A critical resource that cybersecurity professionals worldwide rely on to identify, mitigate and fix security vulnerabilities in software and hardware is in danger of breaking down. The federally funded, non-profit research and development organization MITRE warned today that its contract to maintain the Common Vulnerabilities and Exposures (CVE) program — which is traditionally funded each year by the Department of Homeland Security — expires on April 16.

A letter from MITRE vice president Yosry Barsoum, warning that the funding for the CVE program will expire on April 16, 2025.
Tens of thousands of security flaws in software are found and reported every year, and these vulnerabilities are eventually assigned their own unique CVE tracking number (e.g. CVE-2024-43573, which is a Microsoft Windows bug that Redmond patched last year).
There are hundreds of organizations — known as CVE Numbering Authorities (CNAs) — that are authorized by MITRE to bestow these CVE numbers on newly reported flaws. Many of these CNAs are country and government-specific, or tied to individual software vendors or vulnerability disclosure platforms (a.k.a. bug bounty programs).
Put simply, MITRE is a critical, widely-used resource for centralizing and standardizing information on software vulnerabilities. That means the pipeline of information it supplies is plugged into an array of cybersecurity tools and services that help organizations identify and patch security holes — ideally before malware or malcontents can wriggle through them.
“What the CVE lists really provide is a standardized way to describe the severity of that defect, and a centralized repository listing which versions of which products are defective and need to be updated,” said Matt Tait, chief operating officer of Corellium, a cybersecurity firm that sells phone-virtualization software for finding security flaws.
In a letter sent today to the CVE board, MITRE Vice President Yosry Barsoum warned that on April 16, 2025, “the current contracting pathway for MITRE to develop, operate and modernize CVE and several other related programs will expire.”
“If a break in service were to occur, we anticipate multiple impacts to CVE, including deterioration of national vulnerability databases and advisories, tool vendors, incident response operations, and all manner of critical infrastructure,” Barsoum wrote.
MITRE told KrebsOnSecurity the CVE website listing vulnerabilities will remain up after the funding expires, but that new CVEs won’t be added after April 16.
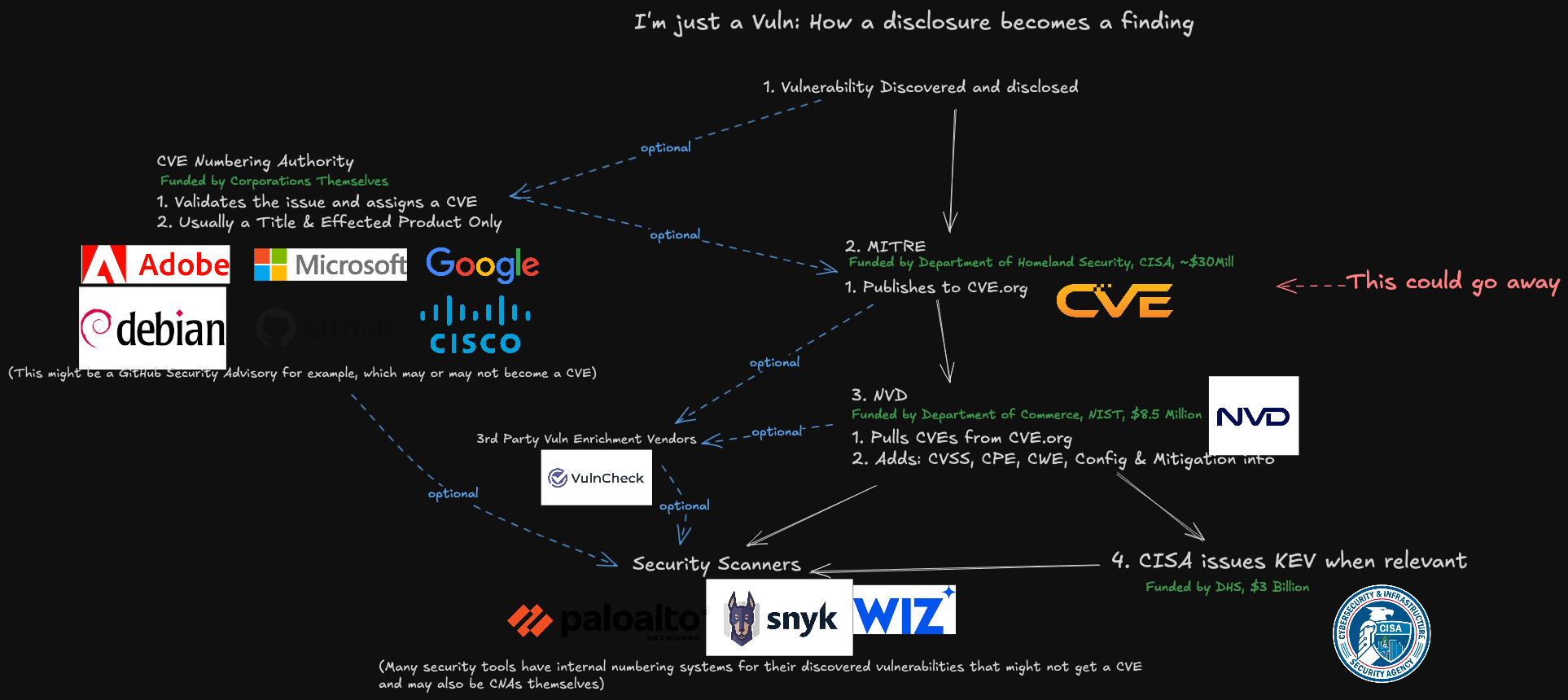
A representation of how a vulnerability becomes a CVE, and how that information is consumed. Image: James Berthoty, Latio Tech, via LinkedIn.
DHS officials did not immediately respond to a request for comment. The program is funded through DHS’s Cybersecurity & Infrastructure Security Agency (CISA), which is currently facing deep budget and staffing cuts by the Trump administration. The CVE contract available at USAspending.gov says the project was awarded approximately $40 million last year.
Former CISA Director Jen Easterly said the CVE program is a bit like the Dewey Decimal System, but for cybersecurity.
“It’s the global catalog that helps everyone—security teams, software vendors, researchers, governments—organize and talk about vulnerabilities using the same reference system,” Easterly said in a post on LinkedIn. “Without it, everyone is using a different catalog or no catalog at all, no one knows if they’re talking about the same problem, defenders waste precious time figuring out what’s wrong, and worst of all, threat actors take advantage of the confusion.”
John Hammond, principal security researcher at the managed security firm Huntress, told Reuters he swore out loud when he heard the news that CVE’s funding was in jeopardy, and that losing the CVE program would be like losing “the language and lingo we used to address problems in cybersecurity.”
“I really can’t help but think this is just going to hurt,” said Hammond, who posted a Youtube video to vent about the situation and alert others.
Several people close to the matter told KrebsOnSecurity this is not the first time the CVE program’s budget has been left in funding limbo until the last minute. Barsoum’s letter, which was apparently leaked, sounded a hopeful note, saying the government is making “considerable efforts to continue MITRE’s role in support of the program.”
Tait said that without the CVE program, risk managers inside companies would need to continuously monitor many other places for information about new vulnerabilities that may jeopardize the security of their IT networks. Meaning, it may become more common that software updates get mis-prioritized, with companies having hackable software deployed for longer than they otherwise would, he said.
“Hopefully they will resolve this, but otherwise the list will rapidly fall out of date and stop being useful,” he said.
Update, April 16, 11:00 a.m. ET: The CVE board today announced the creation of non-profit entity called The CVE Foundation that will continue the program’s work under a new, unspecified funding mechanism and organizational structure.
“Since its inception, the CVE Program has operated as a U.S. government-funded initiative, with oversight and management provided under contract,” the press release reads. “While this structure has supported the program’s growth, it has also raised longstanding concerns among members of the CVE Board about the sustainability and neutrality of a globally relied-upon resource being tied to a single government sponsor.”
The organization’s website, thecvefoundation.org, is less than a day old and currently hosts no content other than the press release heralding its creation. The announcement said the foundation would release more information about its structure and transition planning in the coming days.
Update, April 16, 4:26 p.m. ET: MITRE issued a statement today saying it “identified incremental funding to keep the programs operational. We appreciate the overwhelming support for these programs that have been expressed by the global cyber community, industry and government over the last 24 hours. The government continues to make considerable efforts to support MITRE’s role in the program and MITRE remains committed to CVE and CWE as global resources.”

There’s little rest for your hard-working smartphone. If you’re like many professionals today, you use it for work, play, and a mix of personal business in between. Now, what if something went wrong with that phone, like loss or theft? Worse yet, what if your smartphone got hacked?
Globally, plenty of people pull double duty with their smartphones. One survey found that 87% of companies have policies that integrate personal devices in the workplace. Therein lies the higher potential for security risks such as data breaches, malware infection, and difficulties in maintaining data privacy and compliance. You see, a smartphone loaded with both business and personal data makes it a desirable, high-value target. It only takes one dedicated hacker—and there are plenty—to infiltrate an unprotected smartphone and access the treasure trove of both your personal and company information in a single effort.
Let’s try to keep that from happening to you. This guide will walk you through exactly how to keep your digital life secure.
Smartphone hacking is when someone gains unauthorized access to your phone and the vast amount of personal data it contains. As you can imagine, this type of digital break-in can have serious real-world consequences, including financial loss from compromised banking apps, identity theft using your private information, and a complete invasion of your privacy through access to your emails, photos, and messages. This isn’t a distant threat; mobile malware is consistently on the rise, with cybercriminals developing more sophisticated methods to target unsuspecting users. The good news is that you have the power to stop them. Understanding how to protect your phone from hackers is the first step.
If you notice one or more of these signs, don’t panic. Investigate further and follow the recovery steps below. Sometimes, these issues can be caused by a legitimate but buggy app or an aging battery.
Once you’ve resolved an attack, the next step is to prevent phone hacking from happening again. Think of it as strengthening your digital front door. As both a parent and professional, I have put together a few things you can do to protect your smartphone from future hacks, so that you can keep your personal and work life safe:
Locking your phone with facial ID, a fingerprint, a pattern, or a PIN is your most basic form of protection, particularly in the event of loss or theft. (Your options will vary depending on the device, operating system, and manufacturer.) Take it a step further for even more protection. Secure the accounts on your phone with strong passwords and use two-factor authentication on the apps that offer it.
Don’t hop onto public Wi-Fi networks without protection. A virtual private network (VPN) masks your connection from hackers, allowing you to browse privately on unsecure public networks at airports, cafes, hotels, and the like. With a VPN connection, your sensitive data, documents, and activities are protected from snooping. It’s definitely a great feeling given the amount of personal and professional business we manage with our smartphones.
Both Google Play and Apple’s App Store have measures in place to help prevent potentially dangerous apps from making it into their stores. Malicious apps are often found outside of the app stores, which can run in the background and compromise your personal data such as passwords, credit card numbers, and more—practically everything that you keep on your phone. Further, when you are in the app stores, look closely at the descriptions and reviews for apps before you download them as malicious apps and counterfeits can still find their way into stores.
Backing up your phone is always a good idea for two reasons:
Both iPhones and Android phones have straightforward ways of backing up your phone regularly.
Worst case scenario—your phone is gone. Really gone. Either it’s hopelessly lost or got stolen. What now? Lock it remotely or even wipe its data entirely. While it seems like a drastic move, your data is secure in the cloud ready to be restored IF you maintain regular backups as mentioned above. This means hackers won’t be able to access your or your company’s sensitive information, keeping you and your professional business safe. Apple and Google provide their users with a step-by-step guide for remotely wiping devices.
Needless to say, smartphone updates should always start with the operating system (OS). In addition, you also need to conduct app updates as soon as they’re available, as they contain critical security patches. Take a few moments to swipe through your screen, see which ones you’re truly done with and delete them along with their data. Every extra app is another app that needs updating or that may come with a security issue. Along with deleting the app, also delete your account associated with it. As for the ones you keep, update them regularly and turn on auto-updates if that’s an option.
With so much of your life on your phone, getting security software installed on it can protect you and the things you keep. Whether you’re an Android owner or iOS owner, McAfee+ conducts regular security scans to help you keep your personal, financial, and even company data secure.
While it’s convenient to have everything at your fingertips, storing too much sensitive information on your smartphone makes you vulnerable if your device is lost, stolen, or compromised. Here are some tips to limit the data on your phone and reduce your risk of identity theft, financial fraud, and privacy breaches.
At a deeper level, there are several lesser-known settings you can adjust to protect your phone from being hacked. These advanced steps add extra layers of security to your device.
Yes, malware or spyware can give a hacker access to your camera and microphone, allowing them to see and hear you without your knowledge. To prevent this, be cautious about app permissions and consider using a physical camera cover for peace of mind.
It’s possible. Some malicious websites can attempt to automatically download malware or exploit browser vulnerabilities to compromise your device. Using a secure browser and comprehensive security software that warns you of risky sites is your best defense.
For the vast majority of users, a phone that is completely powered off cannot be hacked remotely. Hacking requires the device’s operating system and network connections to be active, so turning it off effectively cuts that connection.
Simply answering a call from an unknown number is highly unlikely to hack your phone. The real danger lies in social engineering, where the scammer on the other end tries to trick you into revealing personal information, visiting a malicious website, or dialing a specific code.
Your smartphone is central to your life, and understanding how to keep your phone safe from hackers is not about being fearful, but about being prepared. By taking proactive and consistent steps, you create powerful layers of defense that make you a much harder target for cybercriminals. Combining smart habits with the advanced protection offered by security solutions like McAfee+ ensures your data, privacy, and peace of mind are always safeguarded. Stay informed about new threats, keep your security software current, and enjoy all the good your connected life has to offer, safely and securely.
The post 7 Tips to Protect Your Smartphone from Getting Hacked appeared first on McAfee Blog.
Introduction In the previous article, we understood how print functions like printf work. This article provides further definition of Format String vulnerabilities. We will begin by discussing how Format Strings can be used in an unusual way, which is a starting point to understanding Format String exploits. Next, we will understand what kind of mistakes […]
The post Format String Vulnerabilities: Use and Definitions appeared first on Infosec Resources.
Introduction In the previous articles, we discussed printing functions, format strings and format string vulnerabilities. This article provides an overview of how Format String vulnerabilities can be exploited. In this article, we will begin by solving a simple challenge to leak a secret from memory. In the next article, we will discuss another example, where […]
The post How to exploit Format String Vulnerabilities appeared first on Infosec Resources.

In July 2015, I did my first threat webinar. I had planned to do it on a monthly basis, and never imagined I would still be doing it five years later, but here I am, still creating monthly webinars. I still do. I started the webinar series to help people understand the different threats targeting our customers and I have always tried to focus on three areas:
|
|
This last point, discussing technologies versus solutions, has been one of the key items I try to follow as much as possible – after all, the goal of my webinars is to be educational, not a sales pitch.
Coming from a technical background, BS in Electrical Engineering from Michigan State University (Go Spartans!!), I enjoy learning about the new technologies being used to detect the latest threats and to ensure you know what to look for when selecting a vendor and/or a security solution. Over the years, I’ve discussed everything from APTs, coinminers, exploits, messaging threats, ransomware, underground activity and lots in between. It is pretty easy to find topics to discuss, as there is so much going on in our industry, and with the malicious actors regularly shifting their tactics, techniques and procedures, I can keep the content fairly fresh.
I really enjoy having guest speakers on my webinars to mix things up a bit for the viewers as well, as I know my limitations – there are just too many threats out there to keep up with all of them. The main reason I love doing the threat webinars is that I enjoy sharing information and teaching others about our industry and the threats affecting them. If you want to check out any of my previous five years of webinars you can watch them here.
For my fifth year anniversary I wanted to try something different and I would like to do an open Q&A session. As I’ve never done this before, it will certainly be an interesting experience for me, but hopefully for you as well. I hope I can answer a majority of your questions, but I know some of you are way too smart for me, so please bear with me.
Our registration page for this webinar allows you to submit any pre-session questions that I’ll answer throughout the webinar. You can ask me anything that is on your mind and if I cannot get to your question, I’ll do my best to answer you afterwards in an email.
I hope to continue to do these webinars for the foreseeable future and I would like to end my post by thanking each and every one of you who has participated in my webinars over the years. It has been a pleasure, and I look forward to answering your questions.
Take care, stay healthy, and keep on smiling!
Jon
The post Ask Me Anything – Celebrating The Fifth Anniversary Of My Monthly Threat Webinar appeared first on .

Risk decisions are the foundation of information security. Sadly, they are also one of the most often misunderstood parts of information security.
This is bad enough on its own but can sink any effort at education as an organization moves towards a DevOps philosophy.
To properly evaluate the risk of an event, two components are required:
Unfortunately, teams—and humans in general—are reasonably good at the first part and unreasonably bad at the second.
This is a problem.
It’s a problem that is amplified when security starts to integration with teams in a DevOps environment. Originally presented as part of AllTheTalks.online, this talk examines the ins and outs of risk decisions and how we can start to work on improving how our teams handle them.
The post Risk Decisions in an Imperfect World appeared first on .
 So much for a quiet January! By now you must have heard about the new Microsoft® vulnerability CVE-2020-0601, first disclosed by the NSA (making it the first Windows bug publicly attributed to the National Security Agency). This vulnerability is found in a cryptographic component that has a range of functions—an important one being the ability to digitally sign software, which certifies that the software has not been tampered with. Using this vulnerability, attackers can sign malicious executables to make them look legitimate, leading to potentially disastrous man-in-the-middle attacks.
So much for a quiet January! By now you must have heard about the new Microsoft® vulnerability CVE-2020-0601, first disclosed by the NSA (making it the first Windows bug publicly attributed to the National Security Agency). This vulnerability is found in a cryptographic component that has a range of functions—an important one being the ability to digitally sign software, which certifies that the software has not been tampered with. Using this vulnerability, attackers can sign malicious executables to make them look legitimate, leading to potentially disastrous man-in-the-middle attacks.
Here’s the good news. Microsoft has already released a patch to protect against any exploits stemming from this vulnerability. But here’s the catch: You have to patch!
While Trend Micro offers industry-leading virtual patching capabilities via our endpoint, cloud, and network security solutions, the best protection against vulnerabilities is to deploy a real patch from the software vendor. Let me say it again for effect – the best protection against this very serious vulnerability is to ensure the affected systems are patched with Microsoft’s latest security update.
We understand how difficult it can be to patch systems in a timely manner, so we created a valuable tool that will test your endpoints to see if whether they have been patched against this latest threat or if they are still vulnerable. Additionally, to ensure you are protected against any potential threats, we have just released additional layers of protection in the form of IPS rules for Trend Micro Deep Security and Trend Micro Vulnerability Protection
and Trend Micro Vulnerability Protection (including Trend Micro Apex One
(including Trend Micro Apex One ). This was rolled out to help organizations strengthen their overall security posture and provide some protection during lengthy patching processes.
). This was rolled out to help organizations strengthen their overall security posture and provide some protection during lengthy patching processes.
You can download our Trend Micro Vulnerability Assessment Tool right now to see if you are protected against the latest Microsoft vulnerability. And while you’re at it, check out our latest Knowledge Based Article for additional information on this new vulnerability along with Trend Micro security capabilities that help protect customers like you 24/7. Even during those quiet days in January.
The post Don’t Let the Vulnera-Bullies Win. Use our free tool to see if you are patched against Vulnerability CVE-2020-0601 appeared first on .