An old but persistent email scam known as “sextortion” has a new personalized touch: The missives, which claim that malware has captured webcam footage of recipients pleasuring themselves, now include a photo of the target’s home in a bid to make threats about publishing the videos more frightening and convincing.

This week, several readers reported receiving sextortion emails that addressed them by name and included images of their street or front yard that were apparently lifted from an online mapping application such as Google Maps.
The message purports to have been sent from a hacker who’s compromised your computer and used your webcam to record a video of you while you were watching porn. The missive threatens to release the video to all of your contacts unless you pay a Bitcoin ransom. In this case, the demand is just shy of $2,000, payable by scanning a QR code embedded in the email.
Following a salutation that includes the recipient’s full name, the start of the message reads, “Is visiting [recipient’s street address] a more convenient way to contact if you don’t take action. Nice location btw.” Below that is the photo of the recipient’s street address.
A semi-redacted screenshot of a newish sextortion scam that includes a photo of the target’s front yard.
The message tells people they have 24 hours to pay up, or else their embarrassing videos will be released to all of their contacts, friends and family members.
“Don’t even think about replying to this, it’s pointless,” the message concludes. “I don’t make mistakes, [recipient’s name]. If I notice that you’ve shared or discussed this email with someone else, your shitty video will instantly start getting sent to your contacts.”
The remaining sections of the two-page sextortion message (which arrives as a PDF attachment) are fairly formulaic and include thematic elements seen in most previous sextortion waves. Those include claims that the extortionist has installed malware on your computer (in this case the scammer claims the spyware is called “Pegasus,” and that they are watching everything you do on your machine).
Previous innovations in sextortion customization involved sending emails that included at least one password they had previously used at an account online that was tied to their email address.
Sextortion — even semi-automated scams like this one with no actual physical leverage to backstop the extortion demand — is a serious crime that can lead to devastating consequences for victims. Sextortion occurs when someone threatens to distribute your private and sensitive material if you don’t provide them with images of a sexual nature, sexual favors, or money.
According to the FBI, here are some things you can do to avoid becoming a victim:
-Never send compromising images of yourself to anyone, no matter who they are — or who they say they are.
-Don’t open attachments from people you don’t know, and be wary of opening attachments even from those you do know.
-Turn off [and/or cover] any web cameras when you are not using them.
The FBI says in many sextortion cases, the perpetrator is an adult pretending to be a teenager, and you are just one of the many victims being targeted by the same person. If you believe you’re a victim of sextortion, or know someone else who is, the FBI wants to hear from you: Contact your local FBI office (or toll-free at 1-800-CALL-FBI).
Borrowing from the playbook of ransomware purveyors, the darknet narcotics bazaar Incognito Market has begun extorting all of its vendors and buyers, threatening to publish cryptocurrency transaction and chat records of users who refuse to pay a fee ranging from $100 to $20,000. The bold mass extortion attempt comes just days after Incognito Market administrators reportedly pulled an “exit scam” that left users unable to withdraw millions of dollars worth of funds from the platform.
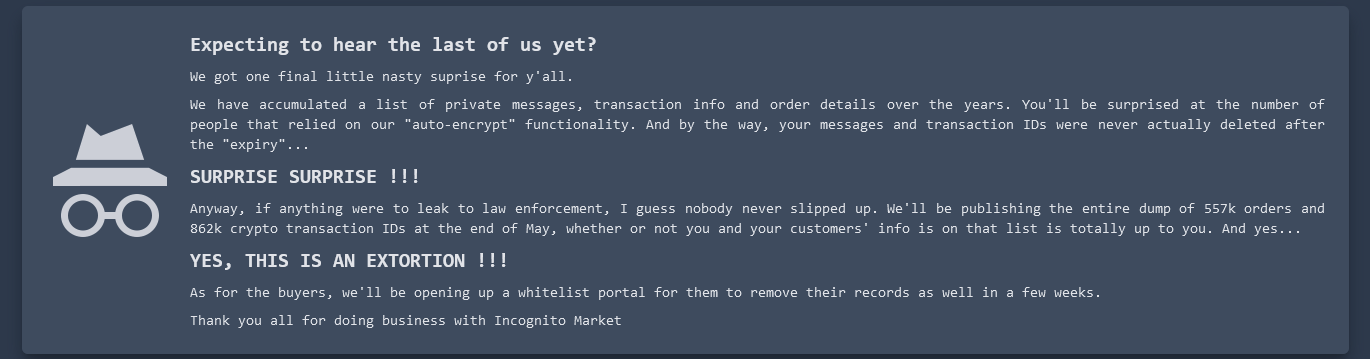
An extortion message currently on the Incognito Market homepage.
In the past 24 hours, the homepage for the Incognito Market was updated to include a blackmail message from its owners, saying they will soon release purchase records of vendors who refuse to pay to keep the records confidential.
“We got one final little nasty surprise for y’all,” reads the message to Incognito Market users. “We have accumulated a list of private messages, transaction info and order details over the years. You’ll be surprised at the number of people that relied on our ‘auto-encrypt’ functionality. And by the way, your messages and transaction IDs were never actually deleted after the ‘expiry’….SURPRISE SURPRISE!!! Anyway, if anything were to leak to law enforcement, I guess nobody never slipped up.”
Incognito Market says it plans to publish the entire dump of 557,000 orders and 862,000 cryptocurrency transaction IDs at the end of May.
“Whether or not you and your customers’ info is on that list is totally up to you,” the Incognito administrators advised. “And yes, this is an extortion!!!!”
The extortion message includes a “Payment Status” page that lists the darknet market’s top vendors by their handles, saying at the top that “you can see which vendors care about their customers below.” The names in green supposedly correspond to users who have already opted to pay.
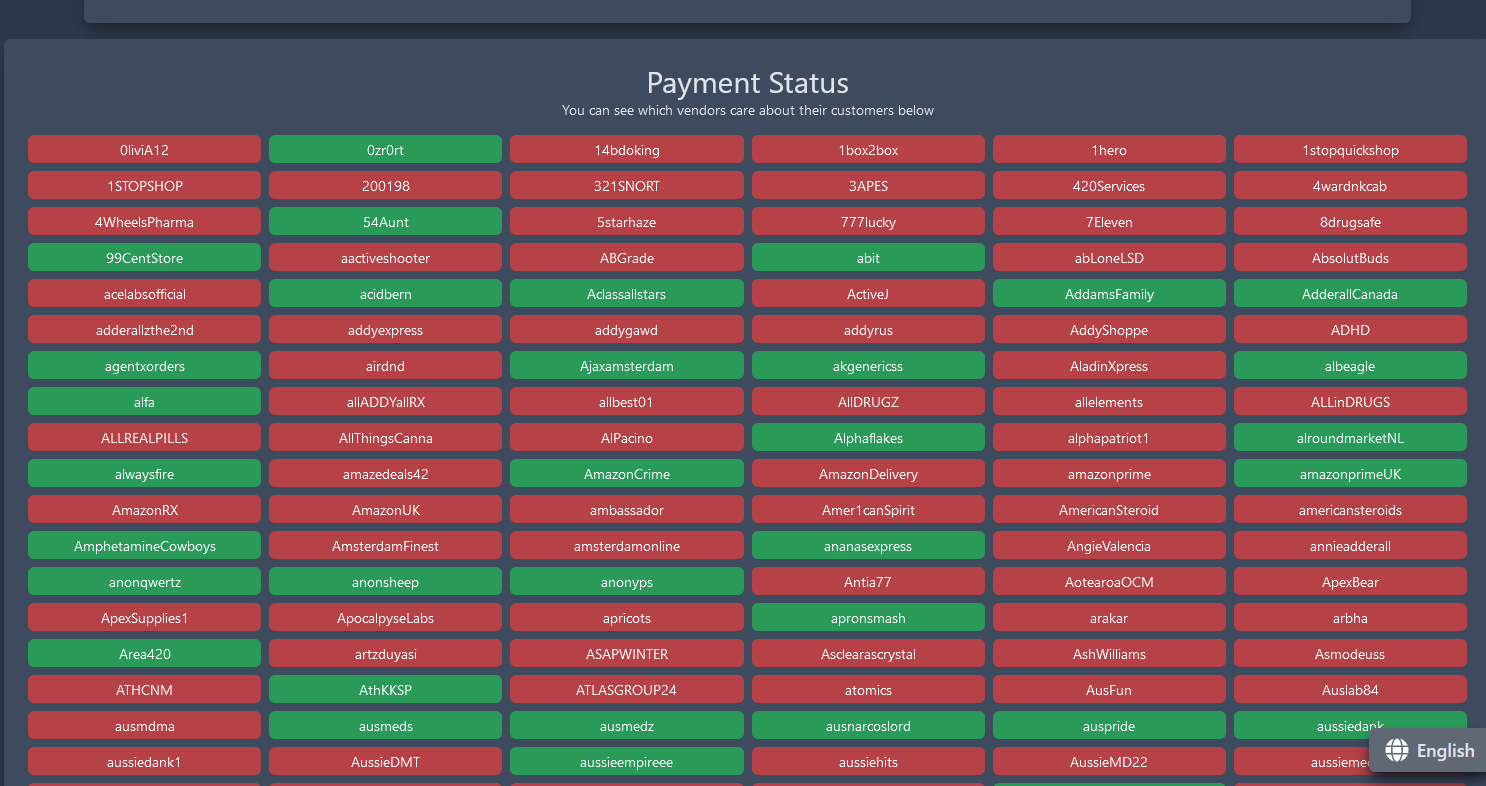
The “Payment Status” page set up by the Incognito Market extortionists.
We’ll be publishing the entire dump of 557k orders and 862k crypto transaction IDs at the end of May, whether or not you and your customers’ info is on that list is totally up to you. And yes, this is an extortion!!!!
Incognito Market said it plans to open up a “whitelist portal” for buyers to remove their transaction records “in a few weeks.”
The mass-extortion of Incognito Market users comes just days after a large number of users reported they were no longer able to withdraw funds from their buyer or seller accounts. The cryptocurrency-focused publication Cointelegraph.com reported Mar. 6 that Incognito was exit-scamming its users out of their bitcoins and Monero deposits.
CoinTelegraph notes that Incognito Market administrators initially lied about the situation, and blamed users’ difficulties in withdrawing funds on recent changes to Incognito’s withdrawal systems.
Incognito Market deals primarily in narcotics, so it’s likely many users are now worried about being outed as drug dealers. Creating a new account on Incognito Market presents one with an ad for 5 grams of heroin selling for $450.
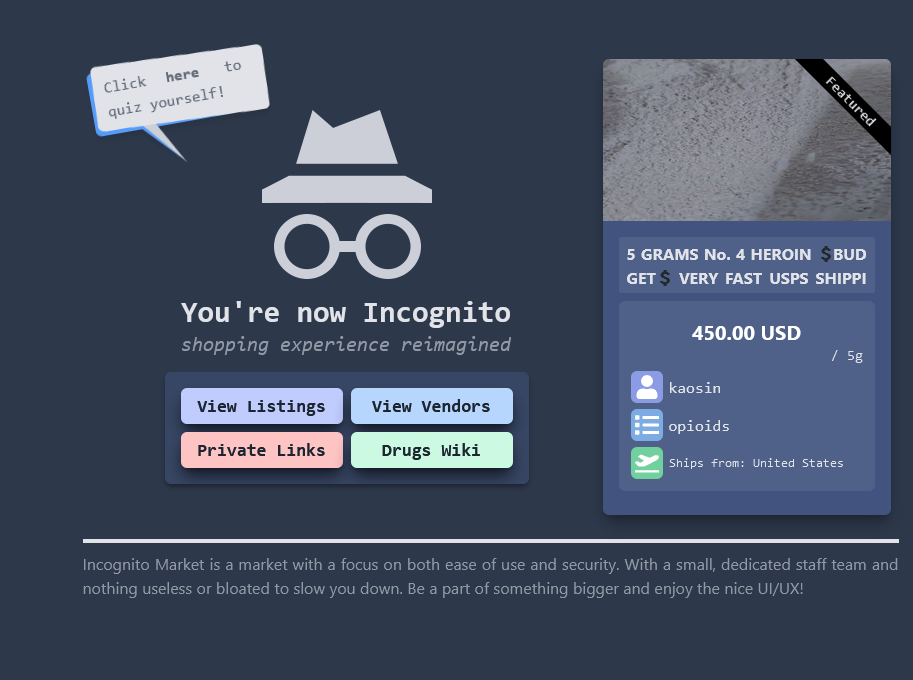
New Incognito Market users are treated to an ad for $450 worth of heroin.
The double whammy now hitting Incognito Market users is somewhat akin to the double extortion techniques employed by many modern ransomware groups, wherein victim organizations are hacked, relieved of sensitive information and then presented with two separate ransom demands: One in exchange for a digital key needed to unlock infected systems, and another to secure a promise that any stolen data will not be published or sold, and will be destroyed.
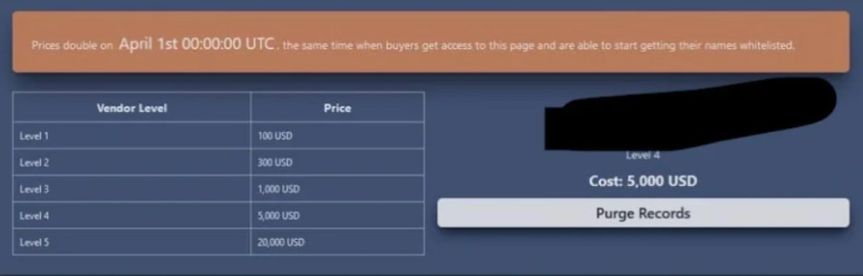
Incognito Market has priced its extortion for vendors based on their status or “level” within the marketplace. Level 1 vendors can supposedly have their information removed by paying a $100 fee. However, larger “Level 5” vendors are asked to cough up $20,000 payments.
The past is replete with examples of similar darknet market exit scams, which tend to happen eventually to all darknet markets that aren’t seized and shut down by federal investigators, said Brett Johnson, a convicted and reformed cybercriminal who built the organized cybercrime community Shadowcrew many years ago.
“Shadowcrew was the precursor to today’s Darknet Markets and laid the foundation for the way modern cybercrime channels still operate today,” Johnson said. “The Truth of Darknet Markets? ALL of them are Exit Scams. The only question is whether law enforcement can shut down the market and arrest its operators before the exit scam takes place.”









s3-ep124-auth--1200






































