A sprawling academic cheating network turbocharged by Google Ads that has generated nearly $25 million in revenue has curious ties to a Kremlin-connected oligarch whose Russian university builds drones for Russia’s war against Ukraine.
The Nerdify homepage.
The link between essay mills and Russian attack drones might seem improbable, but understanding it begins with a simple question: How does a human-intensive academic cheating service stay relevant in an era when students can simply ask AI to write their term papers? The answer – recasting the business as an AI company – is just the latest chapter in a story of many rebrands that link the operation to Russia’s largest private university.
Search in Google for any terms related to academic cheating services — e.g., “help with exam online” or “term paper online” — and you’re likely to encounter websites with the words “nerd” or “geek” in them, such as thenerdify[.]com and geekly-hub[.]com. With a simple request sent via text message, you can hire their tutors to help with any assignment.
These nerdy and geeky-branded websites frequently cite their “honor code,” which emphasizes they do not condone academic cheating, will not write your term papers for you, and will only offer support and advice for customers. But according to This Isn’t Fine, a Substack blog about contract cheating and essay mills, the Nerdify brand of websites will happily ignore that mantra.
“We tested the quick SMS for a price quote,” wrote This Isn’t Fine author Joseph Thibault. “The honor code references and platitudes apparently stop at the website. Within three minutes, we confirmed that a full three-page, plagiarism- and AI-free MLA formatted Argumentative essay could be ours for the low price of $141.”
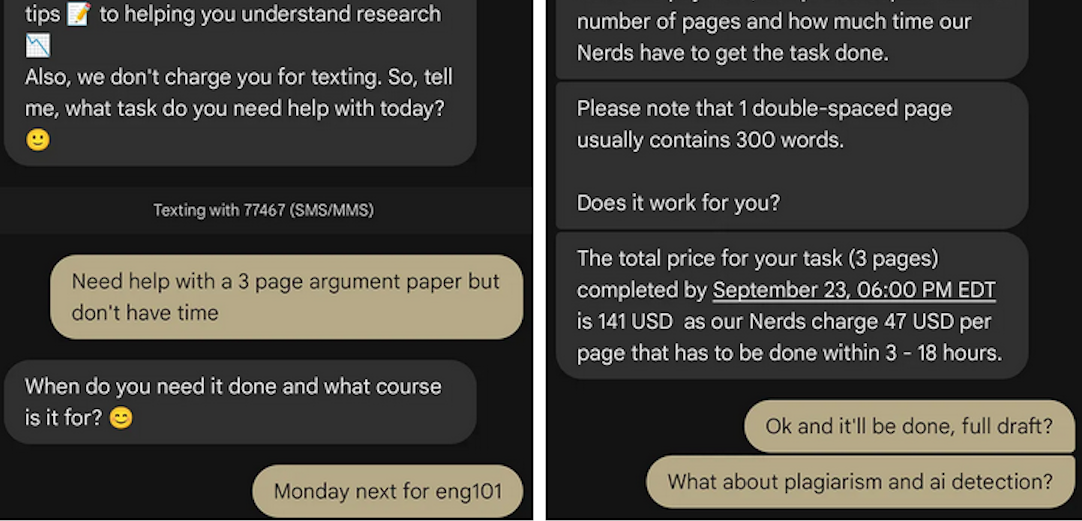
A screenshot from Joseph Thibault’s Substack post shows him purchasing a 3-page paper with the Nerdify service.
Google prohibits ads that “enable dishonest behavior.” Yet, a sprawling global essay and homework cheating network run under the Nerdy brands has quietly bought its way to the top of Google searches – booking revenues of almost $25 million through a maze of companies in Cyprus, Malta and Hong Kong, while pitching “tutoring” that delivers finished work that students can turn in.
When one Nerdy-related Google Ads account got shut down, the group behind the company would form a new entity with a front-person (typically a young Ukrainian woman), start a new ads account along with a new website and domain name (usually with “nerdy” in the brand), and resume running Google ads for the same set of keywords.
UK companies belonging to the group that have been shut down by Google Ads since Jan 2025 include:
–Proglobal Solutions LTD (advertised nerdifyit[.]com);
–AW Tech Limited (advertised thenerdify[.]com);
–Geekly Solutions Ltd (advertised geekly-hub[.]com).
Currently active Google Ads accounts for the Nerdify brands include:
-OK Marketing LTD (advertising geekly-hub[.]net), formed in the name of Olha Karpenko, a young Ukrainian woman;
–Two Sigma Solutions LTD (advertising litero[.]ai), formed in the name of Olekszij (Alexey) Pokatilo.
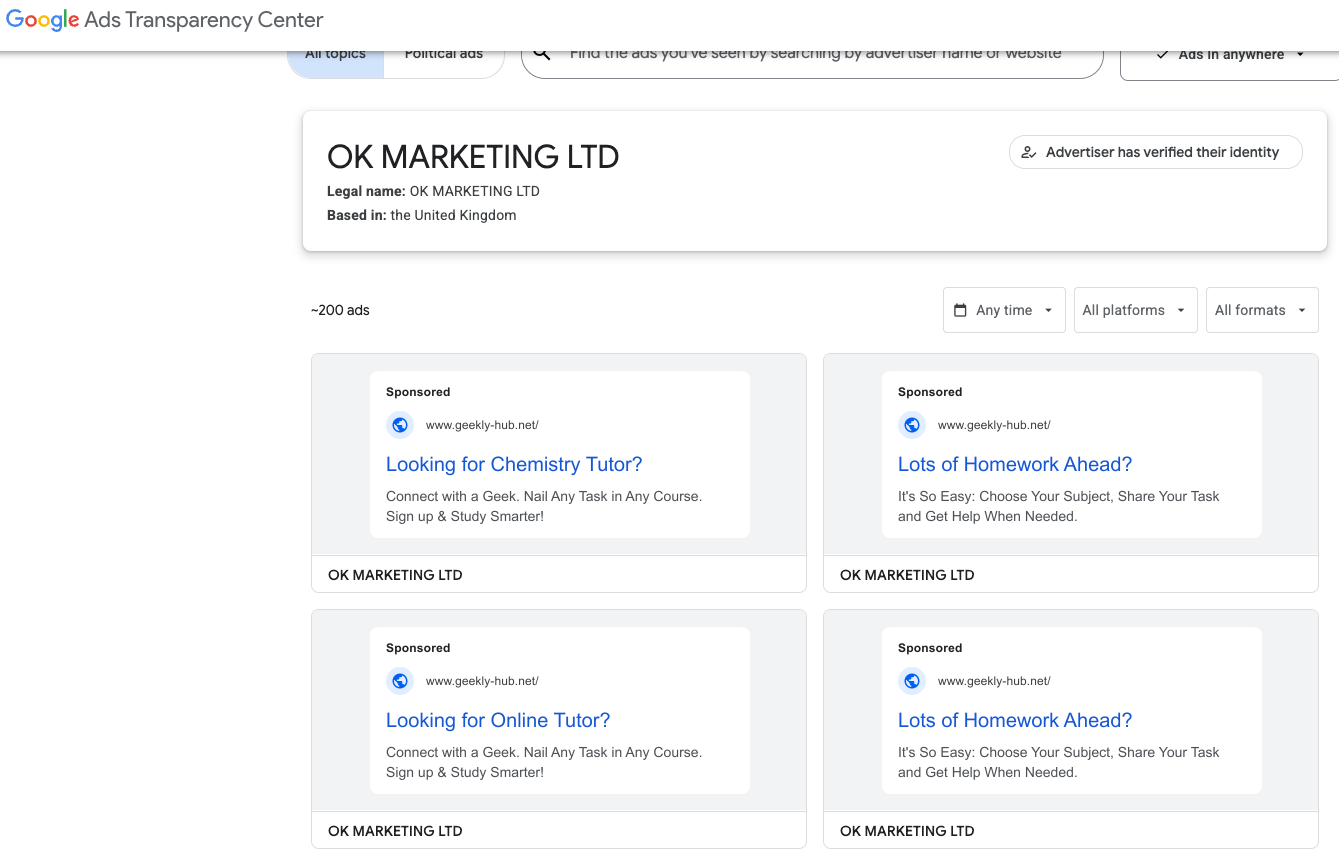
Google’s Ads Transparency page for current Nerdify advertiser OK Marketing LTD.
Mr. Pokatilo has been in the essay-writing business since at least 2009, operating a paper-mill enterprise called Livingston Research alongside Alexander Korsukov, who is listed as an owner. According to a lengthy account from a former employee, Livingston Research mainly farmed its writing tasks out to low-cost workers from Kenya, Philippines, Pakistan, Russia and Ukraine.
Pokatilo moved from Ukraine to the United Kingdom in Sept. 2015 and co-founded a company called Awesome Technologies, which pitched itself as a way for people to outsource tasks by sending a text message to the service’s assistants.
The other co-founder of Awesome Technologies is 36-year-old Filip Perkon, a Swedish man living in London who touts himself as a serial entrepreneur and investor. Years before starting Awesome together, Perkon and Pokatilo co-founded a student group called Russian Business Week while the two were classmates at the London School of Economics. According to the Bulgarian investigative journalist Christo Grozev, Perkon’s birth certificate was issued by the Soviet Embassy in Sweden.

Alexey Pokatilo (left) and Filip Perkon at a Facebook event for startups in San Francisco in mid-2015.
Around the time Perkon and Pokatilo launched Awesome Technologies, Perkon was building a social media propaganda tool called the Russian Diplomatic Online Club, which Perkon said would “turbo-charge” Russian messaging online. The club’s newsletter urged subscribers to install in their Twitter accounts a third-party app called Tweetsquad that would retweet Kremlin messaging on the social media platform.
Perkon was praised by the Russian Embassy in London for his efforts: During the contentious Brexit vote that ultimately led to the United Kingdom leaving the European Union, the Russian embassy in London used this spam tweeting tool to auto-retweet the Russian ambassador’s posts from supporters’ accounts.
Neither Mr. Perkon nor Mr. Pokatilo replied to requests for comment.
A review of corporations tied to Mr. Perkon as indexed by the business research service North Data finds he holds or held director positions in several U.K. subsidiaries of Synergy University, Russia’s largest private education provider. Synergy has more than 35,000 students, and sells T-shirts with patriotic slogans such as “Crimea is Ours,” and “The Russian Empire — Reloaded.”
The president of Synergy University is Vadim Lobov, a Kremlin insider whose headquarters on the outskirts of Moscow reportedly features a wall-sized portrait of Russian President Vladimir Putin in the pop-art style of Andy Warhol. For a number of years, Lobov and Perkon co-produced a cross-cultural event in the U.K. called Russian Film Week.

Synergy President Vadim Lobov and Filip Perkon, speaking at a press conference for Russian Film Week, a cross-cultural event in the U.K. co-produced by both men.
Mr. Lobov was one of 11 individuals reportedly hand-picked by the convicted Russian spy Marina Butina to attend the 2017 National Prayer Breakfast held in Washington D.C. just two weeks after President Trump’s first inauguration.
While Synergy University promotes itself as Russia’s largest private educational institution, hundreds of international students tell a different story. Online reviews from students paint a picture of unkept promises: Prospective students from Nigeria, Kenya, Ghana, and other nations paying thousands in advance fees for promised study visas to Russia, only to have their applications denied with no refunds offered.
“My experience with Synergy University has been nothing short of heartbreaking,” reads one such account. “When I first discovered the school, their representative was extremely responsive and eager to assist. He communicated frequently and made me believe I was in safe hands. However, after paying my hard-earned tuition fees, my visa was denied. It’s been over 9 months since that denial, and despite their promises, I have received no refund whatsoever. My messages are now ignored, and the same representative who once replied instantly no longer responds at all. Synergy University, how can an institution in Europe feel comfortable exploiting the hopes of Africans who trust you with their life savings? This is not just unethical — it’s predatory.”
This pattern repeats across reviews by multilingual students from Pakistan, Nepal, India, and various African nations — all describing the same scheme: Attractive online marketing, promises of easy visa approval, upfront payment requirements, and then silence after visa denials.
Reddit discussions in r/Moscow and r/AskARussian are filled with warnings. “It’s a scam, a diploma mill,” writes one user. “They literally sell exams. There was an investigation on Rossiya-1 television showing students paying to pass tests.”
The Nerdify website’s “About Us” page says the company was co-founded by Pokatilo and an American named Brian Mellor. The latter identity seems to have been fabricated, or at least there is no evidence that a person with this name ever worked at Nerdify.
Rather, it appears that the SMS assistance company co-founded by Messrs. Pokatilo and Perkon (Awesome Technologies) fizzled out shortly after its creation, and that Nerdify soon adopted the process of accepting assignment requests via text message and routing them to freelance writers.
A closer look at an early “About Us” page for Nerdify in The Wayback Machine suggests that Mr. Perkon was the real co-founder of the company: The photo at the top of the page shows four people wearing Nerdify T-shirts seated around a table on a rooftop deck in San Francisco, and the man facing the camera is Perkon.

Filip Perkon, top right, is pictured wearing a Nerdify T-shirt in an archived copy of the company’s About Us page. Image: archive.org.
Where are they now? Pokatilo is currently running a startup called Litero.Ai, which appears to be an AI-based essay writing service. In July 2025, Mr. Pokatilo received pre-seed funding of $800,000 for Litero from an investment program backed by the venture capital firms AltaIR Capital, Yellow Rocks, Smart Partnership Capital, and I2BF Global Ventures.
Meanwhile, Filip Perkon is busy setting up toy rubber duck stores in Miami and in at least three locations in the United Kingdom. These “Duck World” shops market themselves as “the world’s largest duck store.”
This past week, Mr. Lobov was in India with Putin’s entourage on a charm tour with India’s Prime Minister Narendra Modi. Although Synergy is billed as an educational institution, a review of the company’s sprawling corporate footprint (via DNS) shows it also is assisting the Russian government in its war against Ukraine.

Synergy University President Vadim Lobov (right) pictured this week in India next to Natalia Popova, a Russian TV presenter known for her close ties to Putin’s family, particularly Putin’s daughter, who works with Popova at the education and culture-focused Innopraktika Foundation.
The website bpla.synergy[.]bot, for instance, says the company is involved in developing combat drones to aid Russian forces and to evade international sanctions on the supply and re-export of high-tech products.
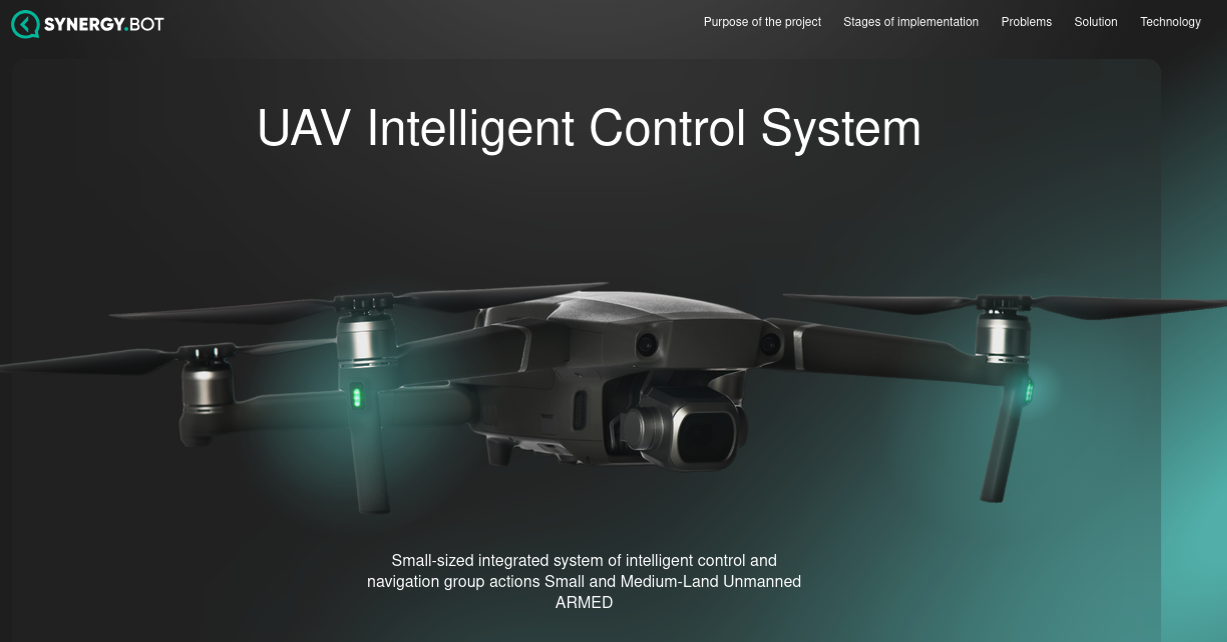
A screenshot from the website of synergy,bot shows the company is actively engaged in building armed drones for the war in Ukraine.
KrebsOnSecurity would like to thank the anonymous researcher NatInfoSec for their assistance in this investigation.
Update, Dec. 8, 10:06 a.m. ET: Mr. Pokatilo responded to requests for comment after the publication of this story. Pokatilo said he has no relation to Synergy nor to Mr. Lobov, and that his work with Mr. Perkon ended with the dissolution of Awesome Technologies.
“I have had no involvement in any of his projects and business activities mentioned in the article and he has no involvement in Litero.ai,” Pokatilo said of Perkon.
Mr. Pokatilo said his new company Litero “does not provide contract cheating services and is built specifically to improve transparency and academic integrity in the age of universal use of AI by students.”
“I am Ukrainian,” he said in an email. “My close friends, colleagues, and some family members continue to live in Ukraine under the ongoing invasion. Any suggestion that I or my company may be connected in any way to Russia’s war efforts is deeply offensive on a personal level and harmful to the reputation of Litero.ai, a company where many team members are Ukrainian.”
Update, Dec. 11, 12:07 p.m. ET: Mr. Perkon responded to requests for comment after the publication of this story. Perkon said the photo of him in a Nerdify T-shirt (see screenshot above) was taken after a startup event in San Francisco, where he volunteered to act as a photo model to help friends with their project.
“I have no business or other relations to Nerdify or any other ventures in that space,” Mr. Perkon said in an email response. “As for Vadim Lobov, I worked for Venture Capital arm at Synergy until 2013 as well as his business school project in the UK, that didn’t get off the ground, so the company related to this was made dormant. Then Synergy kindly provided sponsorship for my Russian Film Week event that I created and ran until 2022 in the U.K., an event that became the biggest independent Russian film festival outside of Russia. Since the start of the Ukraine war in 2022 I closed the festival down.”
“I have had no business with Vadim Lobov since 2021 (the last film festival) and I don’t keep track of his endeavours,” Perkon continued. “As for Alexey Pokatilo, we are university friends. Our business relationship has ended after the concierge service Awesome Technologies didn’t work out, many years ago.”
An intermittent outage at Cloudflare on Tuesday briefly knocked many of the Internet’s top destinations offline. Some affected Cloudflare customers were able to pivot away from the platform temporarily so that visitors could still access their websites. But security experts say doing so may have also triggered an impromptu network penetration test for organizations that have come to rely on Cloudflare to block many types of abusive and malicious traffic.
At around 6:30 EST/11:30 UTC on Nov. 18, Cloudflare’s status page acknowledged the company was experiencing “an internal service degradation.” After several hours of Cloudflare services coming back up and failing again, many websites behind Cloudflare found they could not migrate away from using the company’s services because the Cloudflare portal was unreachable and/or because they also were getting their domain name system (DNS) services from Cloudflare.
However, some customers did manage to pivot their domains away from Cloudflare during the outage. And many of those organizations probably need to take a closer look at their web application firewall (WAF) logs during that time, said Aaron Turner, a faculty member at IANS Research.
Turner said Cloudflare’s WAF does a good job filtering out malicious traffic that matches any one of the top ten types of application-layer attacks, including credential stuffing, cross-site scripting, SQL injection, bot attacks and API abuse. But he said this outage might be a good opportunity for Cloudflare customers to better understand how their own app and website defenses may be failing without Cloudflare’s help.
“Your developers could have been lazy in the past for SQL injection because Cloudflare stopped that stuff at the edge,” Turner said. “Maybe you didn’t have the best security QA [quality assurance] for certain things because Cloudflare was the control layer to compensate for that.”
Turner said one company he’s working with saw a huge increase in log volume and they are still trying to figure out what was “legit malicious” versus just noise.
“It looks like there was about an eight hour window when several high-profile sites decided to bypass Cloudflare for the sake of availability,” Turner said. “Many companies have essentially relied on Cloudflare for the OWASP Top Ten [web application vulnerabilities] and a whole range of bot blocking. How much badness could have happened in that window? Any organization that made that decision needs to look closely at any exposed infrastructure to see if they have someone persisting after they’ve switched back to Cloudflare protections.”
Turner said some cybercrime groups likely noticed when an online merchant they normally stalk stopped using Cloudflare’s services during the outage.
“Let’s say you were an attacker, trying to grind your way into a target, but you felt that Cloudflare was in the way in the past,” he said. “Then you see through DNS changes that the target has eliminated Cloudflare from their web stack due to the outage. You’re now going to launch a whole bunch of new attacks because the protective layer is no longer in place.”
Nicole Scott, senior product marketing manager at the McLean, Va. based Replica Cyber, called yesterday’s outage “a free tabletop exercise, whether you meant to run one or not.”
“That few-hour window was a live stress test of how your organization routes around its own control plane and shadow IT blossoms under the sunlamp of time pressure,” Scott said in a post on LinkedIn. “Yes, look at the traffic that hit you while protections were weakened. But also look hard at the behavior inside your org.”
Scott said organizations seeking security insights from the Cloudflare outage should ask themselves:
1. What was turned off or bypassed (WAF, bot protections, geo blocks), and for how long?
2. What emergency DNS or routing changes were made, and who approved them?
3. Did people shift work to personal devices, home Wi-Fi, or unsanctioned Software-as-a-Service providers to get around the outage?
4. Did anyone stand up new services, tunnels, or vendor accounts “just for now”?
5. Is there a plan to unwind those changes, or are they now permanent workarounds?
6. For the next incident, what’s the intentional fallback plan, instead of decentralized improvisation?
In a postmortem published Tuesday evening, Cloudflare said the disruption was not caused, directly or indirectly, by a cyberattack or malicious activity of any kind.
“Instead, it was triggered by a change to one of our database systems’ permissions which caused the database to output multiple entries into a ‘feature file’ used by our Bot Management system,” Cloudflare CEO Matthew Prince wrote. “That feature file, in turn, doubled in size. The larger-than-expected feature file was then propagated to all the machines that make up our network.”
Cloudflare estimates that roughly 20 percent of websites use its services, and with much of the modern web relying heavily on a handful of other cloud providers including AWS and Azure, even a brief outage at one of these platforms can create a single point of failure for many organizations.
Martin Greenfield, CEO at the IT consultancy Quod Orbis, said Tuesday’s outage was another reminder that many organizations may be putting too many of their eggs in one basket.
“There are several practical and overdue fixes,” Greenfield advised. “Split your estate. Spread WAF and DDoS protection across multiple zones. Use multi-vendor DNS. Segment applications so a single provider outage doesn’t cascade. And continuously monitor controls to detect single-vendor dependency.”
The U.S. government is reportedly preparing to ban the sale of wireless routers and other networking gear from TP-Link Systems, a tech company that currently enjoys an estimated 50% market share among home users and small businesses. Experts say while the proposed ban may have more to do with TP-Link’s ties to China than any specific technical threats, much of the rest of the industry serving this market also sources hardware from China and ships products that are insecure fresh out of the box.

A TP-Link WiFi 6 AX1800 Smart WiFi Router (Archer AX20).
The Washington Post recently reported that more than a half-dozen federal departments and agencies were backing a proposed ban on future sales of TP-Link devices in the United States. The story said U.S. Department of Commerce officials concluded TP-Link Systems products pose a risk because the U.S.-based company’s products handle sensitive American data and because the officials believe it remains subject to jurisdiction or influence by the Chinese government.
TP-Link Systems denies that, saying that it fully split from the Chinese TP-Link Technologies over the past three years, and that its critics have vastly overstated the company’s market share (TP-Link puts it at around 30 percent). TP-Link says it has headquarters in California, with a branch in Singapore, and that it manufactures in Vietnam. The company says it researches, designs, develops and manufactures everything except its chipsets in-house.
TP-Link Systems told The Post it has sole ownership of some engineering, design and manufacturing capabilities in China that were once part of China-based TP-Link Technologies, and that it operates them without Chinese government supervision.
“TP-Link vigorously disputes any allegation that its products present national security risks to the United States,” Ricca Silverio, a spokeswoman for TP-Link Systems, said in a statement. “TP-Link is a U.S. company committed to supplying high-quality and secure products to the U.S. market and beyond.”
Cost is a big reason TP-Link devices are so prevalent in the consumer and small business market: As this February 2025 story from Wired observed regarding the proposed ban, TP-Link has long had a reputation for flooding the market with devices that are considerably cheaper than comparable models from other vendors. That price point (and consistently excellent performance ratings) has made TP-Link a favorite among Internet service providers (ISPs) that provide routers to their customers.
In August 2024, the chairman and the ranking member of the House Select Committee on the Strategic Competition Between the United States and the Chinese Communist Party called for an investigation into TP-Link devices, which they said were found on U.S. military bases and for sale at exchanges that sell them to members of the military and their families.
“TP-Link’s unusual degree of vulnerabilities and required compliance with PRC law are in and of themselves disconcerting,” the House lawmakers warned in a letter (PDF) to the director of the Commerce Department. “When combined with the PRC government’s common use of SOHO [small office/home office] routers like TP-Link to perpetrate extensive cyberattacks in the United States, it becomes significantly alarming.”
The letter cited a May 2023 blog post by Check Point Research about a Chinese state-sponsored hacking group dubbed “Camaro Dragon” that used a malicious firmware implant for some TP-Link routers to carry out a sequence of targeted cyberattacks against European foreign affairs entities. Check Point said while it only found the malicious firmware on TP-Link devices, “the firmware-agnostic nature of the implanted components indicates that a wide range of devices and vendors may be at risk.”
In a report published in October 2024, Microsoft said it was tracking a network of compromised TP-Link small office and home office routers that has been abused by multiple distinct Chinese state-sponsored hacking groups since 2021. Microsoft found the hacker groups were leveraging the compromised TP-Link systems to conduct “password spraying” attacks against Microsoft accounts. Password spraying involves rapidly attempting to access a large number of accounts (usernames/email addresses) with a relatively small number of commonly used passwords.
TP-Link rightly points out that most of its competitors likewise source components from China. The company also correctly notes that advanced persistent threat (APT) groups from China and other nations have leveraged vulnerabilities in products from their competitors, such as Cisco and Netgear.
But that may be cold comfort for TP-Link customers who are now wondering if it’s smart to continue using these products, or whether it makes sense to buy more costly networking gear that might only be marginally less vulnerable to compromise.
Almost without exception, the hardware and software that ships with most consumer-grade routers includes a number of default settings that need to be changed before the devices can be safely connected to the Internet. For example, bring a new router online without changing the default username and password and chances are it will only take a few minutes before it is probed and possibly compromised by some type of Internet-of-Things botnet. Also, it is incredibly common for the firmware in a brand new router to be dangerously out of date by the time it is purchased and unboxed.
Until quite recently, the idea that router manufacturers should make it easier for their customers to use these products safely was something of an anathema to this industry. Consumers were largely left to figure that out on their own, with predictably disastrous results.
But over the past few years, many manufacturers of popular consumer routers have begun forcing users to perform basic hygiene — such as changing the default password and updating the internal firmware — before the devices can be used as a router. For example, most brands of “mesh” wireless routers — like Amazon’s Eero, Netgear’s Orbi series, or Asus’s ZenWifi — require online registration that automates these critical steps going forward (or at least through their stated support lifecycle).
For better or worse, less expensive, traditional consumer routers like those from Belkin and Linksys also now automate this setup by heavily steering customers toward installing a mobile app to complete the installation (this often comes as a shock to people more accustomed to manually configuring a router). Still, these products tend to put the onus on users to check for and install available updates periodically. Also, they’re often powered by underwhelming or else bloated firmware, and a dearth of configurable options.
Of course, not everyone wants to fiddle with mobile apps or is comfortable with registering their router so that it can be managed or monitored remotely in the cloud. For those hands-on folks — and for power users seeking more advanced router features like VPNs, ad blockers and network monitoring — the best advice is to check if your router’s stock firmware can be replaced with open-source alternatives, such as OpenWrt or DD-WRT.
These open-source firmware options are compatible with a wide range of devices, and they generally offer more features and configurability. Open-source firmware can even help extend the life of routers years after the vendor stops supporting the underlying hardware, but it still requires users to manually check for and install any available updates.
Happily, TP-Link users spooked by the proposed ban may have an alternative to outright junking these devices, as many TP-Link routers also support open-source firmware options like OpenWRT. While this approach may not eliminate any potential hardware-specific security flaws, it could serve as an effective hedge against more common vendor-specific vulnerabilities, such as undocumented user accounts, hard-coded credentials, and weaknesses that allow attackers to bypass authentication.
Regardless of the brand, if your router is more than four or five years old it may be worth upgrading for performance reasons alone — particularly if your home or office is primarily accessing the Internet through WiFi.
NB: The Post’s story notes that a substantial portion of TP-Link routers and those of its competitors are purchased or leased through ISPs. In these cases, the devices are typically managed and updated remotely by your ISP, and equipped with custom profiles responsible for authenticating your device to the ISP’s network. If this describes your setup, please do not attempt to modify or replace these devices without first consulting with your Internet provider.
QuickResponseC2 is a stealthy Command and Control (C2) framework that enables indirect and covert communication between the attacker and victim machines via an intermediate HTTP/S server. All network activity is limited to uploading and downloading images, making it an fully undetectable by IPS/IDS Systems and an ideal tool for security research and penetration testing.
Command Execution via QR Codes:
Users can send custom commands to the victim machine, encoded as QR codes.
Victims scan the QR code, which triggers the execution of the command on their system.
The command can be anything from simple queries to complex operations based on the test scenario.
Result Retrieval:
Results of the executed command are returned from the victim system and encoded into a QR code.
The server decodes the result and provides feedback to the attacker for further analysis or follow-up actions.
Built-in HTTP Server:
The tool includes a lightweight HTTP server that facilitates the victim machine's retrieval of command QR codes.
Results are sent back to the server as QR code images, and they are automatically saved with unique filenames for easy management.
The attacker's machine handles multiple requests, with HTTP logs organized and saved separately.
Stealthy Communication:
QuickResponseC2 operates under the radar, with minimal traces, providing a covert way to interact with the victim machine without alerting security defenses.
Ideal for security assessments or testing command-and-control methodologies without being detected.
File Handling:
The tool automatically saves all QR codes (command and result) to the server_files directory, using sequential filenames like command0.png, command1.png, etc.
Decoding and processing of result files are handled seamlessly.
User-Friendly Interface:
The tool is operated via a simple command-line interface, allowing users to set up a C2 server, send commands, and receive results with ease.
No additional complex configurations or dependencies are needed.
pip3 install -r requirements.txt
python3 main.py
1 - Run the C2 Server
2 - Build the Victim Implant
https://github.com/user-attachments/assets/382e9350-d650-44e5-b8ef-b43ec90b315d
8080).commandX.png on the HTTP server.commandX.png), it downloads and decodes the image to retrieve the command.resultX.png.resultX.png).Feel free to fork and contribute! Pull requests are welcome.
OSINT Tool for research social media accounts by username
```Install Requests pip install requests
#### Install BeautifulSoup
```Install BeautifulSoup
pip install beautifulsoup4
Execute Snoop python3 snoop.py
Tool for obfuscating PowerShell scripts written in Go. The main objective of this program is to obfuscate PowerShell code to make its analysis and detection more difficult. The script offers 5 levels of obfuscation, from basic obfuscation to script fragmentation. This allows users to tailor the obfuscation level to their specific needs.
./psobf -h
██████╗ ███████╗ ██████╗ ██████╗ ███████╗
██╔══██╗██╔════╝██╔═══██╗██╔══██╗██╔════╝
██████╔╝███████╗██║ ██║██████╔╝█████╗
██╔═══╝ ╚════██║██║ ██║██╔══██╗██╔══╝
██║ ███████║╚██████╔╝██████╔╝██║
╚═╝ ╚══════╝ ╚═════╝ ╚═════╝ ╚═╝
@TaurusOmar
v.1.0
Usage: ./obfuscator -i <inputFile> -o <outputFile> -level <1|2|3|4|5>
Options:
-i string
Name of the PowerShell script file.
-level int
Obfuscation level (1 to 5). (default 1)
-o string
Name of the output file for the obfuscated script. (default "obfuscated.ps1")
Obfuscation levels:
1: Basic obfuscation by splitting the script into individual characters.
2: Base64 encoding of the script.
3: Alternative Base64 encoding with a different PowerShell decoding method.
4: Compression and Base64 encoding of the script will be decoded and decompressed at runtime.
5: Fragmentation of the script into multiple parts and reconstruction at runtime.
go install github.com/TaurusOmar/psobf@latest
The obfuscation levels are divided into 5 options. First, you need to have a PowerShell file that you want to obfuscate. Let's assume you have a file named script.ps1 with the following content:
Write-Host "Hello, World!"
Run the script with level 1 obfuscation.
./obfuscator -i script.ps1 -o obfuscated_level1.ps1 -level 1
This will generate a file named obfuscated_level1.ps1 with the obfuscated content. The result will be a version of your script where each character is separated by commas and combined at runtime.
Result (level 1)
$obfuscated = $([char[]]("`W`,`r`,`i`,`t`,`e`,`-`,`H`,`o`,`s`,`t`,` `,`"`,`H`,`e`,`l`,`l`,`o`,`,` `,`W`,`o`,`r`,`l`,`d`,`!`,`"`") -join ''); Invoke-Expression $obfuscated
Run the script with level 2 obfuscation:
./obfuscator -i script.ps1 -o obfuscated_level2.ps1 -level 2
This will generate a file named obfuscated_level2.ps1 with the content encoded in base64. When executing this script, it will be decoded and run at runtime.
Result (level 2)
$obfuscated = [System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String('V3JpdGUtSG9zdCAiSGVsbG8sIFdvcmxkISI=')); Invoke-Expression $obfuscated
Execute the script with level 3 obfuscation:
./obfuscator -i script.ps1 -o obfuscated_level3.ps1 -level 3
This level uses a slightly different form of base64 encoding and decoding in PowerShell, adding an additional layer of obfuscation.
Result (level 3)
$e = [System.Convert]::FromBase64String('V3JpdGUtSG9zdCAiSGVsbG8sIFdvcmxkISI='); $obfuscated = [System.Text.Encoding]::UTF8.GetString($e); Invoke-Expression $obfuscated
Execute the script with level 4 obfuscation:
./obfuscator -i script.ps1 -o obfuscated_level4.ps1 -level 4
This level compresses the script before encoding it in base64, making analysis more complicated. The result will be decoded and decompressed at runtime.
Result (level 4)
$compressed = 'H4sIAAAAAAAAC+NIzcnJVyjPL8pJUQQAlRmFGwwAAAA='; $bytes = [System.Convert]::FromBase64String($compressed); $stream = New-Object IO.MemoryStream(, $bytes); $decompressed = New-Object IO.Compression.GzipStream($stream, [IO.Compression.CompressionMode]::Decompress); $reader = New-Object IO.StreamReader($decompressed); $obfuscated = $reader.ReadToEnd(); Invoke-Expression $obfuscated
Run the script with level 5 obfuscation:
./obfuscator -i script.ps1 -o obfuscated_level5.ps1 -level 5
This level fragments the script into multiple parts and reconstructs it at runtime.
Result (level 5)
$fragments = @(
'Write-',
'Output "',
'Hello,',
' Wo',
'rld!',
'"'
);
$script = $fragments -join '';
Invoke-Expression $script
This program is provided for educational and research purposes. It should not be used for malicious activities.
DockerSpy searches for images on Docker Hub and extracts sensitive information such as authentication secrets, private keys, and more.
Docker is an open-source platform that automates the deployment, scaling, and management of applications using containerization technology. Containers allow developers to package an application and its dependencies into a single, portable unit that can run consistently across various computing environments. Docker simplifies the development and deployment process by ensuring that applications run the same way regardless of where they are deployed.
Docker Hub is a cloud-based repository where developers can store, share, and distribute container images. It serves as the largest library of container images, providing access to both official images created by Docker and community-contributed images. Docker Hub enables developers to easily find, download, and deploy pre-built images, facilitating rapid application development and deployment.
Open Source Intelligence (OSINT) on Docker Hub involves using publicly available information to gather insights and data from container images and repositories hosted on Docker Hub. This is particularly important for identifying exposed secrets for several reasons:
Security Audits: By analyzing Docker images, organizations can uncover exposed secrets such as API keys, authentication tokens, and private keys that might have been inadvertently included. This helps in mitigating potential security risks.
Incident Prevention: Proactively searching for exposed secrets in Docker images can prevent security breaches before they happen, protecting sensitive information and maintaining the integrity of applications.
Compliance: Ensuring that container images do not expose secrets is crucial for meeting regulatory and organizational security standards. OSINT helps verify that no sensitive information is unintentionally disclosed.
Vulnerability Assessment: Identifying exposed secrets as part of regular security assessments allows organizations to address these vulnerabilities promptly, reducing the risk of exploitation by malicious actors.
Enhanced Security Posture: Continuously monitoring Docker Hub for exposed secrets strengthens an organization's overall security posture, making it more resilient against potential threats.
Utilizing OSINT on Docker Hub to find exposed secrets enables organizations to enhance their security measures, prevent data breaches, and ensure the confidentiality of sensitive information within their containerized applications.
DockerSpy obtains information from Docker Hub and uses regular expressions to inspect the content for sensitive information, such as secrets.
To use DockerSpy, follow these steps:
git clone https://github.com/UndeadSec/DockerSpy.git && cd DockerSpy && make
dockerspy
To customize DockerSpy configurations, edit the following files: - Regular Expressions - Ignored File Extensions
DockerSpy is intended for educational and research purposes only. Users are responsible for ensuring that their use of this tool complies with applicable laws and regulations.
Contributions to DockerSpy are welcome! Feel free to submit issues, feature requests, or pull requests to help improve this tool.
DockerSpy is developed and maintained by Alisson Moretto (UndeadSec)
I'm a passionate cyber threat intelligence pro who loves sharing insights and crafting cybersecurity tools.
Consider following me:
Special thanks to @akaclandestine

Most accomplished cybercriminals go out of their way to separate their real names from their hacker handles. But among certain old-school Russian hackers it is not uncommon to find major players who have done little to prevent people from figuring out who they are in real life. A case study in this phenomenon is “x999xx,” the nickname chosen by a venerated Russian hacker who specializes in providing the initial network access to various ransomware groups.
x999xx is a well-known “access broker” who frequently sells access to hacked corporate networks — usually in the form of remote access credentials — as well as compromised databases containing large amounts of personal and financial data.
In an analysis published in February 2019, cyber intelligence firm Flashpoint called x999xx one of the most senior and prolific members of the top-tier Russian-language cybercrime forum Exploit, where x999xx could be seen frequently advertising the sale of stolen databases and network credentials.
In August 2023, x999xx sold access to a company that develops software for the real estate industry. In July 2023, x999xx advertised the sale of Social Security numbers, names, and birthdays for the citizenry of an entire U.S. state (unnamed in the auction).
A month earlier, x999xx posted a sales thread for 80 databases taken from Australia’s largest retail company. “You may use this data to demand a ransom or do something different with it,” x999xx wrote on Exploit. “Unfortunately, the flaw was patched fast. [+] no one has used the data yet [+] the data hasn’t been used to send spam [+] the data is waiting for its time.”
In October 2022, x999xx sold administrative access to a U.S. healthcare provider.
The oldest account by the name x999xx appeared in 2009 on the Russian language cybercrime forum Verified, under the email address maxnm@ozersk.com. Ozersk is a city in the Chelyabinsk region of west-central Russia.
According to the breach tracking service Constella Intelligence, the address maxnm@ozersk.com was used more than a decade ago to create an account at Vktontakte (the Russian answer to Facebook) under the name Maxim Kirtsov from Ozersk. Mr. Kirtsov’s profile — “maxnm” — says his birthday is September 5, 1991.

Personal photos Maxnm shared on Vktontakte in 2016. The caption has been machine translated from Russian.
The user x999xx registered on the Russian language cybercrime community Zloy in 2014 using the email address maxnmalias-1@yahoo.com. Constella says this email address was used in 2022 at the Russian shipping service cdek.ru by a Maksim Georgievich Kirtsov from Ozersk.
Additional searches on these contact details reveal that prior to 2009, x999xx favored the handle Maxnm on Russian cybercrime forums. Cyber intelligence company Intel 471 finds the user Maxnm registered on Zloy in 2006 from an Internet address in Chelyabinsk, using the email address kirtsov@telecom.ozersk.ru.
That same email address was used to create Maxnm accounts on several other crime forums, including Spamdot and Exploit in 2005 (also from Chelyabinsk), and Damagelab in 2006.
A search in Constella for the Russian version of Kirtsov’s full name — Кирцов Максим Георгиевич — brings up multiple accounts registered to maksya@icloud.com.
A review of the digital footprint for maksya@icloud.com at osint.industries reveals this address was used a decade ago to register a still-active account at imageshack.com under the name x999xx. That account features numerous screenshots of financial statements from various banks, chat logs with other hackers, and even hacked websites.
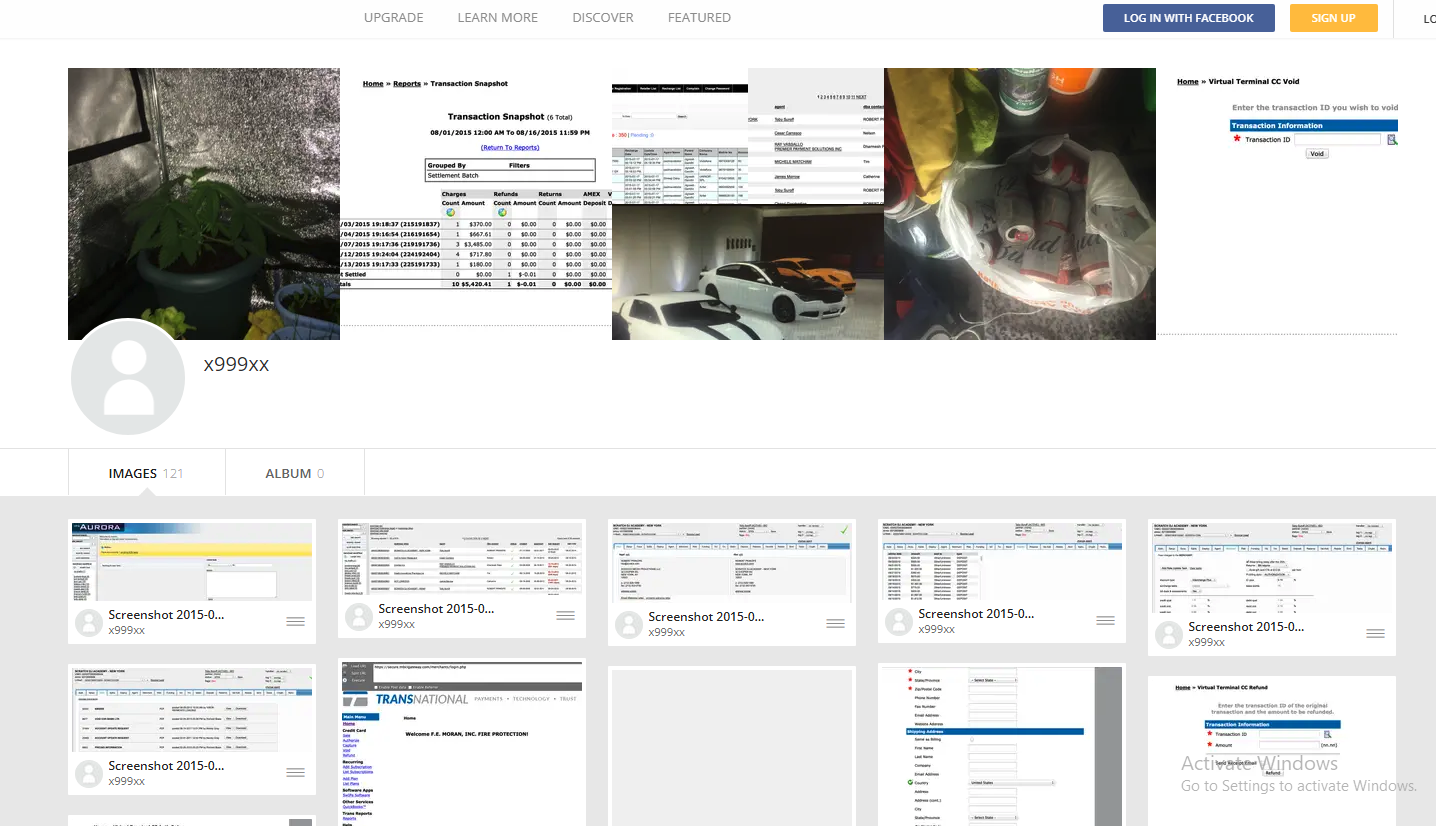
x999xx’s Imageshack account includes screenshots of bank account balances from dozens of financial institutions, as well as chat logs with other hackers and pictures of homegrown weed.
Some of the photos in that Imageshack account also appear on Kirtsov’s Vkontakte page, including images of vehicles he owns, as well as pictures of potted marijuana plants. Kirtsov’s Vkontakte profile says that in 2012 he was a faculty member of the Ozersk Technological Institute National Research Nuclear University.
The Vkontakte page lists Kirtsov’s occupation as a website called ozersk[.]today, which on the surface appears to be a blog about life in Ozersk. However, in 2019 the security firm Recorded Future published a blog post which found this domain was being used to host a malicious Cobalt Strike server.
Cobalt Strike is a commercial network penetration testing and reconnaissance tool that is sold only to vetted partners. But stolen or ill-gotten Cobalt Strike licenses are frequently abused by cybercriminal gangs to help lay the groundwork for the installation of ransomware on a victim network.
In August 2023, x999xx posted a message on Exploit saying he was interested in buying a licensed version of Cobalt Strike. A month earlier, x999xx filed a complaint on Exploit against another forum member named Cobaltforce, an apparent onetime partner whose sudden and prolonged disappearance from the community left x999xx and others in the lurch. Cobaltforce recruited people experienced in using Cobalt Strike for ransomware operations, and offered to monetize access to hacked networks for a share of the profits.
DomainTools.com finds ozersk[.]today was registered to the email address dashin2008@yahoo.com, which also was used to register roughly two dozen other domains, including x999xx[.]biz. Virtually all of those domains were registered to Maxim Kirtsov from Ozersk. Below is a mind map used to track the identities mentioned in this story.
x999xx is a prolific member of the Russian webmaster forum “Gofuckbiz,” with more than 2,000 posts over nearly a decade, according to Intel 471. In one post from 2016, x999xx asked whether anyone knew where he could buy a heat lamp that simulates sunlight, explaining that one his pet rabbits had recently perished for lack of adequate light and heat. Mr. Kirtsov’s Vkontakte page includes several pictures of caged rabbits from 2015 and earlier.
Reached via email, Mr. Kirtsov acknowledged that he is x999xx. Kirtsov said he and his team are also regular readers of KrebsOnSecurity.
“We’re glad to hear and read you,” Kirtsov replied.
Asked whether he was concerned about the legal and moral implications of his work, Kirtsov downplayed his role in ransomware intrusions, saying he was more focused on harvesting data.
“I consider myself as committed to ethical practices as you are,” Kirtsov wrote. “I have also embarked on research and am currently mentoring students. You may have noticed my activities on a forum, which I assume you know of through information gathered from public sources, possibly using the new tool you reviewed.”
“Regarding my posts about selling access, I must honestly admit, upon reviewing my own actions, I recall such mentions but believe they were never actualized,” he continued. “Many use the forum for self-serving purposes, which explains why listings of targets for sale have dwindled — they simply ceased being viable.”
Kirtsov asserted that he is not interested in harming healthcare institutions, just in stealing their data.
“As for health-related matters, I was once acquainted with affluent webmasters who would pay up to $50 for every 1000 health-themed emails,” Kirtsov said. “Therefore, I had no interest in the more sensitive data from medical institutions like X-rays, insurance numbers, or even names; I focused solely on emails. I am proficient in SQL, hence my ease with handling data like IDs and emails. And i never doing spam or something like this.”
On the Russian crime forums, x999xx said he never targets anything or anyone in Russia, and that he has little to fear from domestic law enforcement agencies provided he remains focused on foreign adversaries.
x999xx’s lackadaisical approach to personal security mirrors that of Wazawaka, another top Russian access broker who sold access to countless organizations and even operated his own ransomware affiliate programs.
“Don’t shit where you live, travel local, and don’t go abroad,” Wazawaka said of his own personal mantra. “Mother Russia will help you. Love your country, and you will always get away with everything.”
In January 2022, KrebsOnSecurity followed clues left behind by Wazawaka to identify him as 32-year-old Mikhail Matveev from Khakassia, Russia. In May 2023, the U.S. Department of Justice indicted Matveev as a key figure in several ransomware groups that collectively extorted hundreds of millions of dollars from victim organizations. The U.S. State Department is offering a $10 million reward for information leading to the capture and/or prosecution of Matveev.
Perhaps in recognition that many top ransomware criminals are largely untouchable so long as they remain in Russia, western law enforcement agencies have begun focusing more on getting inside the heads of those individuals. These so-called “psyops” are aimed at infiltrating ransomware-as-a-service operations, disrupting major cybercrime services, and decreasing trust within cybercriminal communities.
When authorities in the U.S. and U.K. announced in February 2024 that they’d infiltrated and seized the infrastructure used by the infamous LockBit ransomware gang, they borrowed the existing design of LockBit’s victim shaming website to link instead to press releases about the takedown, and included a countdown timer that was eventually replaced with the personal details of LockBit’s alleged leader.
In May 2024, law enforcement agencies in the United States and Europe announced Operation Endgame, a coordinated action against some of the most popular cybercrime platforms for delivering ransomware and data-stealing malware. The Operation Endgame website also included a countdown timer, which served to tease the release of several animated videos that mimic the same sort of flashy, short advertisements that established cybercriminals often produce to promote their services online.
The homepage of Stark Industries Solutions.
Two weeks before Russia invaded Ukraine in February 2022, a large, mysterious new Internet hosting firm called Stark Industries Solutions materialized and quickly became the epicenter of massive distributed denial-of-service (DDoS) attacks on government and commercial targets in Ukraine and Europe. An investigation into Stark Industries reveals it is being used as a global proxy network that conceals the true source of cyberattacks and disinformation campaigns against enemies of Russia.
At least a dozen patriotic Russian hacking groups have been launching DDoS attacks since the start of the war at a variety of targets seen as opposed to Moscow. But by all accounts, few attacks from those gangs have come close to the amount of firepower wielded by a pro-Russia group calling itself “NoName057(16).”
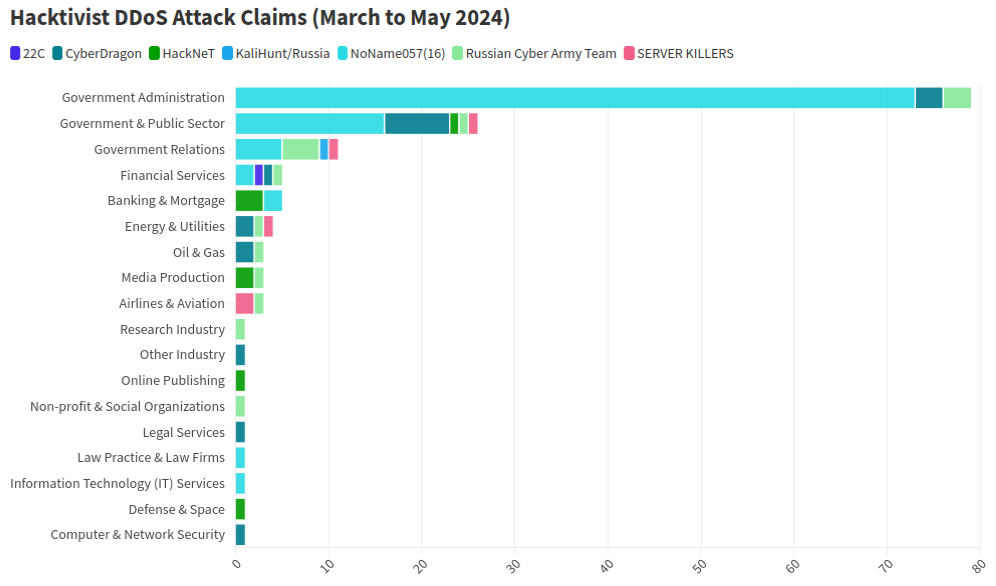
This graphic comes from a recent report from NETSCOUT about DDoS attacks from Russian hacktivist groups.
As detailed by researchers at Radware, NoName has effectively gamified DDoS attacks, recruiting hacktivists via its Telegram channel and offering to pay people who agree to install a piece of software called DDoSia. That program allows NoName to commandeer the host computers and their Internet connections in coordinated DDoS campaigns, and DDoSia users with the most attacks can win cash prizes.
The NoName DDoS group advertising on Telegram. Image: SentinelOne.com.
A report from the security firm Team Cymru found the DDoS attack infrastructure used in NoName campaigns is assigned to two interlinked hosting providers: MIRhosting and Stark Industries. MIRhosting is a hosting provider founded in The Netherlands in 2004. But Stark Industries Solutions Ltd was incorporated on February 10, 2022, just two weeks before the Russian invasion of Ukraine.
Security experts say that not long after the war started, Stark began hosting dozens of proxy services and free virtual private networking (VPN) services, which are designed to help users shield their Internet usage and location from prying eyes.
Proxy providers allow users to route their Internet and Web browsing traffic through someone else’s computer. From a website’s perspective, the traffic from a proxy network user appears to originate from the rented IP address, not from the proxy service customer.

These services can be used in a legitimate manner for several business purposes — such as price comparisons or sales intelligence — but they are also massively abused for hiding cybercrime activity because they can make it difficult to trace malicious traffic to its original source.
What’s more, many proxy services do not disclose how they obtain access to the proxies they are renting out, and in many cases the access is obtained through the dissemination of malicious software that turns the infected system into a traffic relay — usually unbeknownst to the legitimate owner of the Internet connection. Other proxy services will allow users to make money by renting out their Internet connection to anyone.
Spur.us is a company that tracks VPNs and proxy services worldwide. Spur finds that Stark Industries (AS44477) currently is home to at least 74 VPN services, and 40 different proxy services. As we’ll see in the final section of this story, just one of those proxy networks has over a million Internet addresses available for rent across the globe.
Raymond Dijkxhoorn operates a hosting firm in The Netherlands called Prolocation. He also co-runs SURBL, an anti-abuse service that flags domains and Internet address ranges that are strongly associated with spam and cybercrime activity, including DDoS.
Dijkxhoorn said last year SURBL heard from multiple people who said they operated VPN services whose web resources were included in SURBL’s block lists.
“We had people doing delistings at SURBL for domain names that were suspended by the registrars,” Dijkhoorn told KrebsOnSecurity. “And at least two of them explained that Stark offered them free VPN services that they were reselling.”
Dijkxhoorn added that Stark Industries also sponsored activist groups from Ukraine.
“How valuable would it be for Russia to know the real IPs from Ukraine’s tech warriors?” he observed.
Richard Hummel is threat intelligence lead at NETSCOUT. Hummel said when he considers the worst of all the hosting providers out there today, Stark Industries is consistently near or at the top of that list.
“The reason is we’ve had at least a dozen service providers come to us saying, ‘There’s this network out there inundating us with traffic,'” Hummel said. “And it wasn’t even DDoS attacks. [The systems] on Stark were just scanning these providers so fast it was crashing some of their services.”
Hummel said NoName will typically launch their attacks using a mix of resources rented from major, legitimate cloud services, and those from so-called “bulletproof” hosting providers like Stark. Bulletproof providers are so named when they earn or cultivate a reputation for ignoring any abuse complaints or police reports about activity on their networks.
Combining bulletproof providers with legitimate cloud hosting, Hummel said, likely makes NoName’s DDoS campaigns more resilient because many network operators will hesitate to be too aggressive in blocking Internet addresses associated with the major cloud services.
“What we typically see here is a distribution of cloud hosting providers and bulletproof hosting providers in DDoS attacks,” he said. “They’re using public cloud hosting providers because a lot of times that’s your first layer of network defense, and because [many companies are wary of] over-blocking access to legitimate cloud resources.”
But even if the cloud provider detects abuse coming from the customer, the provider is probably not going to shut the customer down immediately, Hummel said.
“There is usually a grace period, and even if that’s only an hour or two, you can still launch a large number of attacks in that time,” he said. “And then they just keep coming back and opening new cloud accounts.”
Stark Industries is incorporated at a mail drop address in the United Kingdom. UK business records list an Ivan Vladimirovich Neculiti as the company’s secretary. Mr. Neculiti also is named as the CEO and founder of PQ Hosting Plus S.R.L. (aka Perfect Quality Hosting), a Moldovan company formed in 2019 that lists the same UK mail drop address as Stark Industries.

Ivan Neculiti, as pictured on LinkedIn.
Reached via LinkedIn, Mr. Neculiti said PQ Hosting established Stark Industries as a “white label” of its brand so that “resellers could distribute our services using our IP addresses and their clients would not have any affairs with PQ Hosting.”
“PQ Hosting is a company with over 1,000+ of [our] own physical servers in 38 countries and we have over 100,000 clients,” he said. “Though we are not as large as Hetzner, Amazon and OVH, nevertheless we are a fast growing company that provides services to tens of thousands of private customers and legal entities.”
Asked about the constant stream of DDoS attacks whose origins have traced back to Stark Industries over the past two years, Neculiti maintained Stark hasn’t received any official abuse reports about attacks coming from its networks.
“It was probably some kind of clever attack that we did not see, I do not rule out this fact, because we have a very large number of clients and our Internet channels are quite large,” he said. “But, in this situation, unfortunately, no one contacted us to report that there was an attack from our addresses; if someone had contacted us, we would have definitely blocked the network data.”
DomainTools.com finds Ivan V. Neculiti was the owner of war[.]md, a website launched in 2008 that chronicled the history of a 1990 armed conflict in Moldova known as the Transnistria War and the Moldo-Russian war.

An ad for war.md, circa 2009.
Transnistria is a breakaway pro-Russian region that declared itself a state in 1990, although it is not internationally recognized. The copyright on that website credits the “MercenarieS TeaM,” which was at one time a Moldovan IT firm. Mr. Neculiti confirmed personally registering this domain.
The data breach tracking service Constella Intelligence reports that an Ivan V. Neculiti registered multiple online accounts under the email address dfyz_bk@bk.ru. Cyber intelligence firm Intel 471 shows this email address is tied to the username “dfyz” on more than a half-dozen Russian language cybercrime forums since 2008. The user dfyz on Searchengines[.]ru in 2008 asked other forum members to review war.md, and said they were part of the MercenarieS TeaM.
Back then, dfyz was selling “bulletproof servers for any purpose,” meaning the hosting company would willfully ignore abuse complaints or police inquiries about the activity of its customers.
DomainTools reports there are at least 33 domain names registered to dfyz_bk@bk.ru. Several of these domains have Ivan Neculiti in their registration records, including tracker-free[.]cn, which was registered to an Ivan Neculiti at dfyz_bk@bk.ru and referenced the MercenarieS TeaM in its original registration records.
Dfyz also used the nickname DonChicho, who likewise sold bulletproof hosting services and access to hacked Internet servers. In 2014, a prominent member of the Russian language cybercrime community Antichat filed a complaint against DonChicho, saying this user scammed them and had used the email address dfyz_bk@bk.ru.
The complaint said DonChicho registered on Antichat from the Transnistria Internet address 84.234.55[.]29. Searching this address in Constella reveals it has been used to register just five accounts online that have been created over the years, including one at ask.ru, where the user registered with the email address neculitzy1@yandex.ru. Constella also returns for that email address a user by the name “Ivan” at memoraleak.com and 000webhost.com.
Constella finds that the password most frequently used by the email address dfyz_bk@bk.ru was “filecast,” and that there are more than 90 email addresses associated with this password. Among them are roughly two dozen addresses with the name “Neculiti” in them, as well as the address support@donservers[.]ru.
Intel 471 says DonChicho posted to several Russian cybercrime forums that support@donservers[.]ru was his address, and that he logged into cybercrime forums almost exclusively from Internet addresses in Tiraspol, the capital of Transnistria. A review of DonChicho’s posts shows this person was banned from several forums in 2014 for scamming other users.
Cached copies of DonChicho’s vanity domain (donchicho[.]ru) show that in 2009 he was a spammer who peddled knockoff prescription drugs via Rx-Promotion, once one of the largest pharmacy spam moneymaking programs for Russian-speaking affiliates.
Mr. Neculiti told KrebsOnSecurity he has never used the nickname DonChicho.
“I may assure you that I have no relation to DonChicho nor to his bulletproof servers,” he said.
Below is a mind map that shows the connections between the accounts mentioned above.
Earlier this year, NoName began massively hitting government and industry websites in Moldova. A new report from Arbor Networks says the attacks began around March 6, when NoName alleged the government of Moldova was “craving for Russophobia.”
“Since early March, more than 50 websites have been targeted, according to posted ‘proof’ by the groups involved in attacking the country,” Arbor’s ASERT Team wrote. “While NoName seemingly initiated the ramp of attacks, a host of other DDoS hacktivists have joined the fray in claiming credit for attacks across more than 15 industries.”
The German independent news outlet Correctiv.org last week published a scathing investigative report on Stark Industries and MIRhosting, which notes that Ivan Neculiti operates his hosting companies with the help of his brother, Yuri.
The report points out that Stark Industries continues to host a Russian disinformation news outlet called “Recent Reliable News” (RRN) that was sanctioned by the European Union in 2023 for spreading links to propaganda blogs and fake European media and government websites.
“The website was not running on computers in Moscow or St. Petersburg until recently, but in the middle of the EU, in the Netherlands, on the computers of the Neculiti brothers,” Correctiv reporters wrote.
“After a request from this editorial team, a well-known service was installed that hides the actual web host,” the report continues. “Ivan Neculiti announced that he had blocked the associated access and server following internal investigations. “We very much regret that we are only now finding out that one of our customers is a sanctioned portal,” said the company boss. However, RRN is still accessible via its servers.”
Correctiv also points to a January 2023 report from the Ukrainian government, which found servers from Stark Industries Solutions were used as part of a cyber attack on the Ukrainian news agency “Ukrinform”. Correctiv notes the notorious hacker group Sandworm — an advanced persistent threat (APT) group operated by a cyberwarfare unit of Russia’s military intelligence service — was identified by Ukrainian government authorities as responsible for that attack.
Public records indicate MIRhosting is based in The Netherlands and is operated by 37-year old Andrey Nesterenko, whose personal website says he is an accomplished concert pianist who began performing publicly at a young age.
DomainTools says mirhosting[.]com is registered to Mr. Nesterenko and to Innovation IT Solutions Corp, which lists addresses in London and in Nesterenko’s stated hometown of Nizhny Novgorod, Russia.
This is interesting because according to the book Inside Cyber Warfare by Jeffrey Carr, Innovation IT Solutions Corp. was responsible for hosting StopGeorgia[.]ru, a hacktivist website for organizing cyberattacks against Georgia that appeared at the same time Russian forces invaded the former Soviet nation in 2008. That conflict was thought to be the first war ever fought in which a notable cyberattack and an actual military engagement happened simultaneously.
Responding to questions from KrebsOnSecurity, Mr. Nesterenko said he couldn’t say whether his network had ever hosted the StopGeorgia website back in 2008 because his company didn’t keep records going back that far. But he said Stark Industries Solutions is indeed one of MIRhsoting’s colocation customers.
“Our relationship is purely provider-customer,” Nesterenko said. “They also utilize multiple providers and data centers globally, so connecting them directly to MIRhosting overlooks their broader network.”
“We take any report of malicious activity seriously and are always open to information that can help us identify and prevent misuse of our infrastructure, whether involving Stark Industries or any other customer,” Nesterenko continued. “In cases where our services are exploited for malicious purposes, we collaborate fully with Dutch cyber police and other relevant authorities to investigate and take appropriate measures. However, we have yet to receive any actionable information beyond the article itself, which has not provided us with sufficient detail to identify or block malicious actors.”
In December 2022, security firm Recorded Future profiled the phishing and credential harvesting infrastructure used for Russia-aligned espionage operations by a group dubbed Blue Charlie (aka TAG-53), which has targeted email accounts of nongovernmental organizations and think tanks, journalists, and government and defense officials.
Recorded Future found that virtually all the Blue Charlie domains existed in just ten different ISPs, with a significant concentration located in two networks, one of which was MIRhosting. Both Microsoft and the UK government assess that Blue Charlie is linked to the Russian threat activity groups variously known as Callisto Group, COLDRIVER, and SEABORGIUM.
Mr. Nesterenko took exception to a story on that report from The Record, which is owned by Recorded Future.
“We’ve discussed its contents with our customer, Stark Industries,” he said. “We understand that they have initiated legal proceedings against the website in question, as they firmly believe that the claims made are inaccurate.”
Recorded Future said they updated their story with comments from Mr. Neculiti, but that they stand by their reporting.
Mr. Nesterenko’s LinkedIn profile says he was previously the foreign region sales manager at Serverius-as, a hosting company in The Netherlands that remains in the same data center as MIRhosting.
In February, the Dutch police took 13 servers offline that were used by the infamous LockBit ransomware group, which had originally bragged on its darknet website that its home base was in The Netherlands. Sources tell KrebsOnSecurity the servers seized by the Dutch police were located in Serverius’ data center in Dronten, which is also shared by MIRhosting.
Serverius-as did not respond to requests for comment. Nesterenko said MIRhosting does use one of Serverius’s data centers for its operations in the Netherlands, alongside two other data centers, but that the recent incident involving the seizure of servers has no connection to MIRhosting.
“We are legally prohibited by Dutch law and police regulations from sharing information with third parties regarding any communications we may have had,” he said.
A February 2024 report from security firm ESET found Serverius-as systems were involved in a series of targeted phishing attacks by Russia-aligned groups against Ukrainian entities throughout 2023. ESET observed that after the spearphishing domains were no longer active, they were converted to promoting rogue Internet pharmacy websites.
A review of the Internet address ranges recently added to the network operated by Stark Industries Solutions offers some insight into its customer base, usage, and maybe even true origins. Here is a snapshot (PDF) of all Internet address ranges announced by Stark Industries so far in the month of May 2024 (this information was graciously collated by the network observability platform Kentik.com).
Those records indicate that the largest portion of the IP space used by Stark is in The Netherlands, followed by Germany and the United States. Stark says it is connected to roughly 4,600 Internet addresses that currently list their ownership as Comcast Cable Communications.
A review of those address ranges at spur.us shows all of them are connected to an entity called Proxyline, which is a sprawling proxy service based in Russia that currently says it has more than 1.6 million proxies globally that are available for rent.

Proxyline dot net.
Reached for comment, Comcast said the Internet address ranges never did belong to Comcast, so it is likely that Stark has been fudging the real location of its routing announcements in some cases.
Stark reports that it has more than 67,000 Internet addresses at Santa Clara, Calif.-based EGIhosting. Spur says the Stark addresses involving EGIhosting all map to Proxyline as well. EGIhosting did not respond to requests for comment.
EGIhosting manages Internet addresses for the Cyprus-based hosting firm ITHOSTLINE LTD (aka HOSTLINE-LTD), which is represented throughout Stark’s announced Internet ranges. Stark says it has more than 21,000 Internet addresses with HOSTLINE. Spur.us finds Proxyline addresses are especially concentrated in the Stark ranges labeled ITHOSTLINE LTD, HOSTLINE-LTD, and Proline IT.
Stark’s network list includes approximately 21,000 Internet addresses at Hockessin, De. based DediPath, which abruptly ceased operations without warning in August 2023. According to a phishing report released last year by Interisle Consulting, DediPath was the fourth most common source of phishing attacks in the year ending Oct. 2022. Spur.us likewise finds that virtually all of the Stark address ranges marked “DediPath LLC” are tied to Proxyline.
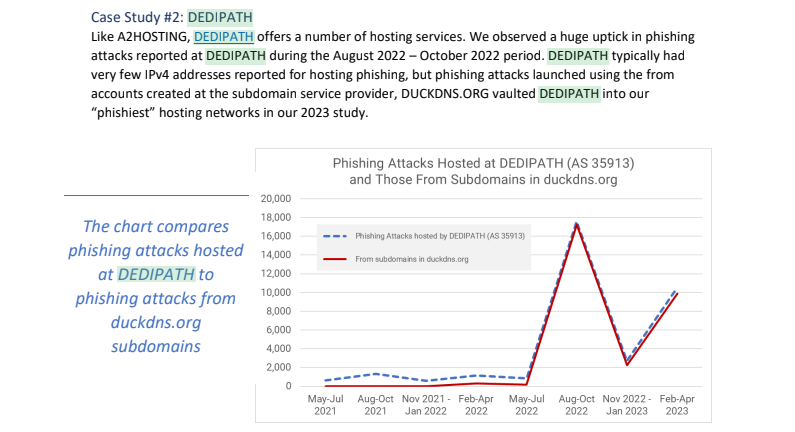
Image: Interisle Consulting.
A large number of the Internet address ranges announced by Stark in May originate in India, and the names that are self-assigned to many of these networks indicate they were previously used to send large volumes of spam for herbal medicinal products, with names like HerbalFarm, AdsChrome, Nutravo, Herbzoot and Herbalve.
The anti-spam organization SpamHaus reports that many of the Indian IP address ranges are associated with known “snowshoe spam,” a form of abuse that involves mass email campaigns spread across several domains and IP addresses to weaken reputation metrics and avoid spam filters.
It’s not clear how much of Stark’s network address space traces its origins to Russia, but big chunks of it recently belonged to some of the oldest entities on the Russian Internet (a.k.a. “Runet”).
For example, many Stark address ranges were most recently assigned to a Russian government entity whose full name is the “Federal State Autonomous Educational Establishment of Additional Professional Education Center of Realization of State Educational Policy and Informational Technologies.”
A review of Internet address ranges adjacent to this entity reveals a long list of Russian government organizations that are part of the Federal Guard Service of the Russian Federation. Wikipedia says the Federal Guard Service is a Russian federal government agency concerned with tasks related to protection of several high-ranking state officials, including the President of Russia, as well as certain federal properties. The agency traces its origins to the USSR’s Ninth Directorate of the KGB, and later the presidential security service.
Stark recently announced the address range 213.159.64.0/20 from April 27 to May 1, and this range was previously assigned to an ancient ISP in St. Petersburg, RU called the Computer Technologies Institute Ltd.
According to a post on the Russian language webmaster forum searchengines[.]ru, the domain for Computer Technologies Institute — ctinet[.]ru — is the seventh-oldest domain in the entire history of the Runet.
Curiously, Stark also lists large tracts of Internet addresses (close to 48,000 in total) assigned to a small ISP in Kharkiv, Ukraine called NetAssist. Reached via email, the CEO of NetAssist Max Tulyev confirmed his company provides a number of services to PQ Hosting.
“We colocate their equipment in Warsaw, Madrid, Sofia and Thessaloniki, provide them IP transit and IPv4 addresses,” Tulyev said. “For their size, we receive relatively low number of complains to their networks. I never seen anything about their pro-Russian activity or support of Russian hackers. It is very interesting for me to see proofs of your accusations.”
Spur.us mapped the entire infrastructure of Proxyline, and found more than one million proxies across multiple providers, but by far the biggest concentration was at Stark Industries Solutions. The full list of Proxyline address ranges (.CSV) shows two other ISPs appear repeatedly throughout the list. One is Kharkiv, Ukraine based ITL LLC, also known as Information Technology Laboratories Group, and Integrated Technologies Laboratory.
The second is a related hosting company in Miami, called Green Floid LLC. Green Floid featured in a 2017 scoop by CNN, which profiled the company’s owner and quizzed him about Russian troll farms using proxy networks on Green Floid and its parent firm ITL to mask disinformation efforts tied to the Kremlin’s Internet Research Agency (IRA). At the time, the IRA was using Facebook and other social media networks to spread videos showing police brutality against African Americans in an effort to encourage protests across the United States.

Doug Madory, director of Internet analysis at Kentik, was able to see at a high level the top sources and destinations for traffic traversing Stark’s network.
“Based on our aggregate NetFlow, we see Iran as the top destination (35.1%) for traffic emanating from Stark (AS44477),” Madory said. “Specifically, the top destination is MTN Irancell, while the top source is Facebook. This data supports the theory that AS44477 houses proxy services as Facebook is blocked in Iran.”
On April 30, the security firm Malwarebytes explored an extensive malware operation that targets corporate Internet users with malicious ads. Among the sites used as lures in that campaign were fake Wall Street Journal and CNN websites that told visitors they were required to install a WSJ or CNN-branded browser extension (malware). Malwarebytes found a domain name central to that operation was hosted at Internet addresses owned by Stark Industries.
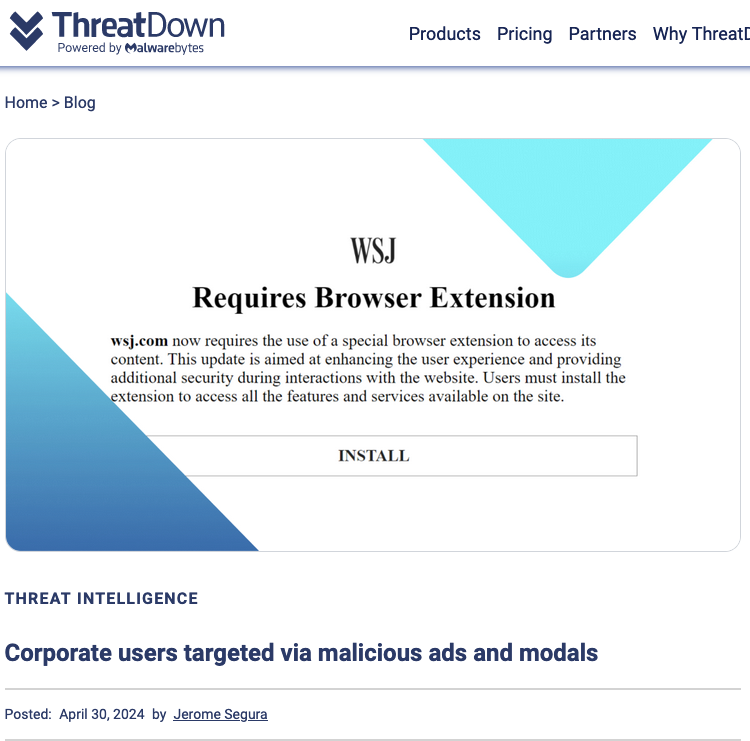
Image: threatdown.com