks, systems, and applications against potential cyber threats.
Clone the repository:
git clone https://github.com/HalilDeniz/DoSinator.gitNavigate to the project directory:
cd DoSinatorInstall the required dependencies:
pip install -r requirements.txtusage: dos_tool.py [-h] -t TARGET -p PORT [-np NUM_PACKETS] [-ps PACKET_SIZE]
[-ar ATTACK_RATE] [-d DURATION] [-am {syn,udp,icmp,http,dns}]
[-sp SPOOF_IP] [--data DATA]
optional arguments:
-h, --help Show this help message and exit.
-t TARGET, --target TARGET
Target IP address.
-p PORT, --port PORT Target port number.
-np NUM_PACKETS, --num_packets NUM_PACKETS
Number of packets to send (default: 500).
-ps PACKET_SIZE, --packet_size PACKET_SIZE
Packet size in bytes (default: 64).
-ar ATTACK_RATE, --attack_rate ATTACK_RATE
Attack rate in packets per second (default: 10).
-d DURATION, --duration DURATION
Duration of the attack in seconds.
-am {syn,udp,icmp,htt p,dns}, --attack-mode {syn,udp,icmp,http,dns}
Attack mode (default: syn).
-sp SPOOF_IP, --spoof-ip SPOOF_IP
Spoof IP address.
--data DATA Custom data string to send.target_ip: IP address of the target system.target_port: Port number of the target service.num_packets: Number of packets to send (default: 500).packet_size: Size of each packet in bytes (default: 64).attack_rate: Attack rate in packets/second (default: 10).duration: Duration of the attack in seconds.attack_mode: Attack mode: syn, udp, icmp, http (default: syn).spoof_ip: Spoof IP address (default: None).data: Custom data string to send.The usage of the Dosinator tool for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state, and federal laws. The author assumes no liability and is not responsible for any misuse or damage caused by this program.
By using Dosinator, you agree to use this tool for educational and ethical purposes only. The author is not responsible for any actions or consequences resulting from misuse of this tool.
Please ensure that you have the necessary permissions to conduct any form of testing on a target network. Use this tool at your own risk.
Contributions are welcome! If you find any issues or have suggestions for improvements, feel free to open an issue or submit a pull request.
If you have any questions, comments, or suggestions about Dosinator, please feel free to contact me:
Upload_Bypass is a powerful tool designed to assist Pentesters and Bug Hunters in testing file upload mechanisms. It leverages various bug bounty techniques to simplify the process of identifying and exploiting vulnerabilities, ensuring thorough assessments of web applications.
Please note that the use of Upload_Bypass and any actions taken with it are solely at your own risk. The tool is provided for educational and testing purposes only. The developer of Upload_Bypass is not responsible for any misuse, damage, or illegal activities caused by its usage.
While Upload_Bypass aims to assist Pentesters and Bug Hunters in testing file upload mechanisms, it is essential to obtain proper authorization and adhere to applicable laws and regulations before performing any security assessments. Always ensure that you have the necessary permissions from the relevant stakeholders before conducting any testing activities.
The results and findings obtained from using Upload_Bypass should be communicated responsibly and in accordance with established disclosure processes. It is crucial to respect the privacy and integrity of the tested systems and refrain from causing harm or disruption.
By using Upload_Bypass, you acknowledge that the developer cannot be held liable for any consequences resulting from its use. Use the tool responsibly and ethically to promote the security and integrity of web applications.
Download the latest version from Releases page.
pip install -r requirements.txt
The tool will not function properly if the file upload mechanism includes CAPTCHA implementation.
Perhaps in the future the tool will include an OCR.
The Tool is compatible exclusively with output file requests generated by Burp Suite.
Before saving the Burp file, replace the file content with the string *content* and filename.ext with the string *filename* and Content-Type header with *mimetype*(only if the tool is not able to recognize it automatically).
How a request should look before the changes:
How it should look after the changes:
If the tool fails to recognize the mime type automatically, you can add *mimetype* in the parameter's value of the Content-Type header.
Options: -h, --help
show this help message and exit
-b BURP_FILE, --burp-file BURP_FILE
Required - Read from a Burp Suite file
Usage: -b / --burp-file ~/Desktop/output
-s SUCCESS_MESSAGE, --success SUCCESS_MESSAGE
Required if -f is not set - Provide the success message when a file is uploaded
Usage: -s /--success 'File uploaded successfully.'
-f FAILURE_MESSAGE, --failure FAILURE_MESSAGE
Required if -s is not set - Provide a failure message when a file is uploaded
Usage: -f /--failure 'File is not allowed!'
-e FILE_EXTENSION, --extension FILE_EXTENSION
Required - Provide server backend extension
Usage: -e / --extension php (Supported extensions: php,asp,jsp,perl,coldfusion)
-a ALLOWED_EXTENSIONS, --allowed ALLOWED_EXTENSIONS
Required - Provide allowed extensions to be uploaded
Usage: -a /--allowed jpeg, png, zip, etc'
-l WEBSHELL_LOCATION, --location WEBSHELL_LOCATION
Provide a remote path where the WebShell will be uploaded (won't work if the file will be uploaded with a UUID).
Usage: -l / --location /uploads/
-rl NUMBER, --rate-limit NUMBER
Set rate-limiting with milliseconds between each request.
Usage: -r / --rate-limit 700
-p PROXY_NUM, --proxy PROXY_NUM
Channel the HTTP requests via proxy client (i.e Burp Suite).
Usage: -p / --proxy http://127.0.0.1:8080
-S, --ssl
If set, the tool will not validate TLS/SSL certificate.
Usage: -S / --ssl
-c, --continue
If set, the brute force will continue even if one of the methods gets a hit!
Usage: -C /--continue
-E, --eicar
If set, an Eicar file(Anti Malware Testfile) will be uploaded only. WebShells will not be uploaded (Suitable for real environments).
Usage: -E / --eicar
-v, --verbose
If set, details about the test will be printed on the screen
Usage: -v / --verbose
-r, --response
If set, HTTP response will be printed on the screen
Usage: -r / --response
--version
Print the current version of the tool.
--update
Checks for new updates. If there is a new update, it will be downloaded and updated automatically.
python upload_bypass.py -b ~/Desktop/burp_output -s 'file upload successfully!' -e php -a jpeg --response -v --eicar --continue
python upload_bypass.py -b ~/Desktop/burp_output -s 'file upload successfully!' -e asp -a zip -v
python upload_bypass.py -b ~/Desktop/burp_output -s 'file upload successfully!' -e jsp -a png -v --proxy http://127.0.0.1:8080
















