Phishing attacks increased nearly 40 percent in the year ending August 2024, with much of that growth concentrated at a small number of new generic top-level domains (gTLDs) — such as .shop, .top, .xyz — that attract scammers with rock-bottom prices and no meaningful registration requirements, new research finds. Meanwhile, the nonprofit entity that oversees the domain name industry is moving forward with plans to introduce a slew of new gTLDs.

Image: Shutterstock.
A study on phishing data released by Interisle Consulting finds that new gTLDs introduced in the last few years command just 11 percent of the market for new domains, but accounted for roughly 37 percent of cybercrime domains reported between September 2023 and August 2024.
Interisle was sponsored by several anti-spam organizations, including the Anti-Phishing Working Group (APWG), the Coalition Against Unsolicited Commercial Email (CAUCE), and the Messaging, Malware, and Mobile Anti-Abuse Working Group (M3AAWG).
The study finds that while .com and .net domains made up approximately half of all domains registered in the past year (more than all of the other TLDs combined) they accounted for just over 40 percent of all cybercrime domains. Interisle says an almost equal share — 37 percent — of cybercrime domains were registered through new gTLDs.
Spammers and scammers gravitate toward domains in the new gTLDs because these registrars tend to offer cheap or free registration with little to no account or identity verification requirements. For example, among the gTLDs with the highest cybercrime domain scores in this year’s study, nine offered registration fees for less than $1, and nearly two dozen offered fees of less than $2.00. By comparison, the cheapest price identified for a .com domain was $5.91.
Currently, there are around 2,500 registrars authorized to sell domains by the Internet Corporation for Assigned Names and Numbers (ICANN), the California nonprofit that oversees the domain industry.
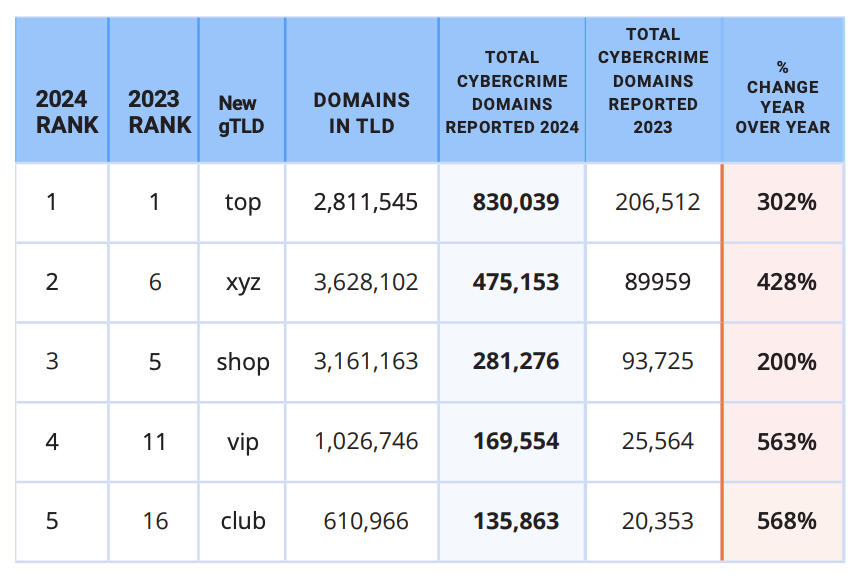
The top 5 new gTLDs, ranked by cybercrime domains reported. Image: Interisle Cybercrime Supply Chain 2014.
Incredibly, despite years of these reports showing phishers heavily abusing new gTLDs, ICANN is shuffling forward on a plan to introduce even more of them. ICANN’s proposed next round envisions accepting applications for new gTLDs in 2026.
John Levine is author of the book “The Internet for Dummies” and president of CAUCE. Levine said adding more TLDs without a much stricter registration policy will likely further expand an already plentiful greenfield for cybercriminals.
“The problem is that ICANN can’t make up their mind whether they are the neutral nonprofit regulator or just the domain speculator trade association,” Levine told KrebsOnSecurity. “But they act a lot more like the latter.”
Levine said the vast majority of new gTLDs have a few thousand domains — a far cry from the number of registrations they would need just to cover the up-front costs of operating a new gTLD (~$180,000-$300,000). New gTLD registrars can quickly attract customers by selling domains cheaply to customers who buy domains in bulk, but that tends to be a losing strategy.
“Selling to criminals and spammers turns out to be lousy business,” Levine said. “You can charge whatever you want on the first year, but you have to charge list price on domain renewals. And criminals and spammers never renew. So if it sounds like the economics makes no sense it’s because the economics makes no sense.”
In virtually all previous spam reports, Interisle found the top brands referenced in phishing attacks were the largest technology companies, including Apple, Facebook, Google and PayPal. But this past year, Interisle found the U.S. Postal Service was by far the most-phished entity, with more than four times the number of phishing domains as the second most-frequent target (Apple).
At least some of that increase is likely from a prolific cybercriminal using the nickname Chenlun, who has been selling phishing kits targeting domestic postal services in the United States and at least a dozen other countries.
Interisle says an increasing number of phishers are eschewing domain registrations altogether, and instead taking advantage of subdomain providers like blogspot.com, pages.dev, and weebly.com. The report notes that cyberattacks hosted at subdomain provider services can be tough to mitigate, because only the subdomain provider can disable malicious accounts or take down malicious web pages.
“Any action upstream, such as blocking the second-level domain, would have an impact across the provider’s whole customer base,” the report observes.
Interisle tracked more than 1.18 million instances of subdomains used for phishing in the past year (a 114 percent increase), and found more than half of those were subdomains at blogspot.com and other services operated by Google.
“Many of these services allow the creation of large numbers of accounts at one time, which is highly exploited by criminals,” the report concludes. “Subdomain providers should limit the number of subdomains (user accounts) a customer can create at one time and suspend automated, high-volume automated account sign-ups – especially using free services.”
Dec. 4, 10:21 a.m. ET: Corrected link to report.
The Russia-based cybercrime group dubbed “Fin7,” known for phishing and malware attacks that have cost victim organizations an estimated $3 billion in losses since 2013, was declared dead last year by U.S. authorities. But experts say Fin7 has roared back to life in 2024 — setting up thousands of websites mimicking a range of media and technology companies — with the help of Stark Industries Solutions, a sprawling hosting provider that is a persistent source of cyberattacks against enemies of Russia.
In May 2023, the U.S. attorney for Washington state declared “Fin7 is an entity no more,” after prosecutors secured convictions and prison sentences against three men found to be high-level Fin7 hackers or managers. This was a bold declaration against a group that the U.S. Department of Justice described as a criminal enterprise with more than 70 people organized into distinct business units and teams.
The first signs of Fin7’s revival came in April 2024, when Blackberry wrote about an intrusion at a large automotive firm that began with malware served by a typosquatting attack targeting people searching for a popular free network scanning tool.
Now, researchers at security firm Silent Push say they have devised a way to map out Fin7’s rapidly regrowing cybercrime infrastructure, which includes more than 4,000 hosts that employ a range of exploits, from typosquatting and booby-trapped ads to malicious browser extensions and spearphishing domains.
Silent Push said it found Fin7 domains targeting or spoofing brands including American Express, Affinity Energy, Airtable, Alliant, Android Developer, Asana, Bitwarden, Bloomberg, Cisco (Webex), CNN, Costco, Dropbox, Grammarly, Google, Goto.com, Harvard, Lexis Nexis, Meta, Microsoft 365, Midjourney, Netflix, Paycor, Quickbooks, Quicken, Reuters, Regions Bank Onepass, RuPay, SAP (Ariba), Trezor, Twitter/X, Wall Street Journal, Westlaw, and Zoom, among others.
Zach Edwards, senior threat analyst at Silent Push, said many of the Fin7 domains are innocuous-looking websites for generic businesses that sometimes include text from default website templates (the content on these sites often has nothing to do with the entity’s stated business or mission).
Edwards said Fin7 does this to “age” the domains and to give them a positive or at least benign reputation before they’re eventually converted for use in hosting brand-specific phishing pages.
“It took them six to nine months to ramp up, but ever since January of this year they have been humming, building a giant phishing infrastructure and aging domains,” Edwards said of the cybercrime group.
In typosquatting attacks, Fin7 registers domains that are similar to those for popular free software tools. Those look-alike domains are then advertised on Google so that sponsored links to them show up prominently in search results, which is usually above the legitimate source of the software in question.
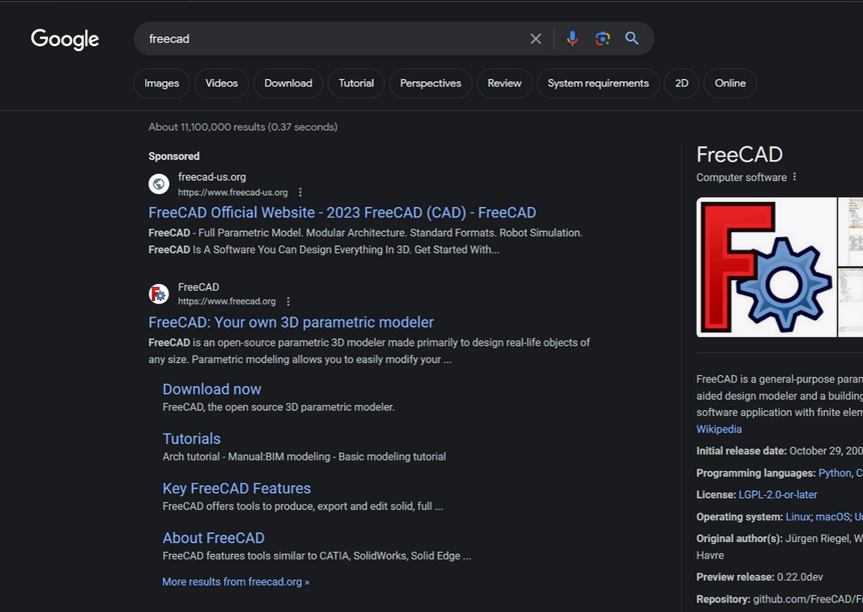
A malicious site spoofing FreeCAD showed up prominently as a sponsored result in Google search results earlier this year.
According to Silent Push, the software currently being targeted by Fin7 includes 7-zip, PuTTY, ProtectedPDFViewer, AIMP, Notepad++, Advanced IP Scanner, AnyDesk, pgAdmin, AutoDesk, Bitwarden, Rest Proxy, Python, Sublime Text, and Node.js.
In May 2024, security firm eSentire warned that Fin7 was spotted using sponsored Google ads to serve pop-ups prompting people to download phony browser extensions that install malware. Malwarebytes blogged about a similar campaign in April, but did not attribute the activity to any particular group.
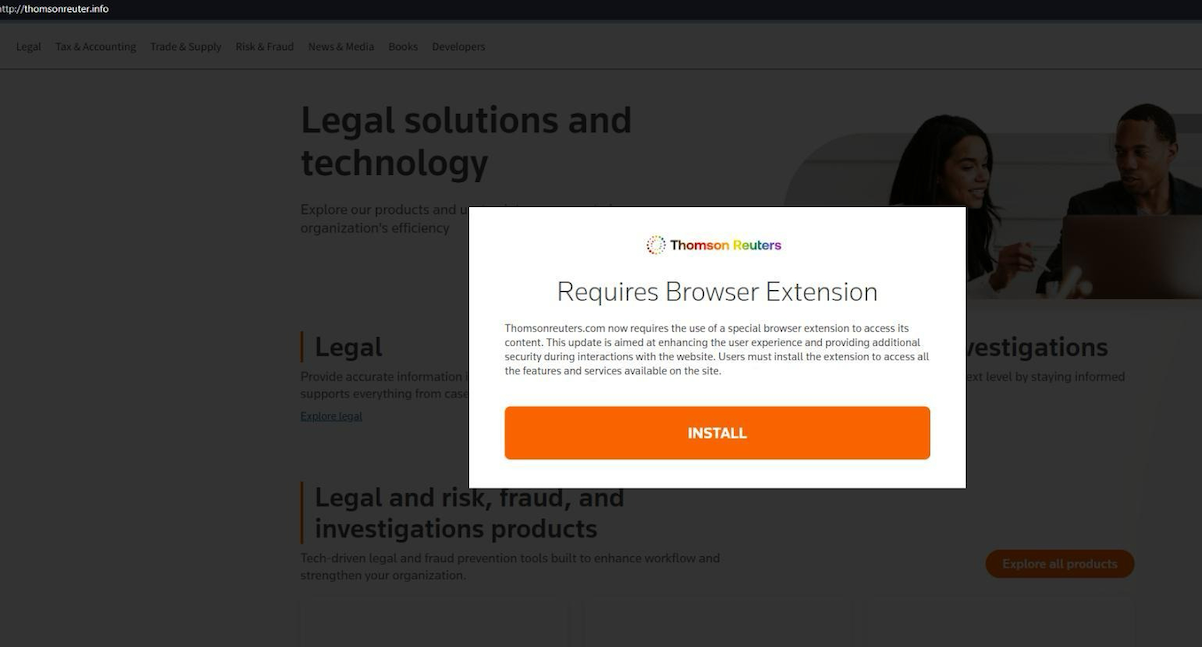
A pop-up at a Thomson Reuters typosquatting domain telling visitors they need to install a browser extension to view the news content.
Edwards said Silent Push discovered the new Fin7 domains after a hearing from an organization that was targeted by Fin7 in years past and suspected the group was once again active. Searching for hosts that matched Fin7’s known profile revealed just one active site. But Edwards said that one site pointed to many other Fin7 properties at Stark Industries Solutions, a large hosting provider that materialized just two weeks before Russia invaded Ukraine.
As KrebsOnSecurity wrote in May, Stark Industries Solutions is being used as a staging ground for wave after wave of cyberattacks against Ukraine that have been tied to Russian military and intelligence agencies.
“FIN7 rents a large amount of dedicated IP on Stark Industries,” Edwards said. “Our analysts have discovered numerous Stark Industries IPs that are solely dedicated to hosting FIN7 infrastructure.”
Fin7 once famously operated behind fake cybersecurity companies — with names like Combi Security and Bastion Secure — which they used for hiring security experts to aid in ransomware attacks. One of the new Fin7 domains identified by Silent Push is cybercloudsec[.]com, which promises to “grow your business with our IT, cyber security and cloud solutions.”
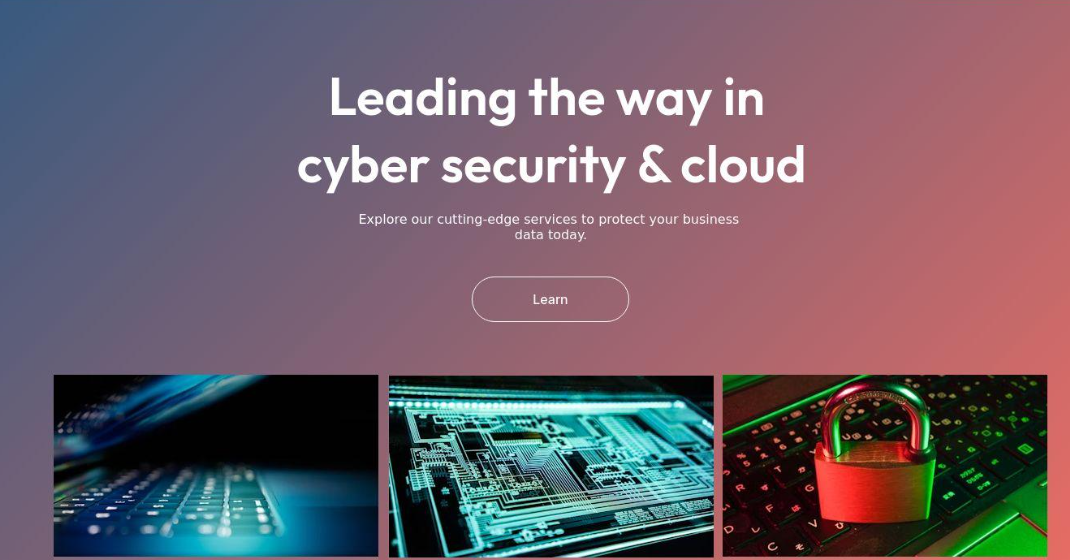
The fake Fin7 security firm Cybercloudsec.
Like other phishing groups, Fin7 seizes on current events, and at the moment it is targeting tourists visiting France for the Summer Olympics later this month. Among the new Fin7 domains Silent Push found are several sites phishing people seeking tickets at the Louvre.
“We believe this research makes it clear that Fin7 is back and scaling up quickly,” Edwards said. “It’s our hope that the law enforcement community takes notice of this and puts Fin7 back on their radar for additional enforcement actions, and that quite a few of our competitors will be able to take this pool and expand into all or a good chunk of their infrastructure.”
Further reading:
Stark Industries Solutions: An Iron Hammer in the Cloud.
A 2022 deep dive on Fin7 from the Swiss threat intelligence firm Prodaft (PDF).
Malicious hackers are targeting people in the cryptocurrency space in attacks that start with a link added to the target’s calendar at Calendly, a popular application for scheduling appointments and meetings. The attackers impersonate established cryptocurrency investors and ask to schedule a video conference call. But clicking the meeting link provided by the scammers prompts the user to run a script that quietly installs malware on macOS systems.
KrebsOnSecurity recently heard from a reader who works at a startup that is seeking investment for building a new blockchain platform for the Web. The reader spoke on condition that their name not be used in this story, so for the sake of simplicity we’ll call him Doug.
Being in the cryptocurrency scene, Doug is also active on the instant messenger platform Telegram. Earlier this month, Doug was approached by someone on Telegram whose profile name, image and description said they were Ian Lee, from Signum Capital, a well-established investment firm based in Singapore. The profile also linked to Mr. Lee’s Twitter/X account, which features the same profile image.
The investor expressed interest in financially supporting Doug’s startup, and asked if Doug could find time for a video call to discuss investment prospects. Sure, Doug said, here’s my Calendly profile, book a time and we’ll do it then.
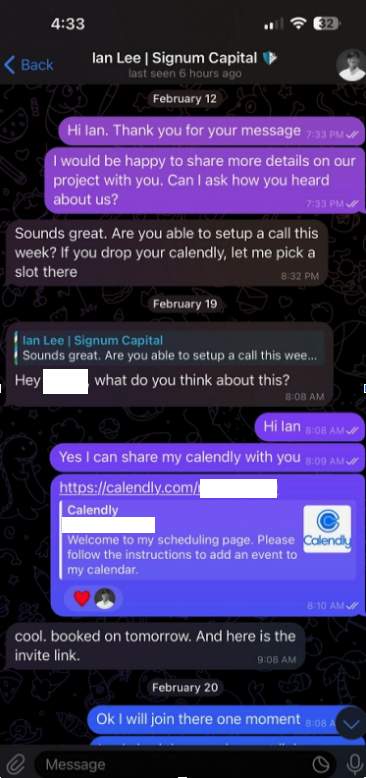
When the day and time of the scheduled meeting with Mr. Lee arrived, Doug clicked the meeting link in his calendar but nothing happened. Doug then messaged the Mr. Lee account on Telegram, who said there was some kind of technology issue with the video platform, and that their IT people suggested using a different meeting link.
Doug clicked the new link, but instead of opening up a videoconference app, a message appeared on his Mac saying the video service was experiencing technical difficulties.
“Some of our users are facing issues with our service,” the message read. “We are actively working on fixing these problems. Please refer to this script as a temporary solution.”
Doug said he ran the script, but nothing appeared to happen after that, and the videoconference application still wouldn’t start. Mr. Lee apologized for the inconvenience and said they would have to reschedule their meeting, but he never responded to any of Doug’s follow-up messages.
It didn’t dawn on Doug until days later that the missed meeting with Mr. Lee might have been a malware attack. Going back to his Telegram client to revisit the conversation, Doug discovered his potential investor had deleted the meeting link and other bits of conversation from their shared chat history.
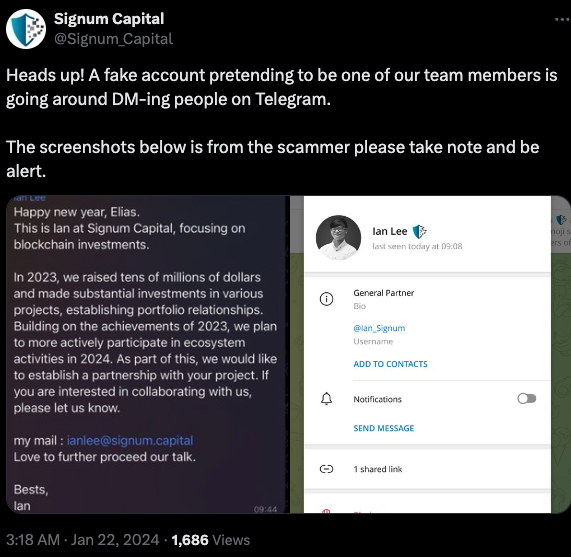
In a post to its Twitter/X account last month, Signum Capital warned that a fake profile pretending to be their employee Mr. Lee was trying to scam people on Telegram.
The file that Doug ran is a simple Apple Script (file extension “.scpt”) that downloads and executes a malicious trojan made to run on macOS systems. Unfortunately for us, Doug freaked out after deciding he’d been tricked — backing up his important documents, changing his passwords, and then reinstalling macOS on his computer. While this a perfectly sane response, it means we don’t have the actual malware that was pushed to his Mac by the script.
But Doug does still have a copy of the malicious script that was downloaded from clicking the meeting link (the online host serving that link is now offline). A search in Google for a string of text from that script turns up a December 2023 blog post from cryptocurrency security firm SlowMist about phishing attacks on Telegram from North Korean state-sponsored hackers.
“When the project team clicks the link, they encounter a region access restriction,” SlowMist wrote. “At this point, the North Korean hackers coax the team into downloading and running a ‘location-modifying’ malicious script. Once the project team complies, their computer comes under the control of the hackers, leading to the theft of funds.”
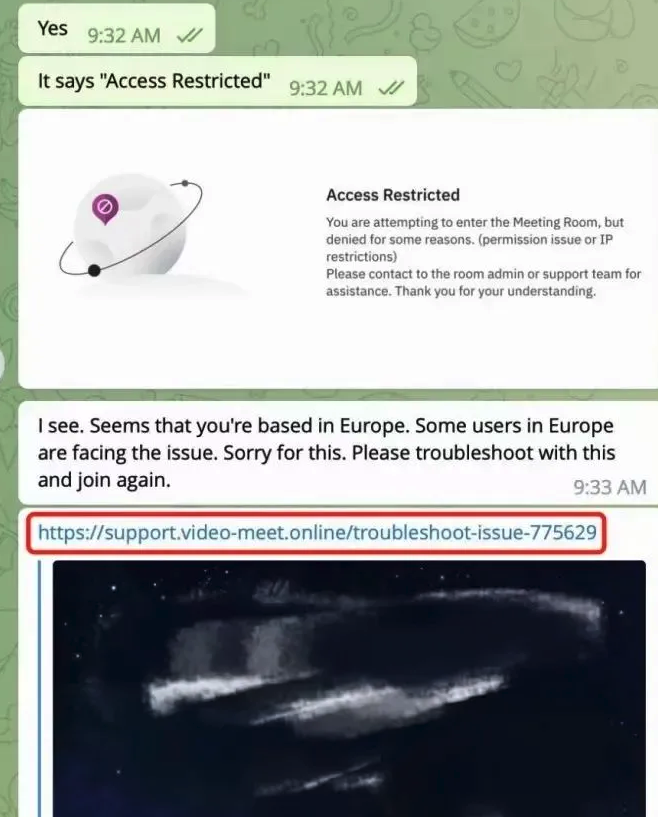
Image: SlowMist.
SlowMist says the North Korean phishing scams used the “Add Custom Link” feature of the Calendly meeting scheduling system on event pages to insert malicious links and initiate phishing attacks.
“Since Calendly integrates well with the daily work routines of most project teams, these malicious links do not easily raise suspicion,” the blog post explains. “Consequently, the project teams may inadvertently click on these malicious links, download, and execute malicious code.”
SlowMist said the malware downloaded by the malicious link in their case comes from a North Korean hacking group dubbed “BlueNoroff, which Kaspersky Labs says is a subgroup of the Lazarus hacking group.
“A financially motivated threat actor closely connected with Lazarus that targets banks, casinos, fin-tech companies, POST software and cryptocurrency businesses, and ATMs,” Kaspersky wrote of BlueNoroff in Dec. 2023.
The North Korean regime is known to use stolen cryptocurrencies to fund its military and other state projects. A recent report from Recorded Future finds the Lazarus Group has stolen approximately $3 billion in cryptocurrency over the past six years.
While there is still far more malware out there today targeting Microsoft Windows PCs, the prevalence of information-stealing trojans aimed at macOS users is growing at a steady clip. MacOS computers include X-Protect, Apple’s built-in antivirus technology. But experts say attackers are constantly changing the appearance and behavior of their malware to evade X-Protect.
“Recent updates to macOS’s XProtect signature database indicate that Apple are aware of the problem, but early 2024 has already seen a number of stealer families evade known signatures,” security firm SentinelOne wrote in January.
According to Chris Ueland from the threat hunting platform Hunt.io, the Internet address of the fake meeting website Doug was tricked into visiting (104.168.163,149) hosts or very recently hosted about 75 different domain names, many of which invoke words associated with videoconferencing or cryptocurrency. Those domains indicate this North Korean hacking group is hiding behind a number of phony crypto firms, like the six-month-old website for Cryptowave Capital (cryptowave[.]capital).
In a statement shared with KrebsOnSecurity, Calendly said it was aware of these types of social engineering attacks by cryptocurrency hackers.
“To help prevent these kinds of attacks, our security team and partners have implemented a service to automatically detect fraud and impersonations that could lead to social engineering,” the company said. “We are also actively scanning content for all our customers to catch these types of malicious links and to prevent hackers earlier on. Additionally, we intend to add an interstitial page warning users before they’re redirected away from Calendly to other websites. Along with the steps we’ve taken, we recommend users stay vigilant by keeping their software secure with running the latest updates and verifying suspicious links through tools like VirusTotal to alert them of possible malware. We are continuously strengthening the cybersecurity of our platform to protect our customers.”
The increasing frequency of new Mac malware is a good reminder that Mac users should not depend on security software and tools to flag malicious files, which are frequently bundled with or disguised as legitimate software.
As KrebsOnSecurity has advised Windows users for years, a good rule of safety to live by is this: If you didn’t go looking for it, don’t install it. Following this mantra heads off a great deal of malware attacks, regardless of the platform used. When you do decide to install a piece of software, make sure you are downloading it from the original source, and then keep it updated with any new security fixes.
On that last front, I’ve found it’s a good idea not to wait until the last minute to configure my system before joining a scheduled videoconference call. Even if the call uses software that is already on my computer, it is often the case that software updates are required before the program can be used, and I’m one of those weird people who likes to review any changes to the software maker’s privacy policies or user agreements before choosing to install updates.
Most of all, verify new contacts from strangers before accepting anything from them. In this case, had Doug simply messaged Mr. Lee’s real account on Twitter/X or contacted Signum Capital directly, he would discovered that the real Mr. Lee never asked for a meeting.
If you’re approached in a similar scheme, the response from the would-be victim documented in the SlowMist blog post is probably the best.
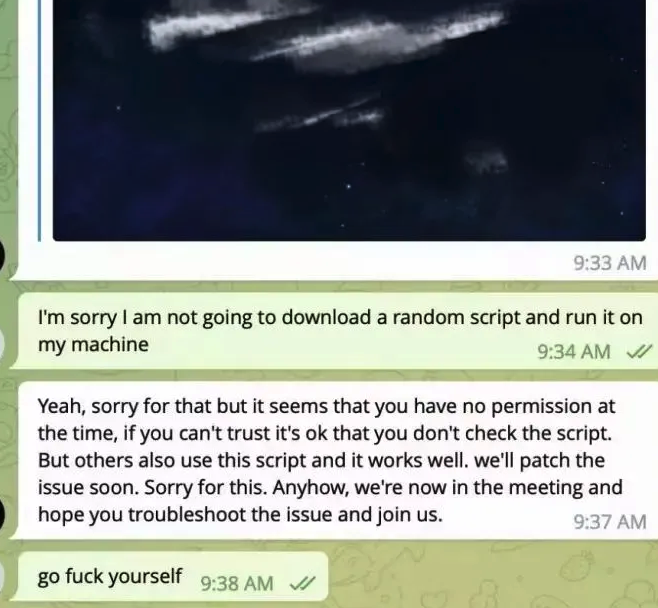
Image: SlowMist.
Update: Added comment from Calendly.