Authorities in Germany this week seized Internet servers that powered FlyHosting, a dark web offering that catered to cybercriminals operating DDoS-for-hire services, KrebsOnSecurity has learned. FlyHosting first advertised on cybercrime forums in November 2022, saying it was a Germany-based hosting firm that was open for business to anyone looking for a reliable place to host malware, botnet controllers, or DDoS-for-hire infrastructure.
A seizure notice left on the FlyHosting domains.
A statement released today by the German Federal Criminal Police Office says they served eight search warrants on March 30, and identified five individuals aged 16-24 suspected of operating “an internet service” since mid-2021. The German authorities did not name the suspects or the Internet service in question.
“Previously unknown perpetrators used the Internet service provided by the suspects in particular for so-called ‘DDoS attacks’, i.e. the simultaneous sending of a large number of data packets via the Internet for the purpose of disrupting other data processing systems,” the statement reads.
News of a raid on FlyHosting first surfaced Thursday in a Telegram chat channel that is frequented by people interested or involved in the DDoS-for-hire industry, where a user by the name Dstatcc broke the news to FlyHosting customers:
“So Flyhosting made a ‘migration’ with it[s] systems to new rooms of the police ;),” the warning read. “Police says: They support ddos attacks, C&C/C2 and stresser a bit too much. We expect the police will take a deeper look into the files, payment logs and IP’s. If you had a server from them and they could find ‘bad things’ connected with you (payed with private paypal) you may ask a lawyer.”
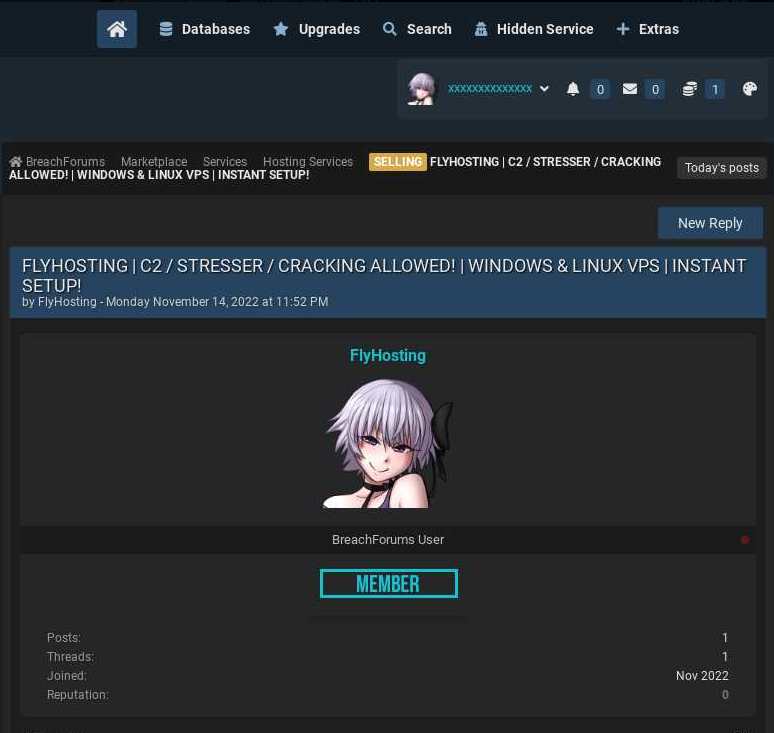
An ad for FlyHosting posted by the the user “bnt” on the now-defunct cybercrime forum BreachForums. Image: Ke-la.com.
The German authorities said that as a result of the DDoS attacks facilitated by the defendants, the websites of various companies as well as those of the Hesse police have been overloaded in several cases since mid-2021, “so that they could only be operated to a limited extent or no longer at times.”
The statement says police seized mobile phones, laptops, tablets, storage media and handwritten notes from the unnamed defendants, and confiscated servers operated by the suspects in Germany, Finland and the Netherlands.
In response to questions from KrebsOnSecurity, Germany’s Hessen Police confirmed that the seizures were executed against FlyHosting.
The raids on FlyHosting come amid a broader law enforcement crackdown on DDoS-for-hire services internationally. The U.K.’s National Crime Agency announced last week that it’s been busy setting up phony DDoS-for-hire websites that seek to collect information on users, remind them that launching DDoS attacks is illegal, and generally increase the level of paranoia for people looking to hire such services.
In mid-December 2022, the U.S. Department of Justice (DOJ) announced “Operation Power Off,” which seized four-dozen DDoS-for-hire domains responsible for more than 30 million DDoS attacks, and charged six U.S. men with computer crimes related to their alleged ownership of popular DDoS-for-hire services.
Update, April 3, 9:30 a.m. ET: Added confirmation from Hesse Police.