A cybercriminal group that used voice phishing attacks to siphon more than a billion records from Salesforce customers earlier this year has launched a website that threatens to publish data stolen from dozens of Fortune 500 firms if they refuse to pay a ransom. The group also claimed responsibility for a recent breach involving Discord user data, and for stealing terabytes of sensitive files from thousands of customers of the enterprise software maker Red Hat.
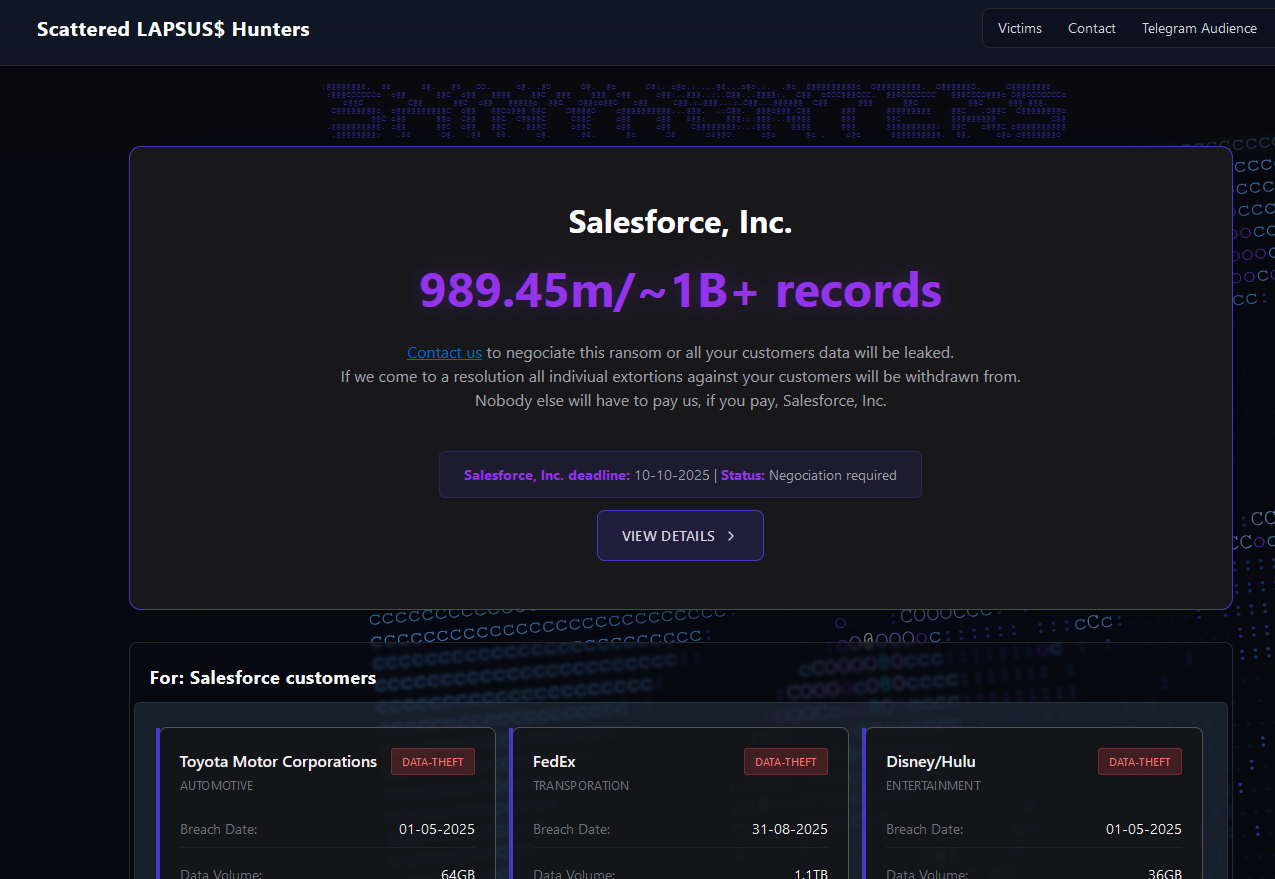
The new extortion website tied to ShinyHunters (UNC6040), which threatens to publish stolen data unless Salesforce or individual victim companies agree to pay a ransom.
In May 2025, a prolific and amorphous English-speaking cybercrime group known as ShinyHunters launched a social engineering campaign that used voice phishing to trick targets into connecting a malicious app to their organization’s Salesforce portal.
The first real details about the incident came in early June, when the Google Threat Intelligence Group (GTIG) warned that ShinyHunters — tracked by Google as UNC6040 — was extorting victims over their stolen Salesforce data, and that the group was poised to launch a data leak site to publicly shame victim companies into paying a ransom to keep their records private. A month later, Google acknowledged that one of its own corporate Salesforce instances was impacted in the voice phishing campaign.
Last week, a new victim shaming blog dubbed “Scattered LAPSUS$ Hunters” began publishing the names of companies that had customer Salesforce data stolen as a result of the May voice phishing campaign.
“Contact us to negotiate this ransom or all your customers data will be leaked,” the website stated in a message to Salesforce. “If we come to a resolution all individual extortions against your customers will be withdrawn from. Nobody else will have to pay us, if you pay, Salesforce, Inc.”
Below that message were more than three dozen entries for companies that allegedly had Salesforce data stolen, including Toyota, FedEx, Disney/Hulu, and UPS. The entries for each company specified the volume of stolen data available, as well as the date that the information was retrieved (the stated breach dates range between May and September 2025).
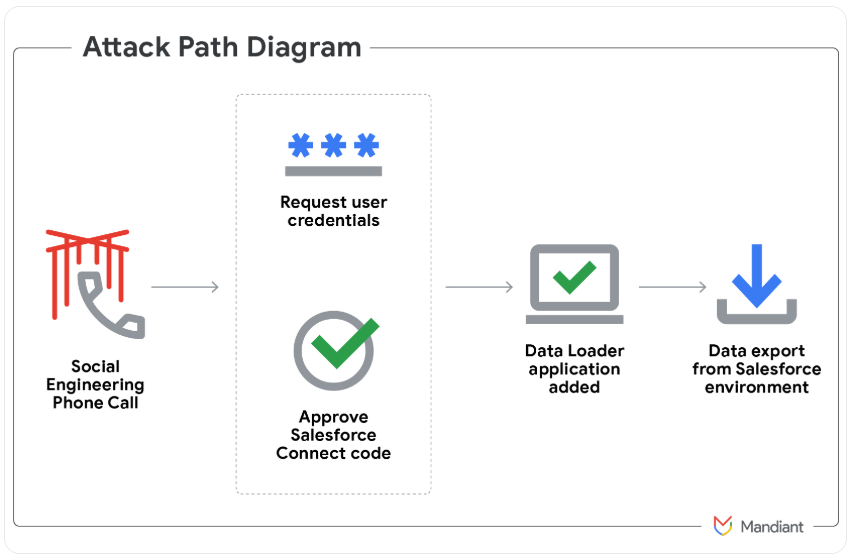
Image: Mandiant.
On October 5, the Scattered LAPSUS$ Hunters victim shaming and extortion blog announced that the group was responsible for a breach in September involving a GitLab server used by Red Hat that contained more than 28,000 Git code repositories, including more than 5,000 Customer Engagement Reports (CERs).
“Alot of folders have their client’s secrets such as artifactory access tokens, git tokens, azure, docker (redhat docker, azure containers, dockerhub), their client’s infrastructure details in the CERs like the audits that were done for them, and a whole LOT more, etc.,” the hackers claimed.
Their claims came several days after a previously unknown hacker group calling itself the Crimson Collective took credit for the Red Hat intrusion on Telegram.
Red Hat disclosed on October 2 that attackers had compromised a company GitLab server, and said it was in the process of notifying affected customers.
“The compromised GitLab instance housed consulting engagement data, which may include, for example, Red Hat’s project specifications, example code snippets, internal communications about consulting services, and limited forms of business contact information,” Red Hat wrote.
Separately, Discord has started emailing users affected by another breach claimed by ShinyHunters. Discord said an incident on September 20 at a “third-party customer service provider” impacted a “limited number of users” who communicated with Discord customer support or Trust & Safety teams. The information included Discord usernames, emails, IP address, the last four digits of any stored payment cards, and government ID images submitted during age verification appeals.
The Scattered Lapsus$ Hunters claim they will publish data stolen from Salesforce and its customers if ransom demands aren’t paid by October 10. The group also claims it will soon begin extorting hundreds more organizations that lost data in August after a cybercrime group stole vast amounts of authentication tokens from Salesloft, whose AI chatbot is used by many corporate websites to convert customer interaction into Salesforce leads.
In a communication sent to customers today, Salesforce emphasized that the theft of any third-party Salesloft data allegedly stolen by ShinyHunters did not originate from a vulnerability within the core Salesforce platform. The company also stressed that it has no plans to meet any extortion demands.
“Salesforce will not engage, negotiate with, or pay any extortion demand,” the message to customers read. “Our focus is, and remains, on defending our environment, conducting thorough forensic analysis, supporting our customers, and working with law enforcement and regulatory authorities.”
The GTIG tracked the group behind the Salesloft data thefts as UNC6395, and says the group has been observed harvesting the data for authentication tokens tied to a range of cloud services like Snowflake and Amazon’s AWS.
Google catalogs Scattered Lapsus$ Hunters by so many UNC names (throw in UNC6240 for good measure) because it is thought to be an amalgamation of three hacking groups — Scattered Spider, Lapsus$ and ShinyHunters. The members of these groups hail from many of the same chat channels on the Com, a mostly English-language cybercriminal community that operates across an ocean of Telegram and Discord servers.
The Scattered Lapsus$ Hunters darknet blog is currently offline. The outage appears to have coincided with the disappearance of the group’s new clearnet blog — breachforums[.]hn — which vanished after shifting its Domain Name Service (DNS) servers from DDoS-Guard to Cloudflare.
But before it died, the websites disclosed that hackers were exploiting a critical zero-day vulnerability in Oracle’s E-Business Suite software. Oracle has since confirmed that a security flaw tracked as CVE-2025-61882 allows attackers to perform unauthenticated remote code execution, and is urging customers to apply an emergency update to address the weakness.
Mandiant’s Charles Carmakal shared on LinkedIn that CVE-2025-61882 was initially exploited in August 2025 by the Clop ransomware gang to steal data from Oracle E-Business Suite servers. Bleeping Computer writes that news of the Oracle zero-day first surfaced on the Scattered Lapsus$ Hunters blog, which published a pair of scripts that were used to exploit vulnerable Oracle E-Business Suite instances.
On Monday evening, KrebsOnSecurity received a malware-laced message from a reader that threatened physical violence unless their unstated demands were met. The missive, titled “Shiny hunters,” contained the hashtag $LAPSU$$SCATEREDHUNTER, and urged me to visit a page on limewire[.]com to view their demands.
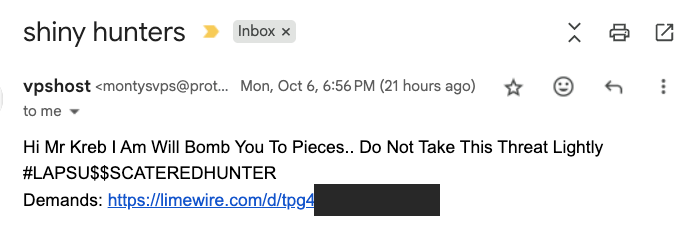
A screenshot of the phishing message linking to a malicious trojan disguised as a Windows screensaver file.
KrebsOnSecurity did not visit this link, but instead forwarded it to Mandiant, which confirmed that similar menacing missives were sent to employees at Mandiant and other security firms around the same time.
The link in the message fetches a malicious trojan disguised as a Windows screensaver file (Virustotal’s analysis on this malware is here). Simply viewing the booby-trapped screensaver on a Windows PC is enough to cause the bundled trojan to launch in the background.
Mandiant’s Austin Larsen said the trojan is a commercially available backdoor known as ASYNCRAT, a .NET-based backdoor that communicates using a custom binary protocol over TCP, and can execute shell commands and download plugins to extend its features.
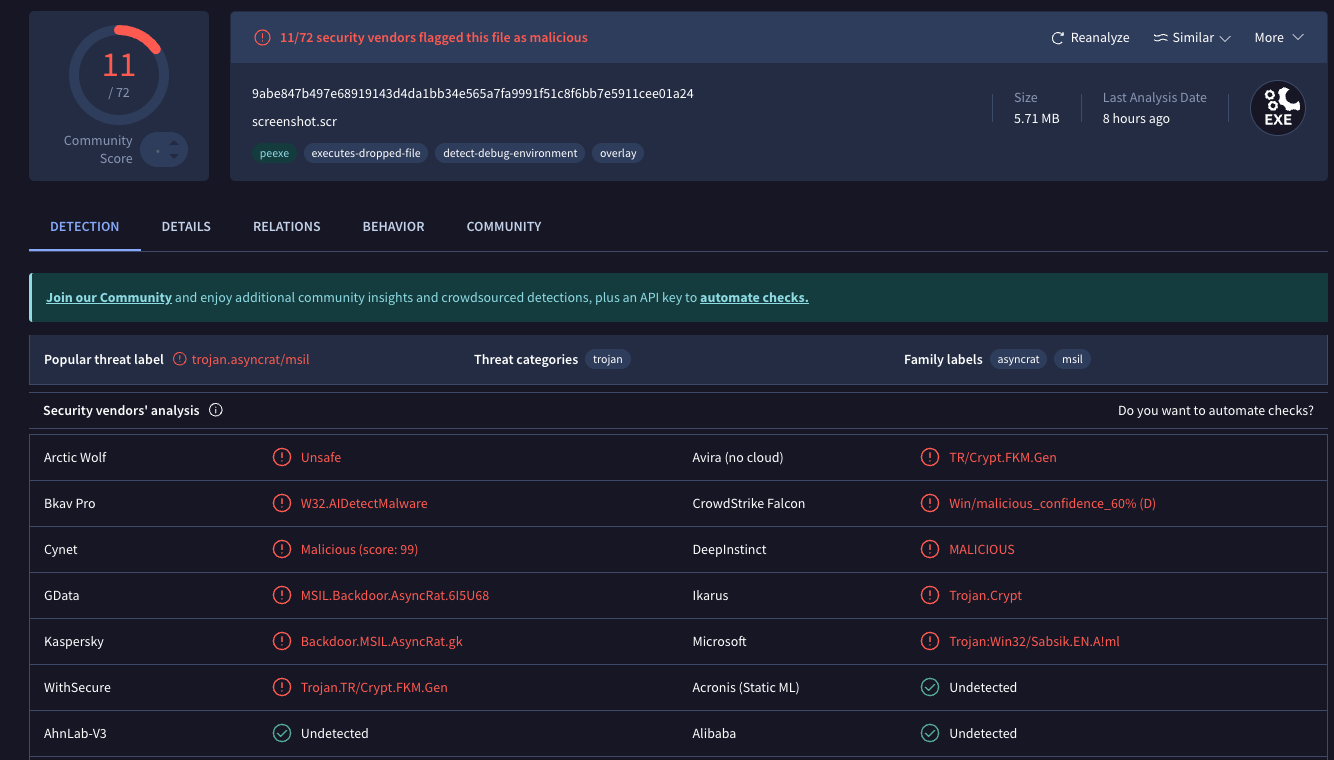
A scan of the malicious screensaver file at Virustotal.com shows it is detected as bad by nearly a dozen security and antivirus tools.
“Downloaded plugins may be executed directly in memory or stored in the registry,” Larsen wrote in an analysis shared via email. “Capabilities added via plugins include screenshot capture, file transfer, keylogging, video capture, and cryptocurrency mining. ASYNCRAT also supports a plugin that targets credentials stored by Firefox and Chromium-based web browsers.”
Malware-laced targeted emails are not out of character for certain members of the Scattered Lapsus$ Hunters, who have previously harassed and threatened security researchers and even law enforcement officials who are investigating and warning about the extent of their attacks.
With so many big data breaches and ransom attacks now coming from cybercrime groups operating on the Com, law enforcement agencies on both sides of the pond are under increasing pressure to apprehend the criminal hackers involved. In late September, prosecutors in the U.K. charged two alleged Scattered Spider members aged 18 and 19 with extorting at least $115 million in ransom payments from companies victimized by data theft.
U.S. prosecutors heaped their own charges on the 19 year-old in that duo — U.K. resident Thalha Jubair — who is alleged to have been involved in data ransom attacks against Marks & Spencer and Harrods, the British food retailer Co-op Group, and the 2023 intrusions at MGM Resorts and Caesars Entertainment. Jubair also was allegedly a key member of LAPSUS$, a cybercrime group that broke into dozens of technology companies beginning in late 2021.
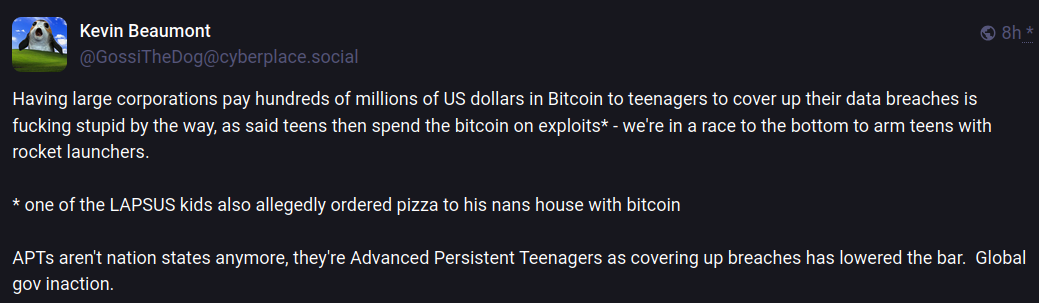
A Mastodon post by Kevin Beaumont, lamenting the prevalence of major companies paying millions to extortionist teen hackers, refers derisively to Thalha Jubair as a part of an APT threat known as “Advanced Persistent Teenagers.”
In August, convicted Scattered Spider member and 20-year-old Florida man Noah Michael Urban was sentenced to 10 years in federal prison and ordered to pay roughly $13 million in restitution to victims.
In April 2025, a 23-year-old Scottish man thought to be an early Scattered Spider member was extradited from Spain to the U.S., where he is facing charges of wire fraud, conspiracy and identity theft. U.S. prosecutors allege Tyler Robert Buchanan and co-conspirators hacked into dozens of companies in the United States and abroad, and that he personally controlled more than $26 million stolen from victims.
Update, Oct. 8, 8:59 a.m. ET: A previous version of this story incorrectly referred to the malware sent by the reader as a Windows screenshot file. Rather, it is a Windows screensaver file.
The recent mass-theft of authentication tokens from Salesloft, whose AI chatbot is used by a broad swath of corporate America to convert customer interaction into Salesforce leads, has left many companies racing to invalidate the stolen credentials before hackers can exploit them. Now Google warns the breach goes far beyond access to Salesforce data, noting the hackers responsible also stole valid authentication tokens for hundreds of online services that customers can integrate with Salesloft, including Slack, Google Workspace, Amazon S3, Microsoft Azure, and OpenAI.

Salesloft says its products are trusted by 5,000+ customers. Some of the bigger names are visible on the company’s homepage.
Salesloft disclosed on August 20 that, “Today, we detected a security issue in the Drift application,” referring to the technology that powers an AI chatbot used by so many corporate websites. The alert urged customers to re-authenticate the connection between the Drift and Salesforce apps to invalidate their existing authentication tokens, but it said nothing then to indicate those tokens had already been stolen.
On August 26, the Google Threat Intelligence Group (GTIG) warned that unidentified hackers tracked as UNC6395 used the access tokens stolen from Salesloft to siphon large amounts of data from numerous corporate Salesforce instances. Google said the data theft began as early as Aug. 8, 2025 and lasted through at least Aug. 18, 2025, and that the incident did not involve any vulnerability in the Salesforce platform.
Google said the attackers have been sifting through the massive data haul for credential materials such as AWS keys, VPN credentials, and credentials to the cloud storage provider Snowflake.
“If successful, the right credentials could allow them to further compromise victim and client environments, as well as pivot to the victim’s clients or partner environments,” the GTIG report stated.
The GTIG updated its advisory on August 28 to acknowledge the attackers used the stolen tokens to access email from “a very small number of Google Workspace accounts” that were specially configured to integrate with Salesloft. More importantly, it warned organizations to immediately invalidate all tokens stored in or connected to their Salesloft integrations — regardless of the third-party service in question.
“Given GTIG’s observations of data exfiltration associated with the campaign, organizations using Salesloft Drift to integrate with third-party platforms (including but not limited to Salesforce) should consider their data compromised and are urged to take immediate remediation steps,” Google advised.
On August 28, Salesforce blocked Drift from integrating with its platform, and with its productivity platforms Slack and Pardot.
The Salesloft incident comes on the heels of a broad social engineering campaign that used voice phishing to trick targets into connecting a malicious app to their organization’s Salesforce portal. That campaign led to data breaches and extortion attacks affecting a number of companies including Adidas, Allianz Life and Qantas.
On August 5, Google disclosed that one of its corporate Salesforce instances was compromised by the attackers, which the GTIG has dubbed UNC6040 (“UNC” stands for “uncategorized threat group”). Google said the extortionists consistently claimed to be the threat group ShinyHunters, and that the group appeared to be preparing to escalate its extortion attacks by launching a data leak site.
ShinyHunters is an amorphous threat group known for using social engineering to break into cloud platforms and third-party IT providers, and for posting dozens of stolen databases to cybercrime communities like the now-defunct Breachforums.
The ShinyHunters brand dates back to 2020, and the group has been credited with or taken responsibility for dozens of data leaks that exposed hundreds of millions of breached records. The group’s member roster is thought to be somewhat fluid, drawing mainly from active denizens of the Com, a mostly English-language cybercrime community scattered across an ocean of Telegram and Discord servers.
Recorded Future’s Alan Liska told Bleeping Computer that the overlap in the “tools, techniques and procedures” used by ShinyHunters and the Scattered Spider extortion group likely indicate some crossover between the two groups.
To muddy the waters even further, on August 28 a Telegram channel that now has nearly 40,000 subscribers was launched under the intentionally confusing banner “Scattered LAPSUS$ Hunters 4.0,” wherein participants have repeatedly claimed responsibility for the Salesloft hack without actually sharing any details to prove their claims.
The Telegram group has been trying to attract media attention by threatening security researchers at Google and other firms. It also is using the channel’s sudden popularity to promote a new cybercrime forum called “Breachstars,” which they claim will soon host data stolen from victim companies who refuse to negotiate a ransom payment.
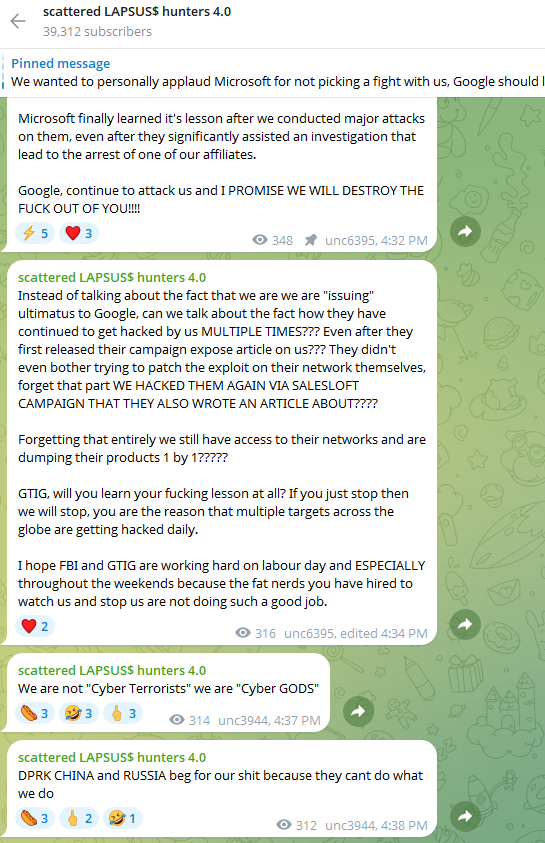
The “Scattered Lapsus$ Hunters 4.0” channel on Telegram now has roughly 40,000 subscribers.
But Austin Larsen, a principal threat analyst at Google’s threat intelligence group, said there is no compelling evidence to attribute the Salesloft activity to ShinyHunters or to other known groups at this time.
“Their understanding of the incident seems to come from public reporting alone,” Larsen told KrebsOnSecurity, referring to the most active participants in the Scattered LAPSUS$ Hunters 4.0 Telegram channel.
Joshua Wright, a senior technical director at Counter Hack, is credited with coining the term “authorization sprawl” to describe one key reason that social engineering attacks from groups like Scattered Spider and ShinyHunters so often succeed: They abuse legitimate user access tokens to move seamlessly between on-premises and cloud systems.
Wright said this type of attack chain often goes undetected because the attacker sticks to the resources and access already allocated to the user.
“Instead of the conventional chain of initial access, privilege escalation and endpoint bypass, these threat actors are using centralized identity platforms that offer single sign-on (SSO) and integrated authentication and authorization schemes,” Wright wrote in a June 2025 column. “Rather than creating custom malware, attackers use the resources already available to them as authorized users.”
It remains unclear exactly how the attackers gained access to all Salesloft Drift authentication tokens. Salesloft announced on August 27 that it hired Mandiant, Google Cloud’s incident response division, to investigate the root cause(s).
“We are working with Salesloft Drift to investigate the root cause of what occurred and then it’ll be up to them to publish that,” Mandiant Consulting CTO Charles Carmakal told Cyberscoop. “There will be a lot more tomorrow, and the next day, and the next day.”
A 25-year-old man in Ontario, Canada has been arrested for allegedly stealing data from and extorting more than 160 companies that used the cloud data service Snowflake.

Image: https://www.pomerium.com/blog/the-real-lessons-from-the-snowflake-breach
On October 30, Canadian authorities arrested Alexander Moucka, a.k.a. Connor Riley Moucka of Kitchener, Ontario, on a provisional arrest warrant from the United States. Bloomberg first reported Moucka’s alleged ties to the Snowflake hacks on Monday.
At the end of 2023, malicious hackers learned that many large companies had uploaded huge volumes of sensitive customer data to Snowflake accounts that were protected with little more than a username and password (no multi-factor authentication required). After scouring darknet markets for stolen Snowflake account credentials, the hackers began raiding the data storage repositories used by some of the world’s largest corporations.
Among those was AT&T, which disclosed in July that cybercriminals had stolen personal information and phone and text message records for roughly 110 million people — nearly all of its customers. Wired.com reported in July that AT&T paid a hacker $370,000 to delete stolen phone records.
A report on the extortion attacks from the incident response firm Mandiant notes that Snowflake victim companies were privately approached by the hackers, who demanded a ransom in exchange for a promise not to sell or leak the stolen data. All told, more than 160 Snowflake customers were relieved of data, including TicketMaster, Lending Tree, Advance Auto Parts and Neiman Marcus.
Moucka is alleged to have used the hacker handles Judische and Waifu, among many others. These monikers correspond to a prolific cybercriminal whose exploits were the subject of a recent story published here about the overlap between Western, English-speaking cybercriminals and extremist groups that harass and extort minors into harming themselves or others.
On May 2, 2024, Judische claimed on the fraud-focused Telegram channel Star Chat that they had hacked Santander Bank, one of the first known Snowflake victims. Judische would repeat that claim in Star Chat on May 13 — the day before Santander publicly disclosed a data breach — and would periodically blurt out the names of other Snowflake victims before their data even went up for sale on the cybercrime forums.
404 Media reports that at a court hearing in Ontario this morning, Moucka called in from a prison phone and said he was seeking legal aid to hire an attorney.
Mandiant has attributed the Snowflake compromises to a group it calls “UNC5537,” with members based in North America and Turkey. Sources close to the investigation tell KrebsOnSecurity the UNC5537 member in Turkey is John Erin Binns, an elusive American man indicted by the U.S. Department of Justice (DOJ) for a 2021 breach at T-Mobile that exposed the personal information of at least 76.6 million customers.
Update: The Justice Department has unsealed an indictment (PDF) against Moucka and Binns, charging them with one count of conspiracy; 10 counts of wire fraud; four counts of computer fraud and abuse; two counts of extortion in relation to computer fraud; and two counts aggravated identity theft.
In a statement on Moucka’s arrest, Mandiant said UNC5537 aka Alexander ‘Connor’ Moucka has proven to be one of the most consequential threat actors of 2024.
“In April 2024, UNC5537 launched a campaign, systematically compromising misconfigured SaaS instances across over a hundred organizations,” wrote Austin Larsen, Mandiant’s senior threat analyst. “The operation, which left organizations reeling from significant data loss and extortion attempts, highlighted the alarming scale of harm an individual can cause using off-the-shelf tools.”
Sources involved in the investigation said UNC5537 has focused on hacking into telecommunications companies around the world. Those sources told KrebsOnSecurity that Binns and Judische are suspected of stealing data from India’s largest state-run telecommunications firm Bharat Sanchar Nigam Ltd (BNSL), and that the duo even bragged about being able to intercept or divert phone calls and text messages for a large portion of the population of India.
Judische appears to have outsourced the sale of databases from victim companies who refuse to pay, delegating some of that work to a cybercriminal who uses the nickname Kiberphant0m on multiple forums. In late May 2024, Kiberphant0m began advertising the sale of hundreds of gigabytes of data stolen from BSNL.
“Information is worth several million dollars but I’m selling for pretty cheap,” Kiberphant0m wrote of the BSNL data in a post on the English-language cybercrime community Breach Forums. “Negotiate a deal in Telegram.”

Also in May 2024, Kiberphant0m took to the Russian-language hacking forum XSS to sell more than 250 gigabytes of data stolen from an unnamed mobile telecom provider in Asia, including a database of all active customers and software allowing the sending of text messages to all customers.
On September 3, 2024, Kiberphant0m posted a sales thread on XSS titled “Selling American Telecom Access (100B+ Revenue).” Kiberphant0m’s asking price of $200,000 was apparently too high because they reposted the sales thread on Breach Forums a month later, with a headline that more clearly explained the data was stolen from Verizon‘s “push-to-talk” (PTT) customers — primarily U.S. government agencies and first responders.
404Media reported recently that the breach does not appear to impact the main consumer Verizon network. Rather, the hackers broke into a third party provider and stole data on Verizon’s PTT systems, which are a separate product marketed towards public sector agencies, enterprises, and small businesses to communicate internally.
Investigators say Moucka shared a home in Kitchener with other tenants, but not his family. His mother was born in Chechnya, and he speaks Russian in addition to French and English. Moucka’s father died of a drug overdose at age 26, when the defendant was roughly five years old.
A person claiming to be Judische began communicating with this author more than three months ago on Signal after KrebsOnSecurity started asking around about hacker nicknames previously used by Judische over the years.
Judische admitted to stealing and ransoming data from Snowflake customers, but he said he’s not interested in selling the information, and that others have done this with some of the data sets he stole.
“I’m not really someone that sells data unless it’s crypto [databases] or credit cards because they’re the only thing I can find buyers for that actually have money for the data,” Judische told KrebsOnSecurity. “The rest is just ransom.”
Judische has sent this reporter dozens of unsolicited and often profane messages from several different Signal accounts, all of which claimed to be an anonymous tipster sharing different identifying details for Judische. This appears to have been an elaborate effort by Judische to “detrace” his movements online and muddy the waters about his identity.
Judische frequently claimed he had unparalleled “opsec” or operational security, a term that refers to the ability to compartmentalize and obfuscate one’s tracks online. In an effort to show he was one step ahead of investigators, Judische shared information indicating someone had given him a Mandiant researcher’s assessment of who and where they thought he was. Mandiant says those were discussion points shared with select reporters in advance of the researcher’s recent talk at the LabsCon security conference.
But in a conversation with KrebsOnSecurity on October 26, Judische acknowledged it was likely that the authorities were closing in on him, and said he would seriously answer certain questions about his personal life.
“They’re coming after me for sure,” he said.
In several previous conversations, Judische referenced suffering from an unspecified personality disorder, and when pressed said he has a condition called “schizotypal personality disorder” (STPD).
According to the Cleveland Clinic, schizotypal personality disorder is marked by a consistent pattern of intense discomfort with relationships and social interactions: “People with STPD have unusual thoughts, speech and behaviors, which usually hinder their ability to form and maintain relationships.”
Judische said he was prescribed medication for his psychological issues, but that he doesn’t take his meds. Which might explain why he never leaves his home.
“I never go outside,” Judische allowed. “I’ve never had a friend or true relationship not online nor in person. I see people as vehicles to achieve my ends no matter how friendly I may seem on the surface, which you can see by how fast I discard people who are loyal or [that] I’ve known a long time.”
Judische later admitted he doesn’t have an official STPD diagnosis from a physician, but said he knows that he exhibits all the signs of someone with this condition.
“I can’t actually get diagnosed with that either,” Judische shared. “Most countries put you on lists and restrict you from certain things if you have it.”
Asked whether he has always lived at his current residence, Judische replied that he had to leave his hometown for his own safety.
“I can’t live safely where I’m from without getting robbed or arrested,” he said, without offering more details.
A source familiar with the investigation said Moucka previously lived in Quebec, which he allegedly fled after being charged with harassing others on the social network Discord.
Judische claims to have made at least $4 million in his Snowflake extortions. Judische said he and others frequently targeted business process outsourcing (BPO) companies, staffing firms that handle customer service for a wide range of organizations. They also went after managed service providers (MSPs) that oversee IT support and security for multiple companies, he claimed.
“Snowflake isn’t even the biggest BPO/MSP multi-company dataset on our networks, but what’s been exfiltrated from them is well over 100TB,” Judische bragged. “Only ones that don’t pay get disclosed (unless they disclose it themselves). A lot of them don’t even do their SEC filing and just pay us to fuck off.”
The other half of UNC5537 — 24-year-old John Erin Binns — was arrested in Turkey in late May 2024, and currently resides in a Turkish prison. However, it is unclear if Binns faces any immediate threat of extradition to the United States, where he is currently wanted on criminal hacking charges tied to the 2021 breach at T-Mobile.
A person familiar with the investigation said Binns’s application for Turkish citizenship was inexplicably approved after his incarceration, leading to speculation that Binns may have bought his way out of a sticky legal situation.
Under the Turkish constitution, a Turkish citizen cannot be extradited to a foreign state. Turkey has been criticized for its “golden passport” program, which provides citizenship and sanctuary for anyone willing to pay several hundred thousand dollars.

This is an image of a passport that Binns shared in one of many unsolicited emails to KrebsOnSecurity since 2021. Binns never explained why he sent this in Feb. 2023.
Binns’s alleged hacker alter egos — “IRDev” and “IntelSecrets” — were at once feared and revered on several cybercrime-focused Telegram communities, because he was known to possess a powerful weapon: A massive botnet. From reviewing the Telegram channels Binns frequented, we can see that others in those communities — including Judische — heavily relied on Binns and his botnet for a variety of cybercriminal purposes.
The IntelSecrets nickname corresponds to an individual who has claimed responsibility for modifying the source code for the Mirai “Internet of Things” botnet to create a variant known as “Satori,” and supplying it to others who used it for criminal gain and were later caught and prosecuted.
Since 2020, Binns has filed a flood of lawsuits naming various federal law enforcement officers and agencies — including the FBI, the CIA, and the U.S. Special Operations Command (PDF), demanding that the government turn over information collected about him and seeking restitution for his alleged kidnapping at the hands of the CIA.
Binns claims he was kidnapped in Turkey and subjected to various forms of psychological and physical torture. According to Binns, the U.S. Central Intelligence Agency (CIA) falsely told their counterparts in Turkey that he was a supporter or member of the Islamic State (ISIS), a claim he says led to his detention and torture by the Turkish authorities.
However, in a 2020 lawsuit he filed against the CIA, Binns himself acknowledged having visited a previously ISIS-controlled area of Syria prior to moving to Turkey in 2017.

A segment of a lawsuit Binns filed in 2020 against the CIA, in which he alleges U.S. put him on a terror watch list after he traveled to Syria in 2017.
Sources familiar with the investigation told KrebsOnSecurity that Binns was so paranoid about possible surveillance on him by American and Turkish intelligence agencies that his erratic behavior and online communications actually brought about the very government snooping that he feared.
In several online chats in late 2023 on Discord, IRDev lamented being lured into a law enforcement sting operation after trying to buy a rocket launcher online. A person close to the investigation confirmed that at the beginning of 2023, IRDev began making earnest inquiries about how to purchase a Stinger, an American-made portable weapon that operates as an infrared surface-to-air missile.
Sources told KrebsOnSecurity Binns’ repeated efforts to purchase the projectile earned him multiple visits from the Turkish authorities, who were justifiably curious why he kept seeking to acquire such a powerful weapon.
A careful study of Judische’s postings on Telegram and Discord since 2019 shows this user is more widely known under the nickname “Waifu,” a moniker that corresponds to one of the more accomplished “SIM swappers” in the English-language cybercrime community over the years.
SIM swapping involves phishing, tricking or bribing mobile phone company employees for credentials needed to redirect a target’s mobile phone number to a device the attackers control — allowing thieves to intercept incoming text messages and phone calls.
Several SIM-swapping channels on Telegram maintain a frequently updated leaderboard of the 100 richest SIM-swappers, as well as the hacker handles associated with specific cybercrime groups (Waifu is ranked #24). That list has long included Waifu on a roster of hackers for a group that called itself “Beige.”
The term “Beige Group” came up in reporting on two stories published here in 2020. The first was in an August 2020 piece called Voice Phishers Targeting Corporate VPNs, which warned that the COVID-19 epidemic had brought a wave of targeted voice phishing attacks that tried to trick work-at-home employees into providing access to their employers’ networks. Frequent targets of the Beige group included employees at numerous top U.S. banks, ISPs, and mobile phone providers.
The second time Beige Group was mentioned by sources was in reporting on a breach at the domain registrar GoDaddy. In November 2020, intruders thought to be associated with the Beige Group tricked a GoDaddy employee into installing malicious software, and with that access they were able to redirect the web and email traffic for multiple cryptocurrency trading platforms. Other frequent targets of the Beige group included employees at numerous top U.S. banks, ISPs, and mobile phone providers.
Judische’s various Telegram identities have long claimed involvement in the 2020 GoDaddy breach, and he didn’t deny his alleged role when asked directly. Judische said he prefers voice phishing or “vishing” attacks that result in the target installing data-stealing malware, as opposed to tricking the user into entering their username, password and one-time code.
“Most of my ops involve malware [because] credential access burns too fast,” Judische explained.
The Telegram channels that the Judische/Waifu accounts frequented over the years show this user divided their time between posting in channels dedicated to financial cybercrime, and harassing and stalking others in harm communities like Leak Society and Court.
Both of these Telegram communities are known for victimizing children through coordinated online campaigns of extortion, doxing, swatting and harassment. People affiliated with harm groups like Court and Leak Society will often recruit new members by lurking on gaming platforms, social media sites and mobile applications that are popular with young people, including Discord, Minecraft, Roblox, Steam, Telegram, and Twitch.
“This type of offence usually starts with a direct message through gaming platforms and can move to more private chatrooms on other virtual platforms, typically one with video enabled features, where the conversation quickly becomes sexualized or violent,” warns a recent alert from the Royal Canadian Mounted Police (RCMP) about the rise of sextortion groups on social media channels.
“One of the tactics being used by these actors is sextortion, however, they are not using it to extract money or for sexual gratification,” the RCMP continued. “Instead they use it to further manipulate and control victims to produce more harmful and violent content as part of their ideological objectives and radicalization pathway.”
Some of the largest such known groups include those that go by the names 764, CVLT, Kaskar, 7997, 8884, 2992, 6996, 555, Slit Town, 545, 404, NMK, 303, and H3ll.
On the various cybercrime-oriented channels Judische frequented, he often lied about his or others’ involvement in various breaches. But Judische also at times shared nuggets of truth about his past, particularly when discussing the early history and membership of specific Telegram- and Discord-based cybercrime and harm groups.
Judische claimed in multiple chats, including on Leak Society and Court, that they were an early member of the Atomwaffen Division (AWD), a white supremacy group whose members are suspected of having committed multiple murders in the U.S. since 2017.
In 2019, KrebsOnSecurity exposed how a loose-knit group of neo-Nazis, some of whom were affiliated with AWD, had doxed and/or swatted nearly three dozen journalists at a range of media publications. Swatting involves communicating a false police report of a bomb threat or hostage situation and tricking authorities into sending a heavily armed police response to a targeted address.
Judsiche also told a fellow denizen of Court that years ago he was active in an older harm community called “RapeLash,” a truly vile Discord server known for attracting Atomwaffen members. A 2018 retrospective on RapeLash posted to the now defunct neo-Nazi forum Fascist Forge explains that RapeLash was awash in gory, violent images and child pornography.
A Fascist Forge member named “Huddy” recalled that RapeLash was the third incarnation of an extremist community also known as “FashWave,” short for Fascist Wave.
“I have no real knowledge of what happened with the intermediary phase known as ‘FashWave 2.0,’ but FashWave 3.0 houses multiple known Satanists and other degenerates connected with AWD, one of which got arrested on possession of child pornography charges, last I heard,” Huddy shared.
In June 2024, a Mandiant employee told Bloomberg that UNC5537 members have made death threats against cybersecurity experts investigating the hackers, and that in one case the group used artificial intelligence to create fake nude photos of a researcher to harass them.
Allison Nixon is chief research officer with the New York-based cybersecurity firm Unit 221B. Nixon is among several researchers who have faced harassment and specific threats of physical violence from Judische.
Nixon said Judische is likely to argue in court that his self-described psychological disorder(s) should somehow excuse his long career in cybercrime and in harming others.
“They ran a misinformation campaign in a sloppy attempt to cover up the hacking campaign,” Nixon said of Judische. “Coverups are an acknowledgment of guilt, which will undermine a mental illness defense in court. We expect that violent hackers from the [cybercrime community] will experience increasingly harsh sentences as the crackdown continues.”
5:34 p.m. ET: Updated story to include a clarification from Mandiant. Corrected Moucka’s age.
Nov. 21, 2024: Included link to a criminal indictment against Moucka and Binns.