Microsoft today released updates to fix more than 100 security flaws in its Windows operating systems and other software. At least 13 of the bugs received Microsoft’s most-dire “critical” rating, meaning they could be abused by malware or malcontents to gain remote access to a Windows system with little or no help from users.

August’s patch batch from Redmond includes an update for CVE-2025-53786, a vulnerability that allows an attacker to pivot from a compromised Microsoft Exchange Server directly into an organization’s cloud environment, potentially gaining control over Exchange Online and other connected Microsoft Office 365 services. Microsoft first warned about this bug on Aug. 6, saying it affects Exchange Server 2016 and Exchange Server 2019, as well as its flagship Exchange Server Subscription Edition.
Ben McCarthy, lead cyber security engineer at Immersive, said a rough search reveals approximately 29,000 Exchange servers publicly facing on the internet that are vulnerable to this issue, with many of them likely to have even older vulnerabilities.
McCarthy said the fix for CVE-2025-53786 requires more than just installing a patch, such as following Microsoft’s manual instructions for creating a dedicated service to oversee and lock down the hybrid connection.
“In effect, this vulnerability turns a significant on-premise Exchange breach into a full-blown, difficult-to-detect cloud compromise with effectively living off the land techniques which are always harder to detect for defensive teams,” McCarthy said.
CVE-2025-53779 is a weakness in the Windows Kerberos authentication system that allows an unauthenticated attacker to gain domain administrator privileges. Microsoft credits the discovery of the flaw to Akamai researcher Yuval Gordon, who dubbed it “BadSuccessor” in a May 2025 blog post. The attack exploits a weakness in “delegated Managed Service Account” or dMSA — a feature that was introduced in Windows Server 2025.
Some of the critical flaws addressed this month with the highest severity (between 9.0 and 9.9 CVSS scores) include a remote code execution bug in the Windows GDI+ component that handles graphics rendering (CVE-2025-53766) and CVE-2025-50165, another graphics rendering weakness. Another critical patch involves CVE-2025-53733, a vulnerability in Microsoft Word that can be exploited without user interaction and triggered through the Preview Pane.
One final critical bug tackled this month deserves attention: CVE-2025-53778, a bug in Windows NTLM, a core function of how Windows systems handle network authentication. According to Microsoft, the flaw could allow an attacker with low-level network access and basic user privileges to exploit NTLM and elevate to SYSTEM-level access — the highest level of privilege in Windows. Microsoft rates the exploitation of this bug as “more likely,” although there is no evidence the vulnerability is being exploited at the moment.
Feel free to holler in the comments if you experience problems installing any of these updates. As ever, the SANS Internet Storm Center has its useful breakdown of the Microsoft patches indexed by severity and CVSS score, and AskWoody.com is keeping an eye out for Windows patches that may cause problems for enterprises and end users.
Windows 10 users out there likely have noticed by now that Microsoft really wants you to upgrade to Windows 11. The reason is that after the Patch Tuesday on October 14, 2025, Microsoft will stop shipping free security updates for Windows 10 computers. The trouble is, many PCs running Windows 10 do not meet the hardware specifications required to install Windows 11 (or they do, but just barely).
If the experience with Windows XP is any indicator, many of these older computers will wind up in landfills or else will be left running in an unpatched state. But if your Windows 10 PC doesn’t have the hardware chops to run Windows 11 and you’d still like to get some use out of it safely, consider installing a newbie-friendly version of Linux, like Linux Mint.
Like most modern Linux versions, Mint will run on anything with a 64-bit CPU that has at least 2GB of memory, although 4GB is recommended. In other words, it will run on almost any computer produced in the last decade.
There are many versions of Linux available, but Linux Mint is likely to be the most intuitive interface for regular Windows users, and it is largely configurable without any fuss at the text-only command-line prompt. Mint and other flavors of Linux come with LibreOffice, which is an open source suite of tools that includes applications similar to Microsoft Office, and it can open, edit and save documents as Microsoft Office files.
If you’d prefer to give Linux a test drive before installing it on a Windows PC, you can always just download it to a removable USB drive. From there, reboot the computer (with the removable drive plugged in) and select the option at startup to run the operating system from the external USB drive. If you don’t see an option for that after restarting, try restarting again and hitting the F8 button, which should open a list of bootable drives. Here’s a fairly thorough tutorial that walks through exactly how to do all this.
And if this is your first time trying out Linux, relax and have fun: The nice thing about a “live” version of Linux (as it’s called when the operating system is run from a removable drive such as a CD or a USB stick) is that none of your changes persist after a reboot. Even if you somehow manage to break something, a restart will return the system back to its original state.
Microsoft today released security updates to fix at least 67 vulnerabilities in its Windows operating systems and software. Redmond warns that one of the flaws is already under active attack, and that software blueprints showing how to exploit a pervasive Windows bug patched this month are now public.

The sole zero-day flaw this month is CVE-2025-33053, a remote code execution flaw in the Windows implementation of WebDAV — an HTTP extension that lets users remotely manage files and directories on a server. While WebDAV isn’t enabled by default in Windows, its presence in legacy or specialized systems still makes it a relevant target, said Seth Hoyt, senior security engineer at Automox.
Adam Barnett, lead software engineer at Rapid7, said Microsoft’s advisory for CVE-2025-33053 does not mention that the Windows implementation of WebDAV is listed as deprecated since November 2023, which in practical terms means that the WebClient service no longer starts by default.
“The advisory also has attack complexity as low, which means that exploitation does not require preparation of the target environment in any way that is beyond the attacker’s control,” Barnett said. “Exploitation relies on the user clicking a malicious link. It’s not clear how an asset would be immediately vulnerable if the service isn’t running, but all versions of Windows receive a patch, including those released since the deprecation of WebClient, like Server 2025 and Windows 11 24H2.”
Microsoft warns that an “elevation of privilege” vulnerability in the Windows Server Message Block (SMB) client (CVE-2025-33073) is likely to be exploited, given that proof-of-concept code for this bug is now public. CVE-2025-33073 has a CVSS risk score of 8.8 (out of 10), and exploitation of the flaw leads to the attacker gaining “SYSTEM” level control over a vulnerable PC.
“What makes this especially dangerous is that no further user interaction is required after the initial connection—something attackers can often trigger without the user realizing it,” said Alex Vovk, co-founder and CEO of Action1. “Given the high privilege level and ease of exploitation, this flaw poses a significant risk to Windows environments. The scope of affected systems is extensive, as SMB is a core Windows protocol used for file and printer sharing and inter-process communication.”
Beyond these highlights, 10 of the vulnerabilities fixed this month were rated “critical” by Microsoft, including eight remote code execution flaws.
Notably absent from this month’s patch batch is a fix for a newly discovered weakness in Windows Server 2025 that allows attackers to act with the privileges of any user in Active Directory. The bug, dubbed “BadSuccessor,” was publicly disclosed by researchers at Akamai on May 21, and several public proof-of-concepts are now available. Tenable’s Satnam Narang said organizations that have at least one Windows Server 2025 domain controller should review permissions for principals and limit those permissions as much as possible.
Adobe has released updates for Acrobat Reader and six other products addressing at least 259 vulnerabilities, most of them in an update for Experience Manager. Mozilla Firefox and Google Chrome both recently released security updates that require a restart of the browser to take effect. The latest Chrome update fixes two zero-day exploits in the browser (CVE-2025-5419 and CVE-2025-4664).
For a detailed breakdown on the individual security updates released by Microsoft today, check out the Patch Tuesday roundup from the SANS Internet Storm Center. Action 1 has a breakdown of patches from Microsoft and a raft of other software vendors releasing fixes this month. As always, please back up your system and/or data before patching, and feel free to drop a note in the comments if you run into any problems applying these updates.
An employee at Elon Musk’s artificial intelligence company xAI leaked a private key on GitHub that for the past two months could have allowed anyone to query private xAI large language models (LLMs) which appear to have been custom made for working with internal data from Musk’s companies, including SpaceX, Tesla and Twitter/X, KrebsOnSecurity has learned.

Image: Shutterstock, @sdx15.
Philippe Caturegli, “chief hacking officer” at the security consultancy Seralys, was the first to publicize the leak of credentials for an x.ai application programming interface (API) exposed in the GitHub code repository of a technical staff member at xAI.
Caturegli’s post on LinkedIn caught the attention of researchers at GitGuardian, a company that specializes in detecting and remediating exposed secrets in public and proprietary environments. GitGuardian’s systems constantly scan GitHub and other code repositories for exposed API keys, and fire off automated alerts to affected users.
GitGuardian’s Eric Fourrier told KrebsOnSecurity the exposed API key had access to several unreleased models of Grok, the AI chatbot developed by xAI. In total, GitGuardian found the key had access to at least 60 fine-tuned and private LLMs.
“The credentials can be used to access the X.ai API with the identity of the user,” GitGuardian wrote in an email explaining their findings to xAI. “The associated account not only has access to public Grok models (grok-2-1212, etc) but also to what appears to be unreleased (grok-2.5V), development (research-grok-2p5v-1018), and private models (tweet-rejector, grok-spacex-2024-11-04).”
Fourrier found GitGuardian had alerted the xAI employee about the exposed API key nearly two months ago — on March 2. But as of April 30, when GitGuardian directly alerted xAI’s security team to the exposure, the key was still valid and usable. xAI told GitGuardian to report the matter through its bug bounty program at HackerOne, but just a few hours later the repository containing the API key was removed from GitHub.
“It looks like some of these internal LLMs were fine-tuned on SpaceX data, and some were fine-tuned with Tesla data,” Fourrier said. “I definitely don’t think a Grok model that’s fine-tuned on SpaceX data is intended to be exposed publicly.”
xAI did not respond to a request for comment. Nor did the 28-year-old xAI technical staff member whose key was exposed.
Carole Winqwist, chief marketing officer at GitGuardian, said giving potentially hostile users free access to private LLMs is a recipe for disaster.
“If you’re an attacker and you have direct access to the model and the back end interface for things like Grok, it’s definitely something you can use for further attacking,” she said. “An attacker could it use for prompt injection, to tweak the (LLM) model to serve their purposes, or try to implant code into the supply chain.”
The inadvertent exposure of internal LLMs for xAI comes as Musk’s so-called Department of Government Efficiency (DOGE) has been feeding sensitive government records into artificial intelligence tools. In February, The Washington Post reported DOGE officials were feeding data from across the Education Department into AI tools to probe the agency’s programs and spending.
The Post said DOGE plans to replicate this process across many departments and agencies, accessing the back-end software at different parts of the government and then using AI technology to extract and sift through information about spending on employees and programs.
“Feeding sensitive data into AI software puts it into the possession of a system’s operator, increasing the chances it will be leaked or swept up in cyberattacks,” Post reporters wrote.
Wired reported in March that DOGE has deployed a proprietary chatbot called GSAi to 1,500 federal workers at the General Services Administration, part of an effort to automate tasks previously done by humans as DOGE continues its purge of the federal workforce.
A Reuters report last month said Trump administration officials told some U.S. government employees that DOGE is using AI to surveil at least one federal agency’s communications for hostility to President Trump and his agenda. Reuters wrote that the DOGE team has heavily deployed Musk’s Grok AI chatbot as part of their work slashing the federal government, although Reuters said it could not establish exactly how Grok was being used.
Caturegli said while there is no indication that federal government or user data could be accessed through the exposed x.ai API key, these private models are likely trained on proprietary data and may unintentionally expose details related to internal development efforts at xAI, Twitter, or SpaceX.
“The fact that this key was publicly exposed for two months and granted access to internal models is concerning,” Caturegli said. “This kind of long-lived credential exposure highlights weak key management and insufficient internal monitoring, raising questions about safeguards around developer access and broader operational security.”
A whistleblower at the National Labor Relations Board (NLRB) alleged last week that denizens of Elon Musk’s Department of Government Efficiency (DOGE) siphoned gigabytes of data from the agency’s sensitive case files in early March. The whistleblower said accounts created for DOGE at the NLRB downloaded three code repositories from GitHub. Further investigation into one of those code bundles shows it is remarkably similar to a program published in January 2025 by Marko Elez, a 25-year-old DOGE employee who has worked at a number of Musk’s companies.
According to a whistleblower complaint filed last week by Daniel J. Berulis, a 38-year-old security architect at the NLRB, officials from DOGE met with NLRB leaders on March 3 and demanded the creation of several all-powerful “tenant admin” accounts that were to be exempted from network logging activity that would otherwise keep a detailed record of all actions taken by those accounts.
Berulis said the new DOGE accounts had unrestricted permission to read, copy, and alter information contained in NLRB databases. The new accounts also could restrict log visibility, delay retention, route logs elsewhere, or even remove them entirely — top-tier user privileges that neither Berulis nor his boss possessed.
Berulis said he discovered one of the DOGE accounts had downloaded three external code libraries from GitHub that neither NLRB nor its contractors ever used. A “readme” file in one of the code bundles explained it was created to rotate connections through a large pool of cloud Internet addresses that serve “as a proxy to generate pseudo-infinite IPs for web scraping and brute forcing.” Brute force attacks involve automated login attempts that try many credential combinations in rapid sequence.
A search on that description in Google brings up a code repository at GitHub for a user with the account name “Ge0rg3” who published a program roughly four years ago called “requests-ip-rotator,” described as a library that will allow the user “to bypass IP-based rate-limits for sites and services.”
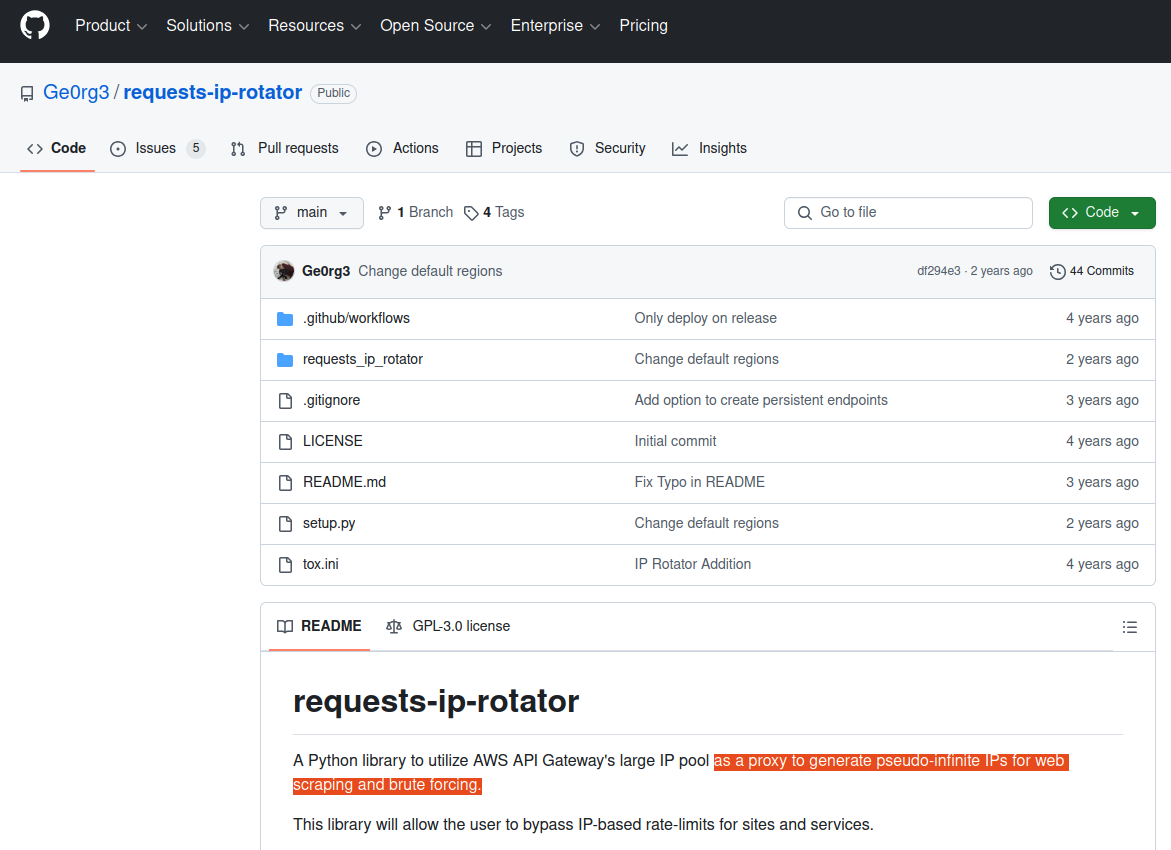
The README file from the GitHub user Ge0rg3’s page for requests-ip-rotator includes the exact wording of a program the whistleblower said was downloaded by one of the DOGE users. Marko Elez created an offshoot of this program in January 2025.
“A Python library to utilize AWS API Gateway’s large IP pool as a proxy to generate pseudo-infinite IPs for web scraping and brute forcing,” the description reads.
Ge0rg3’s code is “open source,” in that anyone can copy it and reuse it non-commercially. As it happens, there is a newer version of this project that was derived or “forked” from Ge0rg3’s code — called “async-ip-rotator” — and it was committed to GitHub in January 2025 by DOGE captain Marko Elez.

The whistleblower stated that one of the GitHub files downloaded by the DOGE employees who transferred sensitive files from an NLRB case database was an archive whose README file read: “Python library to utilize AWS API Gateway’s large IP pool as a proxy to generate pseudo-infinite IPs for web scraping and brute forcing.” Elez’s code pictured here was forked in January 2025 from a code library that shares the same description.
A key DOGE staff member who gained access to the Treasury Department’s central payments system, Elez has worked for a number of Musk companies, including X, SpaceX, and xAI. Elez was among the first DOGE employees to face public scrutiny, after The Wall Street Journal linked him to social media posts that advocated racism and eugenics.
Elez resigned after that brief scandal, but was rehired after President Donald Trump and Vice President JD Vance expressed support for him. Politico reports Elez is now a Labor Department aide detailed to multiple agencies, including the Department of Health and Human Services.
“During Elez’s initial stint at Treasury, he violated the agency’s information security policies by sending a spreadsheet containing names and payments information to officials at the General Services Administration,” Politico wrote, citing court filings.
KrebsOnSecurity sought comment from both the NLRB and DOGE, and will update this story if either responds.
The NLRB has been effectively hobbled since President Trump fired three board members, leaving the agency without the quorum it needs to function. Both Amazon and Musk’s SpaceX have been suing the NLRB over complaints the agency filed in disputes about workers’ rights and union organizing, arguing that the NLRB’s very existence is unconstitutional. On March 5, a U.S. appeals court unanimously rejected Musk’s claim that the NLRB’s structure somehow violates the Constitution.
Berulis’s complaint alleges the DOGE accounts at NLRB downloaded more than 10 gigabytes of data from the agency’s case files, a database that includes reams of sensitive records including information about employees who want to form unions and proprietary business documents. Berulis said he went public after higher-ups at the agency told him not to report the matter to the US-CERT, as they’d previously agreed.
Berulis told KrebsOnSecurity he worried the unauthorized data transfer by DOGE could unfairly advantage defendants in a number of ongoing labor disputes before the agency.
“If any company got the case data that would be an unfair advantage,” Berulis said. “They could identify and fire employees and union organizers without saying why.”

Marko Elez, in a photo from a social media profile.
Berulis said the other two GitHub archives that DOGE employees downloaded to NLRB systems included Integuru, a software framework designed to reverse engineer application programming interfaces (APIs) that websites use to fetch data; and a “headless” browser called Browserless, which is made for automating web-based tasks that require a pool of browsers, such as web scraping and automated testing.
On February 6, someone posted a lengthy and detailed critique of Elez’s code on the GitHub “issues” page for async-ip-rotator, calling it “insecure, unscalable and a fundamental engineering failure.”
“If this were a side project, it would just be bad code,” the reviewer wrote. “But if this is representative of how you build production systems, then there are much larger concerns. This implementation is fundamentally broken, and if anything similar to this is deployed in an environment handling sensitive data, it should be audited immediately.”
Further reading: Berulis’s complaint (PDF).
Update 7:06 p.m. ET: Elez’s code repo was deleted after this story was published. An archived version of it is here.
Welcome to TruffleHog Explorer, a user-friendly web-based tool to visualize and analyze data extracted using TruffleHog. TruffleHog is one of the most powerful secrets discovery, classification, validation, and analysis open source tool. In this context, a secret refers to a credential a machine uses to authenticate itself to another machine. This includes API keys, database passwords, private encryption keys, and more.
With an improved UI/UX, powerful filtering options, and export capabilities, this tool helps security professionals efficiently review potential secrets and credentials found in their repositories.
⚠️ This dashboard has been tested only with GitHub TruffleHog JSON outputs. Expect updates soon to support additional formats and platforms.
You can use online version here: TruffleHog Explorer
$ git clone https://github.com/yourusername/trufflehog-explorer.git
$ cd trufflehog-explorer
index.html
Simply open the index.html file in your preferred web browser.
$ open index.html
.json files from TruffleHog output.Happy Securing! 🔒
Microsoft today released updates to plug at least 121 security holes in its Windows operating systems and software, including one vulnerability that is already being exploited in the wild. Eleven of those flaws earned Microsoft’s most-dire “critical” rating, meaning malware or malcontents could exploit them with little to no interaction from Windows users.

The zero-day flaw already seeing exploitation is CVE-2025-29824, a local elevation of privilege bug in the Windows Common Log File System (CLFS) driver. Microsoft rates it as “important,” but as Chris Goettl from Ivanti points out, risk-based prioritization warrants treating it as critical.
This CLFS component of Windows is no stranger to Patch Tuesday: According to Tenable’s Satnam Narang, since 2022 Microsoft has patched 32 CLFS vulnerabilities — averaging 10 per year — with six of them exploited in the wild. The last CLFS zero-day was patched in December 2024.
Narang notes that while flaws allowing attackers to install arbitrary code are consistently top overall Patch Tuesday features, the data is reversed for zero-day exploitation.
“For the past two years, elevation of privilege flaws have led the pack and, so far in 2025, account for over half of all zero-days exploited,” Narang wrote.
Rapid7’s Adam Barnett warns that any Windows defenders responsible for an LDAP server — which means almost any organization with a non-trivial Microsoft footprint — should add patching for the critical flaw CVE-2025-26663 to their to-do list.
“With no privileges required, no need for user interaction, and code execution presumably in the context of the LDAP server itself, successful exploitation would be an attractive shortcut to any attacker,” Barnett said. “Anyone wondering if today is a re-run of December 2024 Patch Tuesday can take some small solace in the fact that the worst of the trio of LDAP critical RCEs published at the end of last year was likely easier to exploit than today’s example, since today’s CVE-2025-26663 requires that an attacker win a race condition. Despite that, Microsoft still expects that exploitation is more likely.”
Among the critical updates Microsoft patched this month are remote code execution flaws in Windows Remote Desktop services (RDP), including CVE-2025-26671, CVE-2025-27480 and CVE-2025-27482; only the latter two are rated “critical,” and Microsoft marked both of them as “Exploitation More Likely.”
Perhaps the most widespread vulnerabilities fixed this month were in web browsers. Google Chrome updated to fix 13 flaws this week, and Mozilla Firefox fixed eight bugs, with possibly more updates coming later this week for Microsoft Edge.
As it tends to do on Patch Tuesdays, Adobe has released 12 updates resolving 54 security holes across a range of products, including ColdFusion, Adobe Commerce, Experience Manager Forms, After Effects, Media Encoder, Bridge, Premiere Pro, Photoshop, Animate, AEM Screens, and FrameMaker.
Apple users may need to patch as well. On March 31, Apple released a huge security update (more than three gigabytes in size) to fix issues in a range of their products, including at least one zero-day flaw.
And in case you missed it, on March 31, 2025 Apple released a rather large batch of security updates for a wide range of their products, from macOS to the iOS operating systems on iPhones and iPads.
Earlier today, Microsoft included a note saying Windows 10 security updates weren’t available but would be released as soon as possible. It appears from browsing askwoody.com that this snafu has since been rectified. Either way, if you run into complications applying any of these updates please leave a note about it in the comments below, because the chances are good that someone else had the same problem.
As ever, please consider backing up your data and or devices prior to updating, which makes it far less complicated to undo a software update gone awry. For more granular details on today’s Patch Tuesday, check out the SANS Internet Storm Center’s roundup. Microsoft’s update guide for April 2025 is here.
For more details on Patch Tuesday, check out the write-ups from Action1 and Automox.
A Minnesota cybersecurity and computer forensics expert whose testimony has featured in thousands of courtroom trials over the past 30 years is facing questions about his credentials and an inquiry from the Federal Bureau of Investigation (FBI). Legal experts say the inquiry could be grounds to reopen a number of adjudicated cases in which the expert’s testimony may have been pivotal.
One might conclude from reading Mr. Lanterman’s LinkedIn profile that has a degree from Harvard University.
Mark Lanterman is a former investigator for the U.S. Secret Service Electronics Crimes Task Force who founded the Minneapolis consulting firm Computer Forensic Services (CFS). The CFS website says Lanterman’s 30-year career has seen him testify as an expert in more than 2,000 cases, with experience in cases involving sexual harassment and workplace claims, theft of intellectual property and trade secrets, white-collar crime, and class action lawsuits.
Or at least it did until last month, when Lanterman’s profile and work history were quietly removed from the CFS website. The removal came after Hennepin County Attorney’s Office said it was notifying parties to ten pending cases that they were unable to verify Lanterman’s educational and employment background. The county attorney also said the FBI is now investigating the allegations.
Those allegations were raised by Sean Harrington, an attorney and forensics examiner based in Prescott, Wisconsin. Harrington alleged that Lanterman lied under oath in court on multiple occasions when he testified that he has a Bachelor of Science and a Master’s degree in computer science from the now-defunct Upsala College, and that he completed his postgraduate work in cybersecurity at Harvard University.
Harrington’s claims gained steam thanks to digging by the law firm Perkins Coie LLP, which is defending a case wherein a client’s laptop was forensically reviewed by Lanterman. On March 14, Perkins Coie attorneys asked the judge (PDF) to strike Lanterman’s testimony because neither he nor they could substantiate claims about his educational background.
Upsala College, located in East Orange, N.J., operated for 102 years until it closed in 1995 after a period of declining enrollment and financial difficulties. Perkins Coie told the court that they’d visited Felician University, which holds the transcripts for Upsala College during the years Lanterman claimed to have earned undergraduate and graduate degrees. The law firm said Felician had no record of transcripts for Lanterman (PDF), and that his name was absent from all of the Upsala College student yearbooks and commencement programs during that period.
Reached for comment, Lanterman acknowledged he had no way to prove he attended Upsala College, and that his “postgraduate work” at Harvard was in fact an eight-week online cybersecurity class called HarvardX, which cautions that its certificates should not be considered equivalent to a Harvard degree or a certificate earned through traditional, in-person programs at Harvard University.
Lanterman has testified that his first job after college was serving as a police officer in Springfield Township, Pennsylvania, although the Perkins Coie attorneys noted that this role was omitted from his resume. The attorneys said when they tried to verify Lanterman’s work history, “the police department responded with a story that would be almost impossible to believe if it was not corroborated by Lanterman’s own email communications.”
As recounted in the March 14 filing, Lanterman was deposed on Feb. 11, and the following day he emailed the Springfield Township Police Department to see if he could have a peek at his old personnel file. On Feb. 14, Lanterman visited the Springfield Township PD and asked to borrow his employment record. He told the officer he spoke with on the phone that he’d recently been instructed to “get his affairs in order” after being diagnosed with a grave heart condition, and that he wanted his old file to show his family about his early career.
According to Perkins Coie, Lanterman left the Springfield Township PD with his personnel file, and has not returned it as promised.
“It is shocking that an expert from Minnesota would travel to suburban Philadelphia and abscond with his decades-old personnel file to obscure his background,” the law firm wrote. “That appears to be the worst and most egregious form of spoliation, and the deception alone is reason enough to exclude Lanterman and consider sanctions.”
Harrington initially contacted KrebsOnSecurity about his concerns in late 2023, fuming after sitting through a conference speech in which Lanterman shared documents from a ransomware victim and told attendees it was because they’d refused to hire his company to perform a forensic investigation on a recent breach.
“He claims he was involved in the Martha Stewart investigation, the Bernie Madoff trial, Paul McCartney’s divorce, the Tom Petters investigation, the Denny Hecker investigation, and many others,” Harrington said. “He claims to have been invited to speak to the Supreme Court, claims to train the ‘entire federal judiciary’ on cybersecurity annually, and is a faculty member of the United States Judicial Conference and the Judicial College — positions which he obtained, in part, on a house of fraudulent cards.”
In an interview this week, Harrington said court documents reveal that at least two of Lanterman’s previous clients complained CFS had held their data for ransom over billing disputes. In a declaration (PDF) dated August 2022, the co-founder of the law firm MoreLaw Minneapolis LLC said she hired Lanterman in 2014 to examine several electronic devices after learning that one of their paralegals had a criminal fraud history.
But the law firm said when it pushed back on a consulting bill that was far higher than expected, Lanterman told them CFS would “escalate” its collection efforts if they didn’t pay, including “a claim and lien against the data which will result in a public auction of your data.”
“All of us were flabbergasted by Mr. Lanterman’s email,” wrote MoreLaw co-founder Kimberly Hanlon. “I had never heard of any legitimate forensic company threatening to ‘auction’ off an attorney’s data, particularly knowing that the data is comprised of confidential client data, much of which is sensitive in nature.”
In 2009, a Wisconsin-based manufacturing company that had hired Lanterman for computer forensics balked at paying an $86,000 invoice from CFS, calling it “excessive and unsubstantiated.” The company told a Hennepin County court that on April 15, 2009, CFS conducted an auction of its trade secret information in violation of their confidentiality agreement.
“CFS noticed and conducted a Public Sale of electronic information that was entrusted to them pursuant to the terms of the engagement agreement,” the company wrote. “CFS submitted the highest bid at the Public Sale in the amount of $10,000.”

Lanterman briefly responded to a list of questions about his background (and recent heart diagnosis) on March 24, saying he would send detailed replies the following day. Those replies never materialized. Instead, Lanterman forwarded a recent memo he wrote to the court that attacked Harrington and said his accuser was only trying to take out a competitor. He has not responded to further requests for comment.
“When I attended Upsala, I was a commuter student who lived with my grandparents in Morristown, New Jersey approximately 30 minutes away from Upsala College,” Lanterman explained to the judge (PDF) overseeing a separate ongoing case (PDF) in which he has testified. “With limited resources, I did not participate in campus social events, nor did I attend graduation ceremonies. In 2023, I confirmed with Felician University — which maintains Upsala College’s records — that they could not locate my transcripts or diploma, a situation that they indicated was possibly due to unresolved money-related issues.”
Lanterman was ordered to appear in court on April 3 in the case defended by Perkins Coie, but he did not show up. Instead, he sent a message to the judge withdrawing from the case.
“I am 60 years old,” Lanterman told the judge. “I created my business from nothing. I am done dealing with the likes of individuals like Sean Harrington. And quite frankly, I have been planning at turning over my business to my children for years. That time has arrived.”
Lanterman’s letter leaves the impression that it was his decision to retire. But according to an affidavit (PDF) filed in a Florida case on March 28, Mark Lanterman’s son Sean said he’d made the difficult decision to ask his dad to step down given all the negative media attention.
Mark Rasch, a former federal cybercrime prosecutor who now serves as counsel to the New York cybersecurity intelligence firm Unit 221B, said that if an expert witness is discredited, any defendants who lost cases that were strongly influenced by that expert’s conclusions at trial could have grounds for appeal.
Rasch said law firms who propose an expert witness have a duty in good faith to vet that expert’s qualifications, knowing that those credentials will be subject to cross-examination.
“Federal rules of civil procedure and evidence both require experts to list every case they have testified in as an expert for the past few years,” Rasch said. “Part of that due diligence is pulling up the results of those cases and seeing what the nature of their testimony has been.”
Perhaps the most well-publicized case involving significant forensic findings from Lanterman was the 2018 conviction of Stephen Allwine, who was found guilty of killing his wife two years earlier after attempts at hiring a hitman on the dark net fell through. Allwine is serving a sentence of life in prison, and continues to maintain that he was framed, casting doubt on computer forensic evidence found on 64 electronic devices taken from his home.
On March 24, Allwine petitioned a Minnesota court (PDF) to revisit his case, citing the accusations against Lanterman and his role as a key witness for the prosecution.