Microsoft this week pushed security updates to fix more than 60 vulnerabilities in its Windows operating systems and supported software, including at least one zero-day bug that is already being exploited. Microsoft also fixed a glitch that prevented some Windows 10 users from taking advantage of an extra year of security updates, which is nice because the zero-day flaw and other critical weaknesses affect all versions of Windows, including Windows 10.

Affected products this month include the Windows OS, Office, SharePoint, SQL Server, Visual Studio, GitHub Copilot, and Azure Monitor Agent. The zero-day threat concerns a memory corruption bug deep in the Windows innards called CVE-2025-62215. Despite the flaw’s zero-day status, Microsoft has assigned it an “important” rating rather than critical, because exploiting it requires an attacker to already have access to the target’s device.
“These types of vulnerabilities are often exploited as part of a more complex attack chain,” said Johannes Ullrich, dean of research for the SANS Technology Institute. “However, exploiting this specific vulnerability is likely to be relatively straightforward, given the existence of prior similar vulnerabilities.”
Ben McCarthy, lead cybersecurity engineer at Immersive, called attention to CVE-2025-60274, a critical weakness in a core Windows graphic component (GDI+) that is used by a massive number of applications, including Microsoft Office, web servers processing images, and countless third-party applications.
“The patch for this should be an organization’s highest priority,” McCarthy said. “While Microsoft assesses this as ‘Exploitation Less Likely,’ a 9.8-rated flaw in a ubiquitous library like GDI+ is a critical risk.”
Microsoft patched a critical bug in Office — CVE-2025-62199 — that can lead to remote code execution on a Windows system. Alex Vovk, CEO and co-founder of Action1, said this Office flaw is a high priority because it is low complexity, needs no privileges, and can be exploited just by viewing a booby-trapped message in the Preview Pane.
Many of the more concerning bugs addressed by Microsoft this month affect Windows 10, an operating system that Microsoft officially ceased supporting with patches last month. As that deadline rolled around, however, Microsoft began offering Windows 10 users an extra year of free updates, so long as they register their PC to an active Microsoft account.
Judging from the comments on last month’s Patch Tuesday post, that registration worked for a lot of Windows 10 users, but some readers reported the option for an extra year of updates was never offered. Nick Carroll, cyber incident response manager at Nightwing, notes that Microsoft has recently released an out-of-band update to address issues when trying to enroll in the Windows 10 Consumer Extended Security Update program.
“If you plan to participate in the program, make sure you update and install KB5071959 to address the enrollment issues,” Carroll said. “After that is installed, users should be able to install other updates such as today’s KB5068781 which is the latest update to Windows 10.”
Chris Goettl at Ivanti notes that in addition to Microsoft updates today, third-party updates from Adobe and Mozilla have already been released. Also, an update for Google Chrome is expected soon, which means Edge will also be in need of its own update.
The SANS Internet Storm Center has a clickable breakdown of each individual fix from Microsoft, indexed by severity and CVSS score. Enterprise Windows admins involved in testing patches before rolling them out should keep an eye on askwoody.com, which often has the skinny on any updates gone awry.
As always, please don’t neglect to back up your data (if not your entire system) at regular intervals, and feel free to sound off in the comments if you experience problems installing any of these fixes.
[Author’s note: This post was intended to appear on the homepage on Tuesday, Nov. 11. I’m still not sure how it happened, but somehow this story failed to publish that day. My apologies for the oversight.]
Microsoft today released updates to fix more than 100 security flaws in its Windows operating systems and other software. At least 13 of the bugs received Microsoft’s most-dire “critical” rating, meaning they could be abused by malware or malcontents to gain remote access to a Windows system with little or no help from users.

August’s patch batch from Redmond includes an update for CVE-2025-53786, a vulnerability that allows an attacker to pivot from a compromised Microsoft Exchange Server directly into an organization’s cloud environment, potentially gaining control over Exchange Online and other connected Microsoft Office 365 services. Microsoft first warned about this bug on Aug. 6, saying it affects Exchange Server 2016 and Exchange Server 2019, as well as its flagship Exchange Server Subscription Edition.
Ben McCarthy, lead cyber security engineer at Immersive, said a rough search reveals approximately 29,000 Exchange servers publicly facing on the internet that are vulnerable to this issue, with many of them likely to have even older vulnerabilities.
McCarthy said the fix for CVE-2025-53786 requires more than just installing a patch, such as following Microsoft’s manual instructions for creating a dedicated service to oversee and lock down the hybrid connection.
“In effect, this vulnerability turns a significant on-premise Exchange breach into a full-blown, difficult-to-detect cloud compromise with effectively living off the land techniques which are always harder to detect for defensive teams,” McCarthy said.
CVE-2025-53779 is a weakness in the Windows Kerberos authentication system that allows an unauthenticated attacker to gain domain administrator privileges. Microsoft credits the discovery of the flaw to Akamai researcher Yuval Gordon, who dubbed it “BadSuccessor” in a May 2025 blog post. The attack exploits a weakness in “delegated Managed Service Account” or dMSA — a feature that was introduced in Windows Server 2025.
Some of the critical flaws addressed this month with the highest severity (between 9.0 and 9.9 CVSS scores) include a remote code execution bug in the Windows GDI+ component that handles graphics rendering (CVE-2025-53766) and CVE-2025-50165, another graphics rendering weakness. Another critical patch involves CVE-2025-53733, a vulnerability in Microsoft Word that can be exploited without user interaction and triggered through the Preview Pane.
One final critical bug tackled this month deserves attention: CVE-2025-53778, a bug in Windows NTLM, a core function of how Windows systems handle network authentication. According to Microsoft, the flaw could allow an attacker with low-level network access and basic user privileges to exploit NTLM and elevate to SYSTEM-level access — the highest level of privilege in Windows. Microsoft rates the exploitation of this bug as “more likely,” although there is no evidence the vulnerability is being exploited at the moment.
Feel free to holler in the comments if you experience problems installing any of these updates. As ever, the SANS Internet Storm Center has its useful breakdown of the Microsoft patches indexed by severity and CVSS score, and AskWoody.com is keeping an eye out for Windows patches that may cause problems for enterprises and end users.
Windows 10 users out there likely have noticed by now that Microsoft really wants you to upgrade to Windows 11. The reason is that after the Patch Tuesday on October 14, 2025, Microsoft will stop shipping free security updates for Windows 10 computers. The trouble is, many PCs running Windows 10 do not meet the hardware specifications required to install Windows 11 (or they do, but just barely).
If the experience with Windows XP is any indicator, many of these older computers will wind up in landfills or else will be left running in an unpatched state. But if your Windows 10 PC doesn’t have the hardware chops to run Windows 11 and you’d still like to get some use out of it safely, consider installing a newbie-friendly version of Linux, like Linux Mint.
Like most modern Linux versions, Mint will run on anything with a 64-bit CPU that has at least 2GB of memory, although 4GB is recommended. In other words, it will run on almost any computer produced in the last decade.
There are many versions of Linux available, but Linux Mint is likely to be the most intuitive interface for regular Windows users, and it is largely configurable without any fuss at the text-only command-line prompt. Mint and other flavors of Linux come with LibreOffice, which is an open source suite of tools that includes applications similar to Microsoft Office, and it can open, edit and save documents as Microsoft Office files.
If you’d prefer to give Linux a test drive before installing it on a Windows PC, you can always just download it to a removable USB drive. From there, reboot the computer (with the removable drive plugged in) and select the option at startup to run the operating system from the external USB drive. If you don’t see an option for that after restarting, try restarting again and hitting the F8 button, which should open a list of bootable drives. Here’s a fairly thorough tutorial that walks through exactly how to do all this.
And if this is your first time trying out Linux, relax and have fun: The nice thing about a “live” version of Linux (as it’s called when the operating system is run from a removable drive such as a CD or a USB stick) is that none of your changes persist after a reboot. Even if you somehow manage to break something, a restart will return the system back to its original state.
On Sunday, July 20, Microsoft Corp. issued an emergency security update for a vulnerability in SharePoint Server that is actively being exploited to compromise vulnerable organizations. The patch comes amid reports that malicious hackers have used the SharePoint flaw to breach U.S. federal and state agencies, universities, and energy companies.

Image: Shutterstock, by Ascannio.
In an advisory about the SharePoint security hole, a.k.a. CVE-2025-53770, Microsoft said it is aware of active attacks targeting on-premises SharePoint Server customers and exploiting vulnerabilities that were only partially addressed by the July 8, 2025 security update.
The Cybersecurity & Infrastructure Security Agency (CISA) concurred, saying CVE-2025-53770 is a variant on a flaw Microsoft patched earlier this month (CVE-2025-49706). Microsoft notes the weakness applies only to SharePoint Servers that organizations use in-house, and that SharePoint Online and Microsoft 365 are not affected.
The Washington Post reported on Sunday that the U.S. government and partners in Canada and Australia are investigating the hack of SharePoint servers, which provide a platform for sharing and managing documents. The Post reports at least two U.S. federal agencies have seen their servers breached via the SharePoint vulnerability.
According to CISA, attackers exploiting the newly-discovered flaw are retrofitting compromised servers with a backdoor dubbed “ToolShell” that provides unauthenticated, remote access to systems. CISA said ToolShell enables attackers to fully access SharePoint content — including file systems and internal configurations — and execute code over the network.
Researchers at Eye Security said they first spotted large-scale exploitation of the SharePoint flaw on July 18, 2025, and soon found dozens of separate servers compromised by the bug and infected with ToolShell. In a blog post, the researchers said the attacks sought to steal SharePoint server ASP.NET machine keys.
“These keys can be used to facilitate further attacks, even at a later date,” Eye Security warned. “It is critical that affected servers rotate SharePoint server ASP.NET machine keys and restart IIS on all SharePoint servers. Patching alone is not enough. We strongly advise defenders not to wait for a vendor fix before taking action. This threat is already operational and spreading rapidly.”
Microsoft’s advisory says the company has issued updates for SharePoint Server Subscription Edition and SharePoint Server 2019, but that it is still working on updates for supported versions of SharePoint 2019 and SharePoint 2016.
CISA advises vulnerable organizations to enable the anti-malware scan interface (AMSI) in SharePoint, to deploy Microsoft Defender AV on all SharePoint servers, and to disconnect affected products from the public-facing Internet until an official patch is available.
The security firm Rapid7 notes that Microsoft has described CVE-2025-53770 as related to a previous vulnerability — CVE-2025-49704, patched earlier this month — and that CVE-2025-49704 was part of an exploit chain demonstrated at the Pwn2Own hacking competition in May 2025. That exploit chain invoked a second SharePoint weakness — CVE-2025-49706 — which Microsoft unsuccessfully tried to fix in this month’s Patch Tuesday.
Microsoft also has issued a patch for a related SharePoint vulnerability — CVE-2025-53771; Microsoft says there are no signs of active attacks on CVE-2025-53771, and that the patch is to provide more robust protections than the update for CVE-2025-49706.
This is a rapidly developing story. Any updates will be noted with timestamps.
Microsoft today released updates to fix at least 137 security vulnerabilities in its Windows operating systems and supported software. None of the weaknesses addressed this month are known to be actively exploited, but 14 of the flaws earned Microsoft’s most-dire “critical” rating, meaning they could be exploited to seize control over vulnerable Windows PCs with little or no help from users.

While not listed as critical, CVE-2025-49719 is a publicly disclosed information disclosure vulnerability, with all versions as far back as SQL Server 2016 receiving patches. Microsoft rates CVE-2025-49719 as less likely to be exploited, but the availability of proof-of-concept code for this flaw means its patch should probably be a priority for affected enterprises.
Mike Walters, co-founder of Action1, said CVE-2025-49719 can be exploited without authentication, and that many third-party applications depend on SQL server and the affected drivers — potentially introducing a supply-chain risk that extends beyond direct SQL Server users.
“The potential exposure of sensitive information makes this a high-priority concern for organizations handling valuable or regulated data,” Walters said. “The comprehensive nature of the affected versions, spanning multiple SQL Server releases from 2016 through 2022, indicates a fundamental issue in how SQL Server handles memory management and input validation.”
Adam Barnett at Rapid7 notes that today is the end of the road for SQL Server 2012, meaning there will be no future security patches even for critical vulnerabilities, even if you’re willing to pay Microsoft for the privilege.
Barnett also called attention to CVE-2025-47981, a vulnerability with a CVSS score of 9.8 (10 being the worst), a remote code execution bug in the way Windows servers and clients negotiate to discover mutually supported authentication mechanisms. This pre-authentication vulnerability affects any Windows client machine running Windows 10 1607 or above, and all current versions of Windows Server. Microsoft considers it more likely that attackers will exploit this flaw.
Microsoft also patched at least four critical, remote code execution flaws in Office (CVE-2025-49695, CVE-2025-49696, CVE-2025-49697, CVE-2025-49702). The first two are both rated by Microsoft as having a higher likelihood of exploitation, do not require user interaction, and can be triggered through the Preview Pane.
Two more high severity bugs include CVE-2025-49740 (CVSS 8.8) and CVE-2025-47178 (CVSS 8.0); the former is a weakness that could allow malicious files to bypass screening by Microsoft Defender SmartScreen, a built-in feature of Windows that tries to block untrusted downloads and malicious sites.
CVE-2025-47178 involves a remote code execution flaw in Microsoft Configuration Manager, an enterprise tool for managing, deploying, and securing computers, servers, and devices across a network. Ben Hopkins at Immersive said this bug requires very low privileges to exploit, and that it is possible for a user or attacker with a read-only access role to exploit it.
“Exploiting this vulnerability allows an attacker to execute arbitrary SQL queries as the privileged SMS service account in Microsoft Configuration Manager,” Hopkins said. “This access can be used to manipulate deployments, push malicious software or scripts to all managed devices, alter configurations, steal sensitive data, and potentially escalate to full operating system code execution across the enterprise, giving the attacker broad control over the entire IT environment.”
Separately, Adobe has released security updates for a broad range of software, including After Effects, Adobe Audition, Illustrator, FrameMaker, and ColdFusion.
The SANS Internet Storm Center has a breakdown of each individual patch, indexed by severity. If you’re responsible for administering a number of Windows systems, it may be worth keeping an eye on AskWoody for the lowdown on any potentially wonky updates (considering the large number of vulnerabilities and Windows components addressed this month).
If you’re a Windows home user, please consider backing up your data and/or drive before installing any patches, and drop a note in the comments if you encounter any problems with these updates.
Microsoft today released security updates to fix at least 67 vulnerabilities in its Windows operating systems and software. Redmond warns that one of the flaws is already under active attack, and that software blueprints showing how to exploit a pervasive Windows bug patched this month are now public.

The sole zero-day flaw this month is CVE-2025-33053, a remote code execution flaw in the Windows implementation of WebDAV — an HTTP extension that lets users remotely manage files and directories on a server. While WebDAV isn’t enabled by default in Windows, its presence in legacy or specialized systems still makes it a relevant target, said Seth Hoyt, senior security engineer at Automox.
Adam Barnett, lead software engineer at Rapid7, said Microsoft’s advisory for CVE-2025-33053 does not mention that the Windows implementation of WebDAV is listed as deprecated since November 2023, which in practical terms means that the WebClient service no longer starts by default.
“The advisory also has attack complexity as low, which means that exploitation does not require preparation of the target environment in any way that is beyond the attacker’s control,” Barnett said. “Exploitation relies on the user clicking a malicious link. It’s not clear how an asset would be immediately vulnerable if the service isn’t running, but all versions of Windows receive a patch, including those released since the deprecation of WebClient, like Server 2025 and Windows 11 24H2.”
Microsoft warns that an “elevation of privilege” vulnerability in the Windows Server Message Block (SMB) client (CVE-2025-33073) is likely to be exploited, given that proof-of-concept code for this bug is now public. CVE-2025-33073 has a CVSS risk score of 8.8 (out of 10), and exploitation of the flaw leads to the attacker gaining “SYSTEM” level control over a vulnerable PC.
“What makes this especially dangerous is that no further user interaction is required after the initial connection—something attackers can often trigger without the user realizing it,” said Alex Vovk, co-founder and CEO of Action1. “Given the high privilege level and ease of exploitation, this flaw poses a significant risk to Windows environments. The scope of affected systems is extensive, as SMB is a core Windows protocol used for file and printer sharing and inter-process communication.”
Beyond these highlights, 10 of the vulnerabilities fixed this month were rated “critical” by Microsoft, including eight remote code execution flaws.
Notably absent from this month’s patch batch is a fix for a newly discovered weakness in Windows Server 2025 that allows attackers to act with the privileges of any user in Active Directory. The bug, dubbed “BadSuccessor,” was publicly disclosed by researchers at Akamai on May 21, and several public proof-of-concepts are now available. Tenable’s Satnam Narang said organizations that have at least one Windows Server 2025 domain controller should review permissions for principals and limit those permissions as much as possible.
Adobe has released updates for Acrobat Reader and six other products addressing at least 259 vulnerabilities, most of them in an update for Experience Manager. Mozilla Firefox and Google Chrome both recently released security updates that require a restart of the browser to take effect. The latest Chrome update fixes two zero-day exploits in the browser (CVE-2025-5419 and CVE-2025-4664).
For a detailed breakdown on the individual security updates released by Microsoft today, check out the Patch Tuesday roundup from the SANS Internet Storm Center. Action 1 has a breakdown of patches from Microsoft and a raft of other software vendors releasing fixes this month. As always, please back up your system and/or data before patching, and feel free to drop a note in the comments if you run into any problems applying these updates.
Microsoft Corp. today issued software updates to plug at least 139 security holes in various flavors of Windows and other Microsoft products. Redmond says attackers are already exploiting at least two of the vulnerabilities in active attacks against Windows users.

The first Microsoft zero-day this month is CVE-2024-38080, a bug in the Windows Hyper-V component that affects Windows 11 and Windows Server 2022 systems. CVE-2024-38080 allows an attacker to increase their account privileges on a Windows machine. Although Microsoft says this flaw is being exploited, it has offered scant details about its exploitation.
The other zero-day is CVE-2024-38112, which is a weakness in MSHTML, the proprietary engine of Microsoft’s Internet Explorer web browser. Kevin Breen, senior director of threat research at Immersive Labs, said exploitation of CVE-2024-38112 likely requires the use of an “attack chain” of exploits or programmatic changes on the target host, a la Microsoft’s description: “Successful exploitation of this vulnerability requires an attacker to take additional actions prior to exploitation to prepare the target environment.”
“Despite the lack of details given in the initial advisory, this vulnerability affects all hosts from Windows Server 2008 R2 onwards, including clients,” Breen said. “Due to active exploitation in the wild this one should be prioritized for patching.”
Satnam Narang, senior staff research engineer at Tenable, called special attention to CVE-2024-38021, a remote code execution flaw in Microsoft Office. Attacks on this weakness would lead to the disclosure of NTLM hashes, which could be leveraged as part of an NTLM relay or “pass the hash” attack, which lets an attacker masquerade as a legitimate user without ever having to log in.
“One of the more successful attack campaigns from 2023 used CVE-2023-23397, an elevation of privilege bug in Microsoft Outlook that could also leak NTLM hashes,” Narang said. “However, CVE-2024-38021 is limited by the fact that the Preview Pane is not an attack vector, which means that exploitation would not occur just by simply previewing the file.”
The security firm Morphisec, credited with reporting CVE-2024-38021 to Microsoft, said it respectfully disagrees with Microsoft’s “important” severity rating, arguing the Office flaw deserves a more dire “critical” rating given how easy it is for attackers to exploit.
“Their assessment differentiates between trusted and untrusted senders, noting that while the vulnerability is zero-click for trusted senders, it requires one click user interaction for untrusted senders,” Morphisec’s Michael Gorelik said in a blog post about their discovery. “This reassessment is crucial to reflect the true risk and ensure adequate attention and resources are allocated for mitigation.”
In last month’s Patch Tuesday, Microsoft fixed a flaw in its Windows WiFi driver that attackers could use to install malicious software just by sending a vulnerable Windows host a specially crafted data packet over a local network. Jason Kikta at Automox said this month’s CVE-2024-38053 — a security weakness in Windows Layer Two Bridge Network — is another local network “ping-of-death” vulnerability that should be a priority for road warriors to patch.
“This requires close access to a target,” Kikta said. “While that precludes a ransomware actor in Russia, it is something that is outside of most current threat models. This type of exploit works in places like shared office environments, hotels, convention centers, and anywhere else where unknown computers might be using the same physical link as you.”
Automox also highlighted three vulnerabilities in Windows Remote Desktop a service that allocates Client Access Licenses (CALs) when a client connects to a remote desktop host (CVE-2024-38077, CVE-2024-38074, and CVE-2024-38076). All three bugs have been assigned a CVSS score of 9.8 (out of 10) and indicate that a malicious packet could trigger the vulnerability.
Tyler Reguly at Fortra noted that today marks the End of Support date for SQL Server 2014, a platform that according to Shodan still has ~110,000 instances publicly available. On top of that, more than a quarter of all vulnerabilities Microsoft fixed this month are in SQL server.
“A lot of companies don’t update quickly, but this may leave them scrambling to update those environments to supported versions of MS-SQL,” Reguly said.
It’s a good idea for Windows end-users to stay current with security updates from Microsoft, which can quickly pile up otherwise. That doesn’t mean you have to install them on Patch Tuesday. Indeed, waiting a day or three before updating is a sane response, given that sometimes updates go awry and usually within a few days Microsoft has fixed any issues with its patches. It’s also smart to back up your data and/or image your Windows drive before applying new updates.
For a more detailed breakdown of the individual flaws addressed by Microsoft today, check out the SANS Internet Storm Center’s list. For those admins responsible for maintaining larger Windows environments, it often pays to keep an eye on Askwoody.com, which frequently points out when specific Microsoft updates are creating problems for a number of users.
As ever, if you experience any problems applying any of these updates, consider dropping a note about it in the comments; chances are decent someone else reading here has experienced the same issue, and maybe even has a solution.
The homepage of Stark Industries Solutions.
Two weeks before Russia invaded Ukraine in February 2022, a large, mysterious new Internet hosting firm called Stark Industries Solutions materialized and quickly became the epicenter of massive distributed denial-of-service (DDoS) attacks on government and commercial targets in Ukraine and Europe. An investigation into Stark Industries reveals it is being used as a global proxy network that conceals the true source of cyberattacks and disinformation campaigns against enemies of Russia.
At least a dozen patriotic Russian hacking groups have been launching DDoS attacks since the start of the war at a variety of targets seen as opposed to Moscow. But by all accounts, few attacks from those gangs have come close to the amount of firepower wielded by a pro-Russia group calling itself “NoName057(16).”
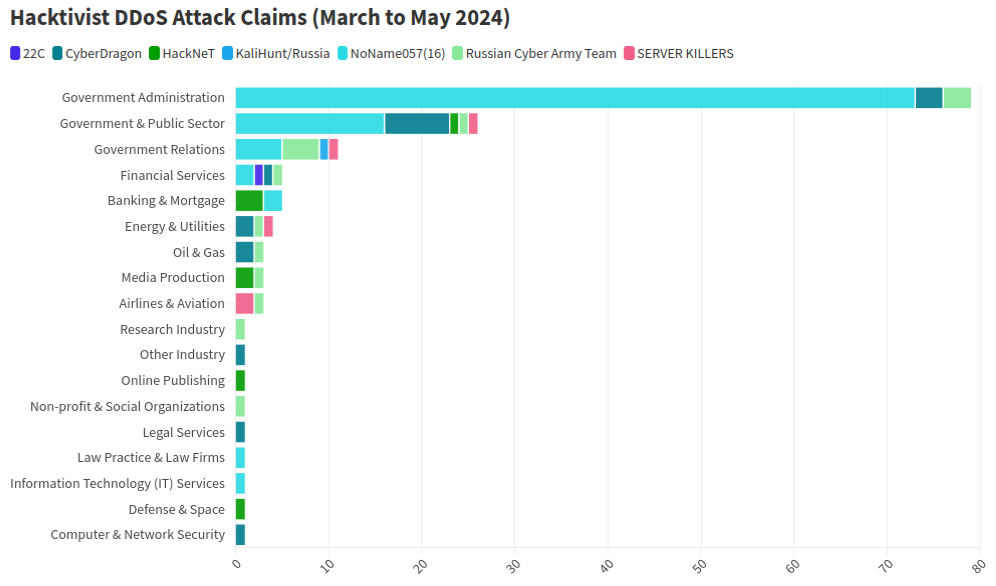
This graphic comes from a recent report from NETSCOUT about DDoS attacks from Russian hacktivist groups.
As detailed by researchers at Radware, NoName has effectively gamified DDoS attacks, recruiting hacktivists via its Telegram channel and offering to pay people who agree to install a piece of software called DDoSia. That program allows NoName to commandeer the host computers and their Internet connections in coordinated DDoS campaigns, and DDoSia users with the most attacks can win cash prizes.
The NoName DDoS group advertising on Telegram. Image: SentinelOne.com.
A report from the security firm Team Cymru found the DDoS attack infrastructure used in NoName campaigns is assigned to two interlinked hosting providers: MIRhosting and Stark Industries. MIRhosting is a hosting provider founded in The Netherlands in 2004. But Stark Industries Solutions Ltd was incorporated on February 10, 2022, just two weeks before the Russian invasion of Ukraine.
Security experts say that not long after the war started, Stark began hosting dozens of proxy services and free virtual private networking (VPN) services, which are designed to help users shield their Internet usage and location from prying eyes.
Proxy providers allow users to route their Internet and Web browsing traffic through someone else’s computer. From a website’s perspective, the traffic from a proxy network user appears to originate from the rented IP address, not from the proxy service customer.

These services can be used in a legitimate manner for several business purposes — such as price comparisons or sales intelligence — but they are also massively abused for hiding cybercrime activity because they can make it difficult to trace malicious traffic to its original source.
What’s more, many proxy services do not disclose how they obtain access to the proxies they are renting out, and in many cases the access is obtained through the dissemination of malicious software that turns the infected system into a traffic relay — usually unbeknownst to the legitimate owner of the Internet connection. Other proxy services will allow users to make money by renting out their Internet connection to anyone.
Spur.us is a company that tracks VPNs and proxy services worldwide. Spur finds that Stark Industries (AS44477) currently is home to at least 74 VPN services, and 40 different proxy services. As we’ll see in the final section of this story, just one of those proxy networks has over a million Internet addresses available for rent across the globe.
Raymond Dijkxhoorn operates a hosting firm in The Netherlands called Prolocation. He also co-runs SURBL, an anti-abuse service that flags domains and Internet address ranges that are strongly associated with spam and cybercrime activity, including DDoS.
Dijkxhoorn said last year SURBL heard from multiple people who said they operated VPN services whose web resources were included in SURBL’s block lists.
“We had people doing delistings at SURBL for domain names that were suspended by the registrars,” Dijkhoorn told KrebsOnSecurity. “And at least two of them explained that Stark offered them free VPN services that they were reselling.”
Dijkxhoorn added that Stark Industries also sponsored activist groups from Ukraine.
“How valuable would it be for Russia to know the real IPs from Ukraine’s tech warriors?” he observed.
Richard Hummel is threat intelligence lead at NETSCOUT. Hummel said when he considers the worst of all the hosting providers out there today, Stark Industries is consistently near or at the top of that list.
“The reason is we’ve had at least a dozen service providers come to us saying, ‘There’s this network out there inundating us with traffic,'” Hummel said. “And it wasn’t even DDoS attacks. [The systems] on Stark were just scanning these providers so fast it was crashing some of their services.”
Hummel said NoName will typically launch their attacks using a mix of resources rented from major, legitimate cloud services, and those from so-called “bulletproof” hosting providers like Stark. Bulletproof providers are so named when they earn or cultivate a reputation for ignoring any abuse complaints or police reports about activity on their networks.
Combining bulletproof providers with legitimate cloud hosting, Hummel said, likely makes NoName’s DDoS campaigns more resilient because many network operators will hesitate to be too aggressive in blocking Internet addresses associated with the major cloud services.
“What we typically see here is a distribution of cloud hosting providers and bulletproof hosting providers in DDoS attacks,” he said. “They’re using public cloud hosting providers because a lot of times that’s your first layer of network defense, and because [many companies are wary of] over-blocking access to legitimate cloud resources.”
But even if the cloud provider detects abuse coming from the customer, the provider is probably not going to shut the customer down immediately, Hummel said.
“There is usually a grace period, and even if that’s only an hour or two, you can still launch a large number of attacks in that time,” he said. “And then they just keep coming back and opening new cloud accounts.”
Stark Industries is incorporated at a mail drop address in the United Kingdom. UK business records list an Ivan Vladimirovich Neculiti as the company’s secretary. Mr. Neculiti also is named as the CEO and founder of PQ Hosting Plus S.R.L. (aka Perfect Quality Hosting), a Moldovan company formed in 2019 that lists the same UK mail drop address as Stark Industries.

Ivan Neculiti, as pictured on LinkedIn.
Reached via LinkedIn, Mr. Neculiti said PQ Hosting established Stark Industries as a “white label” of its brand so that “resellers could distribute our services using our IP addresses and their clients would not have any affairs with PQ Hosting.”
“PQ Hosting is a company with over 1,000+ of [our] own physical servers in 38 countries and we have over 100,000 clients,” he said. “Though we are not as large as Hetzner, Amazon and OVH, nevertheless we are a fast growing company that provides services to tens of thousands of private customers and legal entities.”
Asked about the constant stream of DDoS attacks whose origins have traced back to Stark Industries over the past two years, Neculiti maintained Stark hasn’t received any official abuse reports about attacks coming from its networks.
“It was probably some kind of clever attack that we did not see, I do not rule out this fact, because we have a very large number of clients and our Internet channels are quite large,” he said. “But, in this situation, unfortunately, no one contacted us to report that there was an attack from our addresses; if someone had contacted us, we would have definitely blocked the network data.”
DomainTools.com finds Ivan V. Neculiti was the owner of war[.]md, a website launched in 2008 that chronicled the history of a 1990 armed conflict in Moldova known as the Transnistria War and the Moldo-Russian war.

An ad for war.md, circa 2009.
Transnistria is a breakaway pro-Russian region that declared itself a state in 1990, although it is not internationally recognized. The copyright on that website credits the “MercenarieS TeaM,” which was at one time a Moldovan IT firm. Mr. Neculiti confirmed personally registering this domain.
The data breach tracking service Constella Intelligence reports that an Ivan V. Neculiti registered multiple online accounts under the email address dfyz_bk@bk.ru. Cyber intelligence firm Intel 471 shows this email address is tied to the username “dfyz” on more than a half-dozen Russian language cybercrime forums since 2008. The user dfyz on Searchengines[.]ru in 2008 asked other forum members to review war.md, and said they were part of the MercenarieS TeaM.
Back then, dfyz was selling “bulletproof servers for any purpose,” meaning the hosting company would willfully ignore abuse complaints or police inquiries about the activity of its customers.
DomainTools reports there are at least 33 domain names registered to dfyz_bk@bk.ru. Several of these domains have Ivan Neculiti in their registration records, including tracker-free[.]cn, which was registered to an Ivan Neculiti at dfyz_bk@bk.ru and referenced the MercenarieS TeaM in its original registration records.
Dfyz also used the nickname DonChicho, who likewise sold bulletproof hosting services and access to hacked Internet servers. In 2014, a prominent member of the Russian language cybercrime community Antichat filed a complaint against DonChicho, saying this user scammed them and had used the email address dfyz_bk@bk.ru.
The complaint said DonChicho registered on Antichat from the Transnistria Internet address 84.234.55[.]29. Searching this address in Constella reveals it has been used to register just five accounts online that have been created over the years, including one at ask.ru, where the user registered with the email address neculitzy1@yandex.ru. Constella also returns for that email address a user by the name “Ivan” at memoraleak.com and 000webhost.com.
Constella finds that the password most frequently used by the email address dfyz_bk@bk.ru was “filecast,” and that there are more than 90 email addresses associated with this password. Among them are roughly two dozen addresses with the name “Neculiti” in them, as well as the address support@donservers[.]ru.
Intel 471 says DonChicho posted to several Russian cybercrime forums that support@donservers[.]ru was his address, and that he logged into cybercrime forums almost exclusively from Internet addresses in Tiraspol, the capital of Transnistria. A review of DonChicho’s posts shows this person was banned from several forums in 2014 for scamming other users.
Cached copies of DonChicho’s vanity domain (donchicho[.]ru) show that in 2009 he was a spammer who peddled knockoff prescription drugs via Rx-Promotion, once one of the largest pharmacy spam moneymaking programs for Russian-speaking affiliates.
Mr. Neculiti told KrebsOnSecurity he has never used the nickname DonChicho.
“I may assure you that I have no relation to DonChicho nor to his bulletproof servers,” he said.
Below is a mind map that shows the connections between the accounts mentioned above.
Earlier this year, NoName began massively hitting government and industry websites in Moldova. A new report from Arbor Networks says the attacks began around March 6, when NoName alleged the government of Moldova was “craving for Russophobia.”
“Since early March, more than 50 websites have been targeted, according to posted ‘proof’ by the groups involved in attacking the country,” Arbor’s ASERT Team wrote. “While NoName seemingly initiated the ramp of attacks, a host of other DDoS hacktivists have joined the fray in claiming credit for attacks across more than 15 industries.”
The German independent news outlet Correctiv.org last week published a scathing investigative report on Stark Industries and MIRhosting, which notes that Ivan Neculiti operates his hosting companies with the help of his brother, Yuri.
The report points out that Stark Industries continues to host a Russian disinformation news outlet called “Recent Reliable News” (RRN) that was sanctioned by the European Union in 2023 for spreading links to propaganda blogs and fake European media and government websites.
“The website was not running on computers in Moscow or St. Petersburg until recently, but in the middle of the EU, in the Netherlands, on the computers of the Neculiti brothers,” Correctiv reporters wrote.
“After a request from this editorial team, a well-known service was installed that hides the actual web host,” the report continues. “Ivan Neculiti announced that he had blocked the associated access and server following internal investigations. “We very much regret that we are only now finding out that one of our customers is a sanctioned portal,” said the company boss. However, RRN is still accessible via its servers.”
Correctiv also points to a January 2023 report from the Ukrainian government, which found servers from Stark Industries Solutions were used as part of a cyber attack on the Ukrainian news agency “Ukrinform”. Correctiv notes the notorious hacker group Sandworm — an advanced persistent threat (APT) group operated by a cyberwarfare unit of Russia’s military intelligence service — was identified by Ukrainian government authorities as responsible for that attack.
Public records indicate MIRhosting is based in The Netherlands and is operated by 37-year old Andrey Nesterenko, whose personal website says he is an accomplished concert pianist who began performing publicly at a young age.
DomainTools says mirhosting[.]com is registered to Mr. Nesterenko and to Innovation IT Solutions Corp, which lists addresses in London and in Nesterenko’s stated hometown of Nizhny Novgorod, Russia.
This is interesting because according to the book Inside Cyber Warfare by Jeffrey Carr, Innovation IT Solutions Corp. was responsible for hosting StopGeorgia[.]ru, a hacktivist website for organizing cyberattacks against Georgia that appeared at the same time Russian forces invaded the former Soviet nation in 2008. That conflict was thought to be the first war ever fought in which a notable cyberattack and an actual military engagement happened simultaneously.
Responding to questions from KrebsOnSecurity, Mr. Nesterenko said he couldn’t say whether his network had ever hosted the StopGeorgia website back in 2008 because his company didn’t keep records going back that far. But he said Stark Industries Solutions is indeed one of MIRhsoting’s colocation customers.
“Our relationship is purely provider-customer,” Nesterenko said. “They also utilize multiple providers and data centers globally, so connecting them directly to MIRhosting overlooks their broader network.”
“We take any report of malicious activity seriously and are always open to information that can help us identify and prevent misuse of our infrastructure, whether involving Stark Industries or any other customer,” Nesterenko continued. “In cases where our services are exploited for malicious purposes, we collaborate fully with Dutch cyber police and other relevant authorities to investigate and take appropriate measures. However, we have yet to receive any actionable information beyond the article itself, which has not provided us with sufficient detail to identify or block malicious actors.”
In December 2022, security firm Recorded Future profiled the phishing and credential harvesting infrastructure used for Russia-aligned espionage operations by a group dubbed Blue Charlie (aka TAG-53), which has targeted email accounts of nongovernmental organizations and think tanks, journalists, and government and defense officials.
Recorded Future found that virtually all the Blue Charlie domains existed in just ten different ISPs, with a significant concentration located in two networks, one of which was MIRhosting. Both Microsoft and the UK government assess that Blue Charlie is linked to the Russian threat activity groups variously known as Callisto Group, COLDRIVER, and SEABORGIUM.
Mr. Nesterenko took exception to a story on that report from The Record, which is owned by Recorded Future.
“We’ve discussed its contents with our customer, Stark Industries,” he said. “We understand that they have initiated legal proceedings against the website in question, as they firmly believe that the claims made are inaccurate.”
Recorded Future said they updated their story with comments from Mr. Neculiti, but that they stand by their reporting.
Mr. Nesterenko’s LinkedIn profile says he was previously the foreign region sales manager at Serverius-as, a hosting company in The Netherlands that remains in the same data center as MIRhosting.
In February, the Dutch police took 13 servers offline that were used by the infamous LockBit ransomware group, which had originally bragged on its darknet website that its home base was in The Netherlands. Sources tell KrebsOnSecurity the servers seized by the Dutch police were located in Serverius’ data center in Dronten, which is also shared by MIRhosting.
Serverius-as did not respond to requests for comment. Nesterenko said MIRhosting does use one of Serverius’s data centers for its operations in the Netherlands, alongside two other data centers, but that the recent incident involving the seizure of servers has no connection to MIRhosting.
“We are legally prohibited by Dutch law and police regulations from sharing information with third parties regarding any communications we may have had,” he said.
A February 2024 report from security firm ESET found Serverius-as systems were involved in a series of targeted phishing attacks by Russia-aligned groups against Ukrainian entities throughout 2023. ESET observed that after the spearphishing domains were no longer active, they were converted to promoting rogue Internet pharmacy websites.
A review of the Internet address ranges recently added to the network operated by Stark Industries Solutions offers some insight into its customer base, usage, and maybe even true origins. Here is a snapshot (PDF) of all Internet address ranges announced by Stark Industries so far in the month of May 2024 (this information was graciously collated by the network observability platform Kentik.com).
Those records indicate that the largest portion of the IP space used by Stark is in The Netherlands, followed by Germany and the United States. Stark says it is connected to roughly 4,600 Internet addresses that currently list their ownership as Comcast Cable Communications.
A review of those address ranges at spur.us shows all of them are connected to an entity called Proxyline, which is a sprawling proxy service based in Russia that currently says it has more than 1.6 million proxies globally that are available for rent.

Proxyline dot net.
Reached for comment, Comcast said the Internet address ranges never did belong to Comcast, so it is likely that Stark has been fudging the real location of its routing announcements in some cases.
Stark reports that it has more than 67,000 Internet addresses at Santa Clara, Calif.-based EGIhosting. Spur says the Stark addresses involving EGIhosting all map to Proxyline as well. EGIhosting did not respond to requests for comment.
EGIhosting manages Internet addresses for the Cyprus-based hosting firm ITHOSTLINE LTD (aka HOSTLINE-LTD), which is represented throughout Stark’s announced Internet ranges. Stark says it has more than 21,000 Internet addresses with HOSTLINE. Spur.us finds Proxyline addresses are especially concentrated in the Stark ranges labeled ITHOSTLINE LTD, HOSTLINE-LTD, and Proline IT.
Stark’s network list includes approximately 21,000 Internet addresses at Hockessin, De. based DediPath, which abruptly ceased operations without warning in August 2023. According to a phishing report released last year by Interisle Consulting, DediPath was the fourth most common source of phishing attacks in the year ending Oct. 2022. Spur.us likewise finds that virtually all of the Stark address ranges marked “DediPath LLC” are tied to Proxyline.
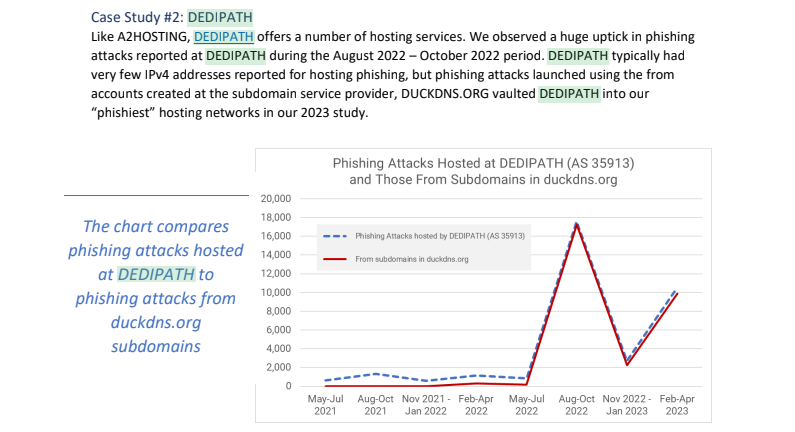
Image: Interisle Consulting.
A large number of the Internet address ranges announced by Stark in May originate in India, and the names that are self-assigned to many of these networks indicate they were previously used to send large volumes of spam for herbal medicinal products, with names like HerbalFarm, AdsChrome, Nutravo, Herbzoot and Herbalve.
The anti-spam organization SpamHaus reports that many of the Indian IP address ranges are associated with known “snowshoe spam,” a form of abuse that involves mass email campaigns spread across several domains and IP addresses to weaken reputation metrics and avoid spam filters.
It’s not clear how much of Stark’s network address space traces its origins to Russia, but big chunks of it recently belonged to some of the oldest entities on the Russian Internet (a.k.a. “Runet”).
For example, many Stark address ranges were most recently assigned to a Russian government entity whose full name is the “Federal State Autonomous Educational Establishment of Additional Professional Education Center of Realization of State Educational Policy and Informational Technologies.”
A review of Internet address ranges adjacent to this entity reveals a long list of Russian government organizations that are part of the Federal Guard Service of the Russian Federation. Wikipedia says the Federal Guard Service is a Russian federal government agency concerned with tasks related to protection of several high-ranking state officials, including the President of Russia, as well as certain federal properties. The agency traces its origins to the USSR’s Ninth Directorate of the KGB, and later the presidential security service.
Stark recently announced the address range 213.159.64.0/20 from April 27 to May 1, and this range was previously assigned to an ancient ISP in St. Petersburg, RU called the Computer Technologies Institute Ltd.
According to a post on the Russian language webmaster forum searchengines[.]ru, the domain for Computer Technologies Institute — ctinet[.]ru — is the seventh-oldest domain in the entire history of the Runet.
Curiously, Stark also lists large tracts of Internet addresses (close to 48,000 in total) assigned to a small ISP in Kharkiv, Ukraine called NetAssist. Reached via email, the CEO of NetAssist Max Tulyev confirmed his company provides a number of services to PQ Hosting.
“We colocate their equipment in Warsaw, Madrid, Sofia and Thessaloniki, provide them IP transit and IPv4 addresses,” Tulyev said. “For their size, we receive relatively low number of complains to their networks. I never seen anything about their pro-Russian activity or support of Russian hackers. It is very interesting for me to see proofs of your accusations.”
Spur.us mapped the entire infrastructure of Proxyline, and found more than one million proxies across multiple providers, but by far the biggest concentration was at Stark Industries Solutions. The full list of Proxyline address ranges (.CSV) shows two other ISPs appear repeatedly throughout the list. One is Kharkiv, Ukraine based ITL LLC, also known as Information Technology Laboratories Group, and Integrated Technologies Laboratory.
The second is a related hosting company in Miami, called Green Floid LLC. Green Floid featured in a 2017 scoop by CNN, which profiled the company’s owner and quizzed him about Russian troll farms using proxy networks on Green Floid and its parent firm ITL to mask disinformation efforts tied to the Kremlin’s Internet Research Agency (IRA). At the time, the IRA was using Facebook and other social media networks to spread videos showing police brutality against African Americans in an effort to encourage protests across the United States.

Doug Madory, director of Internet analysis at Kentik, was able to see at a high level the top sources and destinations for traffic traversing Stark’s network.
“Based on our aggregate NetFlow, we see Iran as the top destination (35.1%) for traffic emanating from Stark (AS44477),” Madory said. “Specifically, the top destination is MTN Irancell, while the top source is Facebook. This data supports the theory that AS44477 houses proxy services as Facebook is blocked in Iran.”
On April 30, the security firm Malwarebytes explored an extensive malware operation that targets corporate Internet users with malicious ads. Among the sites used as lures in that campaign were fake Wall Street Journal and CNN websites that told visitors they were required to install a WSJ or CNN-branded browser extension (malware). Malwarebytes found a domain name central to that operation was hosted at Internet addresses owned by Stark Industries.
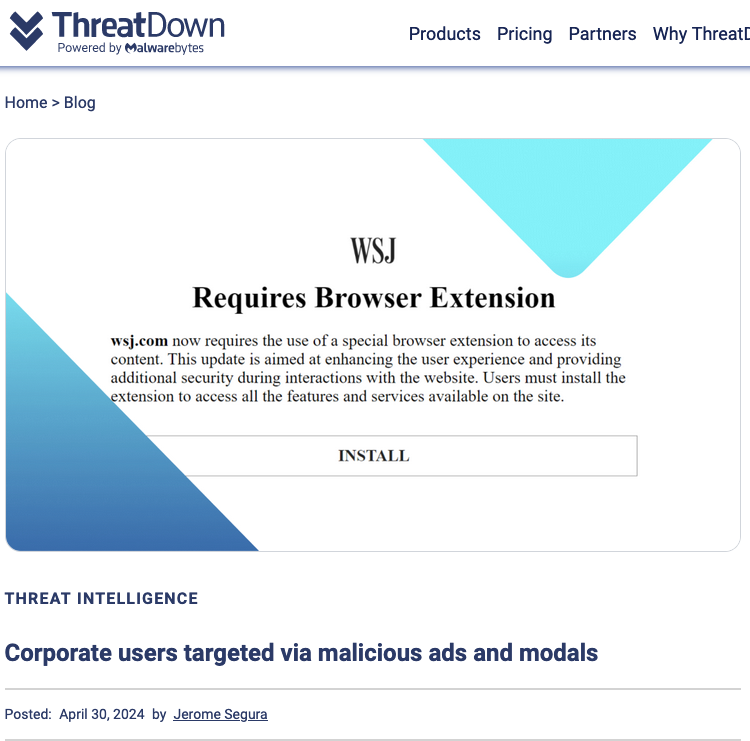
Image: threatdown.com
If only Patch Tuesdays came around infrequently — like total solar eclipse rare — instead of just creeping up on us each month like The Man in the Moon. Although to be fair, it would be tough for Microsoft to eclipse the number of vulnerabilities fixed in this month’s patch batch — a record 147 flaws in Windows and related software.

Yes, you read that right. Microsoft today released updates to address 147 security holes in Windows, Office, Azure, .NET Framework, Visual Studio, SQL Server, DNS Server, Windows Defender, Bitlocker, and Windows Secure Boot.
“This is the largest release from Microsoft this year and the largest since at least 2017,” said Dustin Childs, from Trend Micro’s Zero Day Initiative (ZDI). “As far as I can tell, it’s the largest Patch Tuesday release from Microsoft of all time.”
Tempering the sheer volume of this month’s patches is the middling severity of many of the bugs. Only three of April’s vulnerabilities earned Microsoft’s most-dire “critical” rating, meaning they can be abused by malware or malcontents to take remote control over unpatched systems with no help from users.
Most of the flaws that Microsoft deems “more likely to be exploited” this month are marked as “important,” which usually involve bugs that require a bit more user interaction (social engineering) but which nevertheless can result in system security bypass, compromise, and the theft of critical assets.
Ben McCarthy, lead cyber security engineer at Immersive Labs called attention to CVE-2024-20670, an Outlook for Windows spoofing vulnerability described as being easy to exploit. It involves convincing a user to click on a malicious link in an email, which can then steal the user’s password hash and authenticate as the user in another Microsoft service.
Another interesting bug McCarthy pointed to is CVE-2024-29063, which involves hard-coded credentials in Azure’s search backend infrastructure that could be gleaned by taking advantage of Azure AI search.
“This along with many other AI attacks in recent news shows a potential new attack surface that we are just learning how to mitigate against,” McCarthy said. “Microsoft has updated their backend and notified any customers who have been affected by the credential leakage.”
CVE-2024-29988 is a weakness that allows attackers to bypass Windows SmartScreen, a technology Microsoft designed to provide additional protections for end users against phishing and malware attacks. Childs said one of ZDI’s researchers found this vulnerability being exploited in the wild, although Microsoft doesn’t currently list CVE-2024-29988 as being exploited.
“I would treat this as in the wild until Microsoft clarifies,” Childs said. “The bug itself acts much like CVE-2024-21412 – a [zero-day threat from February] that bypassed the Mark of the Web feature and allows malware to execute on a target system. Threat actors are sending exploits in a zipped file to evade EDR/NDR detection and then using this bug (and others) to bypass Mark of the Web.”
Update, 7:46 p.m. ET: A previous version of this story said there were no zero-day vulnerabilities fixed this month. BleepingComputer reports that Microsoft has since confirmed that there are actually two zero-days. One is the flaw Childs just mentioned (CVE-2024-21412), and the other is CVE-2024-26234, described as a “proxy driver spoofing” weakness.
Satnam Narang at Tenable notes that this month’s release includes fixes for two dozen flaws in Windows Secure Boot, the majority of which are considered “Exploitation Less Likely” according to Microsoft.
“However, the last time Microsoft patched a flaw in Windows Secure Boot in May 2023 had a notable impact as it was exploited in the wild and linked to the BlackLotus UEFI bootkit, which was sold on dark web forums for $5,000,” Narang said. “BlackLotus can bypass functionality called secure boot, which is designed to block malware from being able to load when booting up. While none of these Secure Boot vulnerabilities addressed this month were exploited in the wild, they serve as a reminder that flaws in Secure Boot persist, and we could see more malicious activity related to Secure Boot in the future.”
For links to individual security advisories indexed by severity, check out ZDI’s blog and the Patch Tuesday post from the SANS Internet Storm Center. Please consider backing up your data or your drive before updating, and drop a note in the comments here if you experience any issues applying these fixes.
Adobe today released nine patches tackling at least two dozen vulnerabilities in a range of software products, including Adobe After Effects, Photoshop, Commerce, InDesign, Experience Manager, Media Encoder, Bridge, Illustrator, and Adobe Animate.
KrebsOnSecurity needs to correct the record on a point mentioned at the end of March’s “Fat Patch Tuesday” post, which looked at new AI capabilities built into Adobe Acrobat that are turned on by default. Adobe has since clarified that its apps won’t use AI to auto-scan your documents, as the original language in its FAQ suggested.
“In practice, no document scanning or analysis occurs unless a user actively engages with the AI features by agreeing to the terms, opening a document, and selecting the AI Assistant or generative summary buttons for that specific document,” Adobe said earlier this month.
In 2020, the United States brought charges against four men accused of building a bulletproof hosting empire that once dominated the Russian cybercrime industry and supported multiple organized cybercrime groups. All four pleaded guilty to conspiracy and racketeering charges. But there is a fascinating and untold backstory behind the two Russian men involved, who co-ran the world’s top spam forum and worked closely with Russia’s most dangerous cybercriminals.
From January 2005 to April 2013, there were two primary administrators of the cybercrime forum Spamdot (a.k.a Spamit), an invite-only community for Russian-speaking people in the businesses of sending spam and building botnets of infected computers to relay said spam. The Spamdot admins went by the nicknames Icamis (a.k.a. Ika), and Salomon (a.k.a. Sal).
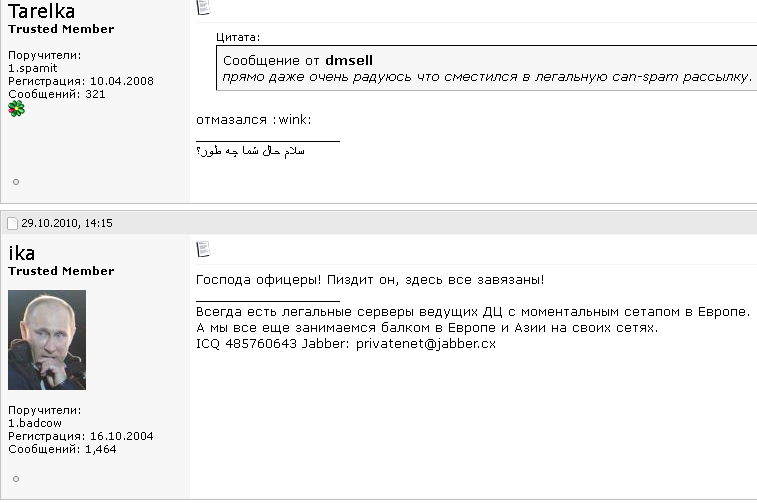
Spamdot forum administrator “Ika” a.k.a. “Icamis” responds to a message from “Tarelka,” the botmaster behind the Rustock botnet. Dmsell said: “I’m actually very glad that I switched to legal spam mailing,” prompting Tarelka and Ika to scoff.
As detailed in my 2014 book, Spam Nation, Spamdot was home to crooks controlling some of the world’s nastiest botnets, global malware contagions that went by exotic names like Rustock, Cutwail, Mega-D, Festi, Waledac, and Grum.
Icamis and Sal were in daily communications with these botmasters, via the Spamdot forum and private messages. Collectively in control over millions of spam-spewing zombies, those botmasters also continuously harvested passwords and other data from infected machines.
As we’ll see in a moment, Salomon is now behind bars, in part because he helped to rob dozens of small businesses in the United States using some of those same harvested passwords. He is currently housed in a federal prison in Michigan, serving the final stretch of a 60-month sentence.
But the identity and whereabouts of Icamis have remained a mystery to this author until recently. For years, security experts — and indeed, many top cybercriminals in the Spamit affiliate program — have expressed the belief that Sal and Icamis were likely the same person using two different identities. And there were many good reasons to support this conclusion.
For example, in 2010 Spamdot and its spam affiliate program Spamit were hacked, and its user database shows Sal and Icamis often accessed the forum from the same Internet address — usually from Cherepovets, an industrial town situated approximately 230 miles north of Moscow. Also, it was common for Icamis to reply when Spamdot members communicated a request or complaint to Sal, and vice versa.
Image: maps.google.com
Still, other clues suggested Icamis and Sal were two separate individuals. For starters, they frequently changed the status on their instant messenger clients at different times. Also, they each privately discussed with others having attended different universities.
KrebsOnSecurity began researching Icamis’s real-life identity in 2012, but failed to revisit any of that research until recently. In December 2023, KrebsOnSecurity published new details about the identity of “Rescator,” a Russian cybercriminal who is thought to be closely connected to the 2013 data breach at Target.
That story mentioned Rescator’s real-life identity was exposed by Icamis in April 2013, as part of a lengthy farewell letter Ika wrote to Spamdot members wherein Ika said he was closing the forum and quitting the cybercrime business entirely.
To no one’s shock, Icamis didn’t quit the business: He simply became more quiet and circumspect about his work, which increasingly was focused on helping crime groups siphon funds from U.S. bank accounts. But the Rescator story was a reminder that 10 years worth of research on who Ika/Icamis is in real life had been completely set aside. This post is an attempt to remedy that omission.
The farewell post from Ika (aka Icamis), the administrator of both the BlackSEO forum and Pustota, the successor forum to Spamit/Spamdot.
Icamis and Sal offered a comprehensive package of goods and services that any aspiring or accomplished spammer would need on a day-to-day basis: Virtually unlimited bulletproof domain registration and hosting services, as well as services that helped botmasters evade spam block lists generated by anti-spam groups like Spamhaus.org. Here’s snippet of Icamis’s ad on Spamdot from Aug. 2008, wherein he addresses forum members with the salutation, “Hello Gentlemen Scammers.”
We are glad to present you our services!
Many are already aware (and are our clients), but publicity is never superfluous.Domains.
– all major gtlds (com, net, org, info, biz)
– many interesting and uninteresting cctlds
– options for any topic
– processing of any quantities
– guarantees
– exceptionally low prices for domains for white and gray schemes (including any SEO and affiliate spam )
– control panel with balances and auto-registration
– all services under the Ikamis brand, proven over the years;)Servers.
– long-term partnerships with several [data centers] in several parts of the world for any topic
– your own data center (no longer in Russia ;)) for gray and white topics
– any configuration and any hardware
– your own IP networks (PI, not PA) and full legal support
– realtime backups to neutral sites
– guarantees and full responsibility for the services provided
– non-standard equipment on request
– our own admins to resolve any technical issues (services are free for clients)
– hosting (shared and vps) is also possibleNon-standard and related services.
– ssl certificates signed by geotrust and thawte
– old domains (any year, any quantity)
– beautiful domains (keyword, short, etc.)
– domains with indicators (any, for SEO, etc.)
– making unstable gtld domains stable
– interception and hijacking of custom domains (expensive)
– full domain posting via web.archive.org with restoration of native content (preliminary applications)
– any updates to our panels to suit your needs upon request (our own coders)All orders for the “Domains” sections and “Servers” are carried out during the day (depending on our workload).
For non-standard and related services, a preliminary application is required 30 days in advance (except for ssl certificates – within 24 hours).
Icamis and Sal frequently claimed that their service kept Spamhaus and other anti-spam groups several steps behind their operations. But it’s clear that those anti-spam operations had a real and painful impact on spam revenues, and Salomon was obsessed with striking back at anti-spam groups, particularly Spamhaus.
In 2007, Salomon collected more than $3,000 from botmasters affiliated with competing spam affiliate programs that wanted to see Spamhaus suffer, and the money was used to fund a week-long distributed denial-of-service (DDoS) attack against Spamhaus and its online infrastructure. But rather than divert their spam botnets from their normal activity and thereby decrease sales, the botmasters voted to create a new DDoS botnet by purchasing installations of DDoS malware on thousands of already-hacked PCs (at a rate of $25 per 1,000 installs).
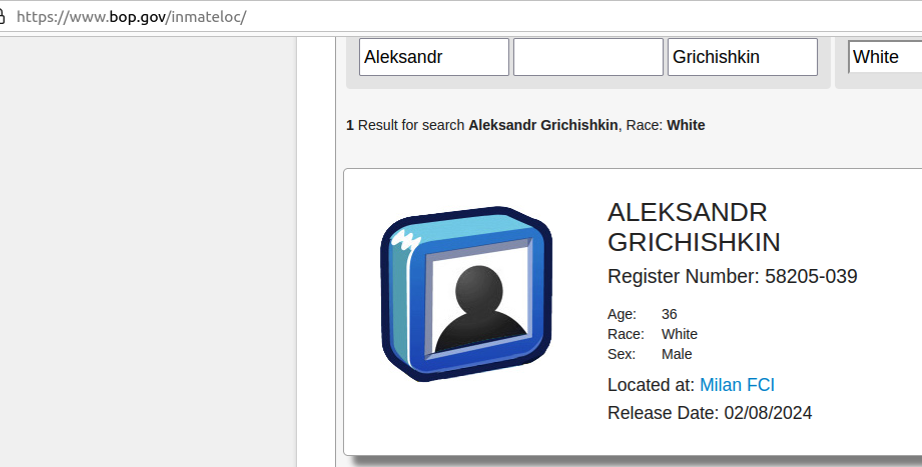
As an affiliate of Spamdot, Salomon used the email address ad1@safe-mail.net, and the password 19871987gr. The breach tracking service Constella Intelligence found the password 19871987gr was used by the email address grichishkin@gmail.com. Multiple accounts are registered to that email address under the name Alexander Valerievich Grichishkin, from Cherepovets.
In 2020, Grichishkin was arrested outside of Russia on a warrant for providing bulletproof hosting services to cybercriminal gangs. The U.S. government said Grichishkin and three others set up the infrastructure used by cybercriminals between 2009 to 2015 to distribute malware and attack financial institutions and victims throughout the United States.
Those clients included crooks using malware like Zeus, SpyEye, Citadel and the Blackhole exploit kit to build botnets and steal banking credentials.
“The Organization and its members helped their clients to access computers without authorization, steal financial information (including banking credentials), and initiate unauthorized wire transfers from victims’ financial accounts,” the government’s complaint stated.
Grichishkin pleaded guilty to conspiracy charges and was sentenced to four years in prison. He is 36 years old, has a wife and kids in Thailand, and is slated for release on February 8, 2024.
The identity of Icamis came into view when KrebsOnSecurity began focusing on clues that might connect Icamis to Cherepovets (Ika’s apparent hometown based on the Internet addresses he regularly used to access Spamdot).
Historic domain ownership records from DomainTools.com reveal that many of the email addresses and domains connected to Icamis invoke the name “Andrew Artz,” including icamis[.]ws, icamis[.]ru, and icamis[.]biz. Icamis promoted his services in 2003 — such as bulk-domains[.]info — using the email address icamis@4host.info. From one of his ads in 2005:
Domains For Projects Advertised By Spam
I can register bulletproof domains for sites and projects advertised by spam(of course they must be legal). I can not provide DNS for u, only domains. The price will be:
65$ for domain[if u will buy less than 5 domains]
50$ for domain[more than 5 domains]
45$ for domain[more than 10 domains]
These prices are for domains in the .net & .com zones.
If u want to order domains write me to: icamis@4host.info
In 2009, an “Andrew Artz” registered at the hosting service FirstVDS.com using the email address icamis@4host.info, with a notation saying the company name attached to the account was “WMPay.” Likewise, the bulletproof domain service icamis[.]ws was registered to an Andrew Artz.
The domain wmpay.ru is registered to the phonetically similar name “Andrew Hertz,” at andrew@wmpay.ru. A search on “icamis.ru” in Google brings up a 2003 post by him on a discussion forum designed by and for students of Amtek, a secondary school in Cherepovets (Icamis was commenting from an Internet address in Cherepovets).
The website amtek-foreva-narod.ru is still online, and it links to several yearbooks for Amtek graduates. It states that the yearbook for the Amtek class of 2004 is hosted at 41.wmpay[.]com.
The yearbook photos for the Amtek class of 2004 are not indexed in the Wayback Machine at archive.org, but the names and nicknames of 16 students remain. However, it appears that the entry for one student — the Wmpay[.]com site administrator — was removed at some point.
In 2004, the administrator of the Amtek discussion forum — a 2003 graduate who used the handle “Grand” — observed that there were three people named Andrey who graduated from Amtek in 2004, but one of them was conspicuously absent from the yearbook at wmpay[.]ru: Andrey Skvortsov.
To bring this full circle, Icamis was Andrey Skvortsov, the other Russian man charged alongside Grichiskin (the two others who pleaded guilty to conspiracy charges were from Estonia and Lithuania). All of the defendants in that case pleaded guilty to conspiracy to engage in a Racketeer Influenced Corrupt Organization (RICO).
[Author’s note: No doubt government prosecutors had their own reasons for omitting the nicknames of the defendants in their press releases, but that information sure would have saved me a lot of time and effort].
Skvortsov was sentenced to time served, and presumably deported. His current whereabouts are unknown and he was not reachable for comment via his known contact addresses.
The government says Ika and Sal’s bulletproof hosting empire provided extensive support for a highly damaging cybercrime group known as the JabberZeus Crew, which worked closely with the author of the Zeus Trojan — Evgeniy Mikhailovich Bogachev — to develop a then-advanced strain of the Zeus malware that was designed to defeat one-time codes for authentication. Bogachev is a top Russian cybercriminal with a standing $3 million bounty on his head from the FBI.
The JabberZeus Crew stole money by constantly recruiting money mules, people in the United States and in Europe who could be enticed or tricked into forwarding money stolen from cybercrime victims. Interestingly, Icamis’s various email addresses are connected to websites for a vast network of phony technology companies that claimed they needed people with bank accounts to help pay their overseas employees.
Icamis used the email address tech@safe-mail.net on Spamdot, and this email address is tied to the registration records for multiple phony technology companies that were set up to recruit money mules.
One such site — sun-technology[.]net — advertised itself as a Hong Kong-based electronics firm that was looking for “honest, responsible and motivated people in UK, USA, AU and NZ to be Sales Representatives in your particular region and receive payments from our clients. Agent commission is 5 percent of total amount received to the personal bank account. You may use your existing bank account or open a new one for these purposes.”
In January 2010, KrebsOnSecurity broke the news that the JabberZeus crew had just used money mules to steal $500,000 from tiny Duanesburg Central School District in upstate New York. As part of his sentence, Skvortsov was ordered to pay $497,200 in restitution to the Duanesburg Central School District.
The JabberZeus Crew operated mainly out of the eastern Ukraine city of Donetsk, which was always pro-Russia and is now occupied by Russian forces. But when Russia invaded Ukraine in February 2022, the alleged leader of the notorious cybercrime gang — Vyacheslav Igoravich Andreev (a.ka. Penchukov) — fled his mandatory military service orders and was arrested in Geneva, Switzerland. He is currently in federal custody awaiting trial, and is slated to be arraigned in U.S. federal court tomorrow (Jan. 9, 2024). A copy of the indictment against Andreev is here (PDF).

Andreev, aka “Tank,” seen here performing as a DJ in Ukraine in an undated photo from social media.




Trend Micro Research has developed a go-to resource for all things related to cybercriminal underground hosting and infrastructure. Today we released the second in this three-part series of reports which detail the what, how, and why of cybercriminal hosting (see the first part here).
As part of this report, we dive into the common life cycle of a compromised server from initial compromise to the different stages of monetization preferred by criminals. It’s also important to note that regardless of whether a company’s server is on-premise or cloud-based, criminals don’t care what kind of server they compromise.
To a criminal, any server that is exposed or vulnerable is fair game.
Cloud vs. On-Premise Servers
Cybercriminals don’t care where servers are located. They can leverage the storage space, computation resources, or steal data no matter what type of server they access. Whatever is most exposed will most likely be abused.
As digital transformation continues and potentially picks up to allow for continued remote working, cloud servers are more likely to be exposed. Many enterprise IT teams, unfortunately, are not arranged to provide the same protection for cloud as on-premise servers.
As a side note, we want to emphasize that this scenario applies only to cloud instances replicating the storage or processing power of an on-premise server. Containers or serverless functions won’t fall victim to this same type of compromise. Additionally, if the attacker compromises the cloud account, as opposed to a single running instance, then there is an entirely different attack life cycle as they can spin up computing resources at will. Although this is possible, however, it is not our focus here.
Attack Red Flags
Many IT and security teams might not look for earlier stages of abuse. Before getting hit by ransomware, however, there are other red flags that could alert teams to the breach.
If a server is compromised and used for cryptocurrency mining (also known as cryptomining), this can be one of the biggest red flags for a security team. The discovery of cryptomining malware running on any server should result in the company taking immediate action and initiating an incident response to lock down that server.
This indicator of compromise (IOC) is significant because while cryptomining malware is often seen as less serious compared to other malware types, it is also used as a monetization tactic that can run in the background while server access is being sold for further malicious activity. For example, access could be sold for use as a server for underground hosting. Meanwhile, the data could be exfiltrated and sold as personally identifiable information (PII) or for industrial espionage, or it could be sold for a targeted ransomware attack. It’s possible to think of the presence of cryptomining malware as the proverbial canary in a coal mine: This is the case, at least, for several access-as-a-service (AaaS) criminals who use this as part of their business model.
Attack Life Cycle
Attacks on compromised servers follow a common path:
|
|

The monetization lifecycle of a compromised server
Often, targeted ransomware is the final stage. In most cases, asset categorization reveals data that is valuable to the business but not necessarily valuable for espionage.
A deep understanding of the servers and network allows criminals behind a targeted ransomware attack to hit the company where it hurts the most. These criminals would know the dataset, where they live, whether there are backups of the data, and more. With such a detailed blueprint of the organization in their hands, cybercriminals can lock down critical systems and demand higher ransom, as we saw in our 2020 midyear security roundup report.
In addition, while a ransomware attack would be the visible urgent issue for the defender to solve in such an incident, the same attack could also indicate that something far more serious has likely already taken place: the theft of company data, which should be factored into the company’s response planning. More importantly, it should be noted that once a company finds an IOC for cryptocurrency, stopping the attacker right then and there could save them considerable time and money in the future.
Ultimately, no matter where a company’s data is stored, hybrid cloud security is critical to preventing this life cycle.
The post The Life Cycle of a Compromised (Cloud) Server appeared first on .

If the first few months of 2020 have taught us anything, it’s the importance of collaboration and partnership to tackle a common enemy. This is true of efforts to fight the current pandemic, and it’s also true of the fight against cybercrime. That’s why Trend Micro has, over the years, struck partnerships with various organizations that share a common goal of securing our connected world.
So when we heard that one of these partners, the non-profit Shadowserver Foundation, was in urgent need of financial help, we didn’t hesitate to step in. Our new $600,000 commitment over three years will help to support the vital work it does collecting and sharing global threat data for the next three years.
What is Shadowserver?
Founded in 2004, The Shadowserver Foundation is now one of the world’s leading resources for reporting vulnerabilities, threats and malicious activity. Their work has helped to pioneer a more collaborative approach among the international cybersecurity community, from vendors and academia to governments and law enforcement.
Today, its volunteers, 16 full-time staff and global infrastructure of sinkholes, honeypots and honeyclients help run 45 scans across 4 billion IPv4 addresses every single day. It also performs daily sandbox scans on 713,000 unique malware samples, to add to the 12 Petabytes of malware and threat intelligence already stored on its servers. Thousands of network owners, including 109 CSIRTS in 138 countries worldwide, rely on the resulting daily reports — which are available free of charge to help make the digital world a safer place.
A Global Effort
Trend Micro is a long-time partner of The Shadowserver Foundation. We automatically share new malware samples via its malware exchange program, with the end goal of improving protection for both Trend Micro customers and Shadowserver subscribers around the world. Not only that, but we regularly collaborate on global law enforcement-led investigations. Our vision and mission statements of working towards a more secure, connected world couldn’t be more closely aligned.
As COVID-19 has brutally illustrated, protecting one’s own backyard is not enough to tackle a global challenge. Instead, we need to reach out and build alliances to take on the threats and those behind them, wherever they are. These are even more pronounced at a time when remote working has dramatically expanded the corporate attack surface, and offered new opportunities for the black hats to prosper by taking advantage of distracted employees and stretched security teams.
The money Trend Micro has donated over the next three years will help the Shadowserver Foundation migrate to the new data center it urgently needs and support operational costs that combined will exceed $2 million in 2020. We wish the team well with their plans for this year.
It’s no exaggeration to say that our shared digital world is a safer place today because of their efforts, and we hope to continue to collaborate long into the future
The post Securing the Connected World with Support for The Shadowserver Foundation appeared first on .

By Kyle Klassen Product Manager – Cloud Native Application Security at Trend Micro
Containers provide many great benefits to organizations – they’re lightweight, flexible, add consistency across different environments and scale easily.
One of the characteristics of containers is that they run in dedicated namespaces with isolated resource requirements. General purpose OS’s deployed to run containers might be viewed as overkill since many of their features and interfaces aren’t needed.
A key tenant in the cybersecurity doctrine is to harden platforms by exposing only the fewest number of interfaces and applying the tightest configurations required to run only the required operations.
Developers deploying containers to restricted platforms or “serverless” containers to the likes of AWS Fargate for example, should think about security differently – by looking upward, looking left and also looking all-around your cloud domain for opportunities to properly security your cloud native applications. Oh, and don’t forget to look outside. Let me explain…
Looking Upward
As infrastructure, OS, container orchestration and runtimes become the domain of the cloud provider, the user’s primary responsibility becomes securing the containers and applications themselves. This is where Trend Micro Cloud One , a security services platform for cloud builders, can help Dev and Ops teams better implement build pipeline and runtime security requirements. Cloud One – Application Security embeds a security library within the application itself to provide defense against web application attacks and to detect malicious activity.
, a security services platform for cloud builders, can help Dev and Ops teams better implement build pipeline and runtime security requirements. Cloud One – Application Security embeds a security library within the application itself to provide defense against web application attacks and to detect malicious activity.
One of the greatest benefits of this technology is that once an application is secured in this manner, it can be deployed anywhere and the protection comes along for the ride. Users can be confident their applications are secure whether deployed in a container on traditional hosts, into EKS on AWS Bottlerocket, serverless on AWS Fargate, or even as an AWS Lambda function!
Looking Left
It’s great that cloud providers are taking security seriously and providing increasingly secure environments within which to deploy your containers. But you need to make sure your containers themselves are not introducing security risks. This can be accomplished with container image scanning to identify security issues before these images ever make it to the production environment.
Enter Deep Security Smart Check – Container Image Scanning part of the Cloud One offering. Scans must be able to detect more than just vulnerabilities. Developer reliance on code re-use, public images, and 3rd party contributions mean that malware injection into private images is a real concern. Sensitive objects like secrets, keys and certificates must be found and removed and assurance against regulatory requirements like PCI, HIPAA or NIST should be a requirement before a container image is allowed to run.
Looking All-Around
Imagine taking the effort to ensure your applications, containers and functions are built securely, comply with strict security regulations and are deployed into container optimized cloud environments only to find out that you’ve still become a victim of an attack! How could this be? Well, one common oversight is recognizing the importance of disciplined configuration and management of the cloud resources themselves – you can’t assume they’re secure just because they’re working.
But, making sure your cloud services are secure can be a daunting task – likely comprised of dozens of cloud services, each with as many configuration options – these environments are complex. Cloud One – Conformity is your cloud security companion and gives you assurance that any hidden security issues with your cloud configurations are detected and prioritized. Disabled security options, weak keys, open permissions, encryption options, high-risk exposures and many, many more best practice security rules make it easy to conform to security best practices and get the most from your cloud provider services.
Look Outside
All done? Not quite. You also need to think about how the business workflows of your cloud applications ingest files (or malware?). Cloud storage like S3 Buckets are often used to accept files from external customers and partners. Blindly accepting uploads and pulling them into your workflows is an open door for attack.
Cloud One – File Storage Security incorporates Trend Micro’s best-in-class malware detection technology to identify and remove files infected with malware. As a cloud native application itself, the service deploys easily with deployment templates and runs as a ‘set and forget’ service – automatically scanning new files of any type, any size and automatically removing malware so you can be confident that all of your downstream workflows are protected.
It’s still about Shared Responsibility
Cloud providers will continue to offer security features for deploying cloud native applications – and you should embrace all of this capability. However, you can’t assume your cloud environment is optimally secure without validating your configurations. And once you have a secure environment, you need to secure all of the components within your control – your functions, applications, containers and workflows. With this practical approach, Trend Micro Cloud One perfectly complements your cloud services with Network Security, Workload Security, Application Security, Container Security, File Storage Security and Conformity for cloud posture management, so you can be confident that you’ve got security covered no matter which way you look.
perfectly complements your cloud services with Network Security, Workload Security, Application Security, Container Security, File Storage Security and Conformity for cloud posture management, so you can be confident that you’ve got security covered no matter which way you look.
To learn more visit Trendmicro.com/CloudOne and join our webinar on cloud native application threats https://resources.trendmicro.com/Cloud-One-Webinar-Series-Cloud-Native-Application-Threats.html
The post What do serverless compute platforms mean for security? appeared first on .